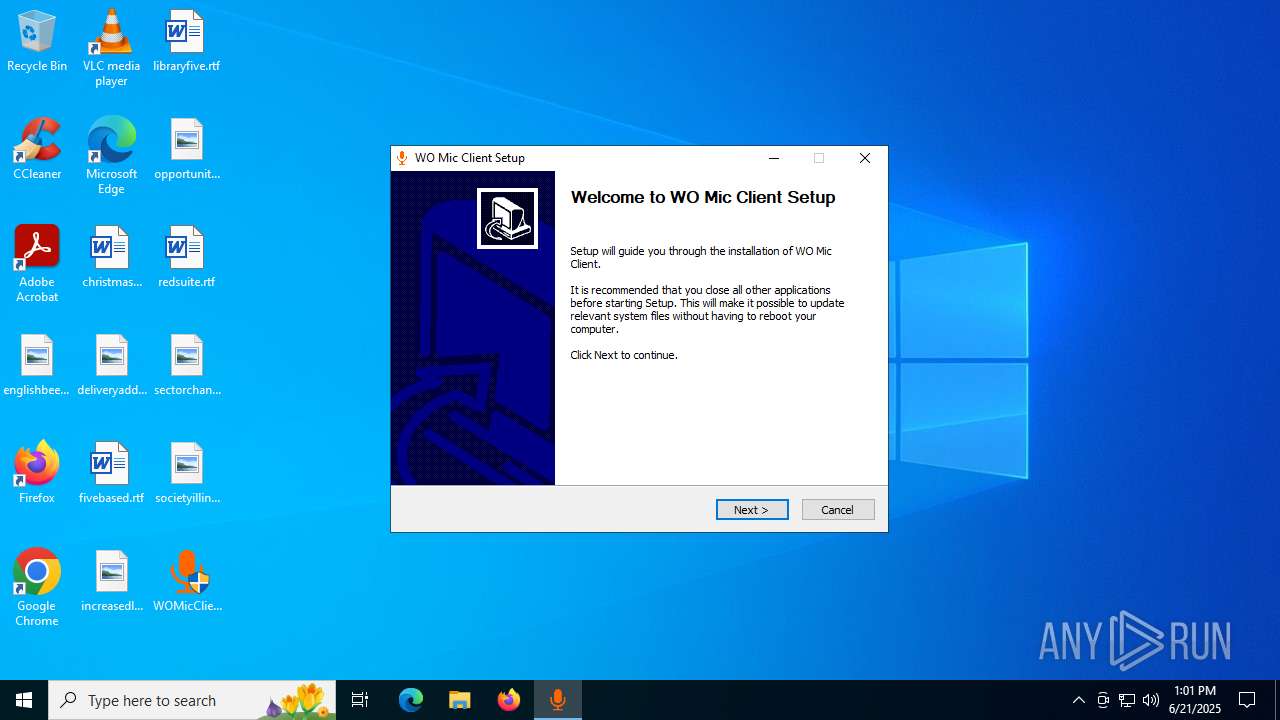
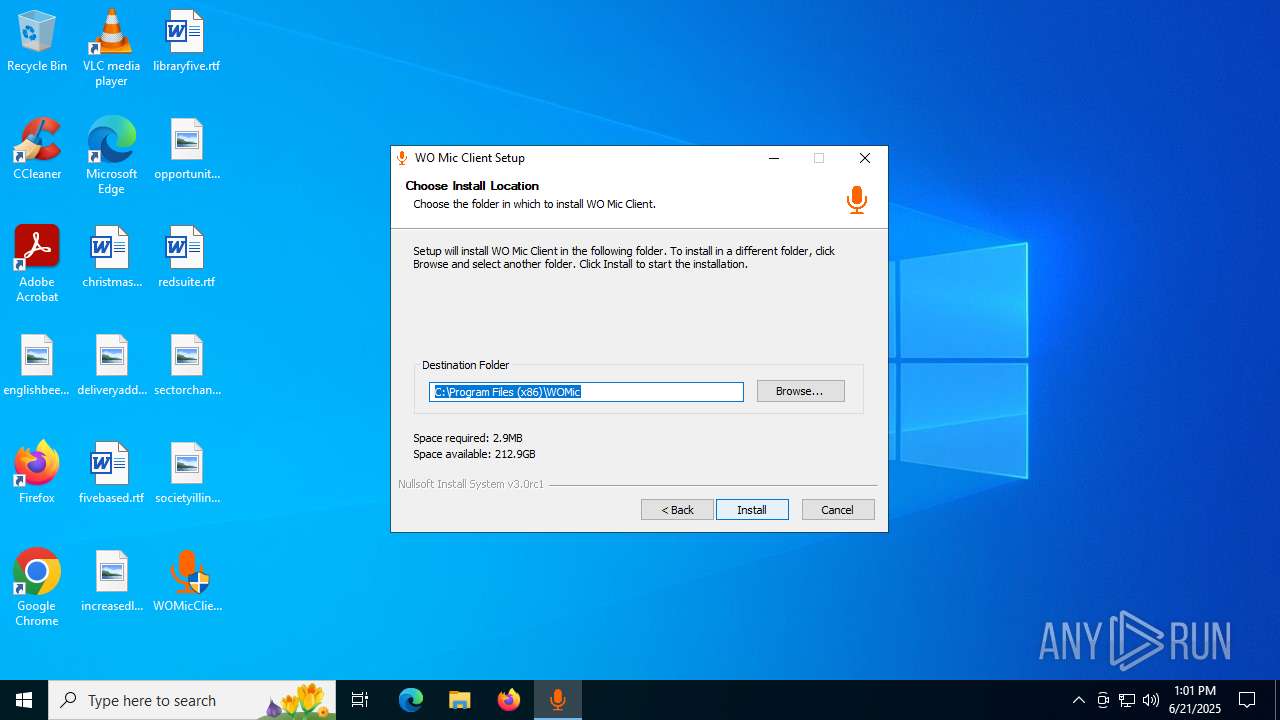
| File name: | WOMicClientSetup6.1.exe |
| Full analysis: | https://app.any.run/tasks/82a6df7f-a027-4bd4-b82f-4b5314770790 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 13:01:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 880A67CBF94ED6D3C62045C1CF2D94A8 |
| SHA1: | 9BB67C0B515234A1452E2DCC48CBCC332A631F15 |
| SHA256: | 28F0C4F4EC7135700BDA47F306AD121BD48E866F16F8C74224FE4E0CF06A9C26 |
| SSDEEP: | 49152:8e3Mscof5Ch/NTpd94tc6dnsZMV9lN7XvpArIpnRR+eAkrh6YdBPdZCaZ7Yczu9L:8e8snmN1d94t5dMWBpAyRR+AF6YdEYzA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- WOMicClientSetup6.1.exe (PID: 5424)
- drvinst.exe (PID: 7020)
- devcon.exe (PID: 2192)
- drvinst.exe (PID: 2368)
The process creates files with name similar to system file names
- WOMicClientSetup6.1.exe (PID: 5424)
Malware-specific behavior (creating "System.dll" in Temp)
- WOMicClientSetup6.1.exe (PID: 5424)
Drops a system driver (possible attempt to evade defenses)
- WOMicClientSetup6.1.exe (PID: 5424)
- devcon.exe (PID: 2192)
- drvinst.exe (PID: 7020)
- drvinst.exe (PID: 2368)
Creates a software uninstall entry
- WOMicClientSetup6.1.exe (PID: 5424)
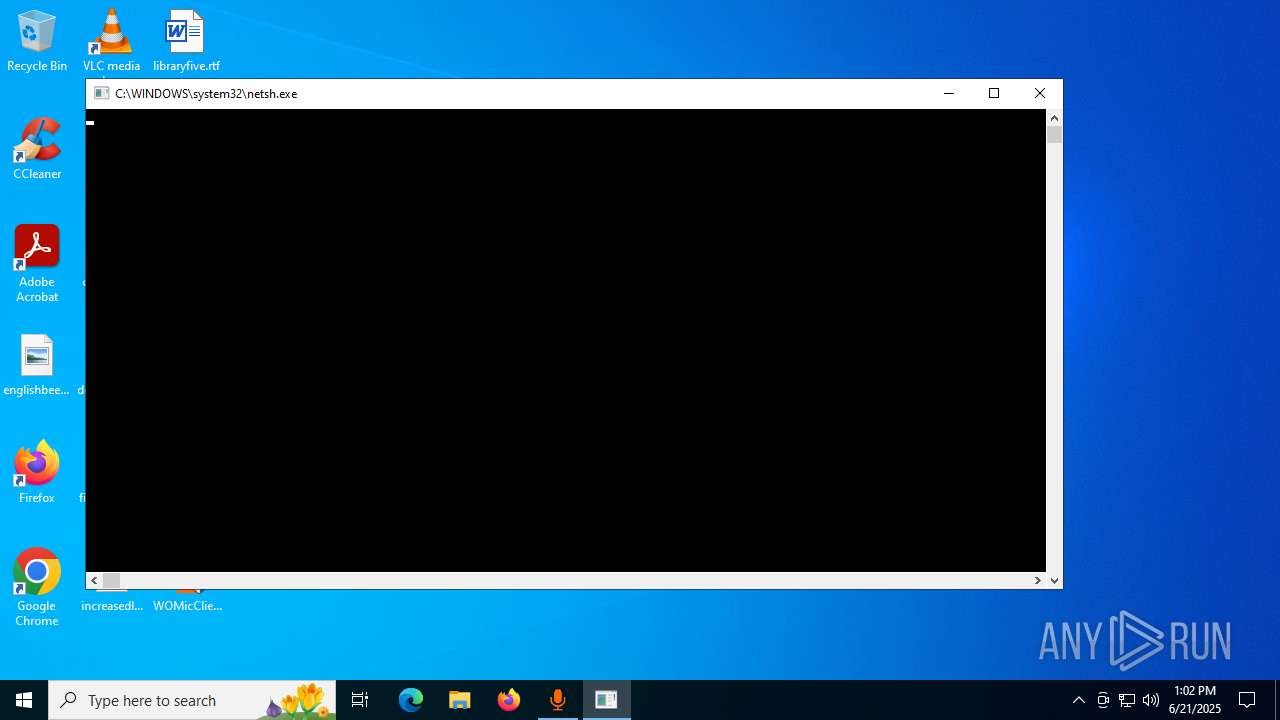
Uses NETSH.EXE to add a firewall rule or allowed programs
- WOMicClientSetup6.1.exe (PID: 5424)
Creates files in the driver directory
- drvinst.exe (PID: 7020)
- drvinst.exe (PID: 2368)
Creates or modifies Windows services
- drvinst.exe (PID: 2368)
There is functionality for taking screenshot (YARA)
- WOMicClientSetup6.1.exe (PID: 5424)
Reads security settings of Internet Explorer
- devcon.exe (PID: 2192)
Process drops legitimate windows executable
- WOMicClientSetup6.1.exe (PID: 5424)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4116)
- updater.exe (PID: 4104)
Application launched itself
- updater.exe (PID: 4104)
INFO
Create files in a temporary directory
- WOMicClientSetup6.1.exe (PID: 5424)
- devcon.exe (PID: 2192)
Checks supported languages
- WOMicClientSetup6.1.exe (PID: 5424)
- drvinst.exe (PID: 7020)
- devcon.exe (PID: 2192)
- drvinst.exe (PID: 2368)
- PLUGScheduler.exe (PID: 4116)
- updater.exe (PID: 5132)
- updater.exe (PID: 4104)
Creates files in the program directory
- WOMicClientSetup6.1.exe (PID: 5424)
- PLUGScheduler.exe (PID: 4116)
Reads the computer name
- WOMicClientSetup6.1.exe (PID: 5424)
- devcon.exe (PID: 2192)
- drvinst.exe (PID: 7020)
- drvinst.exe (PID: 2368)
- updater.exe (PID: 4104)
- PLUGScheduler.exe (PID: 4116)
The sample compiled with english language support
- WOMicClientSetup6.1.exe (PID: 5424)
- devcon.exe (PID: 2192)
- drvinst.exe (PID: 7020)
- drvinst.exe (PID: 2368)
Reads the machine GUID from the registry
- devcon.exe (PID: 2192)
- drvinst.exe (PID: 7020)
Reads the software policy settings
- drvinst.exe (PID: 7020)
- devcon.exe (PID: 2192)
Creates files or folders in the user directory
- WOMicClientSetup6.1.exe (PID: 5424)
Process checks whether UAC notifications are on
- updater.exe (PID: 4104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:03 20:19:02+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25600 |
| InitializedDataSize: | 186368 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x32a0 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
289
Monitored processes
17
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | devcon.exe install womic.inf Root\WOMic | C:\Program Files (x86)\WOMic\driver\devcon.exe | WOMicClientSetup6.1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Device Console Exit code: 0 Version: 10.0.19041.685 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2368 | DrvInst.exe "2" "211" "ROOT\MEDIA\0000" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:ed86ca11fdcda04c:InstallWOMic:2.1.0.0:root\womic," "46d27e6e7" "00000000000001D8" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4104 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4104 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 4116 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4860 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | devcon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5132 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x274,0x2a4,0x11dc460,0x11dc46c,0x11dc478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 5424 | "C:\Users\admin\Desktop\WOMicClientSetup6.1.exe" | C:\Users\admin\Desktop\WOMicClientSetup6.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
9 460
Read events
8 816
Write events
637
Delete events
7
Modification events
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | language |
Value: 1033 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | bluetoothDevice |
Value: 00:00:00:00:00:00 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | hotSpot |
Value: 192.168.43.1 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | wifiAddr |
Value: 192.168.1.101 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | transport |
Value: 3 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | bufferSize |
Value: 5 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | controlPort |
Value: 8125 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | mediaPort |
Value: 60000 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | x |
Value: 500 | |||
| (PID) Process: | (5424) WOMicClientSetup6.1.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Wolicheng\WOMic |
| Operation: | write | Name: | y |
Value: 200 | |||
Executable files
21
Suspicious files
52
Text files
3
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5424 | WOMicClientSetup6.1.exe | C:\Users\admin\AppData\Local\Temp\nsn6F26.tmp\nsDialogs.dll | executable | |
MD5:D6C3DD680C6467D07D730255D0EE5D87 | SHA256:AEDB5122C12037BCF5C79C2197D1474E759CF47C67C37CDB21CF27428854A55B | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Users\admin\AppData\Local\Temp\nsn6F26.tmp\LangDLL.dll | executable | |
MD5:174708997758321CF926B69318C6C3F5 | SHA256:F577B66492E97C7B8BF515398D8DEB745ABAFD74F56FC03E67FCE248EBBEB873 | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\WO Mic Client\WO Mic Client.lnk | binary | |
MD5:C3ABEE478B3598B471A236DF38FBF02E | SHA256:1476089C2690E019E60ECF97A2396A4C1310F07DE6679F8E800B99DB1B1F2DED | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Program Files (x86)\WOMic\adb.exe | executable | |
MD5:884242FB6CBBEC1F7711B946EF669E0E | SHA256:65210CB4139672B53ACAA2222B1005D036B0B02C437AA47E0E7B616FAB0E2F6F | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Users\admin\AppData\Local\Temp\nsn6F26.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Program Files (x86)\WOMic\Resource_en.dll | executable | |
MD5:47390427993916E5BDD3DF6FD3407E8A | SHA256:3538BA720D59DE7F4A4F34BD16E7834DF954216D1F090920BF2E1CB2BF2CFDD5 | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Users\admin\AppData\Local\Temp\nsn6F26.tmp\nsExec.dll | executable | |
MD5:01E76FE9D2033606A48D4816BD9C2D9D | SHA256:EE052FD5141BF769B841846170AABF0D7C2BB922C74C623C3F109344534F7A70 | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Program Files (x86)\WOMic\Resource_cn.dll | executable | |
MD5:DE6489770C4B410B3A5F1A46A854C409 | SHA256:A89CBBB5FE79E83816A9B4E440334955F9B135FFD55F7EAE0D6B192B175AE3EA | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Program Files (x86)\WOMic\AdbWinUsbApi.dll | executable | |
MD5:0E24119DAF1909E398FA1850B6112077 | SHA256:25207C506D29C4E8DCEB61B4BD50E8669BA26012988A43FBF26A890B1E60FC97 | |||
| 5424 | WOMicClientSetup6.1.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\WO Mic Client\Uninstall.lnk | binary | |
MD5:1557272AFE5CC4C4B0E65610BF37A9AA | SHA256:019ADEE251ED9A019B8AB2E9D18C5C6F46B50E2899D4E74BA0BC989B846F1629 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
83
TCP/UDP connections
70
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3732 | RUXIMICS.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.128:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
3732 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 403 | 95.101.149.131:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
— | — | POST | 403 | 95.101.149.131:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
— | — | POST | 403 | 95.101.149.131:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
— | — | POST | 403 | 95.101.149.131:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
— | — | POST | 403 | 95.101.149.131:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3732 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3732 | RUXIMICS.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
3732 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |