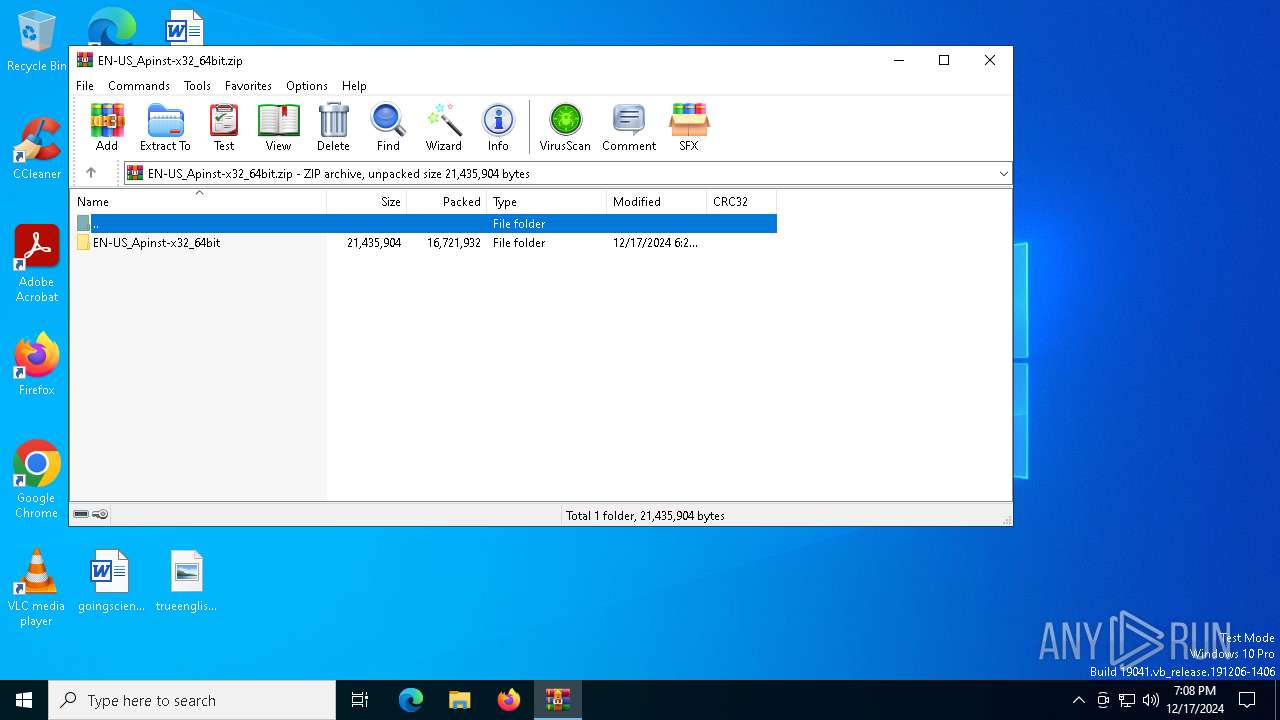
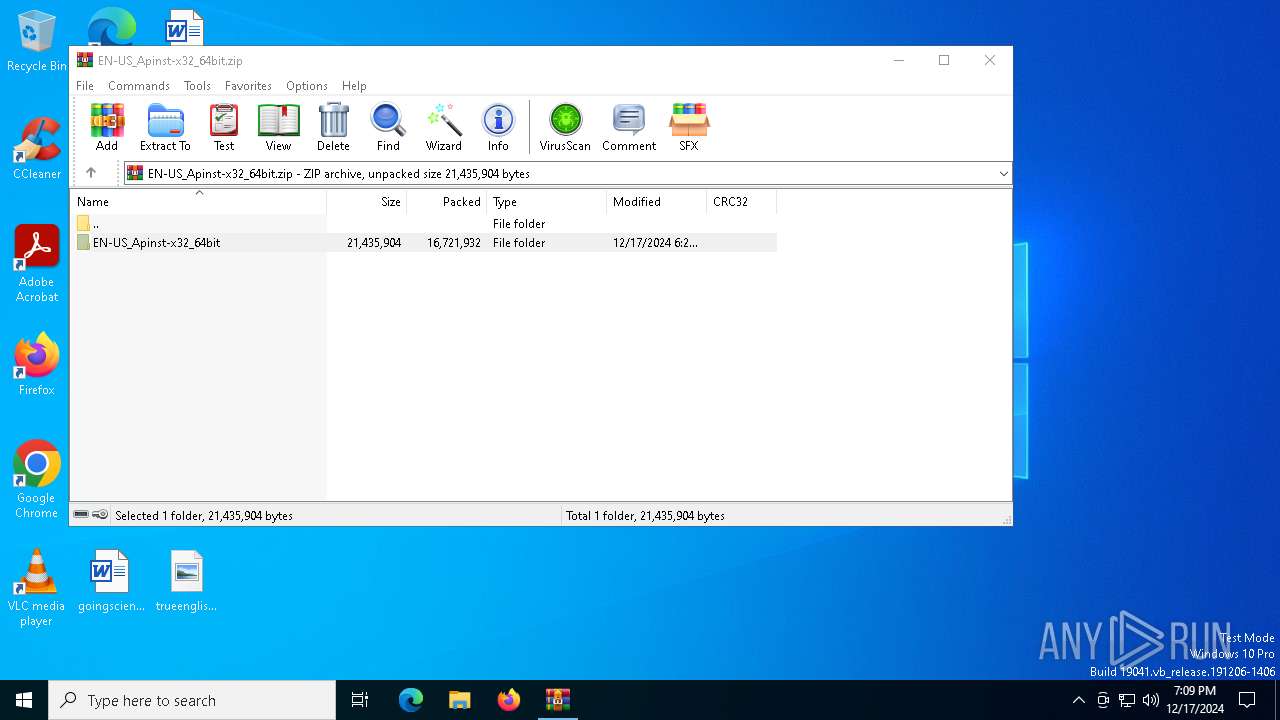
| File name: | EN-US_Apinst-x32_64bit.zip |
| Full analysis: | https://app.any.run/tasks/5f8f2418-91b4-4317-82ce-9b14640472ed |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2024, 19:08:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 24B3C01FDE22167ADA7503FE8439FB0F |
| SHA1: | 48C4E0BC61DDB67E154FFD683F50CE8BB8534AFE |
| SHA256: | 28B7F43BCE8BDD98C7ADF838667FA3F05241C430C19B97C283A53DBE1935F1AD |
| SSDEEP: | 196608:jy89uPhV6ZALjISDnCQGv6N1NVy5U9jUu:jR9uPhKALjIynjGvY1y5URp |
MALICIOUS
No malicious indicators.SUSPICIOUS
Loads Python modules
- Setup.exe (PID: 6308)
- Setup.exe (PID: 3812)
Generic archive extractor
- WinRAR.exe (PID: 6440)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6440)
INFO
Checks supported languages
- Setup.exe (PID: 6308)
- Setup.exe (PID: 3812)
Manual execution by a user
- Setup.exe (PID: 3812)
- Setup.exe (PID: 6308)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6440)
The process uses the downloaded file
- WinRAR.exe (PID: 6440)
The sample compiled with english language support
- WinRAR.exe (PID: 6440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:17 19:29:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | EN-US_Apinst-x32_64bit/ |
Total processes
131
Monitored processes
4
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
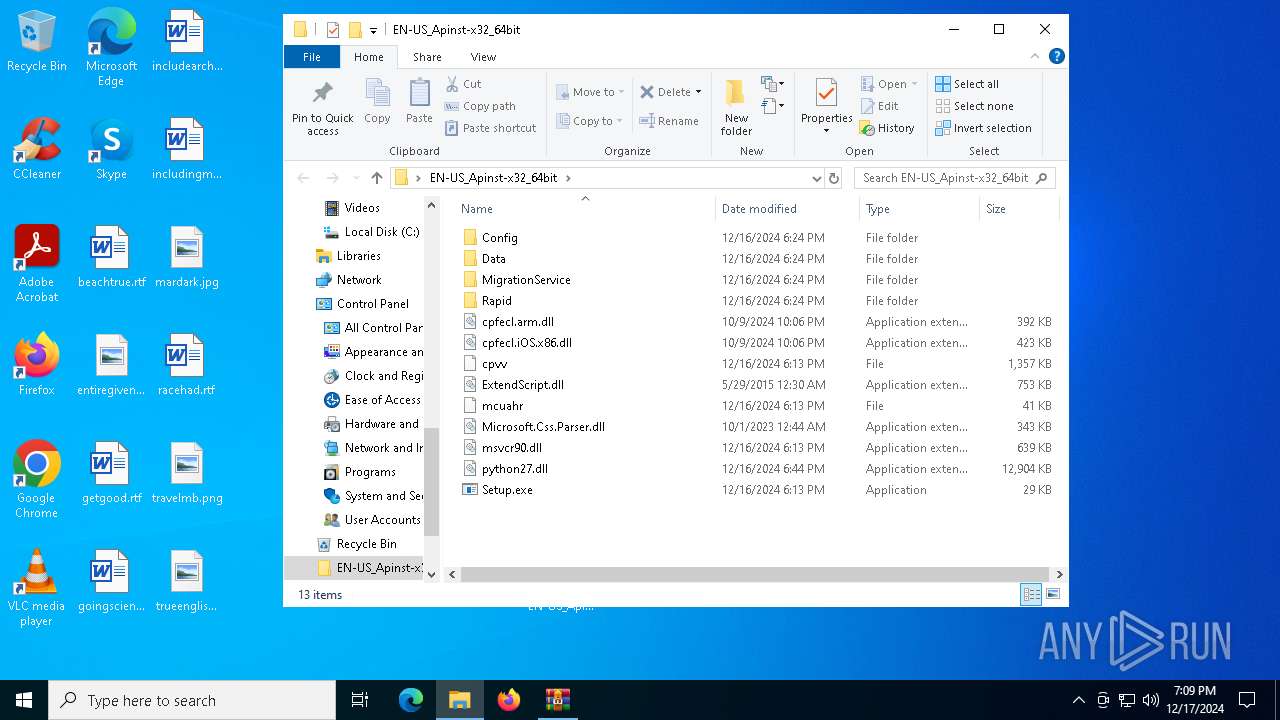
| 3812 | "C:\Users\admin\Desktop\EN-US_Apinst-x32_64bit\Setup.exe" | C:\Users\admin\Desktop\EN-US_Apinst-x32_64bit\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6308 | "C:\Users\admin\Desktop\EN-US_Apinst-x32_64bit\Setup.exe" | C:\Users\admin\Desktop\EN-US_Apinst-x32_64bit\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6440 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\EN-US_Apinst-x32_64bit.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7124 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 683
Read events
1 675
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EN-US_Apinst-x32_64bit.zip | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
12
Suspicious files
3
Text files
60
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\crash1.txt | html | |
MD5:61DECD7D28256AD2516CA0037BE7626F | SHA256:4279460ED2ADADAA640EB3BBB2B49CA2972CF78E600B14CC5F36BC054AD0EDB0 | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\FIND_XXX_REGISTRY_VIEW.txt | text | |
MD5:42E7D85A15B108C49BDF493562A0B57D | SHA256:918D49B3C7AB219CA3C2740EF25115CA5B7F78985AAE70487A2F675C870138E9 | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\CYRILLIC.TXT | text | |
MD5:FFA329FCA82694B8CB2981F98E44683B | SHA256:FB589EF667BC8A441630B830D48E1E38B1282228CF676A9934A2548E17DEA241 | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\COMPILE_PDB_NOTE.txt | text | |
MD5:459E482DB4EF2C93841C5A4A027AFFC2 | SHA256:5BA94580B96A7E9BF4417AA8A667AC5582577D73EF3E3E47C0B224B53D7497D9 | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\cpfecl.iOS.x86.dll | executable | |
MD5:ADACDD3A75919DA648B899C7B91874EB | SHA256:33F3FB246F7C6B367114C0276FB390C09B70E24F14B6D106C040FBBCF89A0BA2 | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\DisplayLanguageNames.be.txt | text | |
MD5:A5DDB28D6F58D13D63005AA329092328 | SHA256:720DFDD82ECBB10CEA5446AAF26ED0CB54C5938815683E86A47309D359DA2FAC | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\go1.16.txt | text | |
MD5:DF57A8B50121787CA106358AD3E93E2A | SHA256:5DD9794572BFC048724C393C4C8D0E3F50B3C589D33584D03A2F23242FEEC32A | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\Swedish.txt | text | |
MD5:C07810393930EDFBBBDBCA8A0F3A6B20 | SHA256:5AC4E6D56CE6B6A82A59610AA4AE174A1B4D638D605423CD4DACCB4501868AB2 | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\ft_ada.txt | text | |
MD5:EB856A17EF68B7C120EBF1A4B667EA7F | SHA256:D814B0CDF405243BF1E2E49BD9E7B59474CE4B89F6E853682F57858ADBE88A57 | |||
| 6440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6440.35024\EN-US_Apinst-x32_64bit\Config\build_relative_tmpdir.txt | text | |
MD5:36FE098201036E184BEF324D5505DDBF | SHA256:7B7454419B0936DC3EDE94AD04FC26BA6D16D2339C3C2849D5862A47DE272D47 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
33
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6620 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6620 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6148 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.30:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |