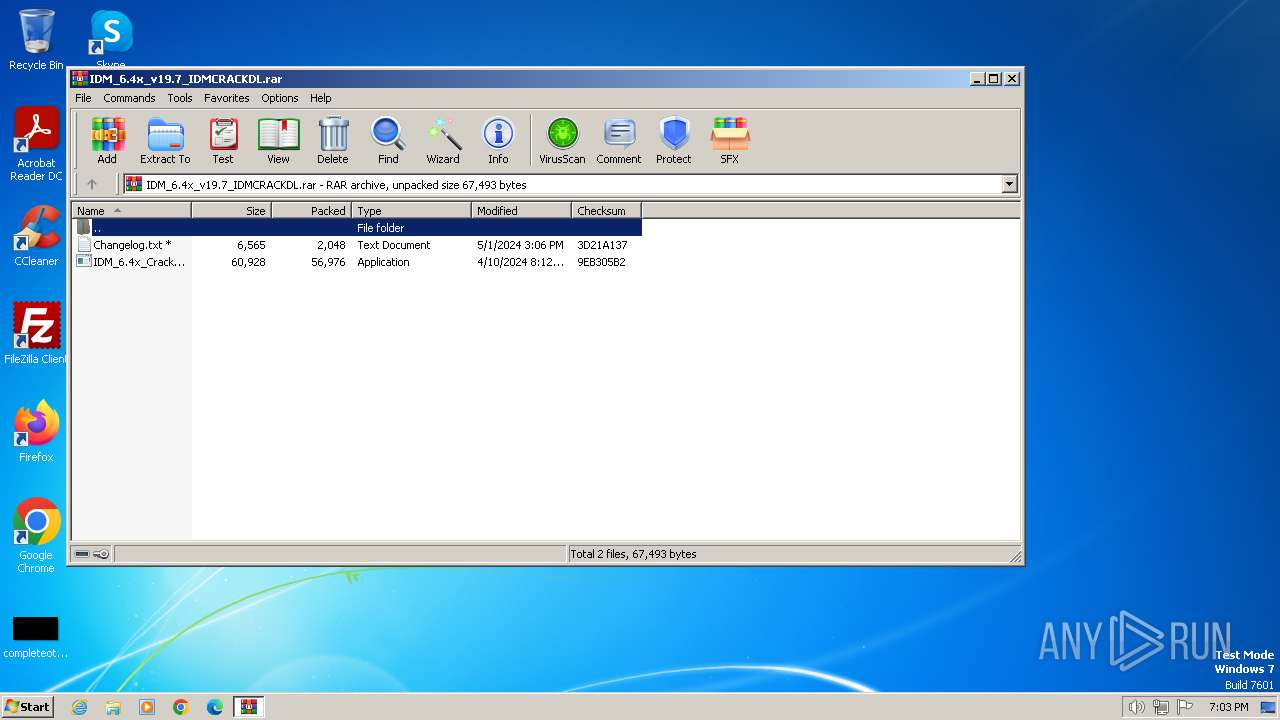
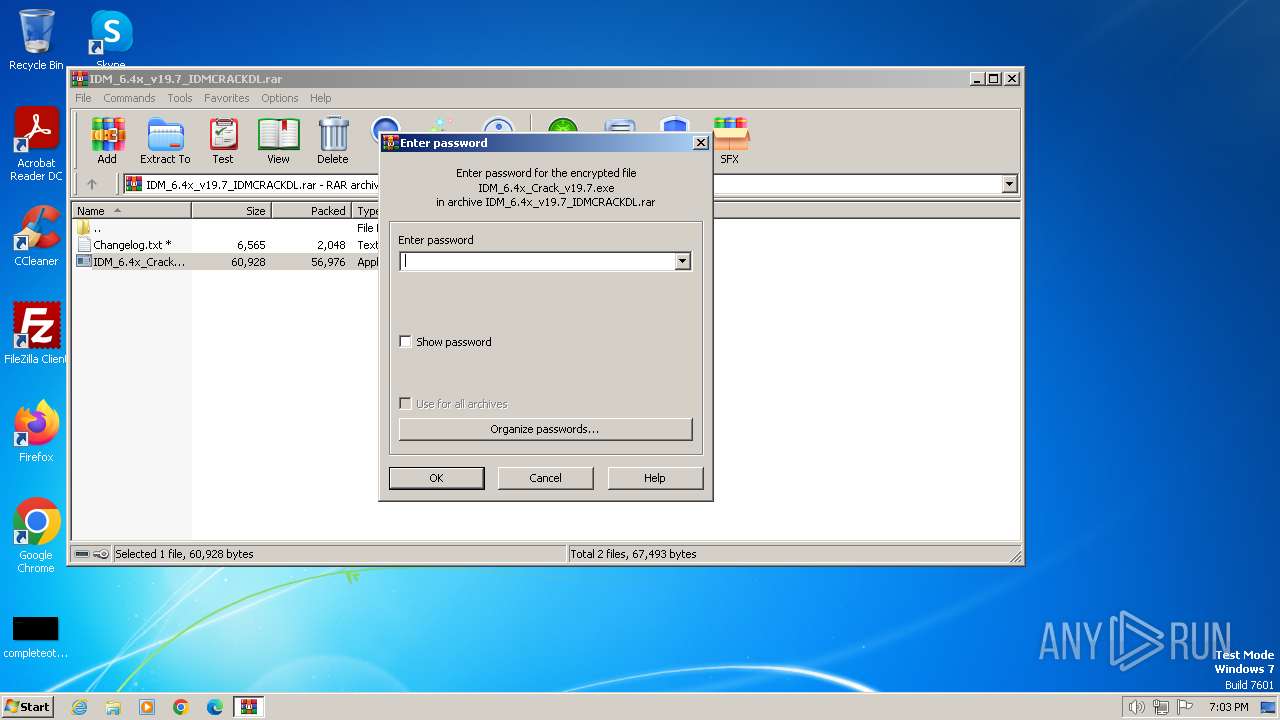
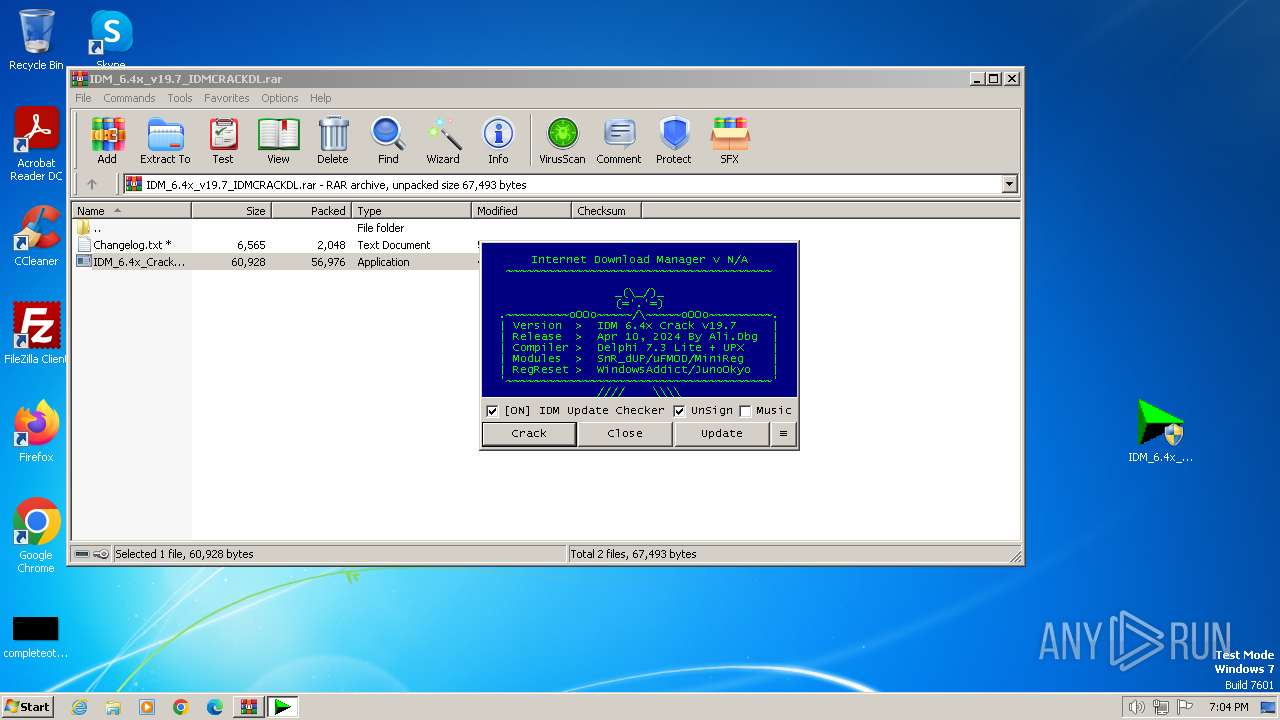
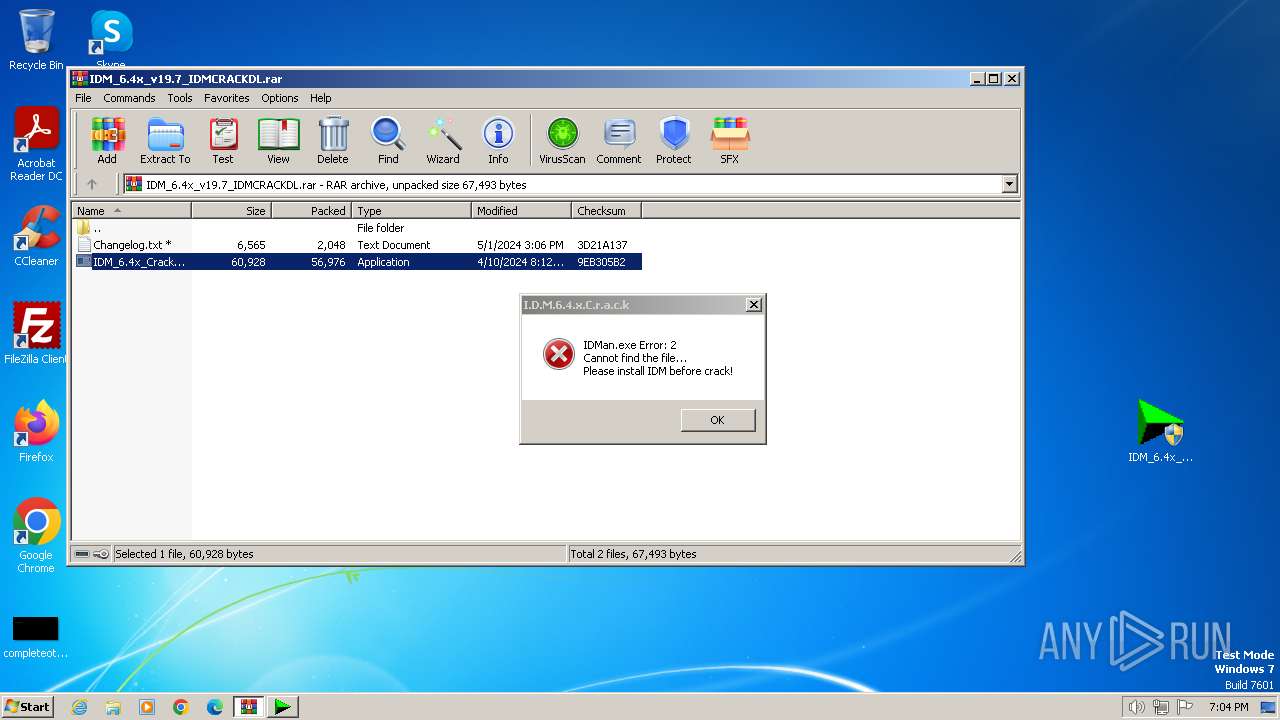
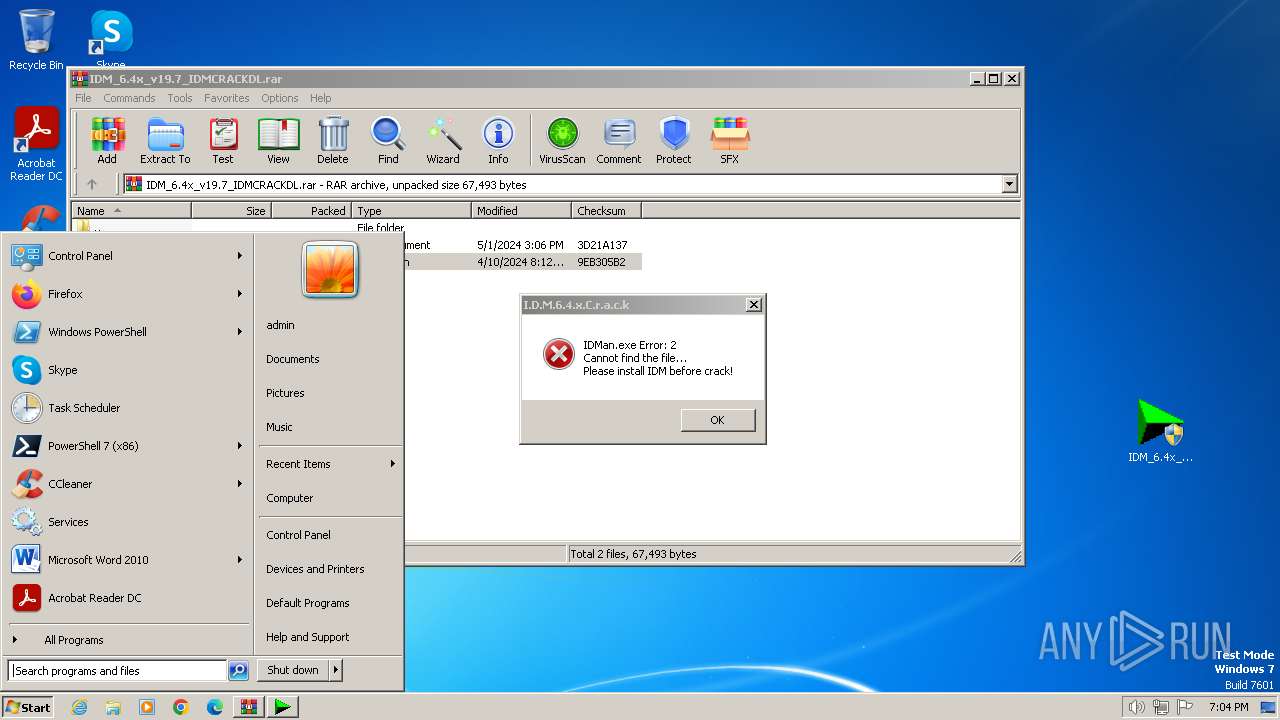
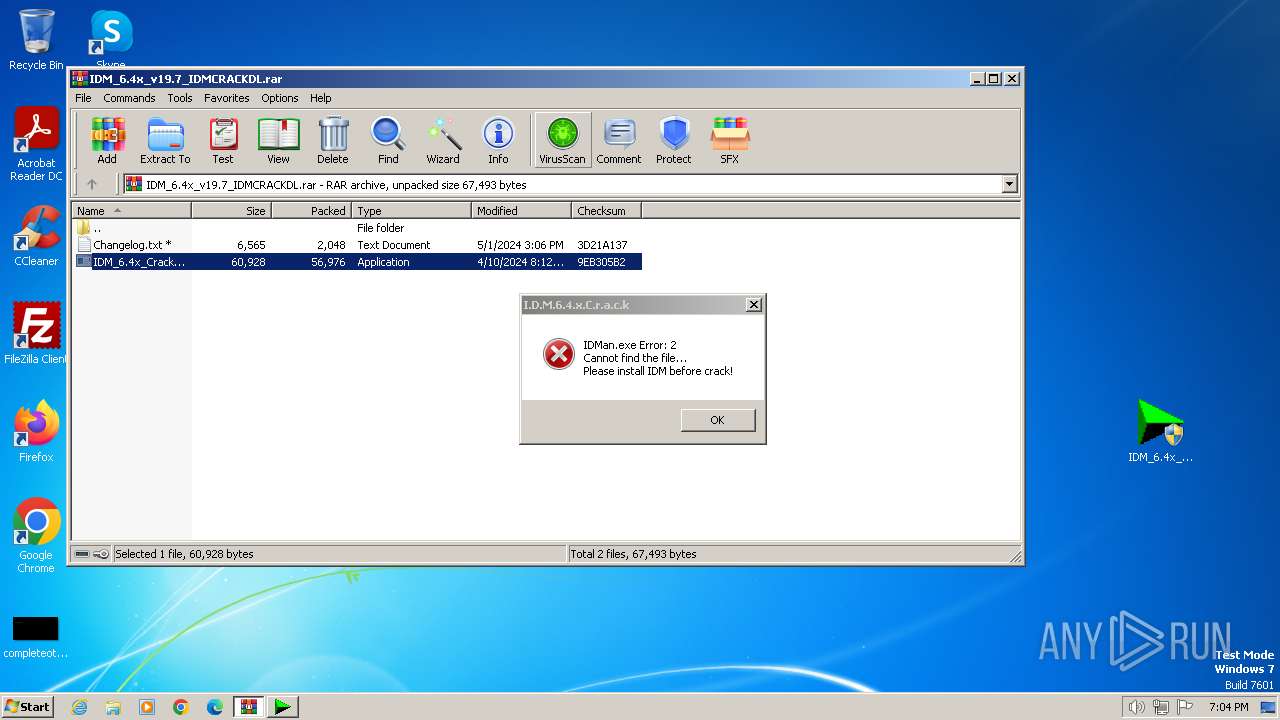
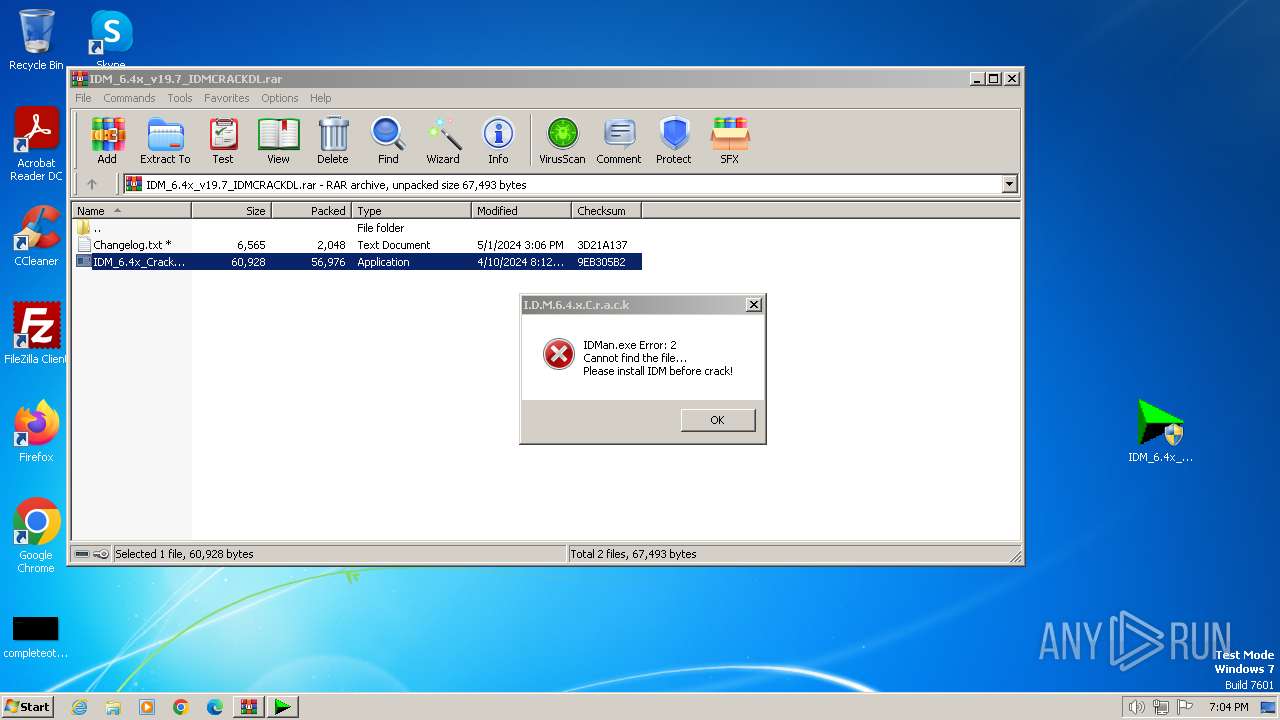
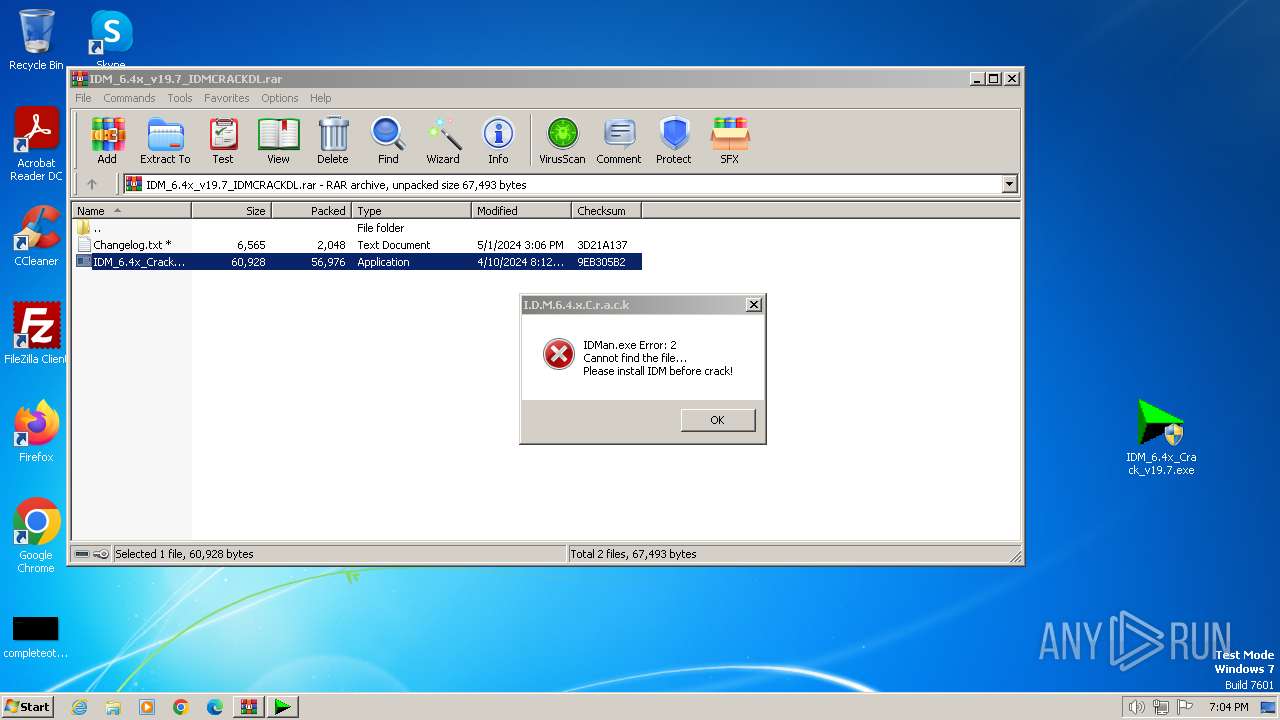
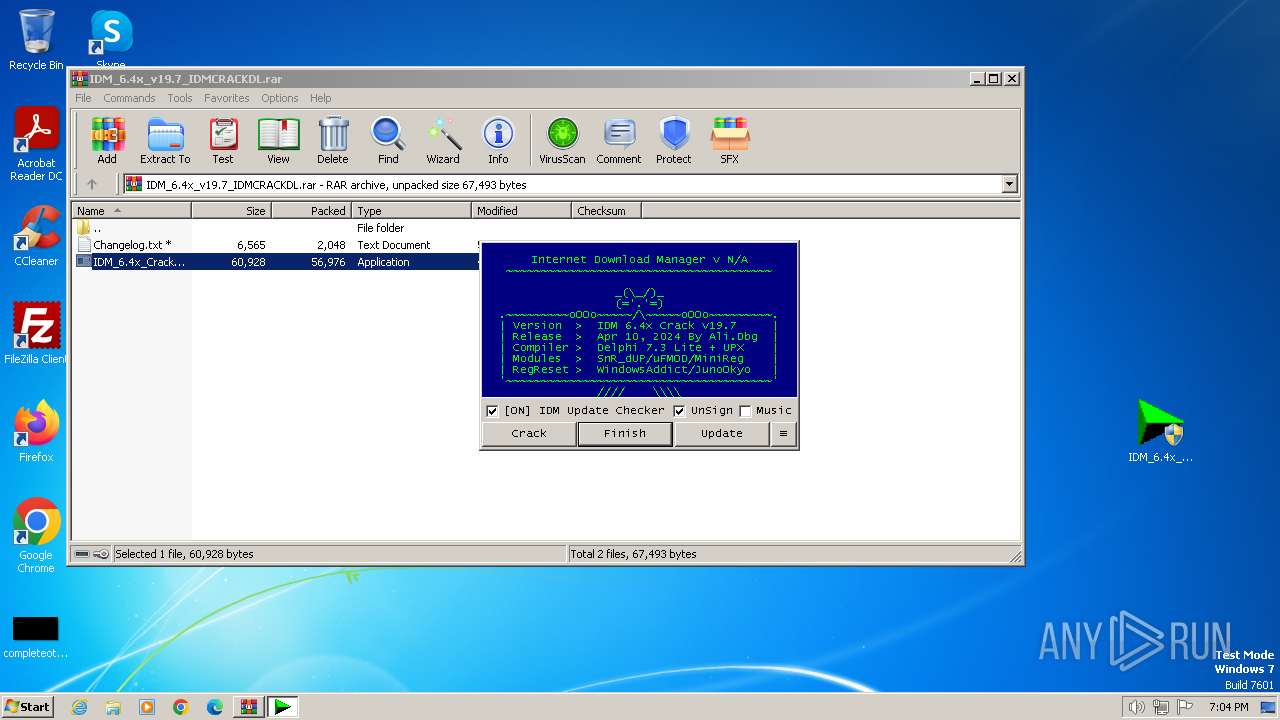
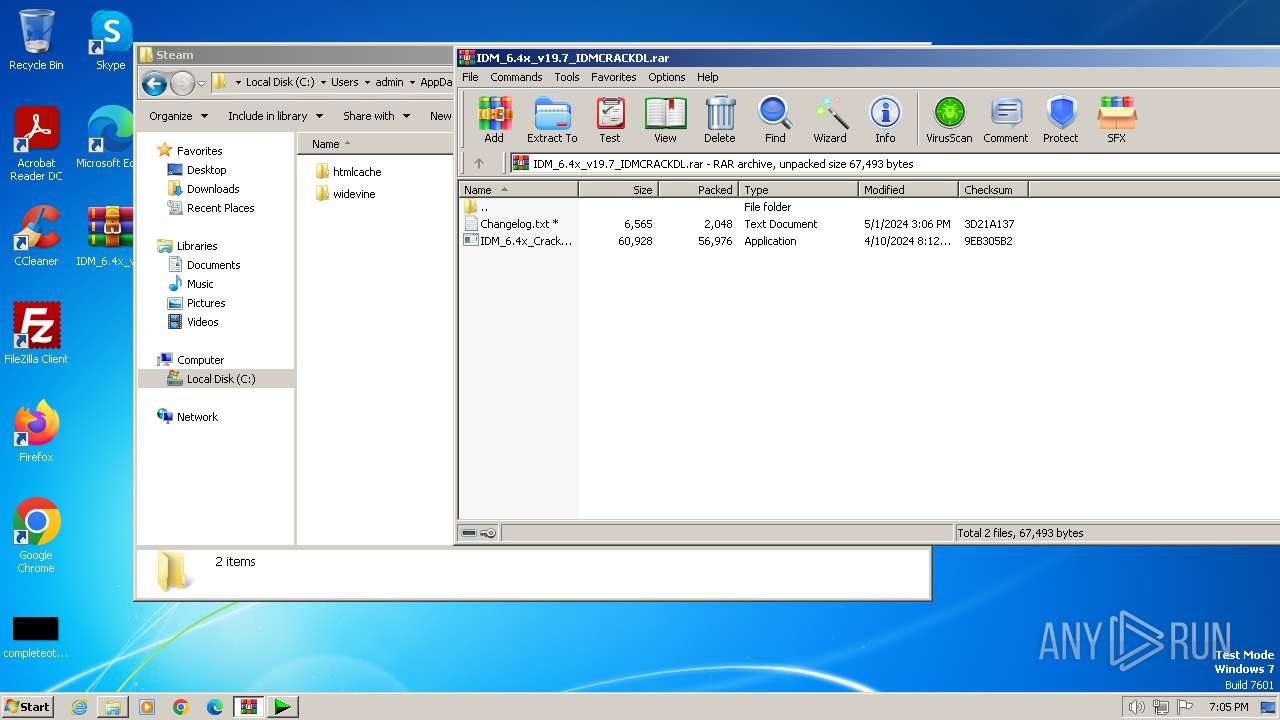
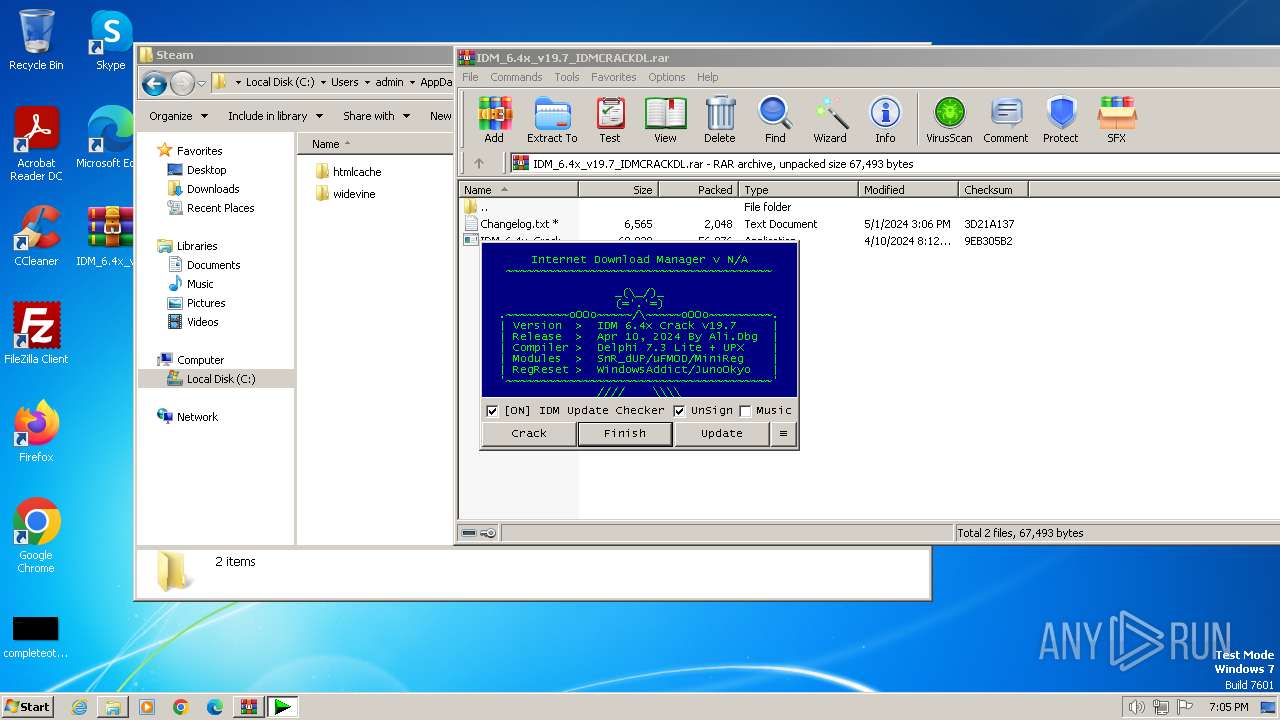
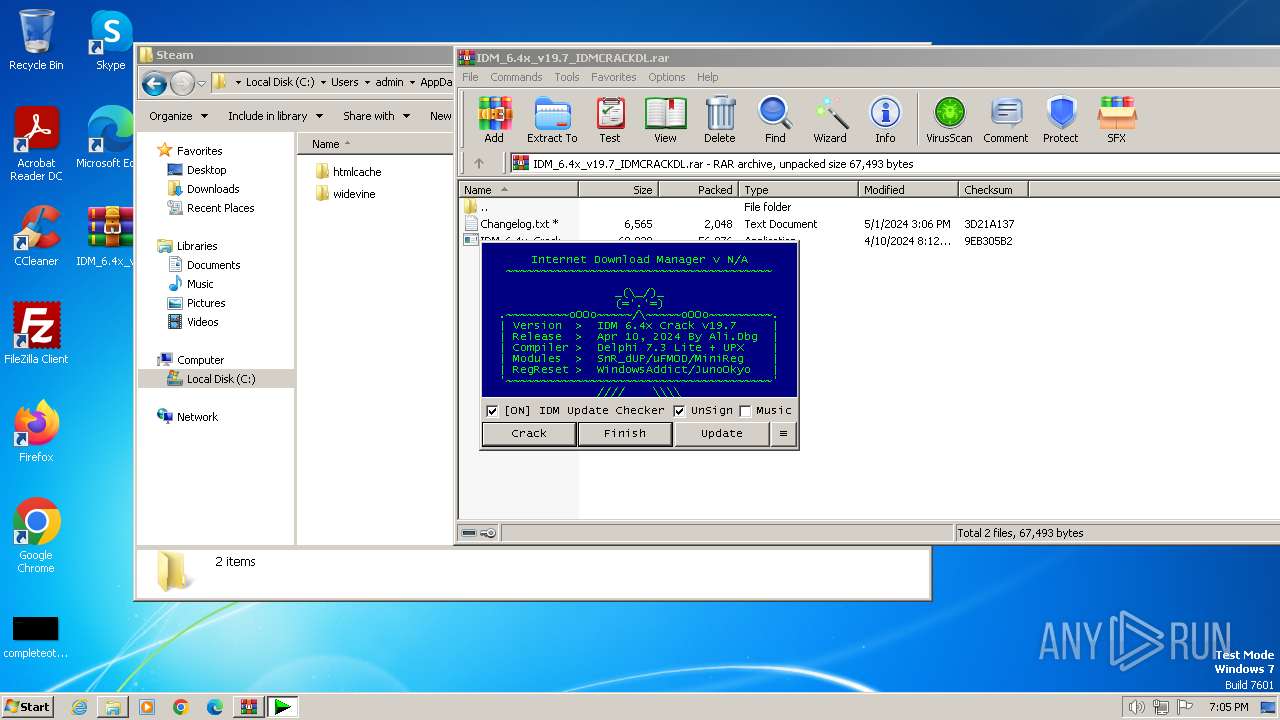
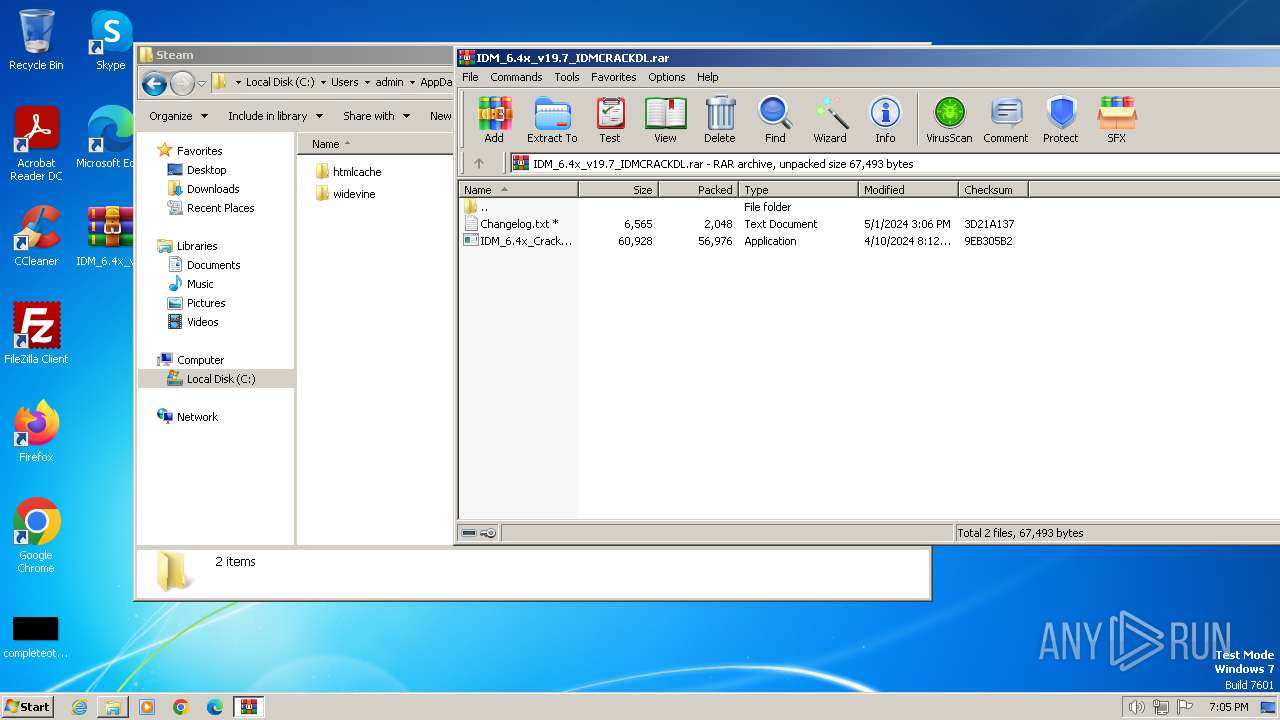
| File name: | IDM_6.4x_v19.7_IDMCRACKDL.rar |
| Full analysis: | https://app.any.run/tasks/3d4f8f56-d685-4257-a575-913f86395993 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2024, 18:03:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E6CC62A826B0F78E45D4902339453CA5 |
| SHA1: | B7E666DF90757DD8C42802B077F32B9E94F9976F |
| SHA256: | 2A1FC528F72C1AAF624B673E74AD866CB49386B7F5DFE03B273CB963ABB0394F |
| SSDEEP: | 1536:9mrqxTDSZMgwlrftmNkWSM79NJ57IrQ2o3PvYUZM4:9mmxTDZr2kyZXFIrQjnYMD |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- cmd.exe (PID: 740)
- cmd.exe (PID: 3176)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 740)
- IDM_6.4x_Crack_v19.7.exe (PID: 2940)
- cmd.exe (PID: 3176)
Executing commands from a ".bat" file
- cmd.exe (PID: 740)
- IDM_6.4x_Crack_v19.7.exe (PID: 2940)
- cmd.exe (PID: 3176)
Uses REG/REGEDIT.EXE to modify registry
- IDM_6.4x_Crack_v19.7.exe (PID: 2940)
- cmd.exe (PID: 2000)
- cmd.exe (PID: 740)
- cmd.exe (PID: 2720)
- cmd.exe (PID: 3176)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 740)
- cmd.exe (PID: 3920)
- cmd.exe (PID: 4036)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 3648)
- cmd.exe (PID: 3936)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 740)
- cmd.exe (PID: 3176)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 740)
- cmd.exe (PID: 3176)
Hides command output
- cmd.exe (PID: 3920)
- cmd.exe (PID: 2000)
- cmd.exe (PID: 2720)
- cmd.exe (PID: 3936)
Starts application with an unusual extension
- cmd.exe (PID: 740)
- cmd.exe (PID: 3176)
INFO
Create files in a temporary directory
- IDM_6.4x_Crack_v19.7.exe (PID: 2940)
- reg.exe (PID: 2032)
- reg.exe (PID: 2756)
Manual execution by a user
- IDM_6.4x_Crack_v19.7.exe (PID: 3200)
- IDM_6.4x_Crack_v19.7.exe (PID: 2940)
- explorer.exe (PID: 952)
- wmpnscfg.exe (PID: 1284)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3368)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3368)
Checks supported languages
- IDM_6.4x_Crack_v19.7.exe (PID: 2940)
- chcp.com (PID: 1580)
- wmpnscfg.exe (PID: 1284)
- chcp.com (PID: 3472)
Checks operating system version
- cmd.exe (PID: 740)
- cmd.exe (PID: 3176)
Reads the computer name
- IDM_6.4x_Crack_v19.7.exe (PID: 2940)
- wmpnscfg.exe (PID: 1284)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1460)
- powershell.exe (PID: 1280)
- powershell.exe (PID: 1840)
- powershell.exe (PID: 2824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
166
Monitored processes
101
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | reg query "HKCU\Software\DownloadManager" "/v" "LastCheckQU" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 400 | reg.exe import C:\Users\admin\AppData\Local\Temp\IDMRegClean.reg | C:\Windows\System32\reg.exe | — | IDM_6.4x_Crack_v19.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 648 | REG ADD "HKLM\Software\Internet Download Manager" /v "AdvIntDriverEnabled2" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 740 | cmd.exe /c call "C:\Users\admin\AppData\Local\Temp\BATCLEN.bat" | C:\Windows\System32\cmd.exe | — | IDM_6.4x_Crack_v19.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 748 | reg query "HKCU\Software\DownloadManager" "/v" "Email" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 940 | find /i "FullLanguage" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 964 | reg query HKCU\Console /v QuickEdit | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 980 | reg query "HKCU\Software\DownloadManager" "/v" "tvfrdt" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1072 | reg add HKCU\IAS_TEST | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
36 388
Read events
36 307
Write events
49
Delete events
32
Modification events
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\IDM_6.4x_v19.7_IDMCRACKDL.rar | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3368) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
25
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2940 | IDM_6.4x_Crack_v19.7.exe | C:\Users\admin\AppData\Local\Temp\IDMRegClean.reg | text | |
MD5:73C023B1480CC88BE4D7761EF11A7703 | SHA256:9C7F6CE7CE6FA4093A20CFA3C1A6D2CDD7D5307AFF7405830C898A21F154ED68 | |||
| 1460 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ybfkyup3.rac.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3368 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3368.4492\IDM_6.4x_Crack_v19.7.exe | executable | |
MD5:27016937B5781C4F84B6B3432170F4D0 | SHA256:FC1A02B509B8F351AC45BD45EFD4E7296B365545A48FFD6A14E8E07BC7189155 | |||
| 2940 | IDM_6.4x_Crack_v19.7.exe | C:\Users\admin\AppData\Local\Temp\BATCLEN.bat | text | |
MD5:9FE22C4AD624881F8F0977CC7614346F | SHA256:12B47C1949CC555C2F68F9FD4677ED5266F25C4DA4630BEC36E303629B133225 | |||
| 4032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\narlaj4l.xqf.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1280 | powershell.exe | C:\Users\admin\AppData\Local\Temp\i3rqy2uw.bid.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3984 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ylyfbnni.5wd.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1280 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hwc4kxbe.qk3.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1100 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hav2rypb.spk.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1100 | powershell.exe | C:\Users\admin\AppData\Local\Temp\zztanwjx.fos.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 217.20.57.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 217.20.57.23:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 217.20.57.18:80 | ctldl.windowsupdate.com | — | US | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1060 | svchost.exe | 217.20.57.23:80 | ctldl.windowsupdate.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |