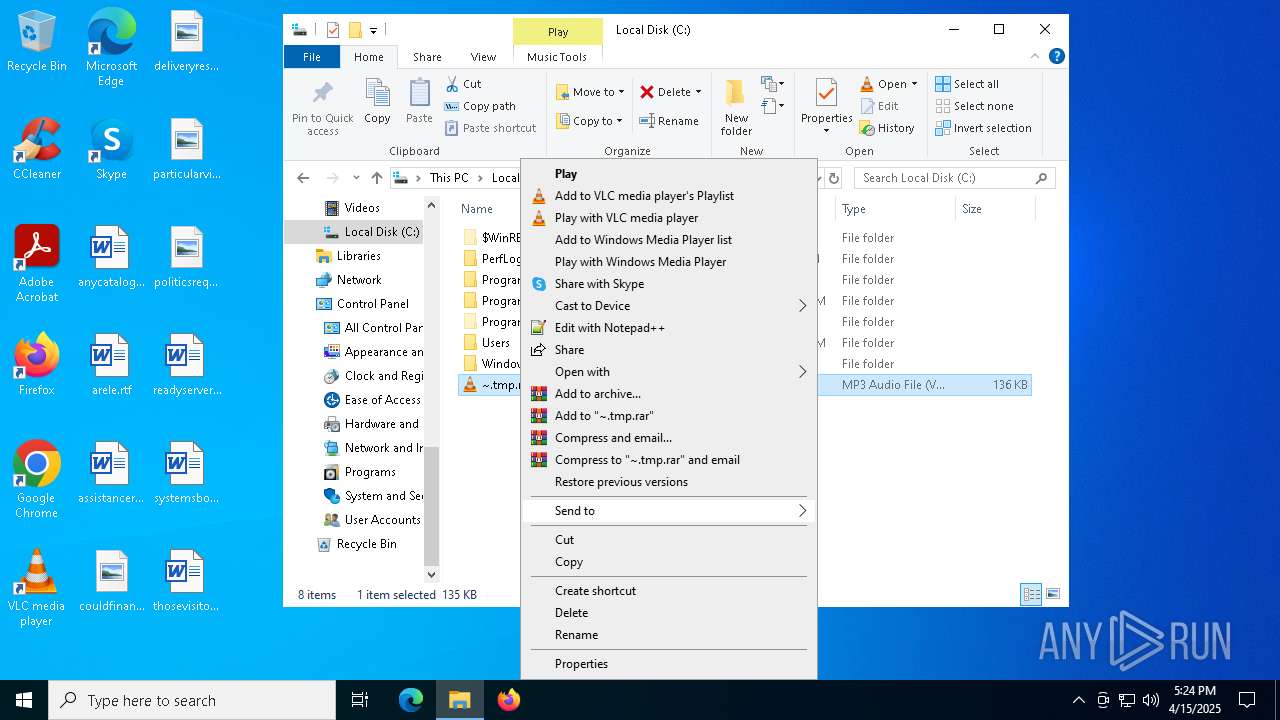
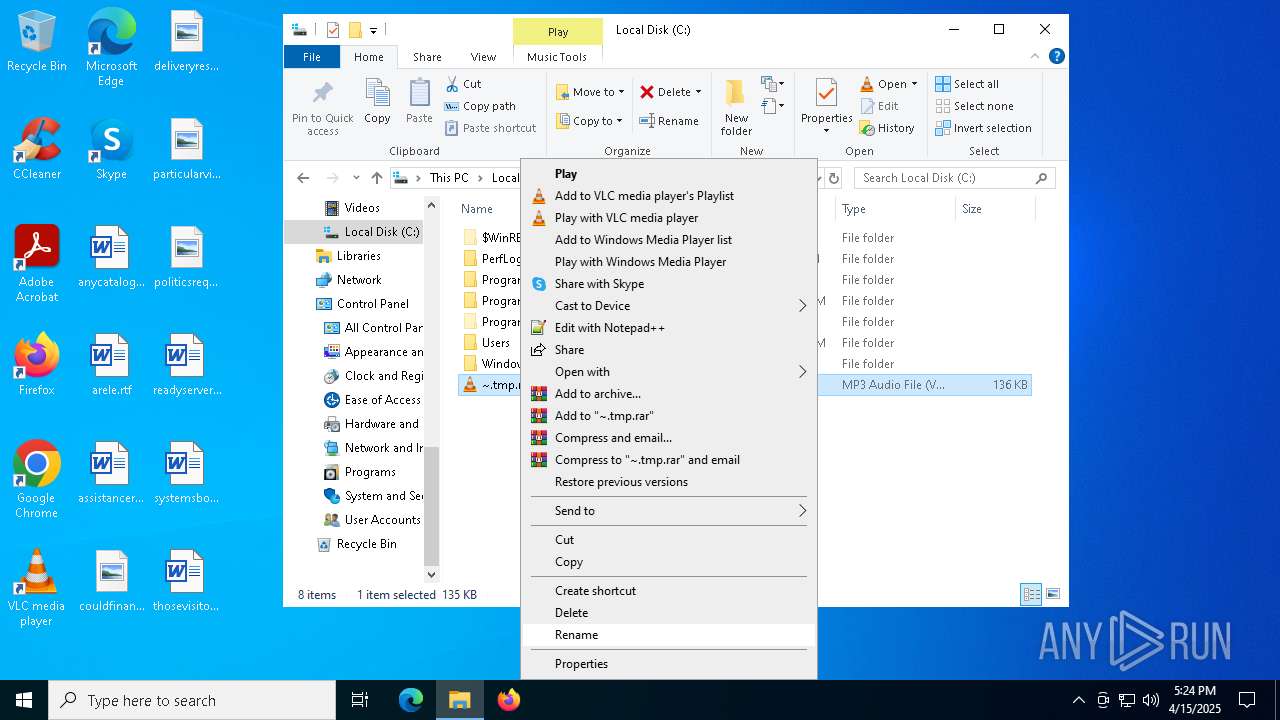
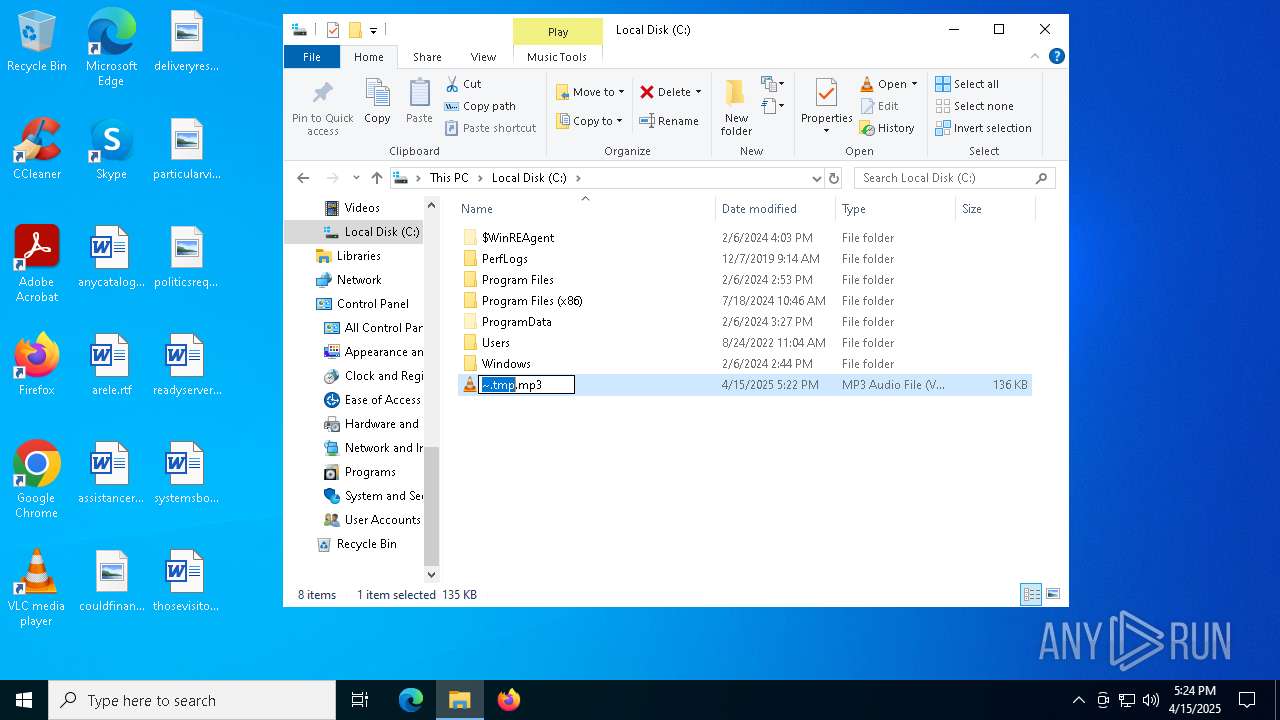
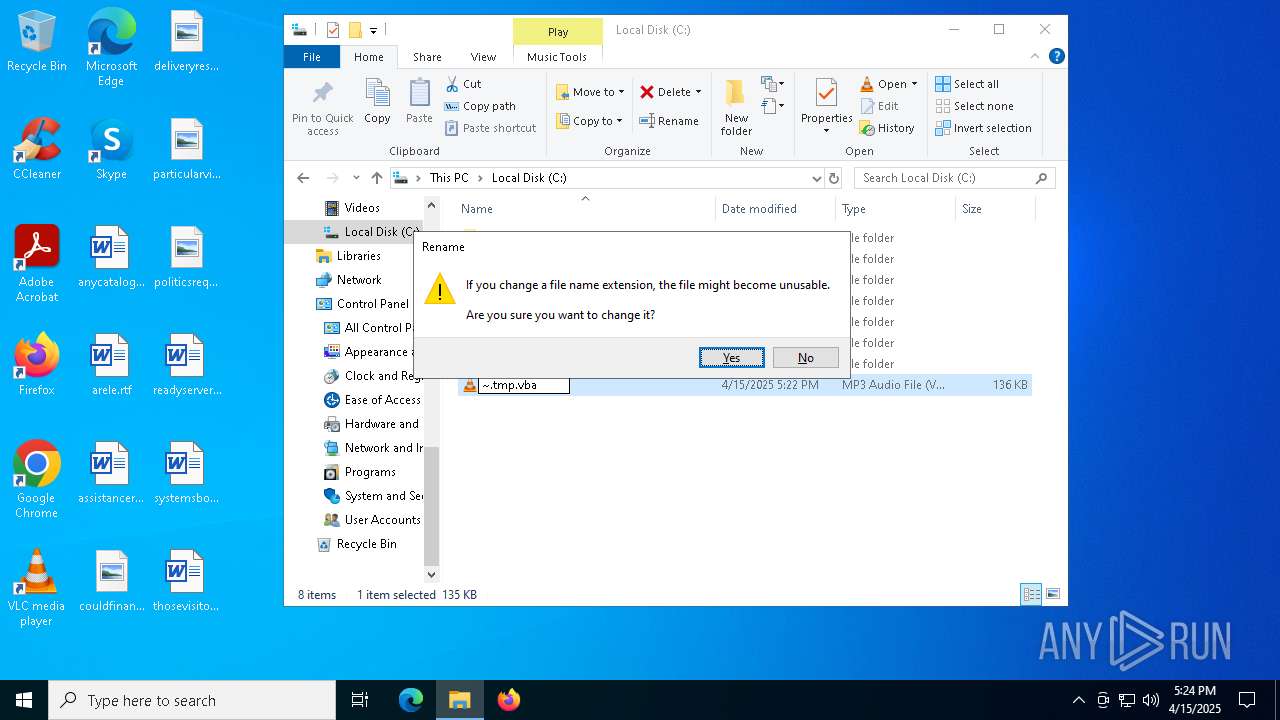
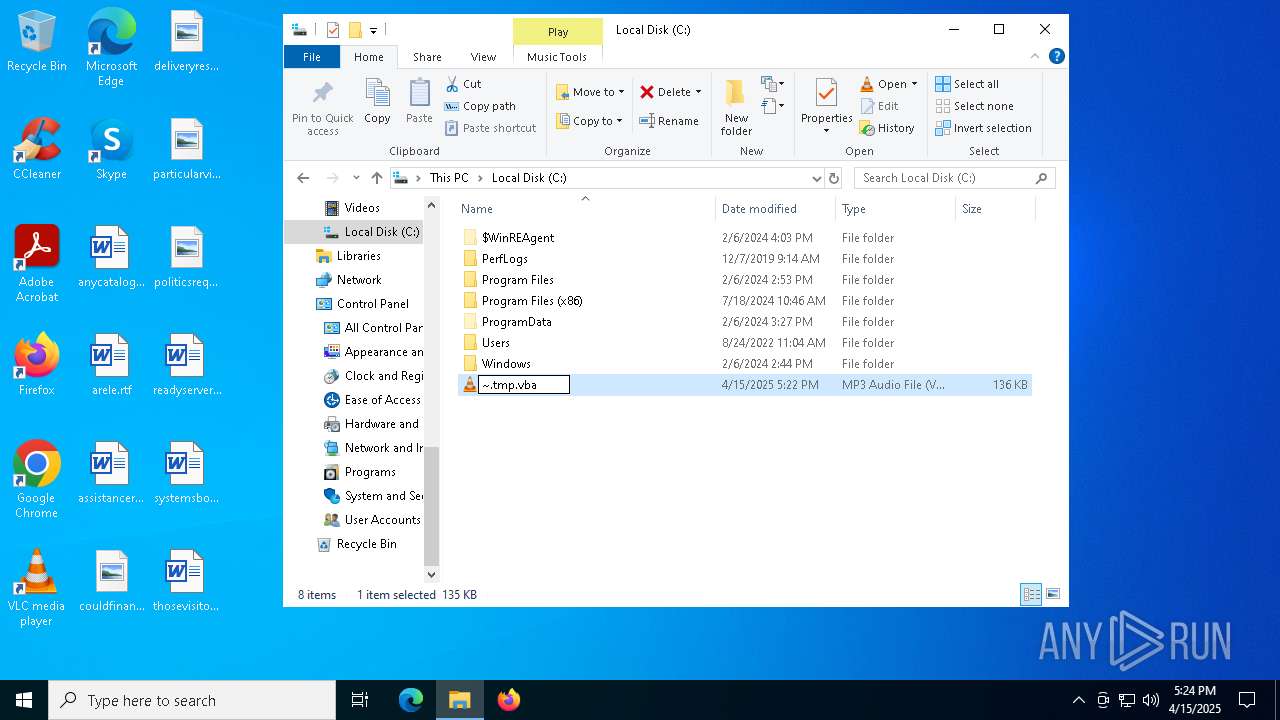
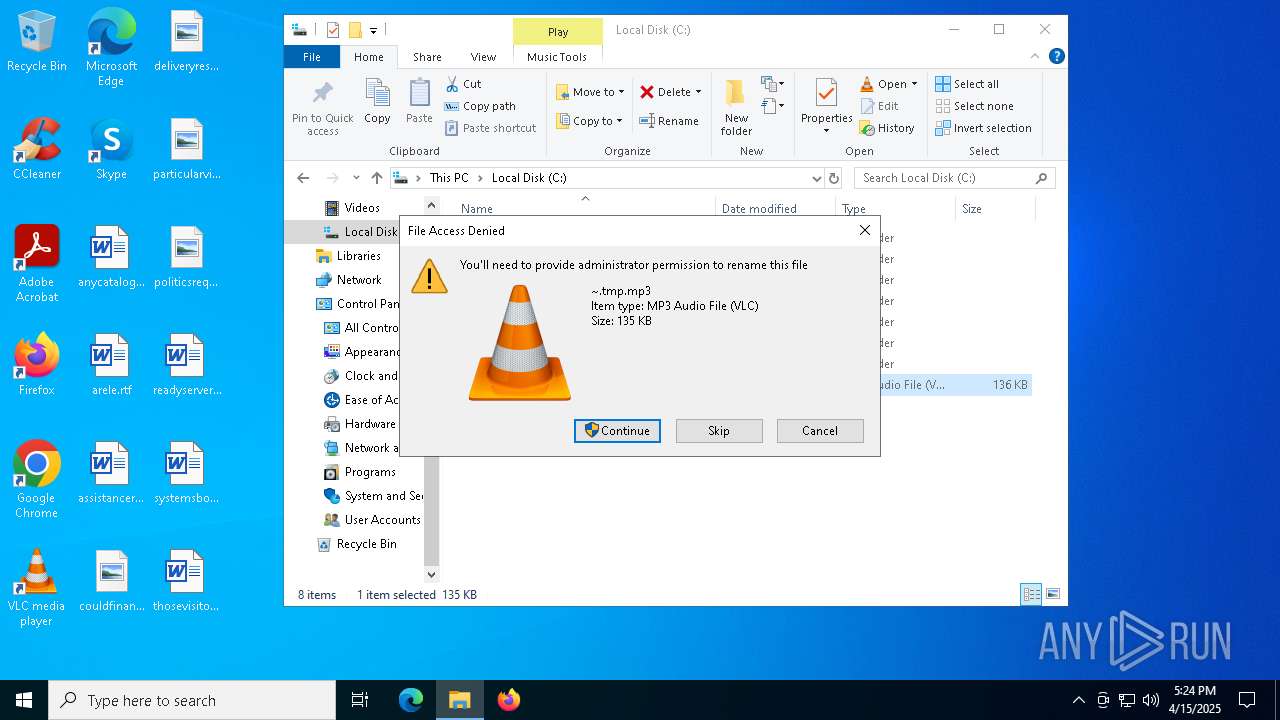
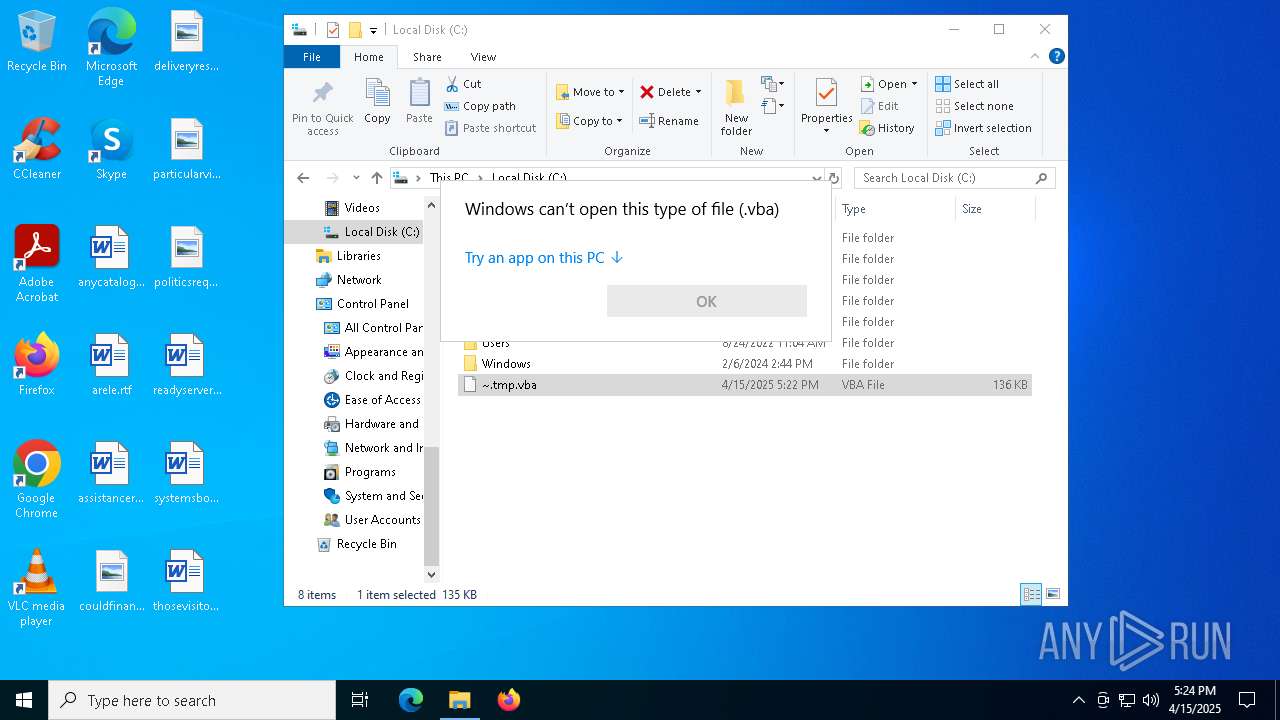
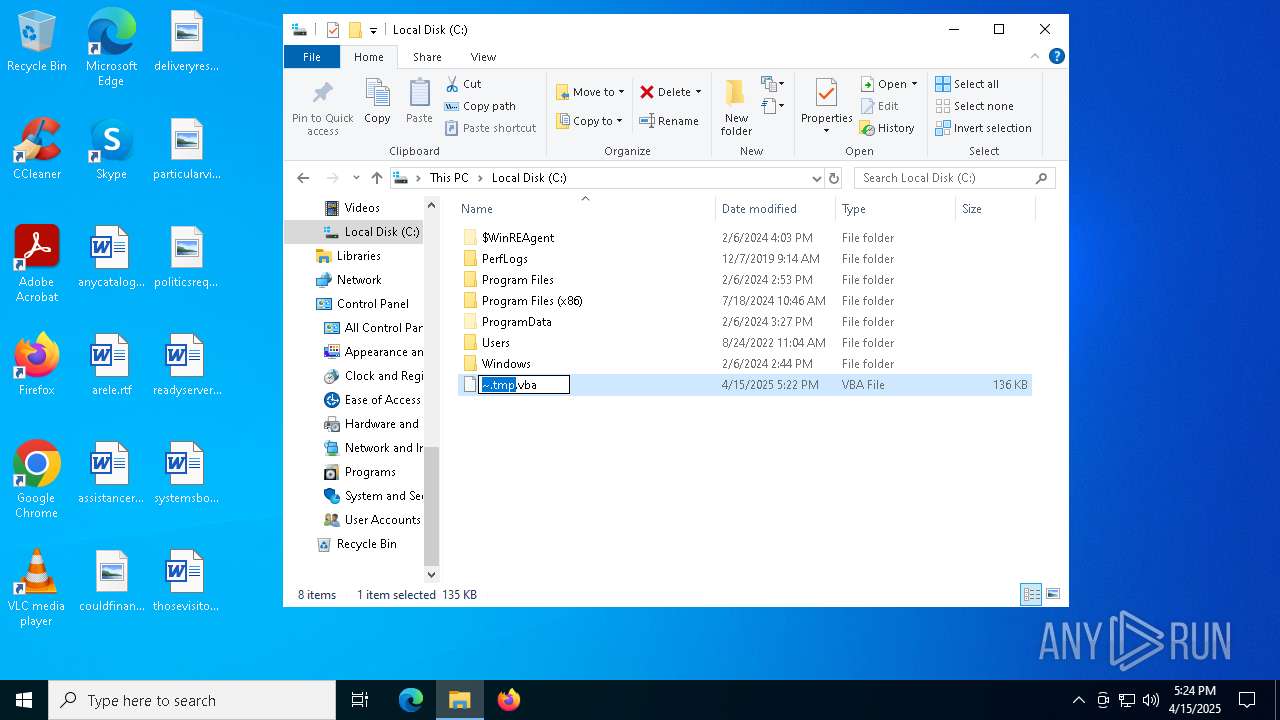
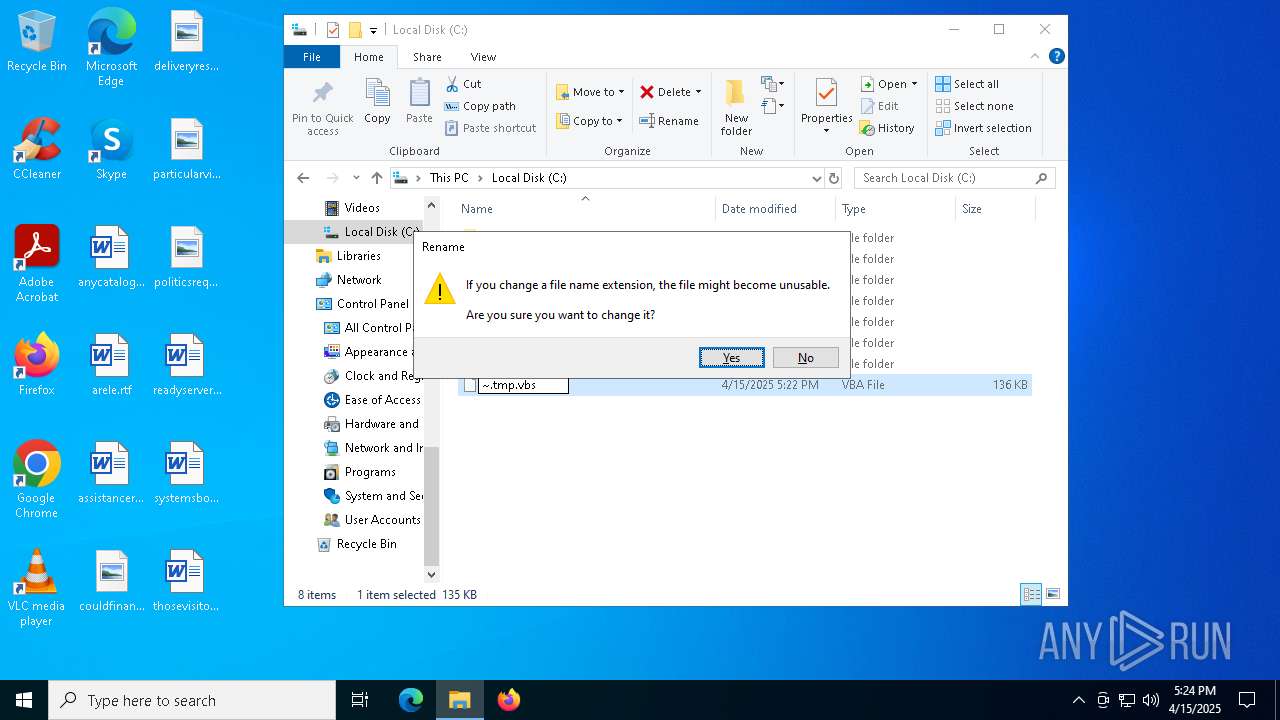
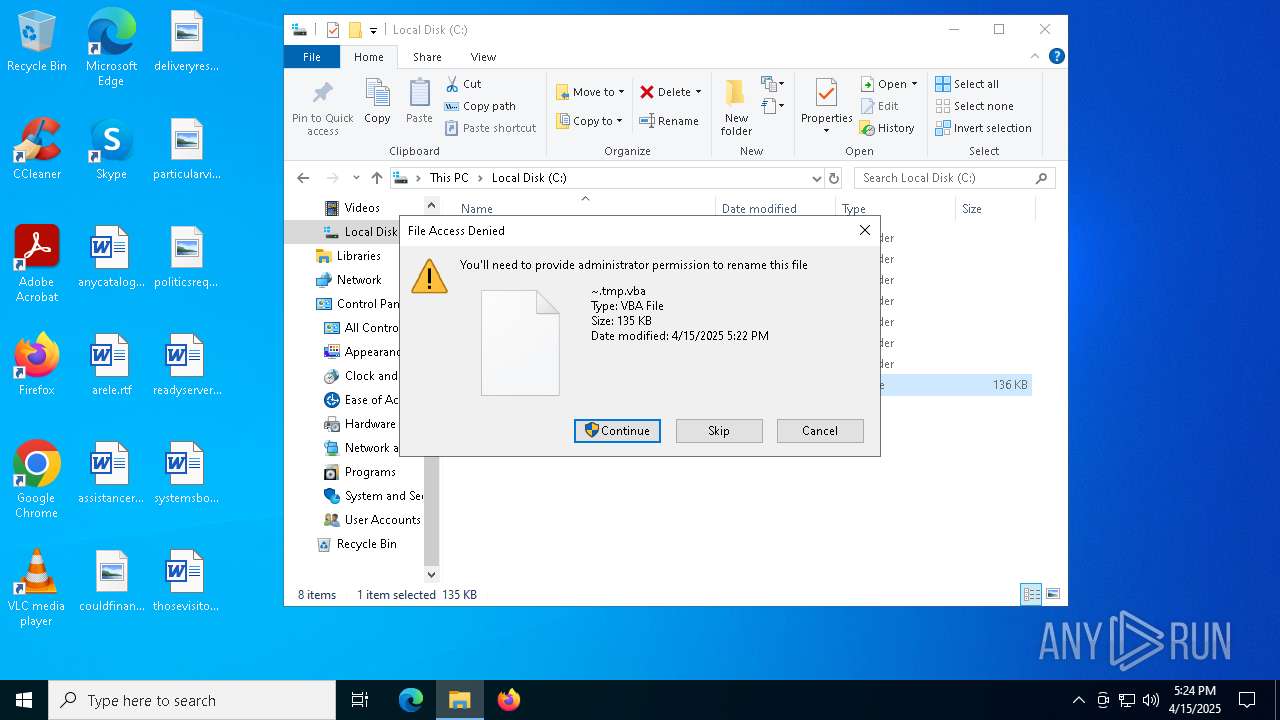
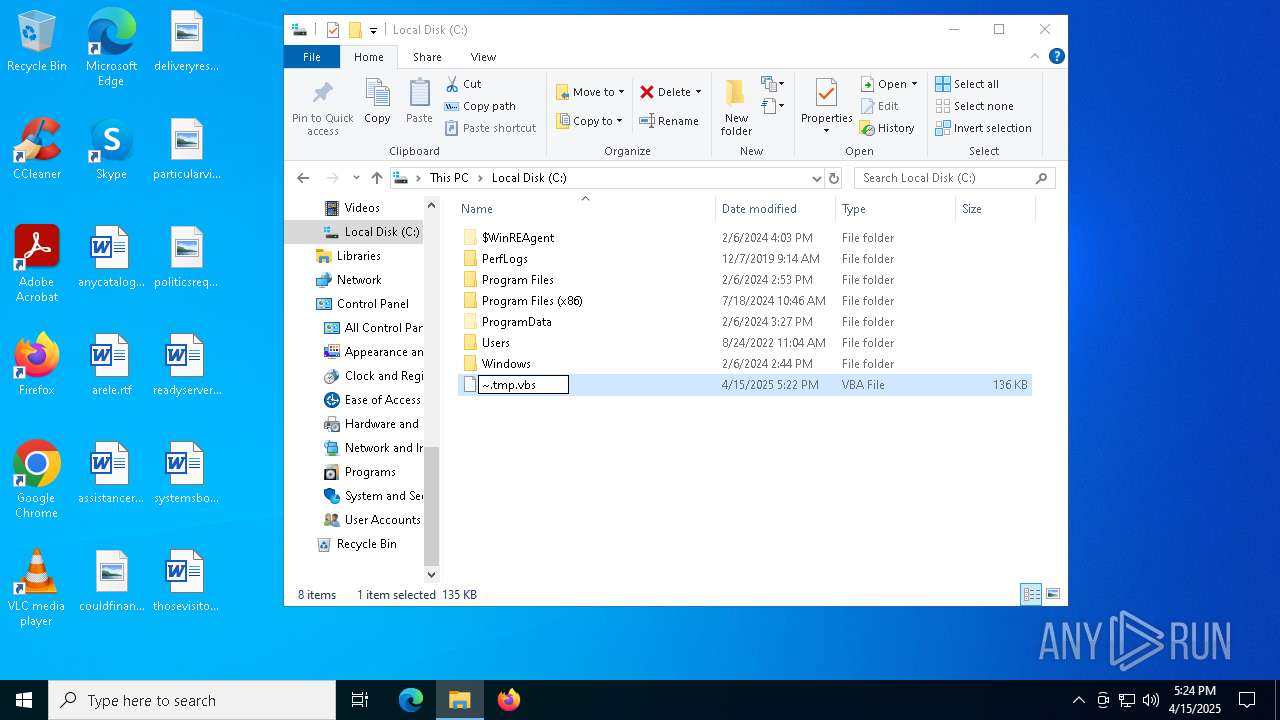
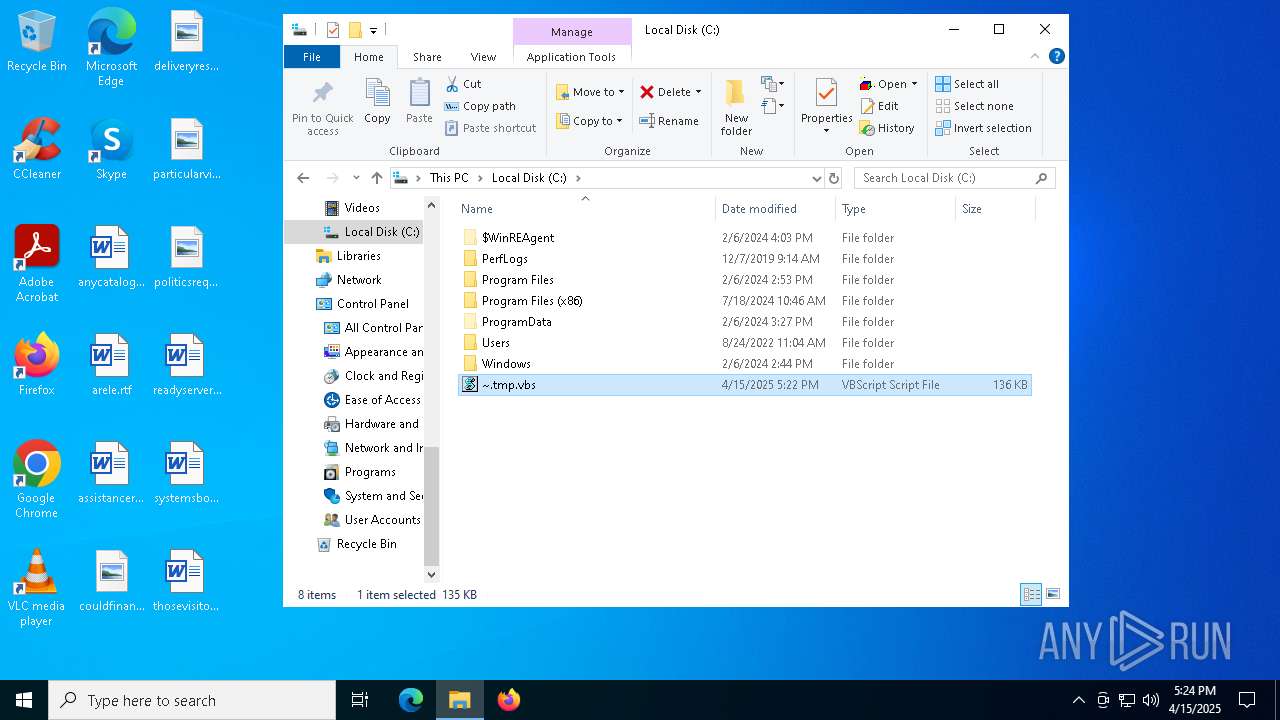
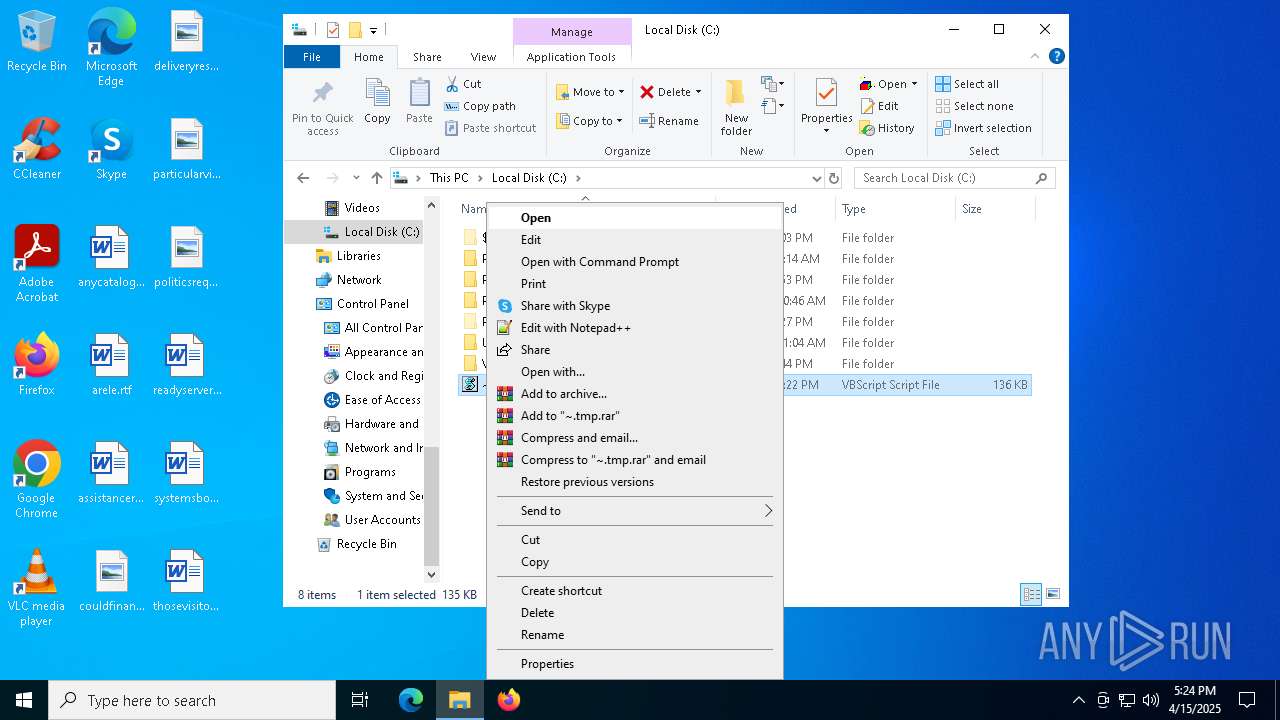
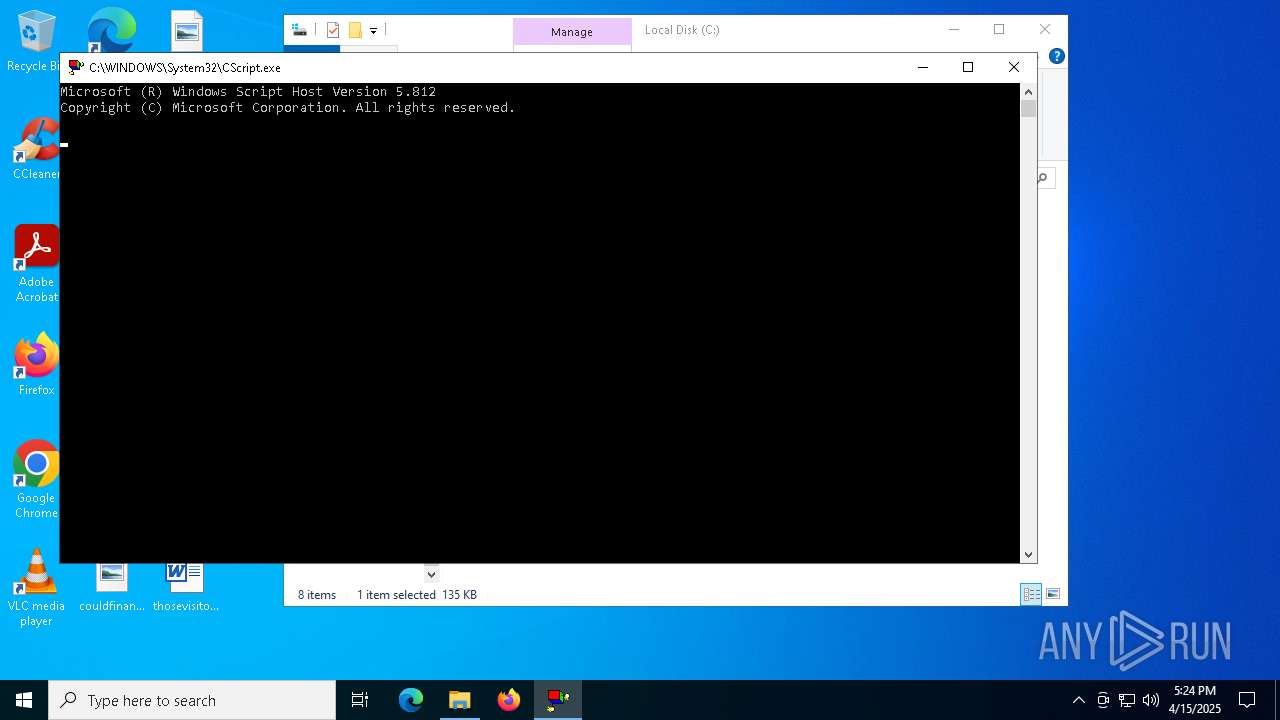
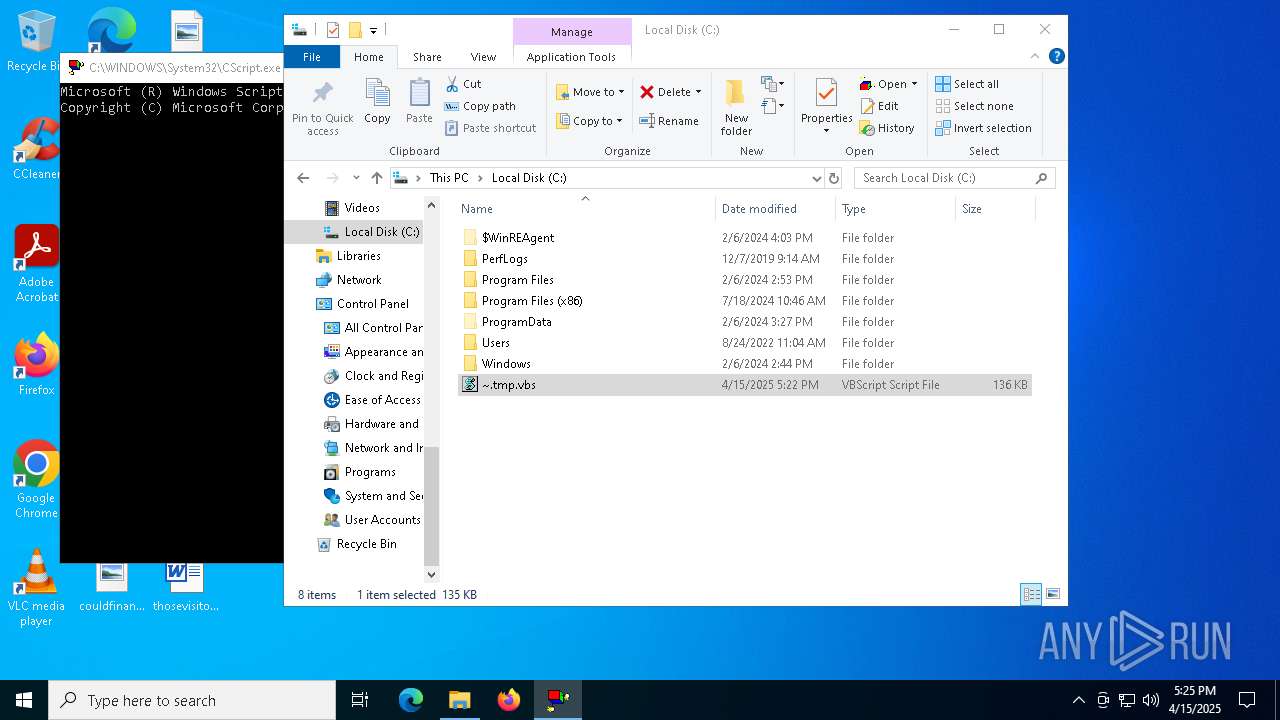
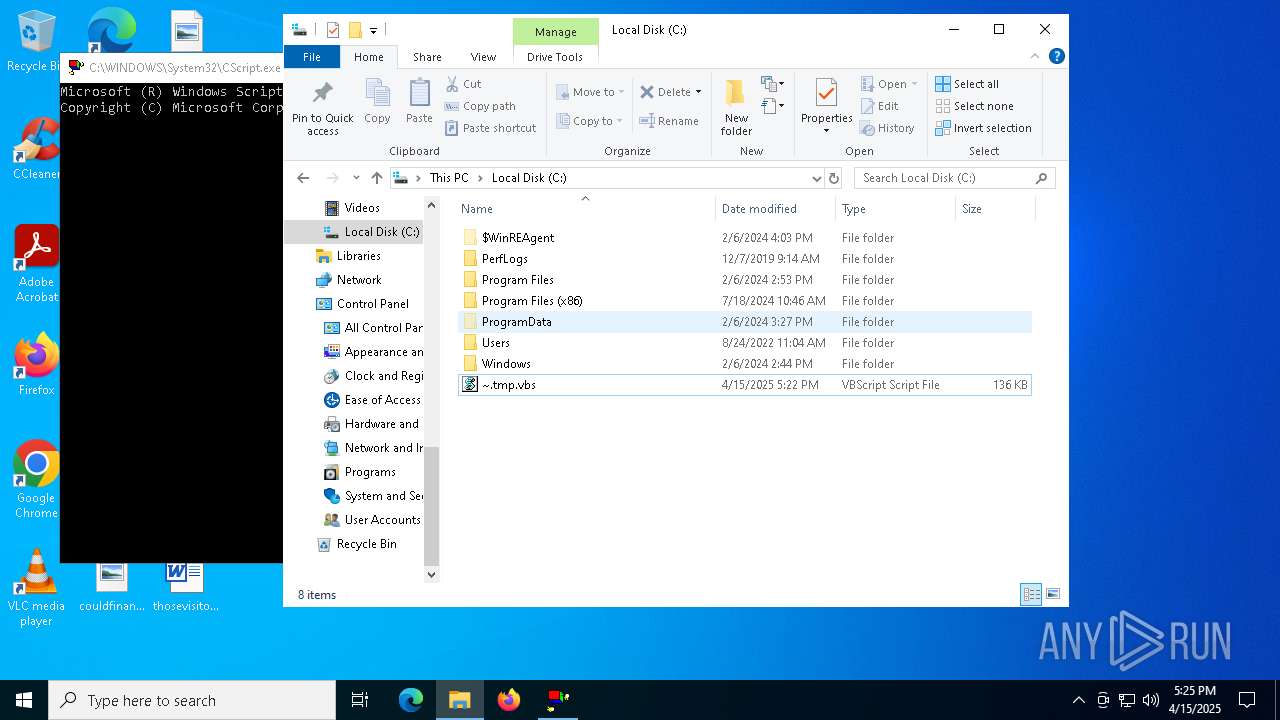
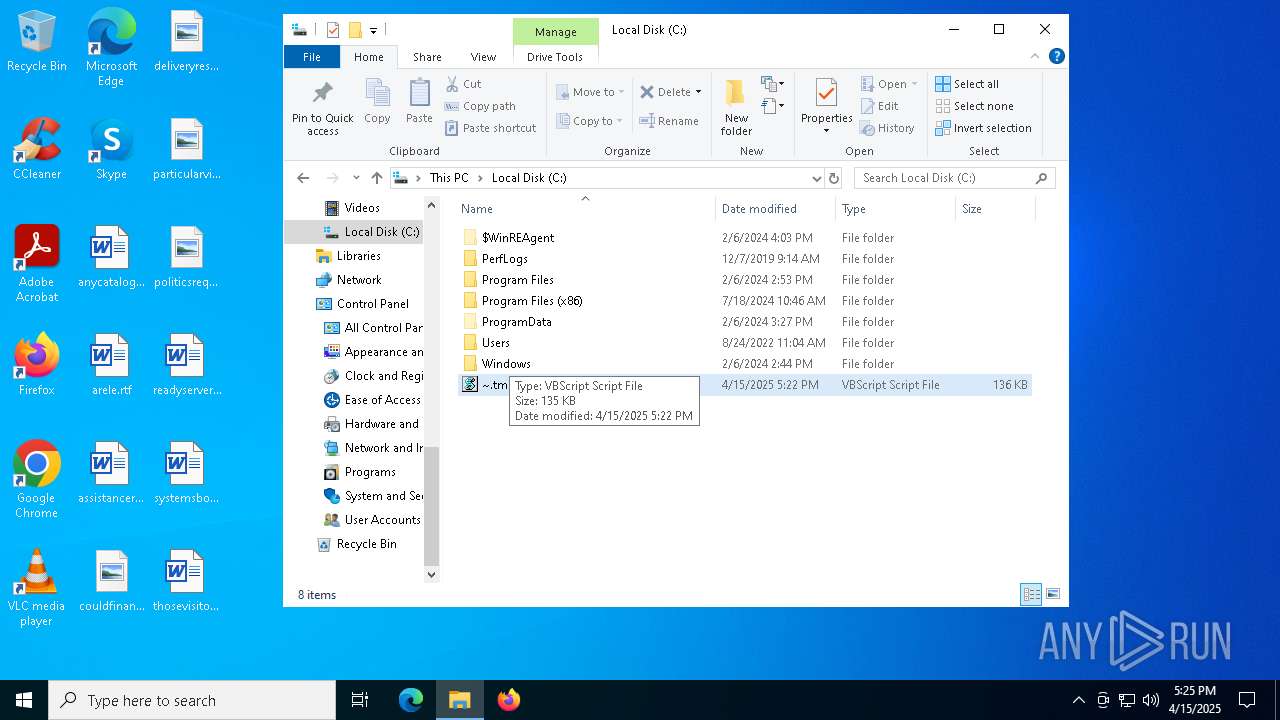
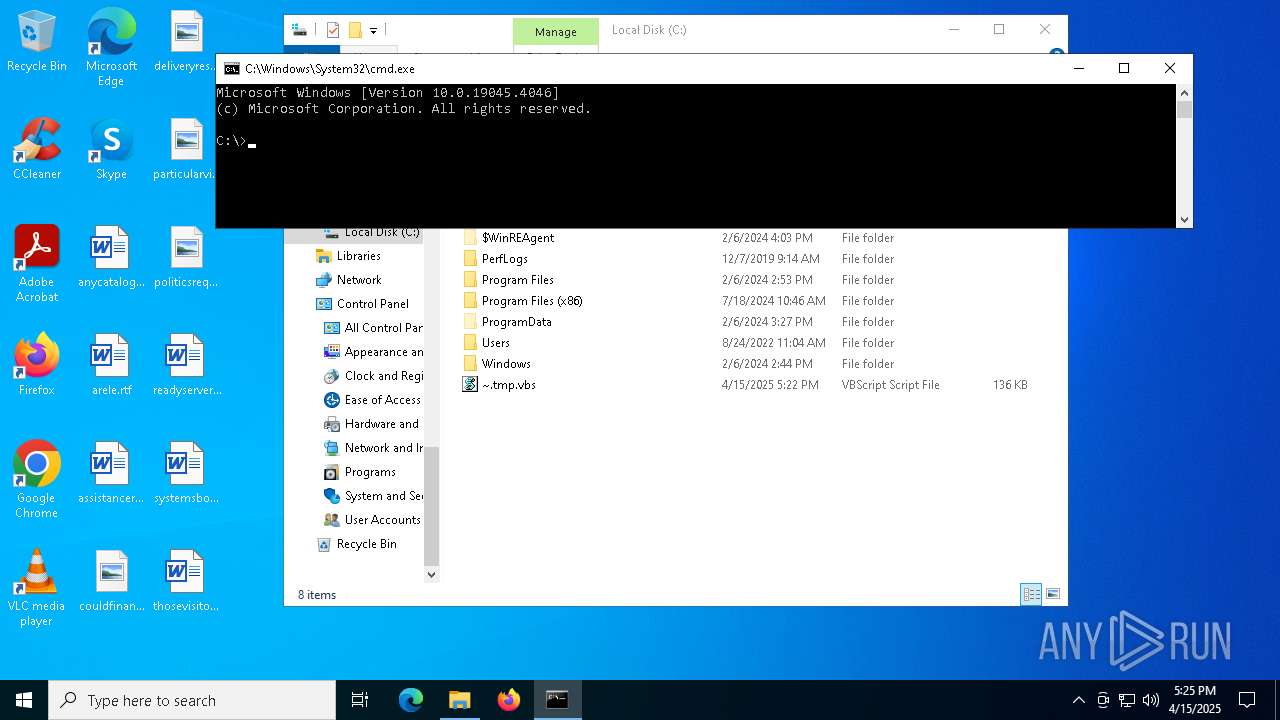
| File name: | ~.tmp |
| Full analysis: | https://app.any.run/tasks/f59dc4ce-ec68-4196-828d-7ab5f5bb9574 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 17:22:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (8696), with CRLF line terminators |
| MD5: | 1DDAB156B9FD709FF8FE61FFA2AFB789 |
| SHA1: | F3626FDAB000C6C634569B95683FD8CF1B2934BB |
| SHA256: | 290863999FD0713841DD7CE2BEC725CEE3F5A467A5DE00F819B2471867BFB105 |
| SSDEEP: | 1536:x0Y6Iij7lm5LxFAHUhpDqxVsOca0GrcFvQYfpy7zdz3G4GD4IuaIJ7fJpZycaCT2:x+KUzxJ3qNRYGr |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 3096)
- wscript.exe (PID: 872)
- cscript.exe (PID: 236)
- wscript.exe (PID: 2096)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 3096)
- wscript.exe (PID: 872)
- cscript.exe (PID: 236)
- wscript.exe (PID: 2096)
Creates a new folder (SCRIPT)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 3096)
- wscript.exe (PID: 872)
- cscript.exe (PID: 236)
- wscript.exe (PID: 2096)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- vlc.exe (PID: 4244)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 3096)
- wscript.exe (PID: 872)
- cscript.exe (PID: 236)
- wscript.exe (PID: 2096)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 3096)
- wscript.exe (PID: 872)
- cscript.exe (PID: 236)
- wscript.exe (PID: 2096)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 3096)
- wscript.exe (PID: 872)
- cscript.exe (PID: 236)
- wscript.exe (PID: 2096)
Executes application which crashes
- wscript.exe (PID: 7020)
- wscript.exe (PID: 3096)
- wscript.exe (PID: 872)
- cscript.exe (PID: 236)
- wscript.exe (PID: 2096)
The process creates files with name similar to system file names
- WerFault.exe (PID: 1272)
- WerFault.exe (PID: 4040)
- WerFault.exe (PID: 5508)
- WerFault.exe (PID: 2596)
- WerFault.exe (PID: 6244)
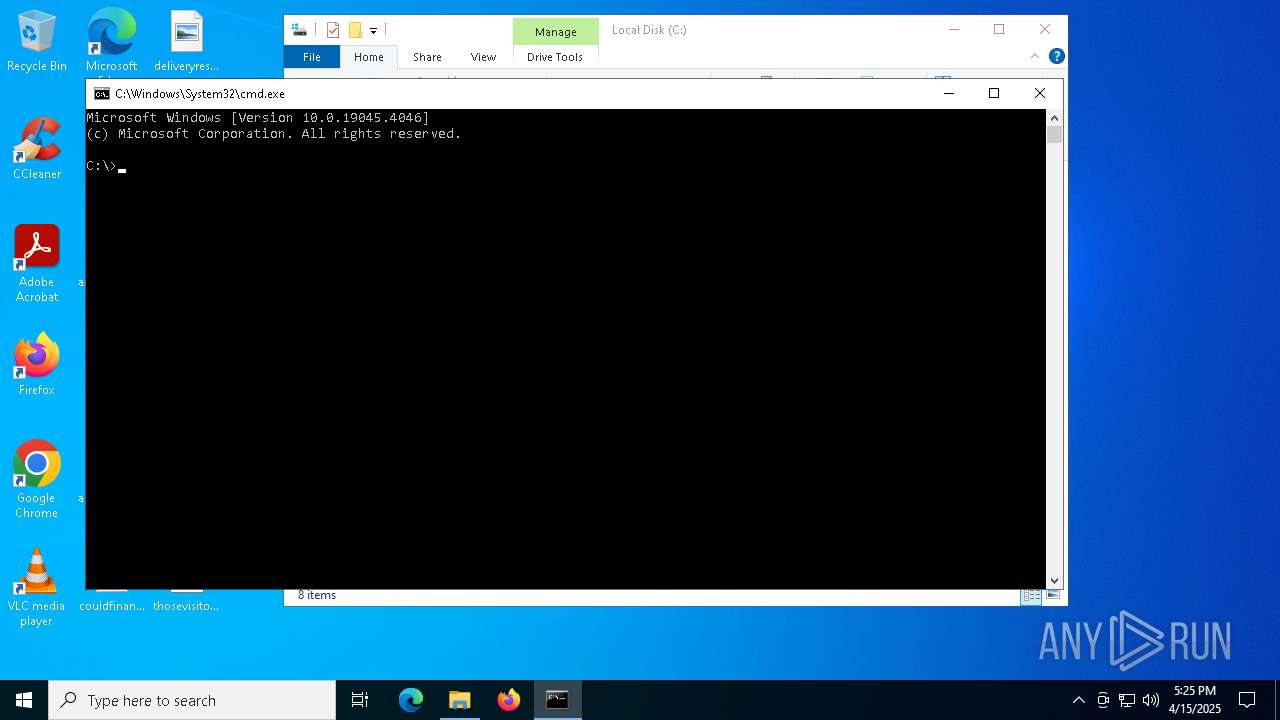
The process executes VB scripts
- cmd.exe (PID: 5308)
INFO
Checks supported languages
- vlc.exe (PID: 4244)
- vlc.exe (PID: 2064)
Reads the computer name
- vlc.exe (PID: 4244)
- vlc.exe (PID: 2064)
The process uses Lua
- vlc.exe (PID: 4244)
Manual execution by a user
- mspaint.exe (PID: 5256)
- WINWORD.EXE (PID: 1324)
- vlc.exe (PID: 2064)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 3096)
- wscript.exe (PID: 872)
- cscript.exe (PID: 236)
- cmd.exe (PID: 5308)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4208)
Checks proxy server information
- slui.exe (PID: 6208)
Reads the software policy settings
- slui.exe (PID: 6208)
- slui.exe (PID: 1300)
Creates files or folders in the user directory
- WerFault.exe (PID: 1272)
- WerFault.exe (PID: 4040)
- WerFault.exe (PID: 5508)
- WerFault.exe (PID: 2596)
- WerFault.exe (PID: 6244)
Reads security settings of Internet Explorer
- cscript.exe (PID: 236)
- dllhost.exe (PID: 5136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
169
Monitored processes
24
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\WINDOWS\System32\CScript.exe" "C:\~.tmp.vbs" | C:\Windows\System32\cscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 744 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | "C:\WINDOWS\System32\WScript.exe" "C:\~.tmp.vbs" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 900 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | C:\WINDOWS\system32\WerFault.exe -u -p 7020 -s 1040 | C:\Windows\System32\WerFault.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\anycatalog.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\VideoLAN\VLC\vlc.exe" | C:\Program Files\VideoLAN\VLC\vlc.exe | — | explorer.exe | |||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 2096 | "C:\WINDOWS\System32\WScript.exe" "C:\~.tmp.vbs" | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2596 | C:\WINDOWS\system32\WerFault.exe -u -p 236 -s 1060 | C:\Windows\System32\WerFault.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 495
Read events
22 189
Write events
281
Delete events
25
Modification events
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | WindowPlacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF7F000000470000007F04000087020000 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowThumbnail |
Value: 0 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPWidth |
Value: 0 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | BMPHeight |
Value: 0 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbXPos |
Value: 0 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbYPos |
Value: 0 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbWidth |
Value: 0 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ThumbHeight |
Value: 0 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | UnitSetting |
Value: 0 | |||
| (PID) Process: | (5256) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\View |
| Operation: | write | Name: | ShowRulers |
Value: 0 | |||
Executable files
10
Suspicious files
44
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4244 | vlc.exe | — | ||
MD5:— | SHA256:— | |||
| 4244 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.Vd4244 | text | |
MD5:C0E7F714F3BB6490047980D732B1AE0D | SHA256:07874D8A8DD4666E851996ABB73A23649A139F9280E921796D435D2FF85B1C8E | |||
| 4244 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.kB4244 | text | |
MD5:D94811EEE2A6753BED0E36DB5ECEA8D1 | SHA256:0B67F201745A652794C739D79FC718BF8541BE453EA7E7F1FBBDD840C80BDACC | |||
| 1324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\3A9C5DB7-D79C-4780-AC36-159EB3D983DF | xml | |
MD5:DA8A3F3D22A4E0902E403844839EDECE | SHA256:D011FFADABF066F3E708C8BE2C35B8B624B19744DD49B7F6F236982F7A260EFD | |||
| 1324 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 4244 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | text | |
MD5:C0E7F714F3BB6490047980D732B1AE0D | SHA256:07874D8A8DD4666E851996ABB73A23649A139F9280E921796D435D2FF85B1C8E | |||
| 4244 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.mS4244 | text | |
MD5:920F0C02F76AF16597856BBDFCC61AEF | SHA256:B8EEAE101881763E3EF4F0BE070144F863F187836D77F3AB0DA02D8BC623C961 | |||
| 4244 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\ml.xspf.tmp4244 | xml | |
MD5:781602441469750C3219C8C38B515ED4 | SHA256:81970DBE581373D14FBD451AC4B3F96E5F69B79645F1EE1CA715CFF3AF0BF20D | |||
| 1324 | WINWORD.EXE | C:\Users\admin\Desktop\~$ycatalog.rtf | binary | |
MD5:8441D002AF5F3B875467BBF0BE4C8EAD | SHA256:CD385F3C6690F8A4B1287784C2971A39DCFE95B5D20D251706729E4A13D32E42 | |||
| 4244 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\ml.xspf | xml | |
MD5:781602441469750C3219C8C38B515ED4 | SHA256:81970DBE581373D14FBD451AC4B3F96E5F69B79645F1EE1CA715CFF3AF0BF20D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
516 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
516 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1324 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1324 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
516 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
516 | SIHClient.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |