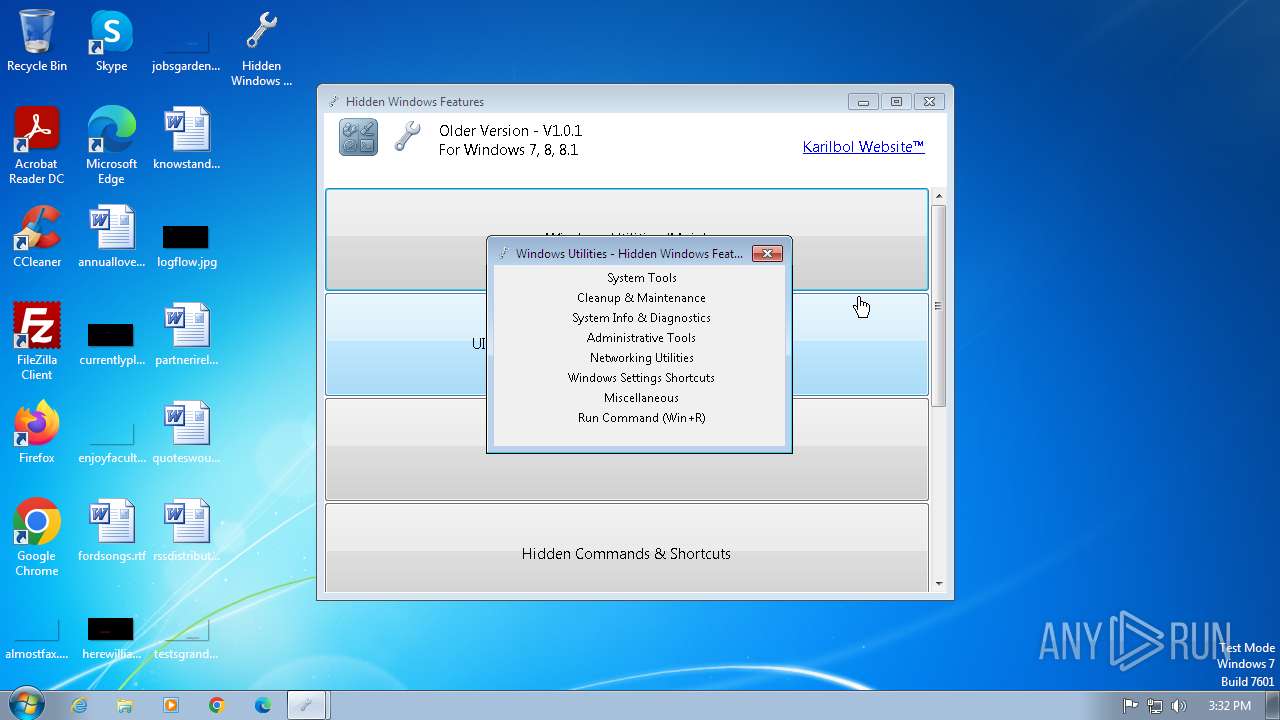
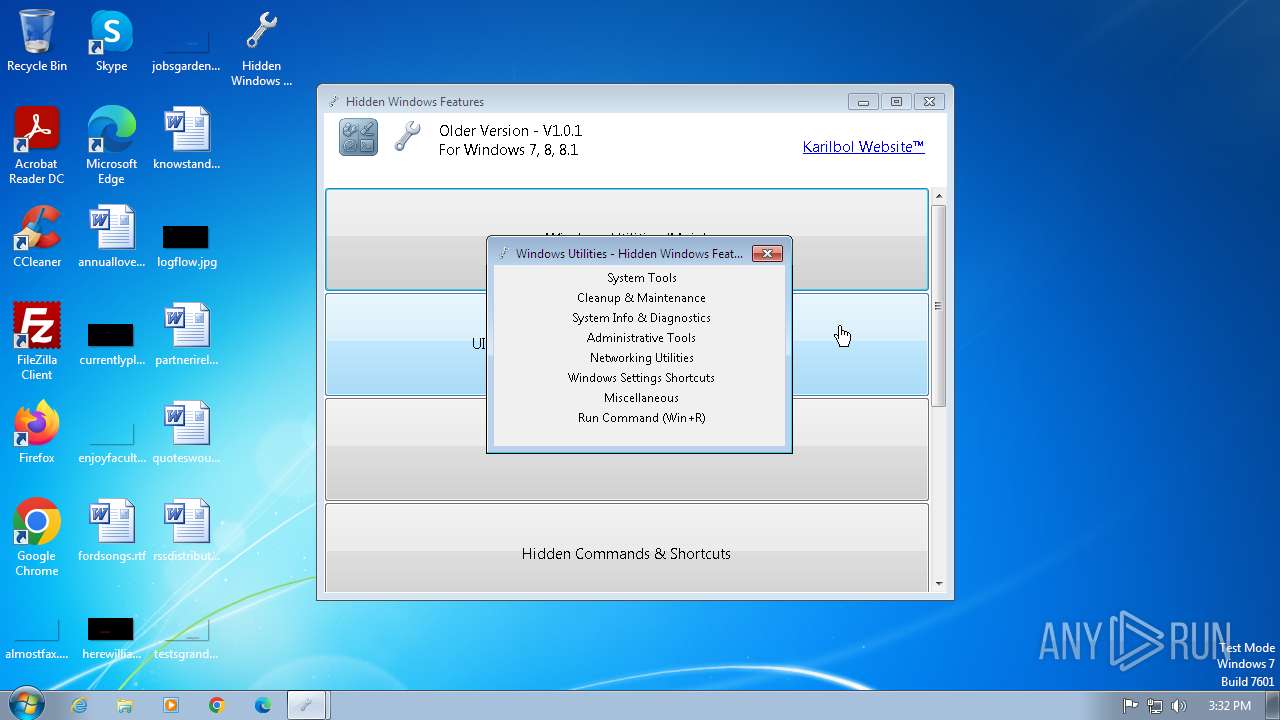
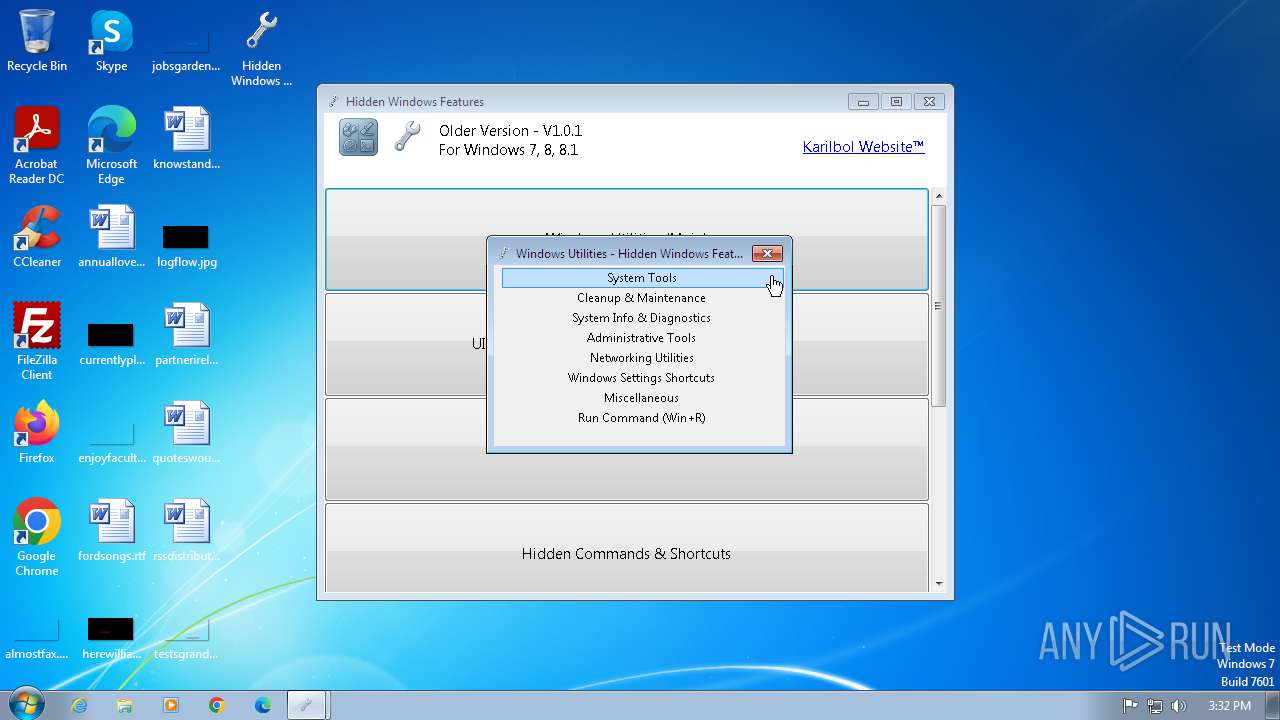
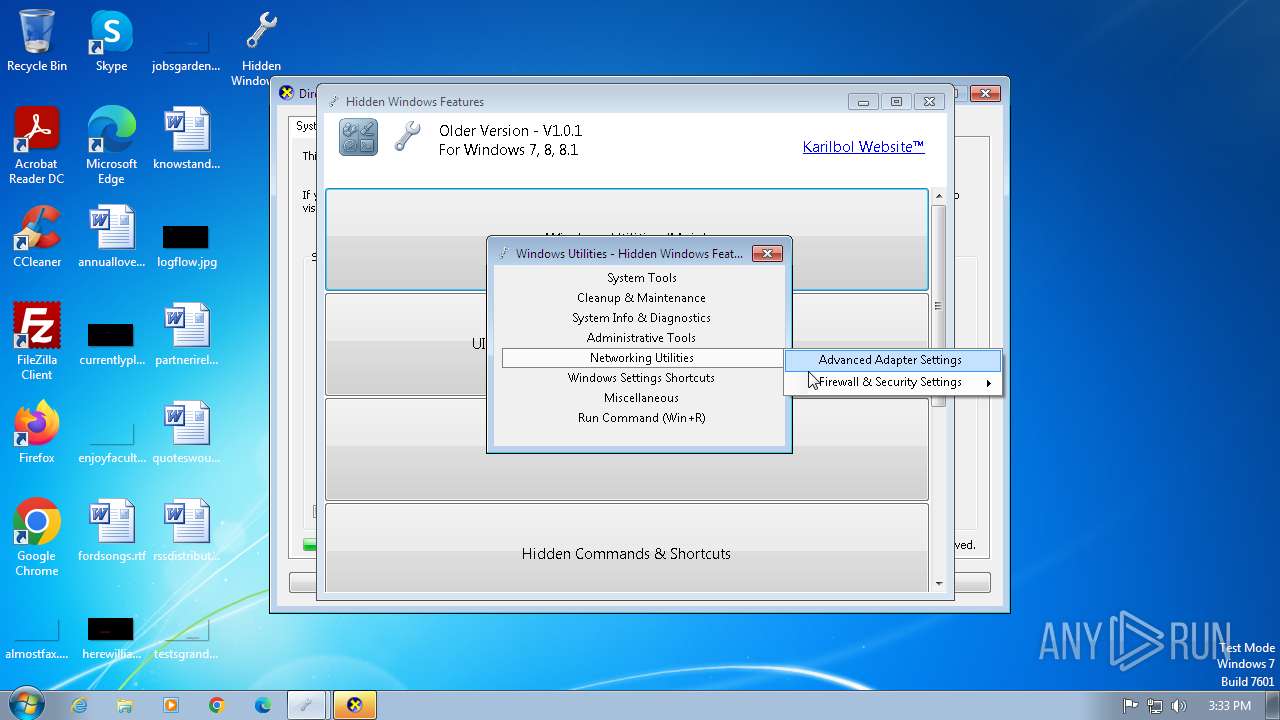
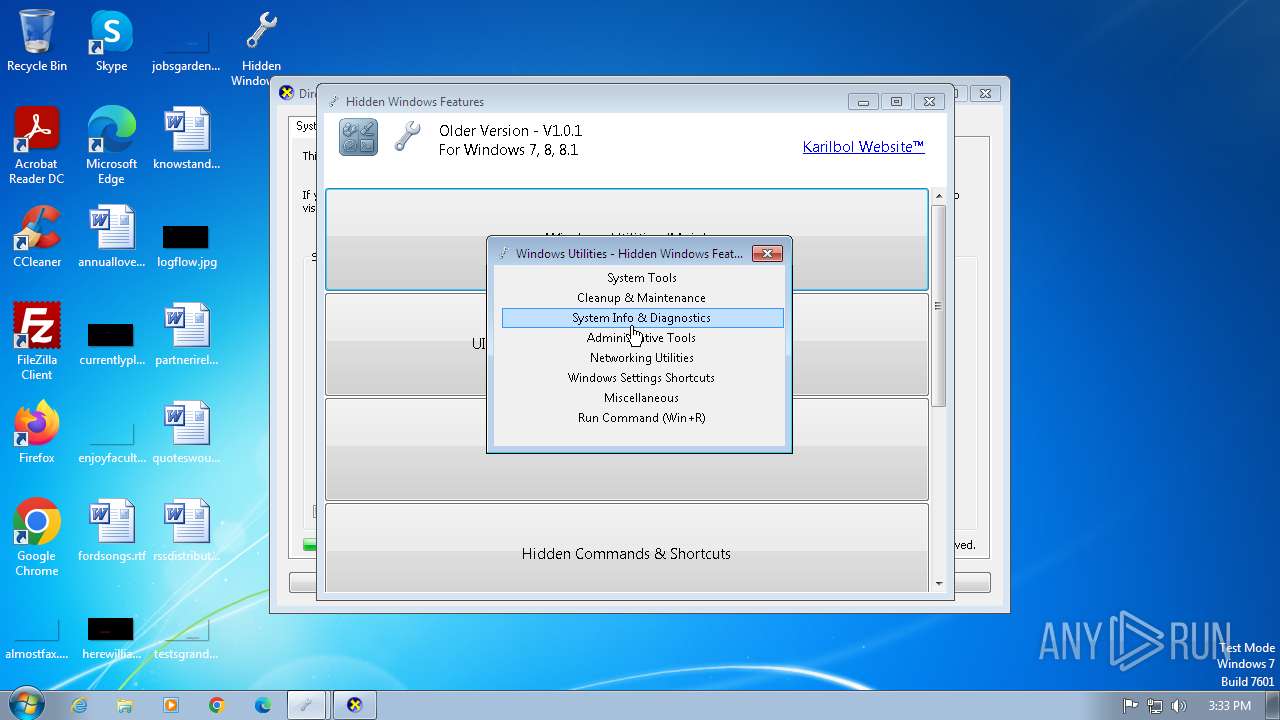
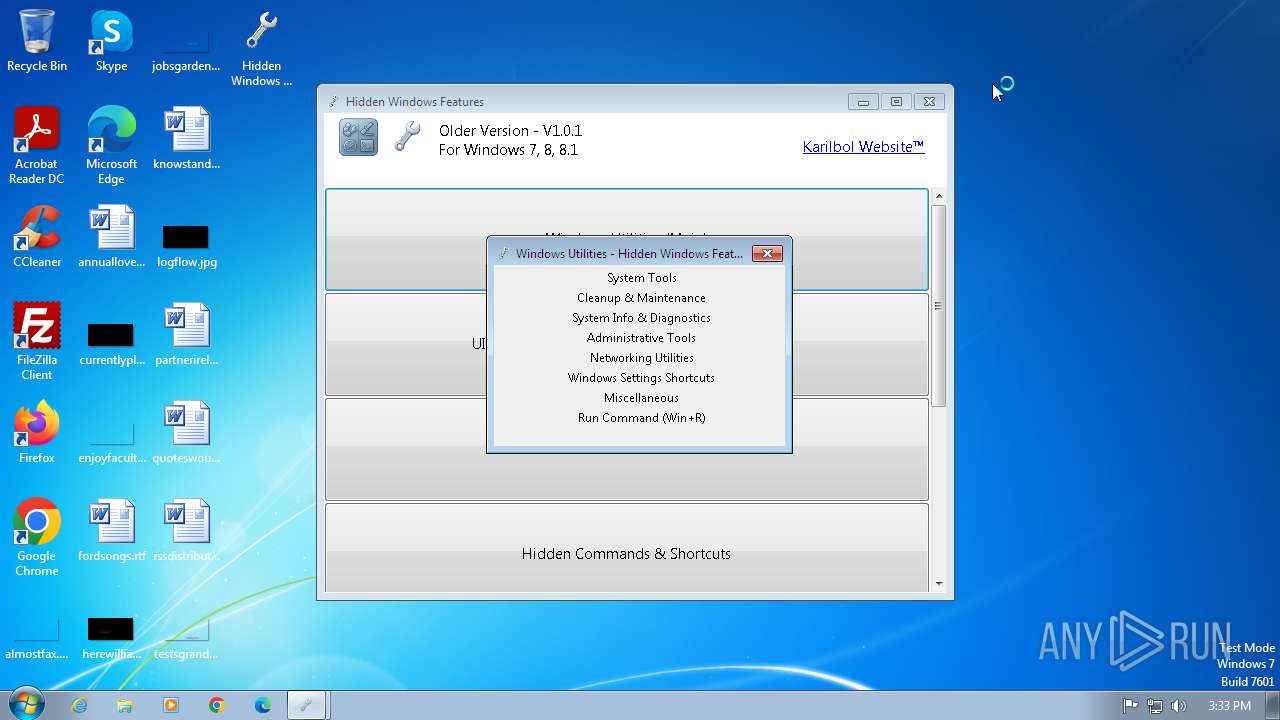
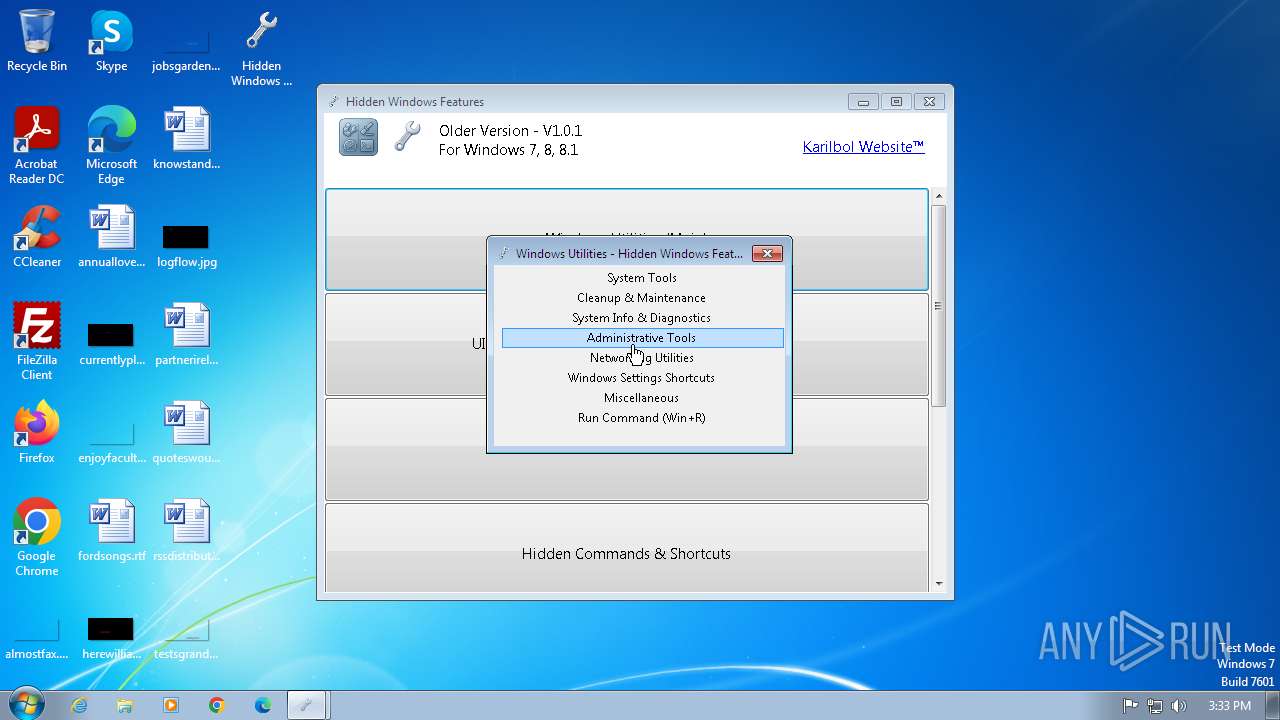
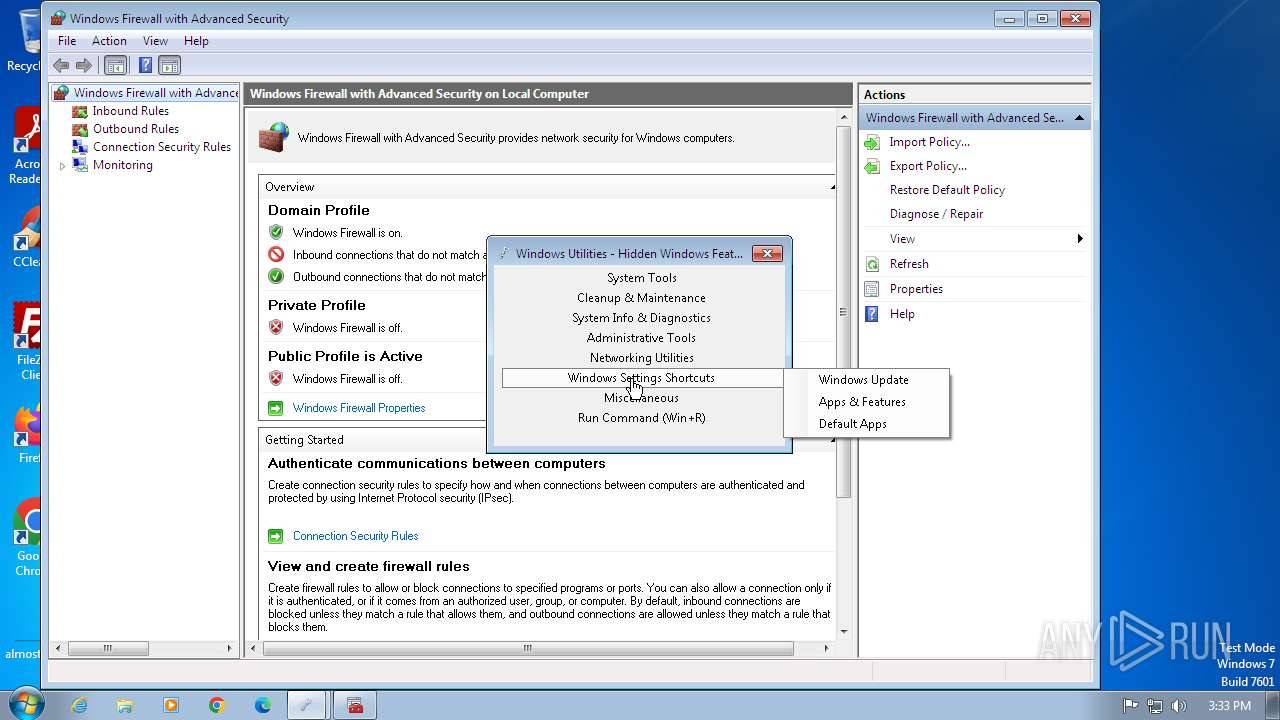
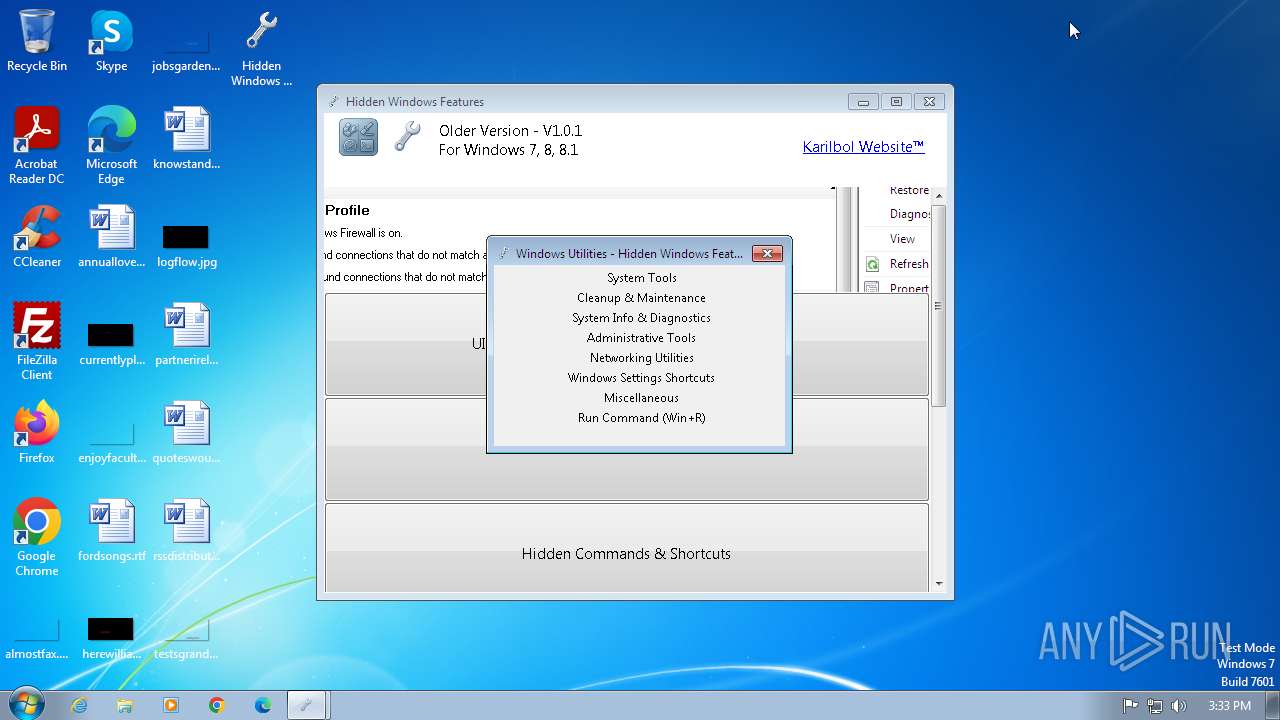
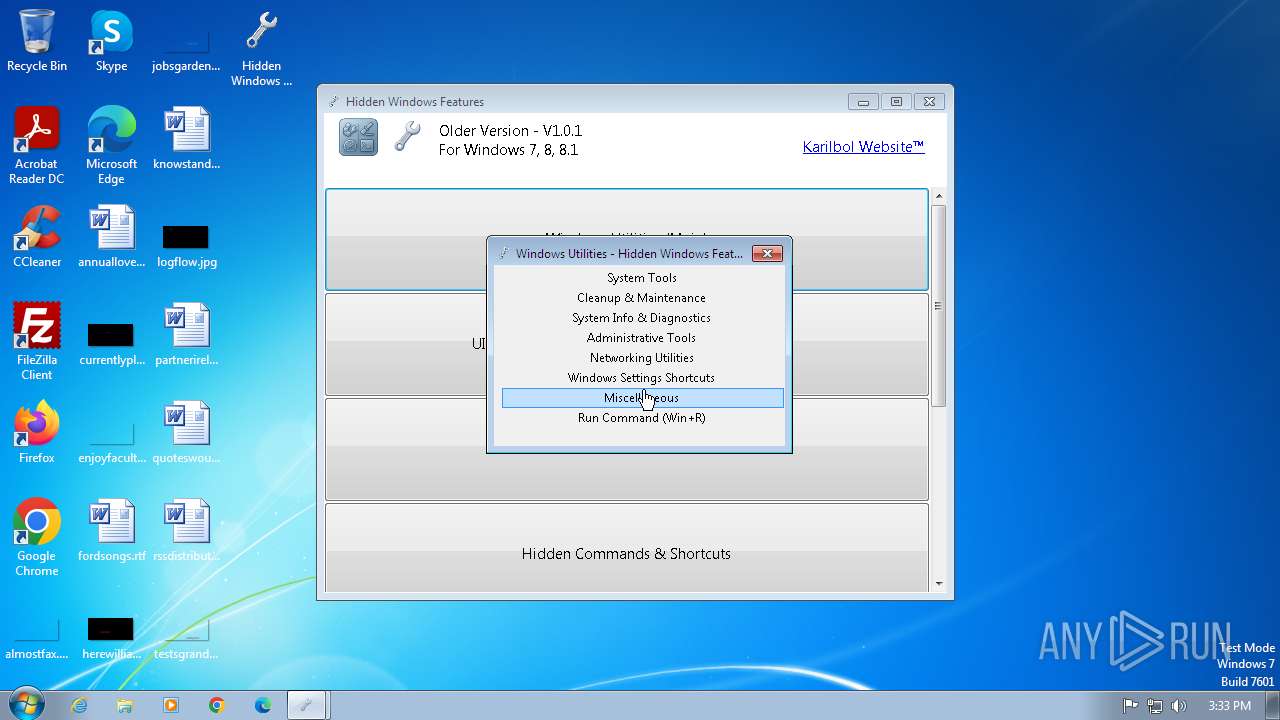
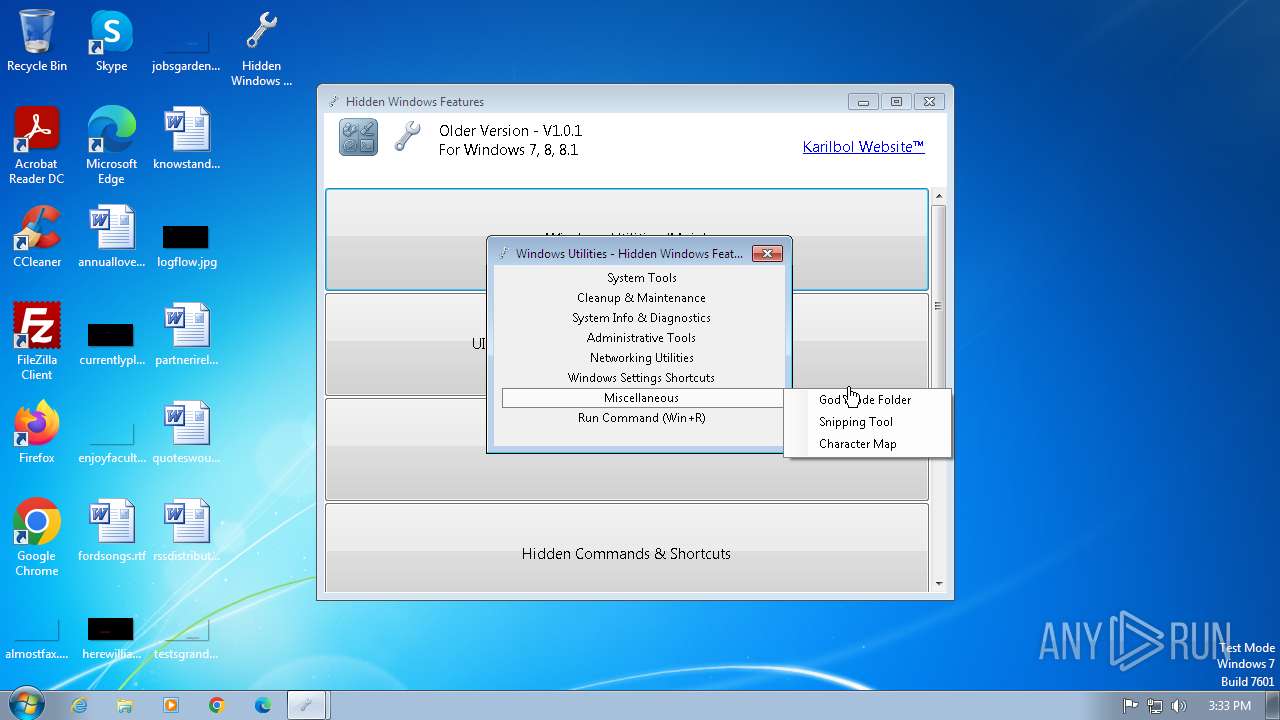
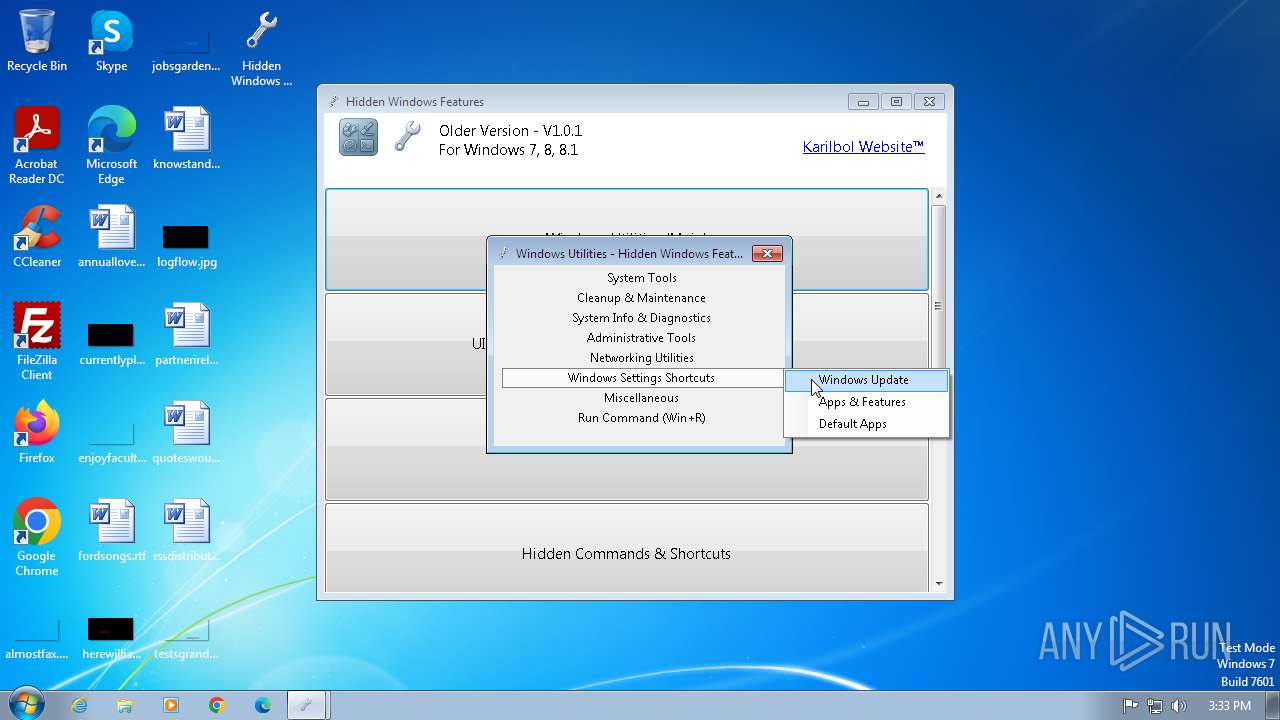
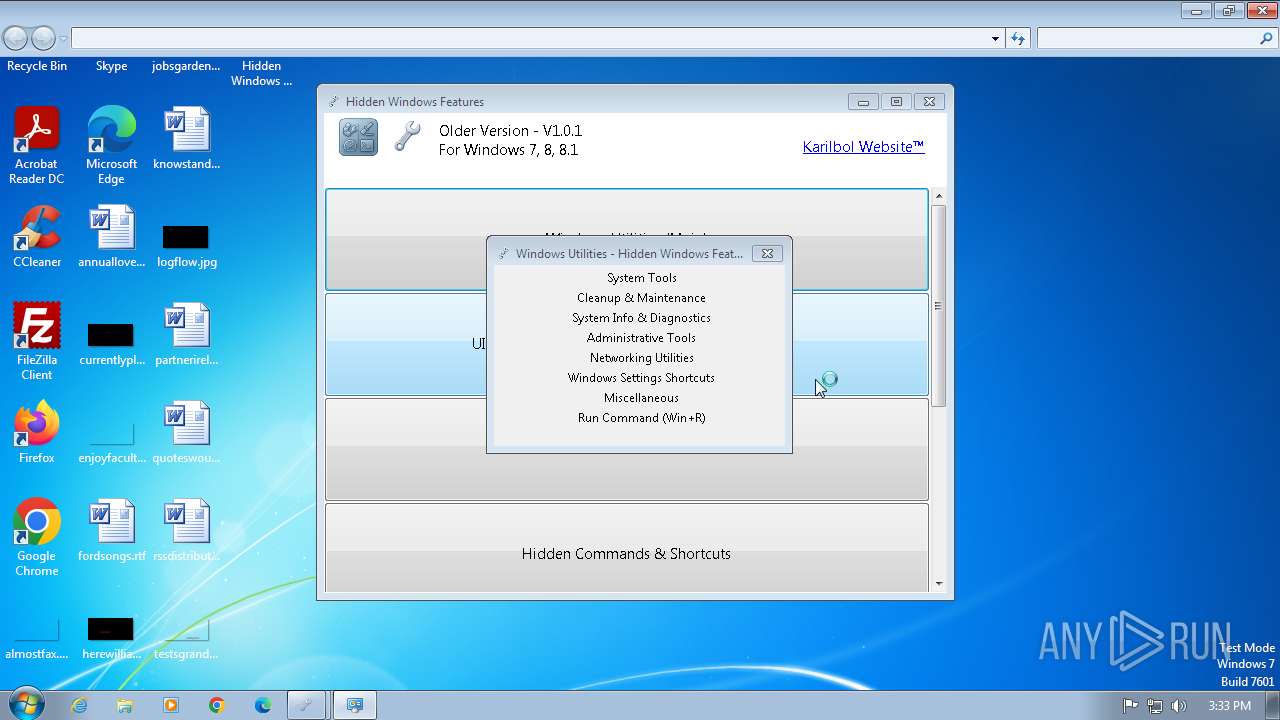
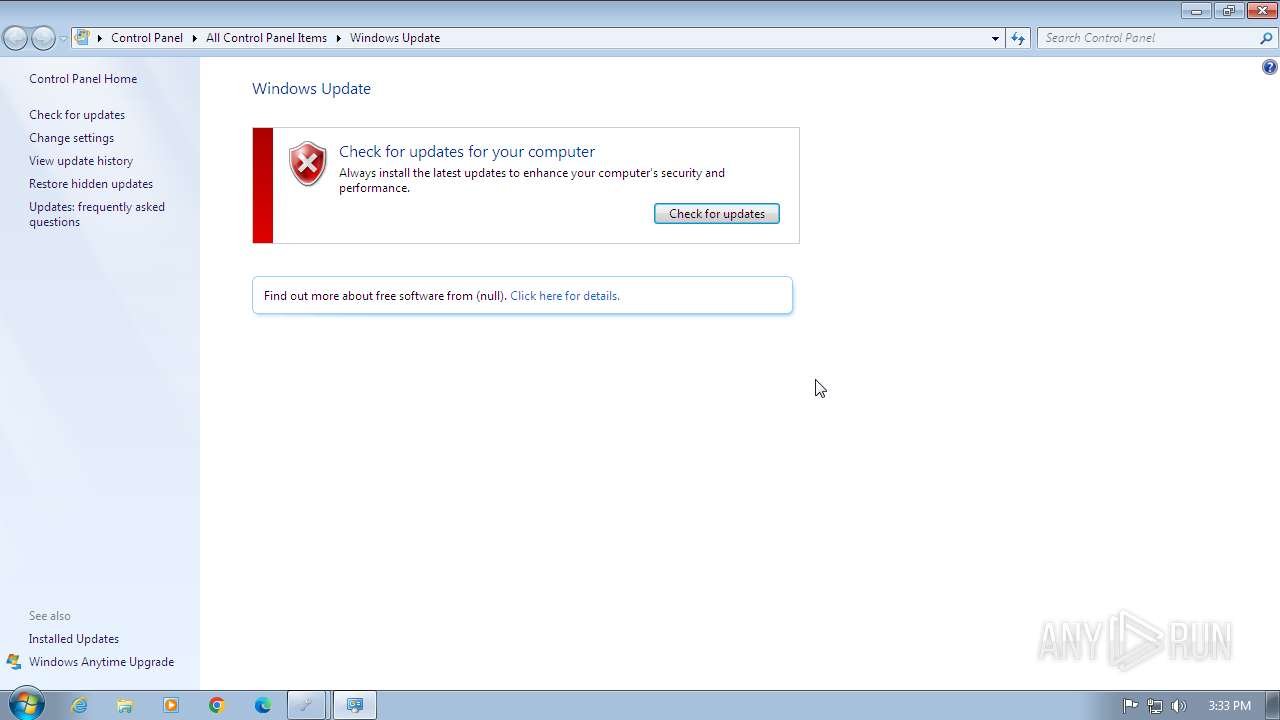
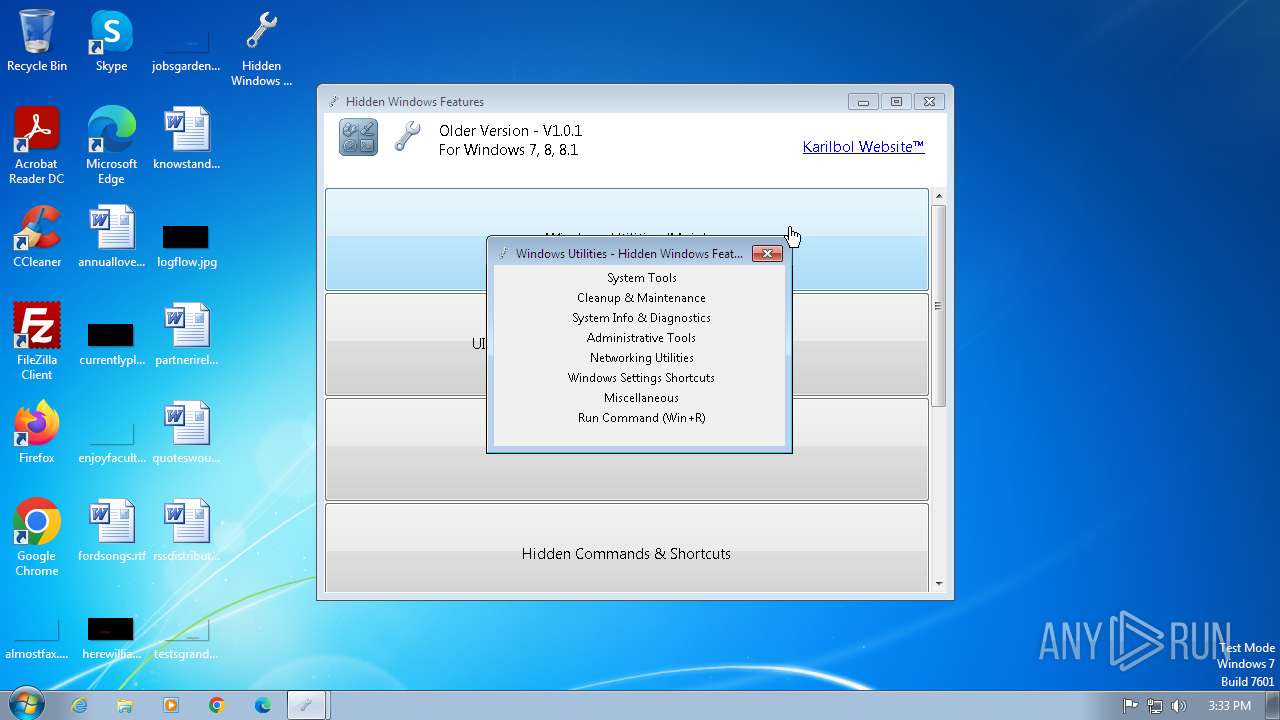
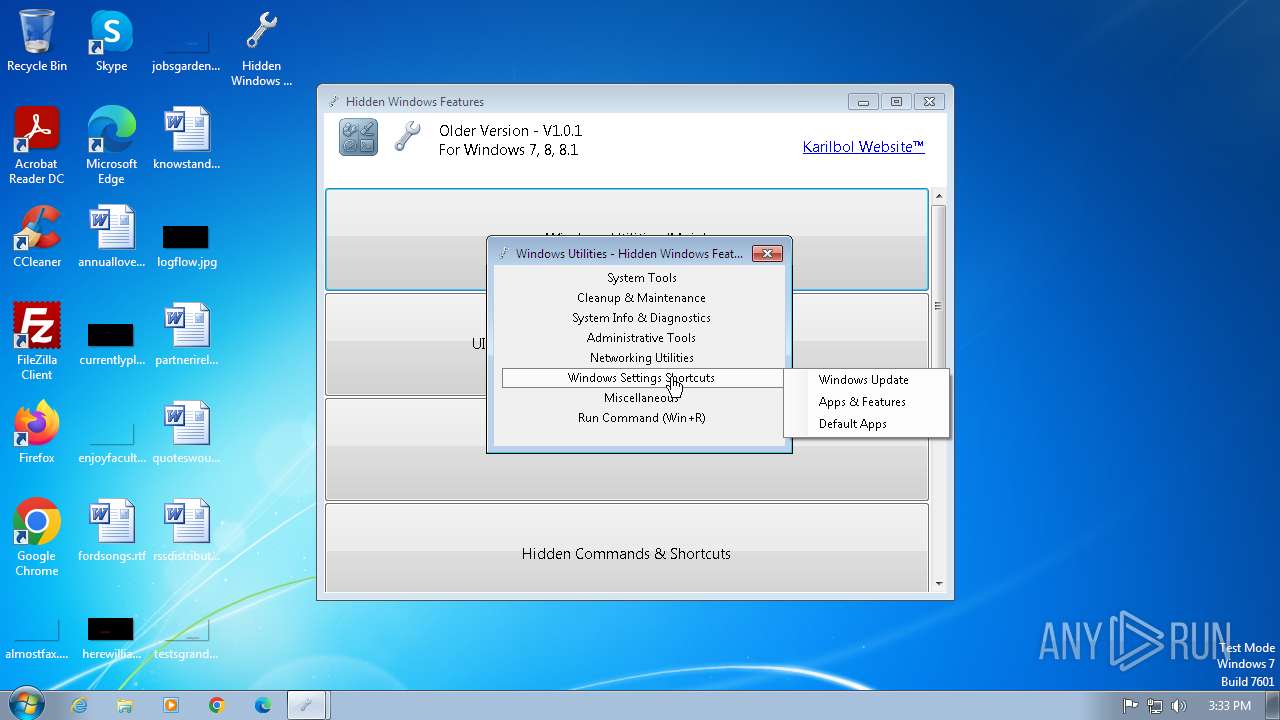
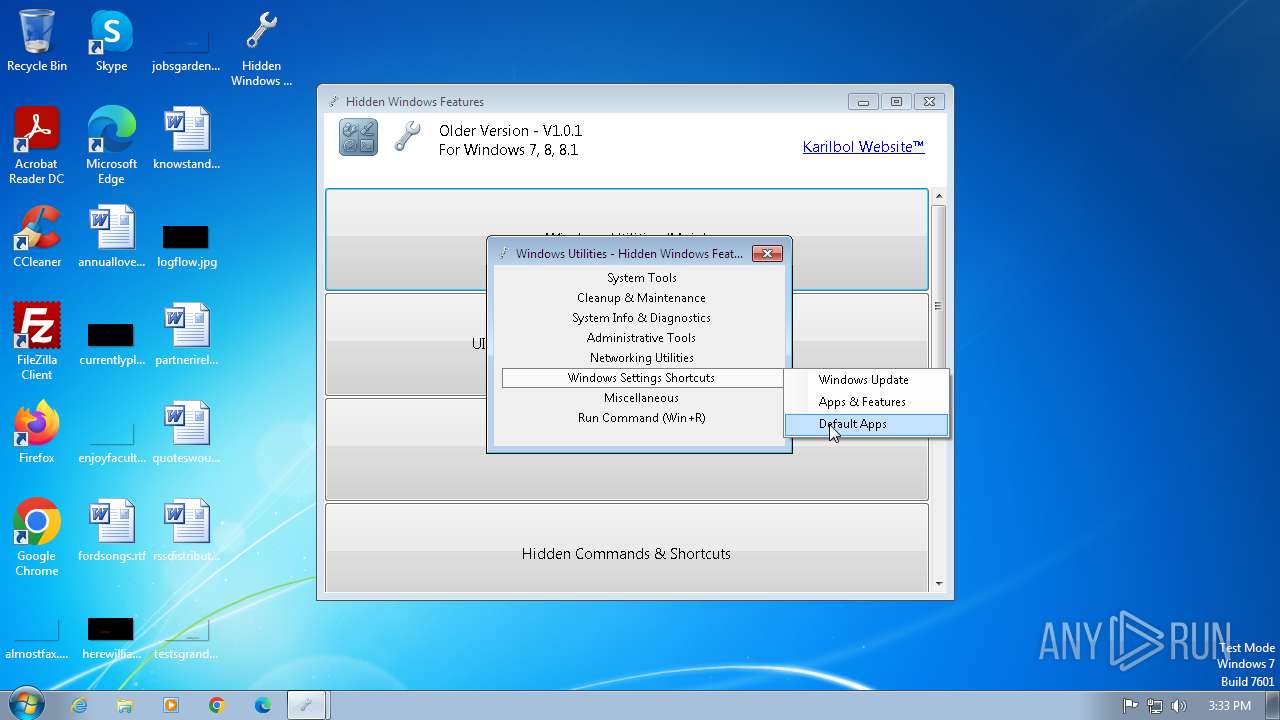
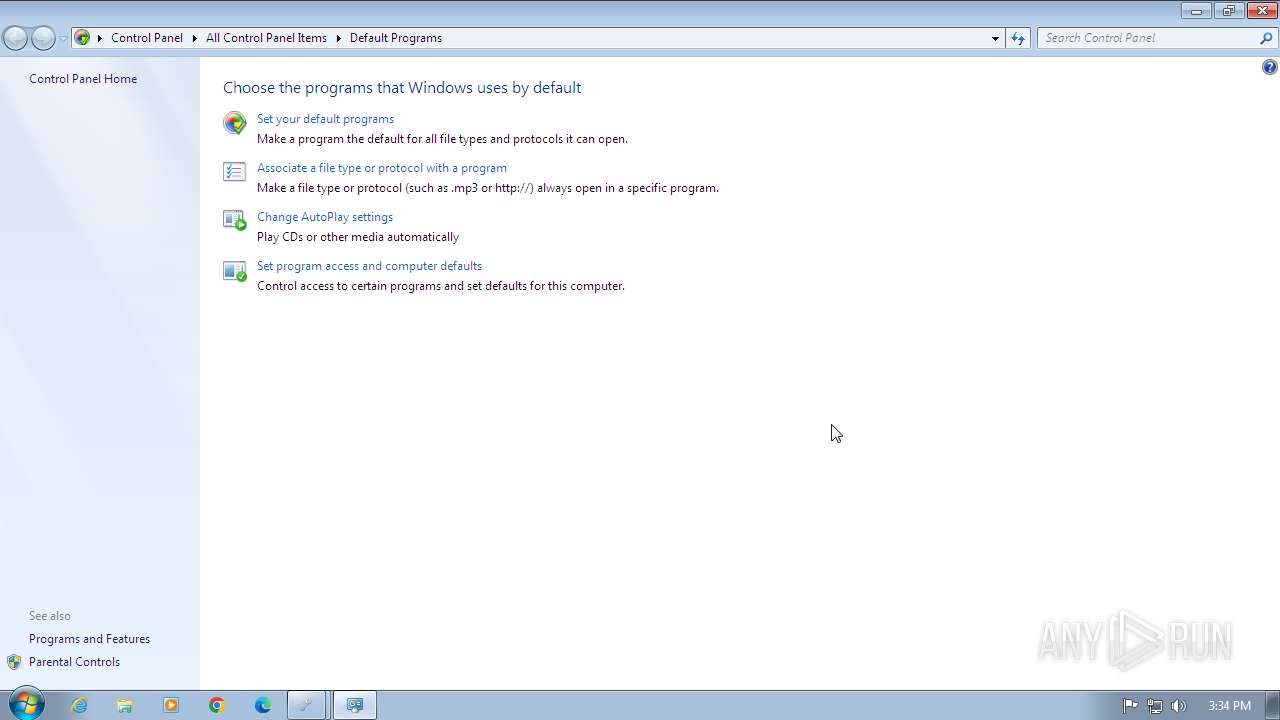
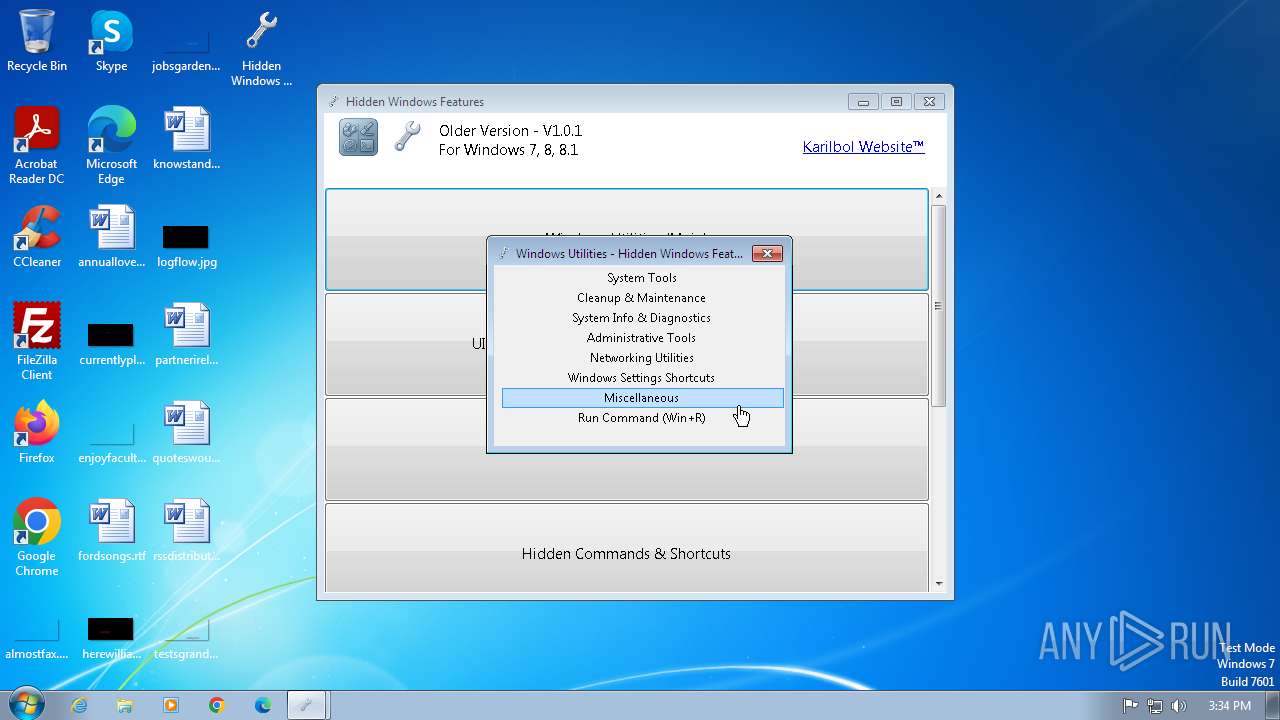
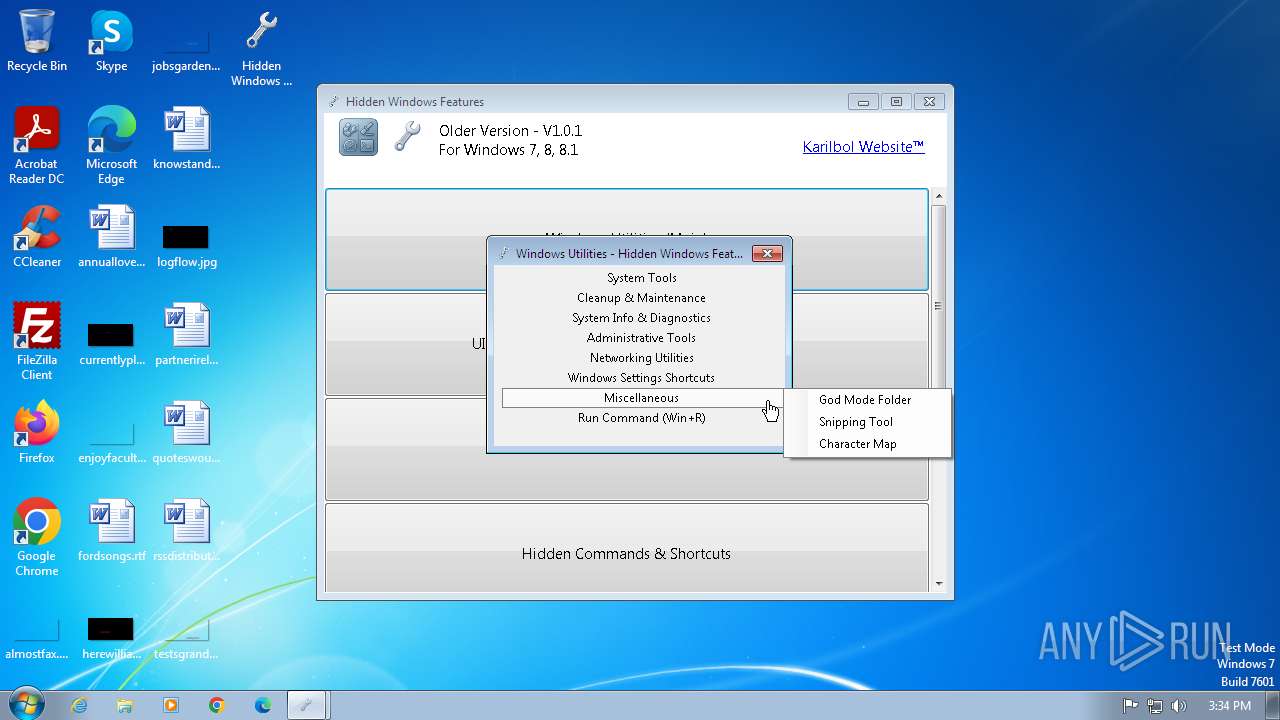
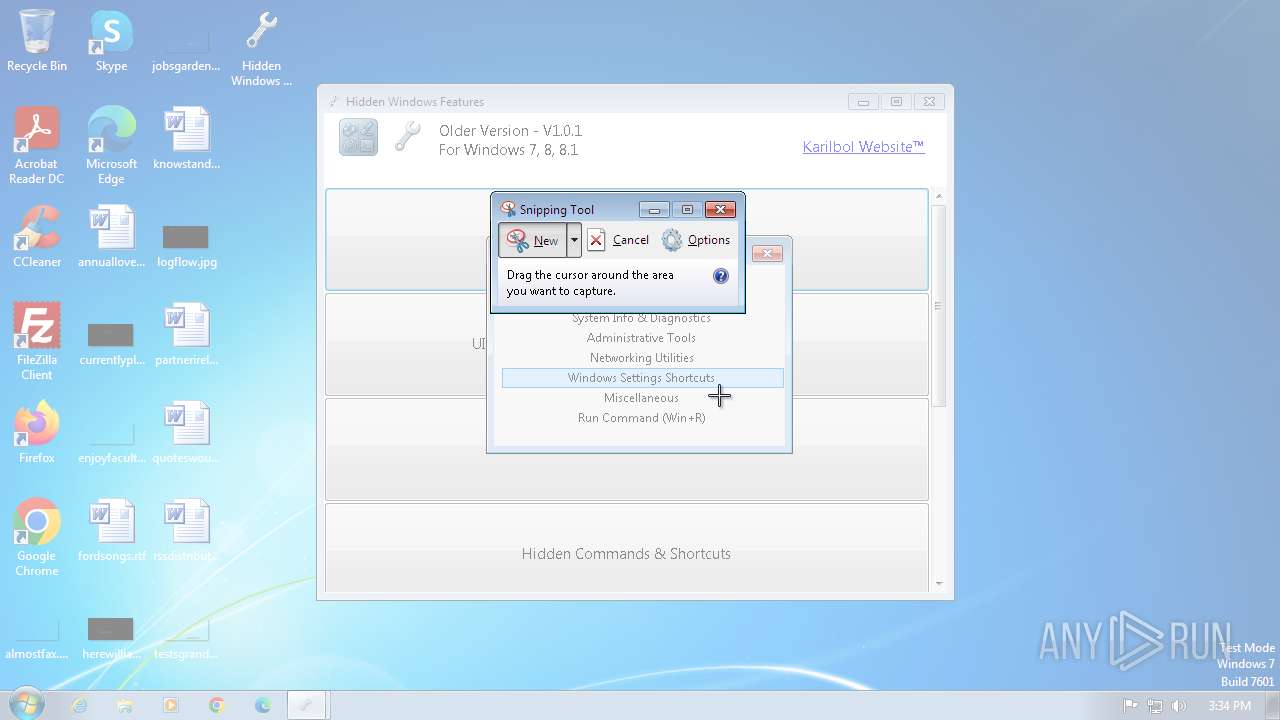
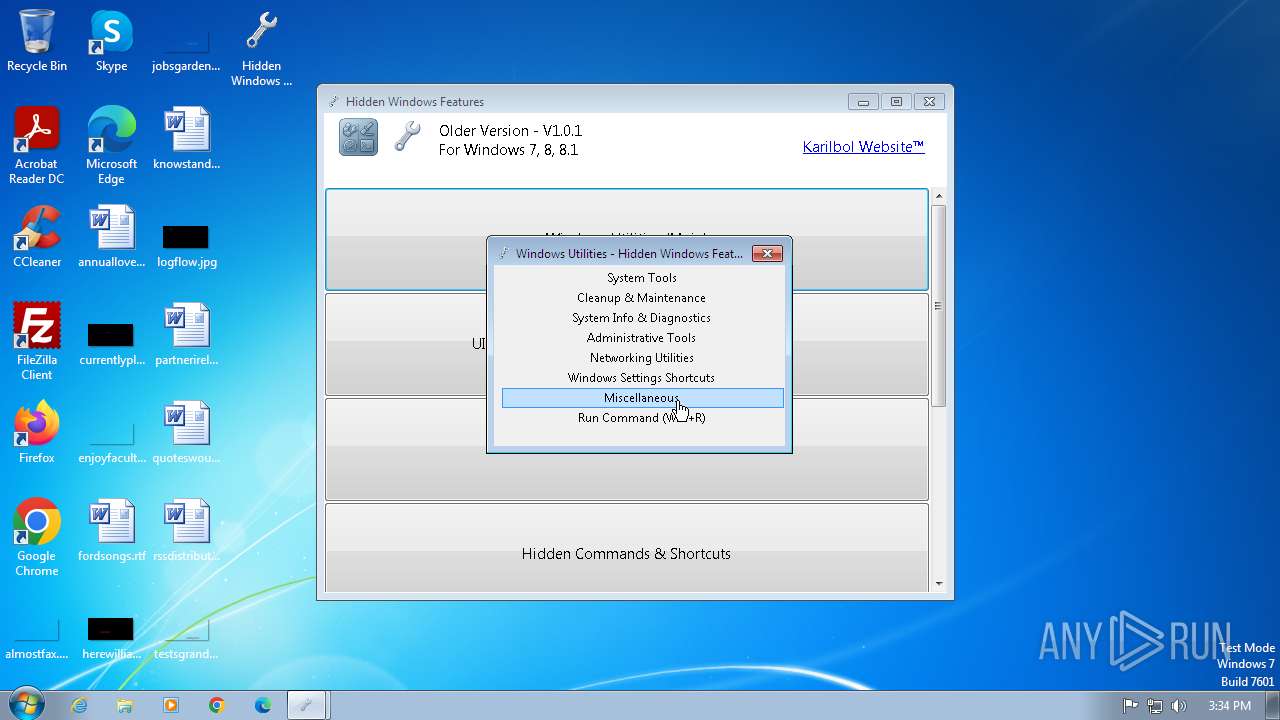
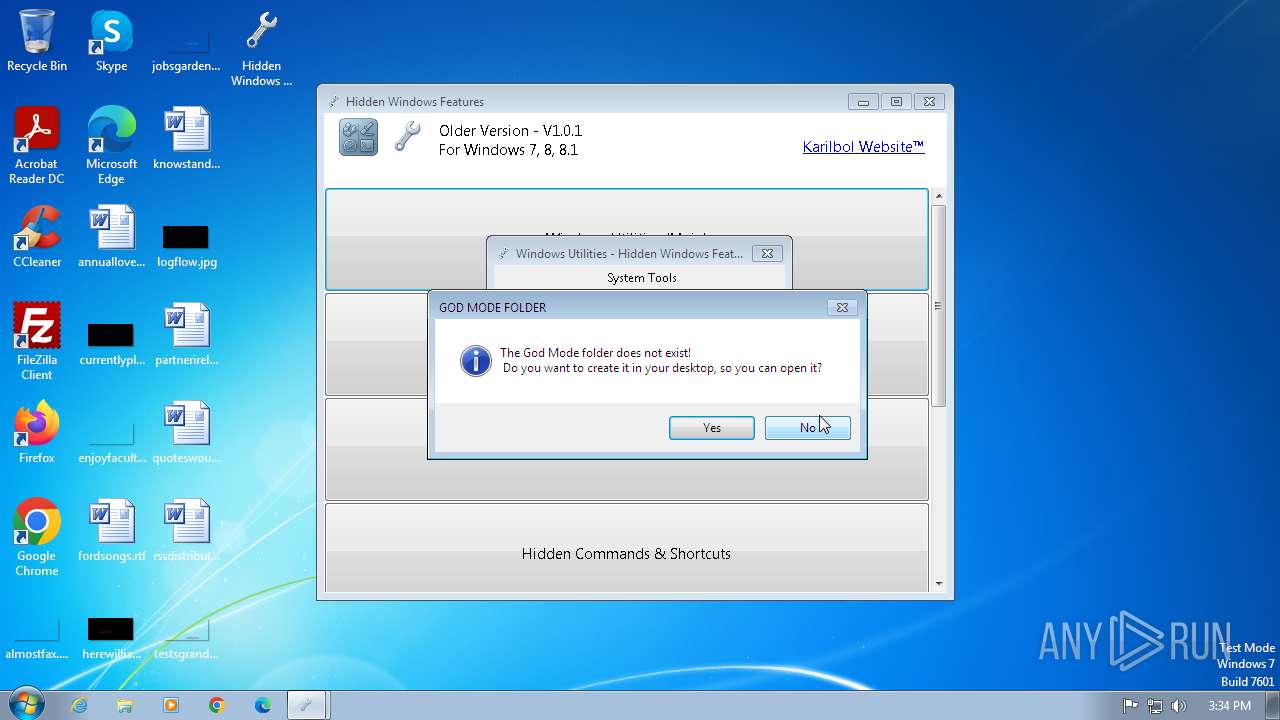
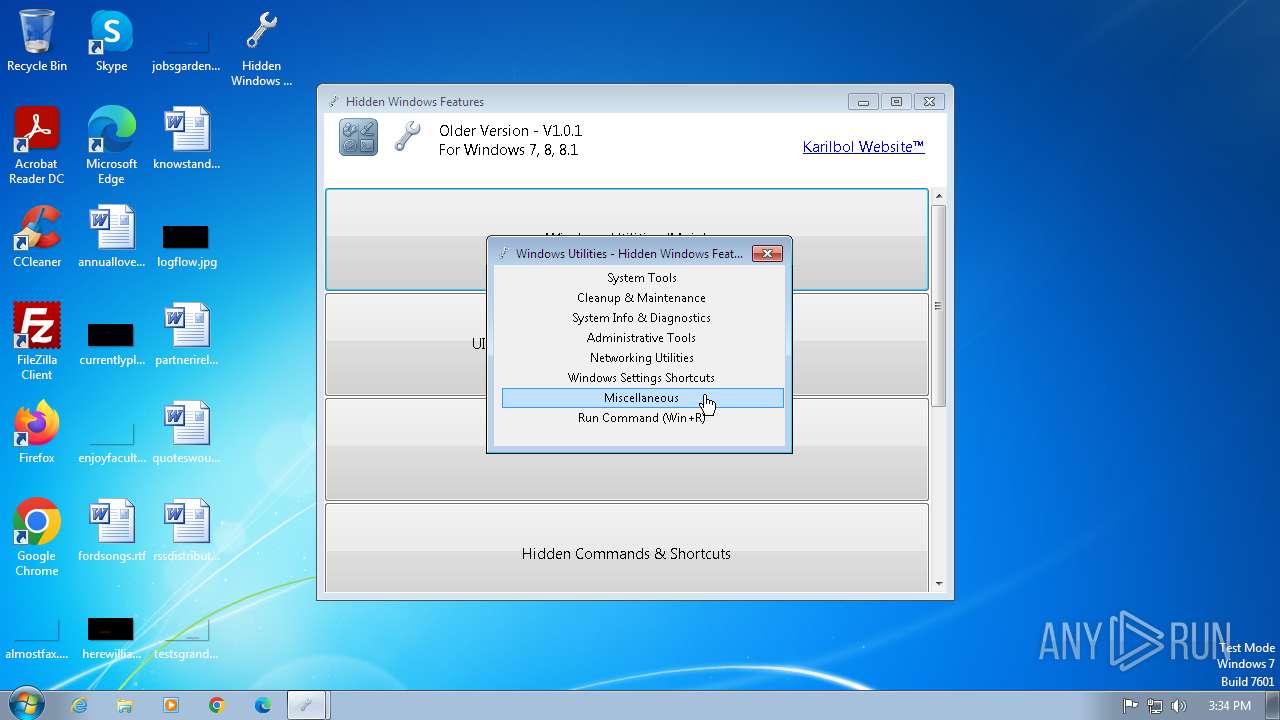
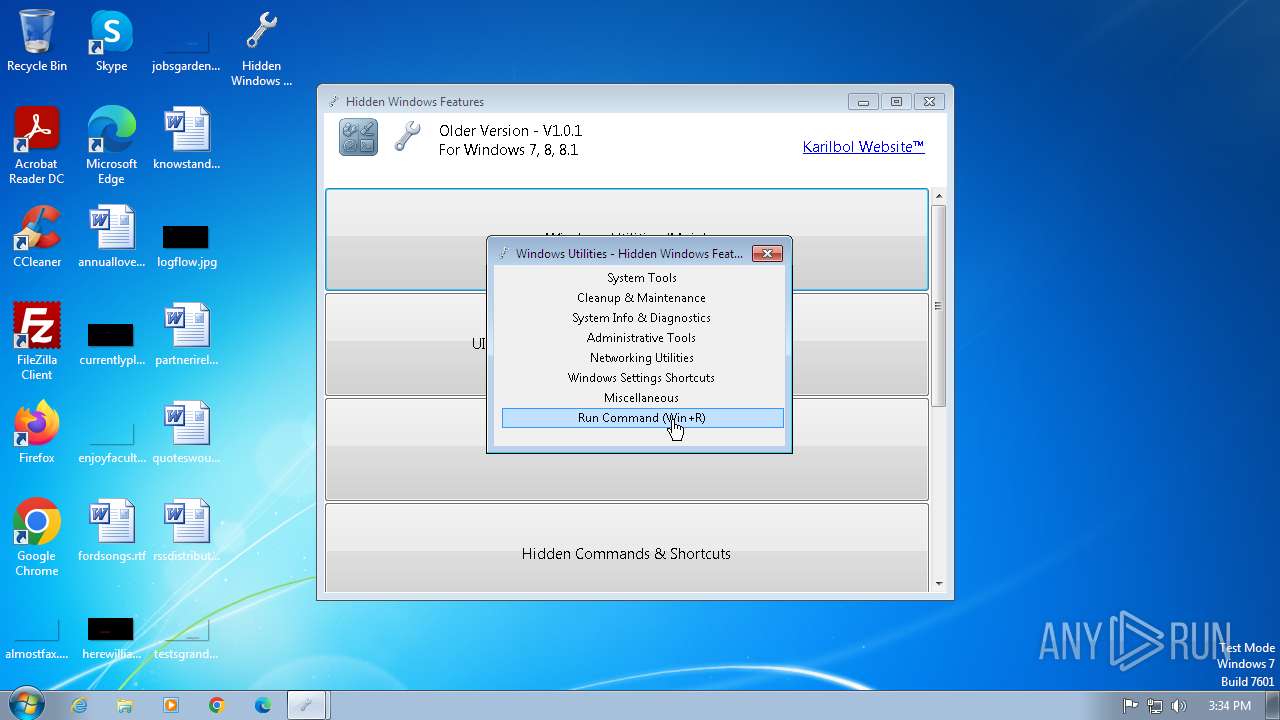
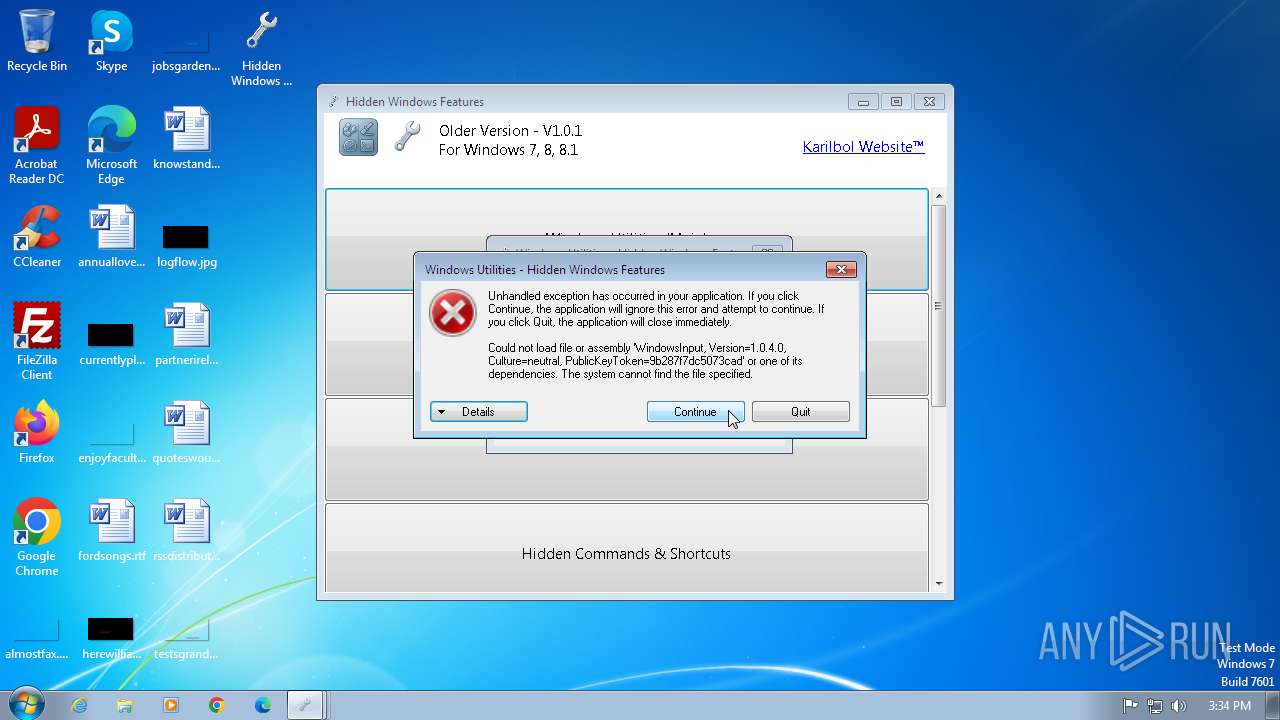
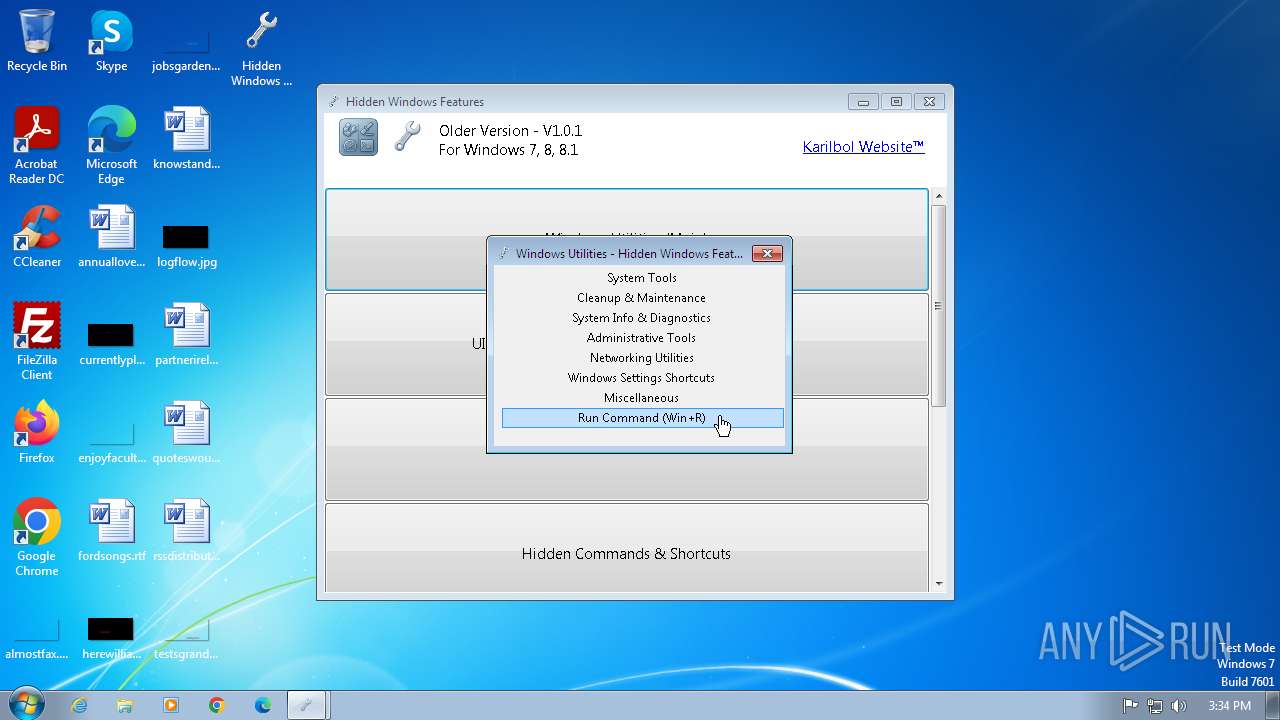
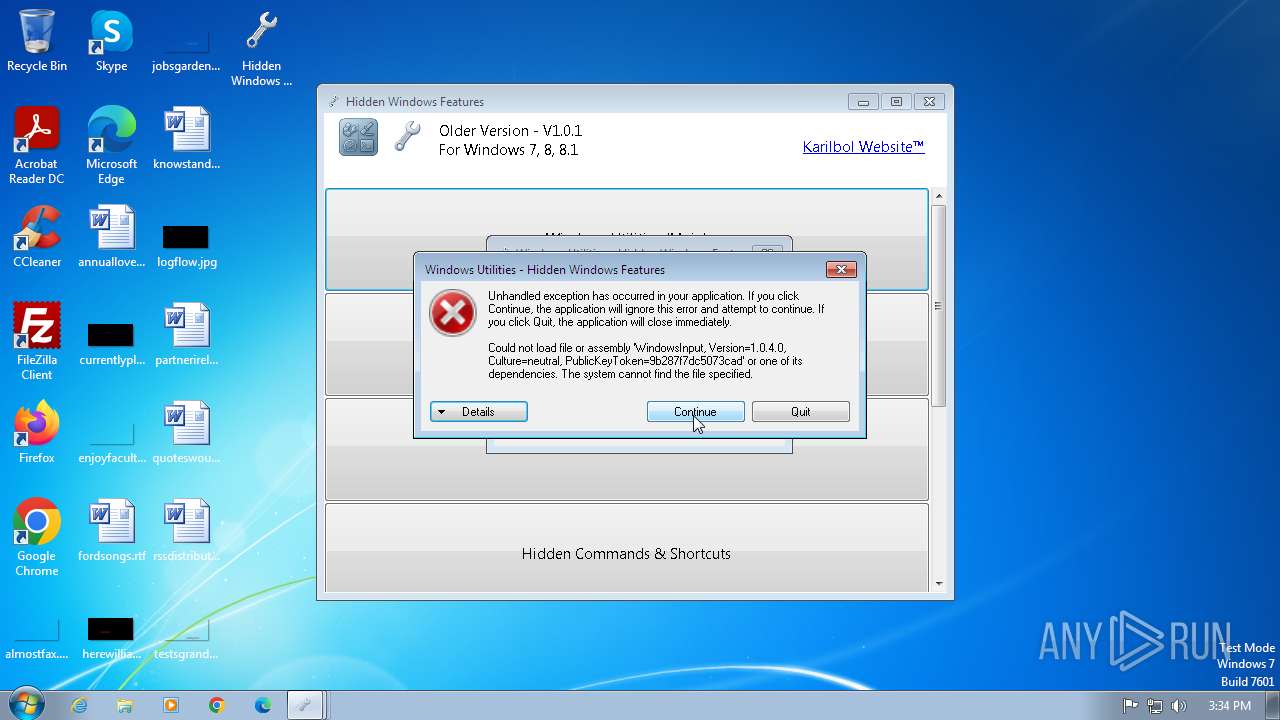
| File name: | Hidden Windows Features.exe |
| Full analysis: | https://app.any.run/tasks/525ab72f-2e16-4b41-9366-d6e3d83fcb00 |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2025, 14:31:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 044D085A58108446EA380FA698F98C69 |
| SHA1: | 64AB7B8D299F80AAA83FE436E0DF0E847C5CAFC7 |
| SHA256: | 299B5E8F8DB18A1B95AB8AF6949D9820FE1320ACA3CFBD5CFAF2F439A380AA21 |
| SSDEEP: | 98304:8rArZrRrRrRrRrxib4dO7XTH4r8pcRG/Hb940WkhOQVLv0dIczymU8CNWA89Xmpd:S+EcV |
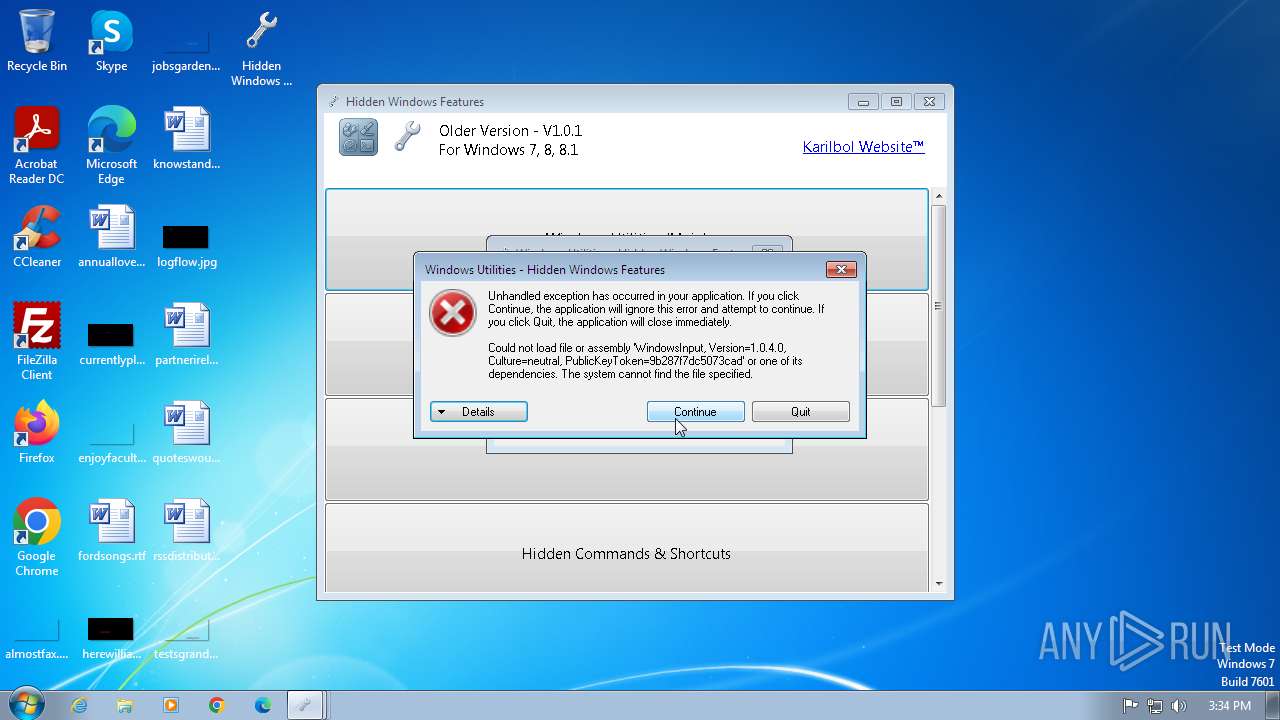
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Explorer settings
- Hidden Windows Features.exe (PID: 2692)
- mmc.exe (PID: 3112)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 3112)
Reads the Internet Settings
- resmon.exe (PID: 2464)
- mmc.exe (PID: 3112)
- Hidden Windows Features.exe (PID: 2692)
- cleanmgr.exe (PID: 4072)
- control.exe (PID: 2592)
Reads security settings of Internet Explorer
- Hidden Windows Features.exe (PID: 2692)
Executes as Windows Service
- wbengine.exe (PID: 3084)
- VSSVC.exe (PID: 3372)
- vds.exe (PID: 1332)
Reads settings of System Certificates
- dxdiag.exe (PID: 3556)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 2592)
INFO
Reads the computer name
- Hidden Windows Features.exe (PID: 2692)
Checks supported languages
- Hidden Windows Features.exe (PID: 2692)
Detects AutoHotkey samples (YARA)
- Hidden Windows Features.exe (PID: 2692)
Reads the machine GUID from the registry
- Hidden Windows Features.exe (PID: 2692)
Creates files or folders in the user directory
- perfmon.exe (PID: 3224)
- mmc.exe (PID: 3112)
- cleanmgr.exe (PID: 4072)
Reads the time zone
- perfmon.exe (PID: 3224)
Reads security settings of Internet Explorer
- resmon.exe (PID: 2464)
- mmc.exe (PID: 3112)
- dxdiag.exe (PID: 3556)
- control.exe (PID: 2592)
Reads Microsoft Office registry keys
- cleanmgr.exe (PID: 4072)
- mmc.exe (PID: 3112)
Checks proxy server information
- mmc.exe (PID: 3112)
Create files in a temporary directory
- cleanmgr.exe (PID: 4072)
Reads the software policy settings
- dxdiag.exe (PID: 3556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2079:01:15 18:54:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 2231808 |
| InitializedDataSize: | 40960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x222d42 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
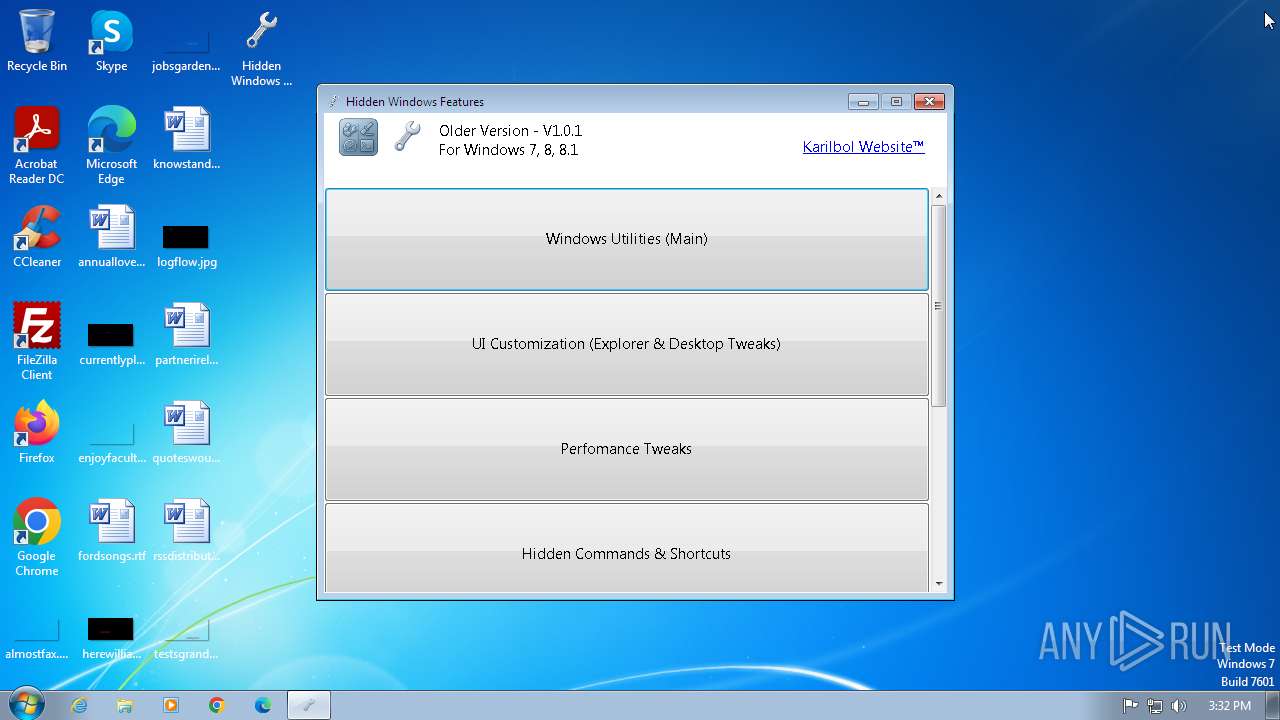
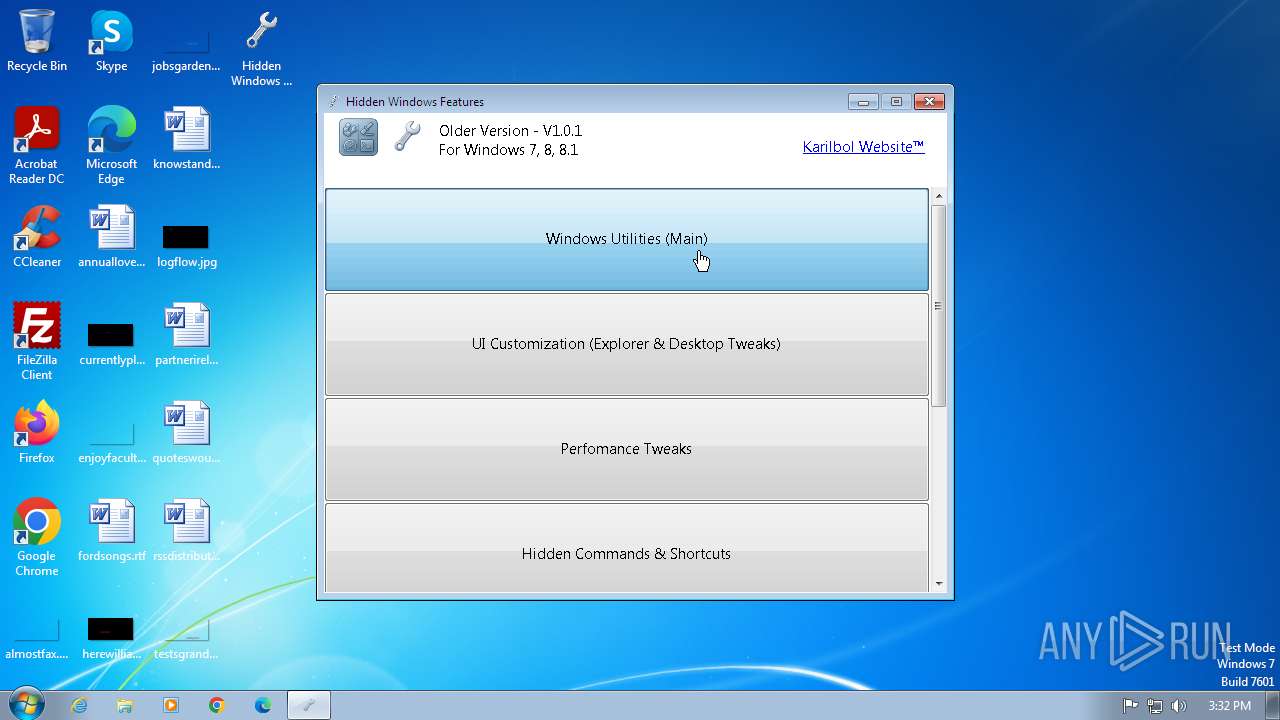
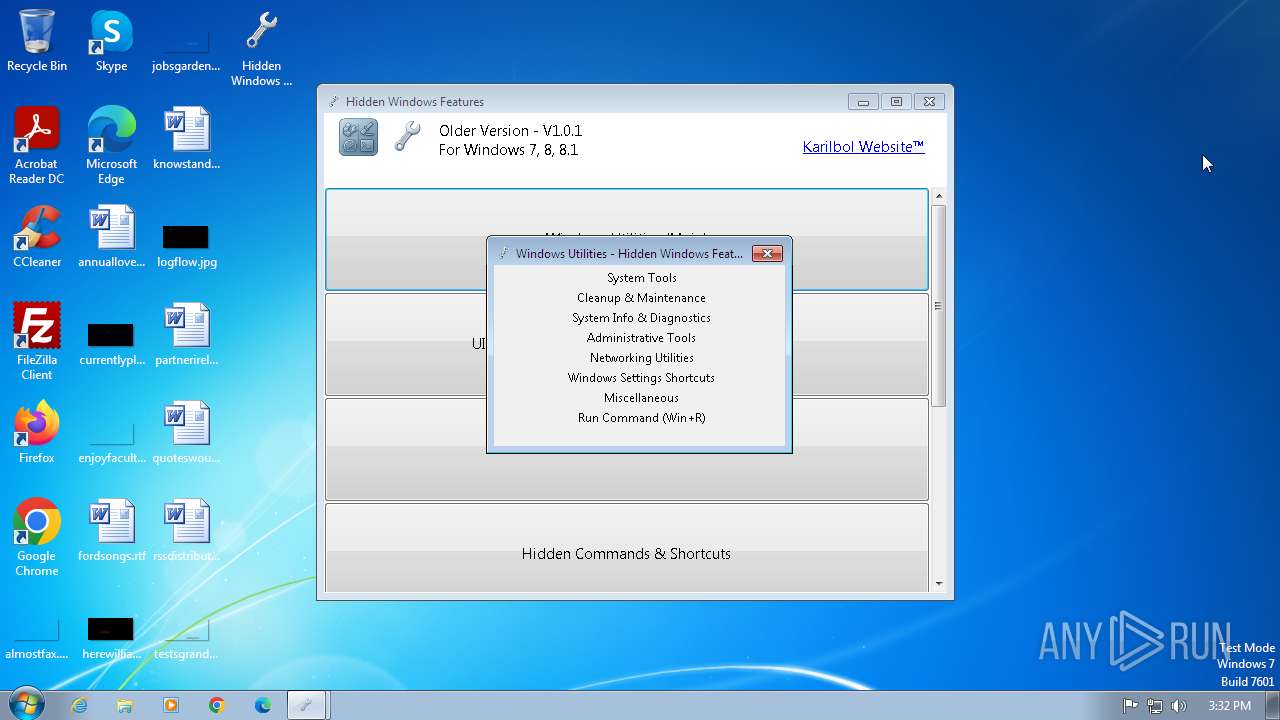
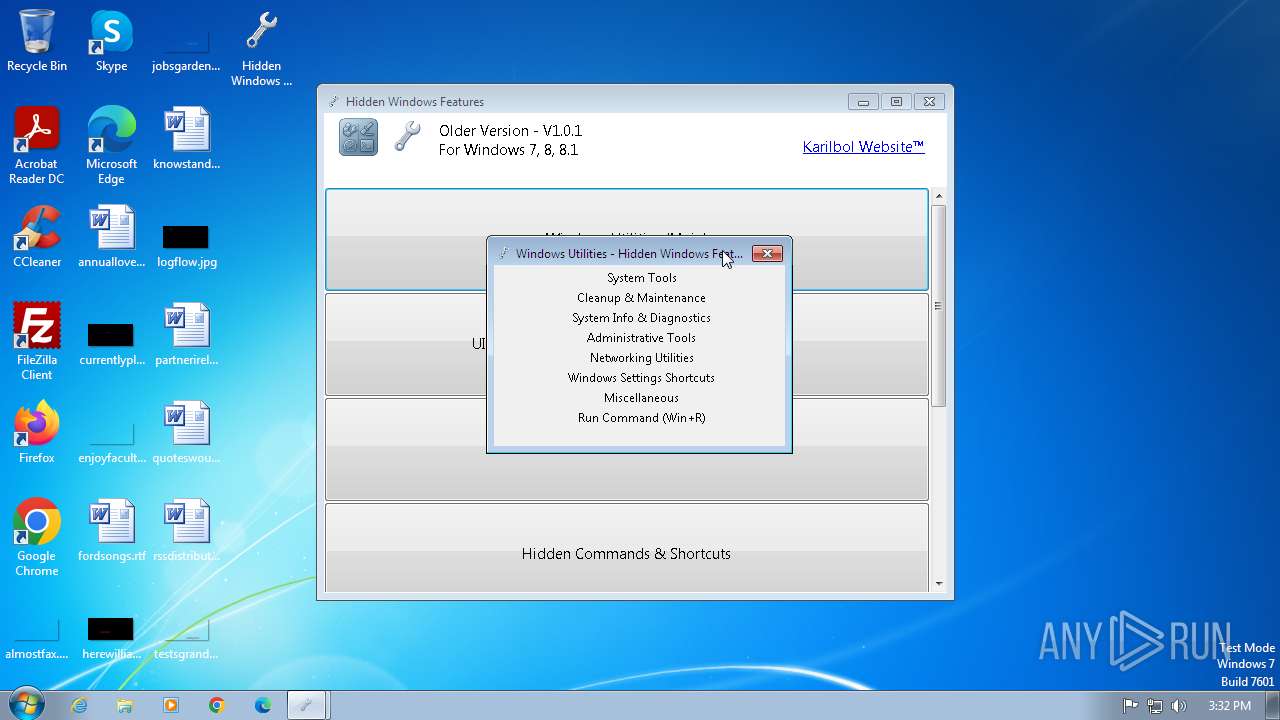
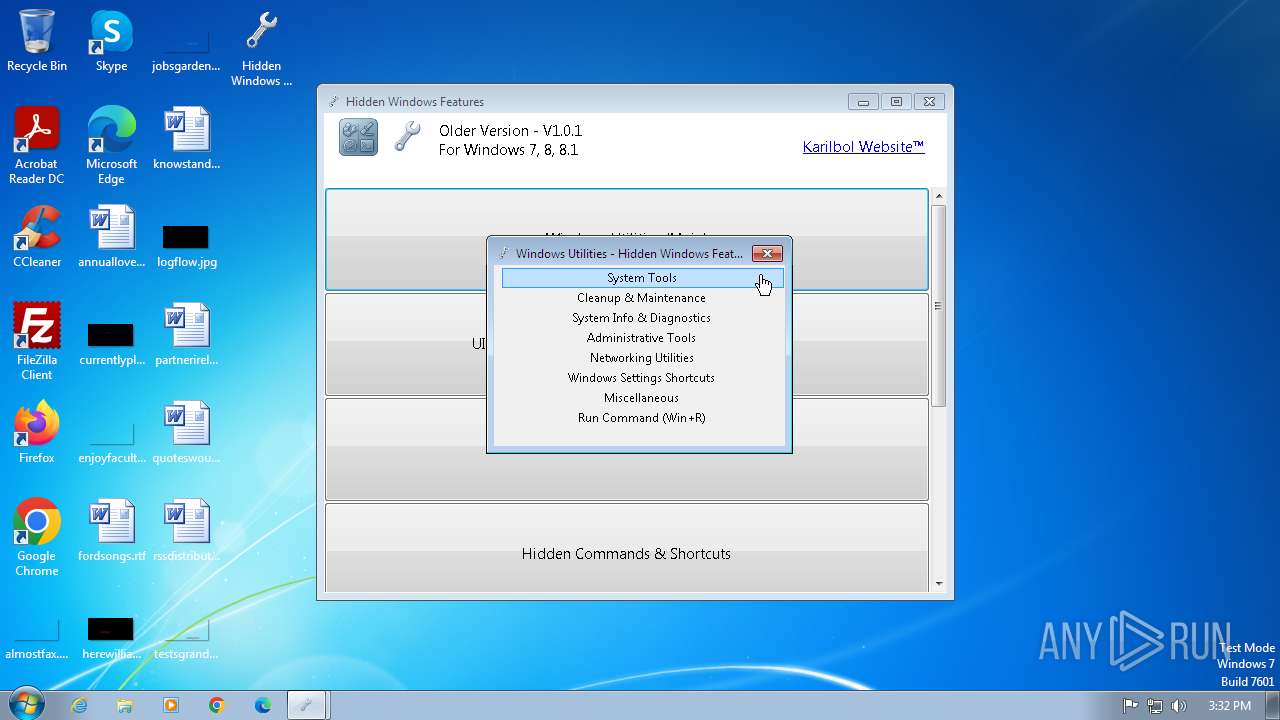
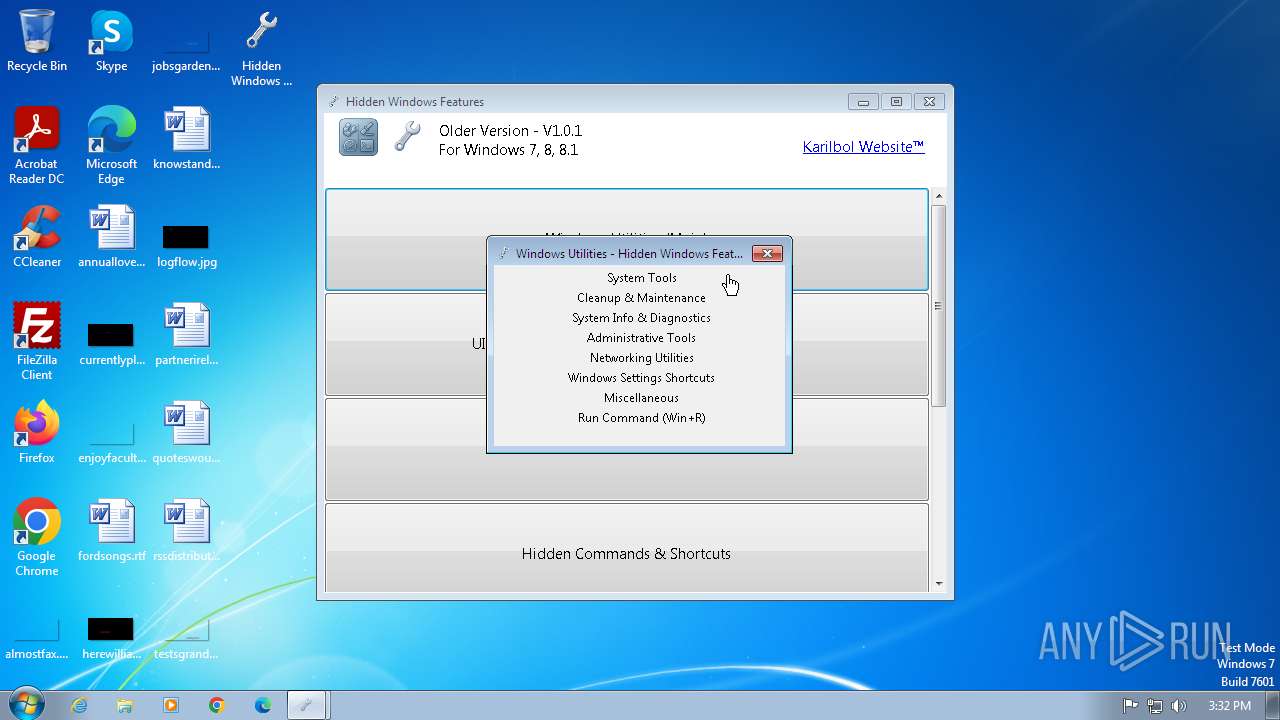
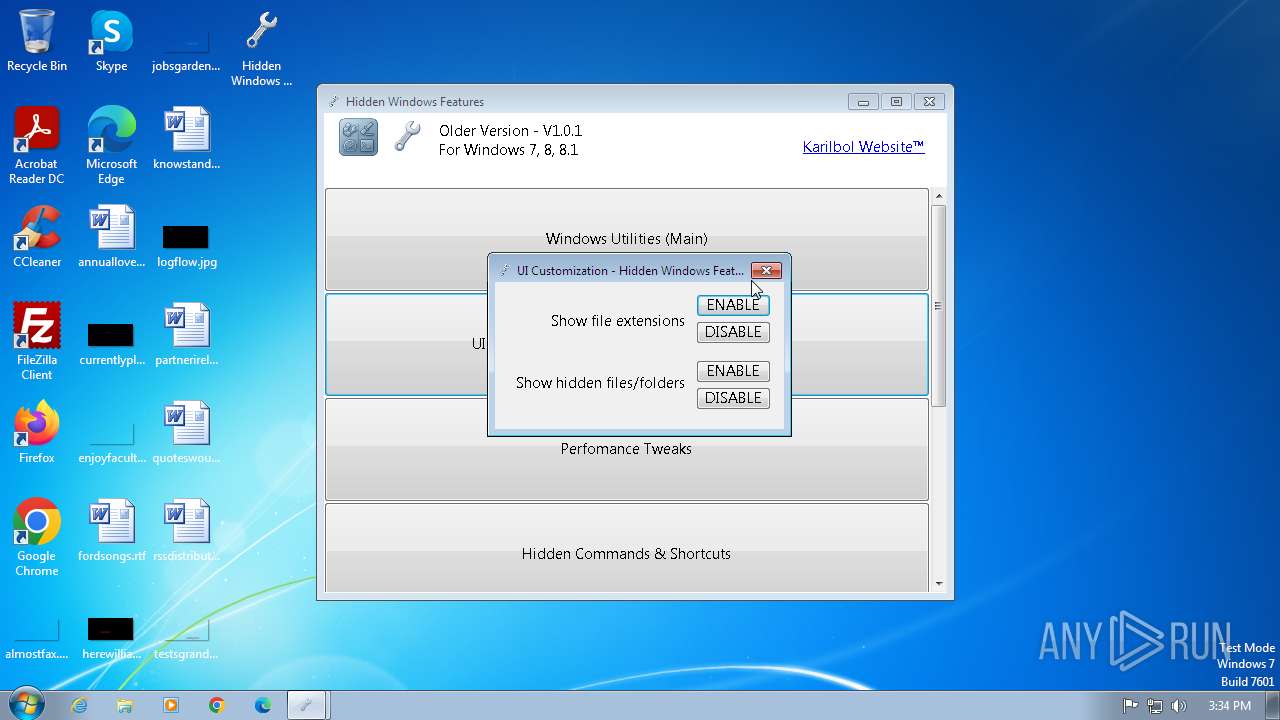
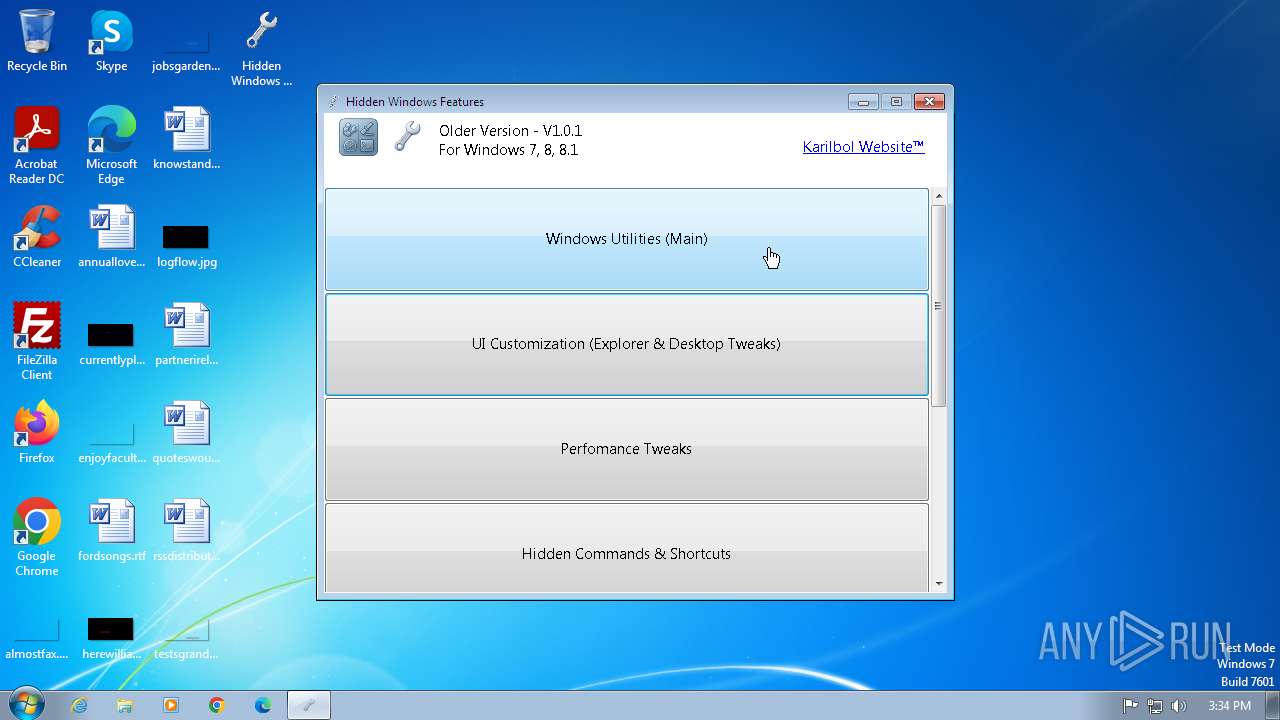
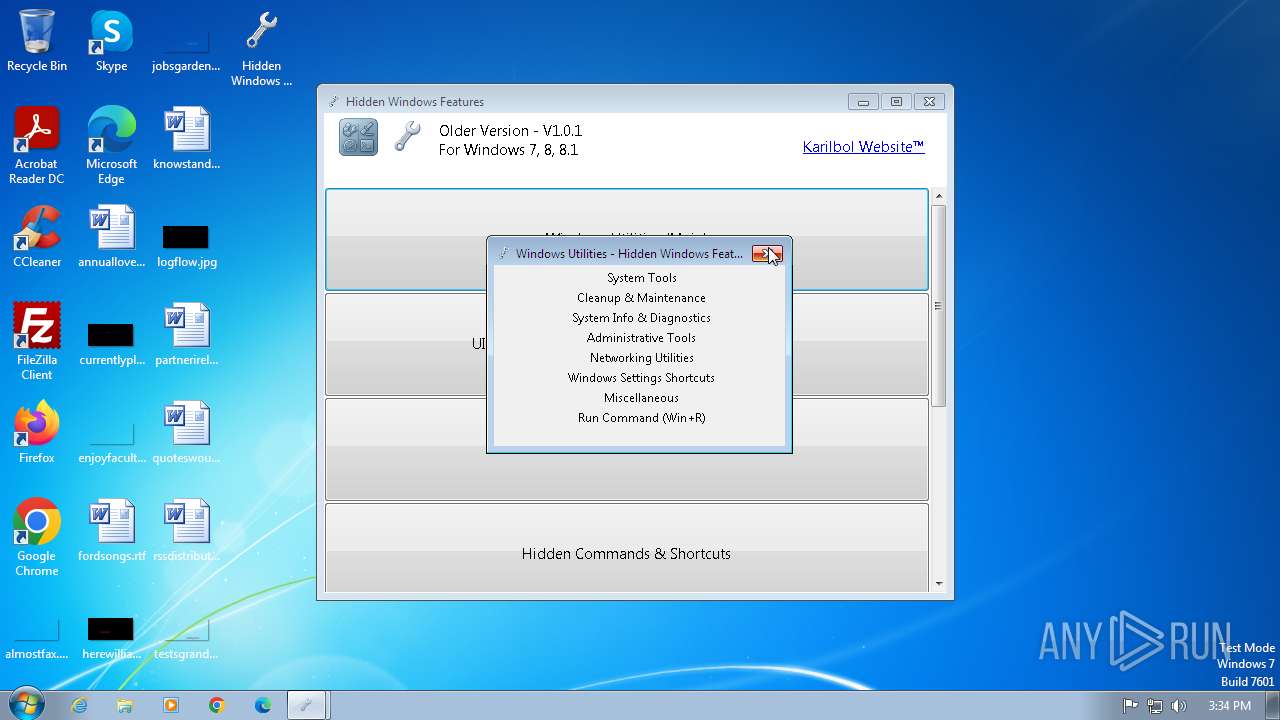
| FileDescription: | Hidden Windows Features |
| FileVersion: | 1.0.0.0 |
| InternalName: | Hidden Windows Features.exe |
| LegalCopyright: | Copyright © 2025 |
| LegalTrademarks: | - |
| OriginalFileName: | Hidden Windows Features.exe |
| ProductName: | Hidden Windows Features |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
76
Monitored processes
25
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Windows\System32\charmap.exe" | C:\Windows\System32\charmap.exe | — | Hidden Windows Features.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Character Map Exit code: 0 Version: 5.2.3668.0 Modules
| |||||||||||||||
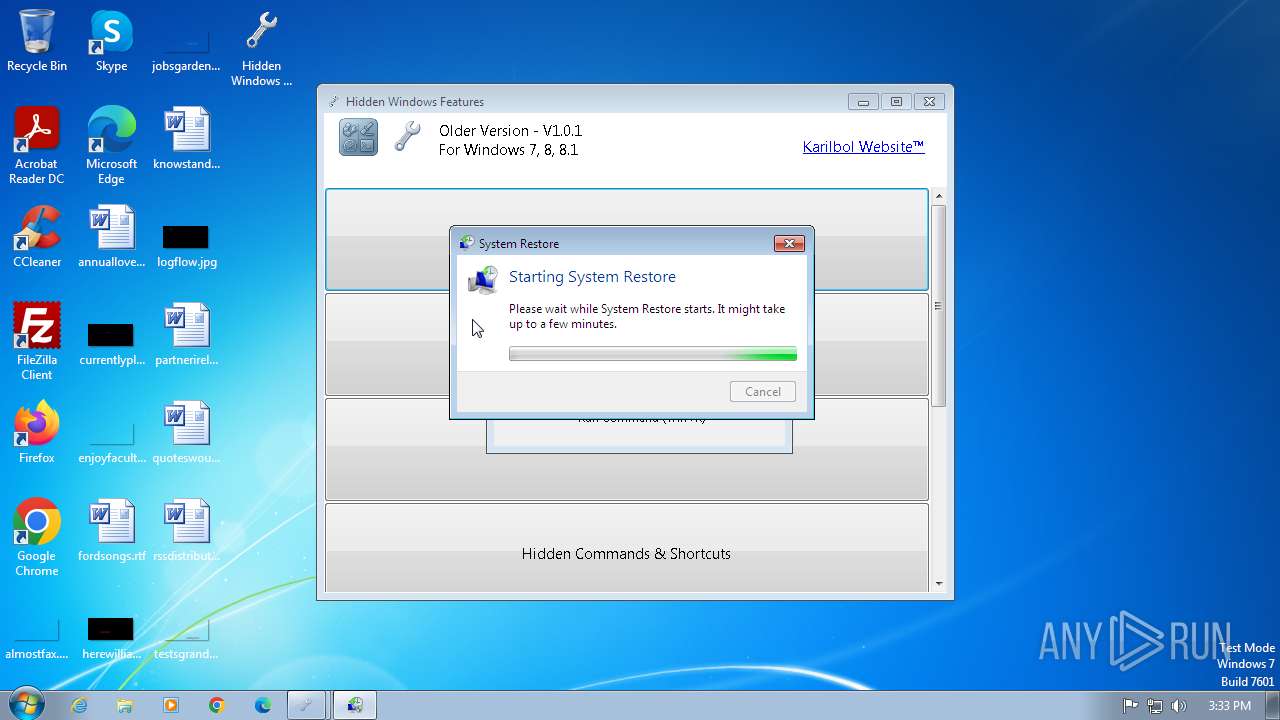
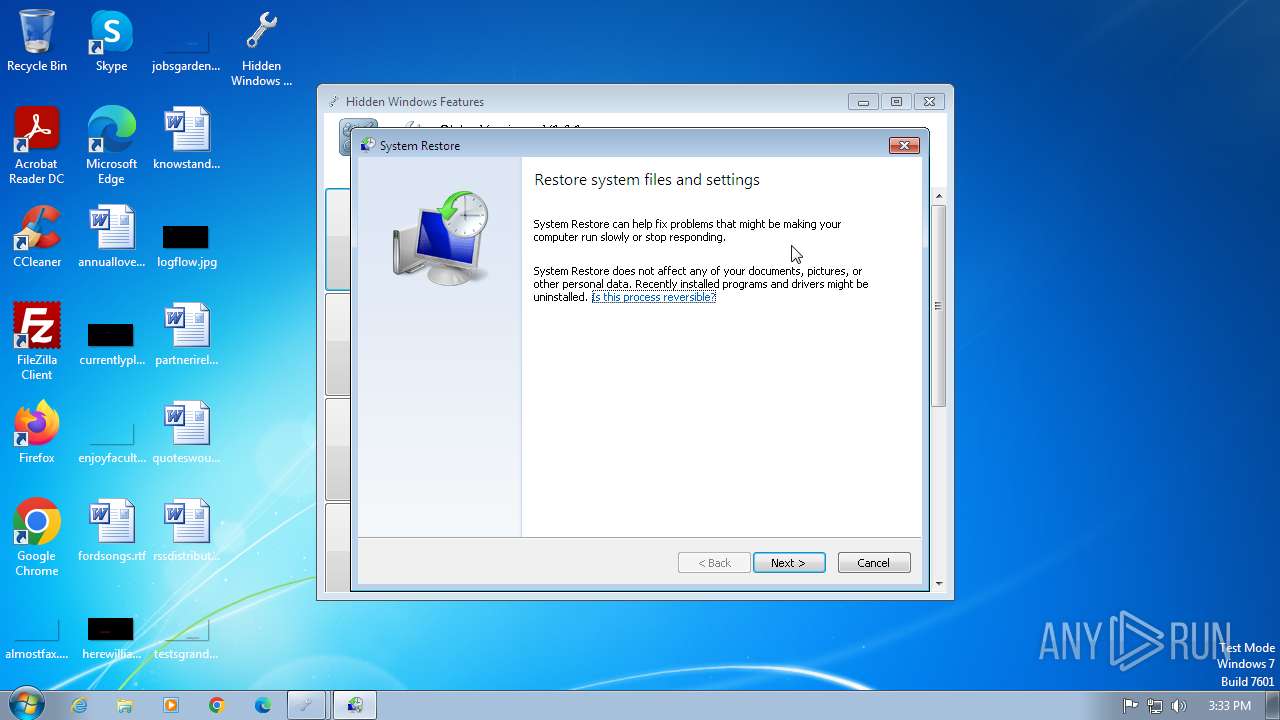
| 1124 | "C:\Windows\System32\rstrui.exe" | C:\Windows\System32\rstrui.exe | — | Hidden Windows Features.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Windows System Restore Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1332 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1400 | "C:\Windows\System32\control.exe" /name Microsoft.DefaultPrograms | C:\Windows\System32\control.exe | — | Hidden Windows Features.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
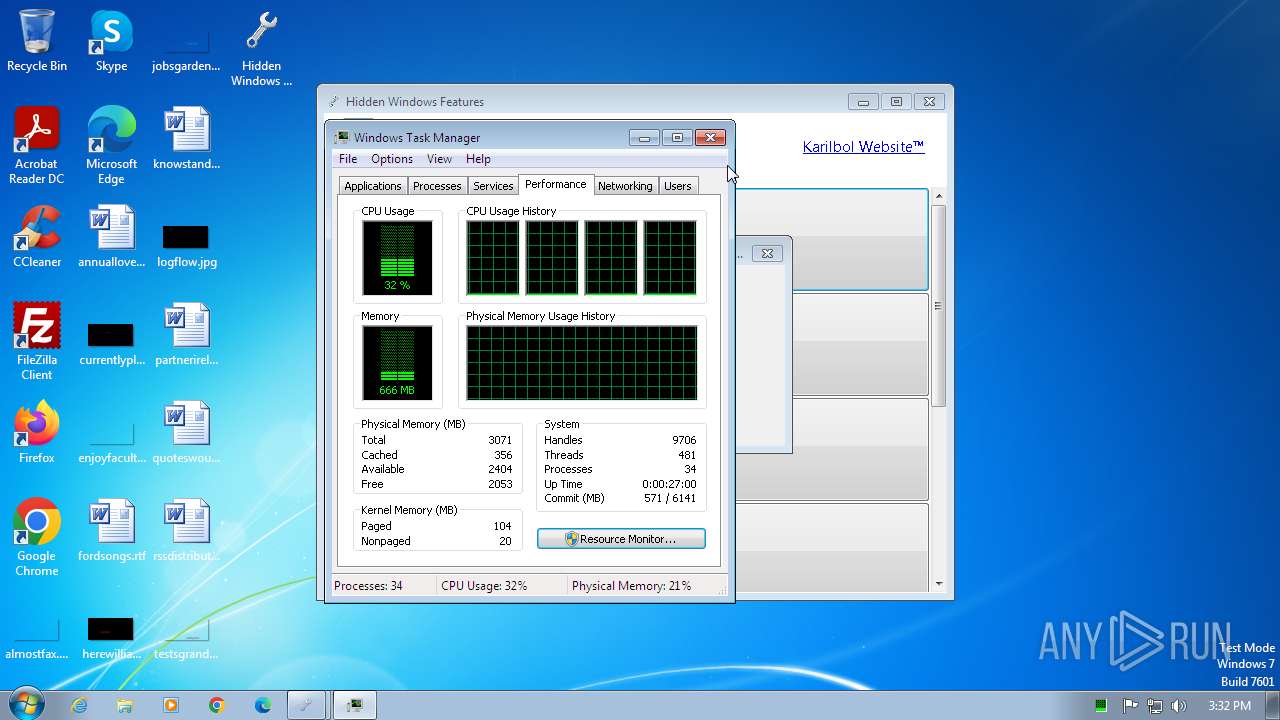
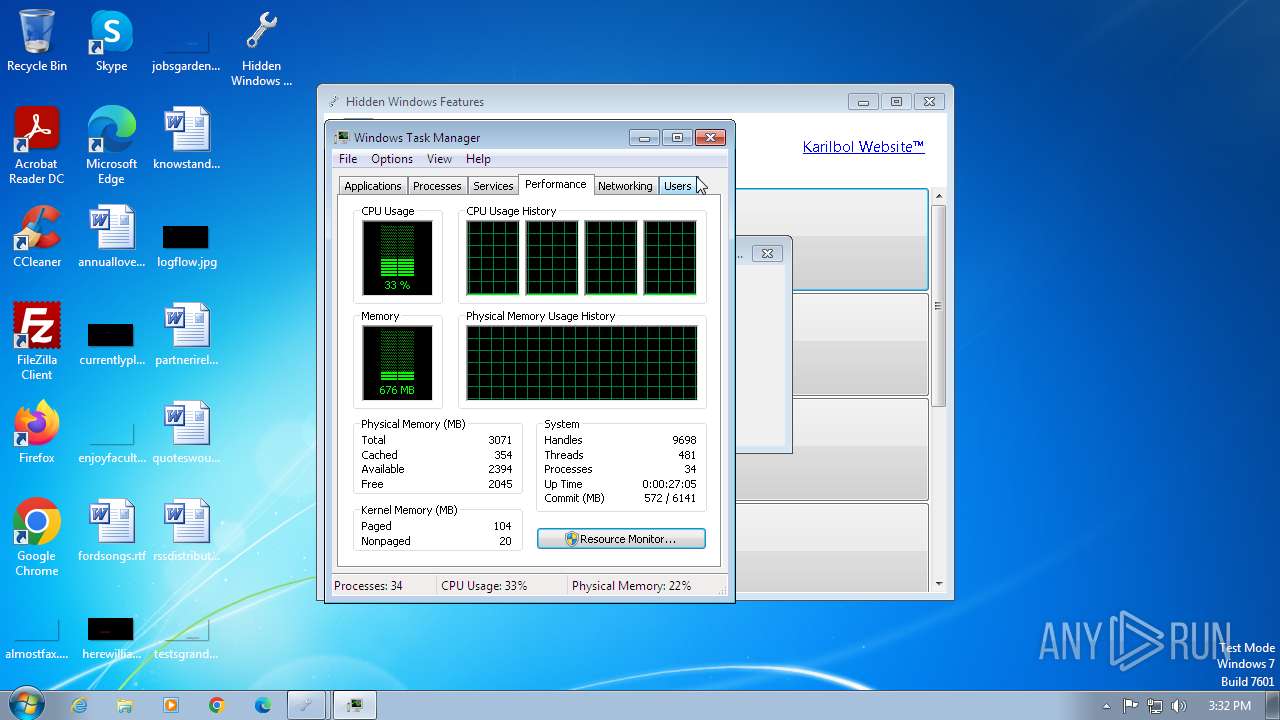
| 1472 | "C:\Windows\System32\taskmgr.exe" | C:\Windows\System32\taskmgr.exe | — | Hidden Windows Features.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
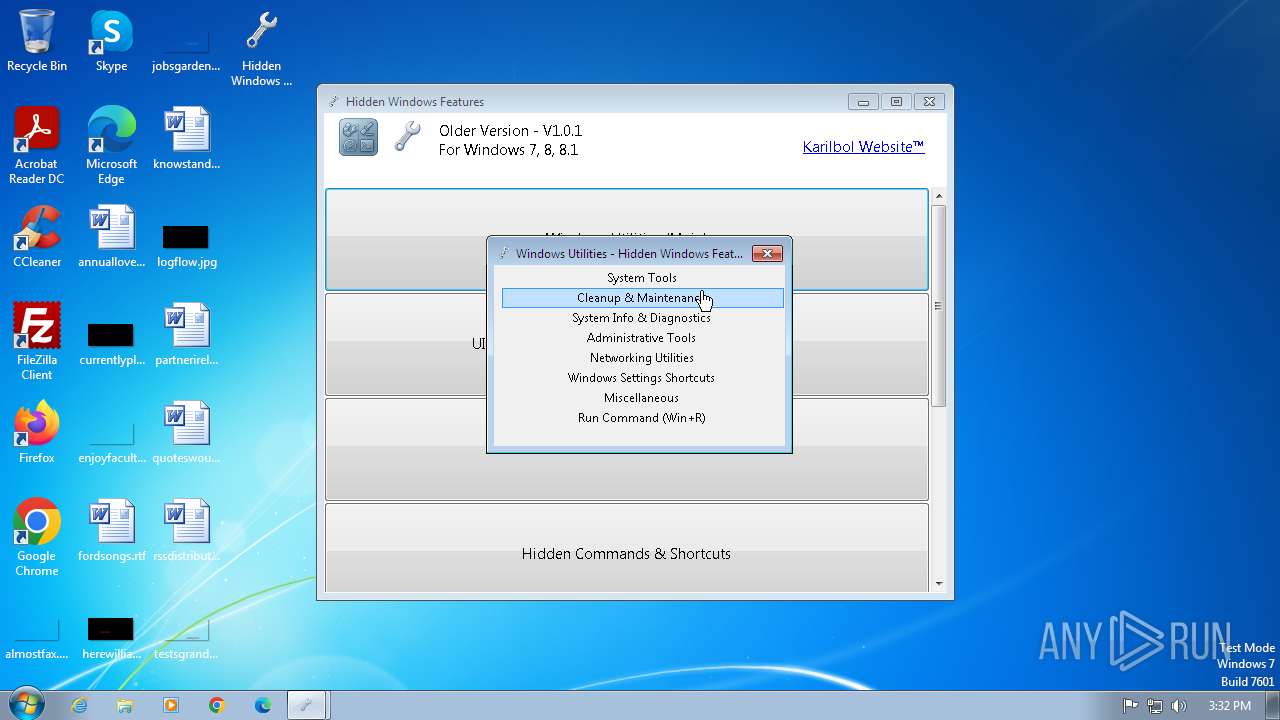
| 2308 | "C:\Windows\system32\mmc.exe" "C:\Windows\System32\WF.msc" | C:\Windows\System32\mmc.exe | — | Hidden Windows Features.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | "C:\Windows\System32\taskmgr.exe" | C:\Windows\System32\taskmgr.exe | — | Hidden Windows Features.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\System32\appwiz.cpl", | C:\Windows\System32\rundll32.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2464 | "C:\Windows\System32\resmon.exe" | C:\Windows\System32\resmon.exe | — | Hidden Windows Features.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Resource Monitor Exit code: 0 Version: 6.1.7601.23841 (win7sp1_ldr.170612-1252) Modules
| |||||||||||||||
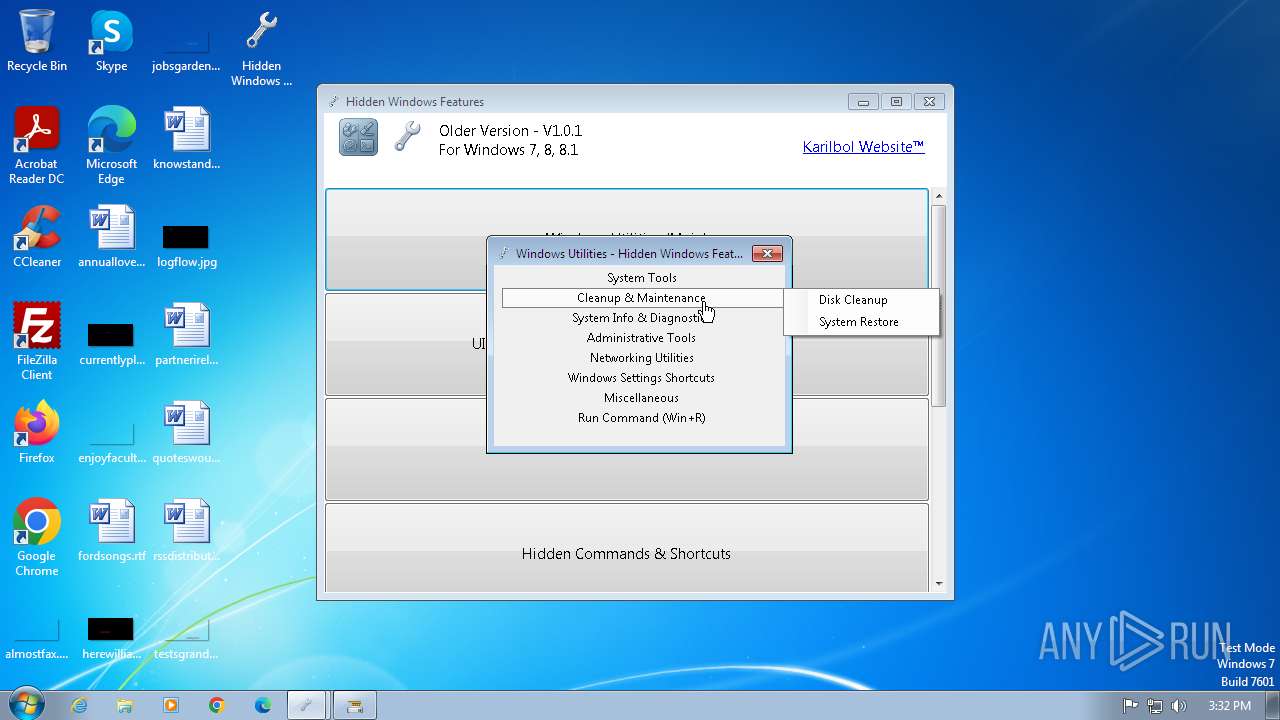
| 2592 | "C:\Windows\System32\control.exe" "C:\Windows\System32\appwiz.cpl", | C:\Windows\System32\control.exe | — | Hidden Windows Features.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 311
Read events
12 995
Write events
292
Delete events
24
Modification events
| (PID) Process: | (2692) Hidden Windows Features.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2692) Hidden Windows Features.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2692) Hidden Windows Features.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2692) Hidden Windows Features.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1472) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 30030000E803000001000000010000004401000077000000E00200005C0200000300000001000000000000000000000001000000000000000100000000000000000000000200000004000000090000001D000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000009C00000040000000210000004600000052000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000000002000000010000000300000004000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0500000000000000FFFFFFFF00000000020000000300000004000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000630060003C005A00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000000010000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0400000000000000FFFFFFFF02000000FFFFFFFF4F00000028000000970000003400000050000000000000000100000002000000030000000400000000000000FFFFFFFF43000000000000000000000001000000 | |||
| (PID) Process: | (1472) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | UsrColumnSettings |
Value: 1C0C0000340400000000000050000000010000001D0C0000350400000000000023000000010000001E0C000036040000000000003C000000010000001F0C000039040000000000004E00000001000000200C000037040000000000004E00000001000000 | |||
| (PID) Process: | (2356) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | UsrColumnSettings |
Value: 1C0C0000340400000000000050000000010000001D0C0000350400000000000023000000010000001E0C000036040000000000003C000000010000001F0C000039040000000000004E00000001000000200C000037040000000000004E00000001000000 | |||
| (PID) Process: | (2356) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 30030000E803000001000000010000004401000077000000E00200005C0200000300000001000000000000000000000001000000000000000100000000000000000000000200000004000000090000001D000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000009C00000040000000210000004600000052000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000000002000000010000000300000004000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0500000000000000FFFFFFFF00000000020000000300000004000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000630060003C005A00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000000010000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0400000000000000FFFFFFFF02000000FFFFFFFF4F00000028000000970000003400000050000000000000000100000002000000030000000400000000000000FFFFFFFF43000000000000000000000001000000 | |||
| (PID) Process: | (2464) resmon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2464) resmon.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
5
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3224 | perfmon.exe | C:\Users\admin\AppData\Local\Resmon.ResmonCfg | xml | |
MD5:0C4B1ACB72943D8D024DABD9CDC37F85 | SHA256:A8E45503FF7DEAD7B109B1EFB96F0ABB15BF09E1FBB1D89EB5EF54365344F2C4 | |||
| 4072 | cleanmgr.exe | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 2892 | rstrui.exe | C:\Windows\WindowsUpdate.log | text | |
MD5:B4CA5E4008BF3F64582D08CA547BD84F | SHA256:EBAE9191D7CA5C2BEF408288F9C11C4FF00C7822F54557D51CA648550136BD29 | |||
| 4072 | cleanmgr.exe | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{03FBC83B-44C5-4AAE-8FB6-BE661E28FDDA}.FSD | binary | |
MD5:61F81EA9F45A08D10521AB38BD4328A9 | SHA256:535347584C2EE95C5A86B44BC0818429937D5D59CFEE229C597C51286F54B3BC | |||
| 4072 | cleanmgr.exe | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:3C0D8B487CBE7B03747E01EBC44A7A84 | SHA256:E662A189F2DA21FD974B4D4EC25984700F9C294F32B900364E4919BF25BF6CDF | |||
| 4072 | cleanmgr.exe | C:\Users\admin\AppData\Local\Temp\{84D73257-8F43-4994-92CC-E5793778ED0B} | binary | |
MD5:3C0D8B487CBE7B03747E01EBC44A7A84 | SHA256:E662A189F2DA21FD974B4D4EC25984700F9C294F32B900364E4919BF25BF6CDF | |||
| 2892 | rstrui.exe | C:\Windows\Logs\SystemRestore\RestoreUI.0.etl | binary | |
MD5:3716CD2F43EE30CFFA3DB402A6816576 | SHA256:CB5A3DD45DC13EA8EF800AB443E505C81AA6CF89B71E4E21FB27A9735CC3600D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
cleanmgr.exe | PID=4072 Failed to create. - CScavengeCleanup::Initialize(hr:0x800702e4) |
cleanmgr.exe | DC:Process is not elevated. |