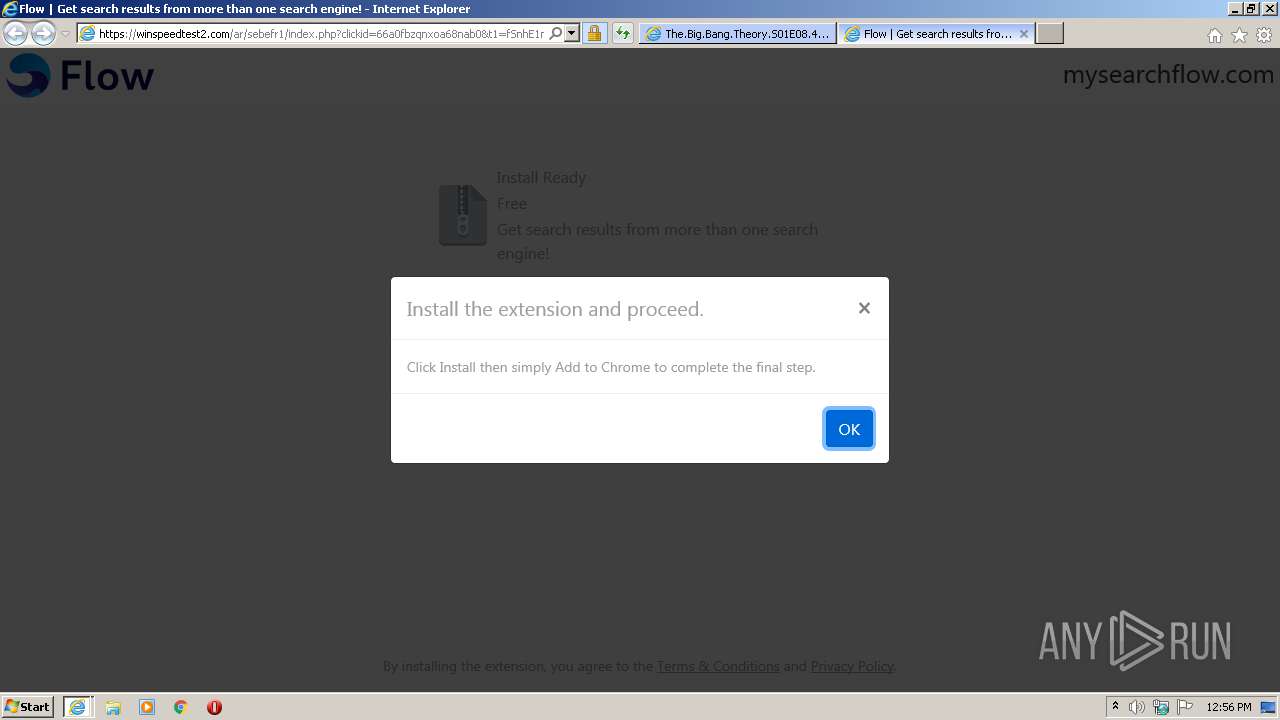
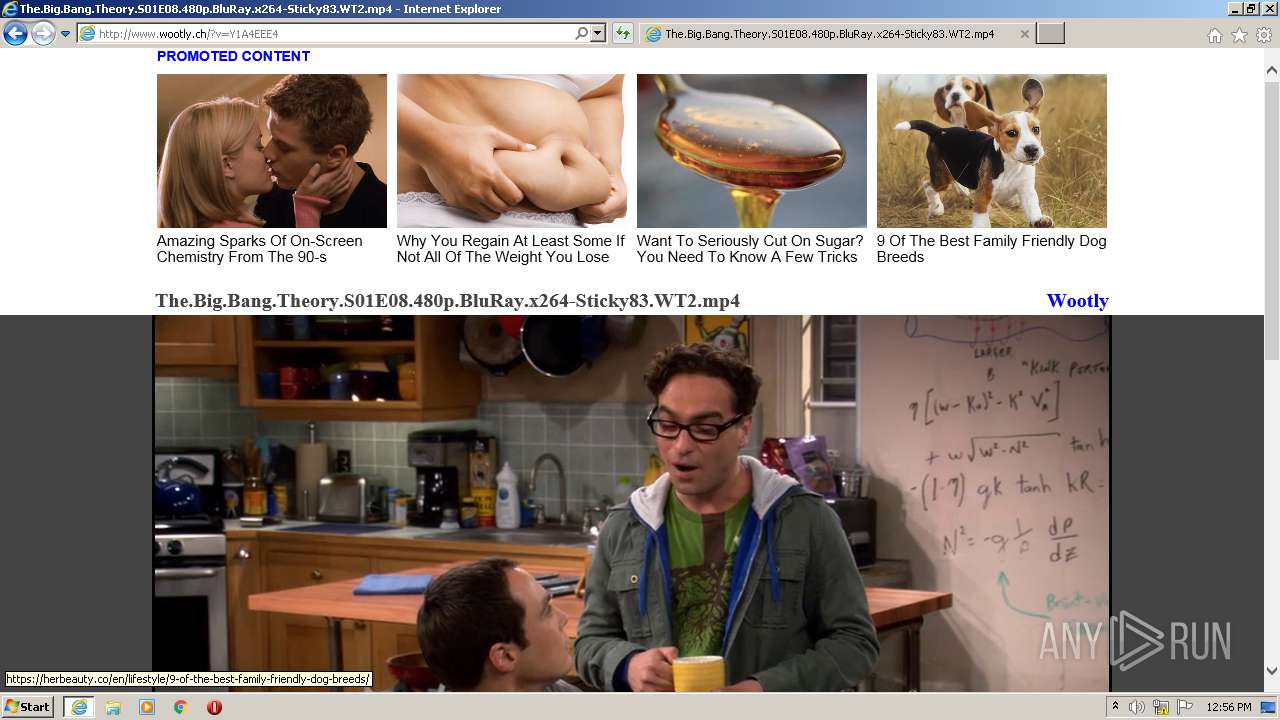
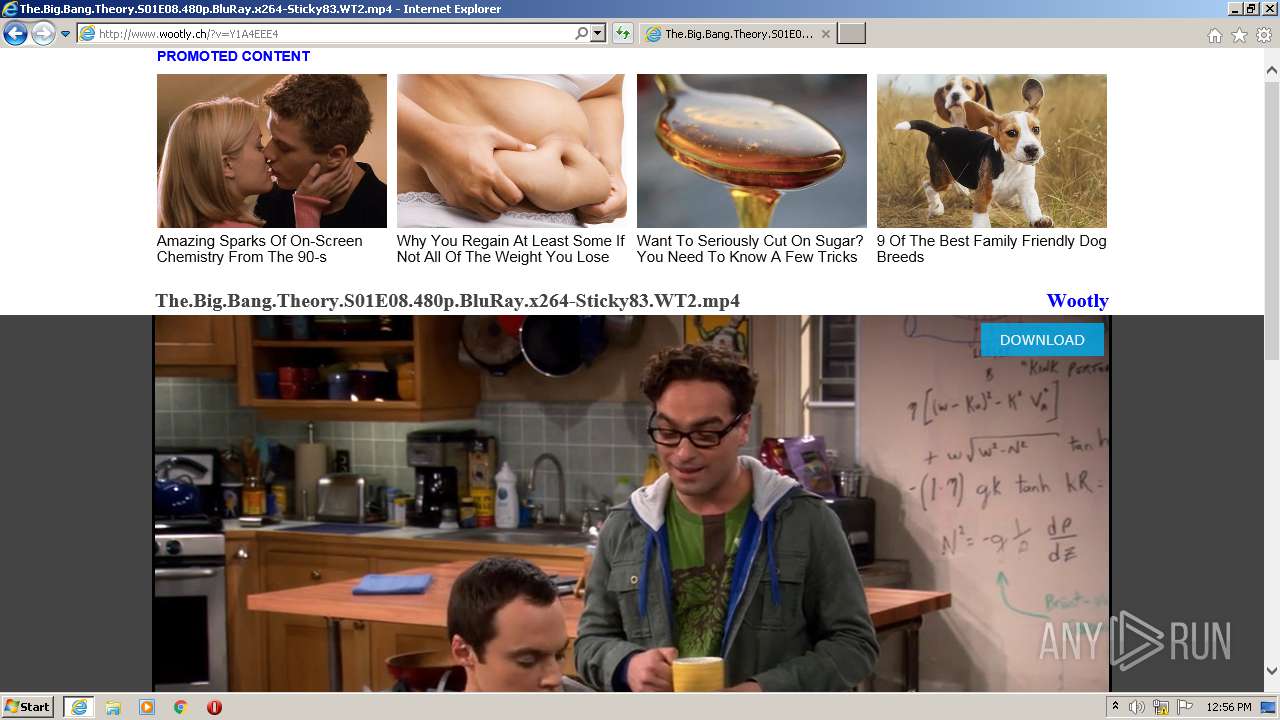
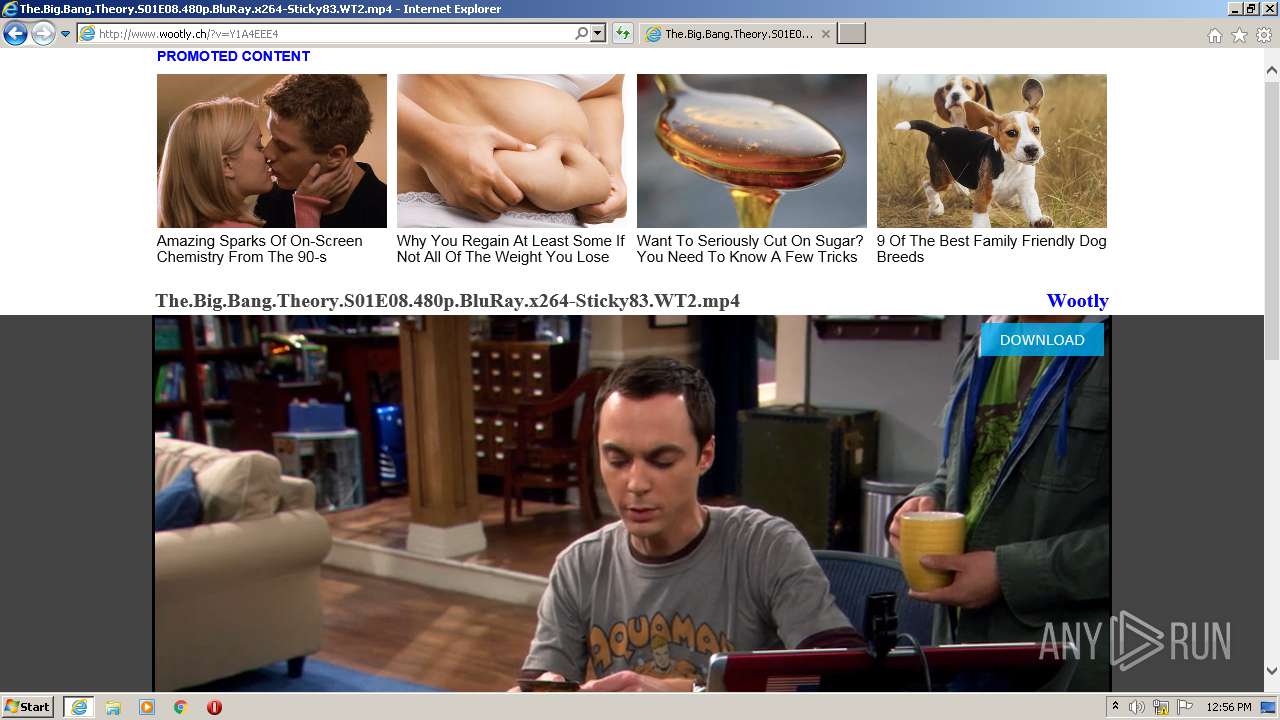
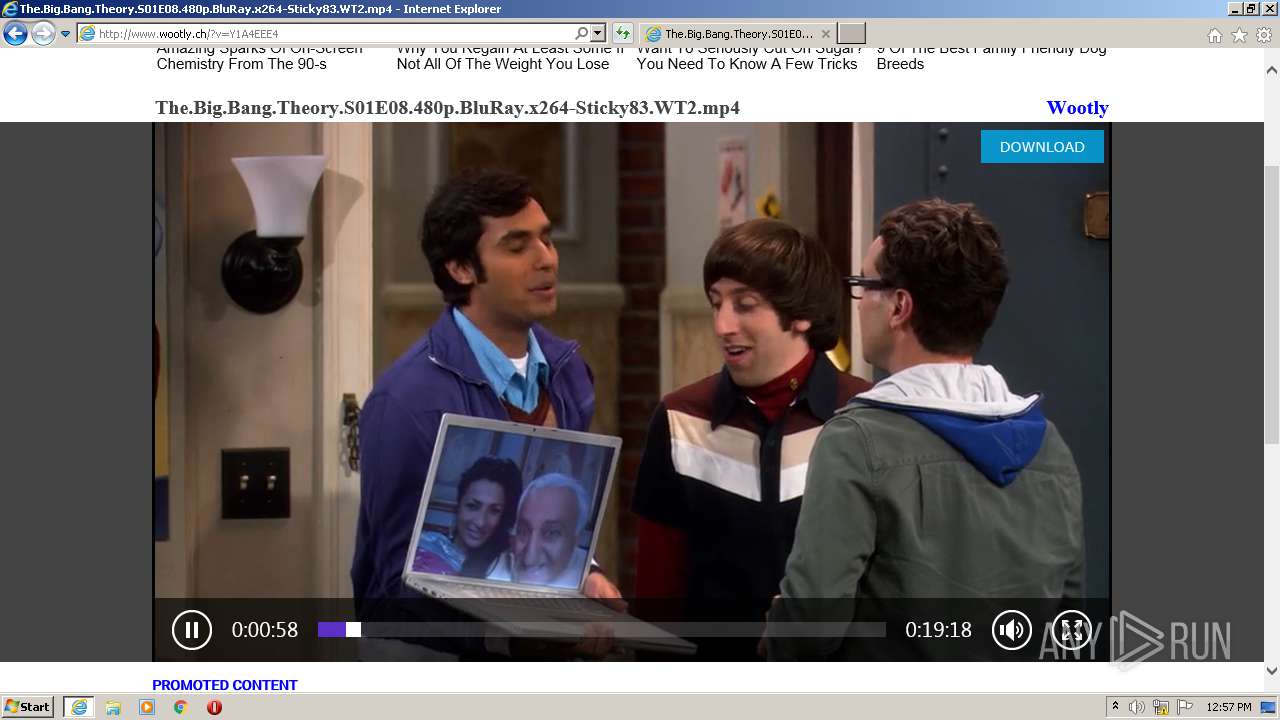
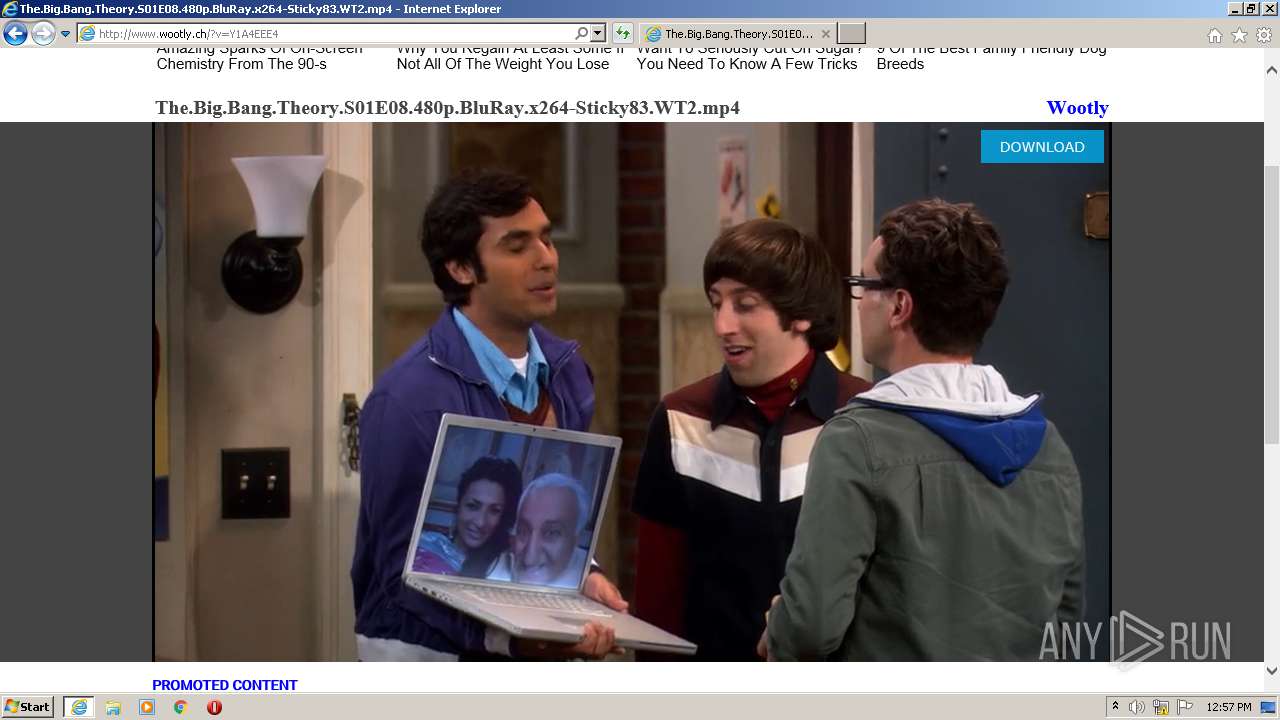
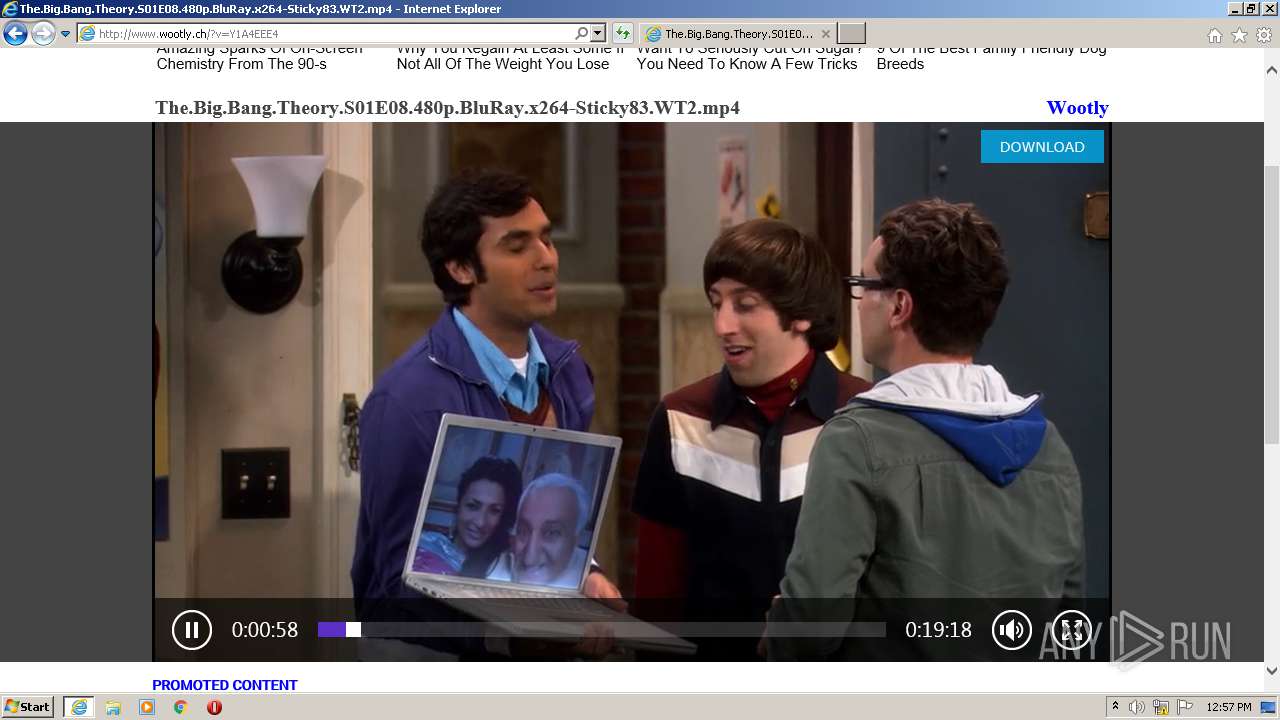
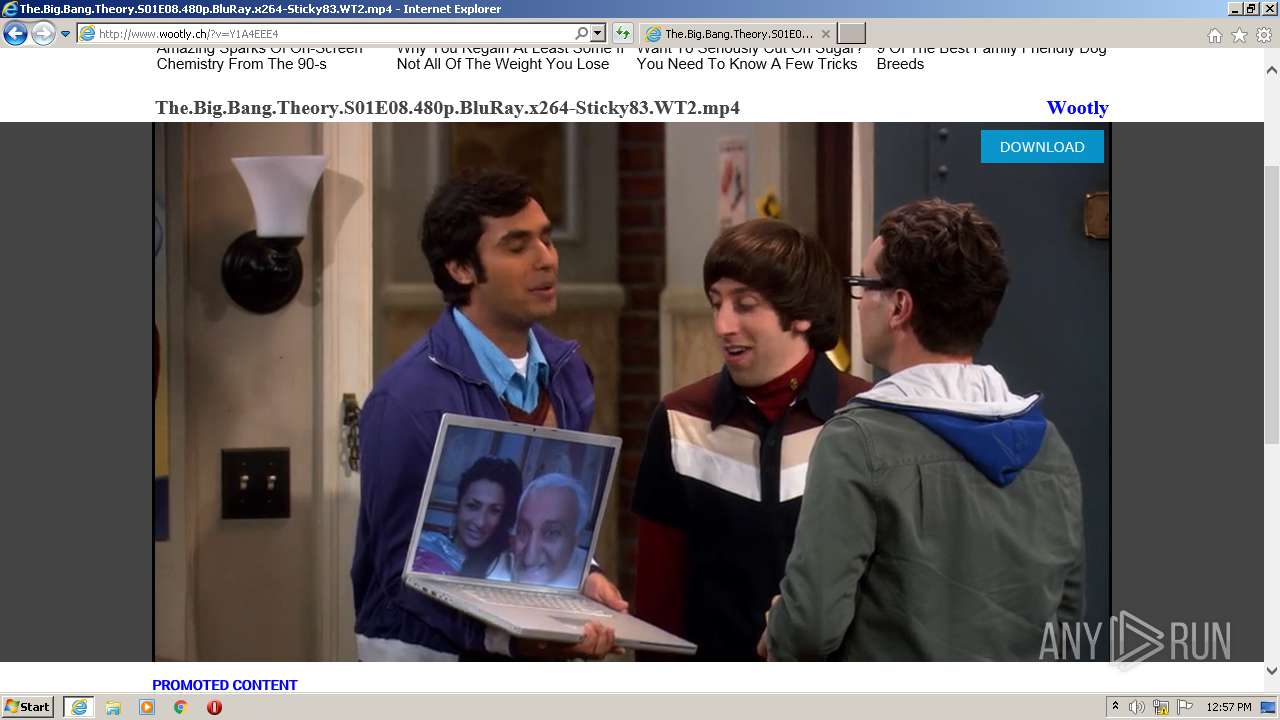
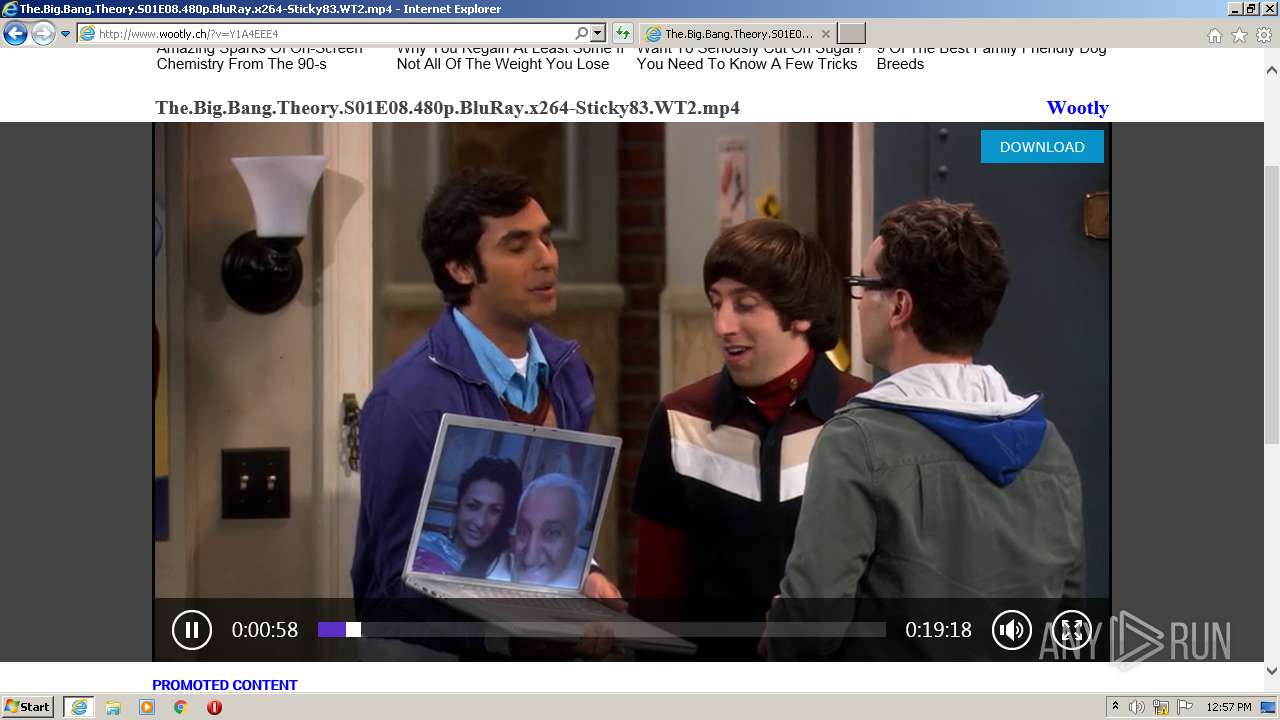
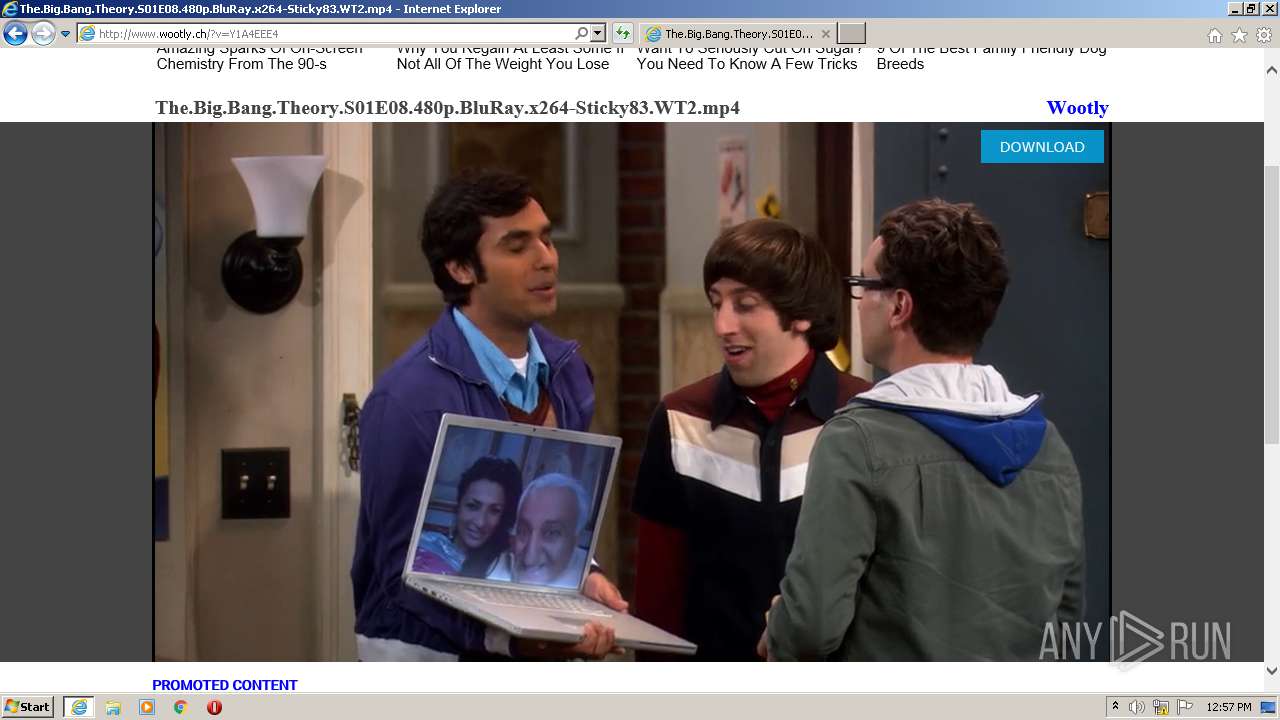
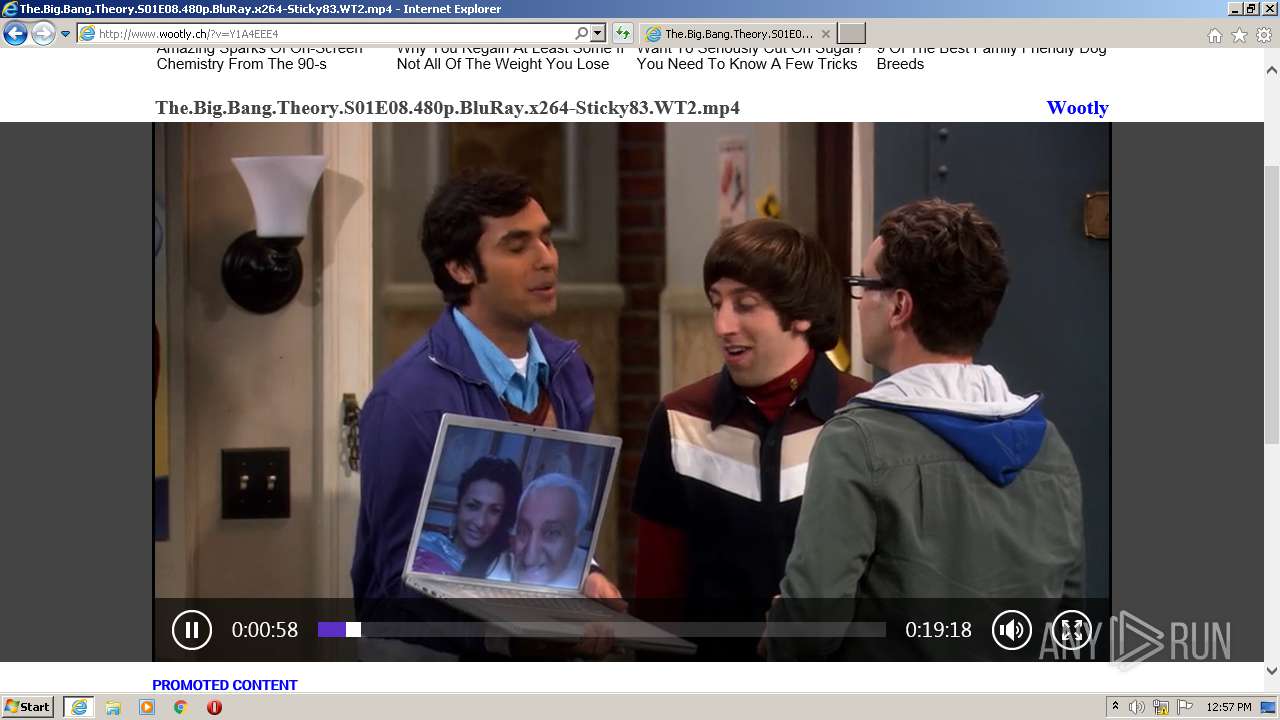
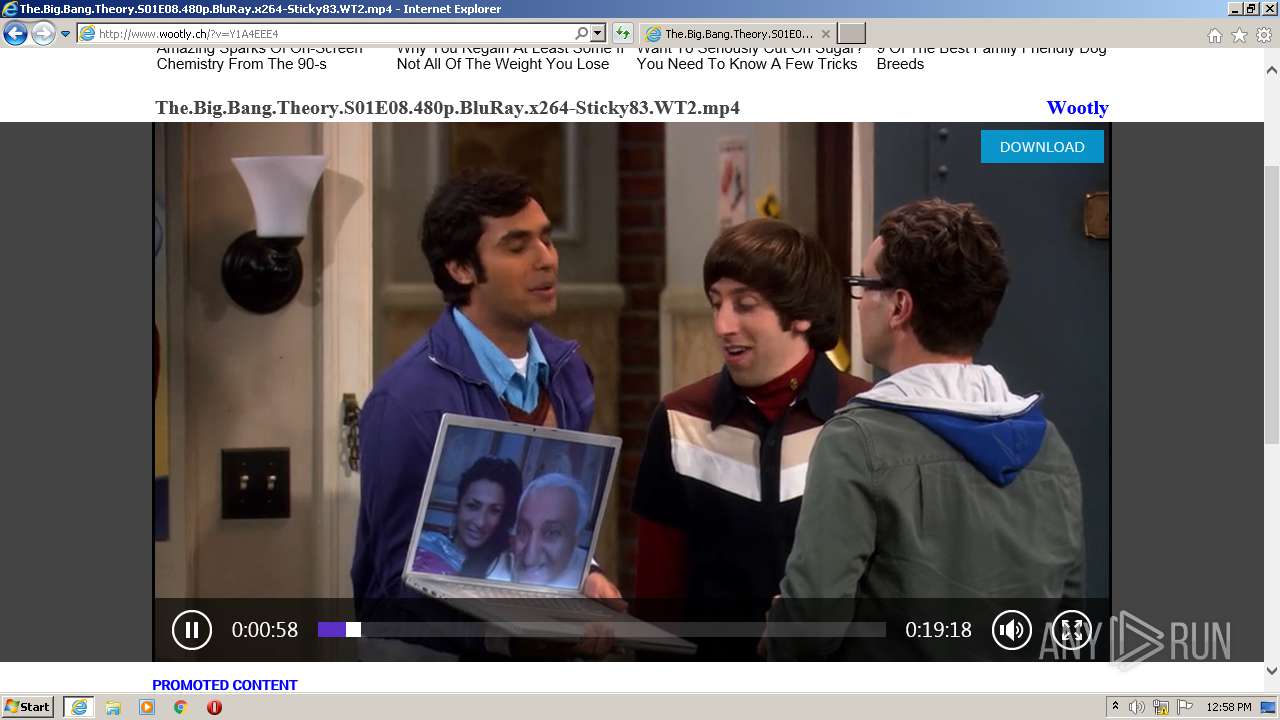
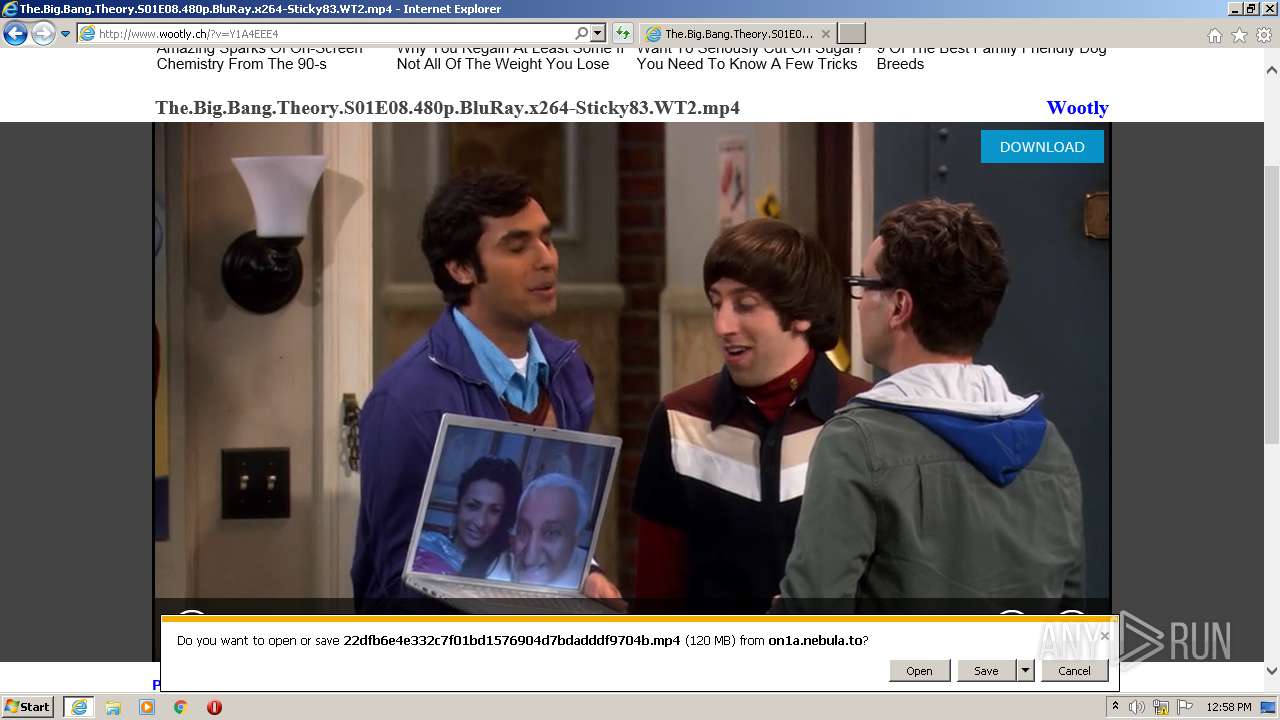
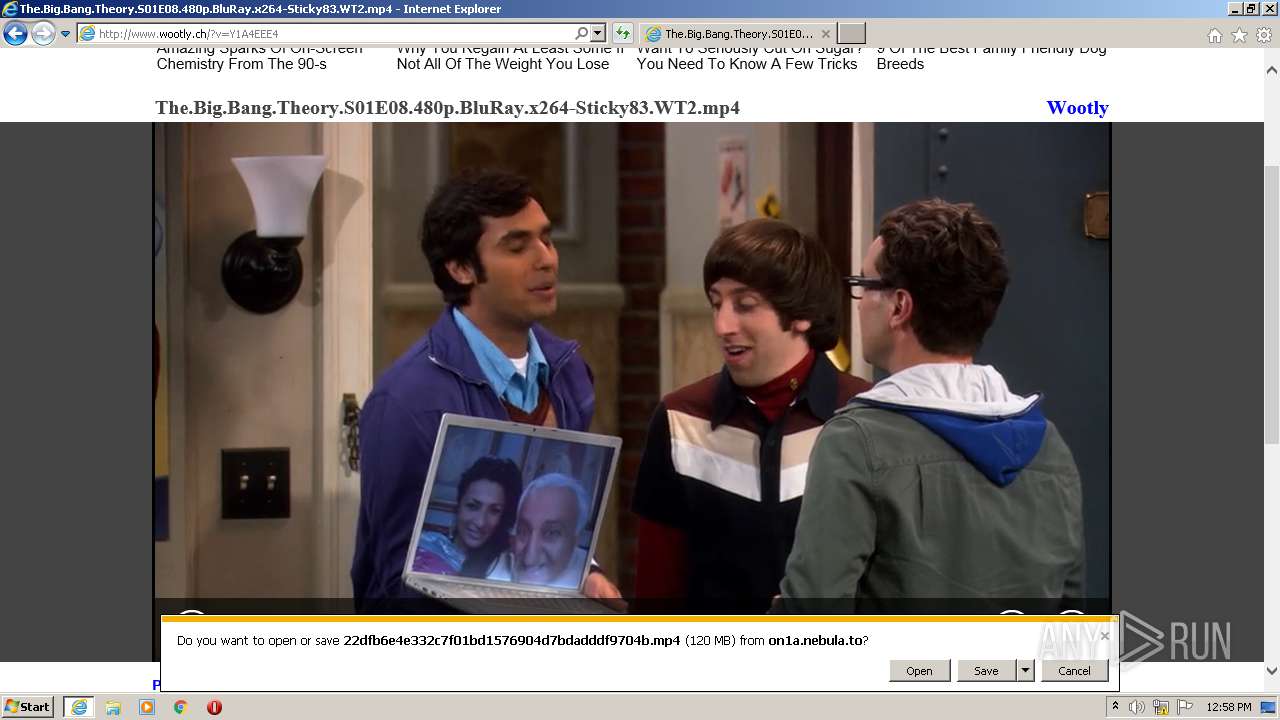
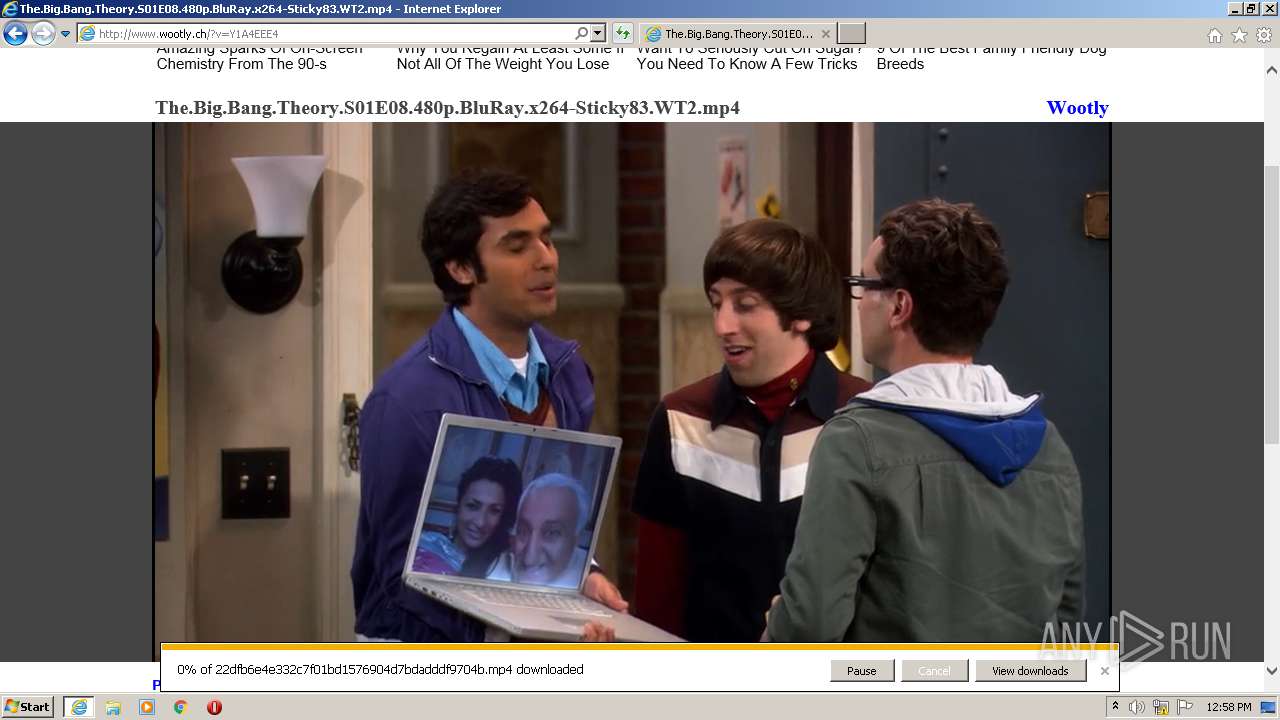
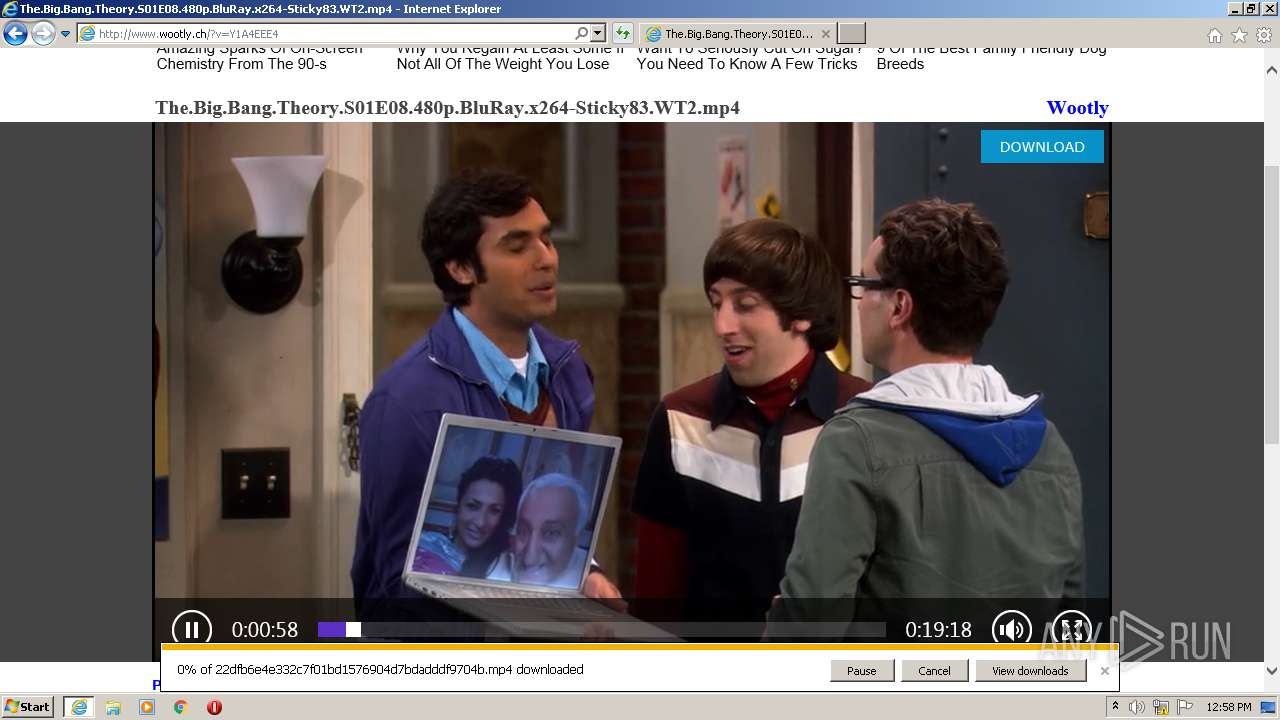
| URL: | http://www.wootly.ch/?v=Y1A4EEE4 |
| Full analysis: | https://app.any.run/tasks/8c266907-c371-4b81-84ce-968b376ace97 |
| Verdict: | Malicious activity |
| Analysis date: | April 08, 2021, 11:55:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F82D5A96909F5F5F069B9333E6444296 |
| SHA1: | 418410C473B686BD7EF209EE2603F88E7E5DC120 |
| SHA256: | 29FEBA7884590C6EA3905D02BE73F41CFB2F7166BED8CAED51A417F18788A12E |
| SSDEEP: | 3:N1KJS4UiLFkR6R:Cc4USFzR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 532)
INFO
Creates files in the user directory
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2444)
- iexplore.exe (PID: 868)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 532)
Application launched itself
- iexplore.exe (PID: 868)
Changes internet zones settings
- iexplore.exe (PID: 868)
Modifies the phishing filter of IE
- iexplore.exe (PID: 868)
Reads internet explorer settings
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2444)
Reads settings of System Certificates
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2444)
- iexplore.exe (PID: 868)
Changes settings of System certificates
- iexplore.exe (PID: 868)
Adds / modifies Windows certificates
- iexplore.exe (PID: 868)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:868 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 868 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://www.wootly.ch/?v=Y1A4EEE4" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2444 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:868 CREDAT:3937553 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
1 834
Read events
1 615
Write events
216
Delete events
3
Modification events
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 846440070 | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30878830 | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A6000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
63
Text files
67
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab113.tmp | — | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar114.tmp | — | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\DQDGAK7Q.txt | — | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\wootly.ch.211773[1].js | text | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\wootly.ch.223736[1].js | text | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\JVZ8YK1U.txt | text | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\aHR0cDovL2ltZ2hvc3RzLmNvbS90LzIwMTktMTEvMTAxOTI0LzRlODVkMWNkOWEzZTVmYmNlMGViM2QwOWZiNjU3ODM4LmpwZWc[1].jpg | image | |
MD5:— | SHA256:— | |||
| 572 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\VW18UR9K.htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
120
DNS requests
41
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2444 | iexplore.exe | GET | 302 | 173.239.53.32:80 | http://xml.pdn-1.com/redirect?feed=232891&auth=m9L488&subid=233138_320439&query=BE&url=&default_url=http%3A%2F%2Fxml.saturndynamic.pt%2Fredirect%3Ffeed%3D294100%26auth%3DIEGzgP%26subid%3D320439%26query%3DBE%26url%3D | US | — | — | malicious |
2444 | iexplore.exe | GET | 200 | 23.55.163.57:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
572 | iexplore.exe | GET | 200 | 23.55.163.48:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgSeLKUaVNhIJRs9Dw2rjv25nQ%3D%3D | US | der | 503 b | shared |
572 | iexplore.exe | POST | 200 | 185.187.81.41:80 | http://xk9o.amgload.net/z | UA | text | 16 b | malicious |
572 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
572 | iexplore.exe | GET | 200 | 2.23.6.217:80 | http://ocsp.trustwave.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQ1mI4Ww4R5LZiQ295pj4OF%2F44yyAQUyk7dWyc1Kdn27sPlU%2B%2BkwBmWHa8CEQCSuHRPcc7Q4mxyo9jV2SWy | unknown | der | 1.52 Kb | whitelisted |
572 | iexplore.exe | GET | 200 | 23.55.163.48:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgN7Oe5d6Wyhh0m5FrGdoCAmyA%3D%3D | US | der | 503 b | shared |
572 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
572 | iexplore.exe | GET | 200 | 23.55.163.73:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
572 | iexplore.exe | GET | 200 | 2.23.6.217:80 | http://ocsp.trustwave.com//MFQwUjBQME4wTDAJBgUrDgMCGgUABBRKUAJ27jxxuy1zYtpUHfLy0MHHugQUys4dGAN3HhzzfFiymnCoCIAW9K4CEwb1lQKy2rx%2FS5DWa947FkCgQKA%3D | unknown | der | 638 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
572 | iexplore.exe | 45.178.5.242:80 | go.wootly.ch | — | — | unknown |
572 | iexplore.exe | 185.187.81.35:80 | kz1c.piguiqproxy.com | LLC id Strategy | UA | unknown |
572 | iexplore.exe | 104.19.134.78:443 | jsc.mgid.com | Cloudflare Inc | US | unknown |
572 | iexplore.exe | 185.187.81.41:80 | xk9o.amgload.net | LLC id Strategy | UA | unknown |
572 | iexplore.exe | 45.178.5.242:443 | go.wootly.ch | — | — | unknown |
572 | iexplore.exe | 104.19.135.80:443 | cdn.steepto.com | Cloudflare Inc | US | unknown |
572 | iexplore.exe | 104.19.136.80:443 | cdn.steepto.com | Cloudflare Inc | US | shared |
572 | iexplore.exe | 23.55.161.177:80 | b.scorecardresearch.com | Akamai International B.V. | US | unknown |
572 | iexplore.exe | 52.18.90.176:443 | match.adsrvr.org | Amazon.com, Inc. | IE | unknown |
572 | iexplore.exe | 2.23.6.217:80 | ocsp.trustwave.com | Telecom Italia | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.wootly.ch |
| suspicious |
jsc.mgid.com |
| whitelisted |
kz1c.piguiqproxy.com |
| unknown |
xk9o.amgload.net |
| malicious |
crl.identrust.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
c.mgid.com |
| whitelisted |
cdn.steepto.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
servicer.mgid.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
2444 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
572 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |