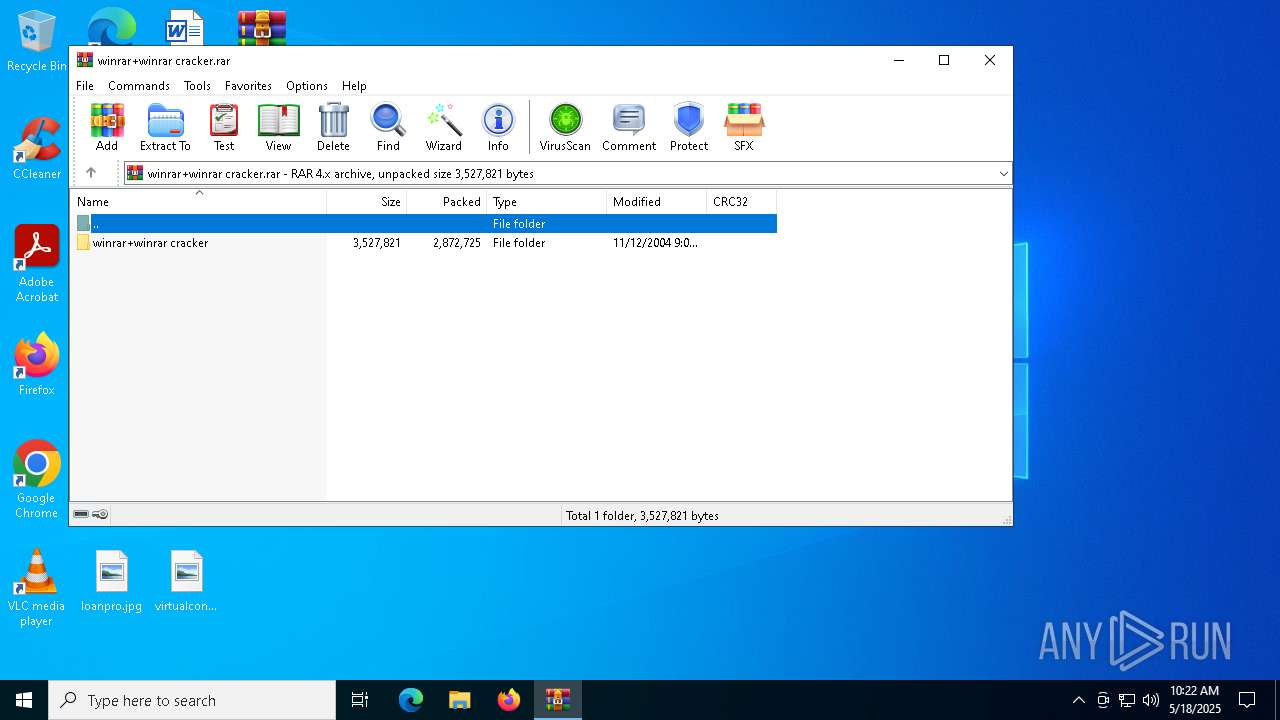
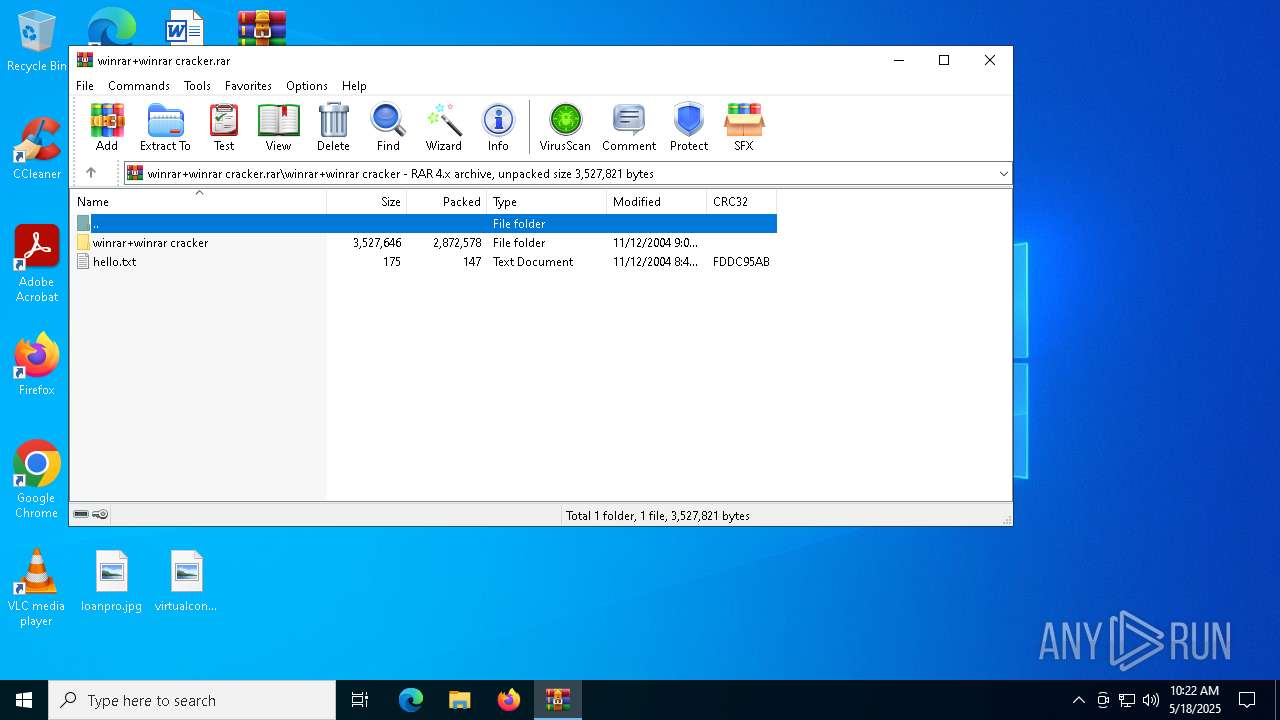
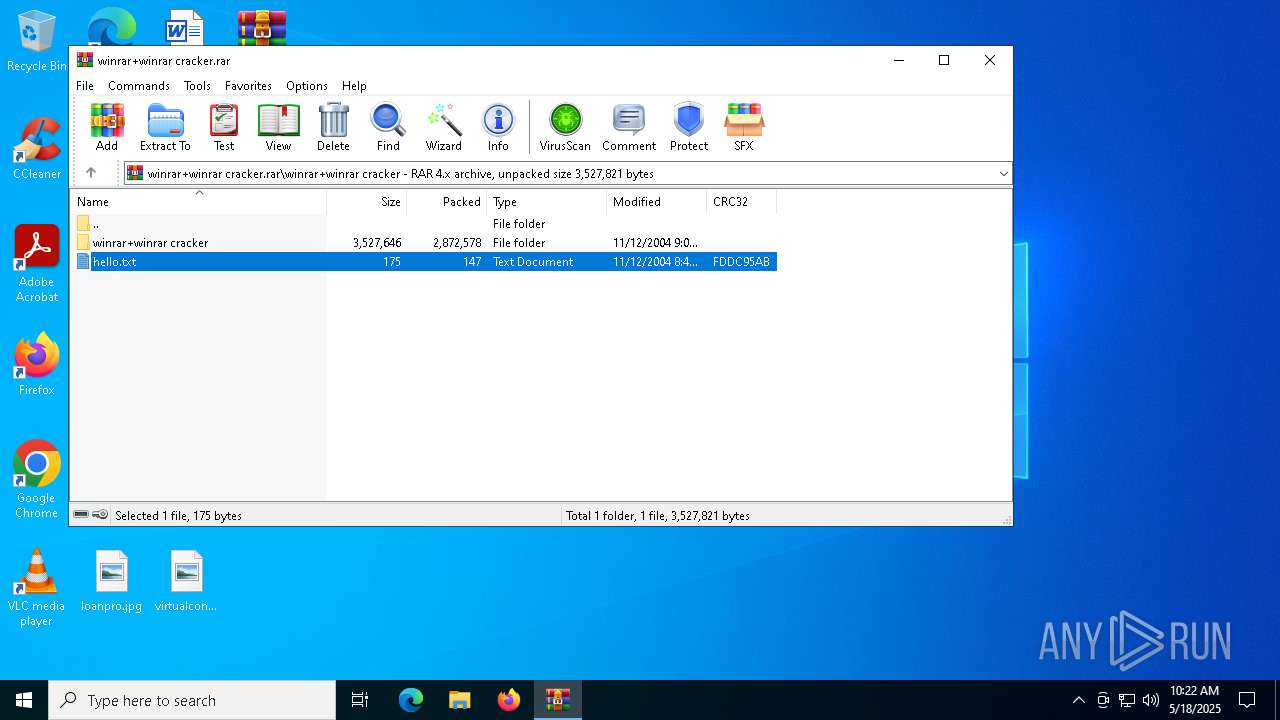
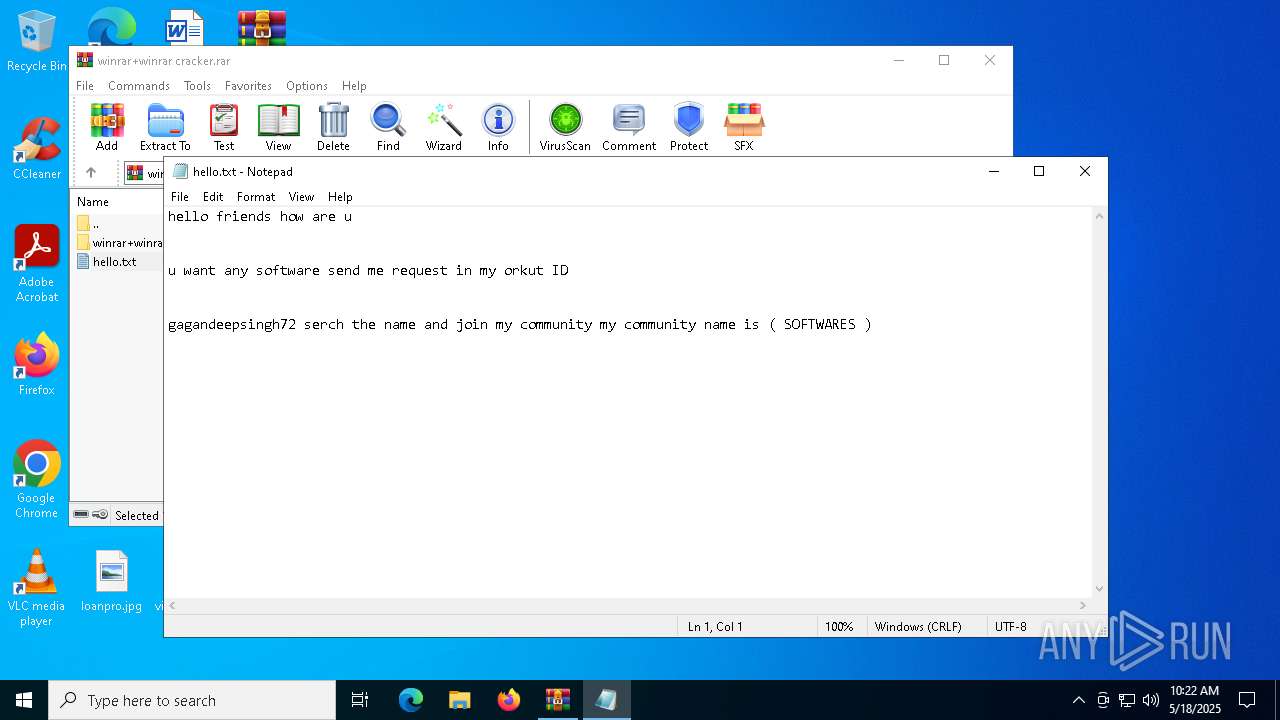
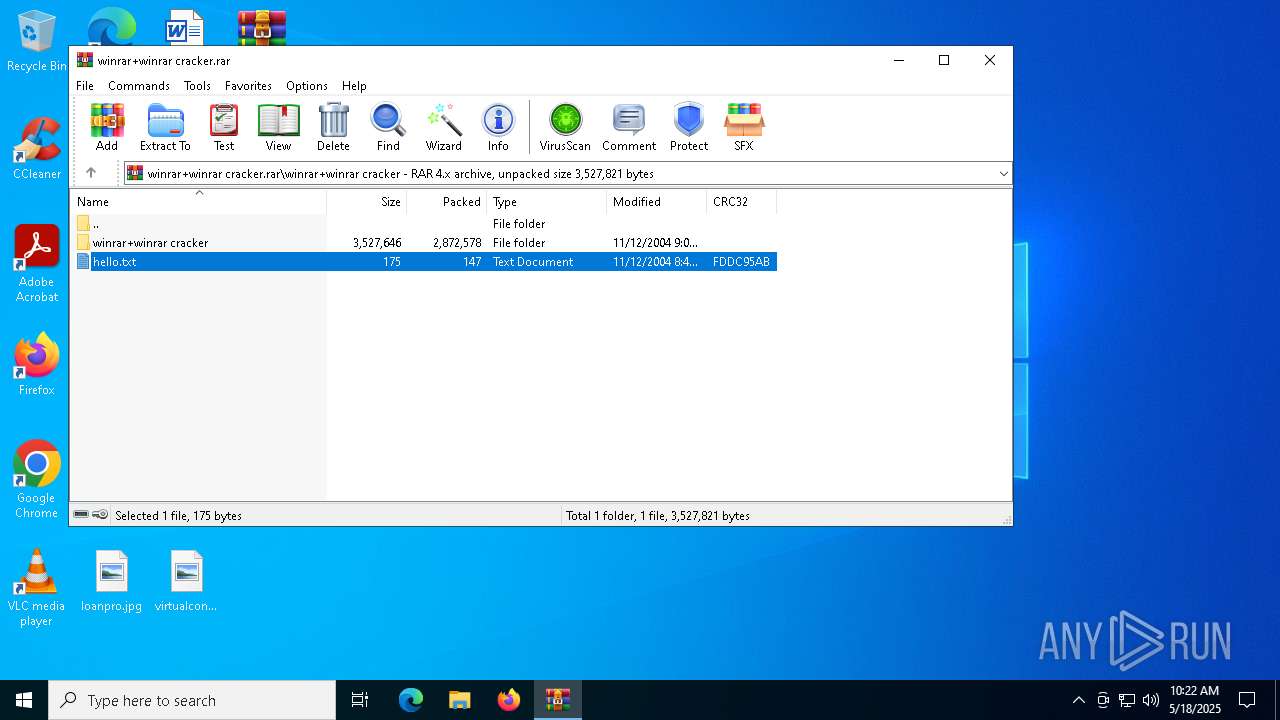
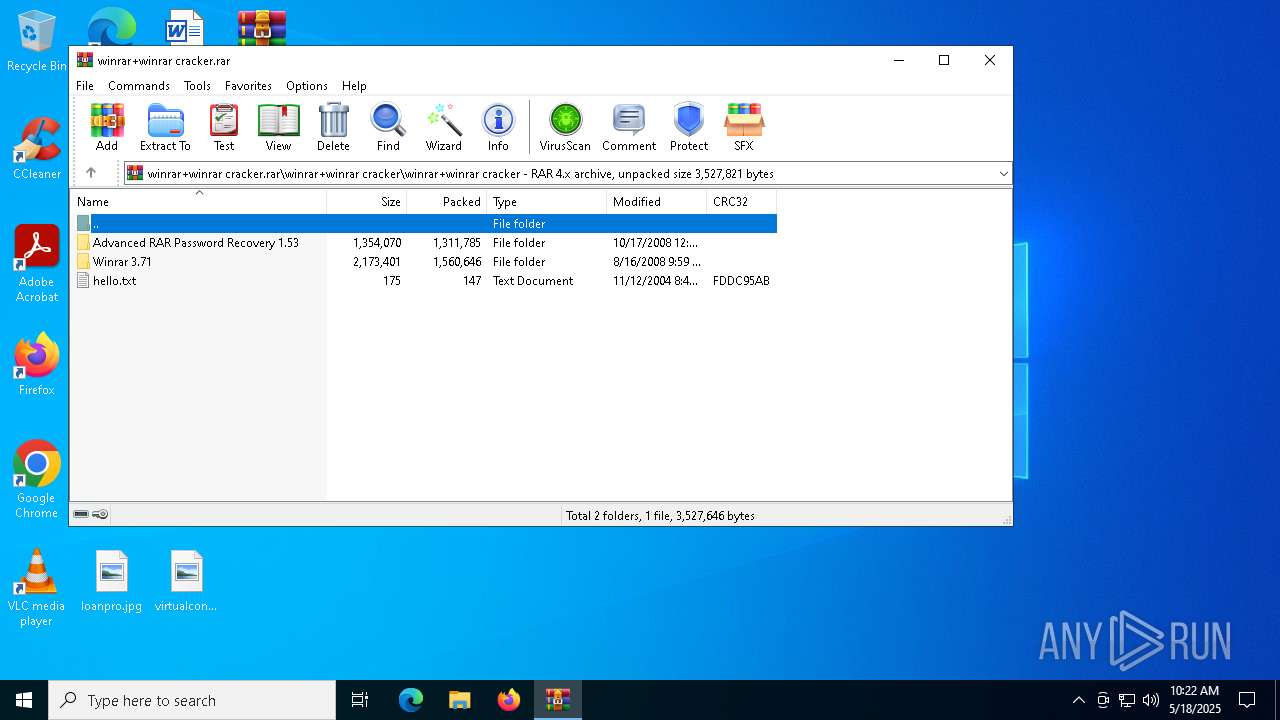
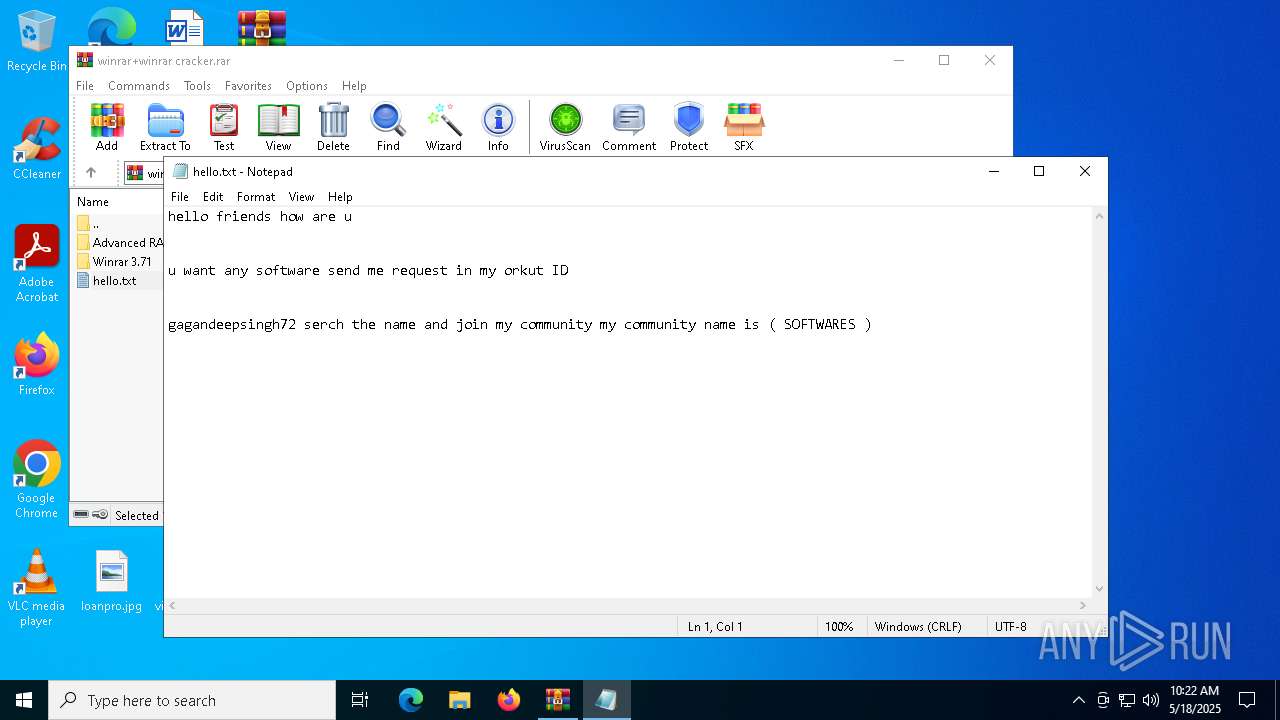
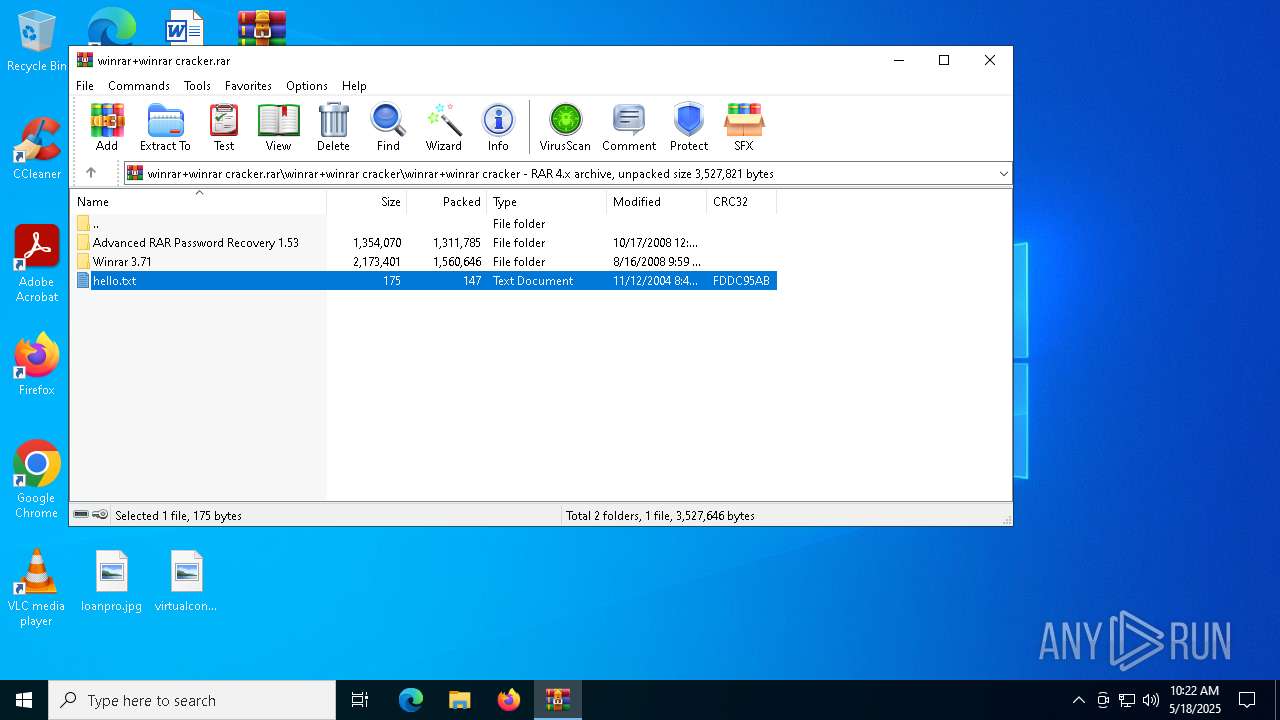
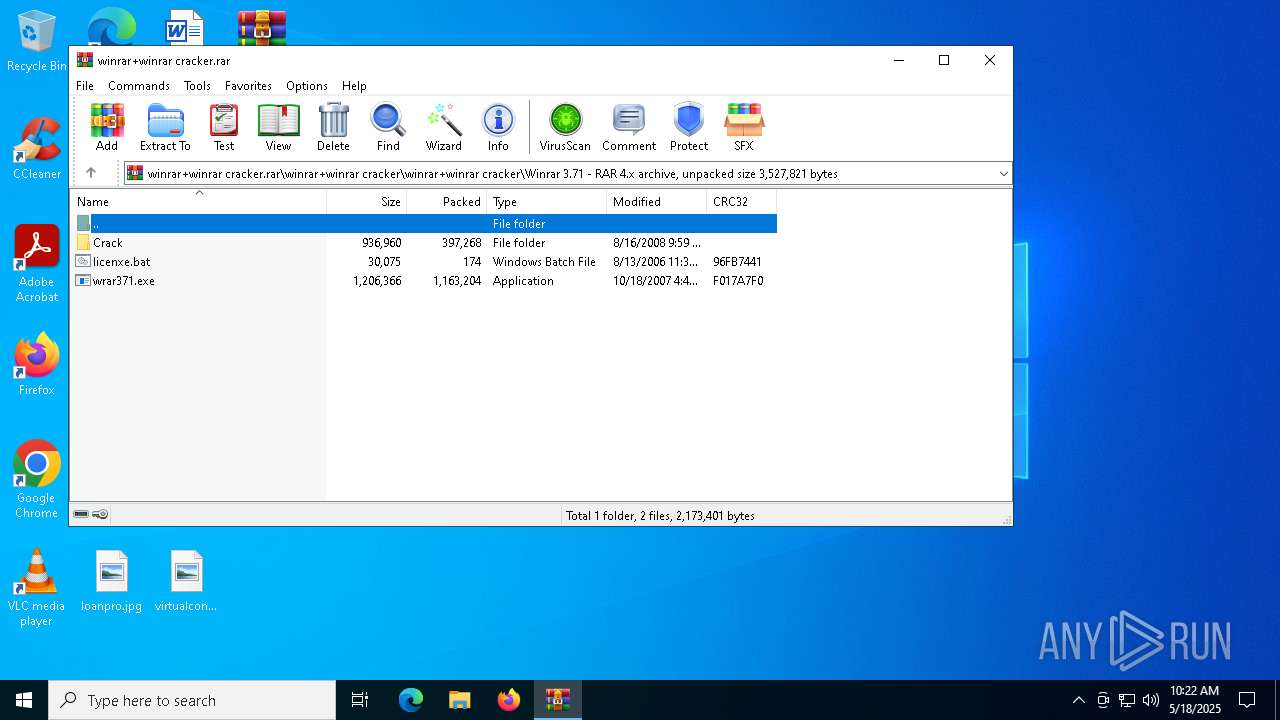
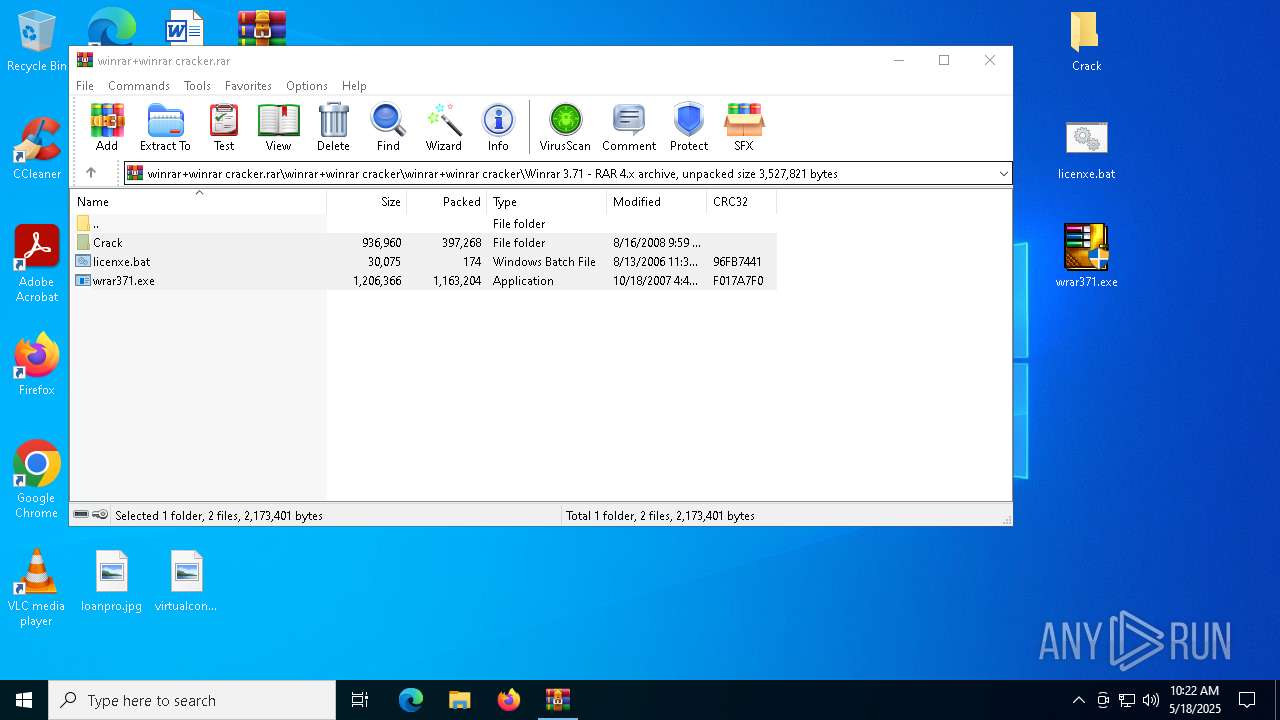
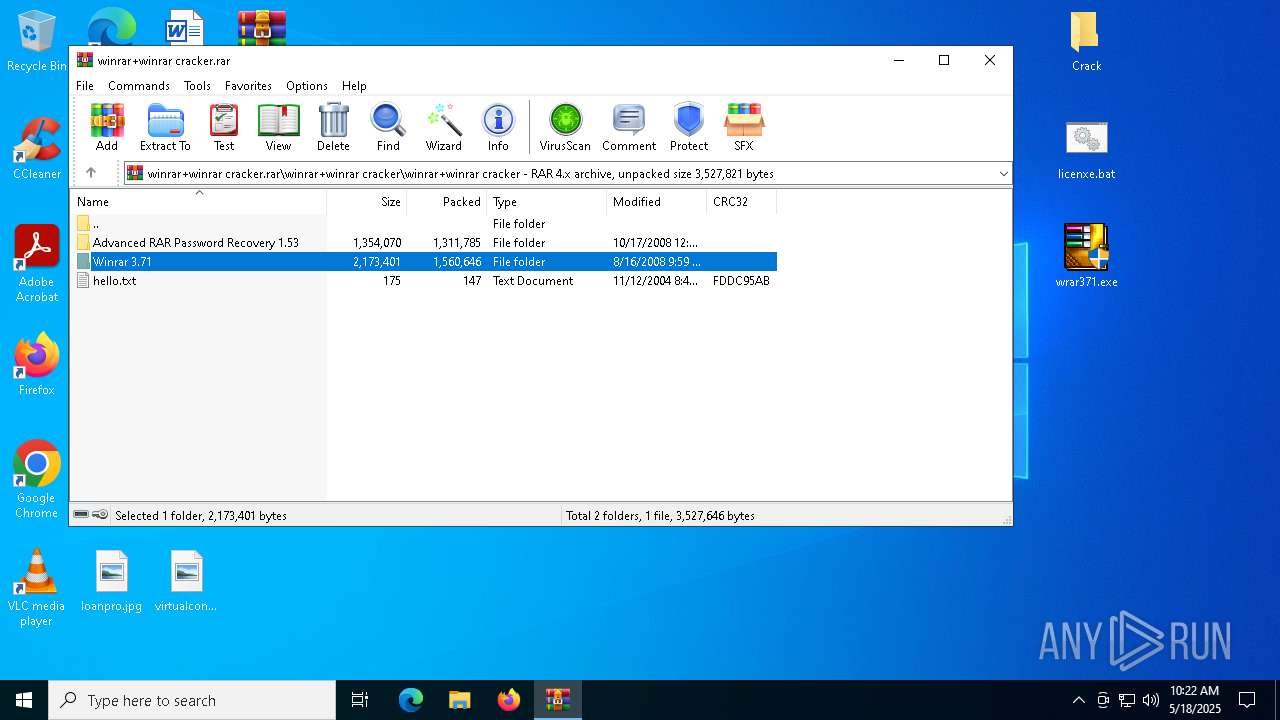
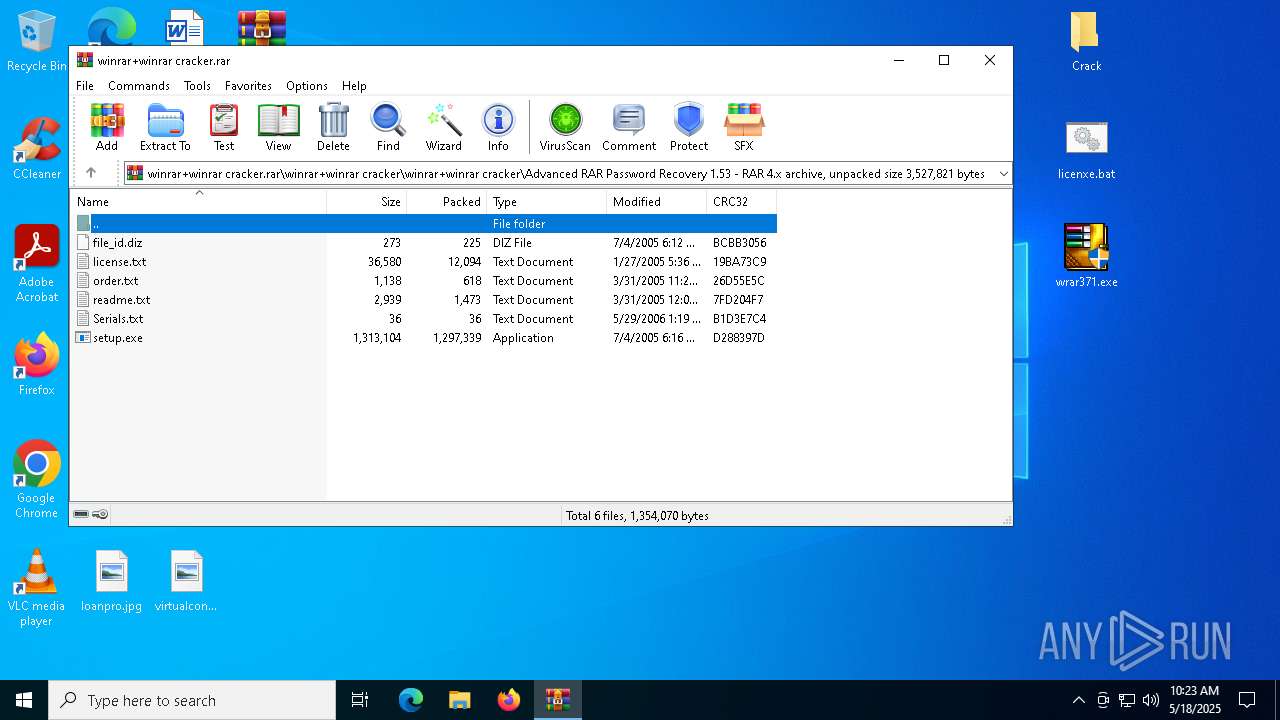
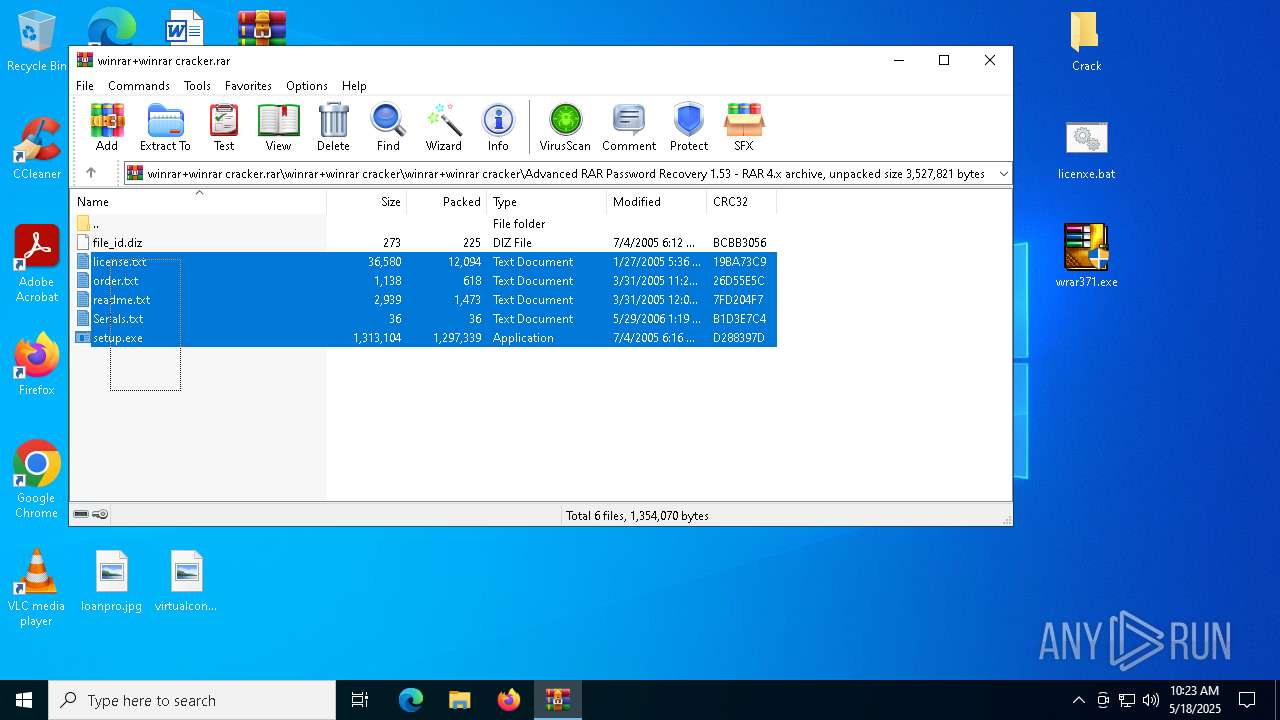
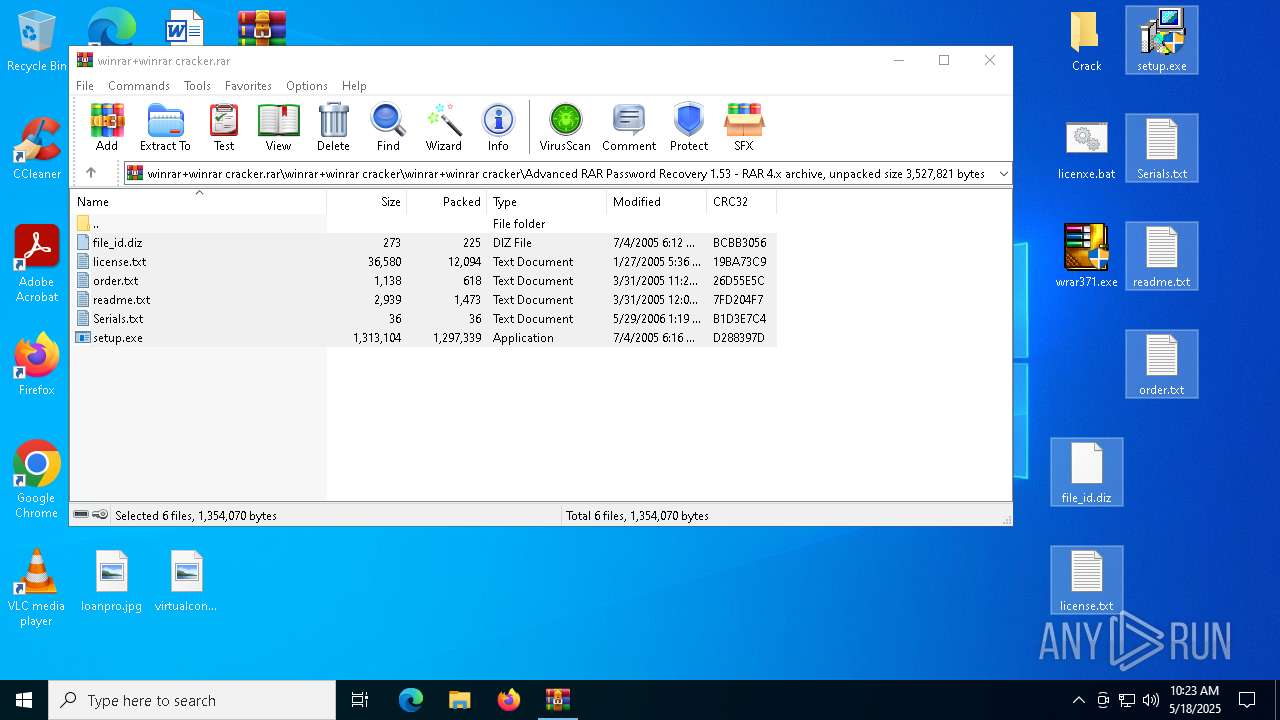
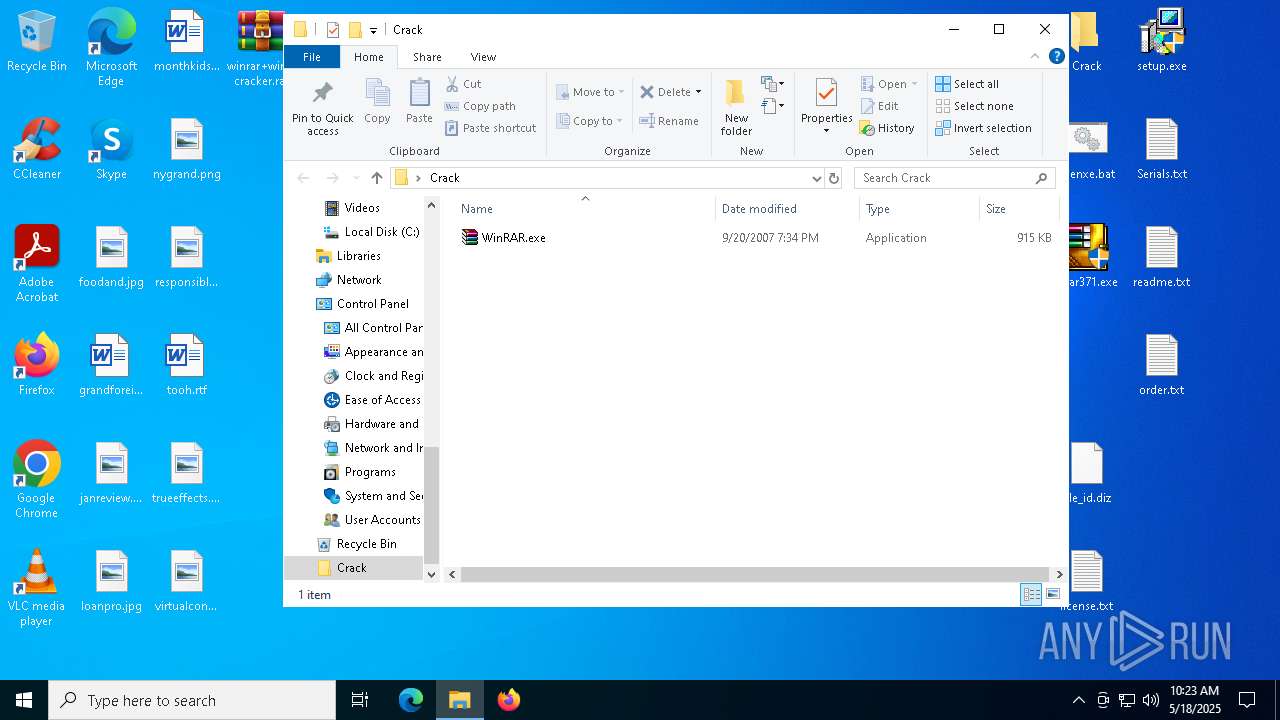
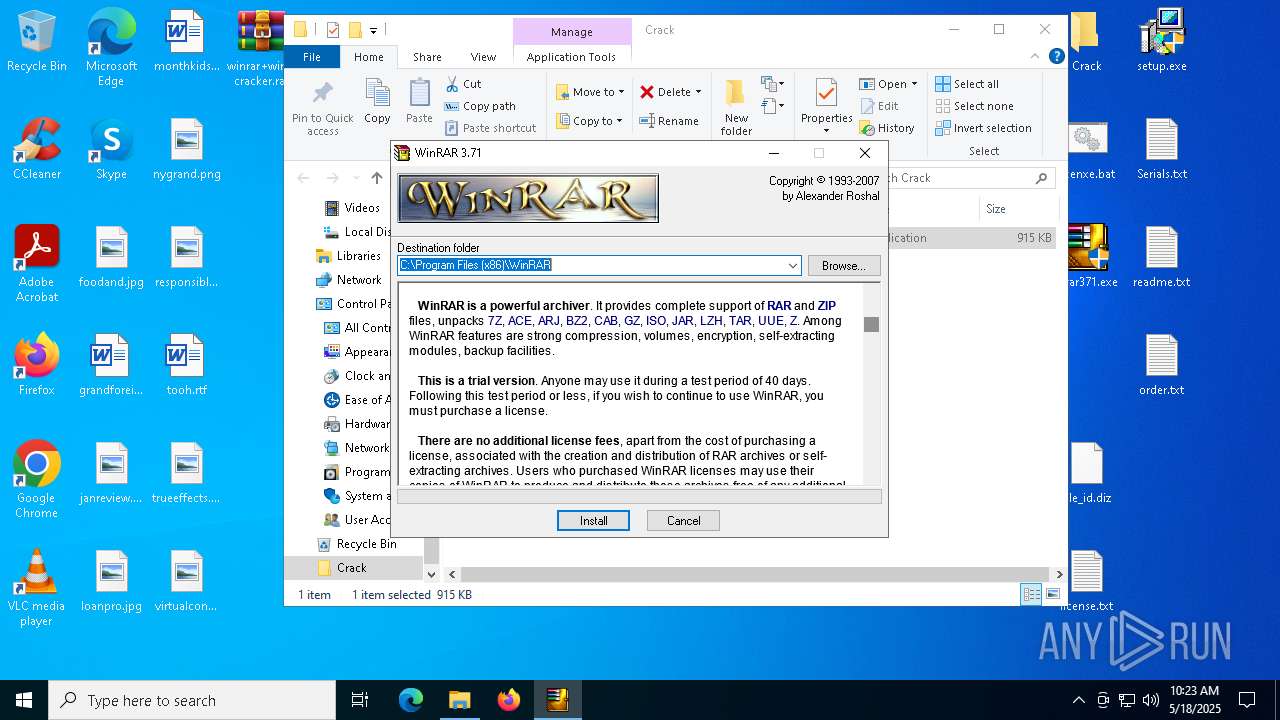
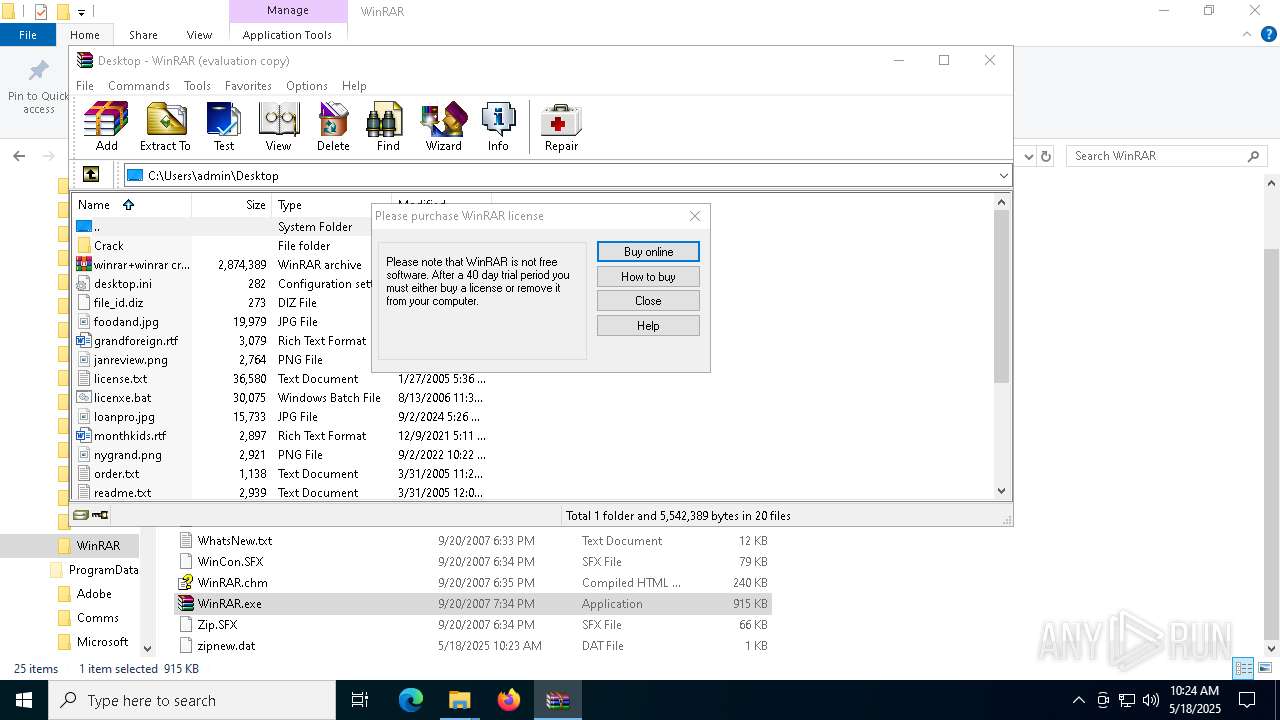
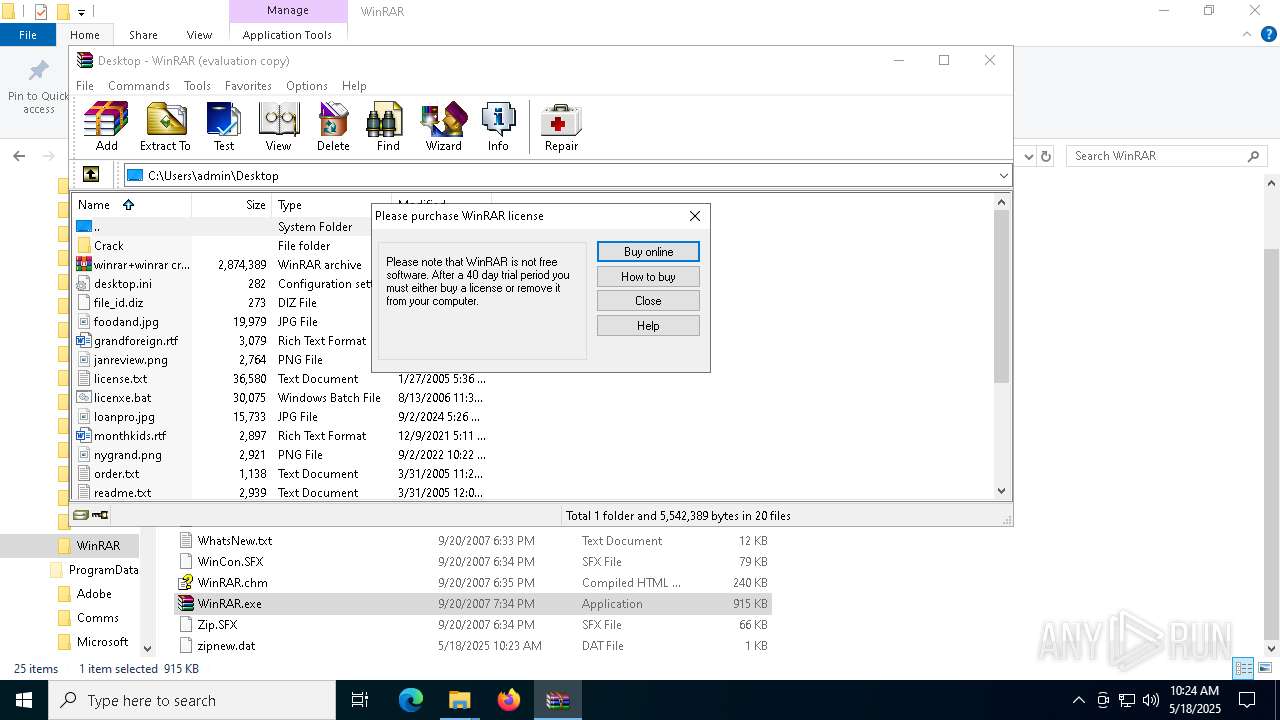
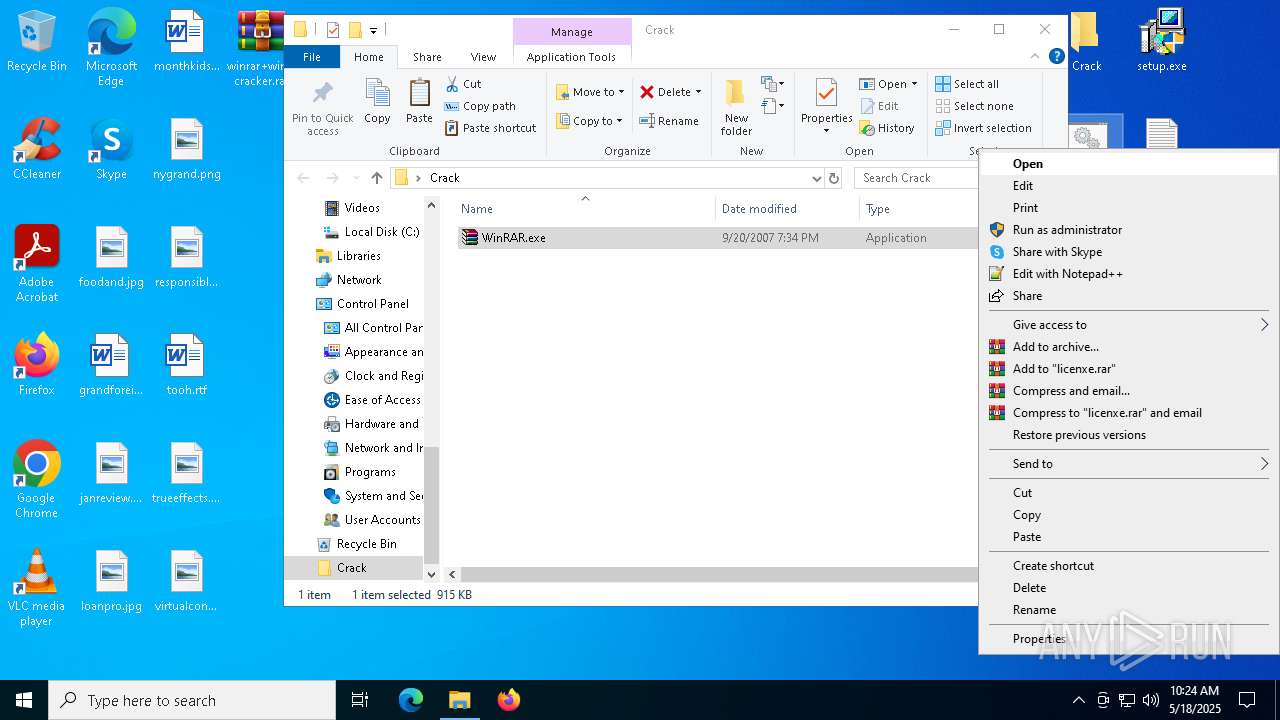
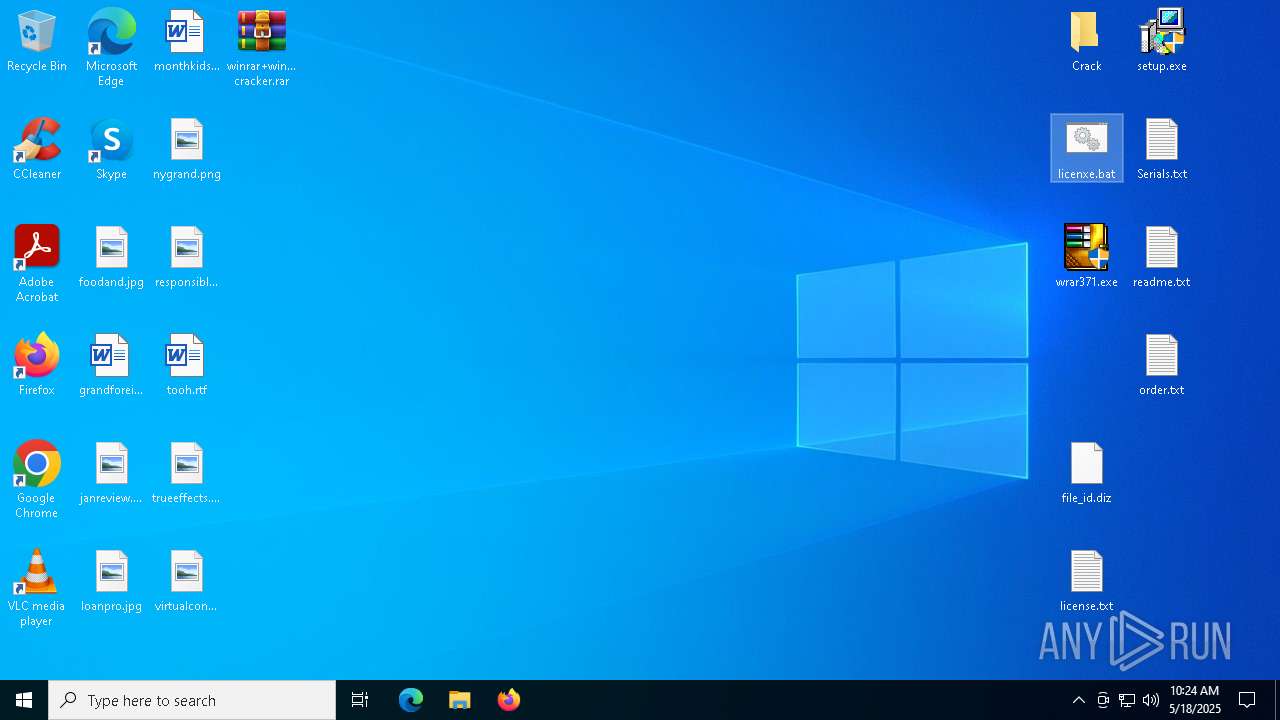
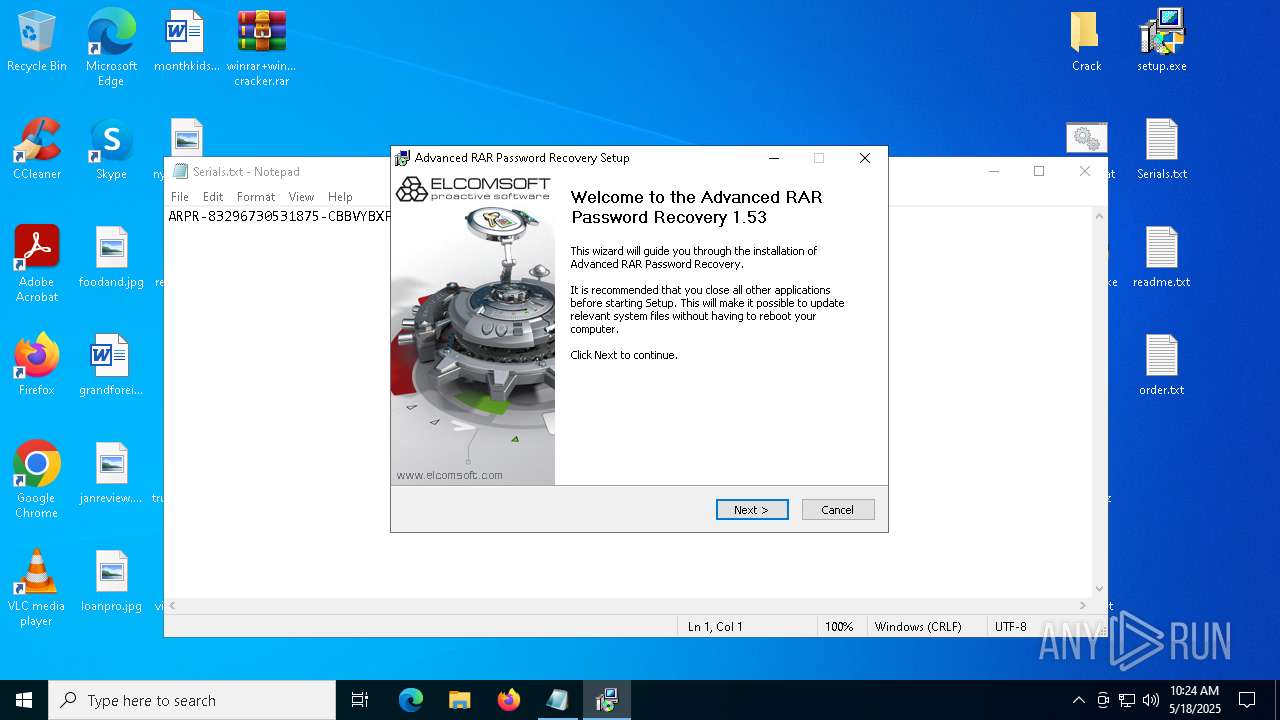
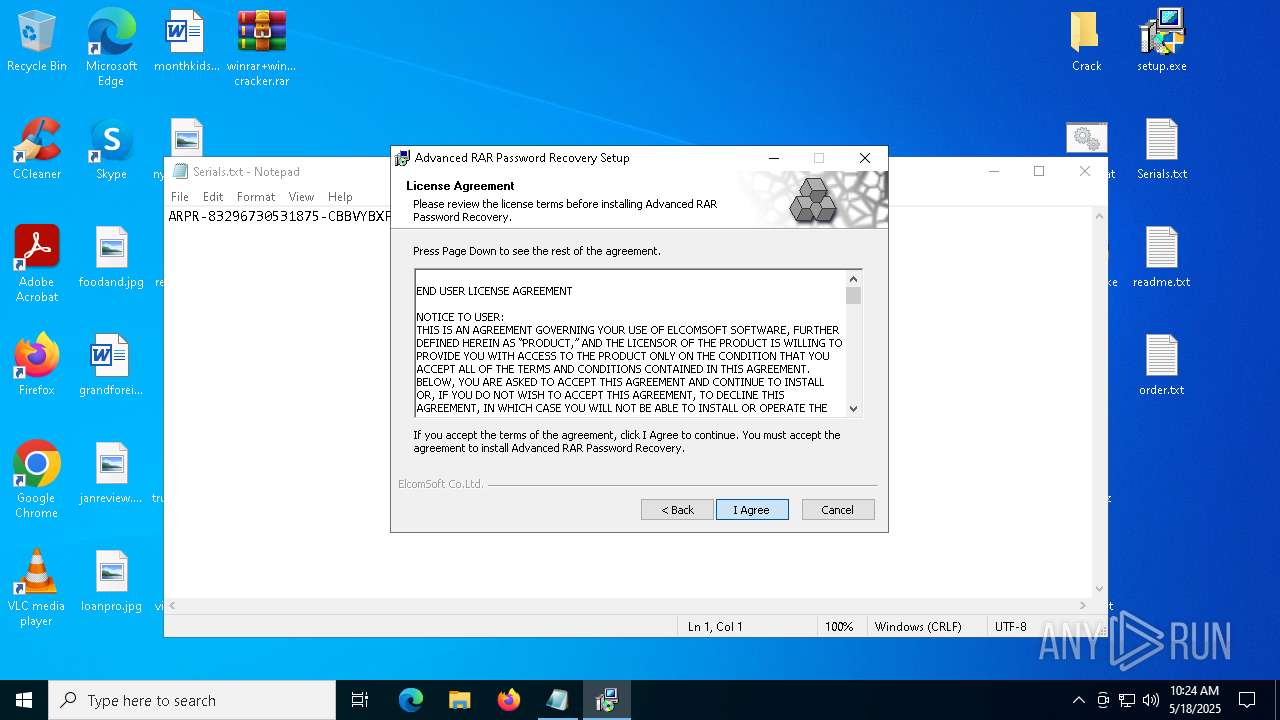
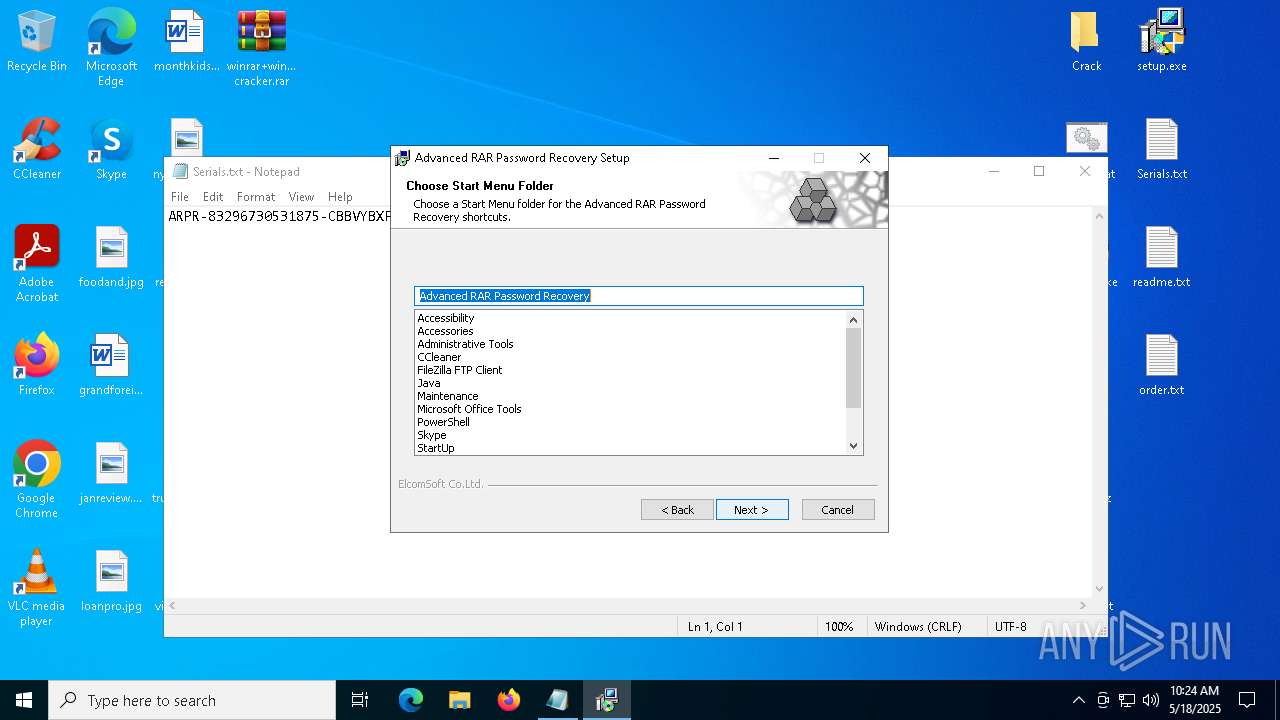
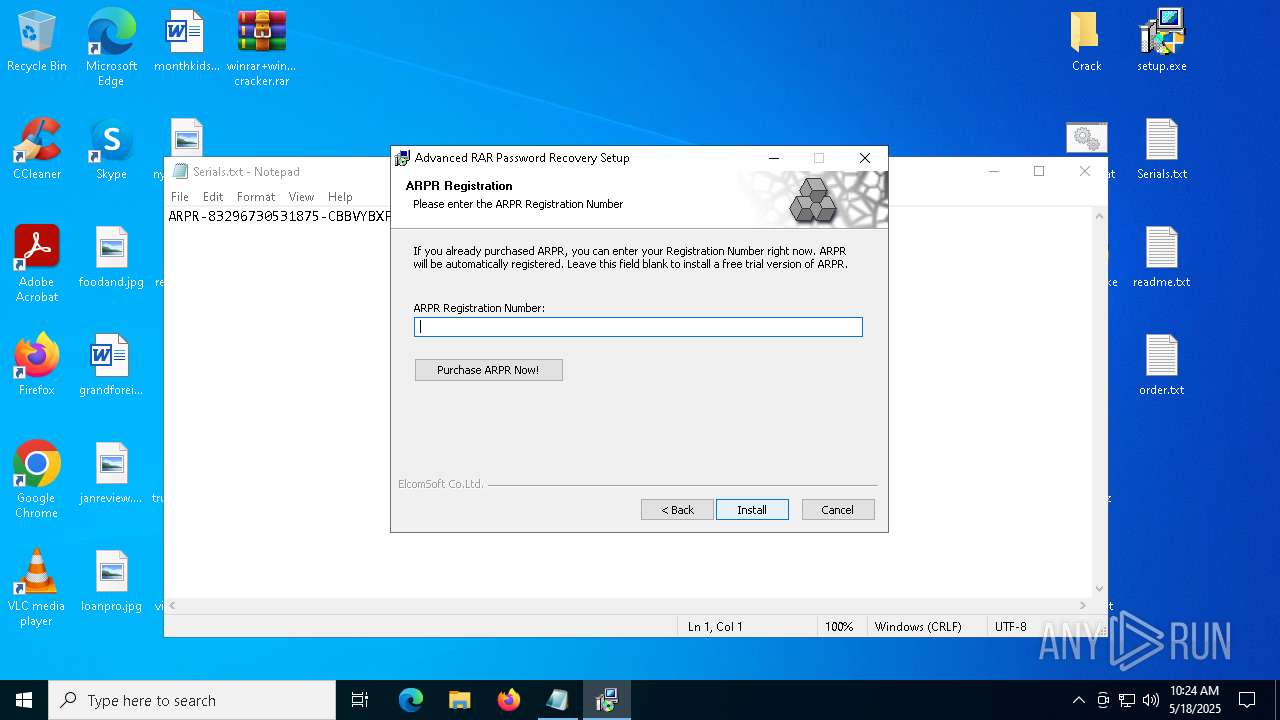
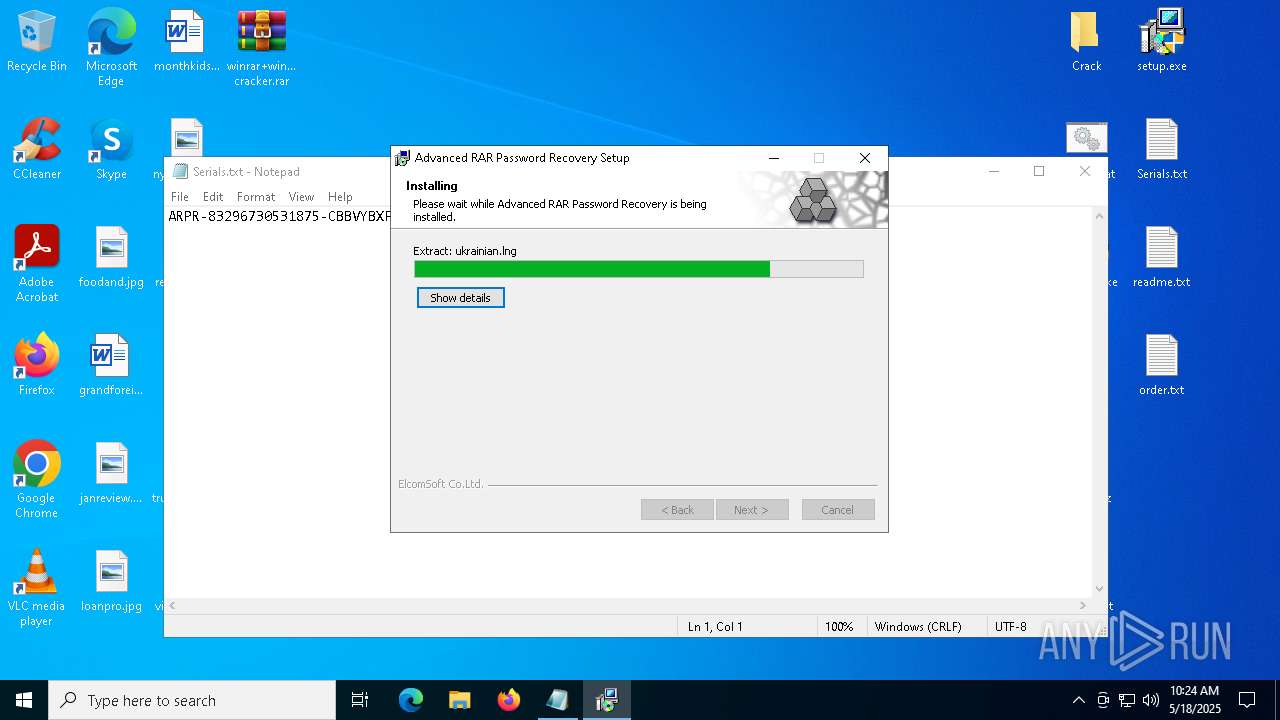
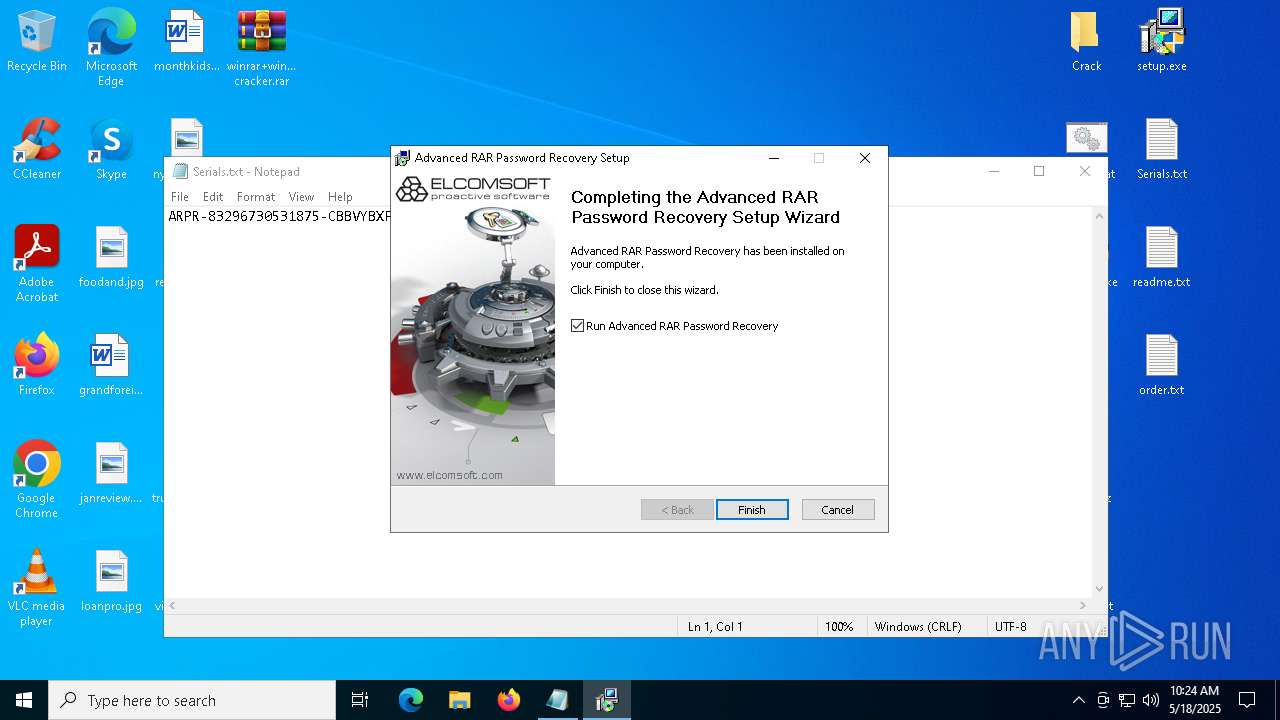
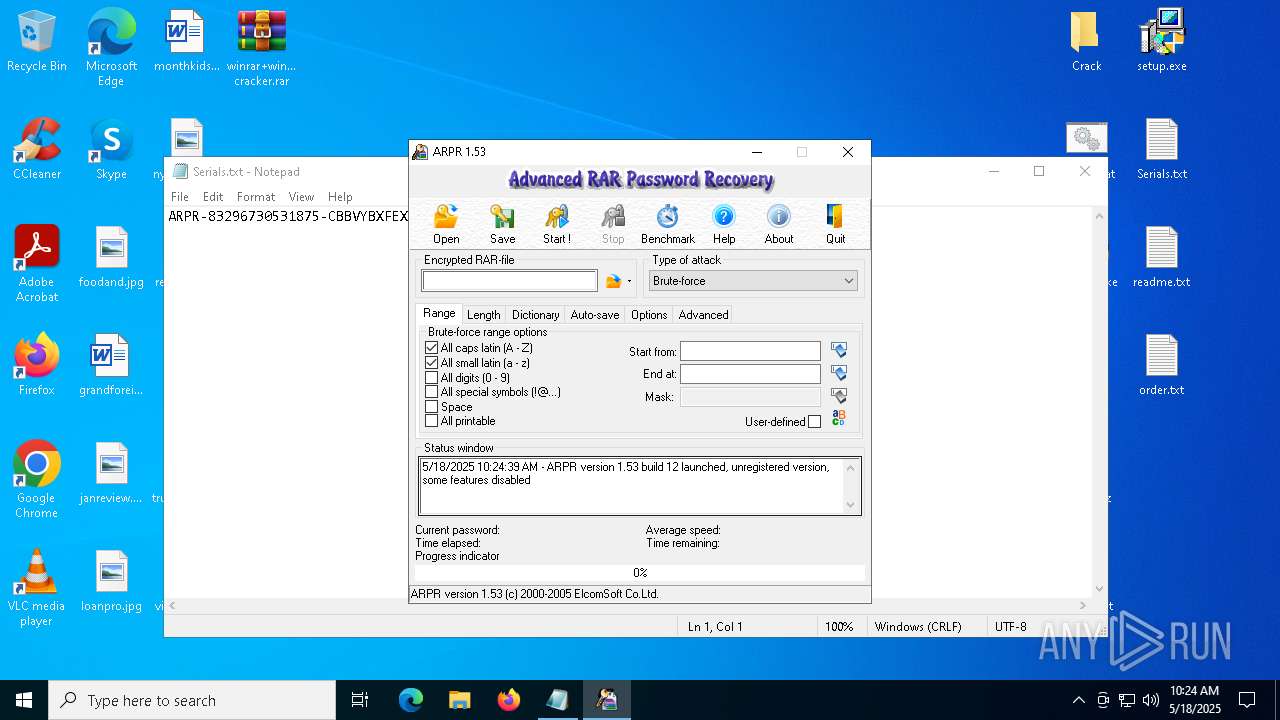
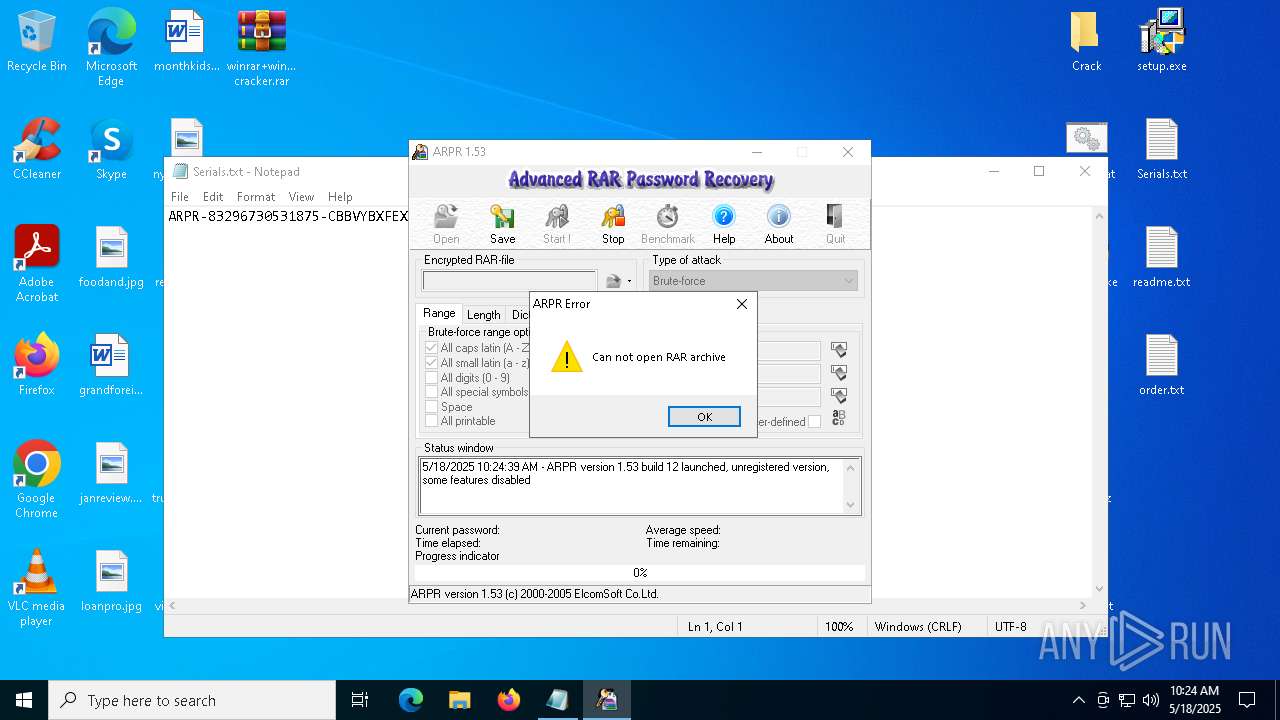
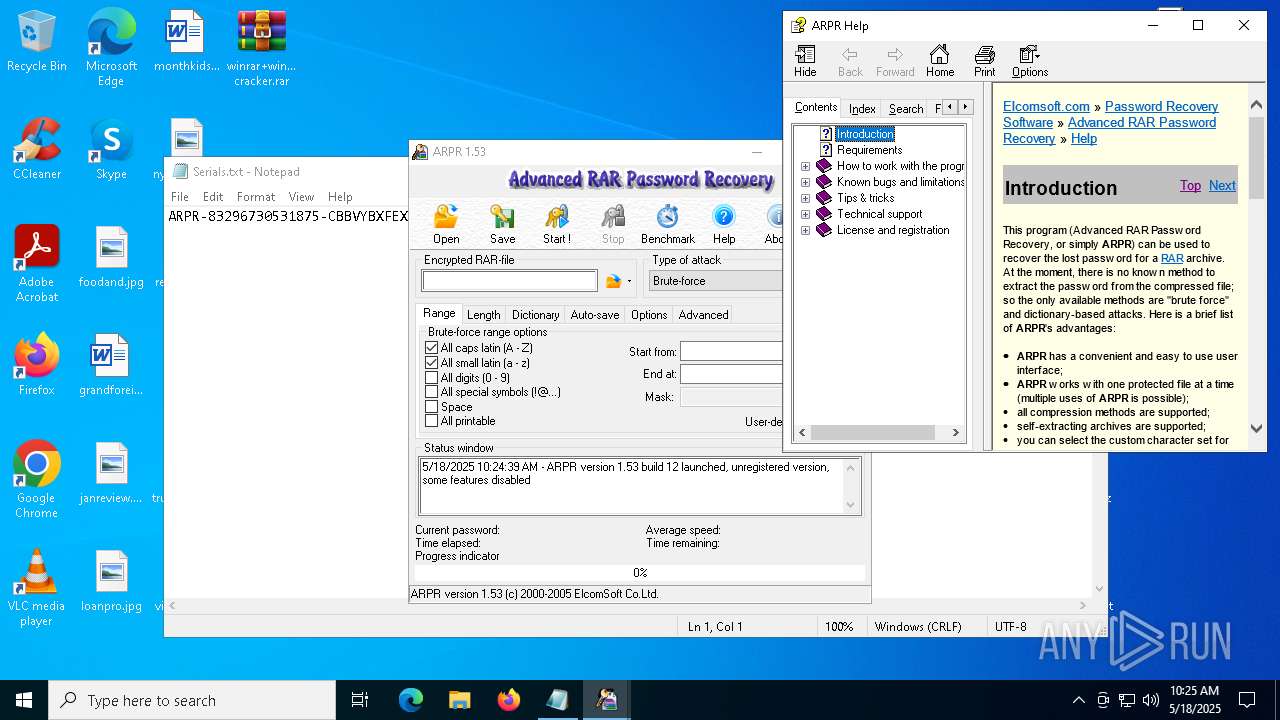
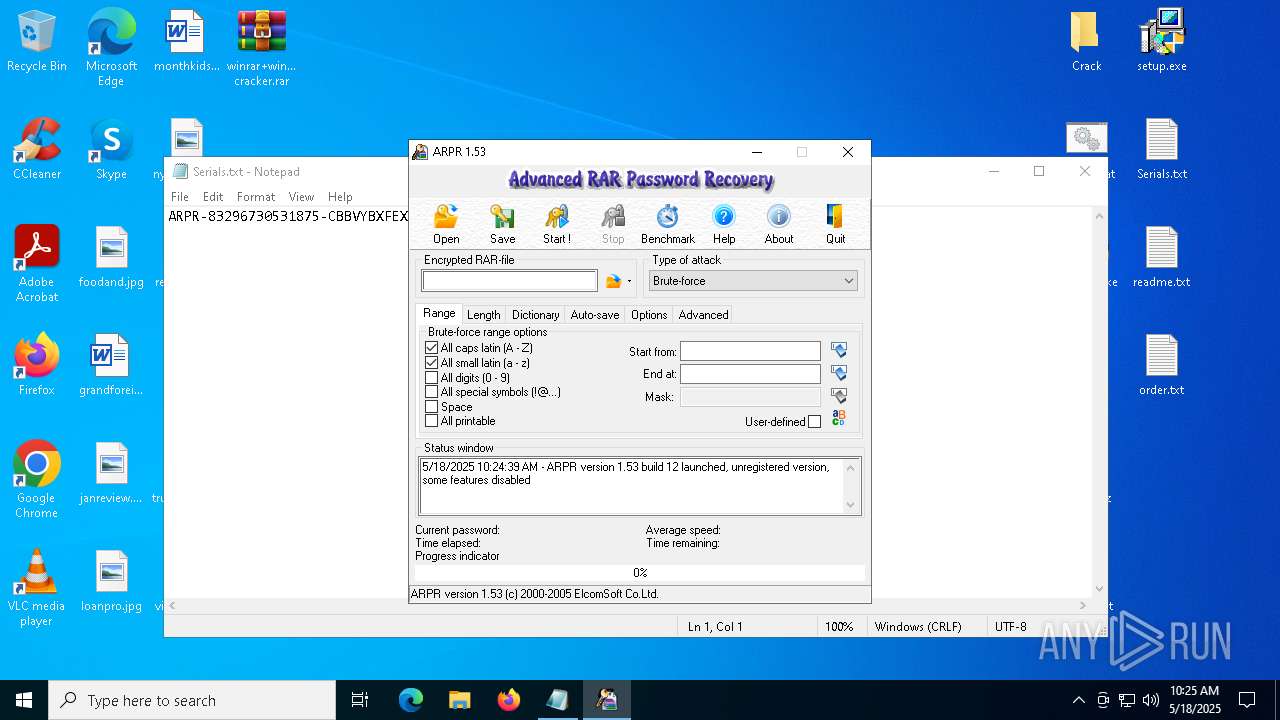
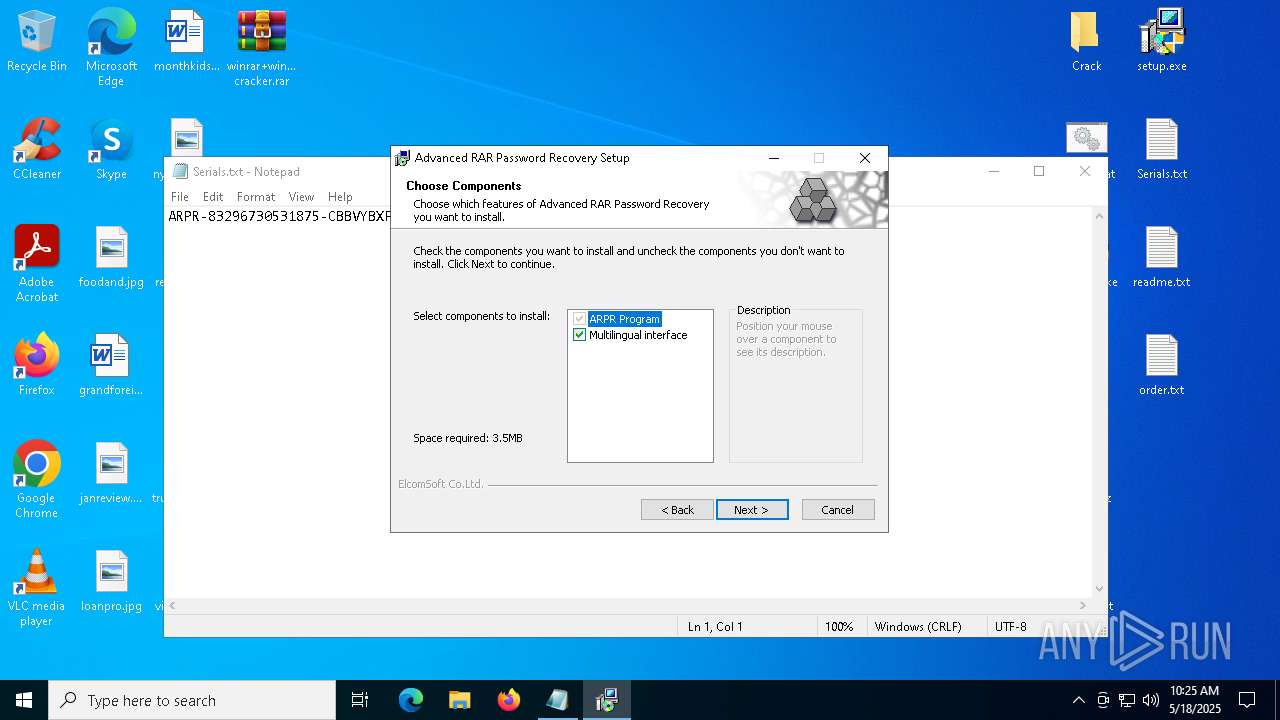
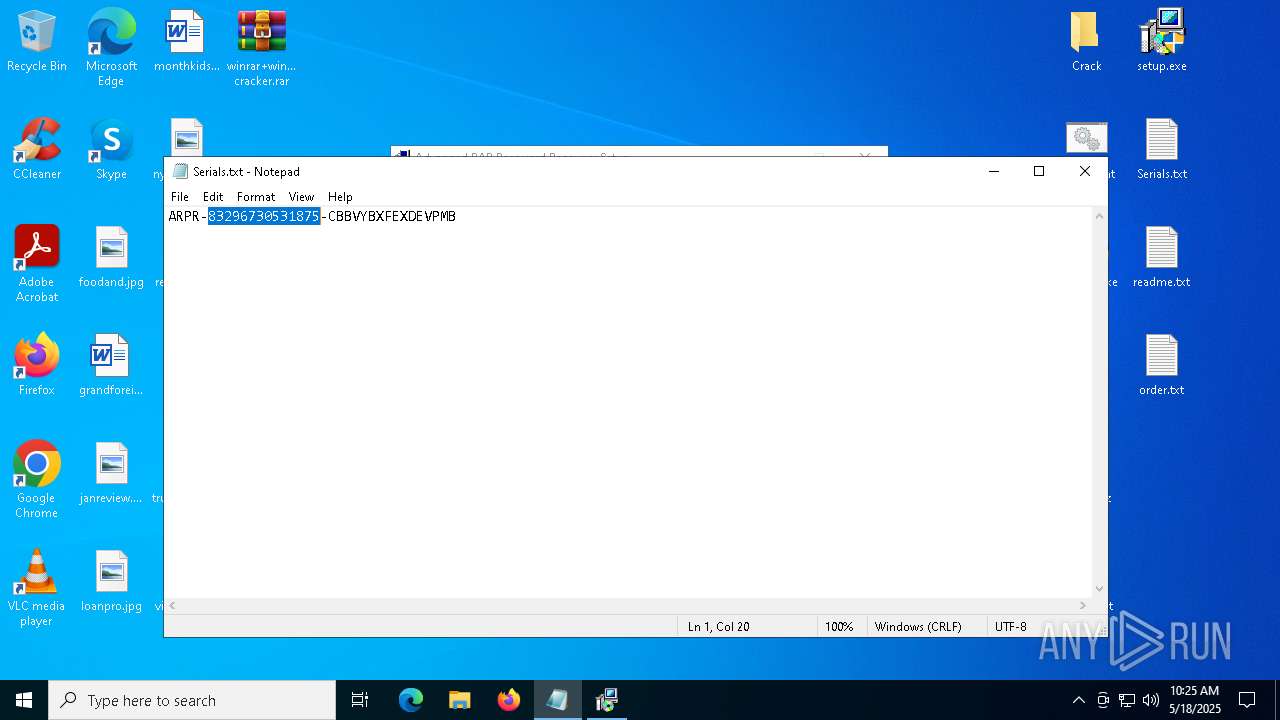
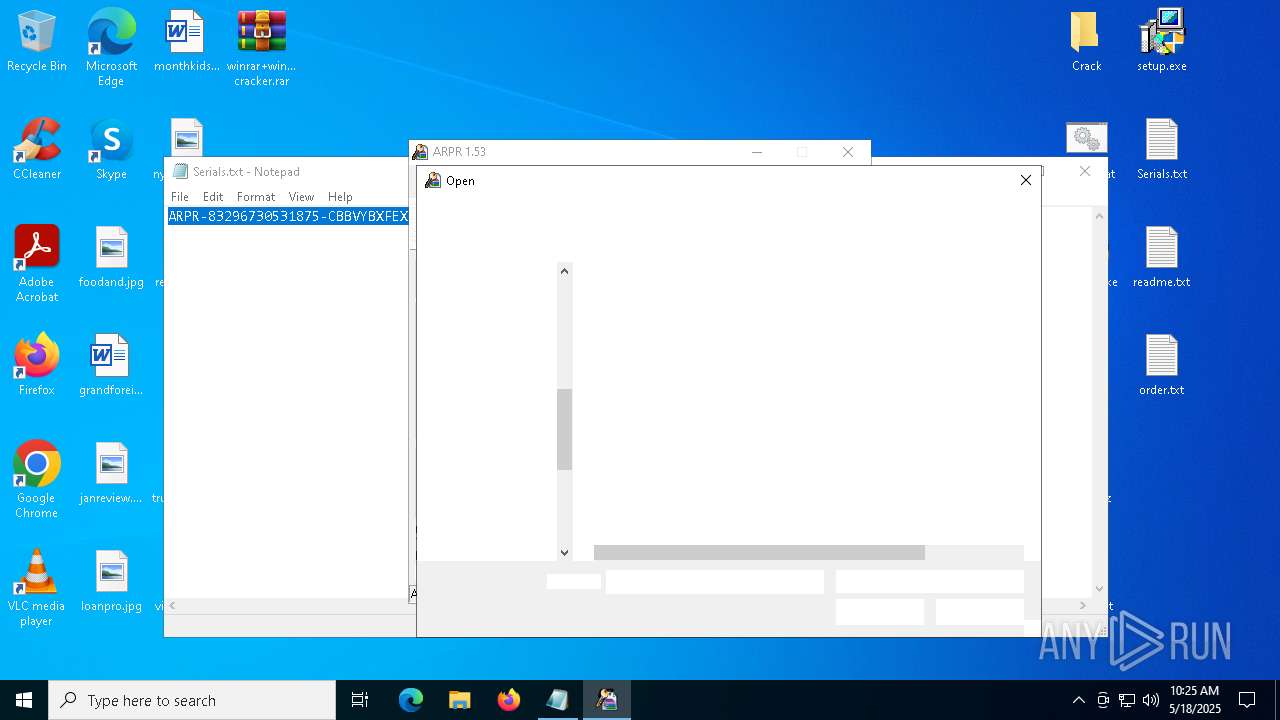
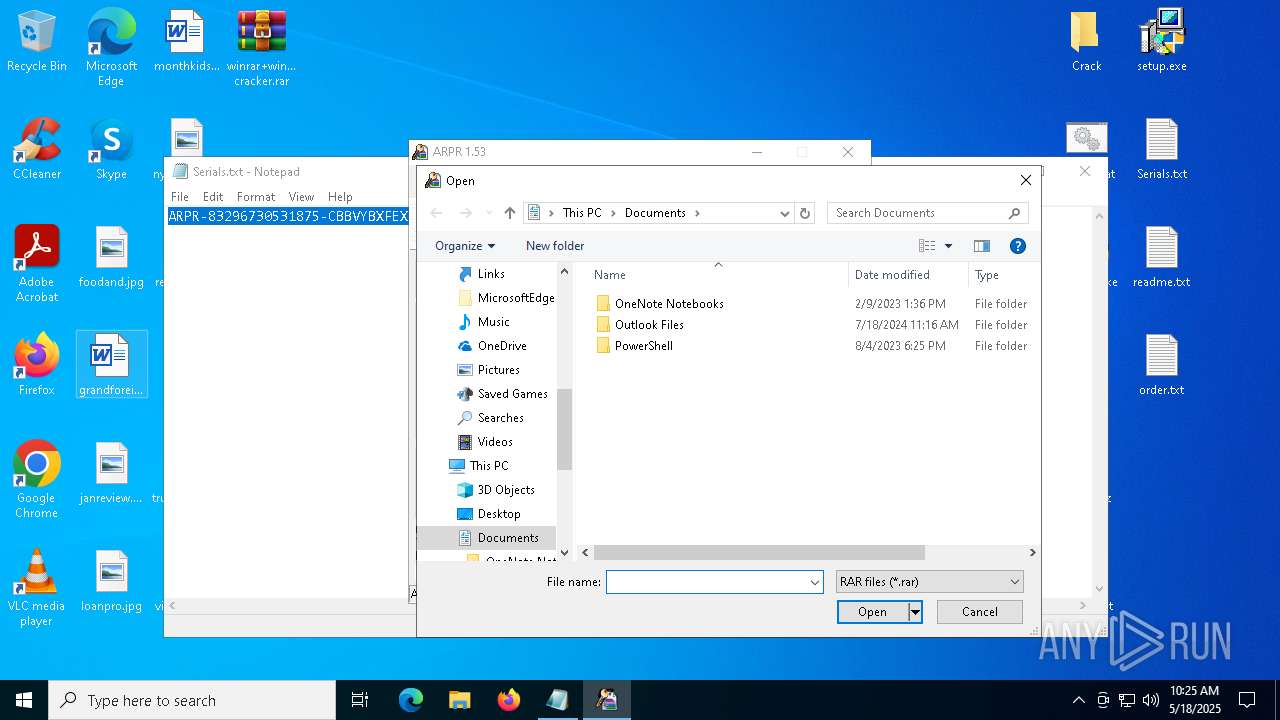
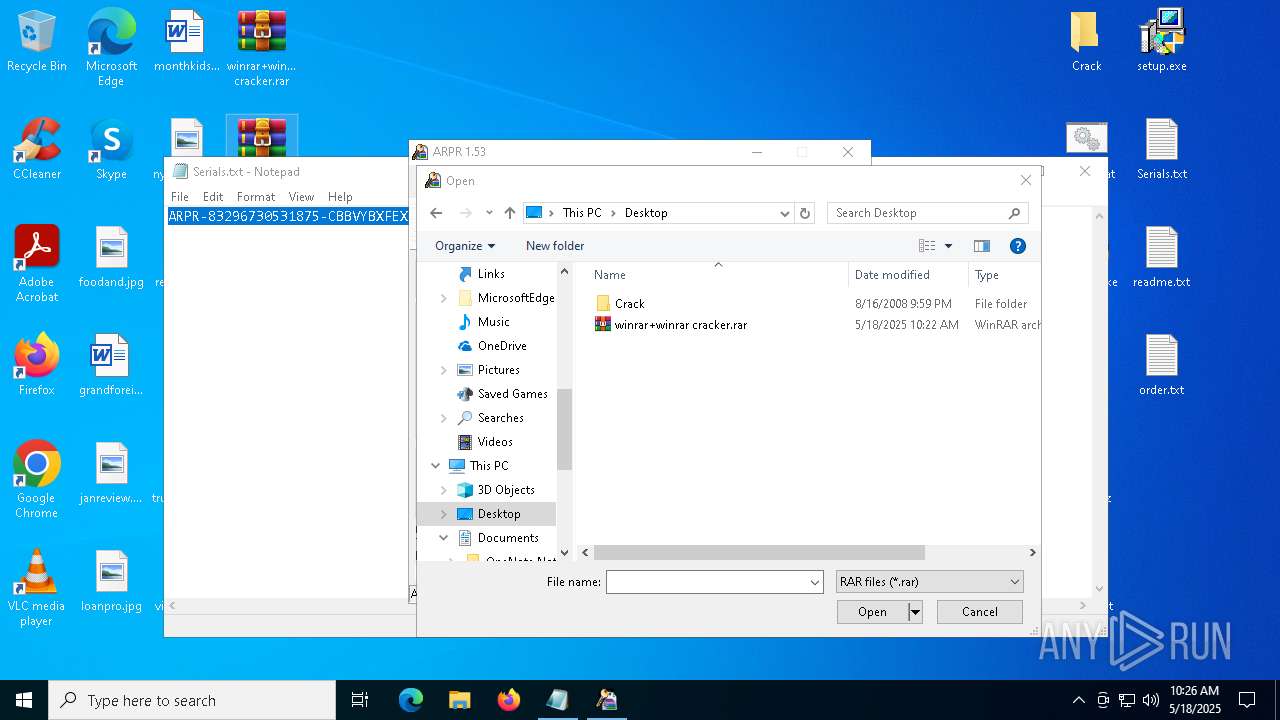
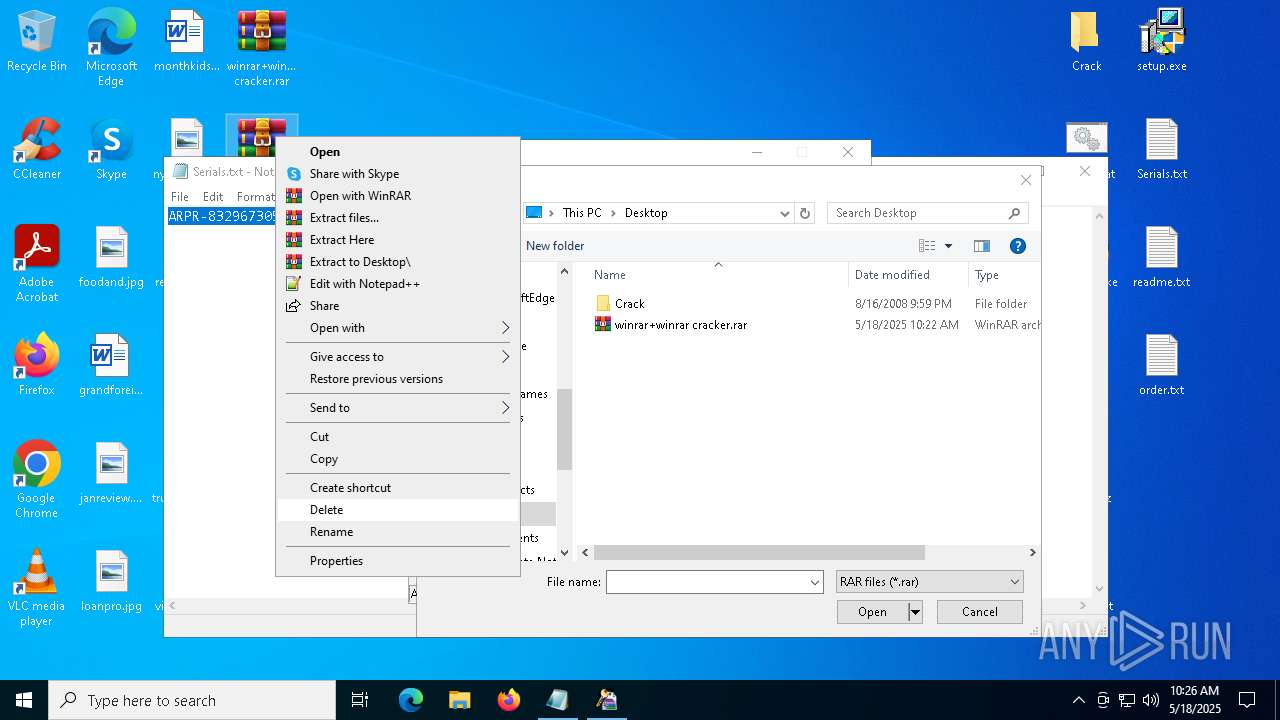
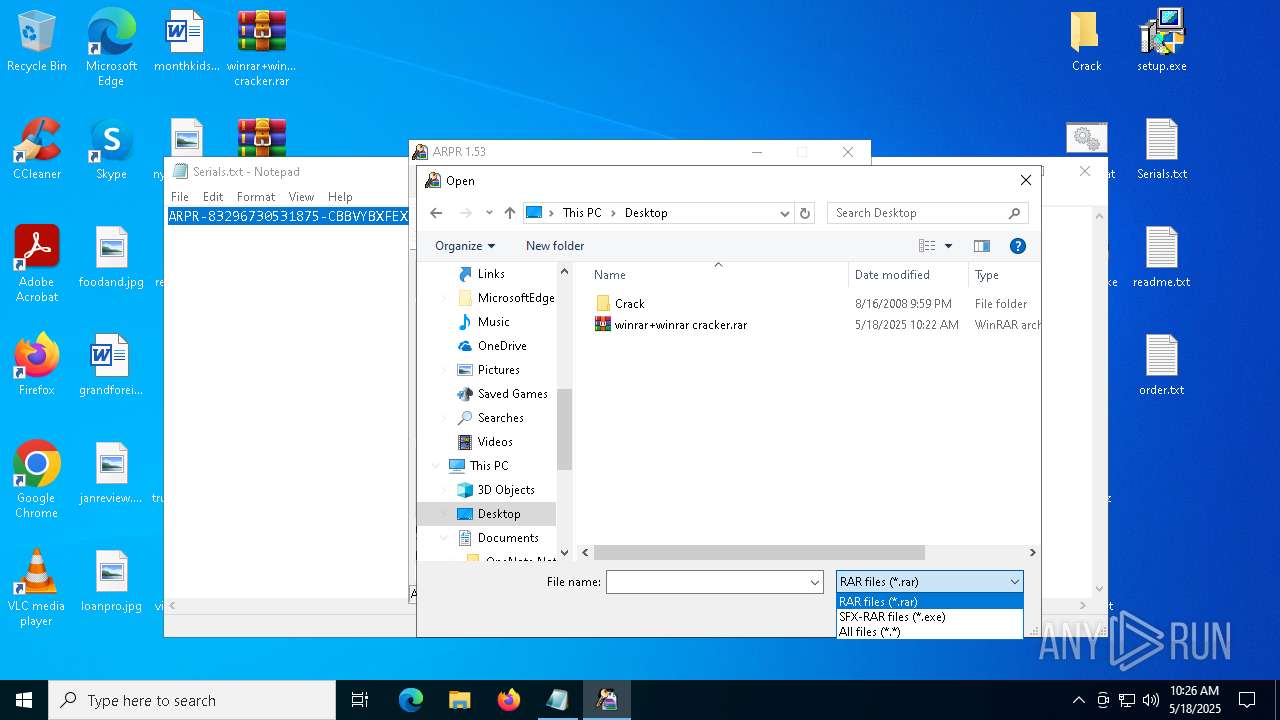
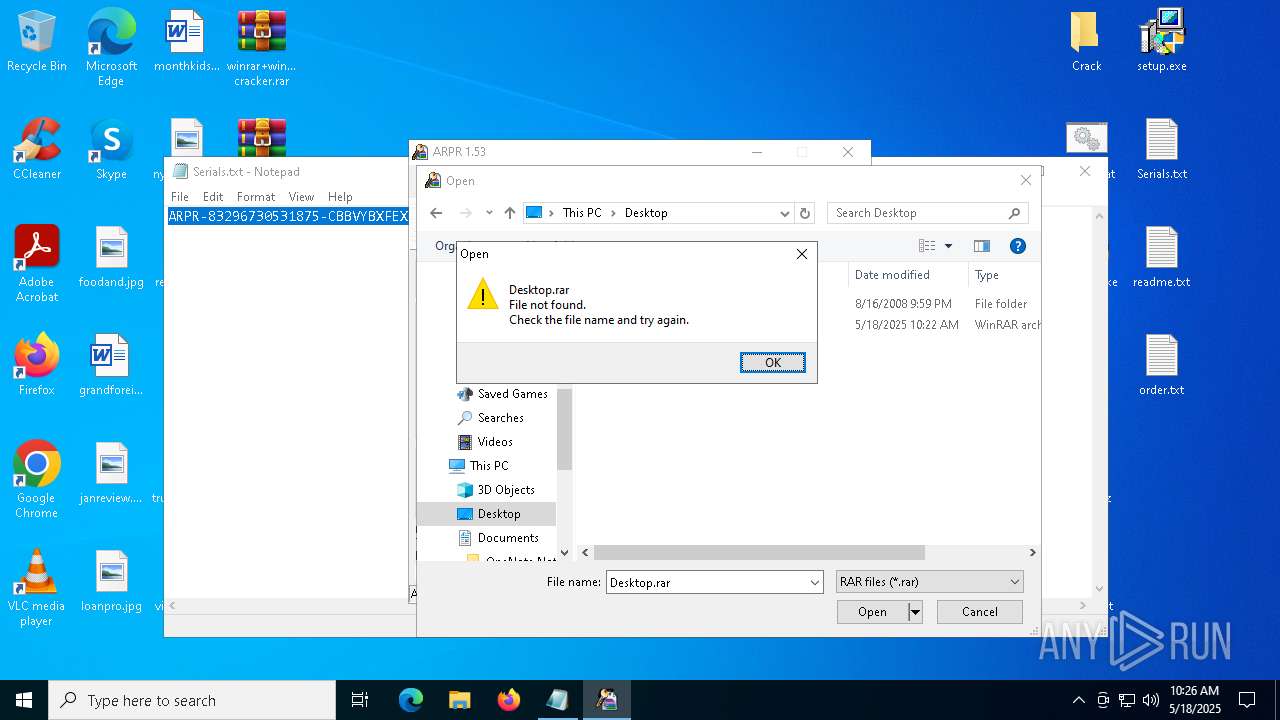
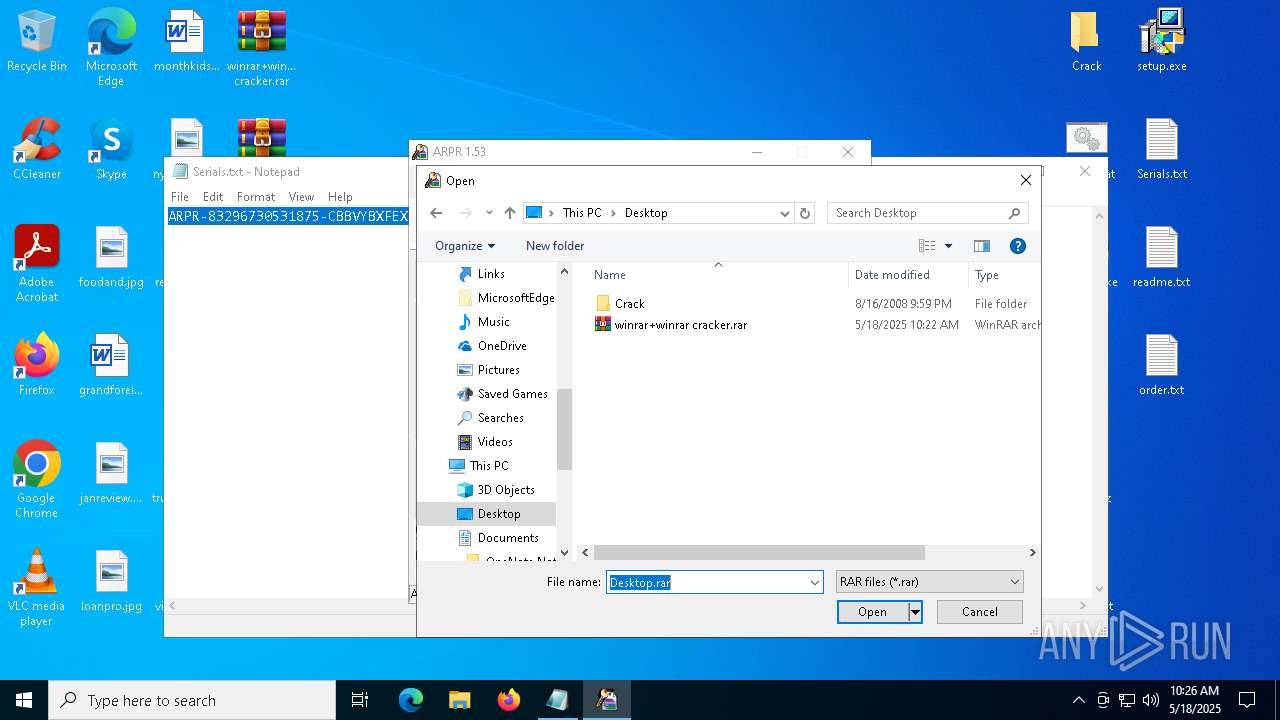
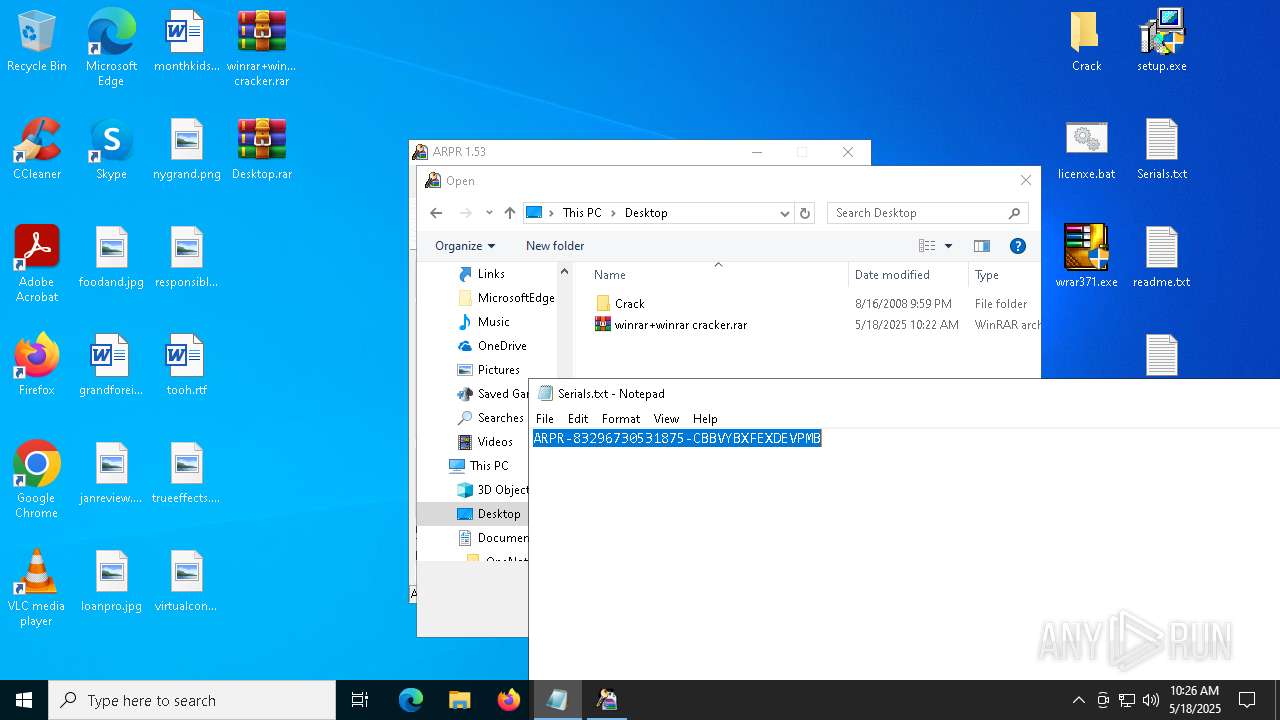
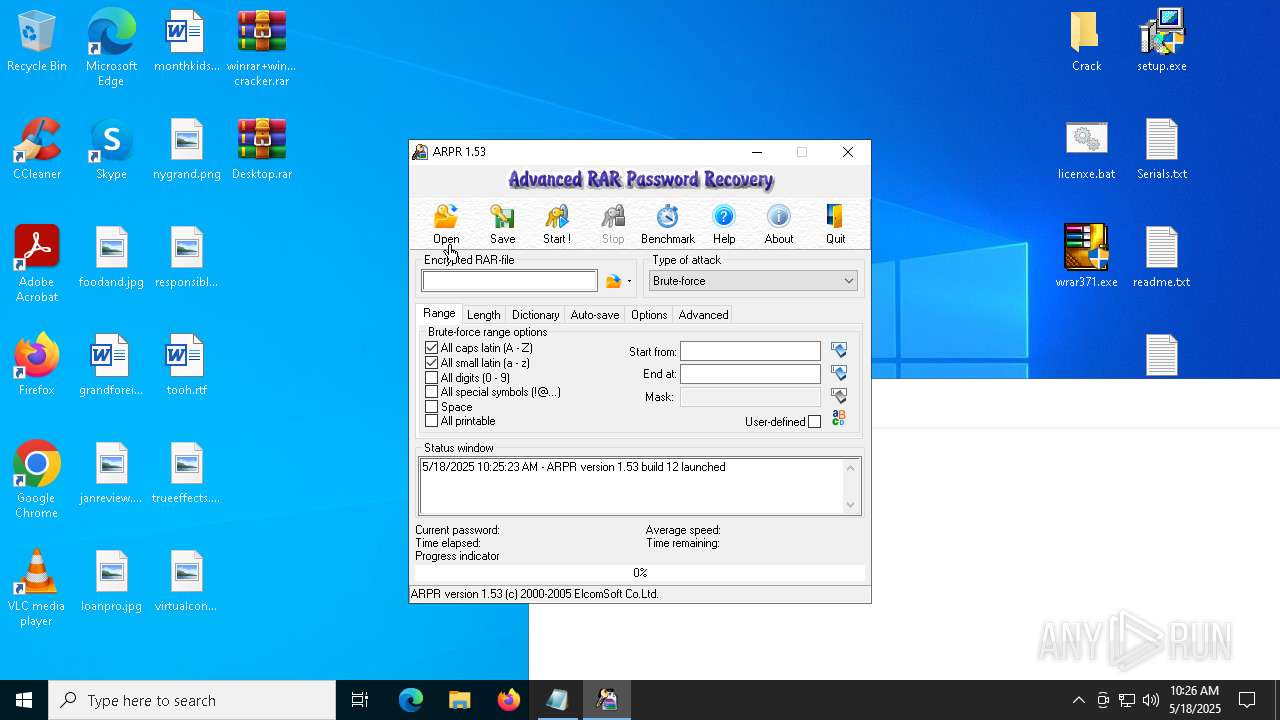
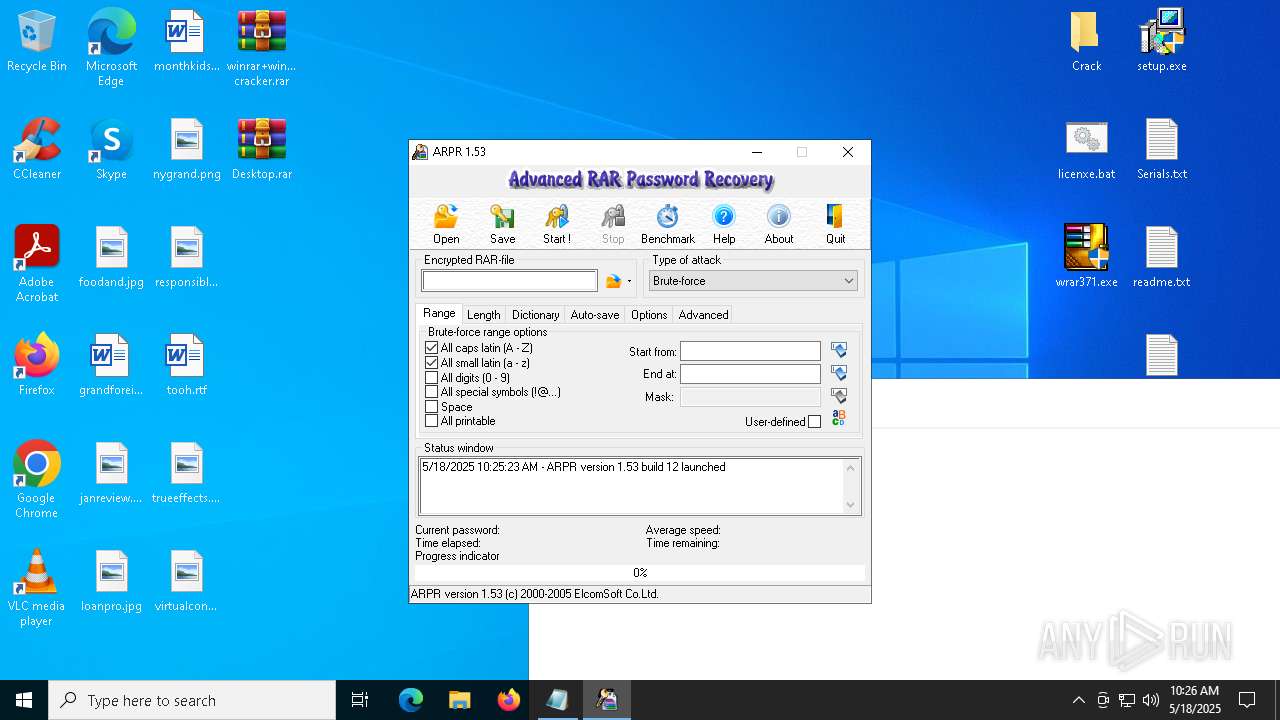
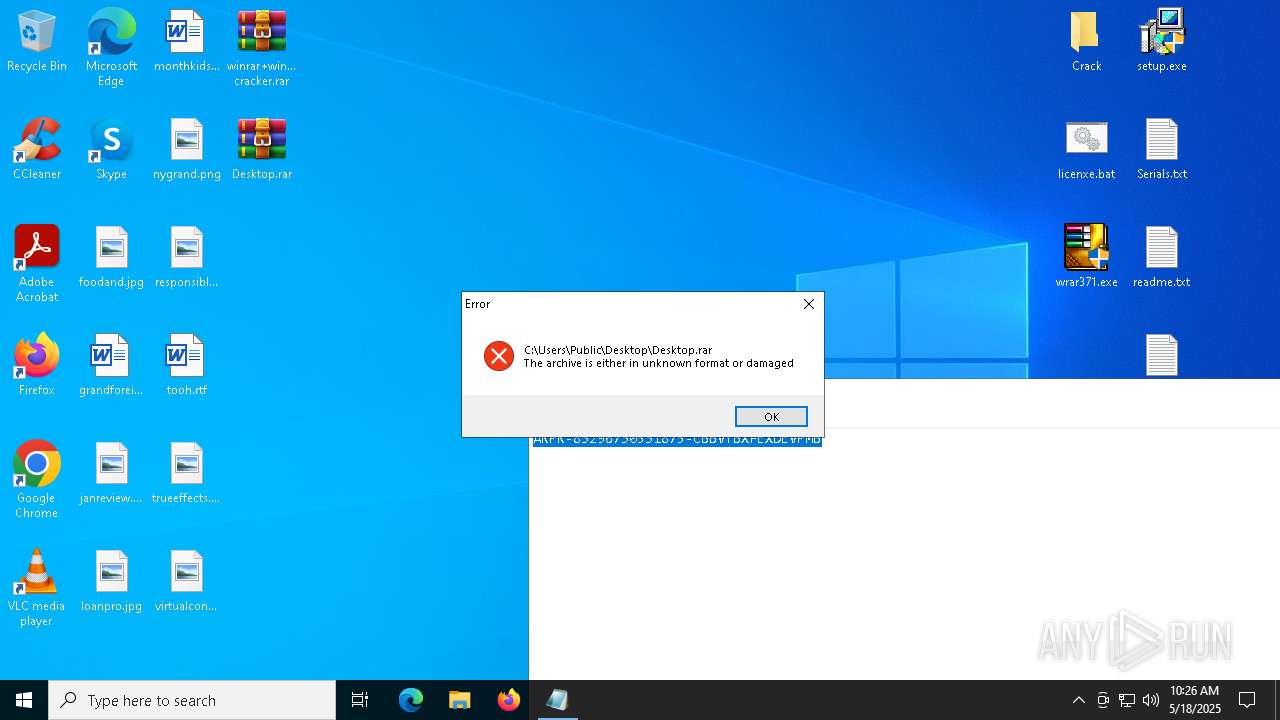
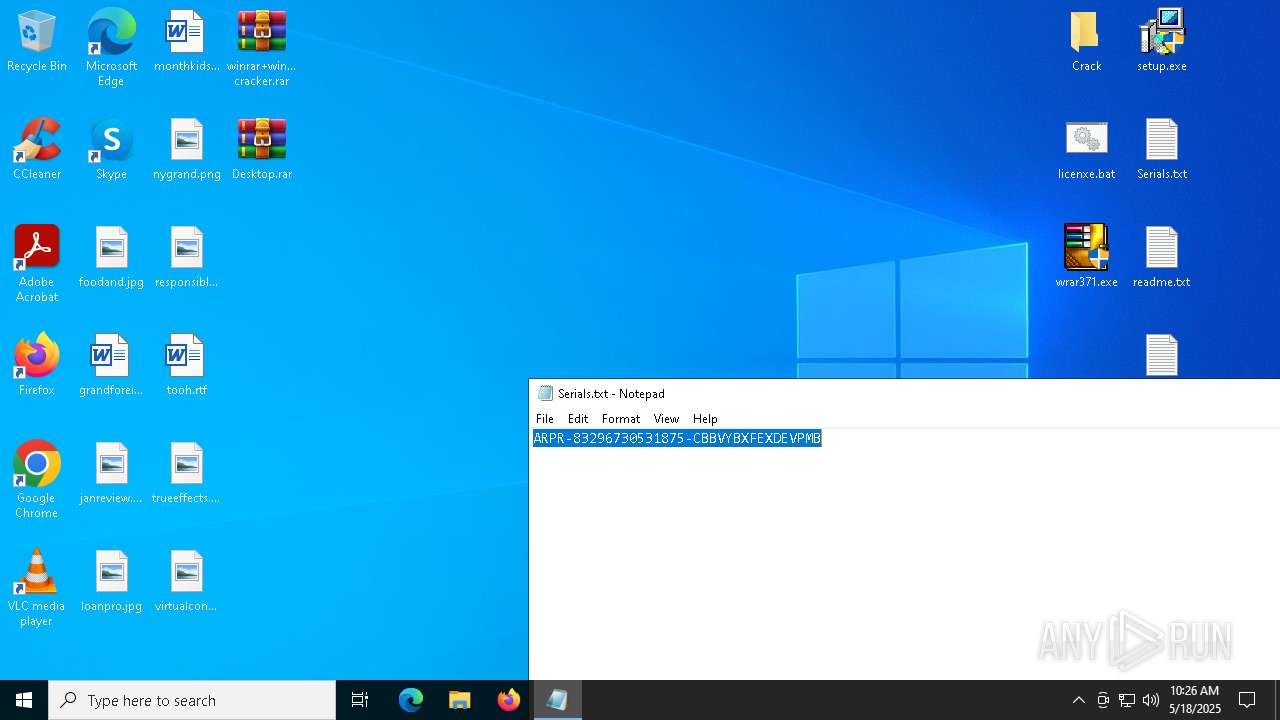
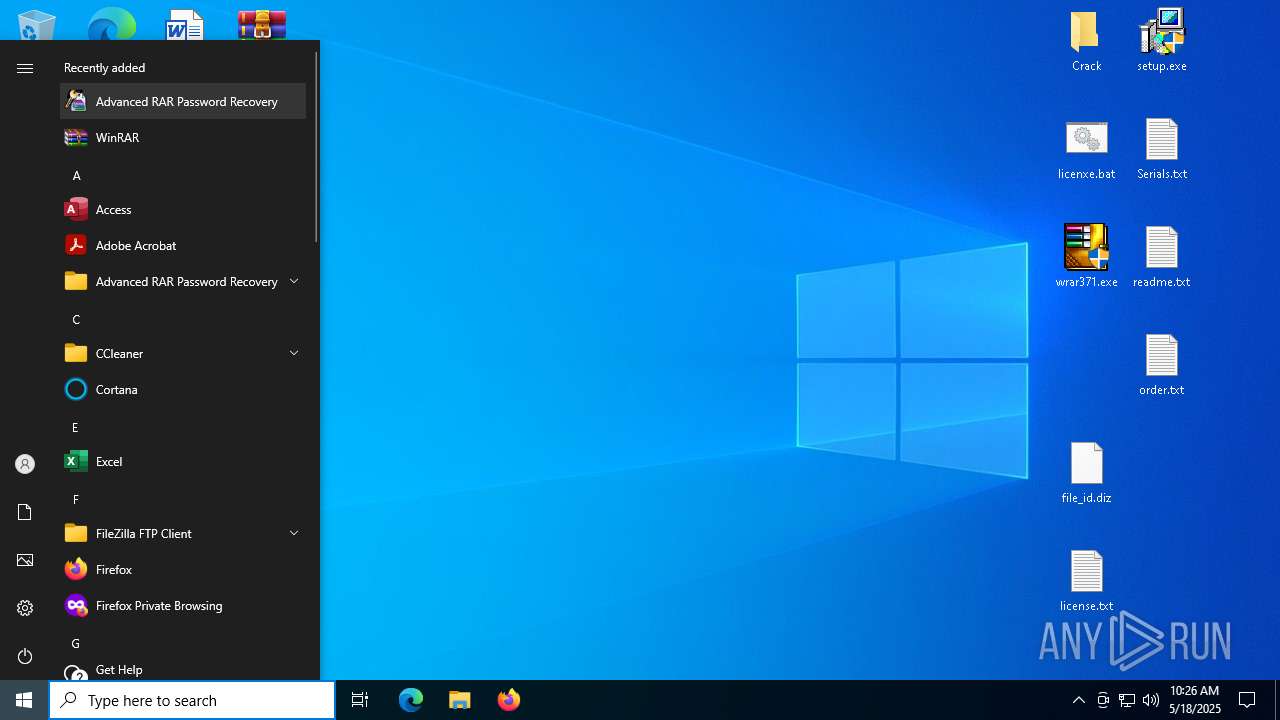
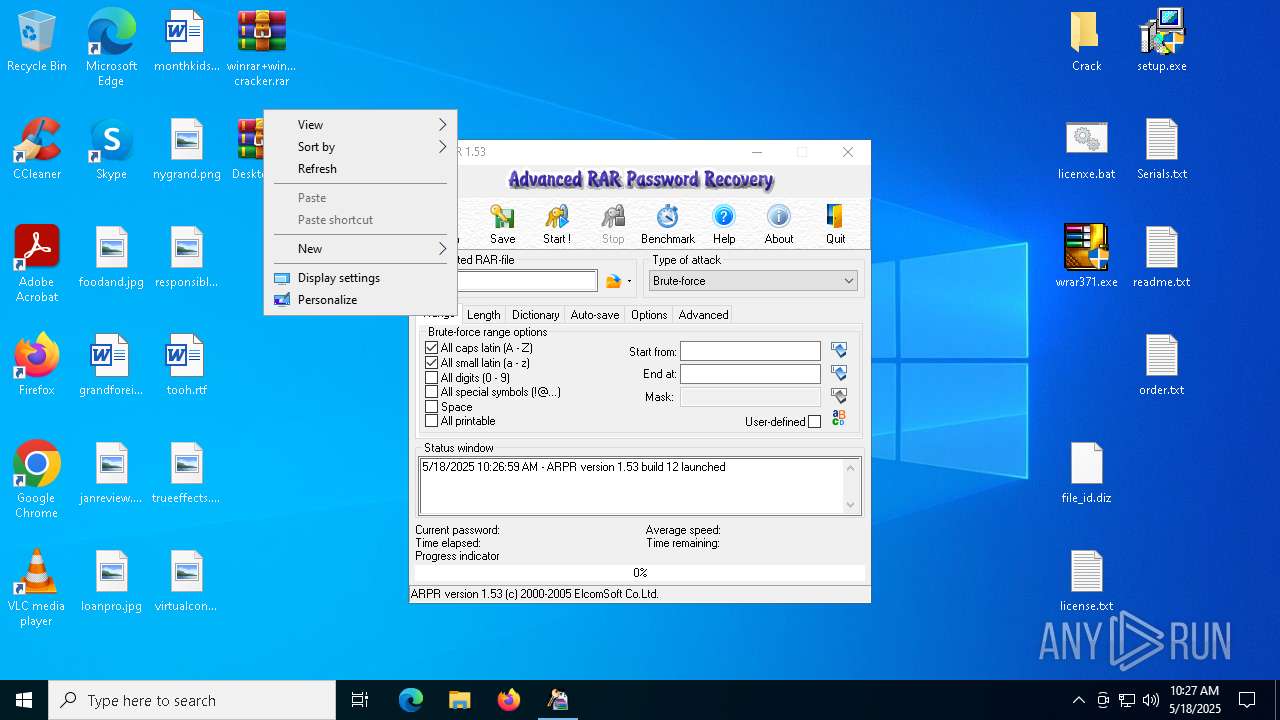
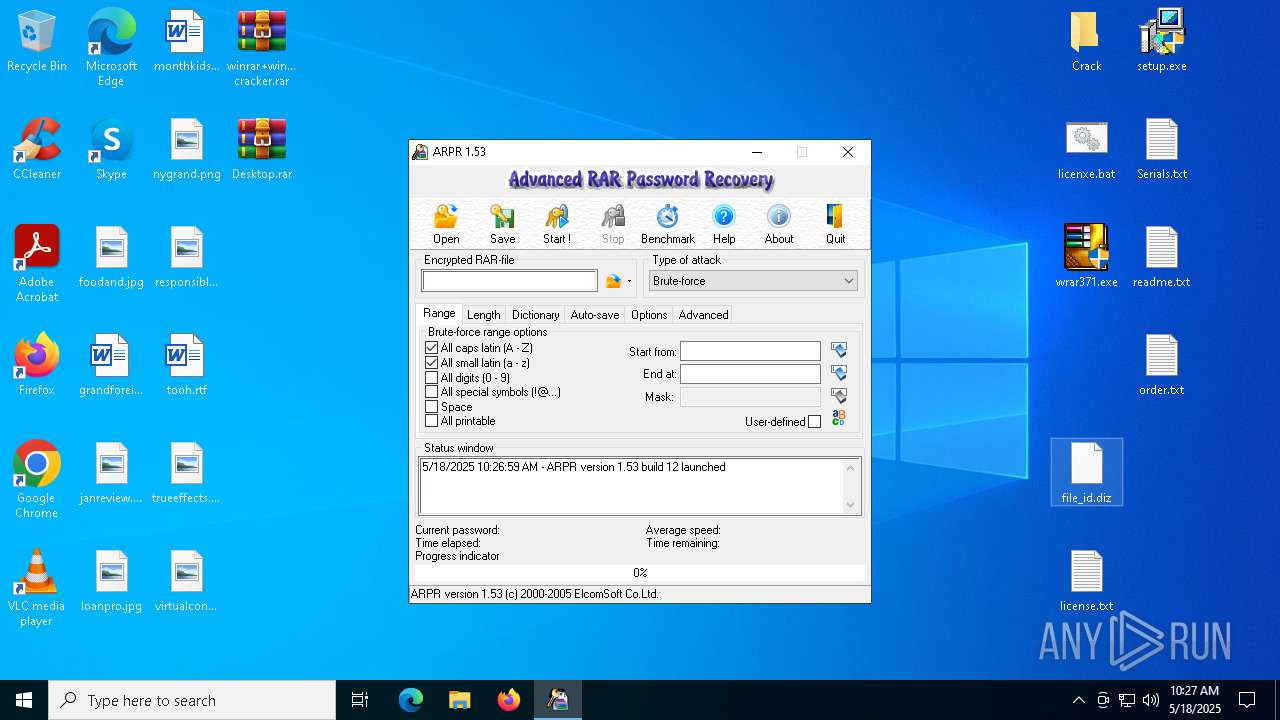
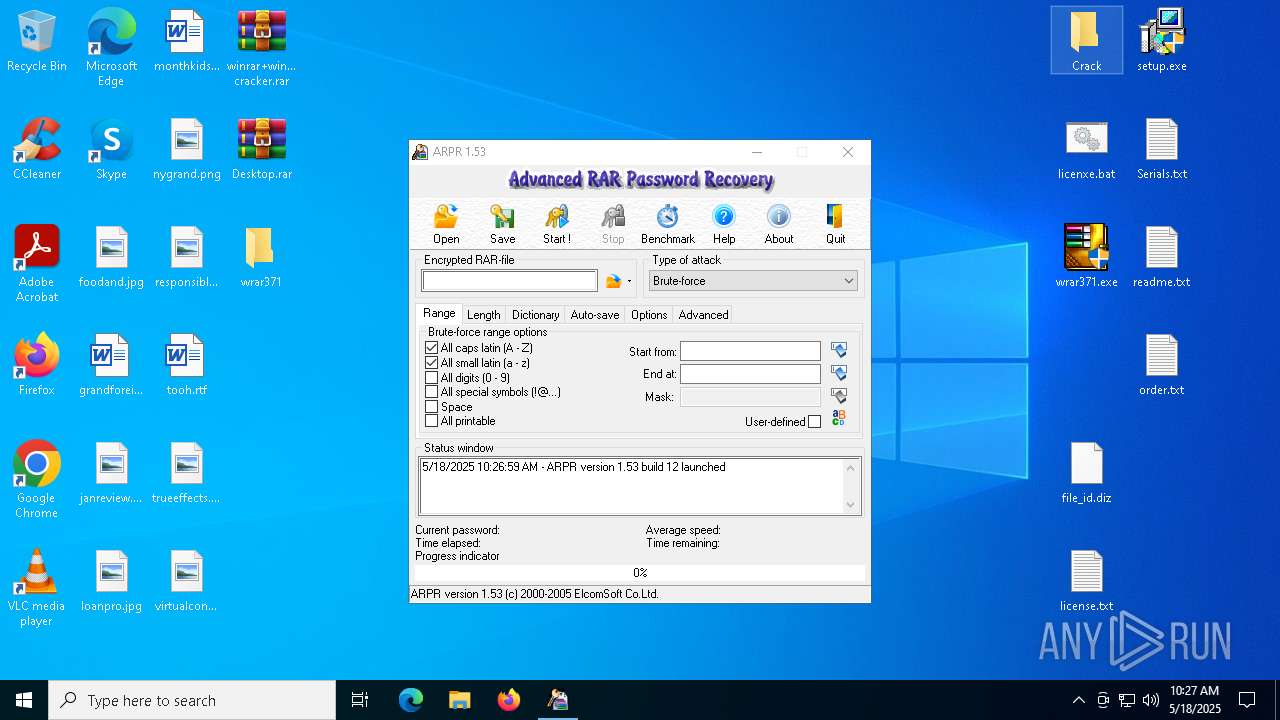
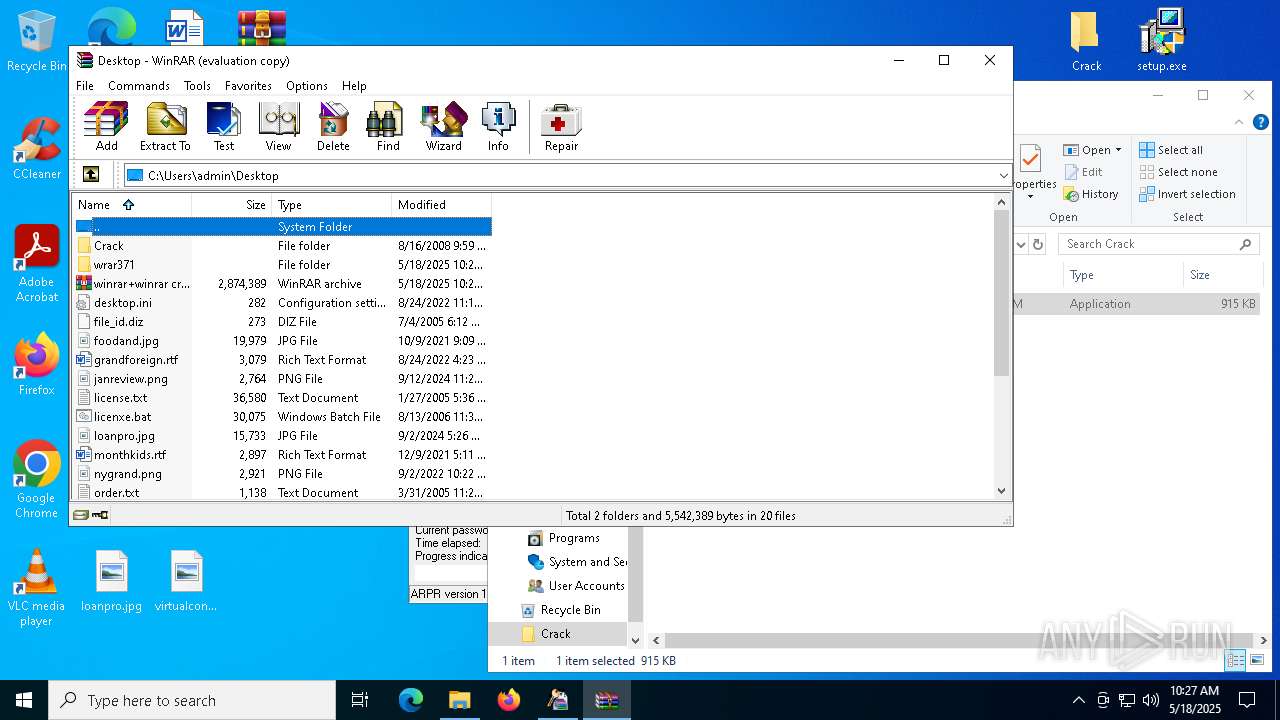
| File name: | winrar+winrar cracker.rar |
| Full analysis: | https://app.any.run/tasks/1c756c8c-2b5d-4ffe-9ec6-6efd951c78ac |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 10:22:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | A1CE1650E36CF91D95E6BB096DEF978C |
| SHA1: | 89C3B17DBFAFFEC1EFB112846F614361A3BD647A |
| SHA256: | 29C2E2BE0C53352F4897DD0C1F0FA663FD9958A4820896859C41FB79F69615DC |
| SSDEEP: | 98304:txbqABBKQFLqpehcfzvtjaZMu2rS7asTj9mp80xo7hFIrpddW6wf8+VJC7KXCBjq:UgLR |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2852)
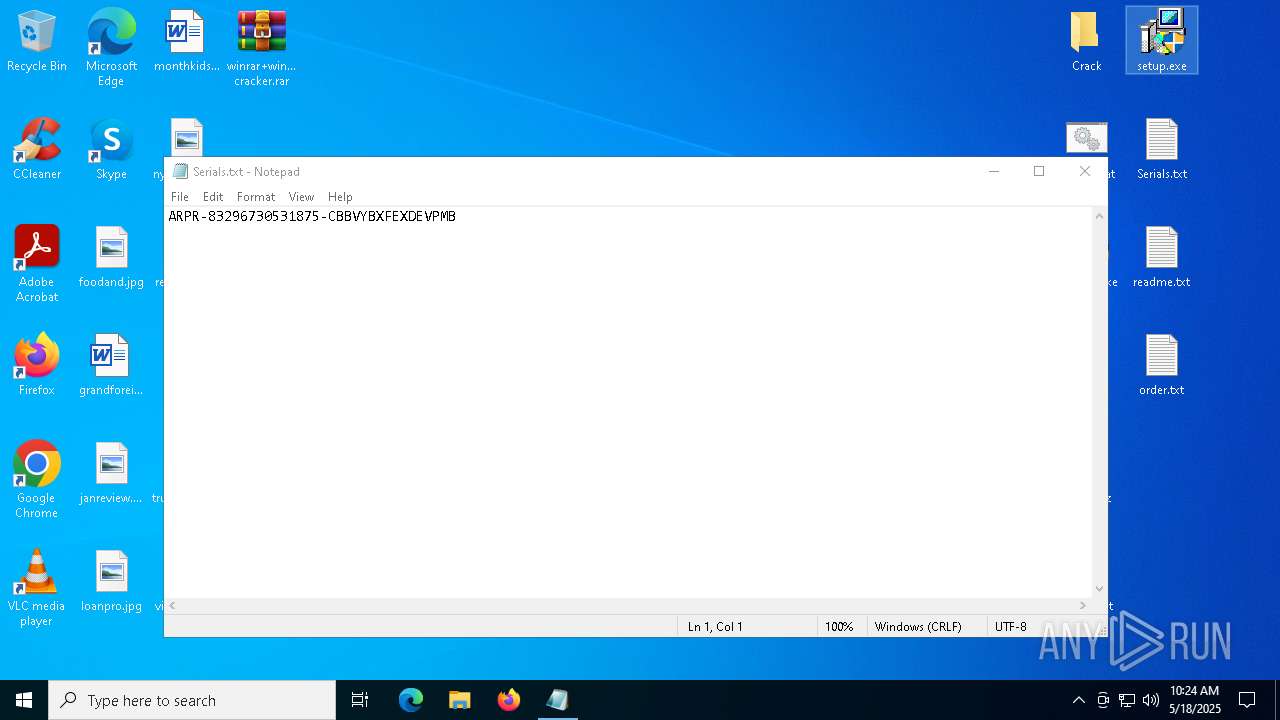
Executing a file with an untrusted certificate
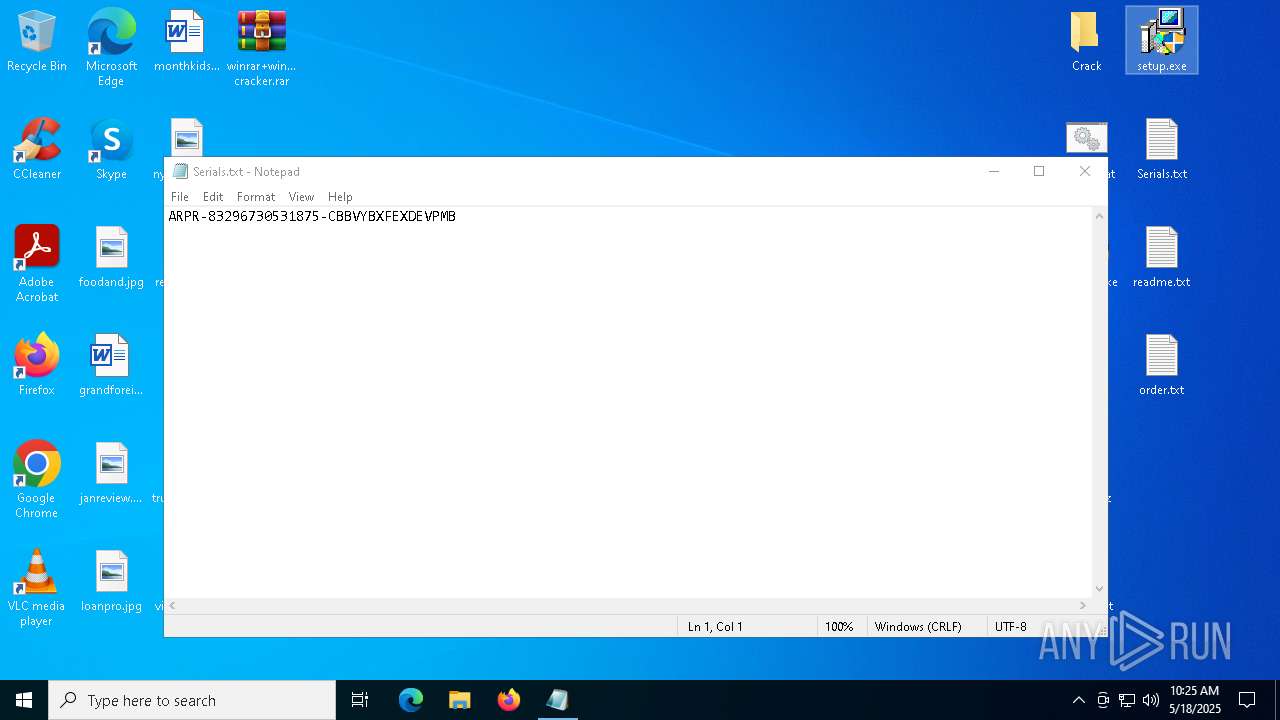
- setup.exe (PID: 1760)
- setup.exe (PID: 7856)
- setup.exe (PID: 7184)
- setup.exe (PID: 904)
SUSPICIOUS
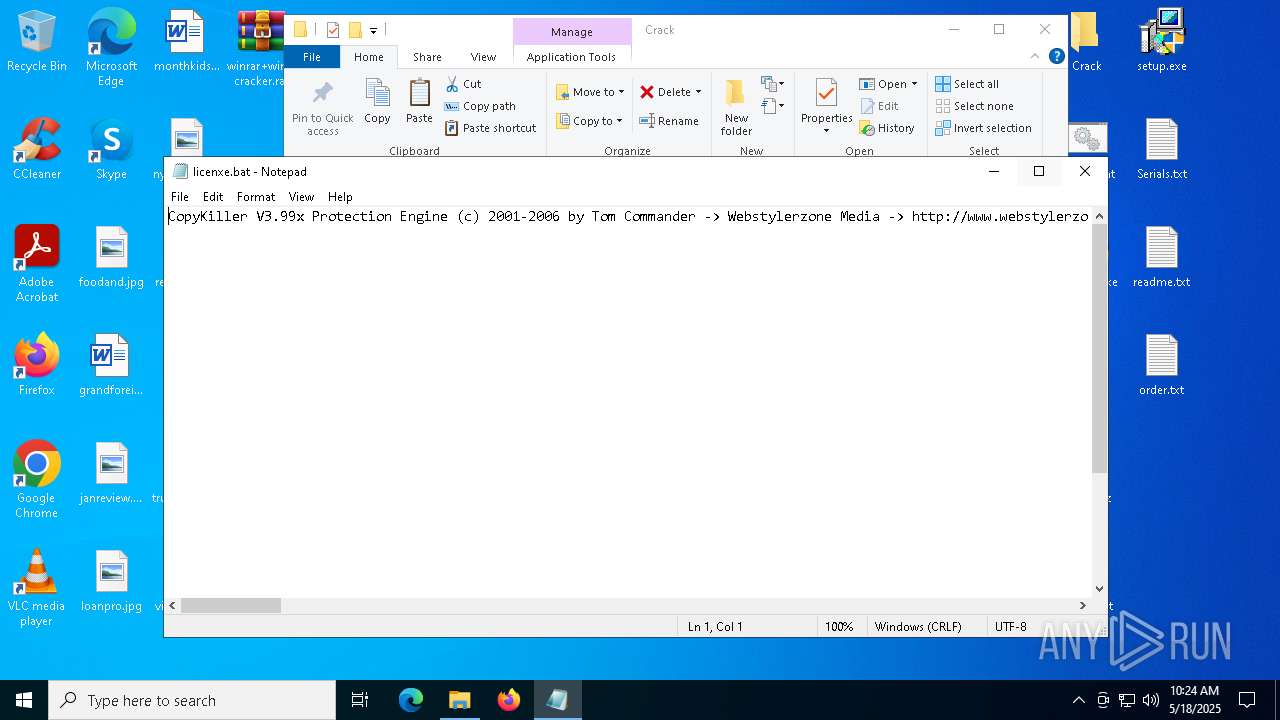
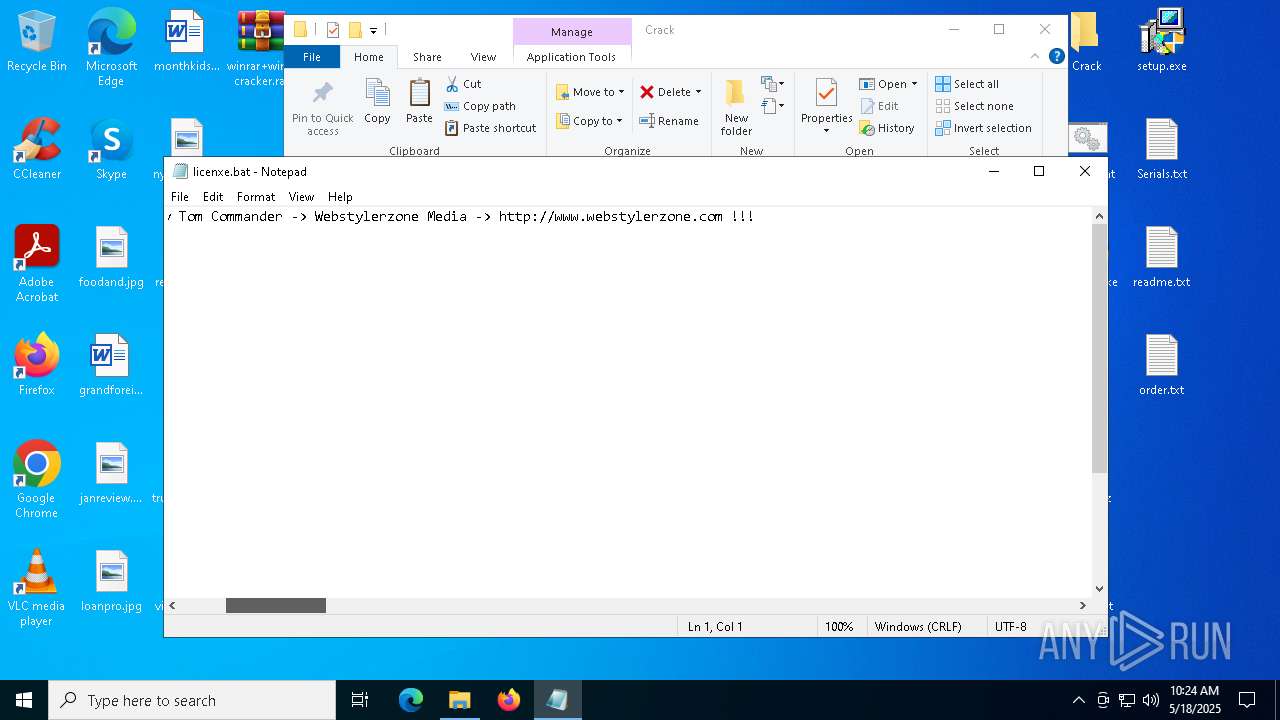
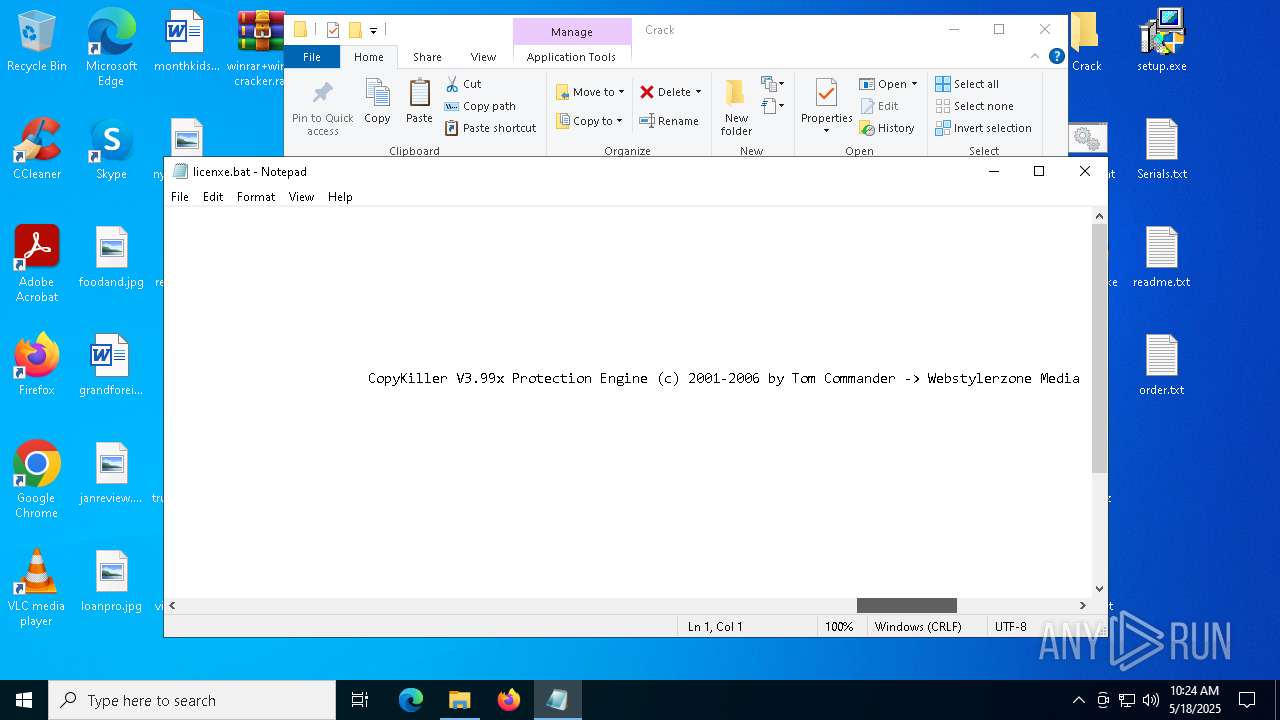
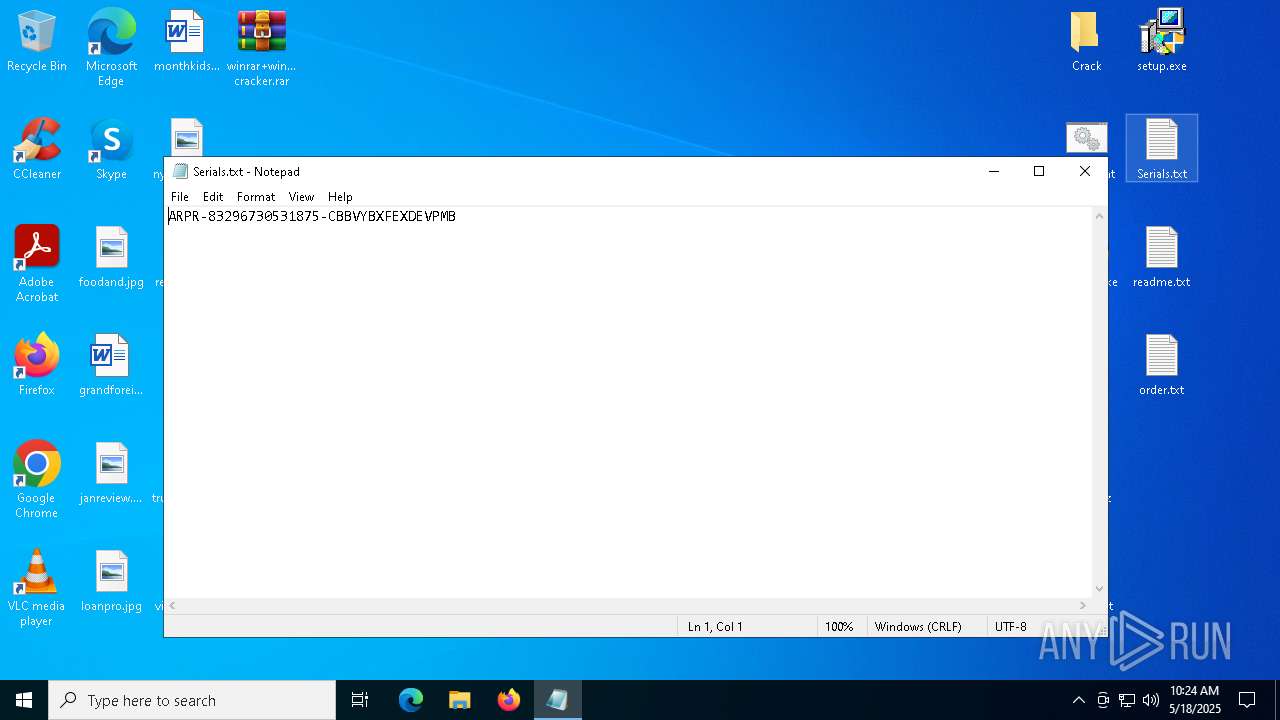
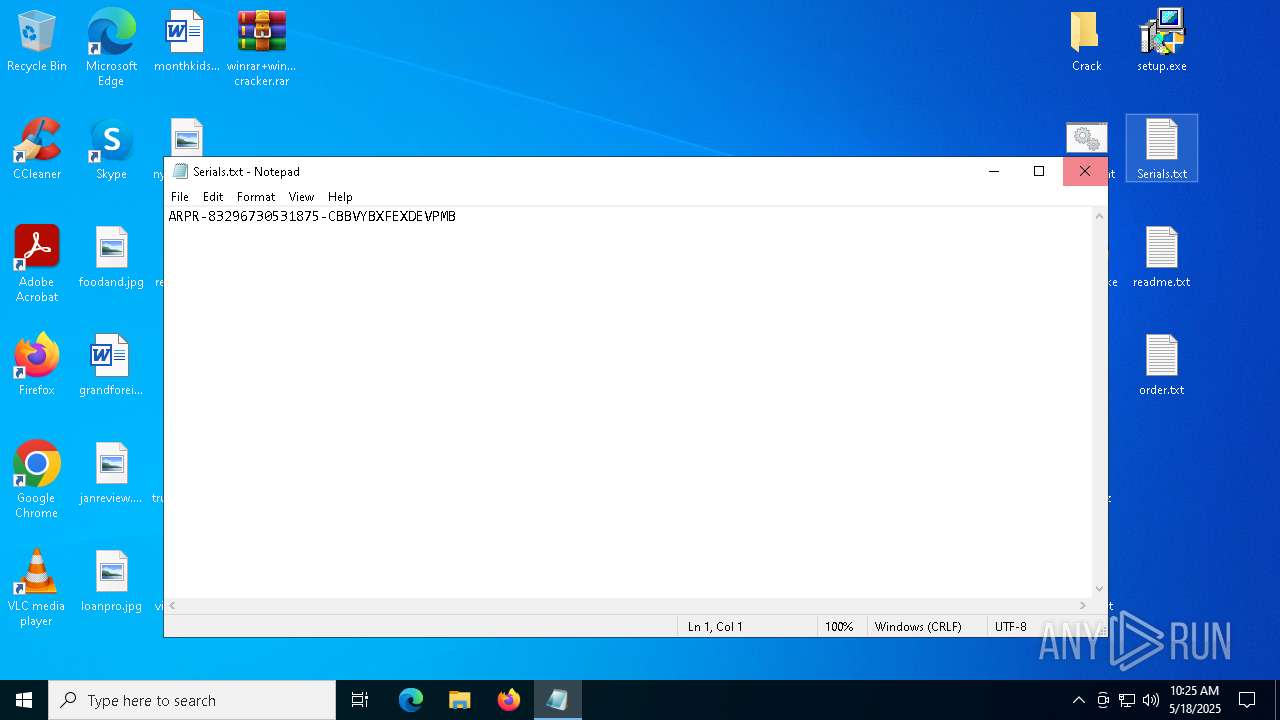
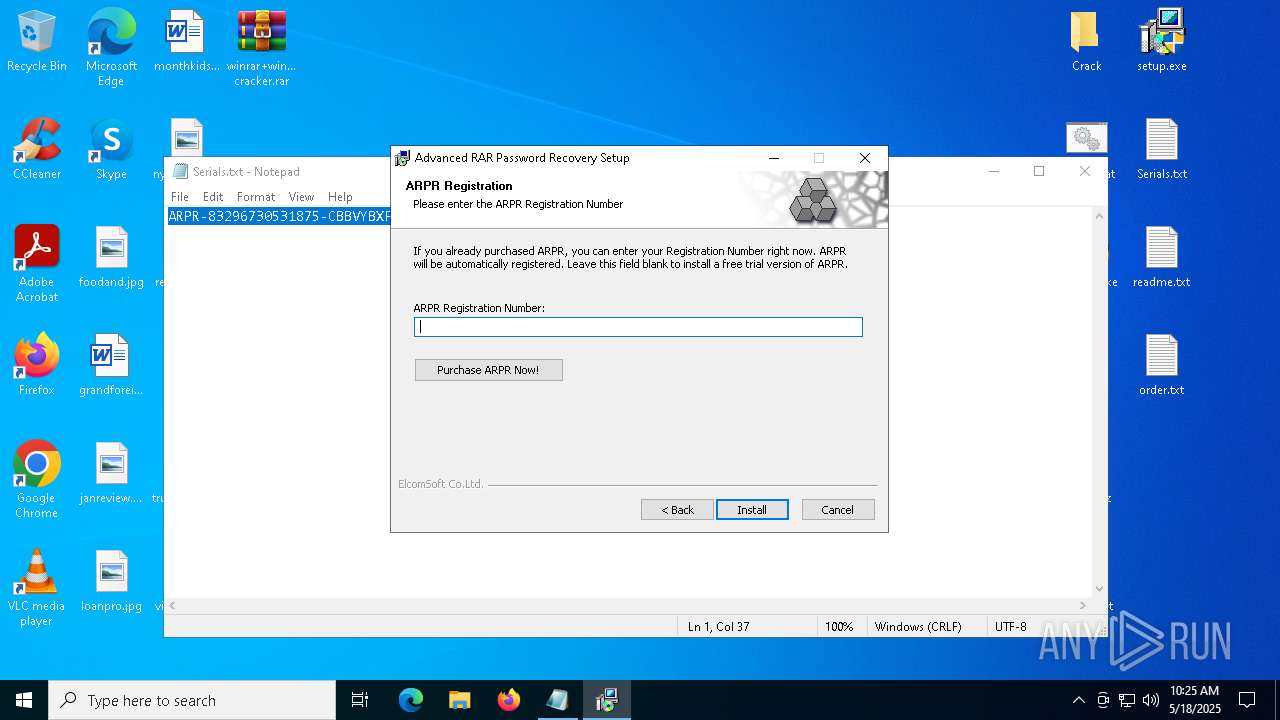
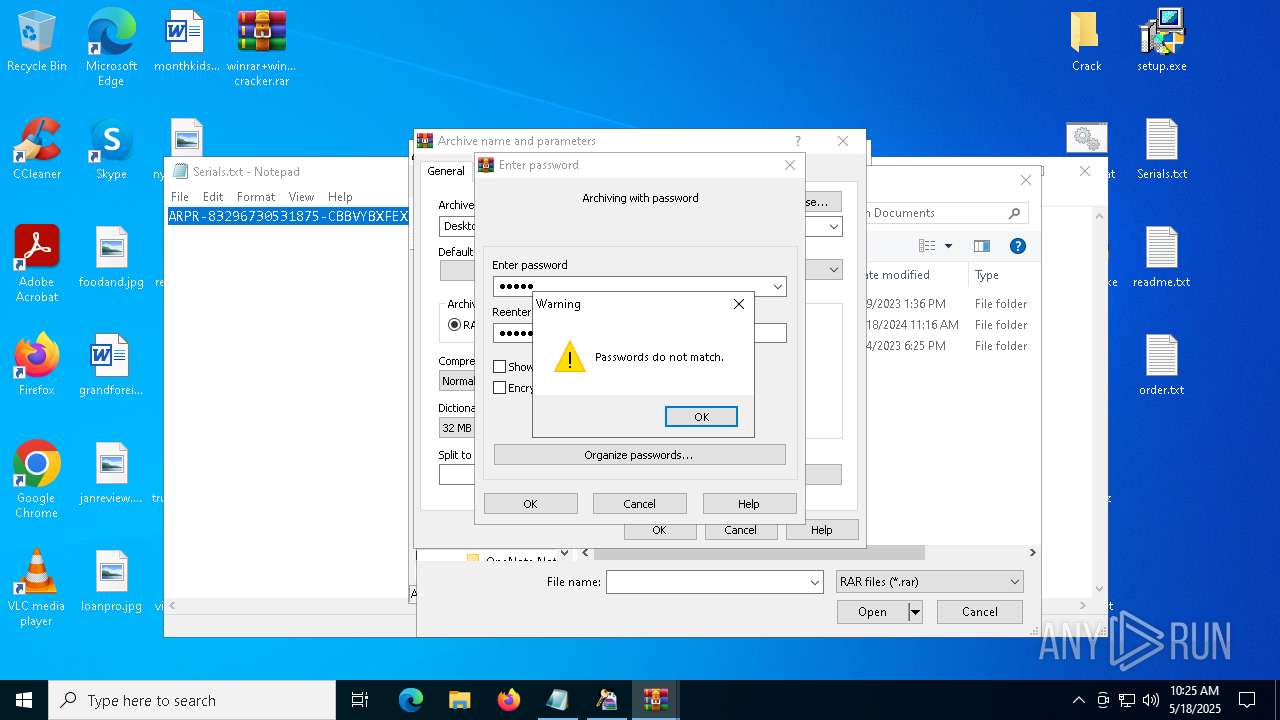
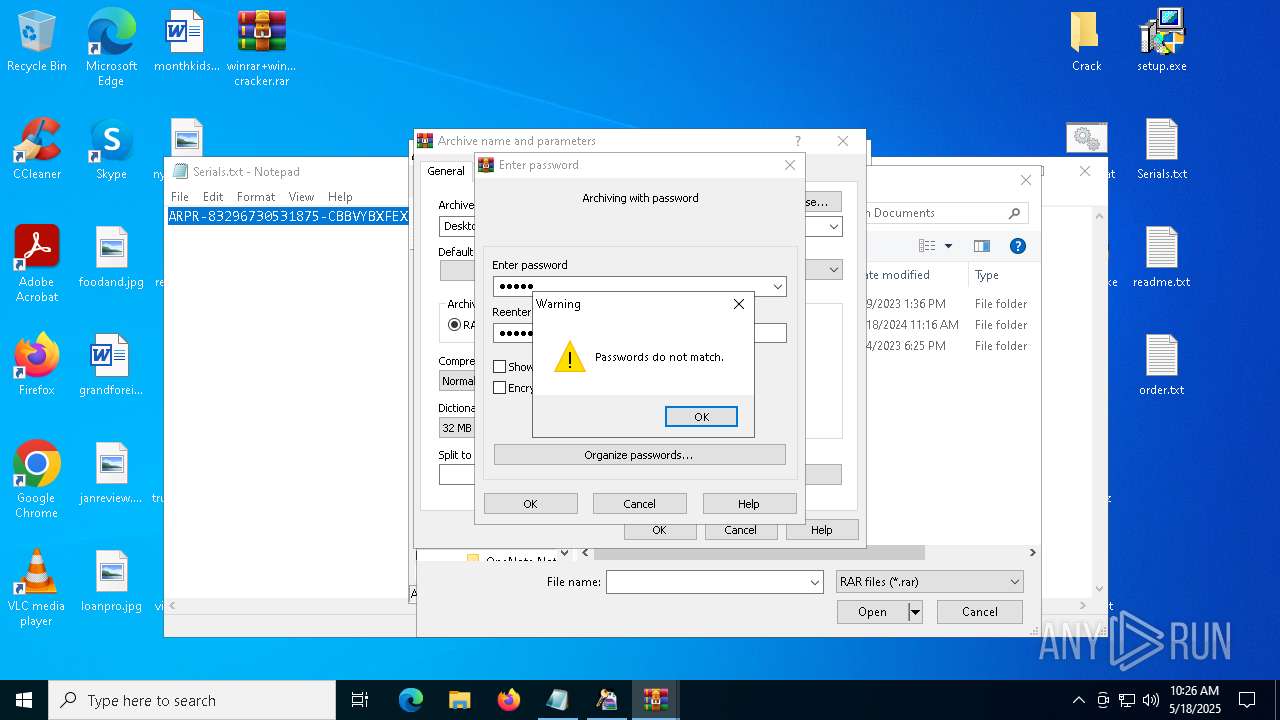
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2852)
Reads Microsoft Outlook installation path
- wrar371.exe (PID: 1072)
Reads Internet Explorer settings
- wrar371.exe (PID: 1072)
Reads security settings of Internet Explorer
- wrar371.exe (PID: 1072)
- Uninstall.exe (PID: 4724)
- WinRAR.exe (PID: 2852)
Executable content was dropped or overwritten
- wrar371.exe (PID: 1072)
- setup.exe (PID: 904)
- setup.exe (PID: 7184)
Drops 7-zip archiver for unpacking
- wrar371.exe (PID: 1072)
- WinRAR.exe (PID: 7552)
Creates a software uninstall entry
- Uninstall.exe (PID: 4724)
Creates/Modifies COM task schedule object
- Uninstall.exe (PID: 4724)
Application launched itself
- WinRAR.exe (PID: 4932)
Likely accesses (executes) a file from the Public directory
- WinRAR.exe (PID: 4932)
- WinRAR.exe (PID: 6072)
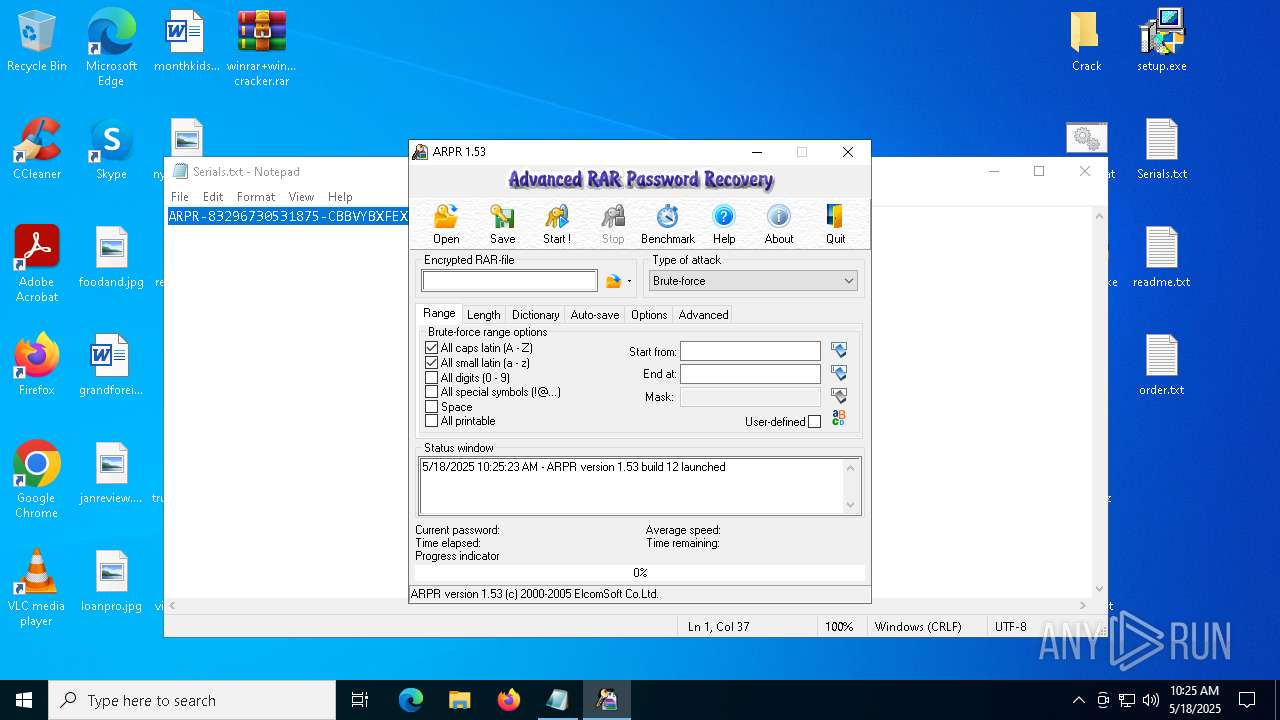
There is functionality for taking screenshot (YARA)
- WinRAR.exe (PID: 7208)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 2852)
Manual execution by a user
- notepad.exe (PID: 8028)
- wrar371.exe (PID: 1672)
- cmd.exe (PID: 8080)
- wrar371.exe (PID: 1072)
- notepad.exe (PID: 1012)
- WinRAR.exe (PID: 1272)
- cmd.exe (PID: 6676)
- notepad.exe (PID: 3396)
- setup.exe (PID: 904)
- setup.exe (PID: 7856)
- setup.exe (PID: 7184)
- WinRAR.exe (PID: 4932)
- WinRAR.exe (PID: 6072)
- WinRAR.exe (PID: 7552)
- ARPR.EXE (PID: 1276)
- setup.exe (PID: 1760)
- WinRAR.exe (PID: 7208)
Reads the computer name
- wrar371.exe (PID: 1072)
- Uninstall.exe (PID: 4724)
Reads security settings of Internet Explorer
- notepad.exe (PID: 8028)
- notepad.exe (PID: 7616)
- notepad.exe (PID: 7708)
Creates files in the program directory
- wrar371.exe (PID: 1072)
- Uninstall.exe (PID: 4724)
Checks proxy server information
- wrar371.exe (PID: 1072)
The sample compiled with english language support
- wrar371.exe (PID: 1072)
- WinRAR.exe (PID: 7552)
- WinRAR.exe (PID: 2852)
Checks supported languages
- wrar371.exe (PID: 1072)
- Uninstall.exe (PID: 4724)
Process checks computer location settings
- wrar371.exe (PID: 1072)
The sample compiled with russian language support
- wrar371.exe (PID: 1072)
- WinRAR.exe (PID: 7552)
Reads the software policy settings
- slui.exe (PID: 7244)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7552)
- WinRAR.exe (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 204 |
| UncompressedSize: | 175 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2004:11:12 20:43:34 |
| PackingMethod: | Normal |
| ArchivedFileName: | winrar+winrar cracker\hello.txt |
Total processes
176
Monitored processes
31
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1012 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\licenxe.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\Desktop\wrar371.exe" | C:\Users\admin\Desktop\wrar371.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\WinRAR\WinRAR.exe" | C:\Program Files (x86)\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
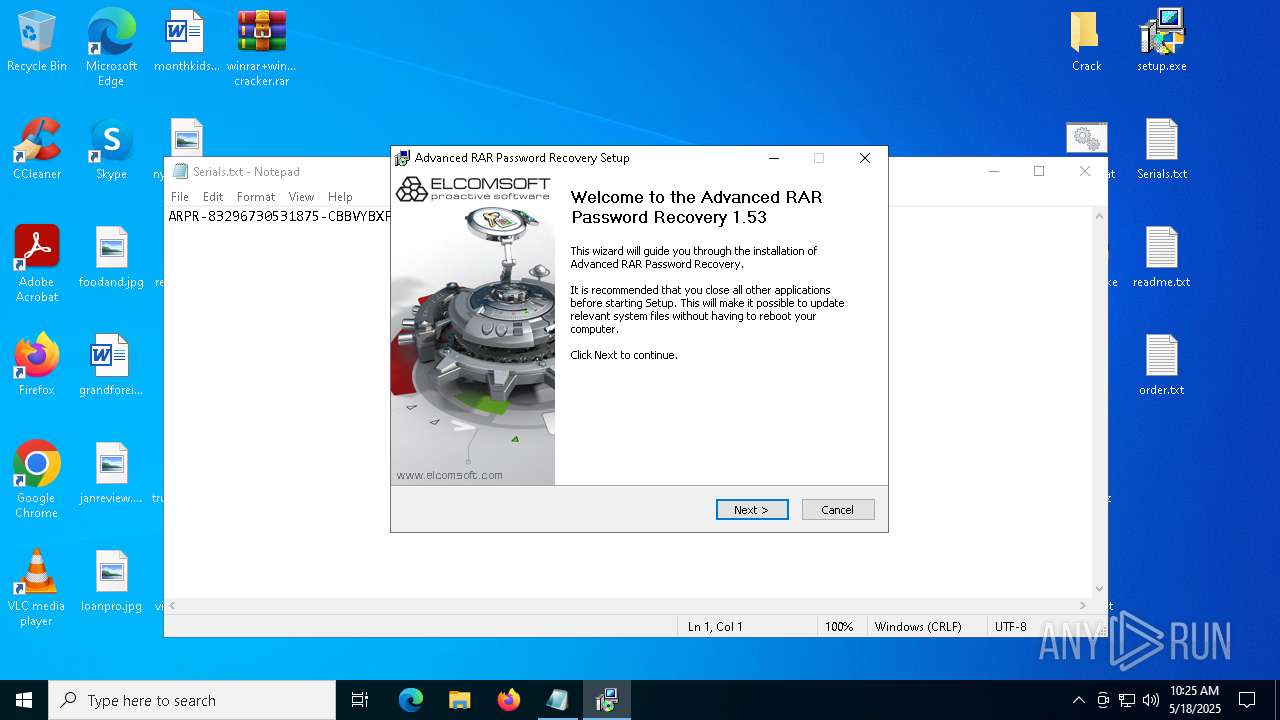
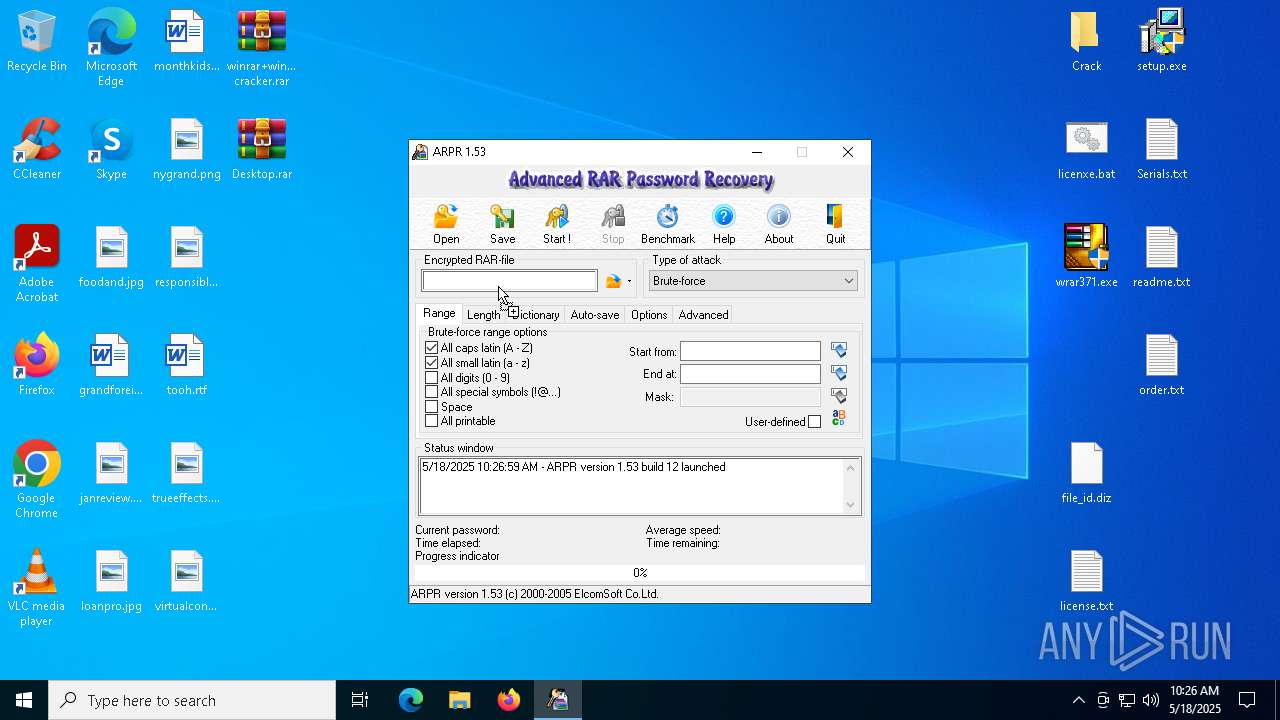
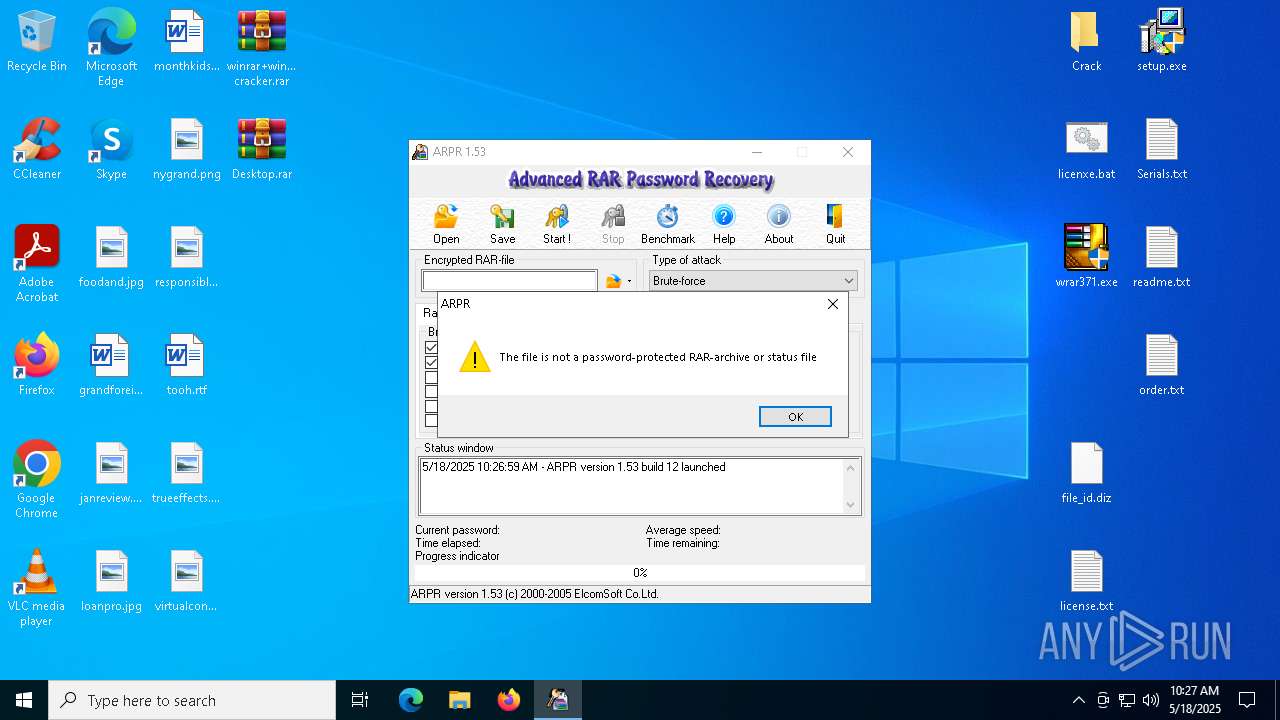
| 1276 | "C:\Program Files (x86)\ElcomSoft\ARPR\ARPR.EXE" | C:\Program Files (x86)\ElcomSoft\ARPR\ARPR.EXE | — | explorer.exe | |||||||||||
User: admin Company: ElcomSoft Co. Ltd. Integrity Level: MEDIUM Description: Advanced RAR Password Recovery Version: 1.53.48.12 Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | "C:\Users\admin\Desktop\wrar371.exe" | C:\Users\admin\Desktop\wrar371.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1760 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\winrar+winrar cracker.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3396 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Serials.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 138
Read events
22 704
Write events
4 366
Delete events
68
Modification events
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\winrar+winrar cracker.rar | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
66
Suspicious files
25
Text files
74
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2852.8713\winrar+winrar cracker\winrar+winrar cracker\Winrar 3.71\Crack\WinRAR.exe | executable | |
MD5:72A47494EEB5936657BED3B036391209 | SHA256:AC6FEABC7647DDE9659ACC5CAD839ABA8EDBF739D46018D67FFAFF028DFA8F8D | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2852.8713\winrar+winrar cracker\winrar+winrar cracker\Winrar 3.71\licenxe.bat | text | |
MD5:EF825C31CC2E5A21EEE32C5A2CF6E612 | SHA256:AD123508F54F77C2E3AE296B8C28E38F63146AABAE7136F2A455C007E1CC8E01 | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2852.9524\winrar+winrar cracker\winrar+winrar cracker\Advanced RAR Password Recovery 1.53\readme.txt | text | |
MD5:605566472DE3D712AAE6A93F11C42238 | SHA256:F6477FD3D02667CB186DBC92A93433C47A907F92B3EA0529D163B77059FEC373 | |||
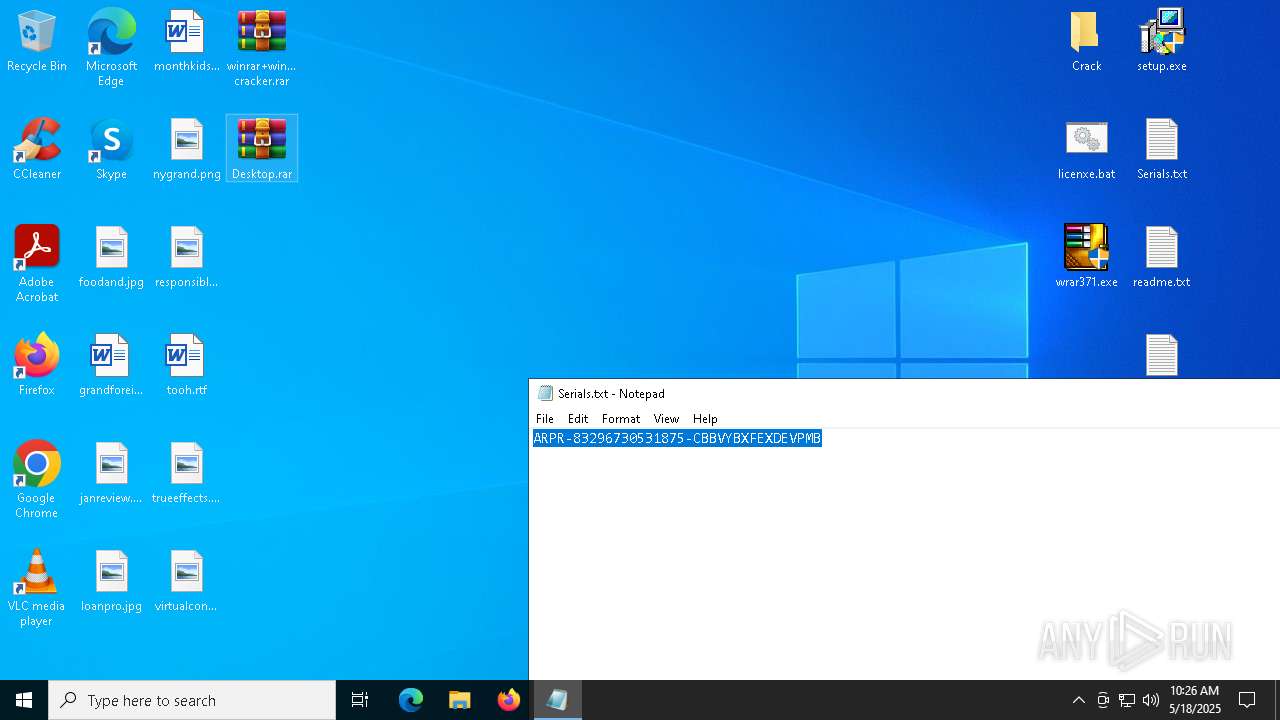
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2852.9524\winrar+winrar cracker\winrar+winrar cracker\Advanced RAR Password Recovery 1.53\Serials.txt | text | |
MD5:0528292010F053F929B7ACDCC3598296 | SHA256:4BC317CCA4106D50381B9964C2F7E4ECB0C7AACB4F8AF841D155F737379767A0 | |||
| 1072 | wrar371.exe | C:\Program Files (x86)\WinRAR\File_Id.diz | text | |
MD5:0698EE8172A5683DA1EE3B845F5D3A7D | SHA256:146EA006B33F2AE4EFC9168BBF4319B213B480BB4E72794BE09B3CCBD8399B9A | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2852.9524\winrar+winrar cracker\winrar+winrar cracker\Advanced RAR Password Recovery 1.53\file_id.diz | text | |
MD5:7577A61465B00ED7FD6FEC1D5E1339D7 | SHA256:8223B9C7F3CC839B82BE8F1C5B895695CF7B6A0AE8DDE286A48828AF8404EED3 | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2852.9524\winrar+winrar cracker\winrar+winrar cracker\Advanced RAR Password Recovery 1.53\setup.exe | executable | |
MD5:B213DBFC88FED5214CB1BF21B3AB6B8C | SHA256:AA4D68575DA1A9C34B2B039DC76DC96F3D5F8810D3D66D7662DEAECF5ECCA139 | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2852.6850\hello.txt | text | |
MD5:313C75B7BEBAA373F25CCDF624F69EAA | SHA256:4967DB016052F4AA0B111380ED50ED67EED9031B504D26C953FB0CC5E8939BA4 | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2852.9524\winrar+winrar cracker\winrar+winrar cracker\Advanced RAR Password Recovery 1.53\order.txt | text | |
MD5:855731747DBC46B882202FFBEAF4D67F | SHA256:3B3EBB04ED293E3F47DC050EB4F436B2E6DCDFCF50B6083C85A070BACD2A66B9 | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2852.8004\hello.txt | text | |
MD5:313C75B7BEBAA373F25CCDF624F69EAA | SHA256:4967DB016052F4AA0B111380ED50ED67EED9031B504D26C953FB0CC5E8939BA4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7844 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7844 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7844 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |