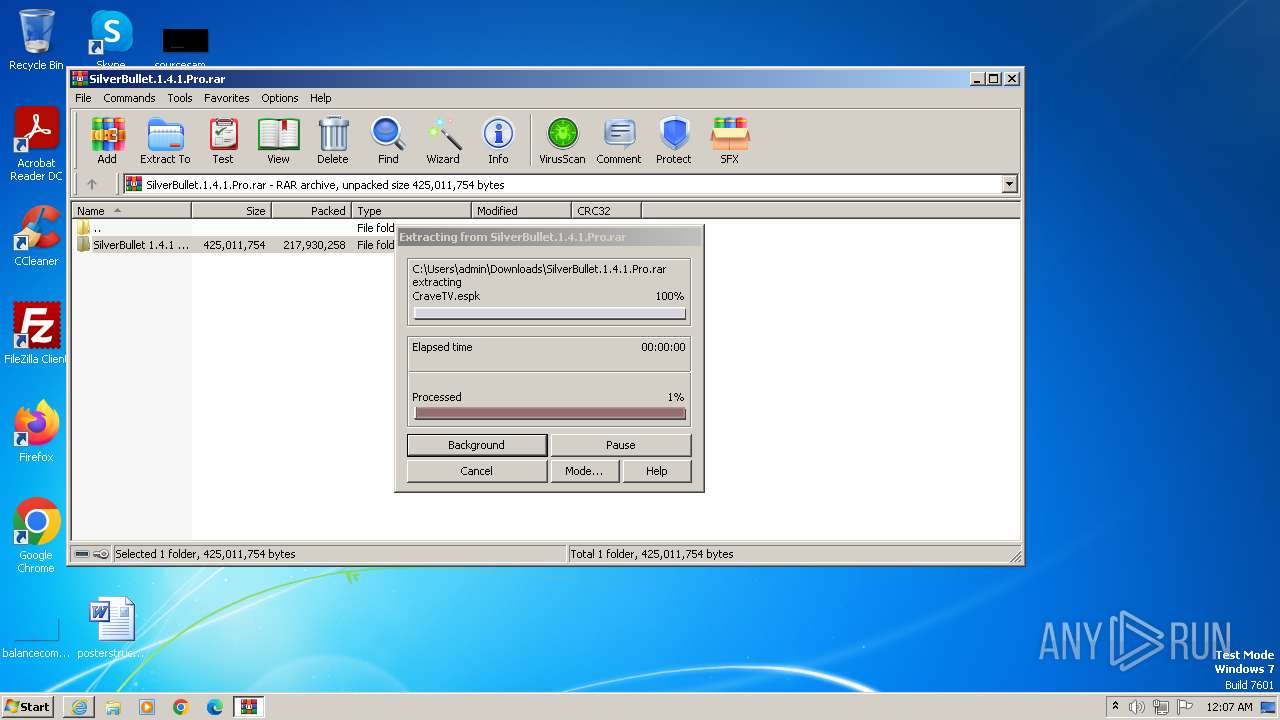
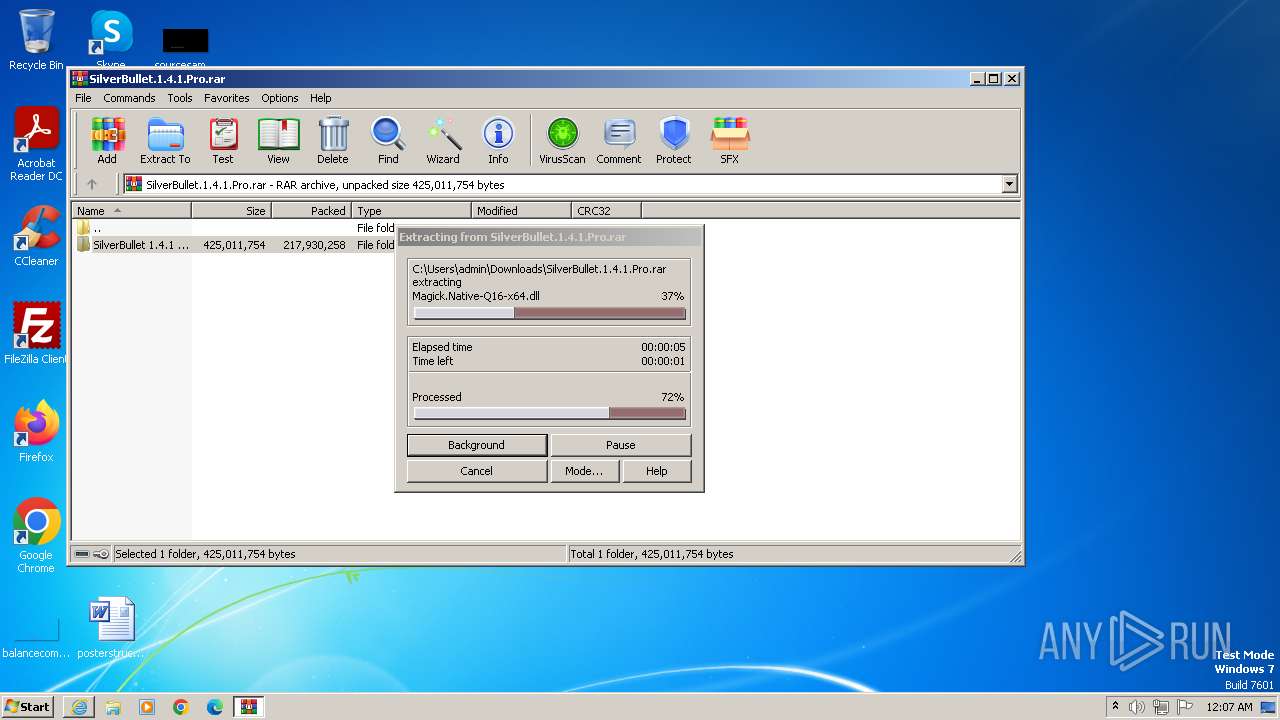
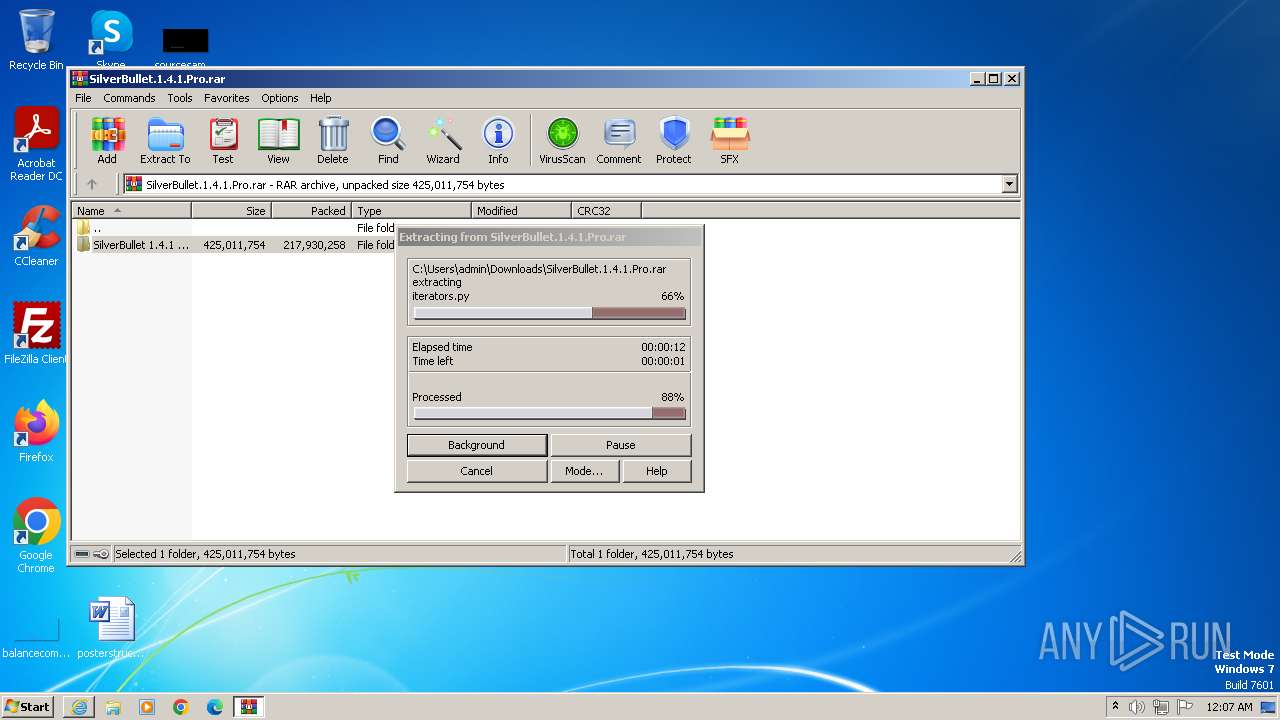
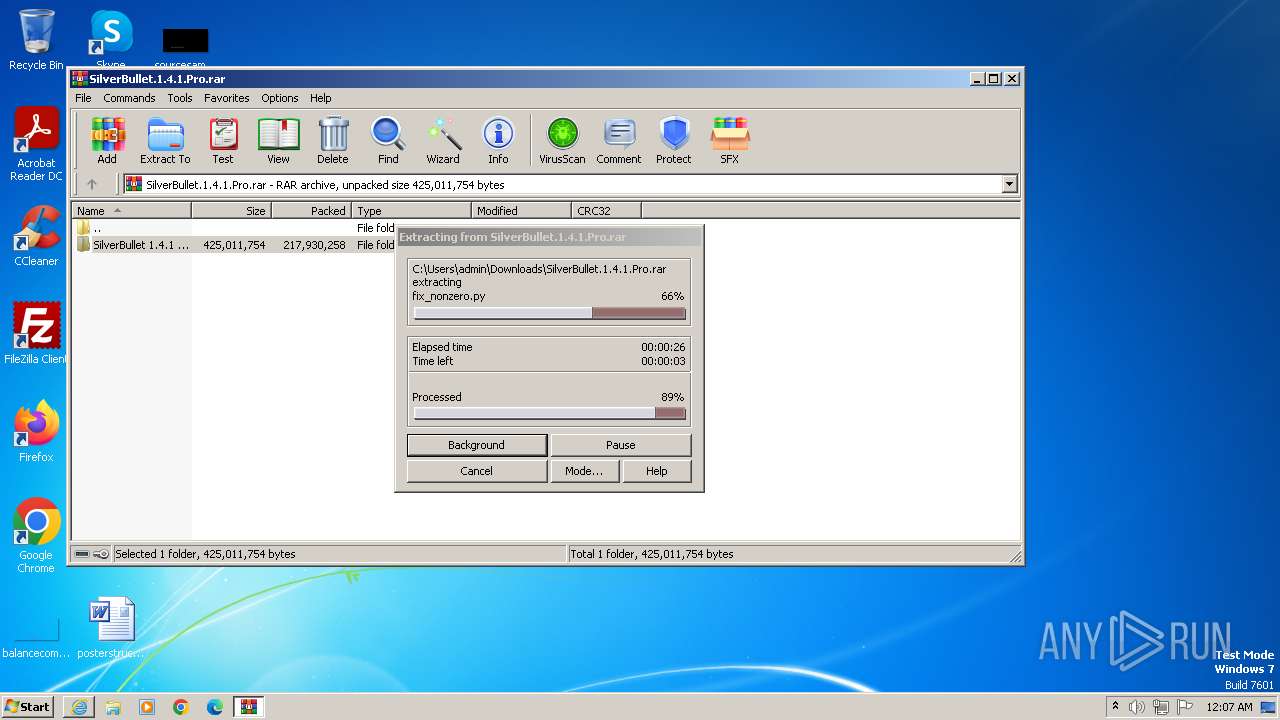
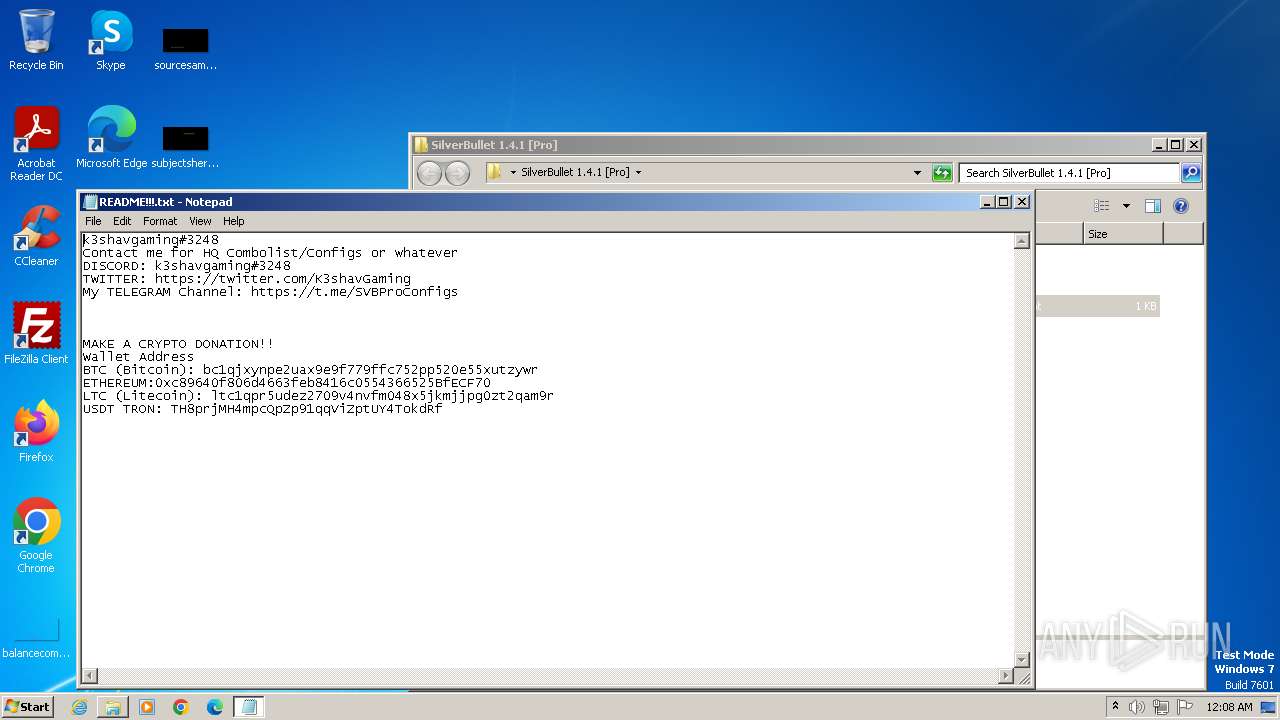
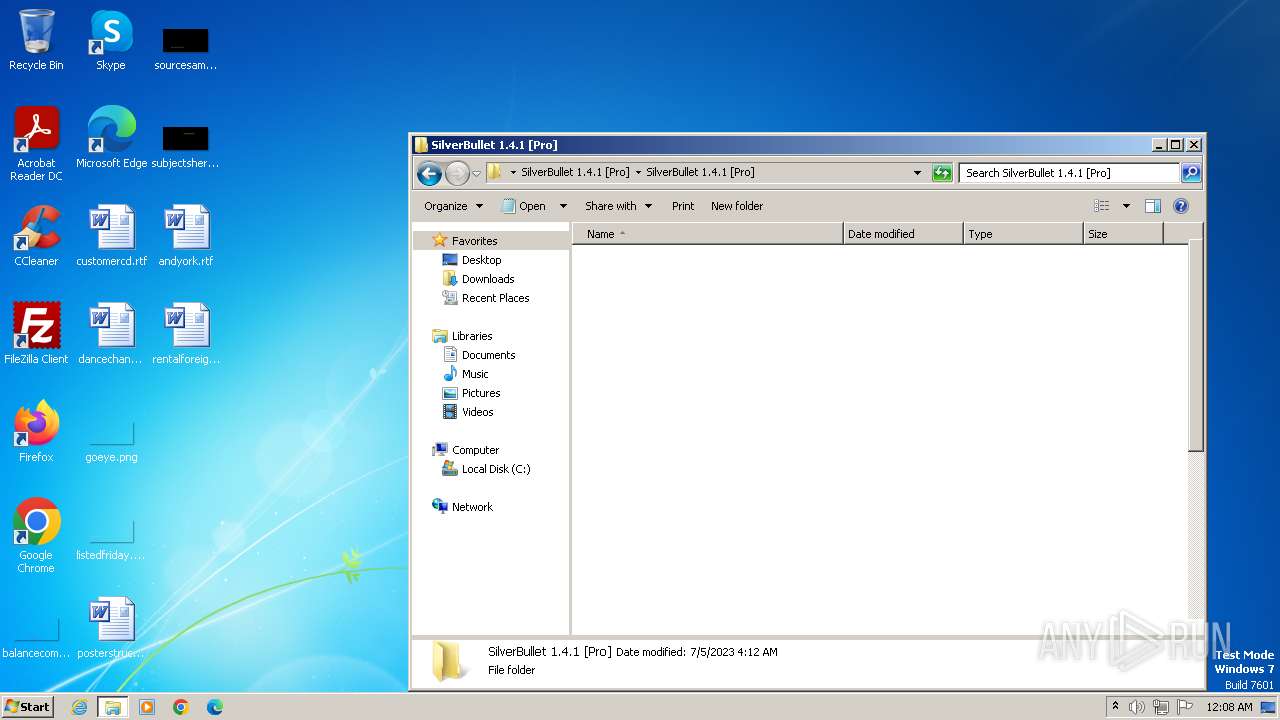
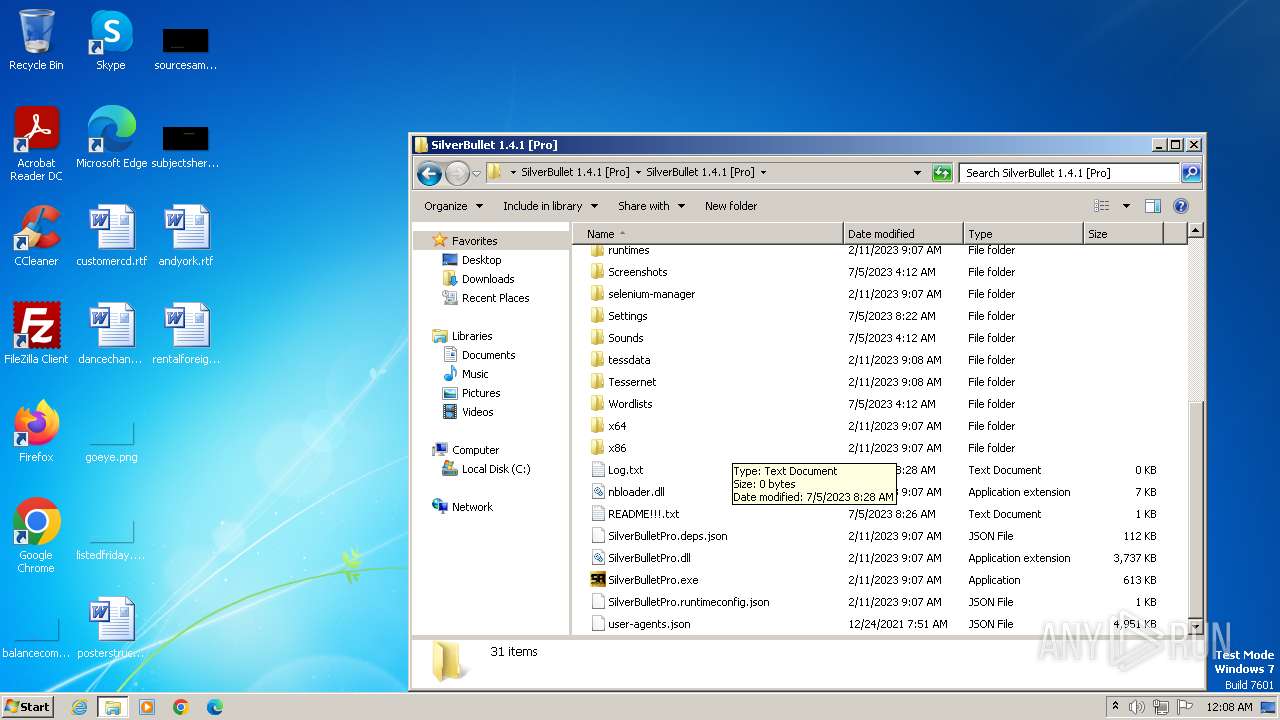
| URL: | https://github.com/K3shavGaming/SILVERBULLET-PRO/releases/download/1.4.1/SilverBullet.1.4.1.Pro.rar |
| Full analysis: | https://app.any.run/tasks/17f0f396-3949-4fd7-9881-4de34e8781d5 |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2023, 00:05:06 |
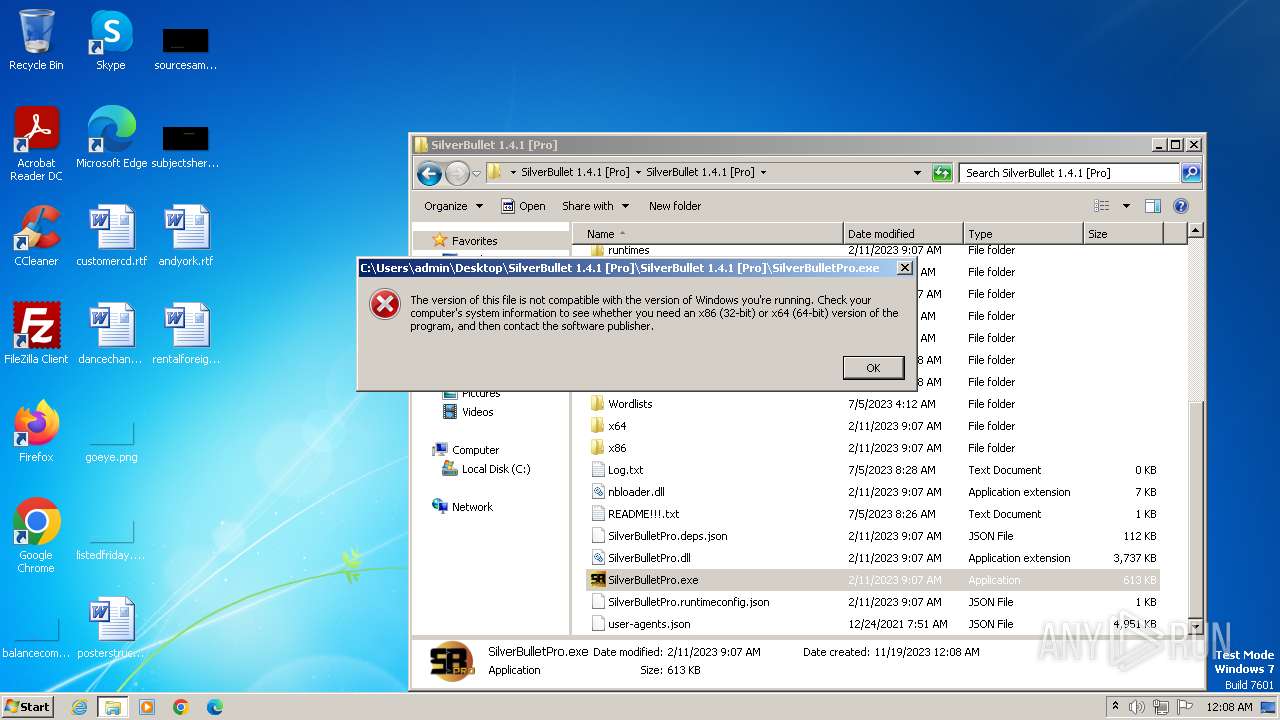
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 33404518481D7F004895892878F58B218CE407E3 |
| SHA256: | 28DECE3387C07A3B370C5B342C7370C41FA25C0229F8417863C7C45C3D4B8CFC |
| SSDEEP: | 3:N8tEdBuepMXcpgxxKXdkCUPTORgyLdC+:2urqXcp0x06ith3 |
MALICIOUS
Actions looks like stealing of personal data
- WinRAR.exe (PID: 3724)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3724)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3528)
Application launched itself
- iexplore.exe (PID: 3440)
Checks supported languages
- wmpnscfg.exe (PID: 3528)
The process uses the downloaded file
- WinRAR.exe (PID: 3724)
- iexplore.exe (PID: 3440)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3528)
Manual execution by a user
- wmpnscfg.exe (PID: 3528)
- notepad.exe (PID: 2116)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2116 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\SilverBullet 1.4.1 [Pro]\README!!!.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3196 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3440 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3440 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/K3shavGaming/SILVERBULLET-PRO/releases/download/1.4.1/SilverBullet.1.4.1.Pro.rar" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3528 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3724 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\SilverBullet.1.4.1.Pro.rar" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
18 859
Read events
18 776
Write events
79
Delete events
4
Modification events
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
233
Suspicious files
240
Text files
684
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:7EF5CDAC99918E6611547BD710D3F5EC | SHA256:0C577C6CDD3ECB25B20BF16F8CFB1BD2F39F49BC29F89862E5F798EECAC91918 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:52C4678ADF7FD874C15F1541FBD4F2D5 | SHA256:B747EF20D5AA4A6D87D718AD6783C3E8F2B2DCF7A1DF9D381B2CE63C332A0336 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:4E89FF65FEBBE85EB87A9FF6C966F732 | SHA256:588C88606CF2C453834949FC43D0143A1FC8F99A4D2A4EDC2A495384E7886479 | |||
| 3440 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\SilverBullet.1.4.1.Pro[1].rar | compressed | |
MD5:212366DCBD8CE34E47FBBA8C7D9F4446 | SHA256:11257B44A91B6885DE51A11D55099120763ED6821E85F9CE168D6A4DCF46E3C9 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:E622EBBEF96A71194289851AAC1D16B7 | SHA256:9ECCD986AF135B1CBAFBFD9CED08A488B513FDD459FDCEE8C868474BE23E7D20 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:4B66A3C233BB98718D5FA759FB29D1E6 | SHA256:F25A159117A880E3F4DCEDB57118B361612A1783404564E64A3514A4241FBFF2 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:F26BAD1D295B9AF7DABE0EC8C8E7F8BC | SHA256:47C3FE287055DBDB712A497CC85EA05F92D8B2D329DE4F09D3A732EDBA00DABE | |||
| 3440 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:369068B806FE477A411DA67E352F7250 | SHA256:123A03C6AFA848B5932E9D378419A388C2D2E59B18B6AF14877BB045659AE9C6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
21
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3196 | iexplore.exe | GET | 200 | 46.228.146.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?24ee352ddd3d4dea | unknown | compressed | 4.66 Kb | unknown |
3196 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
3196 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 312 b | unknown |
3196 | iexplore.exe | GET | 200 | 46.228.146.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?127045ce466871b6 | unknown | compressed | 4.66 Kb | unknown |
3196 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
3440 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3440 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3440 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
3440 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3196 | iexplore.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3196 | iexplore.exe | 46.228.146.128:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
3196 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3196 | iexplore.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | unknown |
3440 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3440 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
objects.githubusercontent.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |