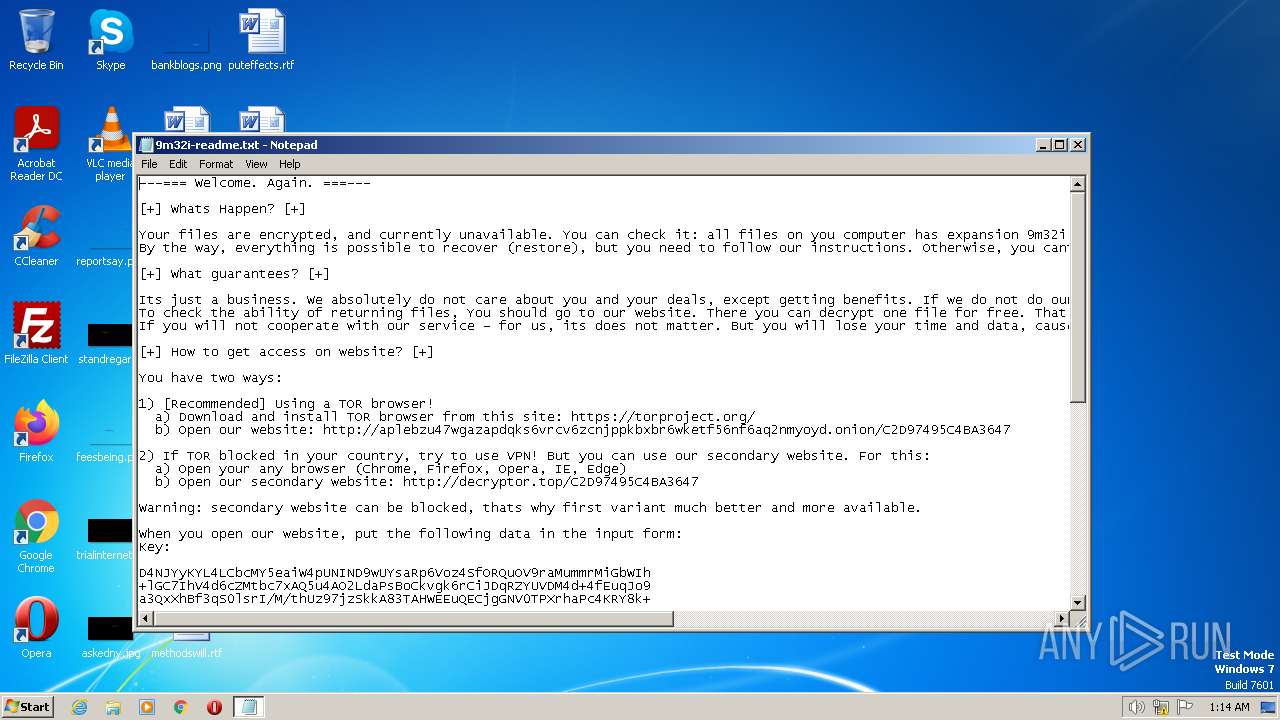
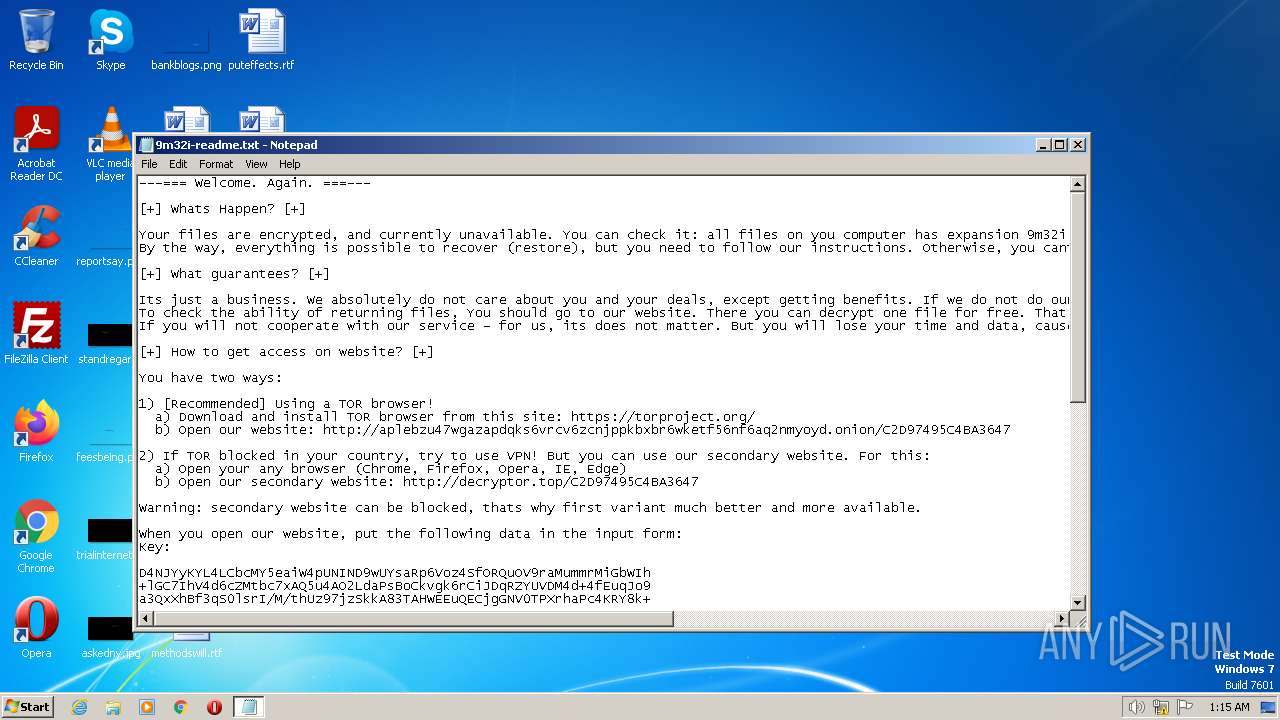
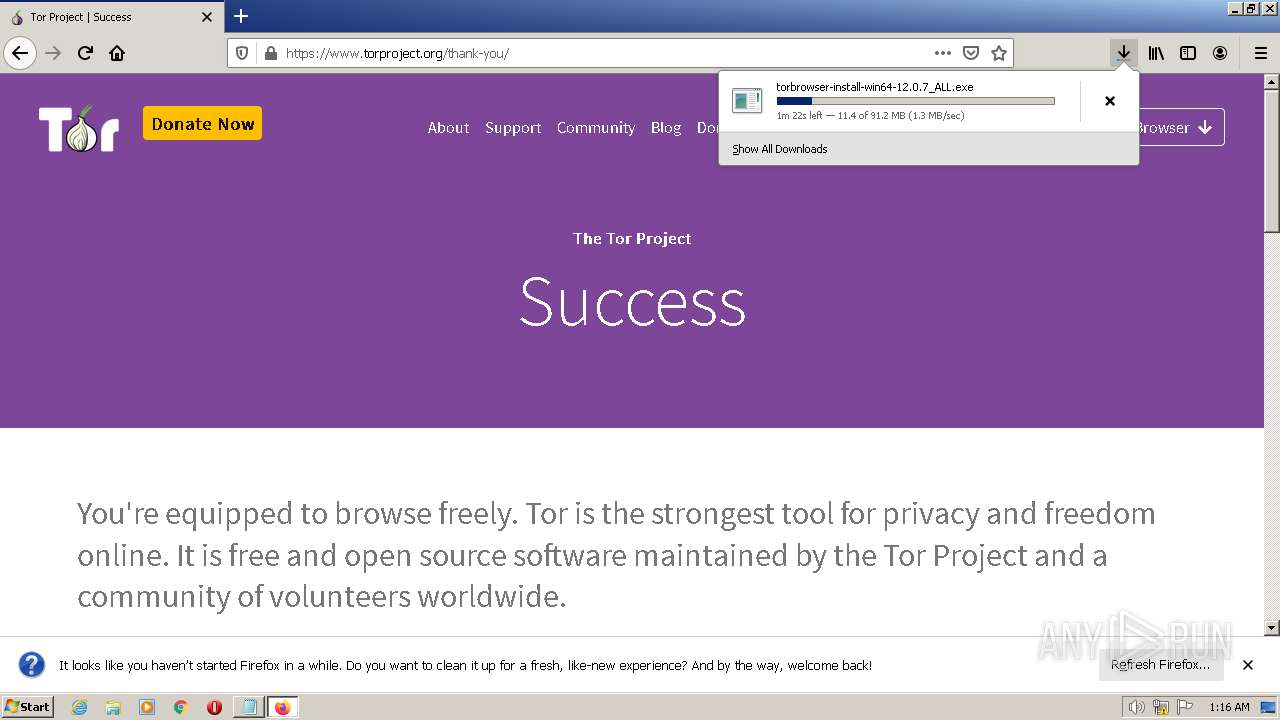
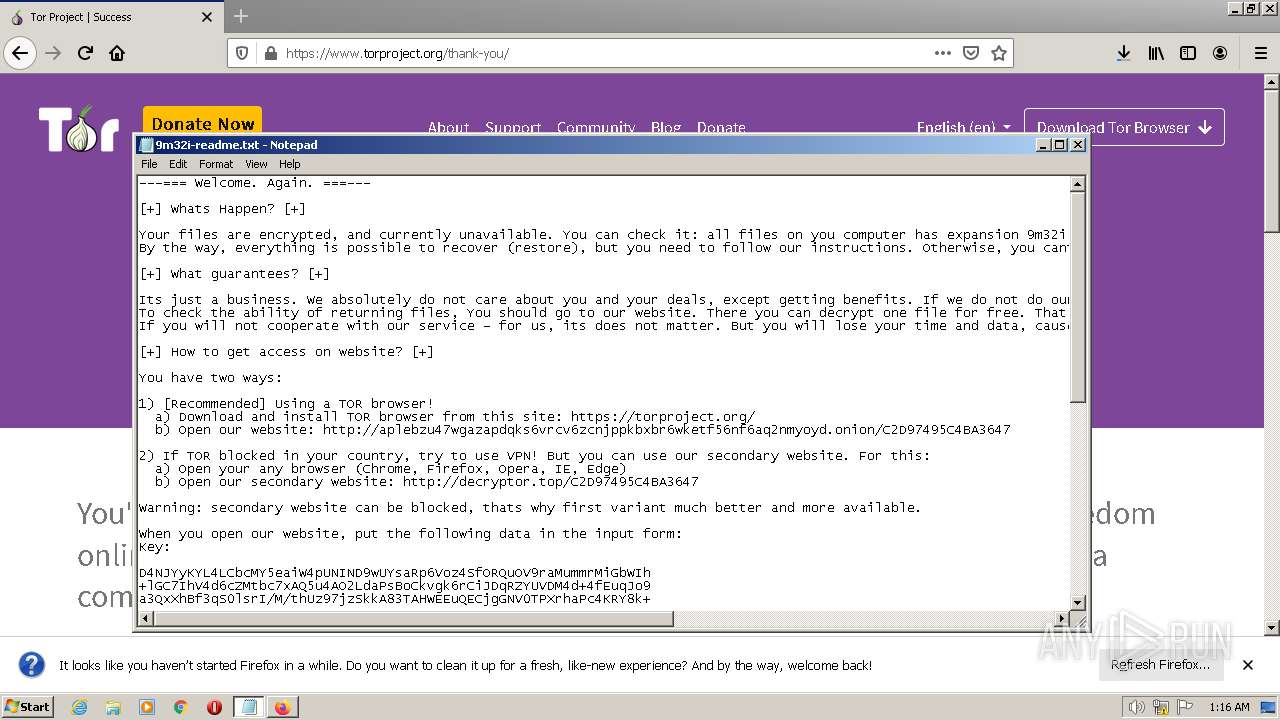
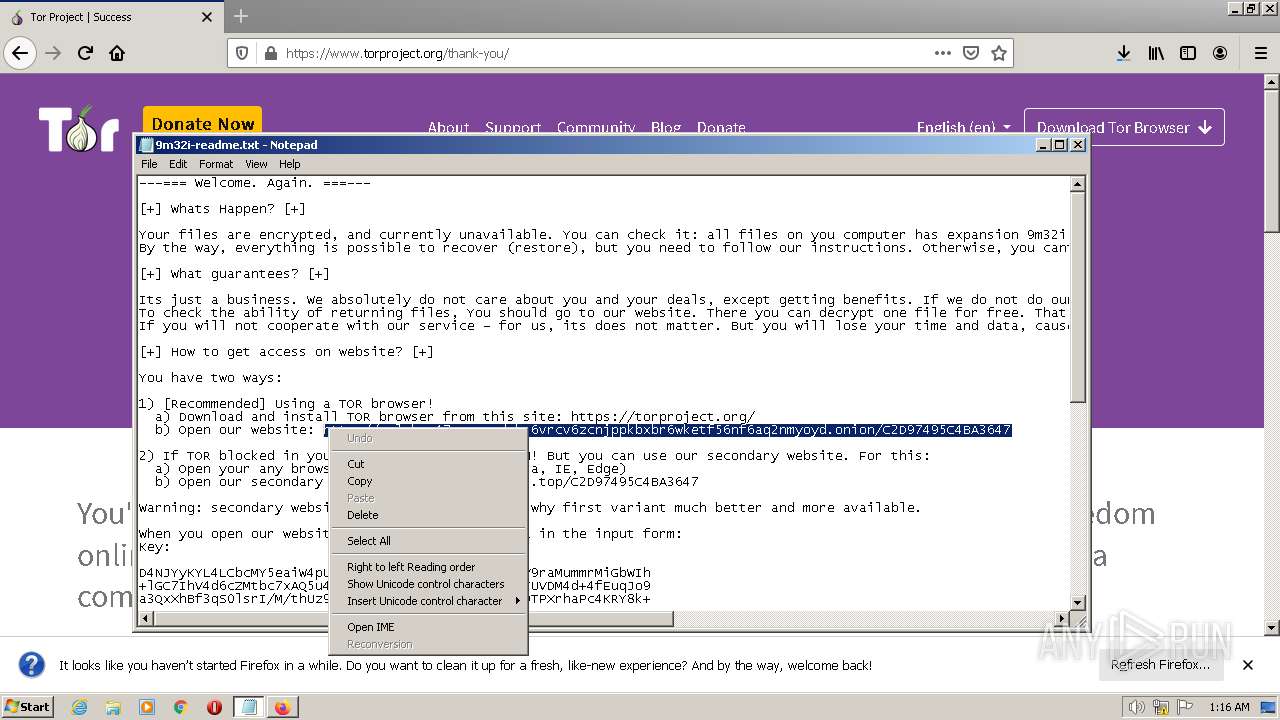
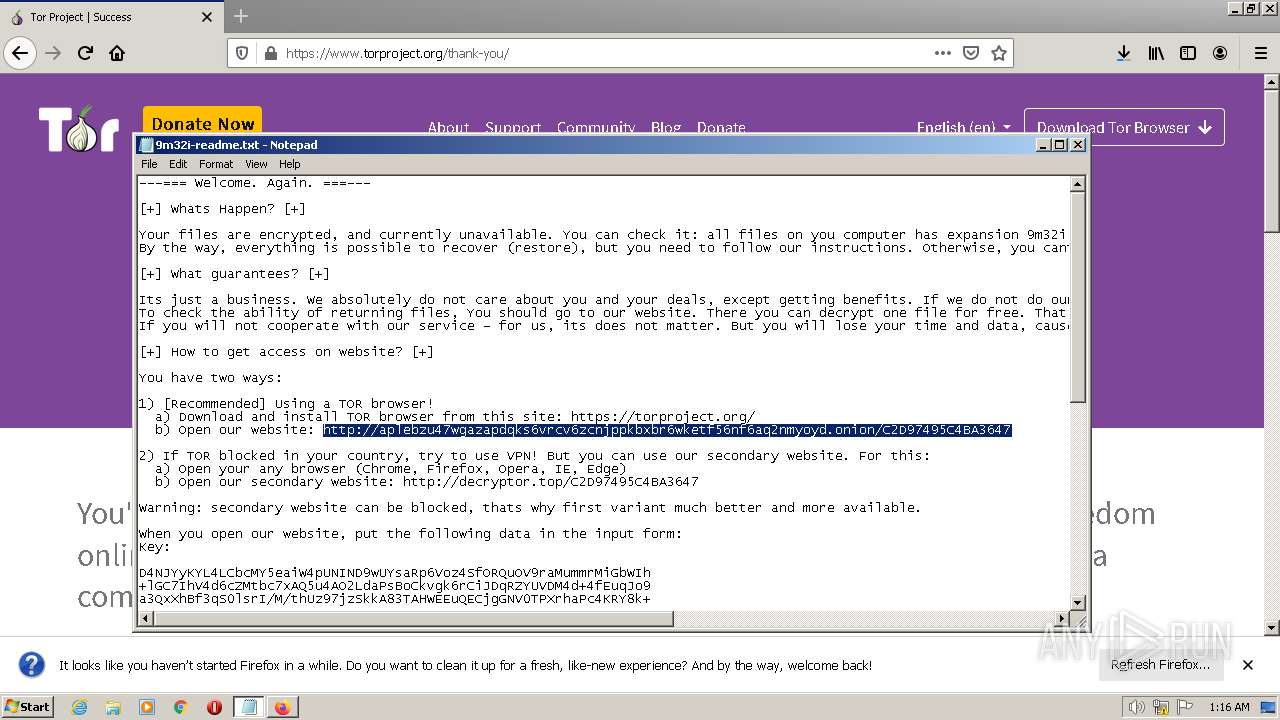
| File name: | 9m32i-readme.txt |
| Full analysis: | https://app.any.run/tasks/037b566c-9e16-45d9-bb08-66accc0b18a4 |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2023, 00:14:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 37395B5FFFEADB0246DF67B4CAA08F7D |
| SHA1: | B5043A3B512EC0CB62A2F9065CBB0983D18C5C82 |
| SHA256: | 29A7964EC2E7F030A877BC7A7ECB9FFBAF232A9C13029B9714B62D6D69DB8BA3 |
| SSDEEP: | 96:GL5iNsgHxU3TPGuaj0LgyMTMw2ziu4Il0NhS8JvOvQufcZyd9PrR5u:GL5J3jGuRs2jIS80Qu0ZSDW |
MALICIOUS
Application was dropped or rewritten from another process
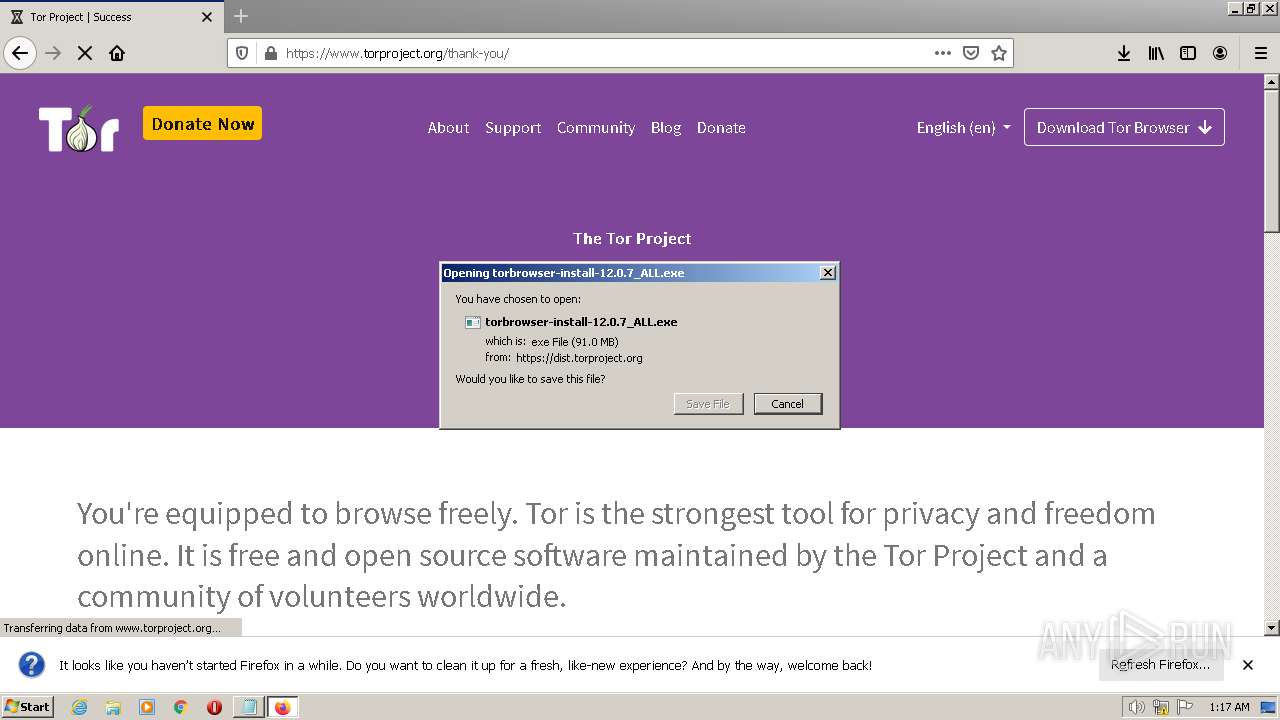
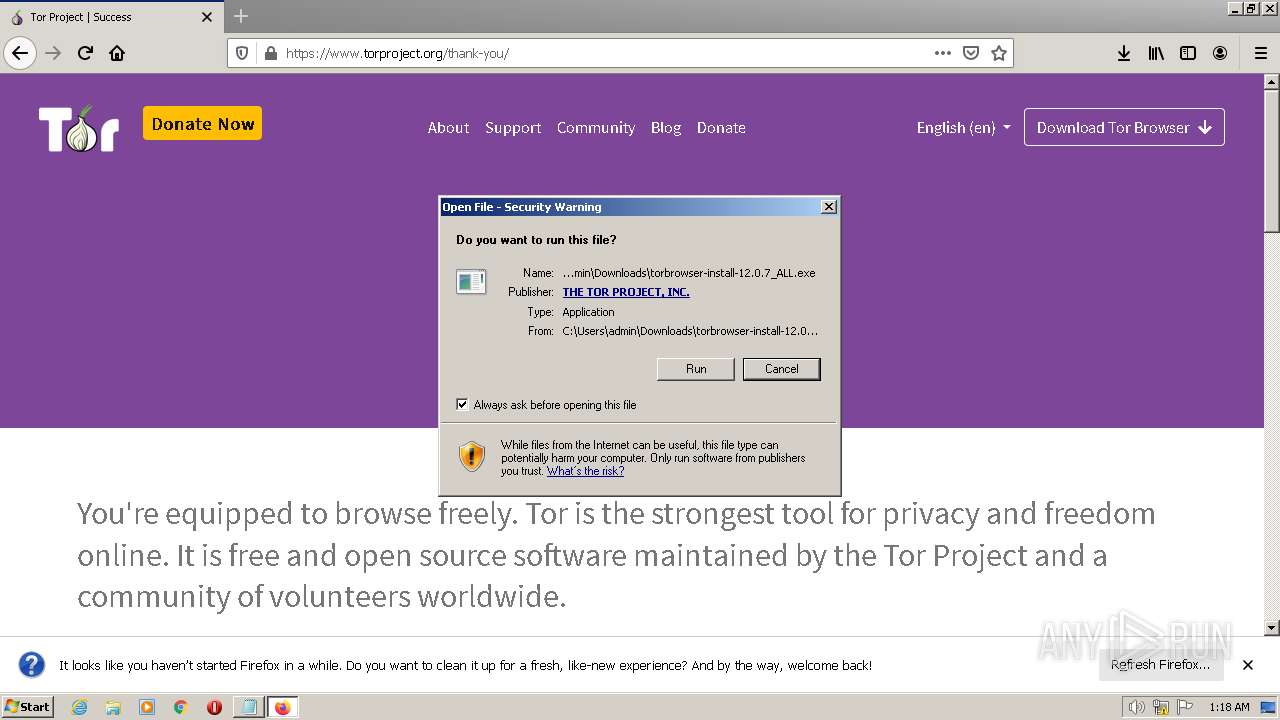
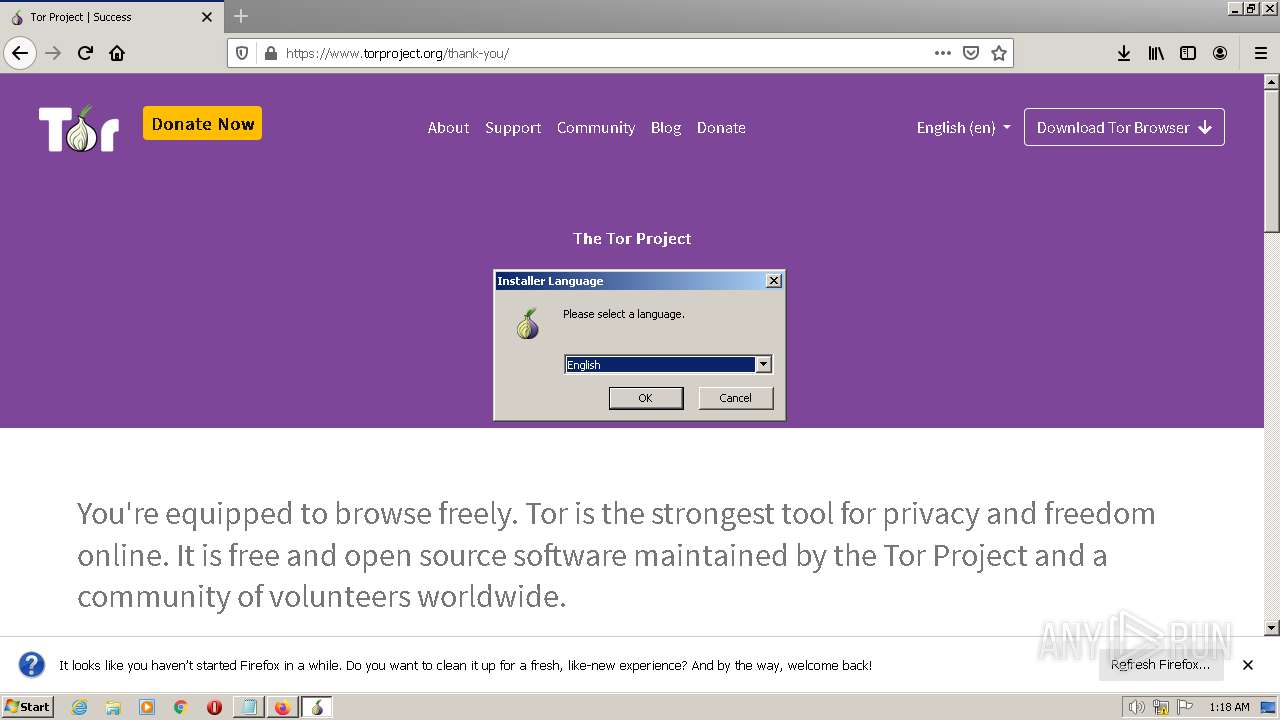
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
- firefox.exe (PID: 3788)
- firefox.exe (PID: 312)
The DLL Hijacking
- SearchProtocolHost.exe (PID: 328)
SUSPICIOUS
Loads DLL from Mozilla Firefox
- csrss.exe (PID: 388)
The process creates files with name similar to system file names
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
Executable content was dropped or overwritten
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
Application launched itself
- firefox.exe (PID: 3788)
- firefox.exe (PID: 312)
Reads the Internet Settings
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
INFO
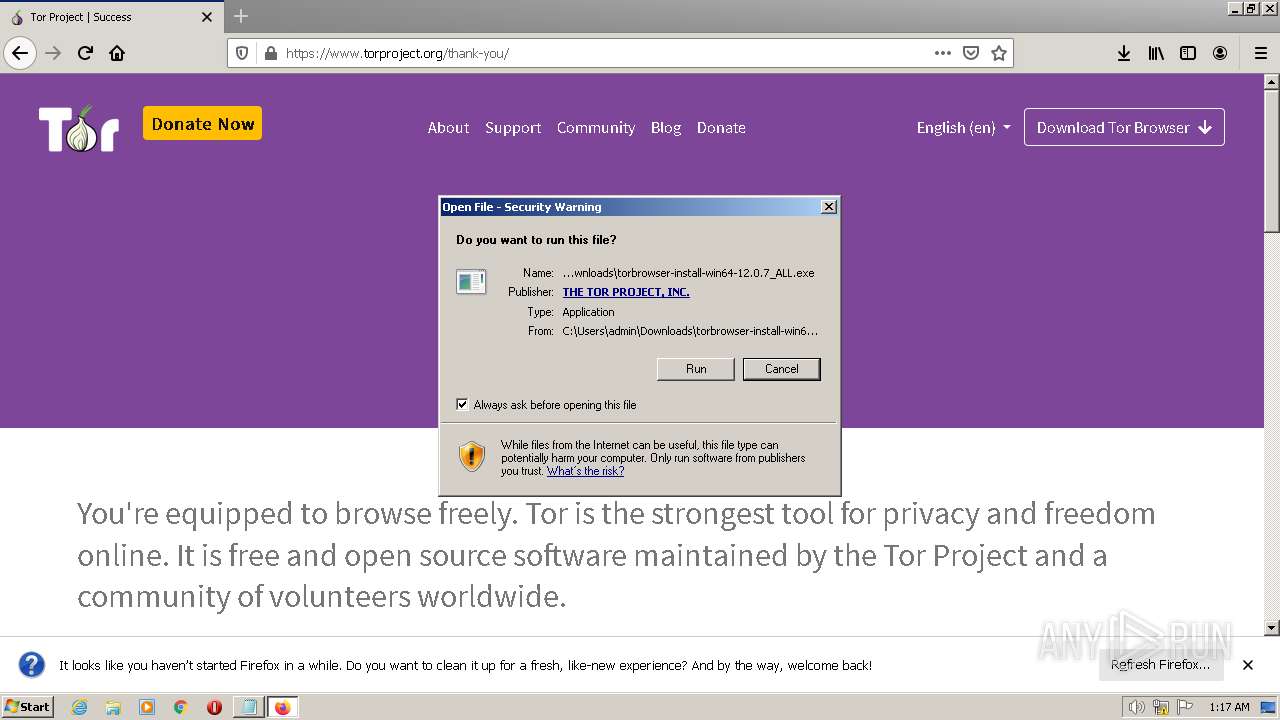
Manual execution by a user
- opera.exe (PID: 2880)
- firefox.exe (PID: 3192)
Application launched itself
- firefox.exe (PID: 3192)
- firefox.exe (PID: 3944)
The process checks LSA protection
- SearchProtocolHost.exe (PID: 328)
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
- firefox.exe (PID: 3788)
- firefox.exe (PID: 312)
Checks supported languages
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
- firefox.exe (PID: 3788)
- firefox.exe (PID: 312)
The process uses the downloaded file
- firefox.exe (PID: 3944)
Reads the computer name
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
- firefox.exe (PID: 312)
Executable content was dropped or overwritten
- firefox.exe (PID: 3944)
Create files in a temporary directory
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
Loads dropped or rewritten executable
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
- firefox.exe (PID: 3944)
- firefox.exe (PID: 3508)
- firefox.exe (PID: 3984)
- firefox.exe (PID: 2800)
- firefox.exe (PID: 1928)
- firefox.exe (PID: 3672)
- firefox.exe (PID: 1604)
- firefox.exe (PID: 2716)
The dropped object may contain a URL to Tor Browser
- firefox.exe (PID: 3944)
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
Reads the machine GUID from the registry
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
- firefox.exe (PID: 3788)
- firefox.exe (PID: 312)
Creates files in the program directory
- firefox.exe (PID: 312)
Dropped object may contain TOR URL's
- firefox.exe (PID: 312)
- torbrowser-install-12.0.7_ALL.exe (PID: 3460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
65
Monitored processes
26
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Users\admin\Desktop\Tor Browser\Browser\firefox.exe" | C:\Users\admin\Desktop\Tor Browser\Browser\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Tor Browser Exit code: 0 Version: 102.12.0 Modules
| |||||||||||||||
| 328 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 388 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | — | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 528 | "C:\Users\admin\Desktop\Tor Browser\Browser\firefox.exe" -contentproc --channel="312.0.604931343\429148253" -parentBuildID 20230702080101 -prefsHandle 1400 -prefMapHandle 1348 -prefsLen 22990 -prefMapSize 228356 -appDir "C:\Users\admin\Desktop\Tor Browser\Browser\browser" - 312 gpu | C:\Users\admin\Desktop\Tor Browser\Browser\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Tor Browser Exit code: 0 Version: 102.12.0 | |||||||||||||||
| 1604 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3944.20.715338907\1259063169" -childID 3 -isForBrowser -prefsHandle 3520 -prefMapHandle 3680 -prefsLen 7307 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3944 "\\.\pipe\gecko-crash-server-pipe.3944" 3452 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3944.34.367043444\577793662" -childID 5 -isForBrowser -prefsHandle 4552 -prefMapHandle 3608 -prefsLen 7676 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3944 "\\.\pipe\gecko-crash-server-pipe.3944" 4524 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2292 | "C:\Users\admin\Desktop\Tor Browser\Browser\firefox.exe" -contentproc --channel="312.1.2075836305\333566264" -childID 1 -isForBrowser -prefsHandle 1888 -prefMapHandle 1076 -prefsLen 25389 -prefMapSize 228356 -jsInitHandle 836 -jsInitLen 277276 -a11yResourceId 32 -parentBuildID 20230702080101 -appDir "C:\Users\admin\Desktop\Tor Browser\Browser\browser" - 312 tab | C:\Users\admin\Desktop\Tor Browser\Browser\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Tor Browser Exit code: 0 Version: 102.12.0 | |||||||||||||||
| 2472 | "C:\Users\admin\Desktop\Tor Browser\Browser\TorBrowser\Tor\tor.exe" --defaults-torrc "C:\Users\admin\Desktop\Tor Browser\Browser\TorBrowser\Data\Tor\torrc-defaults" -f "C:\Users\admin\Desktop\Tor Browser\Browser\TorBrowser\Data\Tor\torrc" DataDirectory "C:\Users\admin\Desktop\Tor Browser\Browser\TorBrowser\Data\Tor" ClientOnionAuthDir "C:\Users\admin\Desktop\Tor Browser\Browser\TorBrowser\Data\Tor\onion-auth" GeoIPFile "C:\Users\admin\Desktop\Tor Browser\Browser\TorBrowser\Data\Tor\geoip" GeoIPv6File "C:\Users\admin\Desktop\Tor Browser\Browser\TorBrowser\Data\Tor\geoip6" HashedControlPassword 16:0f276cc0c20e2921600154b6dc0faed2de6e1d6b6b35db4137e42180cc +__ControlPort 9151 +__SocksPort "127.0.0.1:9150 ExtendedErrors IPv6Traffic PreferIPv6 KeepAliveIsolateSOCKSAuth" __OwningControllerProcess 312 DisableNetwork 1 | C:\Users\admin\Desktop\Tor Browser\Browser\TorBrowser\Tor\tor.exe | — | firefox.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 2716 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3944.41.1596531066\1520601954" -childID 6 -isForBrowser -prefsHandle 4704 -prefMapHandle 3132 -prefsLen 9641 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3944 "\\.\pipe\gecko-crash-server-pipe.3944" 2752 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2720 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\9m32i-readme.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
23 158
Read events
22 797
Write events
361
Delete events
0
Modification events
| (PID) Process: | (2880) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe | |||
| (PID) Process: | (2880) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3192) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 09611C1E1E000000 | |||
| (PID) Process: | (3944) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: AD681C1E1E000000 | |||
| (PID) Process: | (3944) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3944) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3944) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3944) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3944) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (3944) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
Executable files
35
Suspicious files
417
Text files
210
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2880 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:A0932CB087558EFB13125021959575A4 | SHA256:99CF16A82C78AD2C692C794F6E4B0AF8B27CC0722B38C7CAC0B8F778328D91DD | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr83B4.tmp | text | |
MD5:A0932CB087558EFB13125021959575A4 | SHA256:99CF16A82C78AD2C692C794F6E4B0AF8B27CC0722B38C7CAC0B8F778328D91DD | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:FDBCDB294DED05EA01DCAA246B98C2C5 | SHA256:EAEC5A291DBC8E8760BAB0C1BB27CB801F671166CE85310FD173F54111357C4B | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00004.tmp | html | |
MD5:7F077F1FCE3D566040B0D69EB1F27D8F | SHA256:487AD0D2CF075F4328A1ADF57EF428759AD4E2C873A8EBD2AD9653990829C9CF | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:9F0A9EFDDD7D108B4557897867294CFA | SHA256:AA4BE7D514D9B1B5694D761FB25CD9B911C8A83F5F678744A25AFA0C70527EAE | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00003.tmp | html | |
MD5:BFE35A3974D416E2C1AB2160CDDB1FAA | SHA256:F7C0A00C1D1F68ED652963A8F0E9E0FAC6C4CAEEF43DCE9C50277CC66ED8AA4B | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00005.tmp | html | |
MD5:7F077F1FCE3D566040B0D69EB1F27D8F | SHA256:487AD0D2CF075F4328A1ADF57EF428759AD4E2C873A8EBD2AD9653990829C9CF | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprB71A.tmp | text | |
MD5:EA6746E0A9340890DA03C2EBA3843231 | SHA256:FF1108BE26787EAFDDDB1BBBC7DB25C1361F3F030D39E93511FC53328040B447 | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms~RF118edf.TMP | binary | |
MD5:DBC8C3C79F0DFF4745A5E25E13611AEF | SHA256:70C54F2C53CF246603B8DE4755D95C5AA51BF4B232340BEA5879724A1F84F675 | |||
| 2880 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\autosave.win | text | |
MD5:EA6746E0A9340890DA03C2EBA3843231 | SHA256:FF1108BE26787EAFDDDB1BBBC7DB25C1361F3F030D39E93511FC53328040B447 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
115
DNS requests
188
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
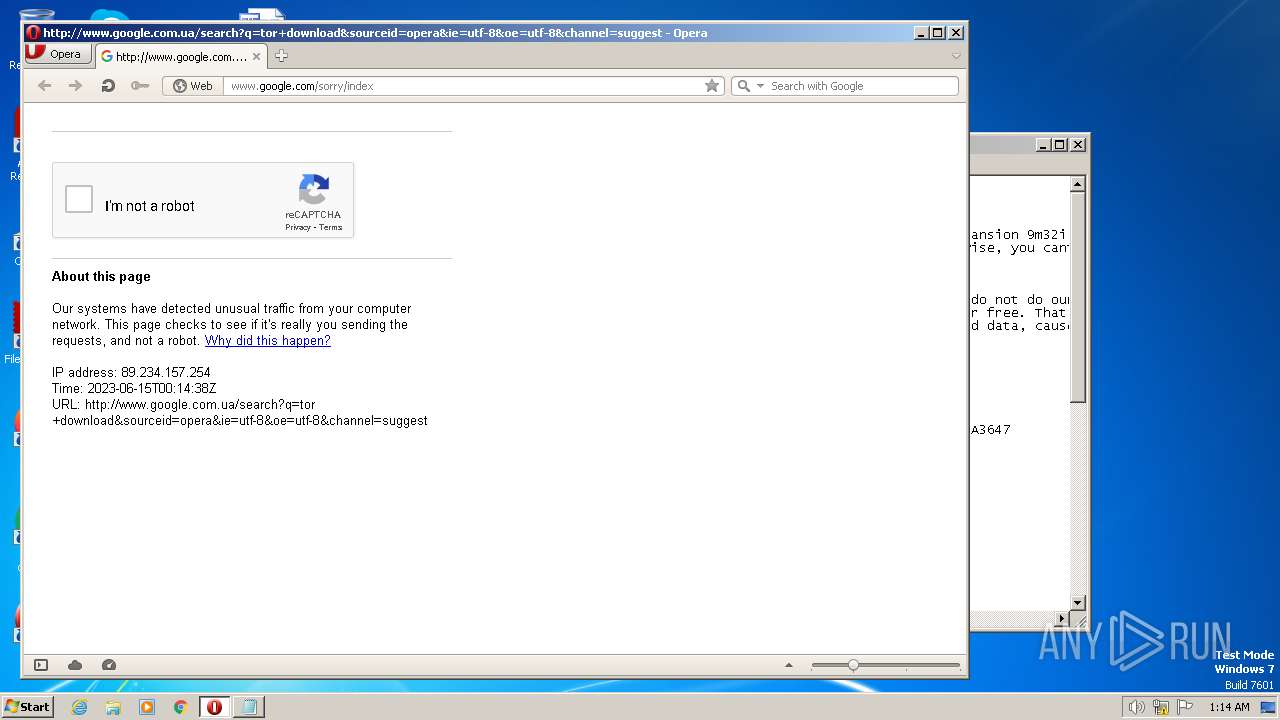
2880 | opera.exe | GET | 302 | 216.58.214.3:80 | http://www.google.com.ua/search?q=tor+download&sourceid=opera&ie=utf-8&oe=utf-8&channel=suggest&google_abuse=GOOGLE_ABUSE_EXEMPTION%3DID%3Da0e203b6a6e83f46:TM%3D1686788077:C%3D%3E:IP%3D89.234.157.254-:S%3Dt00s08z5hEUVtri-u4URsg%3B+path%3D/%3B+domain%3Dgoogle.com%3B+expires%3DThu,+15-Jun-2023+03:14:37+GMT | US | html | 308 b | whitelisted |
2880 | opera.exe | GET | 200 | 142.251.36.14:80 | http://clients1.google.com/complete/search?q=tor+down&client=opera-suggest-omnibox&hl=de | US | text | 145 b | whitelisted |
2880 | opera.exe | GET | 302 | 216.58.214.3:80 | http://www.google.com.ua/search?q=tor+download&sourceid=opera&ie=utf-8&oe=utf-8&channel=suggest | US | html | 455 b | whitelisted |
2880 | opera.exe | GET | 308 | 162.219.224.231:80 | http://www.amazon.fr/favicon.ico | US | html | 113 b | whitelisted |
2880 | opera.exe | GET | 200 | 142.251.36.35:80 | http://crl.pki.goog/gtsr1/gtsr1.crl | US | binary | 760 b | whitelisted |
2880 | opera.exe | GET | 200 | 142.251.36.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGA1zKkB7VojCTuznaB0c44%3D | US | binary | 471 b | whitelisted |
2880 | opera.exe | GET | 302 | 185.26.182.110:80 | http://redir.opera.com/speeddials/amazon/ | unknown | html | 313 b | whitelisted |
2880 | opera.exe | GET | 308 | 162.219.224.231:80 | http://www.amazon.fr/exec/obidos/redirect-home/operasoftware-21 | US | html | 144 b | whitelisted |
2880 | opera.exe | GET | 400 | 82.145.216.15:80 | http://sitecheck2.opera.com/?host=www.google.com&hdn=AGZGLiBzId7nGTYe3dxEwA== | unknown | html | 150 b | whitelisted |
2880 | opera.exe | GET | 200 | 142.251.36.14:80 | http://clients1.google.com/complete/search?q=duc&client=opera-suggest-omnibox&hl=de | US | text | 154 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2880 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3216 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2880 | opera.exe | 142.251.36.14:80 | clients1.google.com | GOOGLE | US | whitelisted |
2880 | opera.exe | 216.58.214.3:80 | www.google.com.ua | GOOGLE | US | whitelisted |
2880 | opera.exe | 82.145.216.15:80 | sitecheck2.opera.com | Opera Software AS | NO | suspicious |
2880 | opera.exe | 216.58.214.4:80 | www.google.com | GOOGLE | US | whitelisted |
2880 | opera.exe | 142.251.36.35:80 | crl.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
www.google.com |
| malicious |
crl.pki.goog |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
redir.opera.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
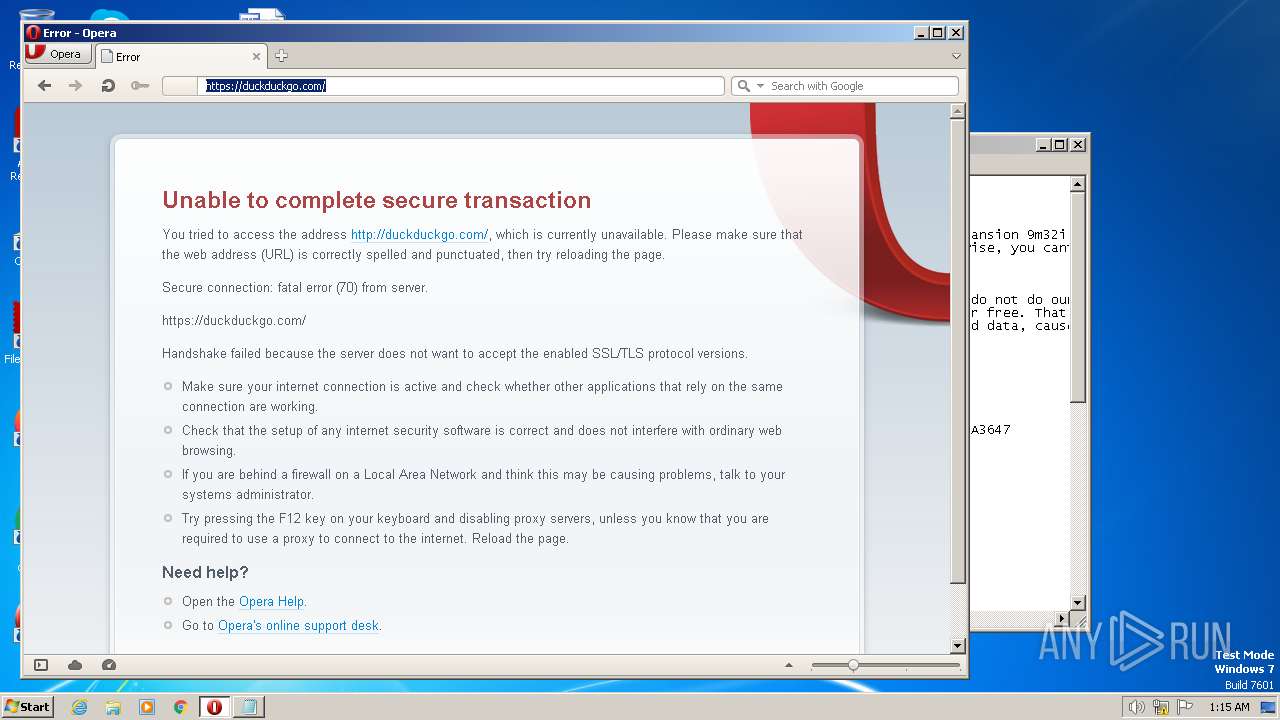
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2880 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 665 |
1 ETPRO signatures available at the full report