| File name: | Lunelior Setup.exe |
| Full analysis: | https://app.any.run/tasks/fa068ee8-bada-41b0-8bd8-3bced6adfa6e |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2025, 16:41:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | B92B986FFE4992A34241B07599A0B9CF |
| SHA1: | 0ED92CA7EB4AF672F3CB4FFDE2309CC328969ABB |
| SHA256: | 29343058F7CA76D213D3D9178530003724AF44A5704CBE9A035888C02EF7D79C |
| SSDEEP: | 393216:sppG3sXquPYAAi7ahDZfpMsbAzDb3CrOliYvg46ZuqRvM4m3KELKY1xnlqlBv0kF:Yxgxifs0zD756ZuH/3KELdA/vZHNZsk |
MALICIOUS
No malicious indicators.SUSPICIOUS
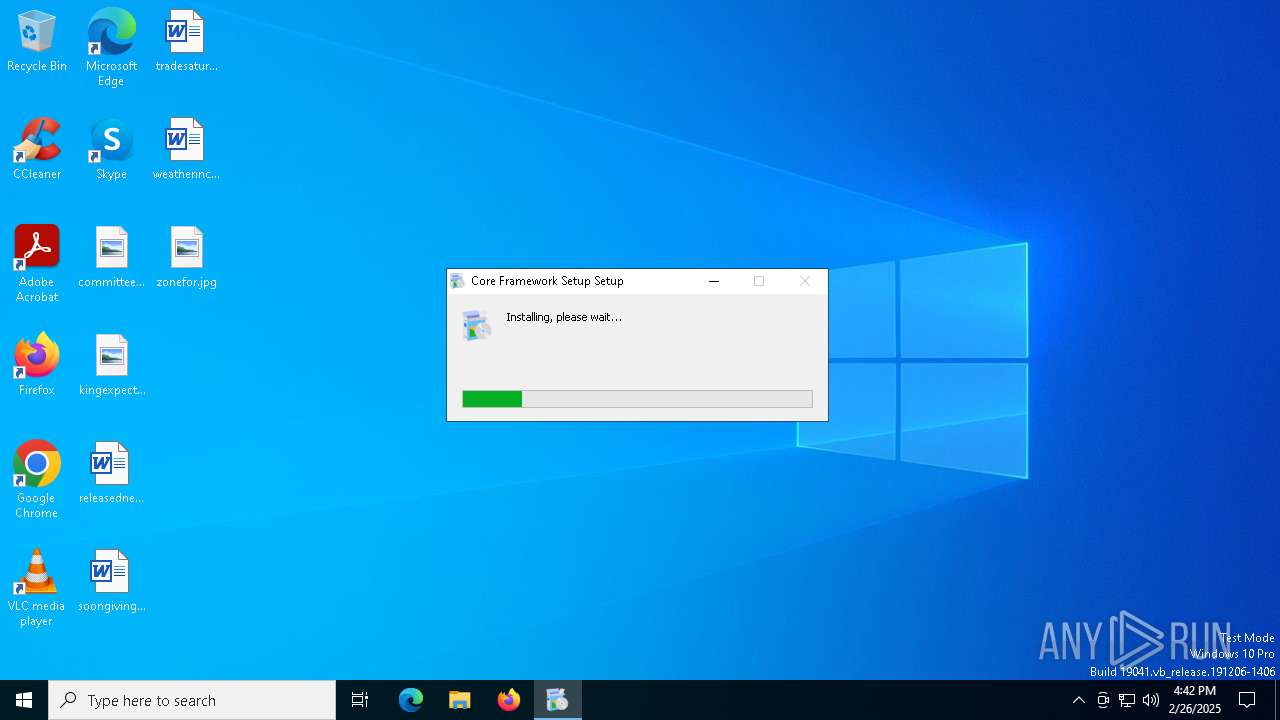
Malware-specific behavior (creating "System.dll" in Temp)
- Lunelior Setup.exe (PID: 6656)
Executable content was dropped or overwritten
- Lunelior Setup.exe (PID: 6656)
Starts CMD.EXE for commands execution
- Lunelior Setup.exe (PID: 6656)
- Core Framework Setup.exe (PID: 2908)
Get information on the list of running processes
- cmd.exe (PID: 6540)
- Lunelior Setup.exe (PID: 6656)
Process drops legitimate windows executable
- Lunelior Setup.exe (PID: 6656)
Reads security settings of Internet Explorer
- Lunelior Setup.exe (PID: 6656)
The process creates files with name similar to system file names
- Lunelior Setup.exe (PID: 6656)
Creates a software uninstall entry
- Lunelior Setup.exe (PID: 6656)
Application launched itself
- Core Framework Setup.exe (PID: 2908)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 2040)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 3768)
- cmd.exe (PID: 456)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 736)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2040)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 3768)
- cmd.exe (PID: 736)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 456)
Drops 7-zip archiver for unpacking
- Lunelior Setup.exe (PID: 6656)
INFO
The sample compiled with english language support
- Lunelior Setup.exe (PID: 6656)
Reads the computer name
- Lunelior Setup.exe (PID: 6656)
- Core Framework Setup.exe (PID: 2908)
- Core Framework Setup.exe (PID: 6248)
- Core Framework Setup.exe (PID: 6456)
Creates files or folders in the user directory
- Lunelior Setup.exe (PID: 6656)
- Core Framework Setup.exe (PID: 2908)
Manual execution by a user
- Core Framework Setup.exe (PID: 2908)
Checks supported languages
- Core Framework Setup.exe (PID: 2908)
- Lunelior Setup.exe (PID: 6656)
- Core Framework Setup.exe (PID: 6248)
- Core Framework Setup.exe (PID: 6456)
Reads Environment values
- Core Framework Setup.exe (PID: 2908)
Reads product name
- Core Framework Setup.exe (PID: 2908)
Checks proxy server information
- Core Framework Setup.exe (PID: 2908)
- slui.exe (PID: 6972)
Reads the machine GUID from the registry
- Core Framework Setup.exe (PID: 2908)
Create files in a temporary directory
- Lunelior Setup.exe (PID: 6656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | - |
| FileVersion: | 2.0.0 |
| LegalCopyright: | Copyright © 2025 Core Framework Setup |
| ProductName: | Core Framework Setup |
| ProductVersion: | 2.0.0 |
Total processes
158
Monitored processes
30
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell -NoProfile -Command "(Get-CimInstance Win32_Processor).NumberOfLogicalProcessors"" | C:\Windows\System32\cmd.exe | — | Core Framework Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell -NoProfile -Command "(Get-CimInstance Win32_Processor).Manufacturer"" | C:\Windows\System32\cmd.exe | — | Core Framework Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | tasklist /FI "USERNAME eq admin" /FI "IMAGENAME eq Core Framework Setup.exe" /FO csv | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell -NoProfile -Command "(Get-CimInstance Win32_Processor).NumberOfCores"" | C:\Windows\System32\cmd.exe | — | Core Framework Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell -NoProfile -Command "(Get-CimInstance Win32_Processor).Name"" | C:\Windows\System32\cmd.exe | — | Core Framework Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | powershell -NoProfile -Command "(Get-CimInstance Win32_ComputerSystem).Model" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | powershell -NoProfile -Command "(Get-CimInstance Win32_Processor).Name" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2852 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 118
Read events
33 107
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\core-framework-setup | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | ShortcutName |
Value: Core Framework Setup | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | DisplayName |
Value: Core Framework Setup 2.0.0 | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\core-framework-setup\Uninstall Core Framework Setup.exe" /currentuser | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\core-framework-setup\Uninstall Core Framework Setup.exe" /currentuser /S | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | DisplayVersion |
Value: 2.0.0 | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Local\Programs\core-framework-setup\Core Framework Setup.exe,0 | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (6656) Lunelior Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\1dc6b84c-73e4-5a5a-ad34-8b81f2bddd3a |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
21
Suspicious files
126
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\7z-out\locales\af.pak | binary | |
MD5:FC32A6B72FC91E1BE9C2C9D2EA586EC3 | SHA256:C56CB2841EE2E40FBDD6B7E293A1CE74BD10FD500465FCF99D1E07F8D69F8CE7 | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\nsExec.dll | executable | |
MD5:EC0504E6B8A11D5AAD43B296BEEB84B2 | SHA256:5D9CEB1CE5F35AEA5F9E5A0C0EDEEEC04DFEFE0C77890C80C70E98209B58B962 | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\nsis7z.dll | executable | |
MD5:80E44CE4895304C6A3A831310FBF8CD0 | SHA256:B393F05E8FF919EF071181050E1873C9A776E1A0AE8329AEFFF7007D0CADF592 | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\7z-out\locales\bn.pak | binary | |
MD5:F22D531DE1EF474D9839C96E22A06277 | SHA256:5A57265EBAC6DF683F0279684909755AD71EA70FEA71C6ECC1810EAC61D1CB3D | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\7z-out\LICENSE.electron.txt | text | |
MD5:4D42118D35941E0F664DDDBD83F633C5 | SHA256:5154E165BD6C2CC0CFBCD8916498C7ABAB0497923BAFCD5CB07673FE8480087D | |||
| 6656 | Lunelior Setup.exe | C:\Users\admin\AppData\Local\Temp\nsk100B.tmp\7z-out\locales\da.pak | binary | |
MD5:7DB5F17D66731B076727181F7F66D867 | SHA256:E32681CDD03DB28EB360B1B4203C2988190B7B6F77679CA807CD95A1967DED04 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
26
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
780 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
780 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2040 | backgroundTaskHost.exe | 20.223.35.26:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
780 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
780 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
780 | SIHClient.exe | 20.3.187.198:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |