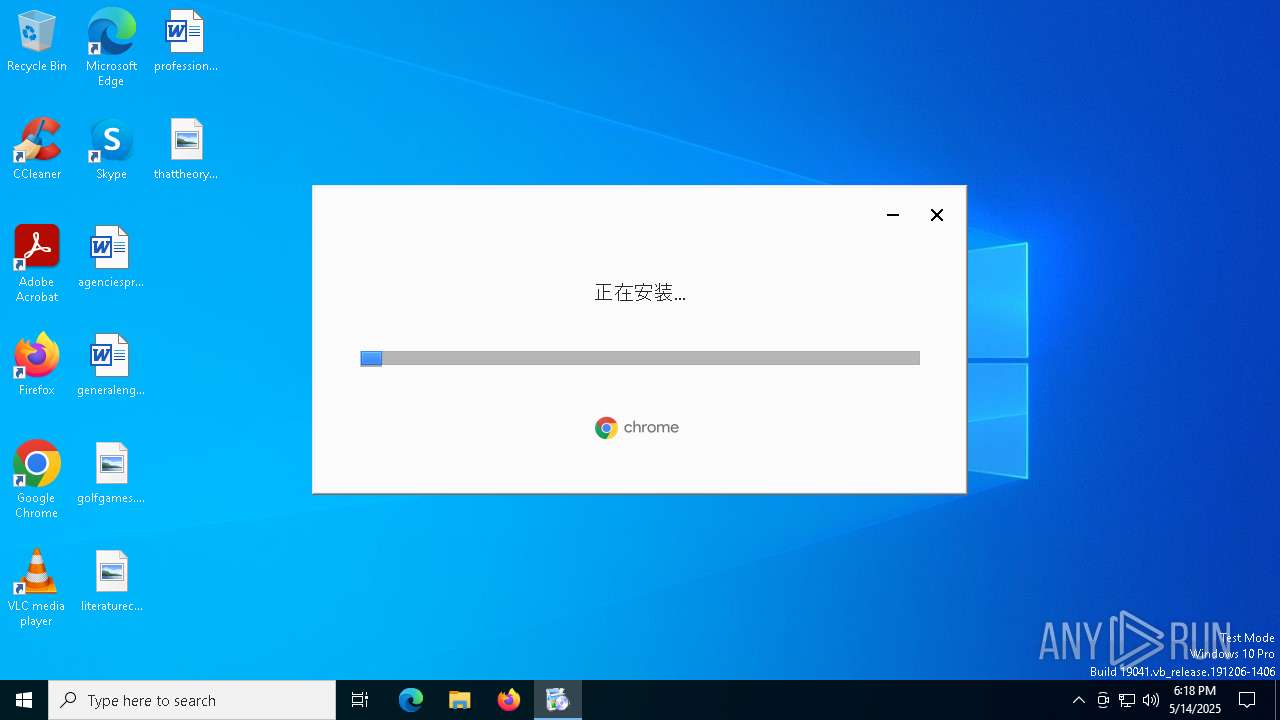
| File name: | 0abca1ff2c425454aa7af034b5e1b124.exe |
| Full analysis: | https://app.any.run/tasks/ec5a2ae9-e478-4705-9740-36d814509c3f |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2025, 18:17:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 0ABCA1FF2C425454AA7AF034B5E1B124 |
| SHA1: | 46B531421236DFDE985C9AF22EA690B2409B60BD |
| SHA256: | 2A18483012A12B11F3589A30B81EC36F6307F791ADB57C82BD1F0D67259A870E |
| SSDEEP: | 786432:ojUIls9q91gMFje6BajwOv8oFWKrudJ3EnwdiSXi4:o5K9ey6eeaj3FeX3Enwov4 |
MALICIOUS
Changes the autorun value in the registry
- setup.exe (PID: 1196)
SUSPICIOUS
The process creates files with name similar to system file names
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
Process drops legitimate windows executable
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
Malware-specific behavior (creating "System.dll" in Temp)
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
The process drops C-runtime libraries
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
Executable content was dropped or overwritten
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
- updater.exe (PID: 1012)
- updater.exe (PID: 2096)
- 136.0.7103.93_chrome_installer.exe (PID: 4108)
- setup.exe (PID: 1196)
Executes application which crashes
- KcInstall.exe (PID: 6468)
Application launched itself
- updater.exe (PID: 1012)
- updater.exe (PID: 2096)
- updater.exe (PID: 4112)
- setup.exe (PID: 1196)
- setup.exe (PID: 5064)
- updater.exe (PID: 3768)
Executes as Windows Service
- updater.exe (PID: 4112)
- updater.exe (PID: 2096)
- updater.exe (PID: 3768)
Reads security settings of Internet Explorer
- updater.exe (PID: 1012)
Creates a software uninstall entry
- setup.exe (PID: 1196)
- chrome.exe (PID: 4040)
Searches for installed software
- setup.exe (PID: 1196)
INFO
The sample compiled with english language support
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
- updater.exe (PID: 1012)
- updater.exe (PID: 2096)
- 136.0.7103.93_chrome_installer.exe (PID: 4108)
- setup.exe (PID: 1196)
Checks supported languages
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
- ChromeSetup.exe (PID: 516)
- KcInstall.exe (PID: 6468)
- updater.exe (PID: 2552)
- updater.exe (PID: 1012)
- updater.exe (PID: 6324)
- updater.exe (PID: 2096)
- updater.exe (PID: 4112)
- updater.exe (PID: 5544)
- 136.0.7103.93_chrome_installer.exe (PID: 4108)
- setup.exe (PID: 1196)
- setup.exe (PID: 5072)
- setup.exe (PID: 5064)
- setup.exe (PID: 684)
- elevation_service.exe (PID: 6944)
- updater.exe (PID: 2384)
- updater.exe (PID: 3768)
Creates files in the program directory
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
- ChromeSetup.exe (PID: 516)
- updater.exe (PID: 2552)
- updater.exe (PID: 1012)
- updater.exe (PID: 2096)
- updater.exe (PID: 4112)
- setup.exe (PID: 1196)
- setup.exe (PID: 5064)
- updater.exe (PID: 3768)
The sample compiled with chinese language support
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
Create files in a temporary directory
- 0abca1ff2c425454aa7af034b5e1b124.exe (PID: 5772)
- ChromeSetup.exe (PID: 516)
- updater.exe (PID: 1012)
Reads the computer name
- ChromeSetup.exe (PID: 516)
- updater.exe (PID: 1012)
- updater.exe (PID: 2096)
- updater.exe (PID: 4112)
- setup.exe (PID: 1196)
- 136.0.7103.93_chrome_installer.exe (PID: 4108)
- setup.exe (PID: 5064)
- elevation_service.exe (PID: 6944)
- updater.exe (PID: 3768)
Creates files or folders in the user directory
- WerFault.exe (PID: 2420)
- updater.exe (PID: 1012)
Process checks whether UAC notifications are on
- updater.exe (PID: 2096)
- updater.exe (PID: 1012)
- updater.exe (PID: 4112)
- updater.exe (PID: 3768)
Reads the software policy settings
- updater.exe (PID: 4112)
- updater.exe (PID: 1012)
- updater.exe (PID: 3768)
Reads the machine GUID from the registry
- updater.exe (PID: 1012)
Checks proxy server information
- updater.exe (PID: 1012)
Auto-launch of the file from Registry key
- setup.exe (PID: 1196)
Manual execution by a user
- chrome.exe (PID: 4040)
- chrmstp.exe (PID: 6240)
Application launched itself
- chrmstp.exe (PID: 6668)
- chrmstp.exe (PID: 6240)
- chrome.exe (PID: 4040)
Executes as Windows Service
- elevation_service.exe (PID: 6944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:55:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
195
Monitored processes
62
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Program Files (x86)\vmware-vm\ChromeSetup.exe" | C:\Program Files (x86)\vmware-vm\ChromeSetup.exe | — | 0abca1ff2c425454aa7af034b5e1b124.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Installer (x86) Exit code: 0 Version: 138.0.7156.0 Modules
| |||||||||||||||
| 684 | C:\WINDOWS\SystemTemp\chrome_Unpacker_BeginUnzipping4112_497702515\CR_CFBDA.tmp\setup.exe --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\WINDOWS\SystemTemp\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=136.0.7103.93 --initial-client-data=0x29c,0x2a0,0x2a4,0x1e8,0x2a8,0x7ff6bea1a3a0,0x7ff6bea1a3ac,0x7ff6bea1a3b8 | C:\Windows\SystemTemp\chrome_Unpacker_BeginUnzipping4112_497702515\CR_CFBDA.tmp\setup.exe | — | setup.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Chrome Installer Exit code: 0 Version: 136.0.7103.93 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --field-trial-handle=2060,i,10223613002702259756,18209671613575070870,262144 --variations-seed-version --mojo-platform-channel-handle=5156 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 136.0.7103.93 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=2060,i,10223613002702259756,18209671613575070870,262144 --variations-seed-version --mojo-platform-channel-handle=3264 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 136.0.7103.93 Modules
| |||||||||||||||
| 976 | "C:\Users\admin\AppData\Local\Temp\0abca1ff2c425454aa7af034b5e1b124.exe" | C:\Users\admin\AppData\Local\Temp\0abca1ff2c425454aa7af034b5e1b124.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1012 | "C:\Users\admin\AppData\Local\Temp\Google516_1181127119\bin\updater.exe" --install=appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={D9C032F3-C330-060E-F713-7EDAD09E36C0}&lang=zh-CN&browser=5&usagestats=1&appname=Google%20Chrome&needsadmin=prefers&ap=x64-statsdef_1&installdataindex=empty --enable-logging --vmodule=*/components/winhttp/*=1,*/components/update_client/*=2,*/chrome/enterprise_companion/*=2,*/chrome/updater/*=2 | C:\Users\admin\AppData\Local\Temp\Google516_1181127119\bin\updater.exe | ChromeSetup.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Updater (x86) Exit code: 0 Version: 138.0.7156.0 Modules
| |||||||||||||||
| 1196 | "C:\WINDOWS\SystemTemp\chrome_Unpacker_BeginUnzipping4112_497702515\CR_CFBDA.tmp\setup.exe" --install-archive="C:\WINDOWS\SystemTemp\chrome_Unpacker_BeginUnzipping4112_497702515\CR_CFBDA.tmp\CHROME.PACKED.7Z" --verbose-logging --do-not-launch-chrome --channel=stable --installerdata="C:\Windows\SystemTemp\chrome_Unpacker_BeginUnzipping4112_497702515\98e82fc6-0fa2-43c7-87de-7023b4473b8a.tmp" | C:\Windows\SystemTemp\chrome_Unpacker_BeginUnzipping4112_497702515\CR_CFBDA.tmp\setup.exe | 136.0.7103.93_chrome_installer.exe | ||||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Chrome Installer Exit code: 0 Version: 136.0.7103.93 Modules
| |||||||||||||||
| 1276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --field-trial-handle=2060,i,10223613002702259756,18209671613575070870,262144 --variations-seed-version --mojo-platform-channel-handle=6656 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 136.0.7103.93 Modules
| |||||||||||||||
| 2096 | "C:\Program Files (x86)\Google\GoogleUpdater\138.0.7156.0\updater.exe" --system --windows-service --service=update-internal | C:\Program Files (x86)\Google\GoogleUpdater\138.0.7156.0\updater.exe | services.exe | ||||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater (x86) Exit code: 0 Version: 138.0.7156.0 Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-pre-read-main-dll --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2060,i,10223613002702259756,18209671613575070870,262144 --variations-seed-version --mojo-platform-channel-handle=2036 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 136.0.7103.93 Modules
| |||||||||||||||
Total events
19 148
Read events
18 864
Write events
251
Delete events
33
Modification events
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\kcinstall.exe|c49938c79522c70f |
| Operation: | write | Name: | ProgramId |
Value: 0006e1d364db3476bb2db28e6eb5bc7a20090000ffff | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\kcinstall.exe|c49938c79522c70f |
| Operation: | write | Name: | FileId |
Value: 00002550846180f5f30e6cb502579cf047cad1eb77ec | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\kcinstall.exe|c49938c79522c70f |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\program files (x86)\vmware-vm\kcinstall.exe | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\kcinstall.exe|c49938c79522c70f |
| Operation: | write | Name: | LongPathHash |
Value: kcinstall.exe|c49938c79522c70f | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\kcinstall.exe|c49938c79522c70f |
| Operation: | write | Name: | Name |
Value: KcInstall.exe | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\kcinstall.exe|c49938c79522c70f |
| Operation: | write | Name: | OriginalFileName |
Value: | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\kcinstall.exe|c49938c79522c70f |
| Operation: | write | Name: | Publisher |
Value: | |||
| (PID) Process: | (2420) WerFault.exe | Key: | \REGISTRY\A\{8b29a971-98fa-bf72-65cb-e466c1b9fc82}\Root\InventoryApplicationFile\kcinstall.exe|c49938c79522c70f |
| Operation: | write | Name: | Version |
Value: | |||
Executable files
24
Suspicious files
168
Text files
72
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Program Files (x86)\vmware-vm\newpet.unity3d | — | |
MD5:— | SHA256:— | |||
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Program Files (x86)\vmware-vm\safew desktop setup.exe | — | |
MD5:— | SHA256:— | |||
| 516 | ChromeSetup.exe | C:\Users\admin\AppData\Local\Temp\Google516_861605424\UPDATER.PACKED.7Z | — | |
MD5:— | SHA256:— | |||
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Program Files (x86)\vmware-vm\KcInst.exe | executable | |
MD5:DB4A9F0855C1297E09315AFA35730044 | SHA256:EC4AC3165A638E0EA2C7CE4C5D347EA4022D6CDC2D6C67150510ADE5C662E9FB | |||
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Program Files (x86)\vmware-vm\vcruntime140.dll | executable | |
MD5:DED0FB624C202E3595551256E3BC0BA2 | SHA256:2AEBC4E4CA7645188D12950CA68B39F71EBD86DA4228419800C1B1A3754F3130 | |||
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Users\admin\AppData\Local\Temp\nsoE61D.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Program Files (x86)\vmware-vm\KcInstall.exe | executable | |
MD5:DB4A9F0855C1297E09315AFA35730044 | SHA256:EC4AC3165A638E0EA2C7CE4C5D347EA4022D6CDC2D6C67150510ADE5C662E9FB | |||
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Program Files (x86)\vmware-vm\vcruntime140_1.dll | executable | |
MD5:F498619721756332EF731F1B72B7F29E | SHA256:FD1CC0C1287CAF736C7E1E4D9AEE80FD74CFDFA52563DDD126C03F45542D45B6 | |||
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Program Files (x86)\vmware-vm\msvcp140.dll | executable | |
MD5:C3D497B0AFEF4BD7E09C7559E1C75B05 | SHA256:1E57A6DF9E3742E31A1C6D9BFF81EBEEAE8A7DE3B45A26E5079D5E1CCE54CD98 | |||
| 5772 | 0abca1ff2c425454aa7af034b5e1b124.exe | C:\Program Files (x86)\vmware-vm\sqlite3.dll | executable | |
MD5:C1676EE751FEF60C629931CB3B5ABB57 | SHA256:5BEEC91B48C902DDEEE4FE03D34CE3AC5C4980A13992374D297D7CEAC66EEF7F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
58
DNS requests
67
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.151:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4112 | updater.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome/lavkrwitlza3b2ssskklc2whmi_136.0.7103.93/-8a69d345-d564-463c-aff1-a69d9e530f96-_136.0.7103.93_all_adh2yb6q7t3w4x6zy5f536dugexq.crx3 | unknown | — | — | whitelisted |
1012 | updater.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
1012 | updater.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1012 | updater.exe | GET | 200 | 172.217.18.99:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEA85wFTvuwmlCdtY0UxEIqg%3D | unknown | — | — | whitelisted |
2268 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2268 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.151:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4112 | updater.exe | 142.250.184.195:443 | update.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
dl.google.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7020 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7020 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |