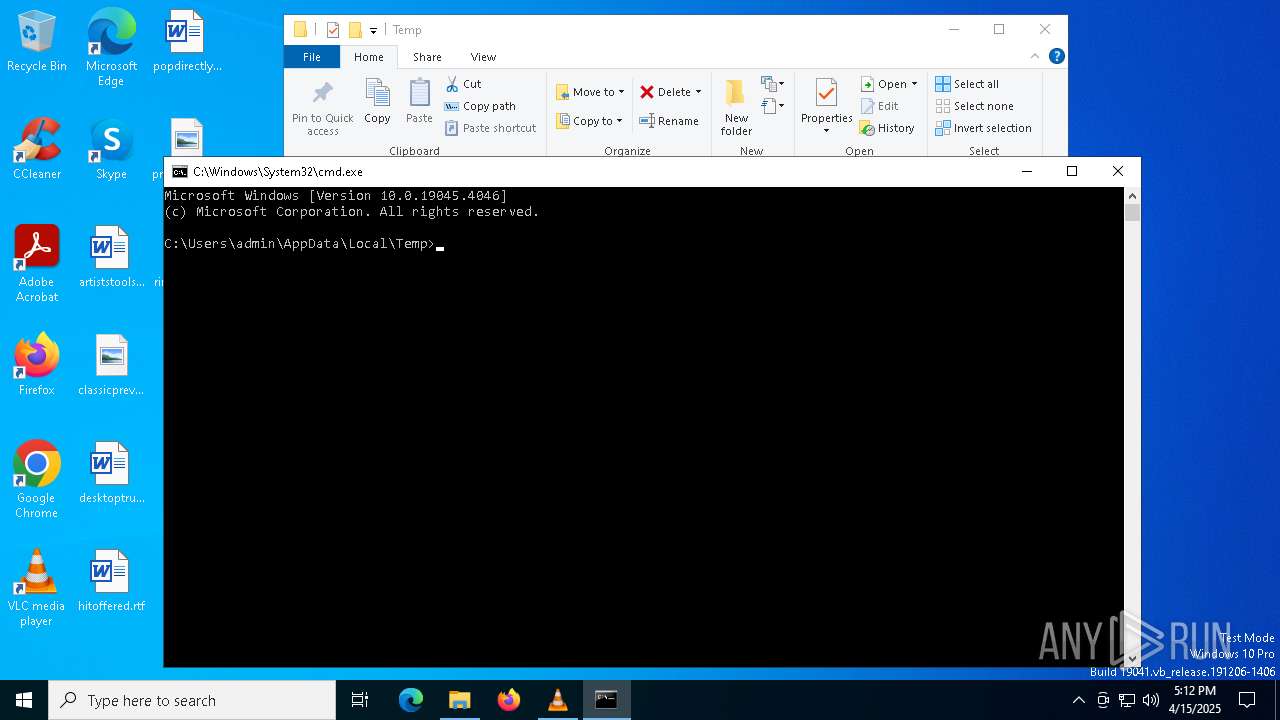
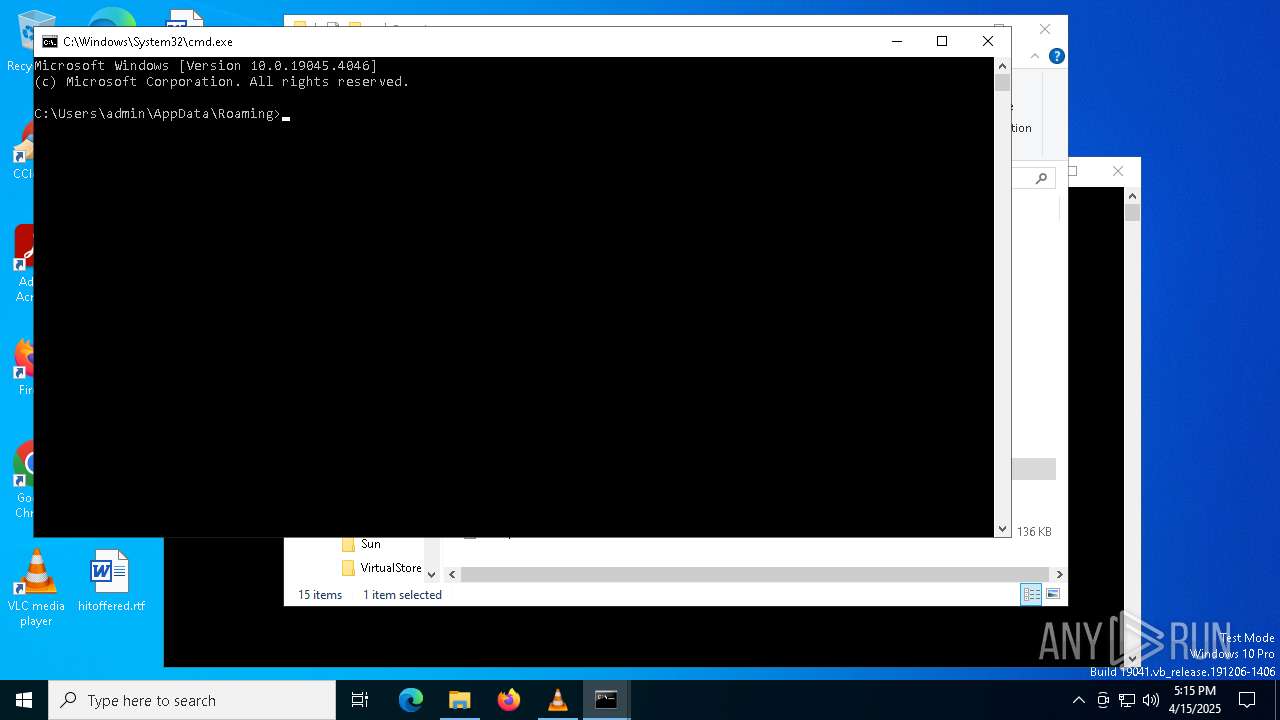
| File name: | ~.tmp |
| Full analysis: | https://app.any.run/tasks/133e48d3-65b8-456d-9f89-66ef922c73dd |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 17:10:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (8696), with CRLF line terminators |
| MD5: | 1DDAB156B9FD709FF8FE61FFA2AFB789 |
| SHA1: | F3626FDAB000C6C634569B95683FD8CF1B2934BB |
| SHA256: | 290863999FD0713841DD7CE2BEC725CEE3F5A467A5DE00F819B2471867BFB105 |
| SSDEEP: | 1536:x0Y6Iij7lm5LxFAHUhpDqxVsOca0GrcFvQYfpy7zdz3G4GD4IuaIJ7fJpZycaCT2:x+KUzxJ3qNRYGr |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1184)
- wscript.exe (PID: 5576)
Creates a new folder (SCRIPT)
- wscript.exe (PID: 1184)
- wscript.exe (PID: 5576)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 1184)
- wscript.exe (PID: 5576)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- vlc.exe (PID: 7476)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1184)
- wscript.exe (PID: 5576)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1184)
- wscript.exe (PID: 5576)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 1184)
- wscript.exe (PID: 5576)
Executes application which crashes
- wscript.exe (PID: 1184)
- wscript.exe (PID: 5576)
The process creates files with name similar to system file names
- WerFault.exe (PID: 5308)
- WerFault.exe (PID: 6516)
INFO
Reads the computer name
- vlc.exe (PID: 7476)
Reads the software policy settings
- slui.exe (PID: 7660)
- slui.exe (PID: 7264)
Checks supported languages
- vlc.exe (PID: 7476)
Manual execution by a user
- cmd.exe (PID: 5404)
- cmd.exe (PID: 5528)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 7968)
The process uses Lua
- vlc.exe (PID: 7476)
Creates files or folders in the user directory
- WerFault.exe (PID: 5308)
- WerFault.exe (PID: 6516)
Checks proxy server information
- slui.exe (PID: 7264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
153
Monitored processes
17
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | wscript.exe //e:vbscript ~.tmp | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2148 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5308 | C:\WINDOWS\system32\WerFault.exe -u -p 1184 -s 1088 | C:\Windows\System32\WerFault.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5404 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\~.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5528 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\~.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | wscript.exe //e:vbscript ~.tmp | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | C:\WINDOWS\system32\WerFault.exe -u -p 5576 -s 1056 | C:\Windows\System32\WerFault.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 003
Read events
6 003
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
6
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5308 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_wscript.exe_158a35e2ae135cb5cc23185ec7683ce9a8c4ad0_2a4c609f_0db6b573-0cae-4e2b-b786-060c58d8f646\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6516 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_wscript.exe_158a35e2ae135cb5cc23185ec7683ce9a8c4ad0_2a4c609f_3ff2ee79-300d-45b8-84f1-77d4ea083d5e\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7476 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | text | |
MD5:B3CA23F00CA5AE7C23D201028FD35F07 | SHA256:129881635A9977A861E1EC021954D73D83B20DA24EB3DF977F7F6C538433D90F | |||
| 5308 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER94A8.tmp.WERInternalMetadata.xml | binary | |
MD5:FBBC7E85F2D0D3FE2697C3A6F87A81FC | SHA256:7F808DE4590A340EC0148E11D222E80840198EC7BDE46C2E078465A43AB52008 | |||
| 5308 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER94B8.tmp.xml | xml | |
MD5:5CD313A68D0F6C1F8936335959803C3D | SHA256:D1553CE0D6A877D02E83DE08F805A01C9FB6EF944B91607BBD98CF2886CECEB5 | |||
| 5308 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\wscript.exe.1184.dmp | binary | |
MD5:54F3CBBF61C211186602BCAD4D3BFFDD | SHA256:F5512556C9B5E5B66FDB70B0CA6B96274B26651D267A9AB33053DA31DAA877F6 | |||
| 6516 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA306.tmp.WERInternalMetadata.xml | binary | |
MD5:E89D7616FB8F2930F921C8D7B619AEEE | SHA256:E8E607FB6B910409B0DED6D1657507B63E8F85CCE7560063BC615796FB5B0B9B | |||
| 6516 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA278.tmp.dmp | binary | |
MD5:FCB95ECF19EB373EECCBA1A160BD9974 | SHA256:562220A209F2D0B195CBAA580DA93DC75CA9FEE70FCC9AEA59FAF15E2B760C40 | |||
| 6516 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\wscript.exe.5576.dmp | binary | |
MD5:47C820F5B912C23D4821DF02108EEAB4 | SHA256:0469A90128BA4FB1F8C1EBD487CF333622833EB6D812CDDC7EA3B817737D1D7E | |||
| 6516 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERA326.tmp.xml | xml | |
MD5:8C6A3DA193B15CA8368D680329DD265D | SHA256:270D01B883542182A43505D6124A51939EF5DDFADBD0477E7533D83FBB776F47 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7316 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7316 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7316 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7316 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |