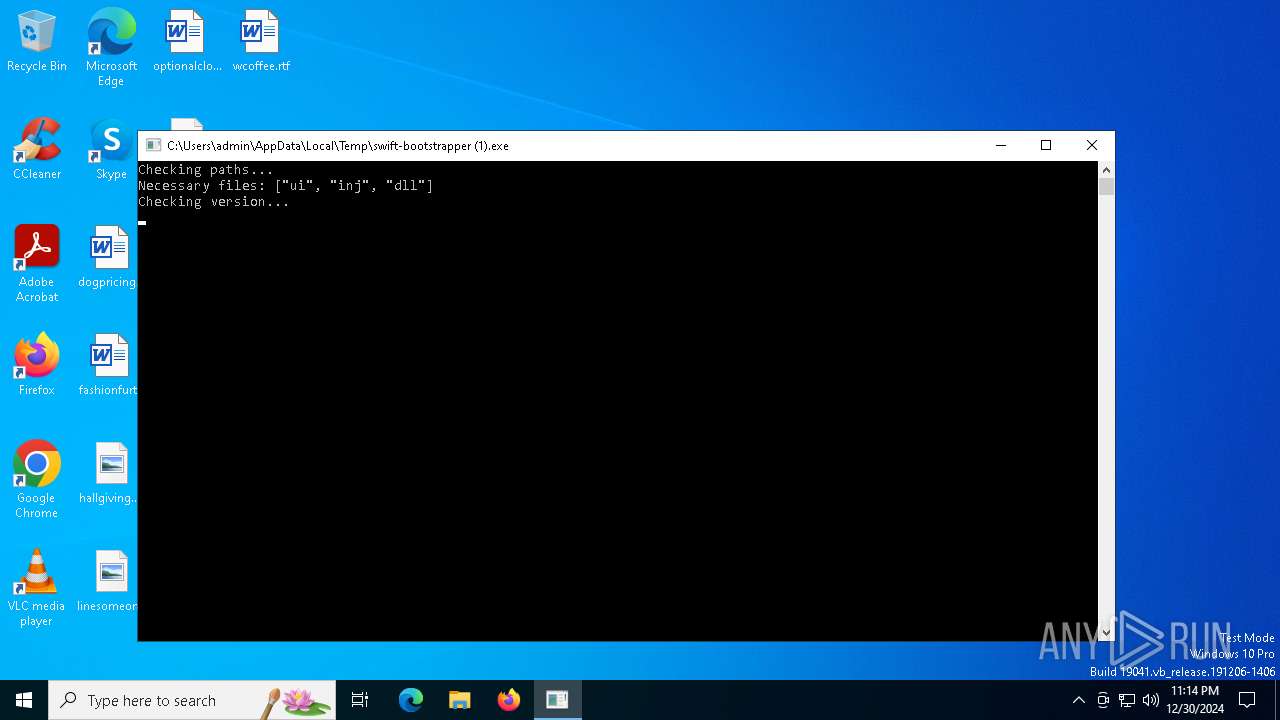
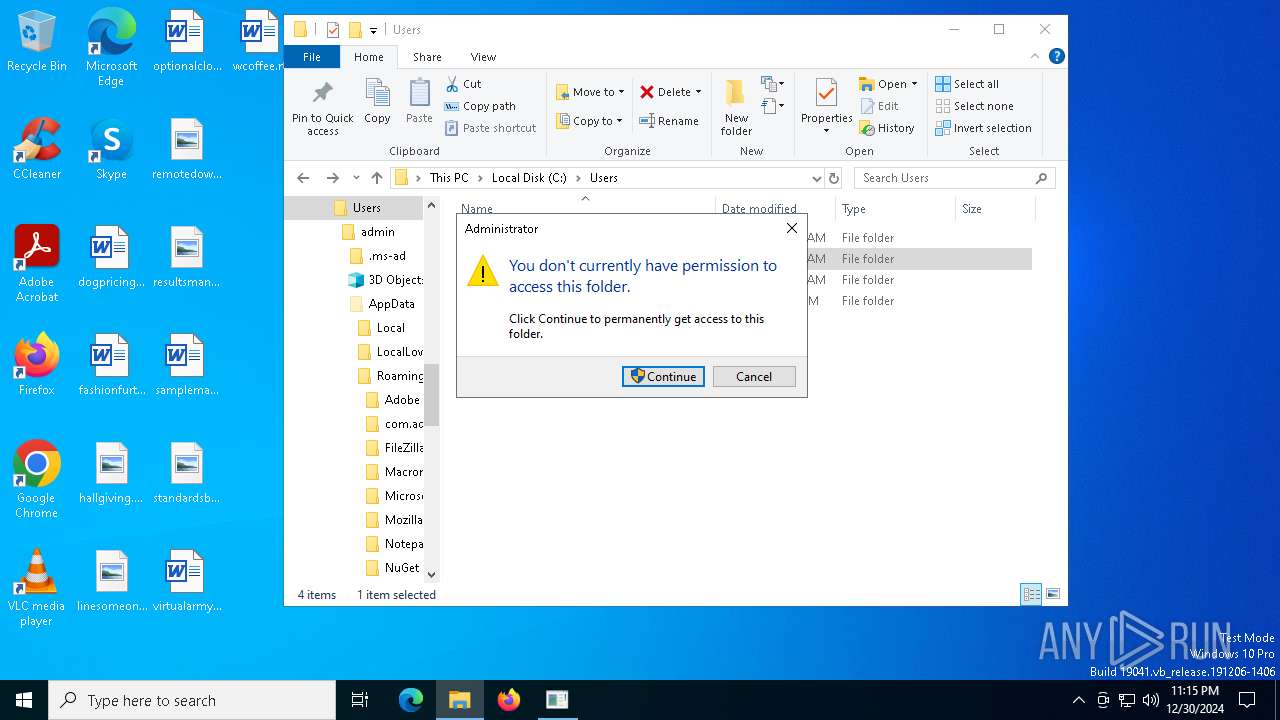
| File name: | swift-bootstrapper (1).exe |
| Full analysis: | https://app.any.run/tasks/05cc7f7c-0967-44d7-a1c5-3232488829dc |
| Verdict: | Malicious activity |
| Analysis date: | December 30, 2024, 23:14:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 5 sections |
| MD5: | 26E350B6F17A777A79B8BE46E1B06AC0 |
| SHA1: | ACDBBEF171B2361604BB7678645ACF62FC2CC7AF |
| SHA256: | 29C535C85CA221059C46B364B9B6A81E68A0E0A6AEF5DA460DCB0DADDF90D2F1 |
| SSDEEP: | 98304:9HSxyqAQYZCPUOdLT5W0rQlKW0AKP7k3ApjBYEQ3jd60roAKCuEJQMUpEPd9B/NX:JI |
MALICIOUS
GENERIC has been found (auto)
- swift-bootstrapper (1).exe (PID: 5920)
SUSPICIOUS
Executable content was dropped or overwritten
- swift-bootstrapper (1).exe (PID: 5920)
INFO
Checks proxy server information
- swift-bootstrapper (1).exe (PID: 5920)
Reads the computer name
- swift-bootstrapper (1).exe (PID: 5920)
Checks supported languages
- swift-bootstrapper (1).exe (PID: 5920)
- SearchApp.exe (PID: 5064)
Reads the software policy settings
- swift-bootstrapper (1).exe (PID: 5920)
- SearchApp.exe (PID: 5064)
Create files in a temporary directory
- swift-bootstrapper (1).exe (PID: 5920)
Application based on Rust
- swift-bootstrapper (1).exe (PID: 5920)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:06 18:09:31+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 4163072 |
| InitializedDataSize: | 1816064 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3f65a0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
135
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | swift-bootstrapper (1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5532 | C:\WINDOWS\system32\DllHost.exe /Processid:{4D111E08-CBF7-4F12-A926-2C7920AF52FC} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
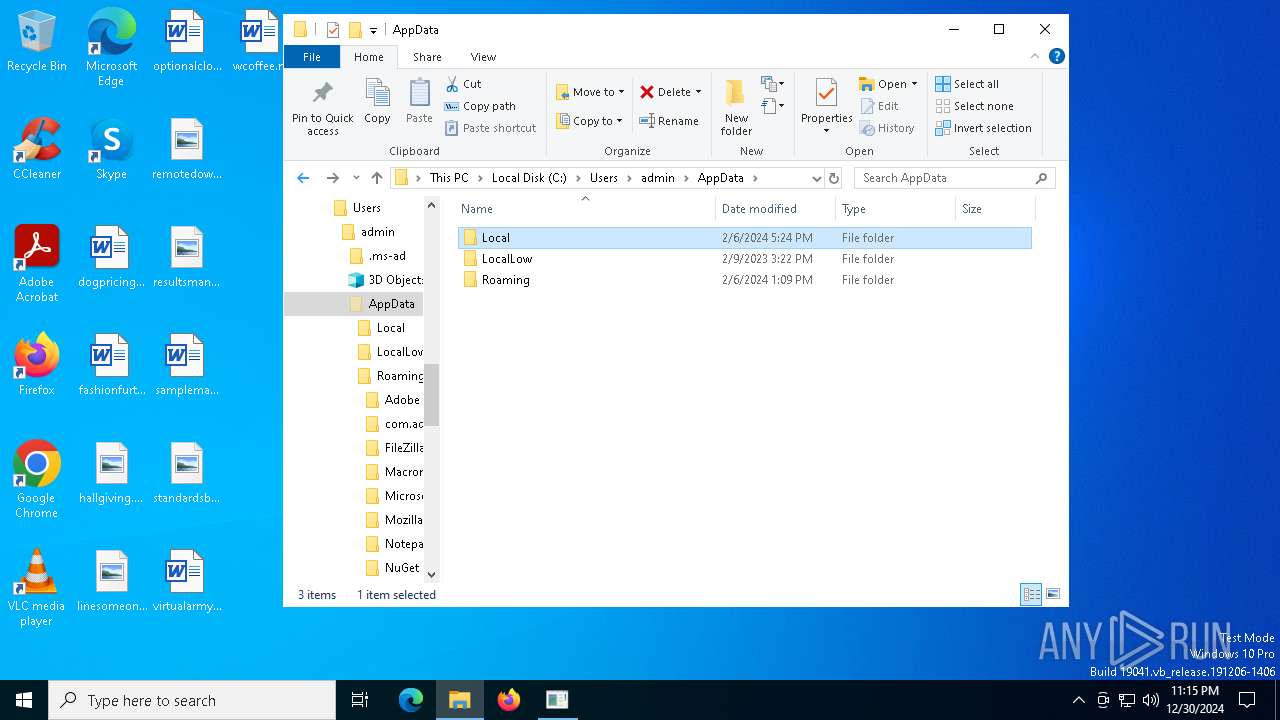
| 5920 | "C:\Users\admin\AppData\Local\Temp\swift-bootstrapper (1).exe" | C:\Users\admin\AppData\Local\Temp\swift-bootstrapper (1).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6824 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 155
Read events
9 023
Write events
129
Delete events
3
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 929 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 0000349AE0A1105BDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 000017FEE2A1105BDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\ConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0049006E007000750074005F007B00380033003200620036003800640032002D0037006600650032002D0034006500370031002D0061003300610064002D003200360031003600360062003600350036006500630036007D00000068AE82A2105BDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0041007000700073005F007B00350032006400380037003900660033002D0062003000390062002D0034006300340061002D0039003200370033002D003100330034003300650039003400620037006100630035007D00000068AE82A2105BDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LastConstraintIndexBuildCompleted |
Value: 104783A2105BDB0168AE82A2105BDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Input_{832b68d2-7fe2-4e71-a3ad-26166b656ec6} | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Microsoft.Windows.Search_cw5n1h2txyewy\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{52d879f3-b09b-4c4a-9273-1343e94b7ac5} | |||
Executable files
3
Suspicious files
85
Text files
250
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{52d879f3-b09b-4c4a-9273-1343e94b7ac5}\0.1.filtertrie.intermediate.txt | text | |
MD5:34BD1DFB9F72CF4F86E6DF6DA0A9E49A | SHA256:8E1E6A3D56796A245D0C7B0849548932FEE803BBDB03F6E289495830E017F14C | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\I6nommjaUrH5K7RnL_cFpH5R7jM[1].css | text | |
MD5:C1AC4CCA38EA836717738D7CF72B45B9 | SHA256:E4C0BF089E674482FA2FE7D558F64F9D3EBDD414EAED18908E34A6140D09B727 | |||
| 5920 | swift-bootstrapper (1).exe | C:\Users\admin\AppData\Local\Temp\Swift.exe | executable | |
MD5:64B0517790437B071FEF6CD6782D4B9F | SHA256:E12D17C65A31989079774E3E465178CDD9FB5D07E101D4654BDF8EA618F6B1F5 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{52d879f3-b09b-4c4a-9273-1343e94b7ac5}\0.2.filtertrie.intermediate.txt | text | |
MD5:C204E9FAAF8565AD333828BEFF2D786E | SHA256:D65B6A3BF11A27A1CED1F7E98082246E40CF01289FD47FE4A5ED46C221F2F73F | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:908AAD7DA3D454D7882E34CD2EF1FCE0 | SHA256:600216492E6C108E3BAE2DA2172CF5B0FFEA209F20DF255922C575C9E980E302 | |||
| 5920 | swift-bootstrapper (1).exe | C:\Users\admin\AppData\Local\Temp\bin\injector.exe | executable | |
MD5:A5CCAEC11B613A44116B6EFF8230664A | SHA256:07409D4ADC7D4F9DB6AD642C1D7F989C69516F0B356214A8C1C1E6BB58F43EF4 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\QNBBNqWD9F_Blep-UqQSqnMp-FI[1].css | text | |
MD5:77373397A17BD1987DFCA2E68D022ECF | SHA256:A319AF2E953E7AFDA681B85A62F629A5C37344AF47D2FCD23AB45E1D99497F13 | |||
| 5920 | swift-bootstrapper (1).exe | C:\Users\admin\AppData\Local\Temp\bin\Dll3.dll | executable | |
MD5:1C10CC2A3331CDE56573063B0EA6CC4F | SHA256:3BFD55ACBD4AB748EB7559E7944993D9D6E05F84A5440BF2E536215079CC0F34 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:908111EB0FFB1360D5DD61279C21703E | SHA256:1ED87CF425DED994B05A842271AB4D28A76F399E571688CF2E7B186F70DC3059 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\95d9a2a97a42f02325559b453ba7f8fe839baa18.tbres | binary | |
MD5:3DC2E5850B0CCD1830068D7898CAF56E | SHA256:E84A15E621F5C5EE8EF38EB15DCBC445C56AD98397A527957C5BBCE30A8270D0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
53
DNS requests
32
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1356 | svchost.exe | GET | 200 | 2.20.245.136:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1356 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7084 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6252 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7084 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1356 | svchost.exe | 2.20.245.136:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1356 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5920 | swift-bootstrapper (1).exe | 128.116.44.4:443 | clientsettings.roblox.com | ROBLOX-PRODUCTION | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5920 | swift-bootstrapper (1).exe | 188.114.97.3:443 | bunni.lol | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientsettings.roblox.com |
| whitelisted |
bunni.lol |
| unknown |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |