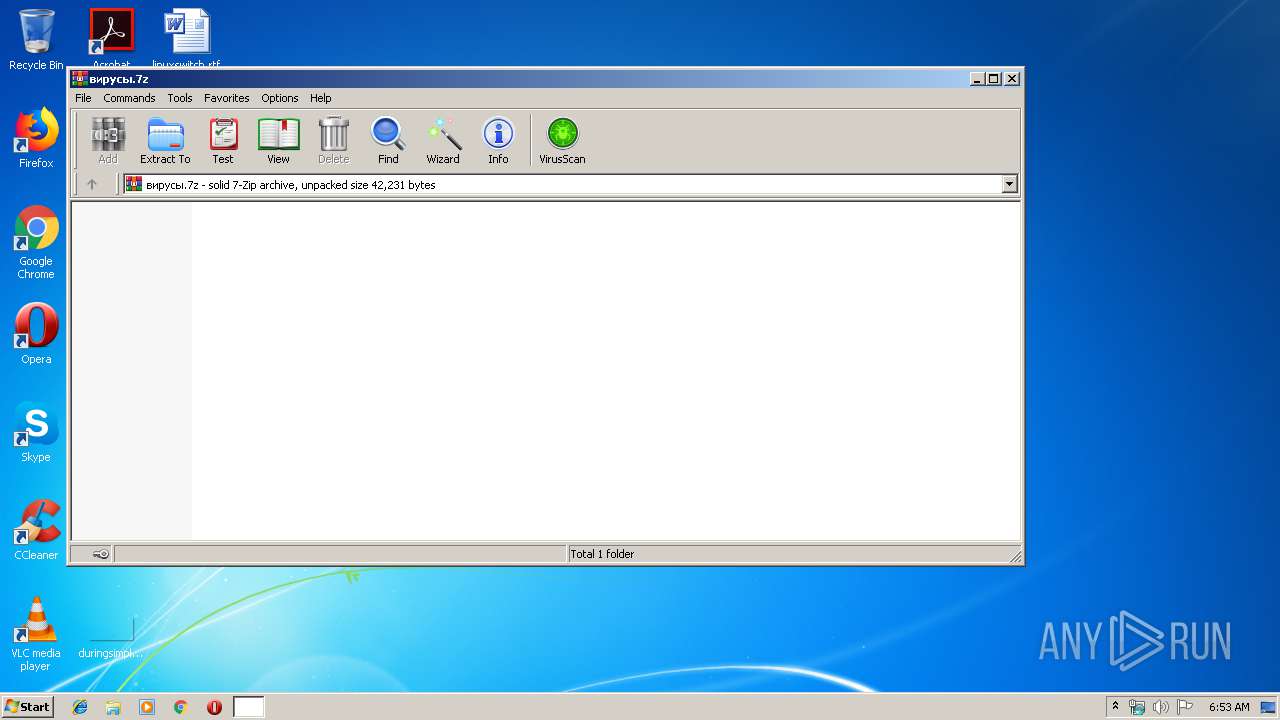
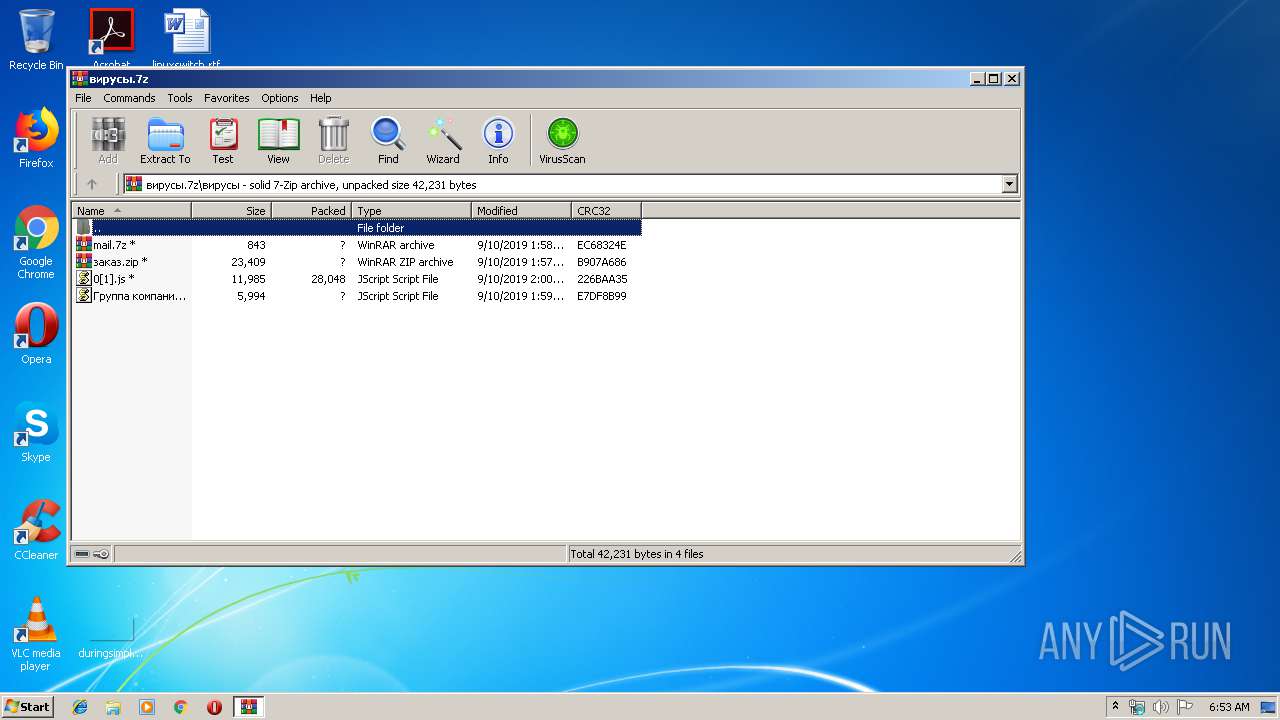
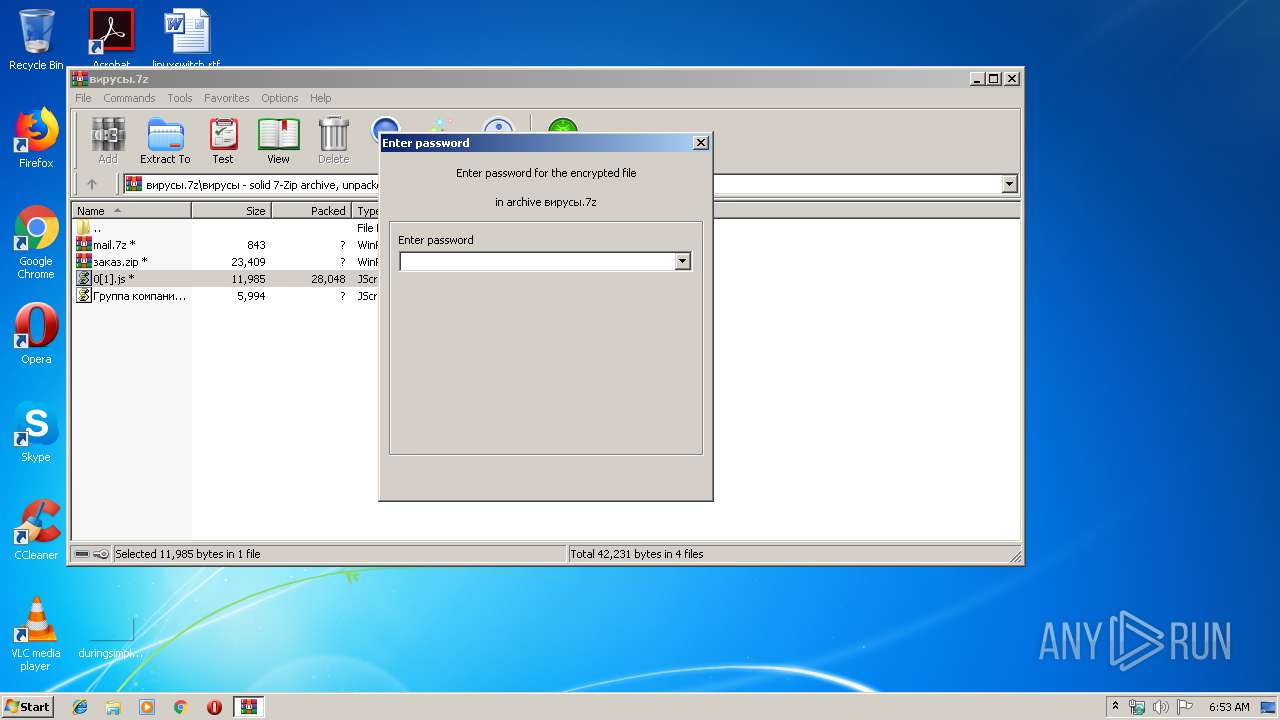
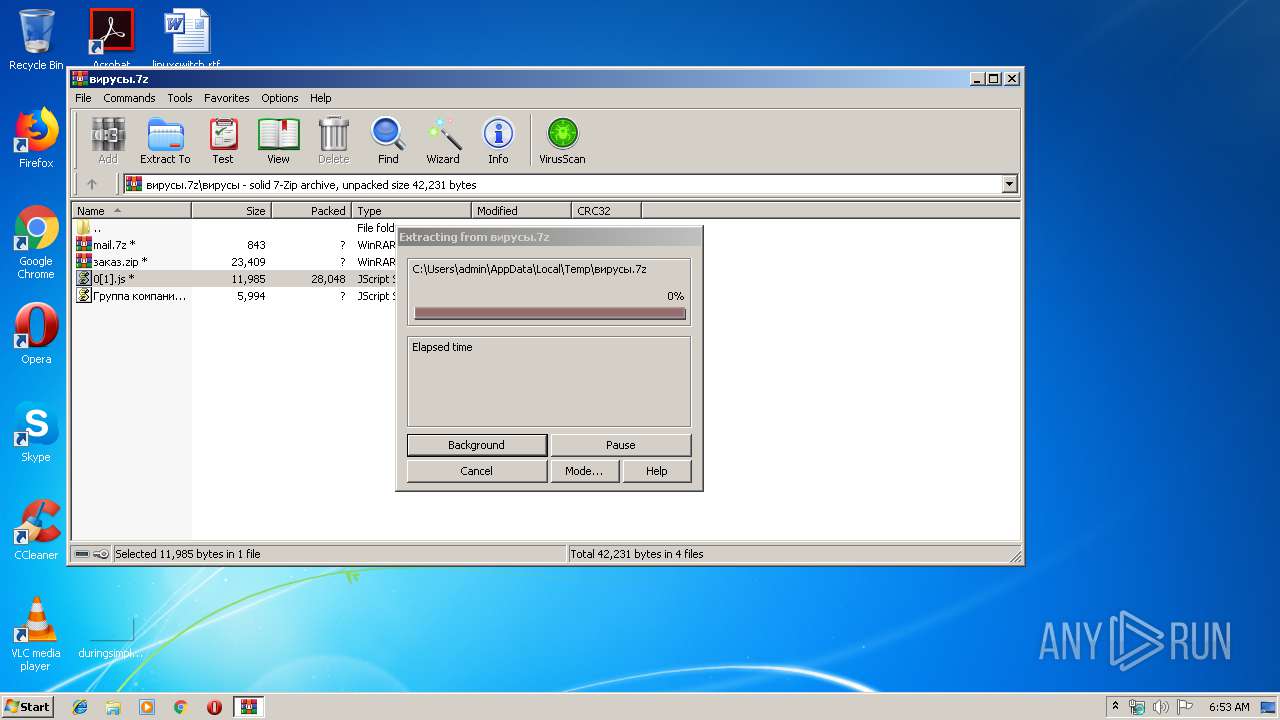
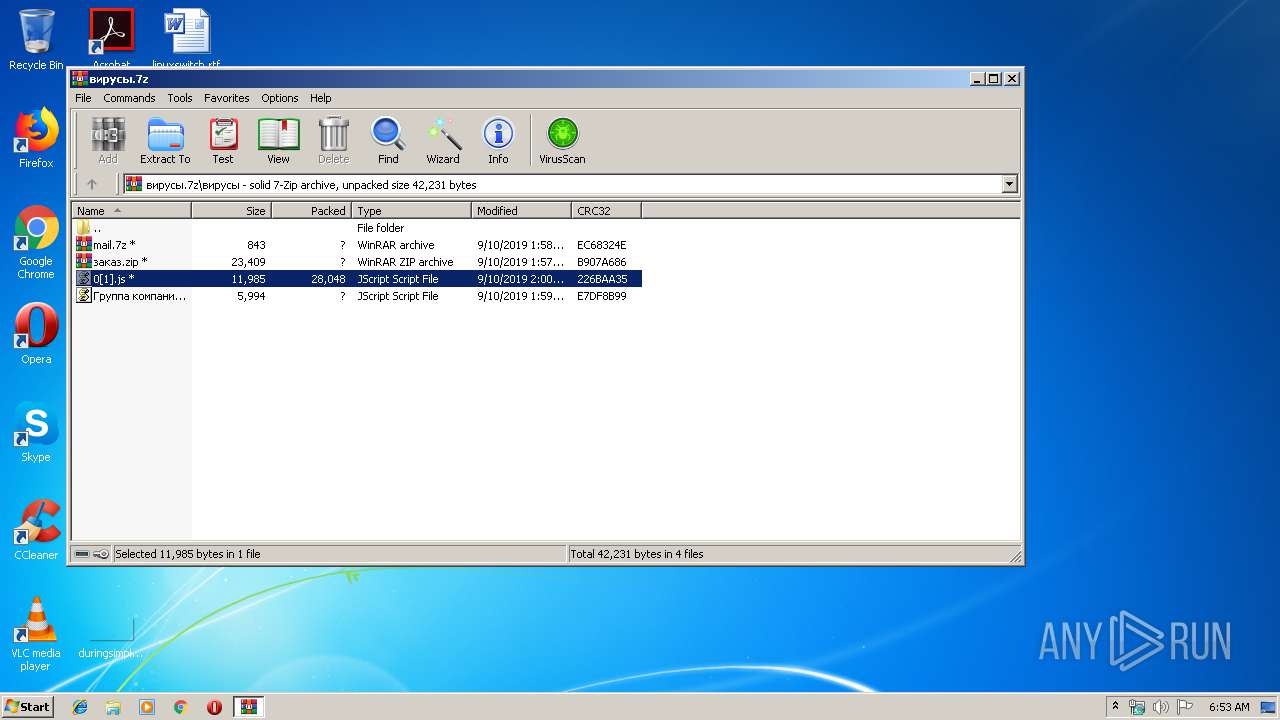
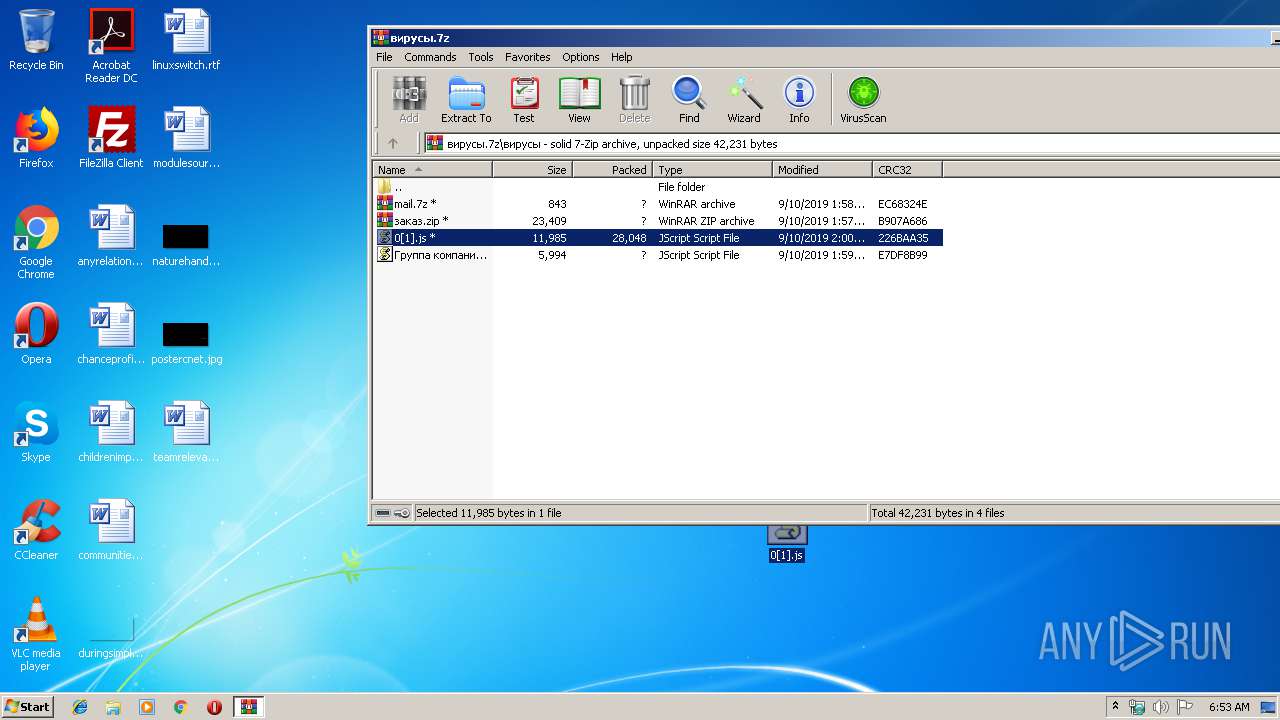
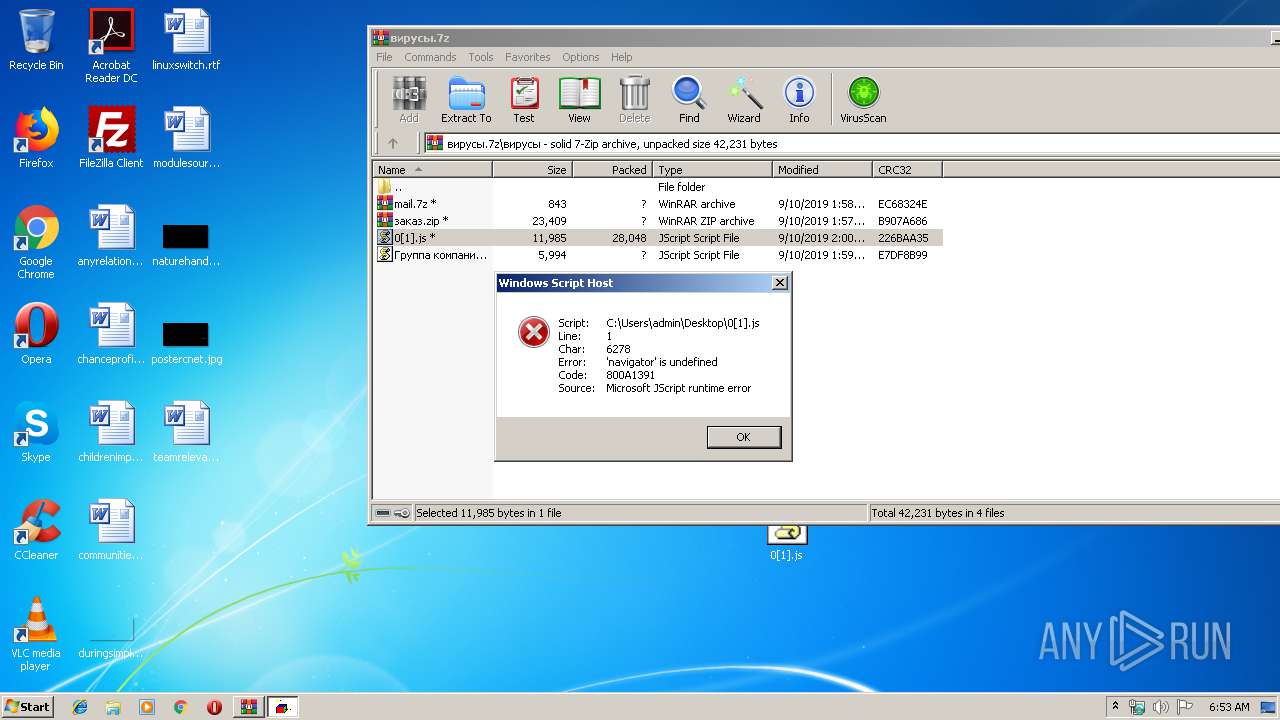
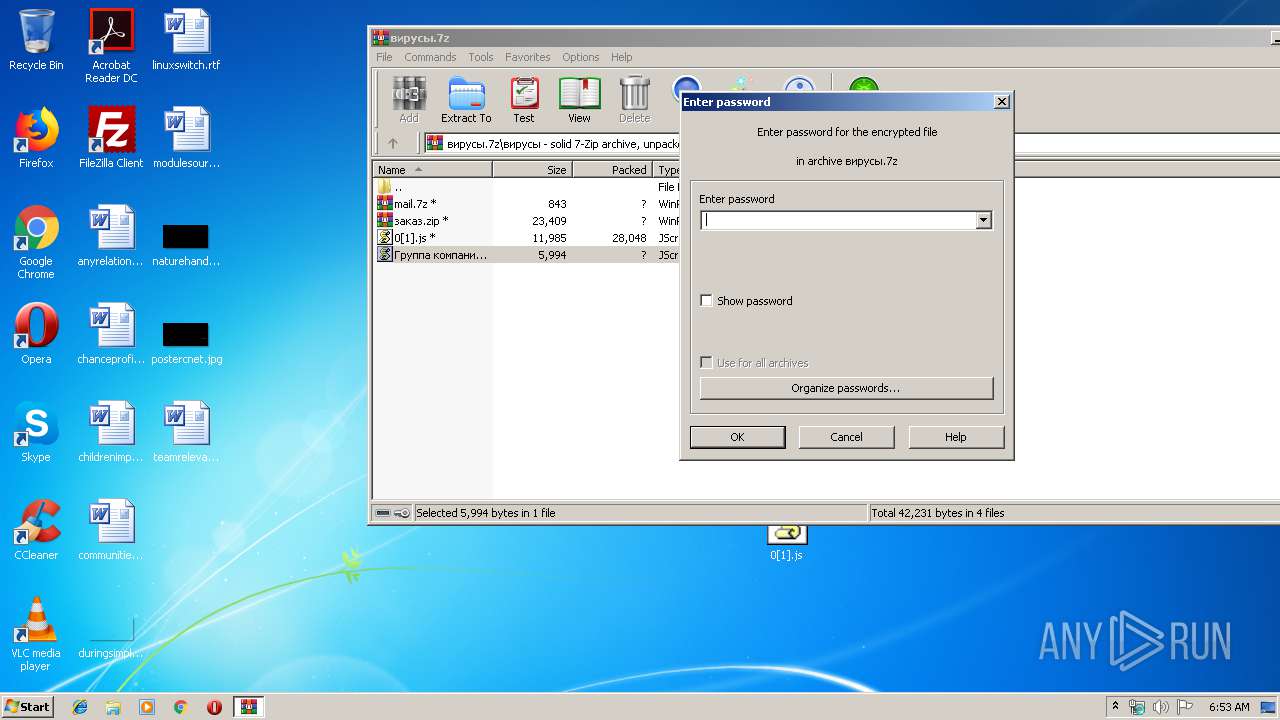
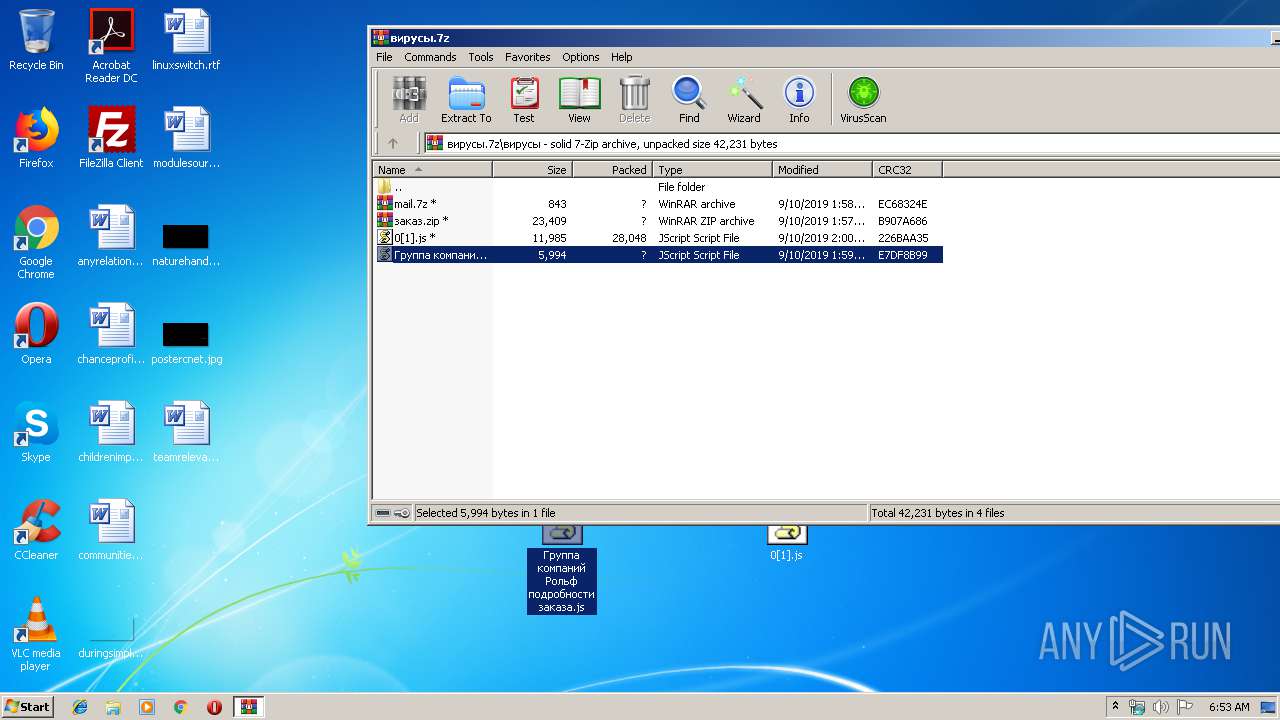
| File name: | вирусы.7z |
| Full analysis: | https://app.any.run/tasks/8c0a7afd-6e3c-42c9-a047-3cccc0baf8de |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2019, 05:52:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | FBD5F1285B72DD1B3F39BC8A7843B5D8 |
| SHA1: | BE9C0D30FED7936429BFCA78A4D0C578F634B004 |
| SHA256: | 29A1D4D563E57D7EFE7D2C29DDF77F803F6D10A416AFF281B84BED99D9BAC9A7 |
| SSDEEP: | 768:LuPOhMw7k9lns2rdUCvInkC9rik9TjRO/s:LuJEoLdvInV3s/s |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2580)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 3188)
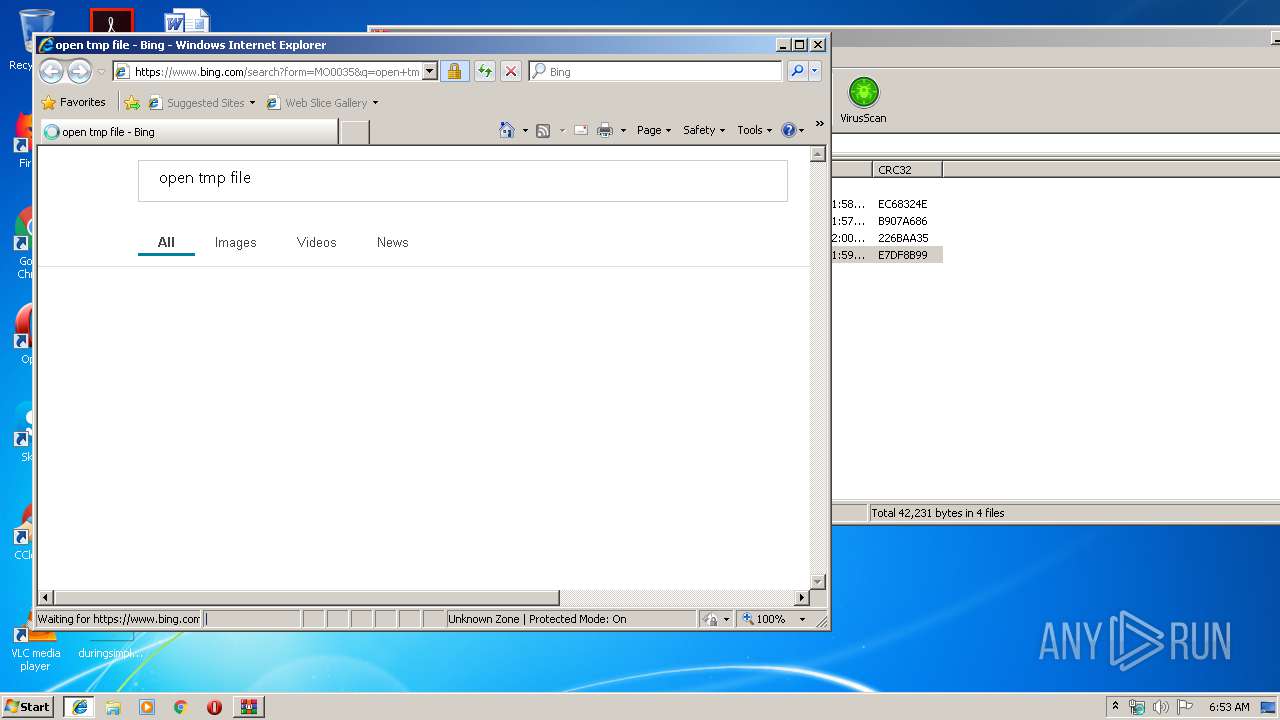
Starts Internet Explorer
- rundll32.exe (PID: 2704)
INFO
Manual execution by user
- WScript.exe (PID: 2604)
- WScript.exe (PID: 2580)
Reads Internet Cache Settings
- iexplore.exe (PID: 2424)
Reads internet explorer settings
- iexplore.exe (PID: 2424)
Changes internet zones settings
- iexplore.exe (PID: 4080)
Creates files in the user directory
- iexplore.exe (PID: 2424)
Application launched itself
- iexplore.exe (PID: 4080)
Adds / modifies Windows certificates
- iexplore.exe (PID: 4080)
Reads settings of System Certificates
- iexplore.exe (PID: 4080)
Changes settings of System certificates
- iexplore.exe (PID: 4080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
42
Monitored processes
7
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2424 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4080 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2580 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Группа компаний Рольф подробности заказа.js" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2604 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\0[1].js" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
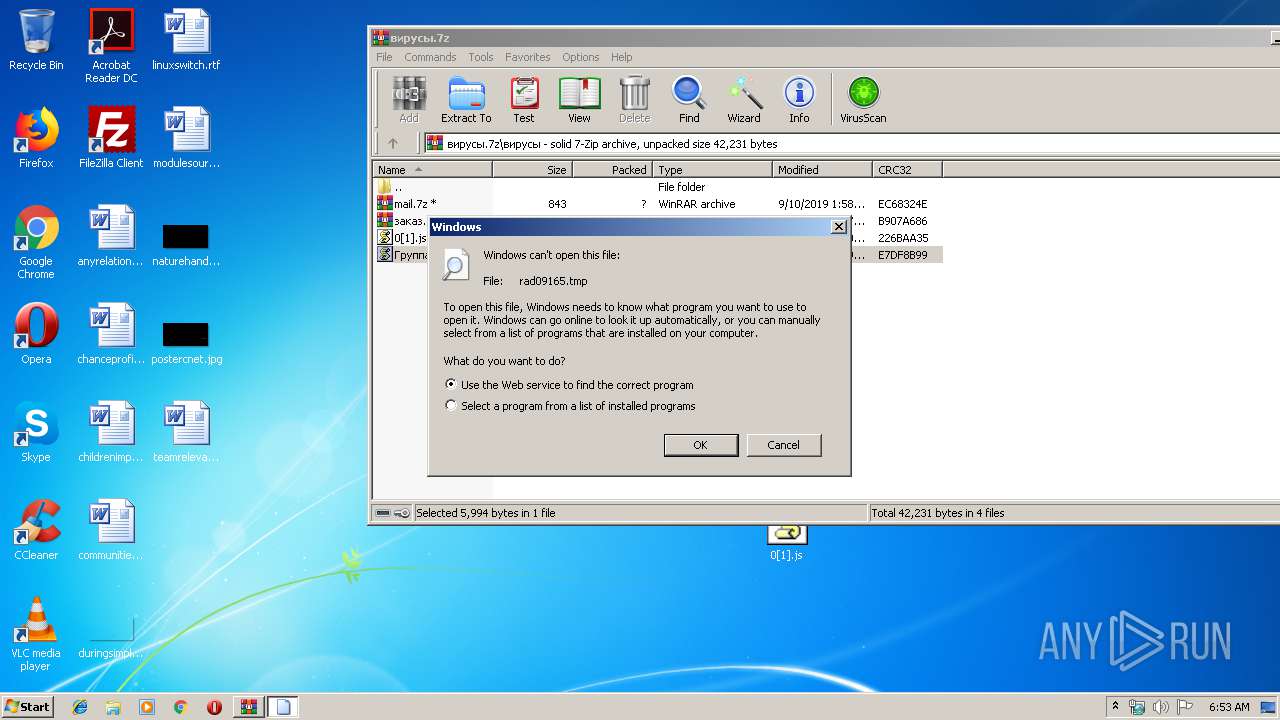
| 2704 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\rad09165.tmp | C:\Windows\system32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3188 | "C:\Windows\System32\cmd.exe" /c C:\Users\admin\AppData\Local\Temp\rad09165.tmp | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3548 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\вирусы.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 4080 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 310
Read events
1 221
Write events
87
Delete events
2
Modification events
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\вирусы.7z | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\wshext.dll,-4804 |
Value: JScript Script File | |||
| (PID) Process: | (3548) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
25
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3548.19760\вирусы\0[1].js | — | |
MD5:— | SHA256:— | |||
| 3548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3548.22150\вирусы\Группа компаний Рольф подробности заказа.js | — | |
MD5:— | SHA256:— | |||
| 2424 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[2].txt | — | |
MD5:— | SHA256:— | |||
| 2424 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\ZXWVJLVW\search[1].txt | — | |
MD5:— | SHA256:— | |||
| 2580 | WScript.exe | C:\Users\admin\AppData\Local\Temp\rad09165.tmp | html | |
MD5:— | SHA256:— | |||
| 2580 | WScript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\suspendedpage[1].htm | html | |
MD5:— | SHA256:— | |||
| 4080 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 4080 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\favicon[1].png | — | |
MD5:— | SHA256:— | |||
| 2424 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\G6FPD0G2\f8c6dd44[1].js | text | |
MD5:— | SHA256:— | |||
| 2424 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\2MXE551W\19b40d8c[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
13
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2424 | iexplore.exe | GET | 302 | 2.19.38.59:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=tmp | unknown | — | — | whitelisted |
2424 | iexplore.exe | GET | 301 | 2.16.186.27:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=tmp | unknown | — | — | whitelisted |
2580 | WScript.exe | GET | 200 | 198.38.82.253:80 | http://oteea-land.com/cgi-sys/suspendedpage.cgi | US | html | 7.41 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2580 | WScript.exe | 198.38.82.253:80 | oteea-land.com | Server Central Network | US | malicious |
4080 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2424 | iexplore.exe | 2.19.38.59:80 | go.microsoft.com | Akamai International B.V. | — | whitelisted |
2424 | iexplore.exe | 2.16.186.27:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
2424 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2424 | iexplore.exe | 40.90.23.206:443 | login.live.com | Microsoft Corporation | US | unknown |
4080 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
oteea-land.com |
| malicious |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
login.live.com |
| whitelisted |