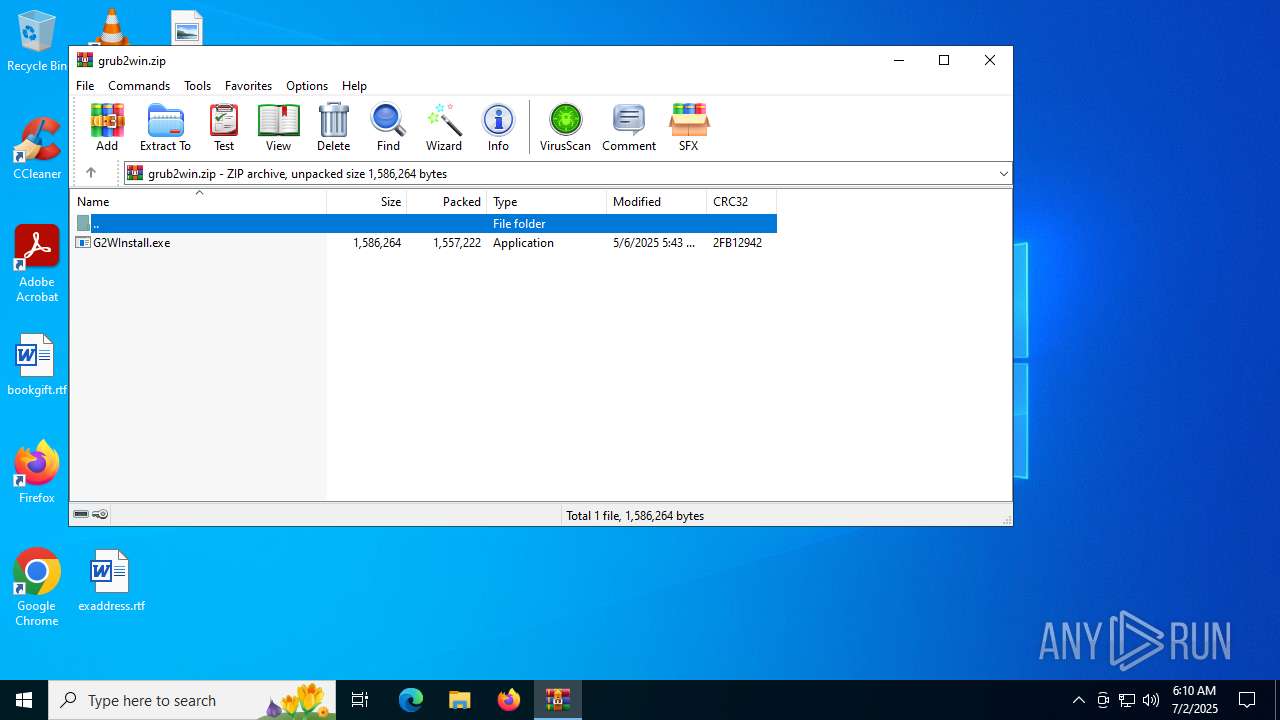
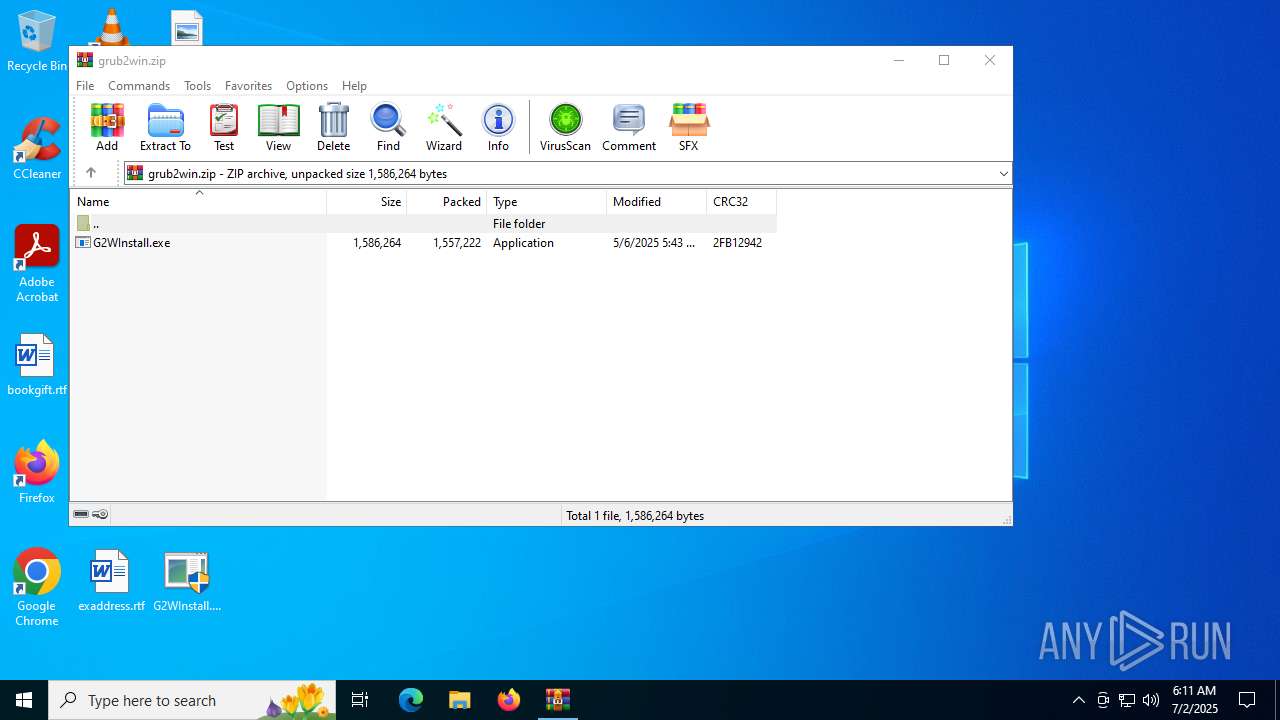
| File name: | grub2win.zip |
| Full analysis: | https://app.any.run/tasks/698586ca-41fa-4a65-8cb1-6cf14e8052a6 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 06:10:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 10EDD6EFC03A0D1F6EDDFE63B7A02919 |
| SHA1: | 33648C491F2FDDE3DB4D13B3A1D8B7CFBDB49574 |
| SHA256: | 29A9F0D6248D62D1EC6BB539F78FD836AE020FD664CC3666214F872669218F0D |
| SSDEEP: | 49152:4VxcnLXU+icC6mzAiKPN/HJWbCBS8gm2lFPrpe4KiX1dQi9e7QYZJJMPn4t6ILsO:2xUbFicC/gpWD8gPrs4JUKe7nZJaw2Ro |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3908)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- G2WInstall.exe (PID: 5920)
Reads the BIOS version
- G2WInstall.exe (PID: 5920)
Reads security settings of Internet Explorer
- G2WInstall.exe (PID: 5920)
Starts CMD.EXE for commands execution
- G2WInstall.exe (PID: 5920)
- cmd.exe (PID: 1660)
Executing commands from a ".bat" file
- G2WInstall.exe (PID: 5920)
Potential Corporate Privacy Violation
- G2WInstall.exe (PID: 5920)
There is functionality for taking screenshot (YARA)
- G2WInstall.exe (PID: 5920)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1660)
Application launched itself
- cmd.exe (PID: 1660)
Checks for external IP
- G2WInstall.exe (PID: 5920)
- svchost.exe (PID: 2200)
INFO
Manual execution by a user
- G2WInstall.exe (PID: 3752)
- G2WInstall.exe (PID: 5920)
Reads mouse settings
- G2WInstall.exe (PID: 5920)
Reads the computer name
- G2WInstall.exe (PID: 5920)
Reads CPU info
- G2WInstall.exe (PID: 5920)
Checks supported languages
- G2WInstall.exe (PID: 5920)
Create files in a temporary directory
- G2WInstall.exe (PID: 5920)
Checks proxy server information
- G2WInstall.exe (PID: 5920)
- slui.exe (PID: 6704)
Creates files or folders in the user directory
- G2WInstall.exe (PID: 5920)
Creates files in the program directory
- G2WInstall.exe (PID: 5920)
- cmd.exe (PID: 3196)
- cmd.exe (PID: 4572)
Process checks computer location settings
- G2WInstall.exe (PID: 5920)
The process uses AutoIt
- G2WInstall.exe (PID: 5920)
UPX packer has been detected
- G2WInstall.exe (PID: 5920)
Reads the software policy settings
- slui.exe (PID: 6704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:06 13:43:48 |
| ZipCRC: | 0x2fb12942 |
| ZipCompressedSize: | 1557222 |
| ZipUncompressedSize: | 1586264 |
| ZipFileName: | G2WInstall.exe |
Total processes
151
Monitored processes
19
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 756 | "C:\WINDOWS\system32\cmd.exe" /c C:\windows\sysnative\mountvol.exe M: /D | C:\Windows\SysWOW64\cmd.exe | — | G2WInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | C:\windows\sysnative\mountvol.exe M: /S | C:\Windows\System32\mountvol.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Mount Volume Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | C:\WINDOWS\system32\cmd.exe /c C:\ProgramData\Grub2Win\Cleanup.Grub2Win.25070206103939.directory.DownLoadEndIt.bat | C:\Windows\SysWOW64\cmd.exe | — | G2WInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | ping -n 3 127.0.0.1 | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | C:\windows\sysnative\mountvol.exe | C:\Windows\System32\mountvol.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Mount Volume Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2664 | C:\windows\sysnative\mountvol.exe M: /D | C:\Windows\System32\mountvol.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Mount Volume Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3196 | "C:\WINDOWS\system32\cmd.exe" /c C:\windows\sysnative\mountvol.exe > C:\ProgramData\Grub2Win\G2WInstall.exe.25070206103939\commands\mountvol.getletter.output.txt | C:\Windows\SysWOW64\cmd.exe | — | G2WInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3752 | "C:\Users\admin\Desktop\G2WInstall.exe" | C:\Users\admin\Desktop\G2WInstall.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
7 266
Read events
7 253
Write events
13
Delete events
0
Modification events
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\grub2win.zip | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3908) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5920 | G2WInstall.exe | C:\ProgramData\Grub2Win\G2WInstall.exe.25070206103939\HTMLCode.Grub2Win.G2WInstall.exe.txt | html | |
MD5:A1D5659D57630065D4FB4F44B9657CB5 | SHA256:EC192CF68DDA0B1C1F71C6930FE5207476466D6E73142B5C38D47AA0220F3747 | |||
| 5920 | G2WInstall.exe | C:\ProgramData\Grub2Win\G2WInstall.exe.25070206103939\inet.work.internet.txt | text | |
MD5:DCF2AB2B9521471324E7CA24A584F304 | SHA256:DCC35082423039DB16C0865A282FA71359A8655E9F87509734C242590DD6300B | |||
| 5920 | G2WInstall.exe | C:\ProgramData\Grub2Win\Cleanup.Grub2Win.25070206103939.bat | text | |
MD5:833B0FE370C983F9A182E7F5C1FC3B3A | SHA256:D3231D70B113BDDC7C828E75A5E18B77F9B0CA037FE1E4A495E063A749A4AD5D | |||
| 3196 | cmd.exe | C:\ProgramData\Grub2Win\G2WInstall.exe.25070206103939\commands\mountvol.getletter.output.txt | text | |
MD5:932DCFC0F143E83B05D4375CE4BBD0B2 | SHA256:E58BB324A2FDD0F57BE5ECC399B95EB86979ADA15E880AE36EE5C14D46DE0E7C | |||
| 5920 | G2WInstall.exe | C:\ProgramData\Grub2Win\Cleanup.Grub2Win.25070206103939.directory.DownLoadEndIt.bat | text | |
MD5:46637701620B961390ACBEF76AFDE950 | SHA256:FBEBC729202673F1DD3B7DAE4ADC2662DAA0237FBF730774A740838FC7F47123 | |||
| 5920 | G2WInstall.exe | C:\Users\admin\AppData\Local\Temp\aut6CD3.tmp | binary | |
MD5:90EBBB9AFD266E72AC54D823E1F7313A | SHA256:51C9DFCA0EA342D7A1253028028D9CD99163B7CF297B09E9410A94CD7A60D875 | |||
| 5920 | G2WInstall.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\line[1].txt | text | |
MD5:DCF2AB2B9521471324E7CA24A584F304 | SHA256:DCC35082423039DB16C0865A282FA71359A8655E9F87509734C242590DD6300B | |||
| 5920 | G2WInstall.exe | C:\Users\admin\AppData\Local\Temp\aut6CE4.tmp | binary | |
MD5:DCD03C1CE93D7DC4213A1E31A0D596A2 | SHA256:CC3354066B5BBBC58F737A14E3DE43014D2818AB9A3810955C94BF75DF1AC363 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
23
DNS requests
9
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3720 | RUXIMICS.exe | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3720 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5920 | G2WInstall.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=status,message,country,countryCode,region,regionName,city,timezone,offset,query | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3720 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.16.241.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.241.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3720 | RUXIMICS.exe | 2.16.241.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ip-api.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
5920 | G2WInstall.exe | Potential Corporate Privacy Violation | ET INFO Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
5920 | G2WInstall.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |