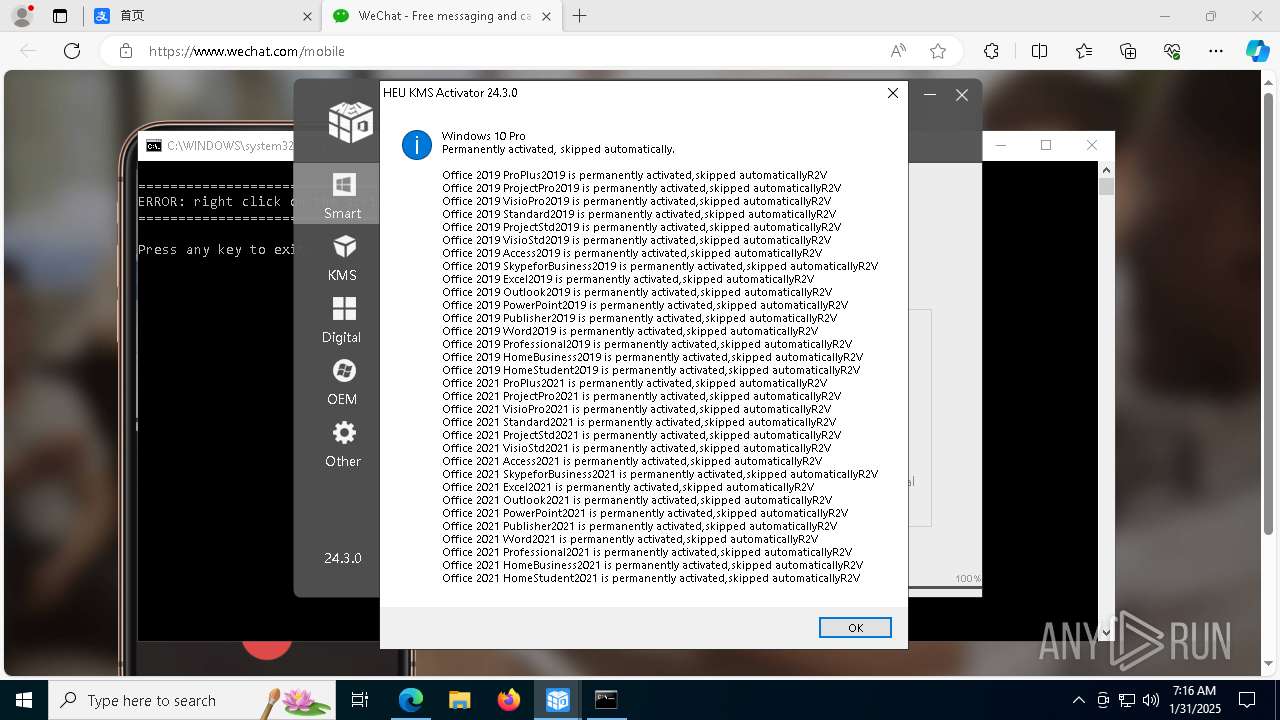
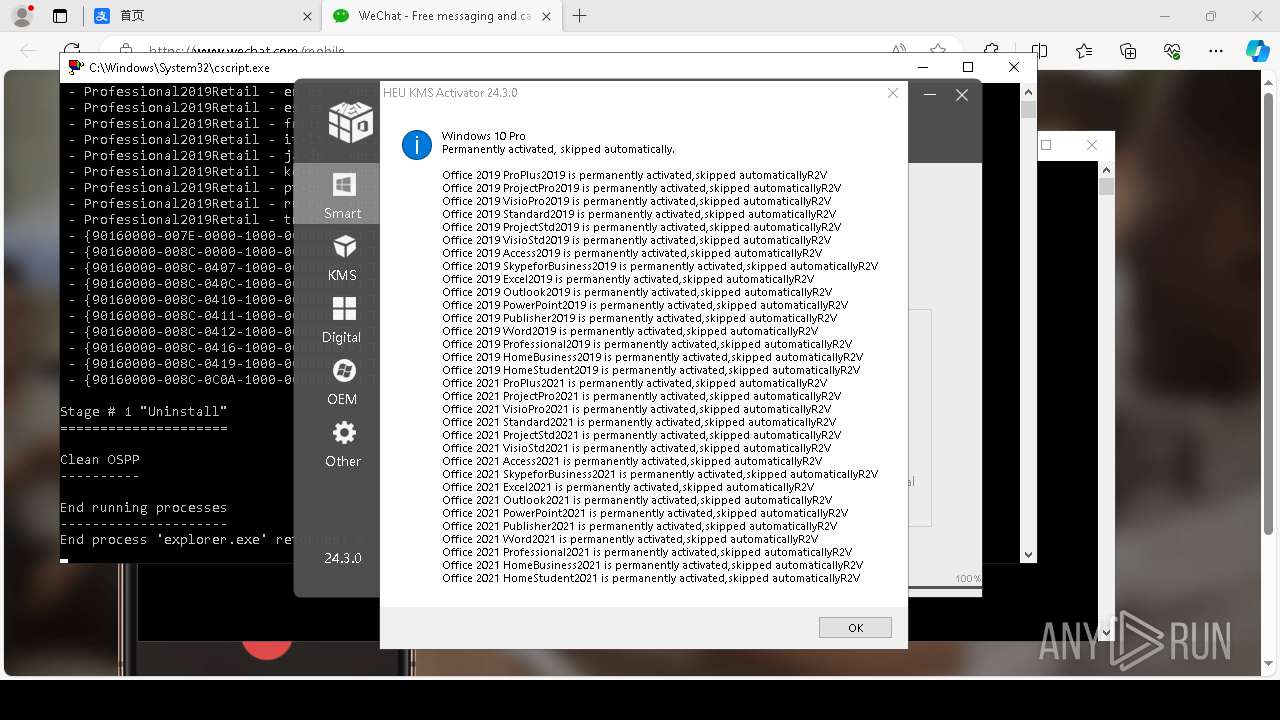
| File name: | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc |
| Full analysis: | https://app.any.run/tasks/84cd6584-fa7c-4796-94e5-b4284d717cbe |
| Verdict: | Malicious activity |
| Analysis date: | January 31, 2025, 07:15:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 9B9C750F54EB7C04F4BA88C14471BA0B |
| SHA1: | 073B1FA97DEE9A3BA13CDD3CF43768536F3B31B9 |
| SHA256: | 2A26951FBE02A3083CC0D22741301018C69ABD88556D67941DECFB6F1BFB9DDC |
| SSDEEP: | 98304:rat/0SdpmYs/Nf4HhSjrckztFmG5Zmy+XerxuU3uvm3A2c8DwRosU/jxKa359bh7:1v7/lq6uDbqOfE |
MALICIOUS
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 3092)
- cmd.exe (PID: 5720)
- cmd.exe (PID: 3436)
- cmd.exe (PID: 6772)
- cmd.exe (PID: 6444)
SUSPICIOUS
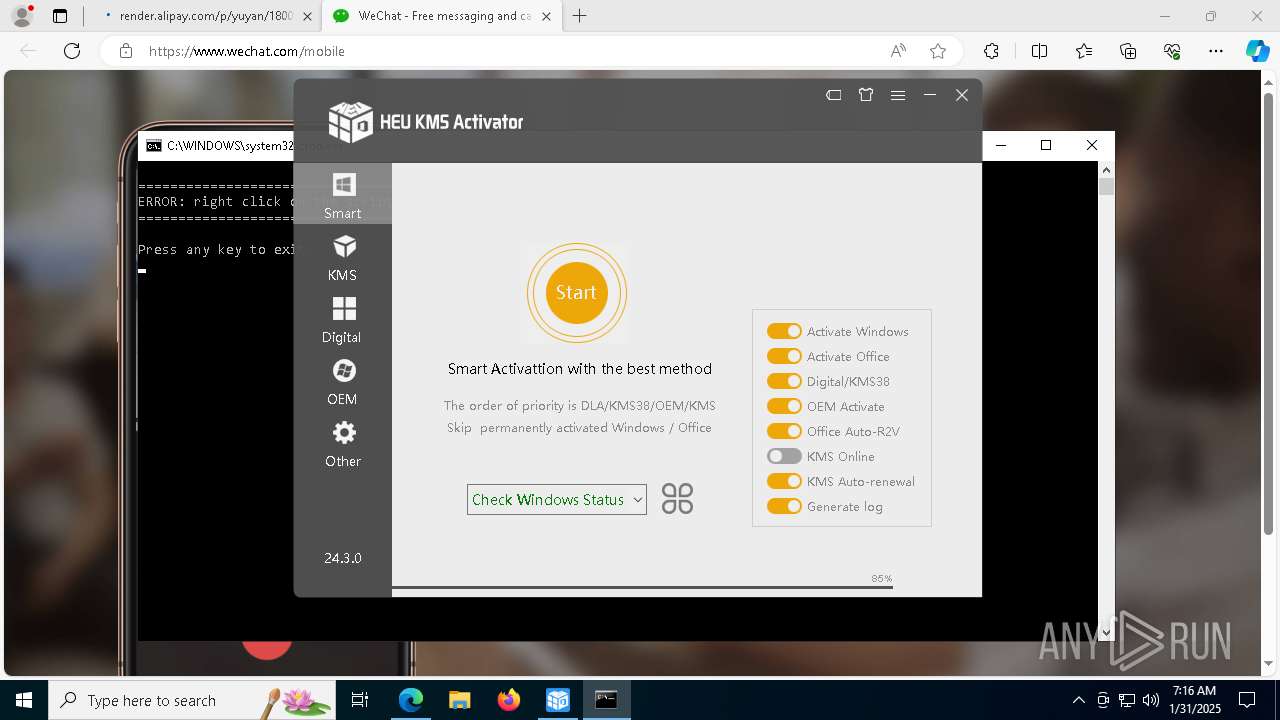
Starts CMD.EXE for commands execution
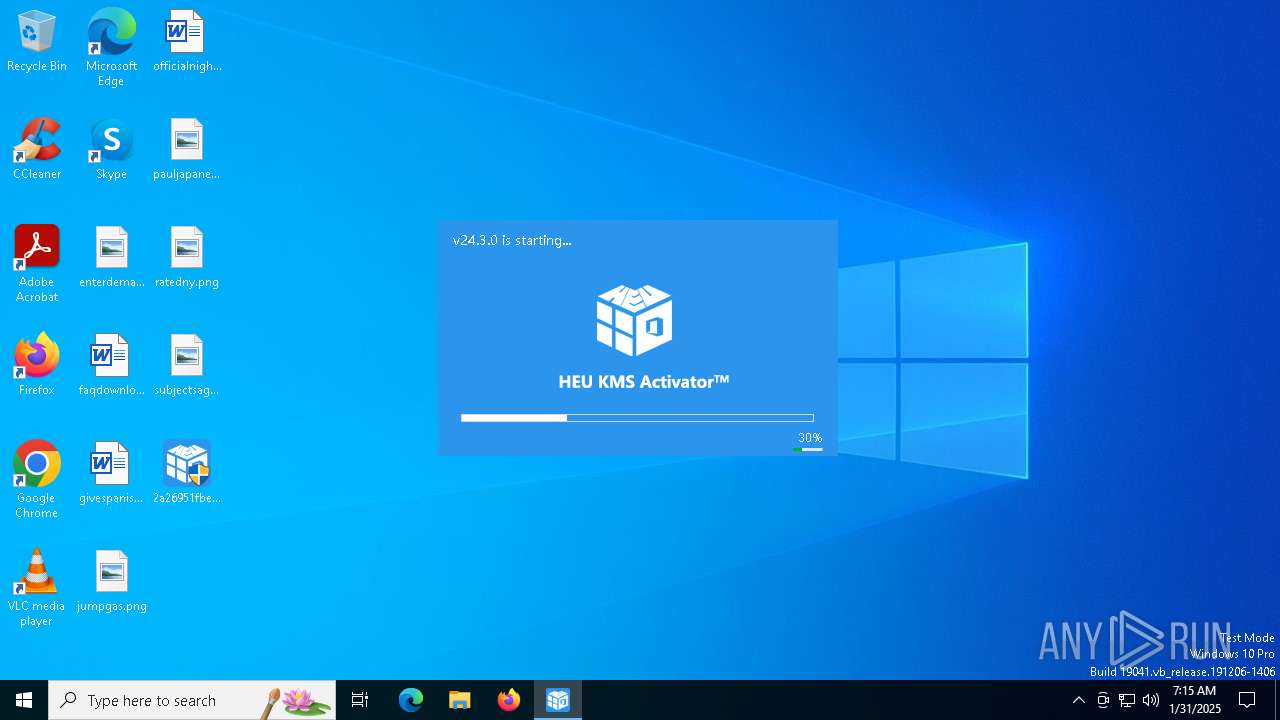
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- kms_x64.exe (PID: 4672)
Executable content was dropped or overwritten
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- 7Z.EXE (PID: 5732)
- kms_x64.exe (PID: 4672)
Process drops legitimate windows executable
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- 7Z.EXE (PID: 5732)
Drops 7-zip archiver for unpacking
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
Detected use of alternative data streams (AltDS)
- kms_x64.exe (PID: 4672)
There is functionality for taking screenshot (YARA)
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
Found strings related to reading or modifying Windows Defender settings
- kms_x64.exe (PID: 4672)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 1804)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 5236)
- cmd.exe (PID: 5572)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 2212)
- cmd.exe (PID: 3928)
Starts SC.EXE for service management
- cmd.exe (PID: 6208)
- cmd.exe (PID: 6748)
- cmd.exe (PID: 6908)
Windows service management via SC.EXE
- sc.exe (PID: 6808)
- sc.exe (PID: 6392)
- sc.exe (PID: 6972)
Lists all scheduled tasks
- schtasks.exe (PID: 7060)
- schtasks.exe (PID: 7148)
INFO
Reads mouse settings
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- kms_x64.exe (PID: 4672)
The sample compiled with chinese language support
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- 7Z.EXE (PID: 5732)
Reads the computer name
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- 7Z.EXE (PID: 5732)
- kms_x64.exe (PID: 4672)
- kms-server.exe (PID: 6836)
- SetACL.exe (PID: 6976)
- SetACL.exe (PID: 6240)
- SetACL.exe (PID: 6304)
- SetACL.exe (PID: 7080)
- SetACL.exe (PID: 6868)
- SetACL.exe (PID: 5540)
- SetACL.exe (PID: 7100)
- SetACL.exe (PID: 7056)
- SetACL.exe (PID: 6572)
- SetACL.exe (PID: 6760)
- SetACL.exe (PID: 6692)
Create files in a temporary directory
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- kms_x64.exe (PID: 4672)
Checks supported languages
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- 7Z.EXE (PID: 5732)
- kms_x64.exe (PID: 4672)
- kms-server.exe (PID: 6836)
- SetACL.exe (PID: 6240)
- SetACL.exe (PID: 6304)
- SetACL.exe (PID: 6572)
- SetACL.exe (PID: 6868)
- SetACL.exe (PID: 5540)
- SetACL.exe (PID: 7080)
- SetACL.exe (PID: 7100)
- SetACL.exe (PID: 6976)
- SetACL.exe (PID: 7056)
- SetACL.exe (PID: 6760)
- SetACL.exe (PID: 6692)
- SetACL.exe (PID: 5572)
Reads Environment values
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- kms_x64.exe (PID: 4672)
The sample compiled with english language support
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
- 7Z.EXE (PID: 5732)
Checks operating system version
- kms_x64.exe (PID: 4672)
The process uses AutoIt
- 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe (PID: 3816)
Reads product name
- kms_x64.exe (PID: 4672)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2600)
- WMIC.exe (PID: 3688)
- WMIC.exe (PID: 6684)
- WMIC.exe (PID: 6792)
- WMIC.exe (PID: 4500)
Manual execution by a user
- msedge.exe (PID: 848)
Application launched itself
- msedge.exe (PID: 848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (49.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.7) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.8) |
| .exe | | | Win32 Executable (generic) (5.3) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:15 16:12:24+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 581120 |
| InitializedDataSize: | 7118848 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27f4a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 24.3.0.0 |
| ProductVersionNumber: | 3.3.14.2 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 24.3.0.0 |
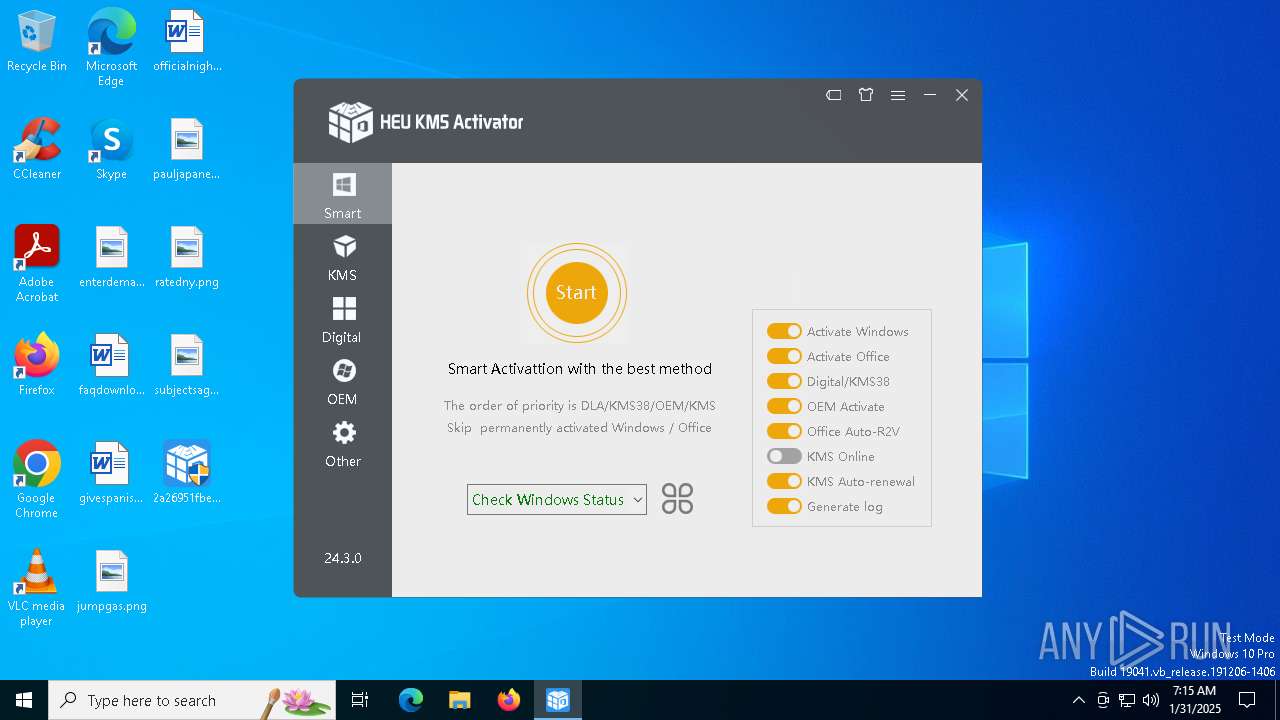
| Comments: | KMS/数字权利/KMS38/OEM激活 |
| FileDescription: | HEU KMS Activator™ |
| ProductVersion: | 3.3.14.2 |
| LegalCopyright: | ©2012-2021 www.heu8.com & 知彼而知己 |
| Productname: | HEU KMS Activator |
| CompanyName: | 知彼而知己 |
| OriginalFileName: | HEU_KMS_Activator_v24.3.0 |
| InternalName: | HEU_KMS_Activator_v24.3.0 |
Total processes
237
Monitored processes
120
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | icacls C:\WINDOWS\System32\SppExtComObjHook.dll /reset | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
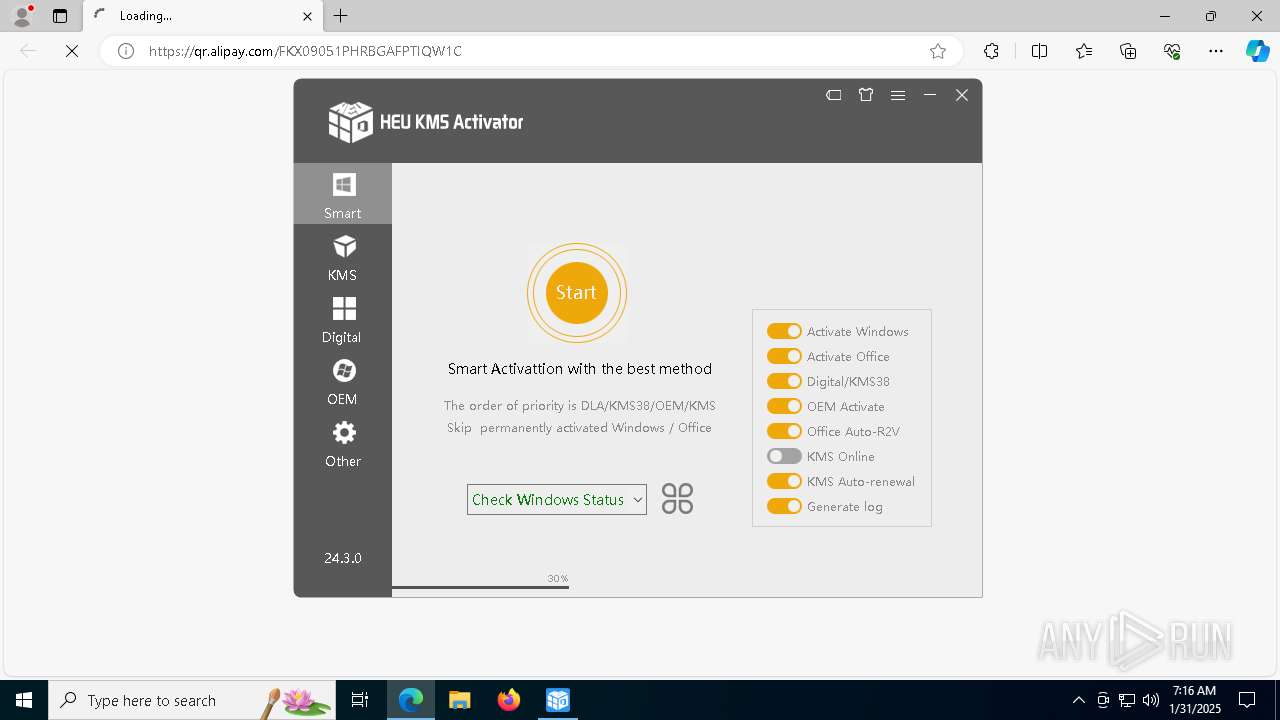
| 848 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" HTTPS://QR.ALIPAY.COM/FKX09051PHRBGAFPTIQW1C | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1688 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | schtasks /delete /f /tn "\Microsoft\Windows\SoftwareProtectionPlatform\SvcTrigger" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | C:\WINDOWS\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\Sysnative;%SystemRoot%\Sysnative\Wbem;%SystemRoot\Sysnative\WindowsPowerShell\v1.0\" & echo Name=2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe >>%windir%\_tempheukms01310715545773\ScriptDir.ini | C:\Windows\SysWOW64\cmd.exe | — | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2212 | C:\WINDOWS\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\system32;%SystemRoot%\System32\Wbem;%SystemRoot\System32\WindowsPowerShell\v1.0\" & netsh advfirewall firewall delete rule name="heu-kms-SppExtComObjHook" > %windir%\HeuKmsLog\advfirewall.log | C:\Windows\System32\cmd.exe | — | kms_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2412 | C:\WINDOWS\system32\cmd.exe /c echo Temp=_tempheukms01310715545773 >>%windir%\ScriptTemp.ini | C:\Windows\SysWOW64\cmd.exe | — | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Remove ExclusionPath="C:\WINDOWS\_tempheukms01310715545773\x86\SppExtComObjHook.dll" Force=True | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2788 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 906
Read events
5 844
Write events
12
Delete events
50
Modification events
| (PID) Process: | (848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (848) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 62D6C099918B2F00 | |||
| (PID) Process: | (848) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\66474 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {2D6F0CFB-330C-492C-8E9F-2C76E1482B4E} | |||
| (PID) Process: | (848) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B23FC799918B2F00 | |||
| (PID) Process: | (4672) kms_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\OfficeSoftwareProtectionPlatform\59a52881-a989-479d-af46-f275c6370663 |
| Operation: | write | Name: | test |
Value: test | |||
| (PID) Process: | (4672) kms_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\OfficeSoftwareProtectionPlatform\59a52881-a989-479d-af46-f275c6370663 |
| Operation: | delete value | Name: | test |
Value: test | |||
| (PID) Process: | (4672) kms_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\OfficeSoftwareProtectionPlatform\59a52881-a989-479d-af46-f275c6370663 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
28
Suspicious files
202
Text files
225
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3816 | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | C:\Users\admin\AppData\Local\Temp\aut7A56.tmp | compressed | |
MD5:CAF71EB57C23CE0D6703414893AED947 | SHA256:7541EC02A4CBD62690D9AEB06D922A7382BCBFD7D17578A9B69CFF3868B096DA | |||
| 3544 | cmd.exe | C:\Windows\ScriptTemp.ini | text | |
MD5:C999B467EE495F6EFFD312BA405D77B0 | SHA256:7CB0B3D2B9D157FBF86A7A882EDB46B5B1B3D1936E21DD1254F9BAFC9FD07D03 | |||
| 3816 | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | C:\Windows\_tempheukms01310715545773\DigitalLicence.7z | compressed | |
MD5:1843AB0C616447ADA3A452F01BC0DF8E | SHA256:67B0363A14716D81A7322F229B634FFA61161F80260D0E0C16AF5A18BBAE2B91 | |||
| 3816 | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | C:\Users\admin\AppData\Local\Temp\aut797A.tmp | compressed | |
MD5:DAFADDFEB8FDE0B9EF6983D12E691BA5 | SHA256:CF31601E36EE52BEB730549C772E7DB4B9BF605F2C08C32479EF39E94AA71B18 | |||
| 3816 | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | C:\Windows\_tempheukms01310715545773\7Z.EXE | executable | |
MD5:43141E85E7C36E31B52B22AB94D5E574 | SHA256:EA308C76A2F927B160A143D94072B0DCE232E04B751F0C6432A94E05164E716D | |||
| 3816 | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | C:\Users\admin\AppData\Local\Temp\aut7B03.tmp | compressed | |
MD5:1843AB0C616447ADA3A452F01BC0DF8E | SHA256:67B0363A14716D81A7322F229B634FFA61161F80260D0E0C16AF5A18BBAE2B91 | |||
| 3816 | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | C:\Windows\_tempheukms01310715545773\cert.7z | compressed | |
MD5:5FFD2C6DC5DC2DC07FE5CD45448061F1 | SHA256:7FD98AAB6BAC7B6264B2EF3BA7818C0521EF02793631F9D23E28929804BAB325 | |||
| 3816 | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | C:\Users\admin\AppData\Local\Temp\aut7B33.tmp | compressed | |
MD5:FF22E900312029C25D6ECD5FB3582601 | SHA256:D3408CA5C70EB0CB054236E46A9D49E18D2DC589E2ECAB16E6C77578EA52F188 | |||
| 3816 | 2a26951fbe02a3083cc0d22741301018c69abd88556d67941decfb6f1bfb9ddc.exe | C:\Users\admin\AppData\Local\Temp\aut7B63.tmp | binary | |
MD5:E25E09DF3DB990F98A165990B2F48B02 | SHA256:52F64C84948068514240283D6C7FA1204E81CA0549CF0159FCACC556A950CD94 | |||
| 5732 | 7Z.EXE | C:\Windows\_tempheukms01310715545773\HEU_Set.ini | text | |
MD5:5251BE66B4B2D836E6ECF183A3AE83E6 | SHA256:EAED66F92EBDCC94DCF567A7E20ECFF799751DED4CF563DC633C5BC13CFE3DC7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
185
TCP/UDP connections
91
DNS requests
87
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | — | — | unknown |
— | — | GET | 302 | 110.76.30.76:443 | https://mobilecodec.alipay.com/client_download.htm?qrcode=FKX09051PHRBGAFPTIQW1C | unknown | — | — | unknown |
— | — | GET | 304 | 13.107.21.239:443 | https://edge.microsoft.com/abusiveadblocking/api/v1/blocklist | unknown | — | — | unknown |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/work/api/v2/tenant/my/settingswithflights?&clienttype=edge-omnibox | unknown | binary | 591 b | whitelisted |
— | — | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v1/Edge/122.0.2365.59?clientId=4489578223053569932&agents=EdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=44&mngd=0&installdate=1661339457&edu=0&bphint=2&soobedate=1504771245&fg=1 | unknown | binary | 768 b | whitelisted |
— | — | GET | 200 | 13.107.21.239:443 | https://edge.microsoft.com/serviceexperimentation/v3/?osname=win&channel=stable&osver=10.0.19045&devicefamily=desktop&installdate=1661339457&clientversion=122.0.2365.59&experimentationmode=2&scpguard=0&scpfull=0&scpver=0 | unknown | binary | 762 b | whitelisted |
— | — | GET | 200 | 43.129.254.124:443 | https://weixin.qq.com/r/XUx3b67EqPPXreoM9xlP | unknown | html | 544 b | whitelisted |
— | — | OPTIONS | 504 | 23.50.131.74:443 | https://bzib.nelreports.net/api/report?cat=bingbusiness | unknown | html | 280 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3976 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3952 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
848 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.baidu.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
qr.alipay.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |