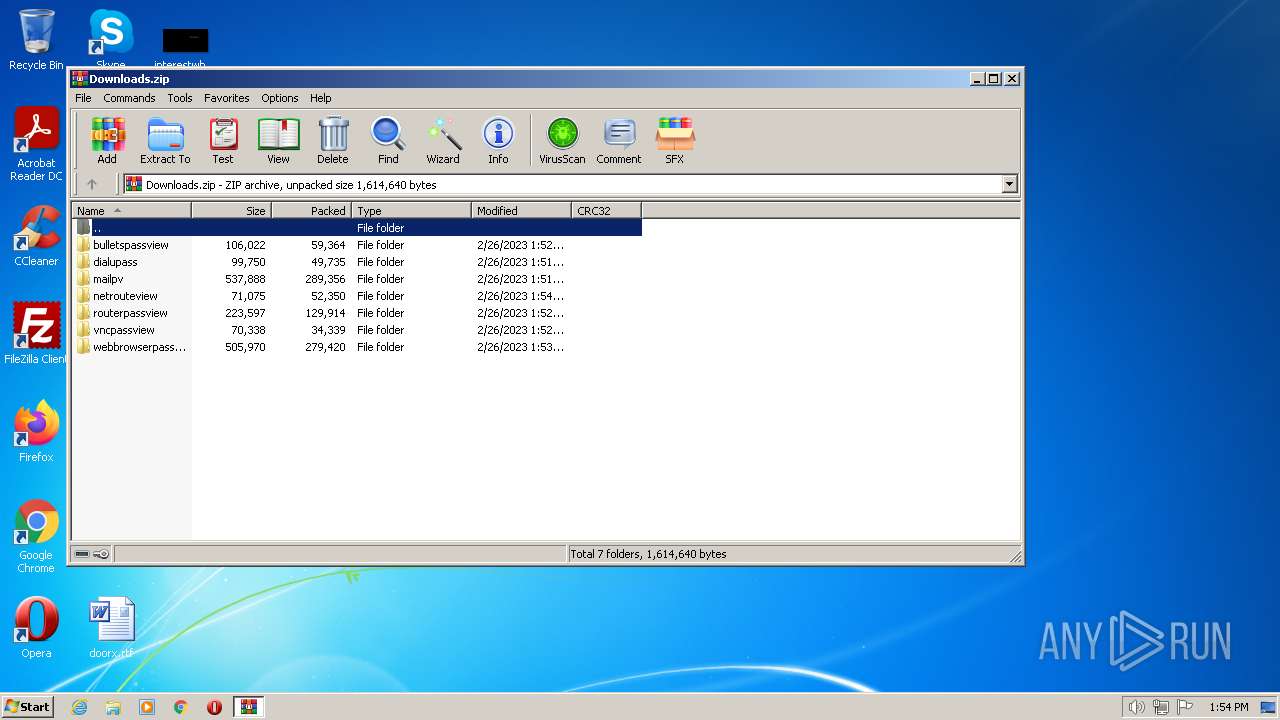
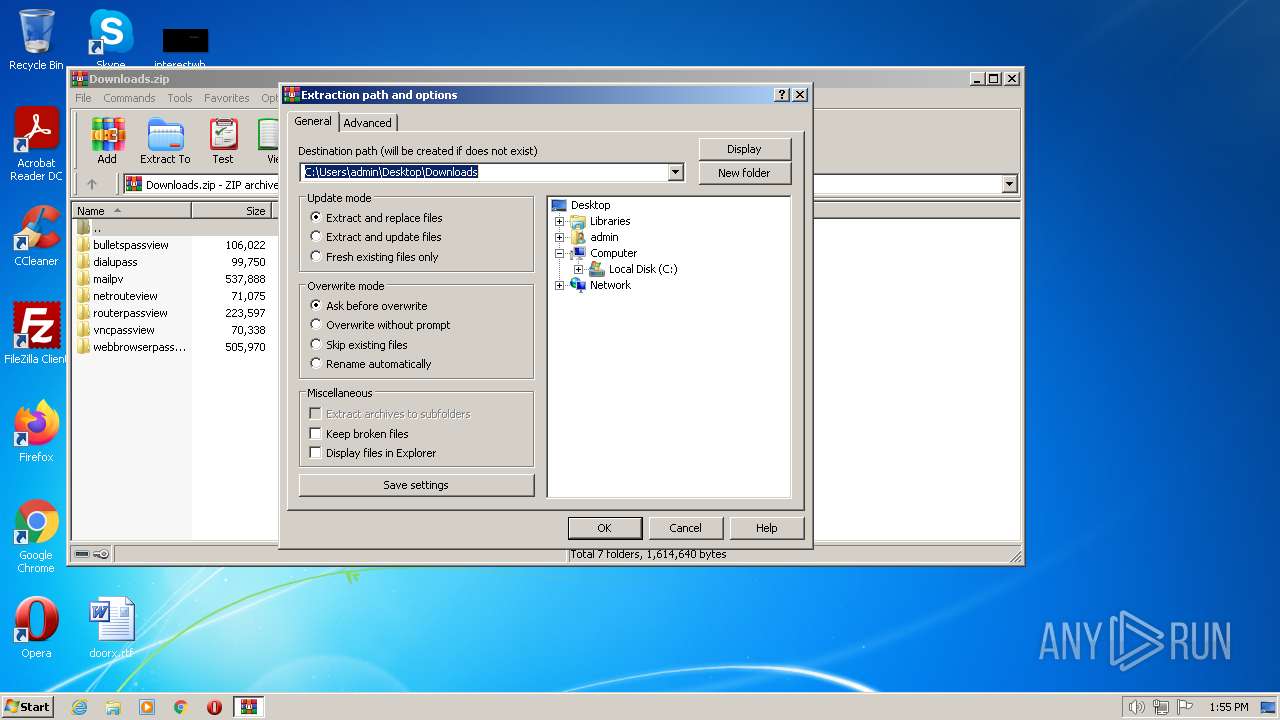
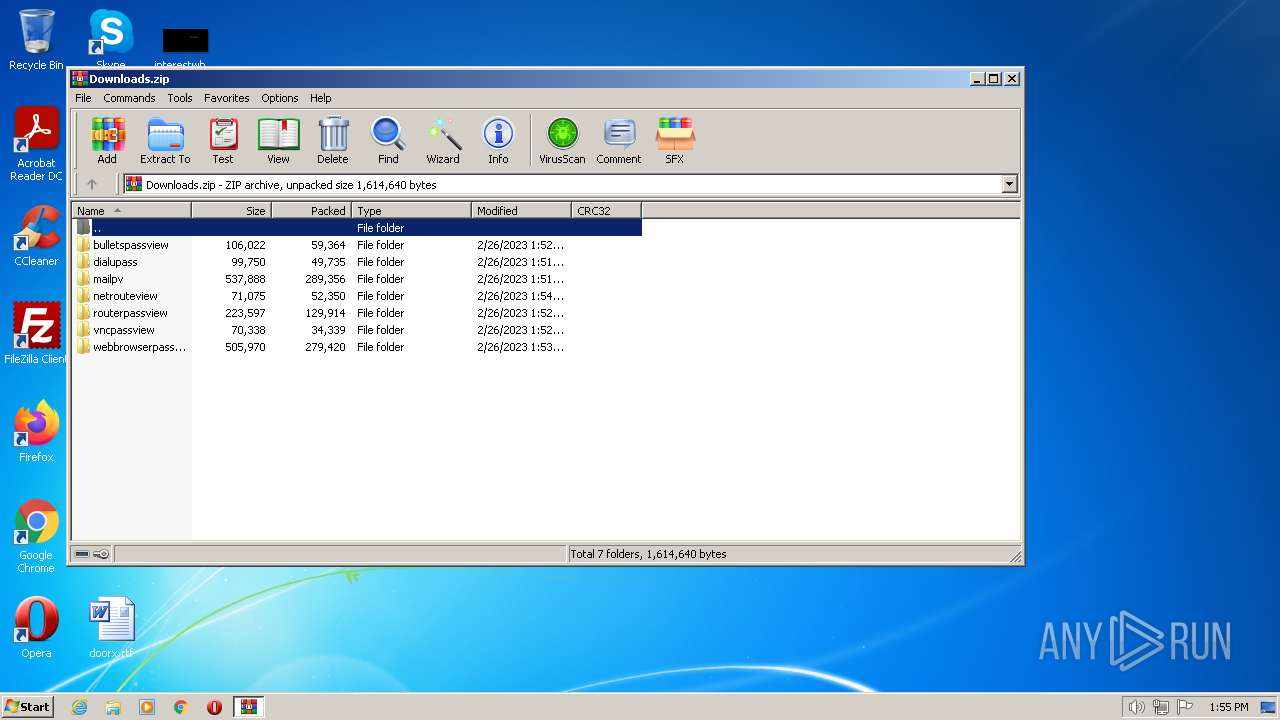
| File name: | Downloads.zip |
| Full analysis: | https://app.any.run/tasks/56dbf239-a6e4-4b9f-b90d-04b1e570663d |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2023, 13:54:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9DBB1905F440548C82E78D4C6618DE64 |
| SHA1: | 0E9E837A434D7E59F794AF6C9EAE8003340383B6 |
| SHA256: | 287375907E26B9FC8C31E72EC23F320815C5EC6A1628494C02EDB7F30F1AB654 |
| SSDEEP: | 12288:gVb1w//9cRa4GSxQmP4kFsz8zZD6u6I7HSD9g/g6nuonqOKUViyxDg9EzCde+Npq:o1vRa4+pzd590TqOYY84NzYuZNmPnSl3 |
MALICIOUS
Application was dropped or rewritten from another process
- Dialupass.exe (PID: 2420)
- Dialupass.exe (PID: 1772)
- BulletsPassView.exe (PID: 3380)
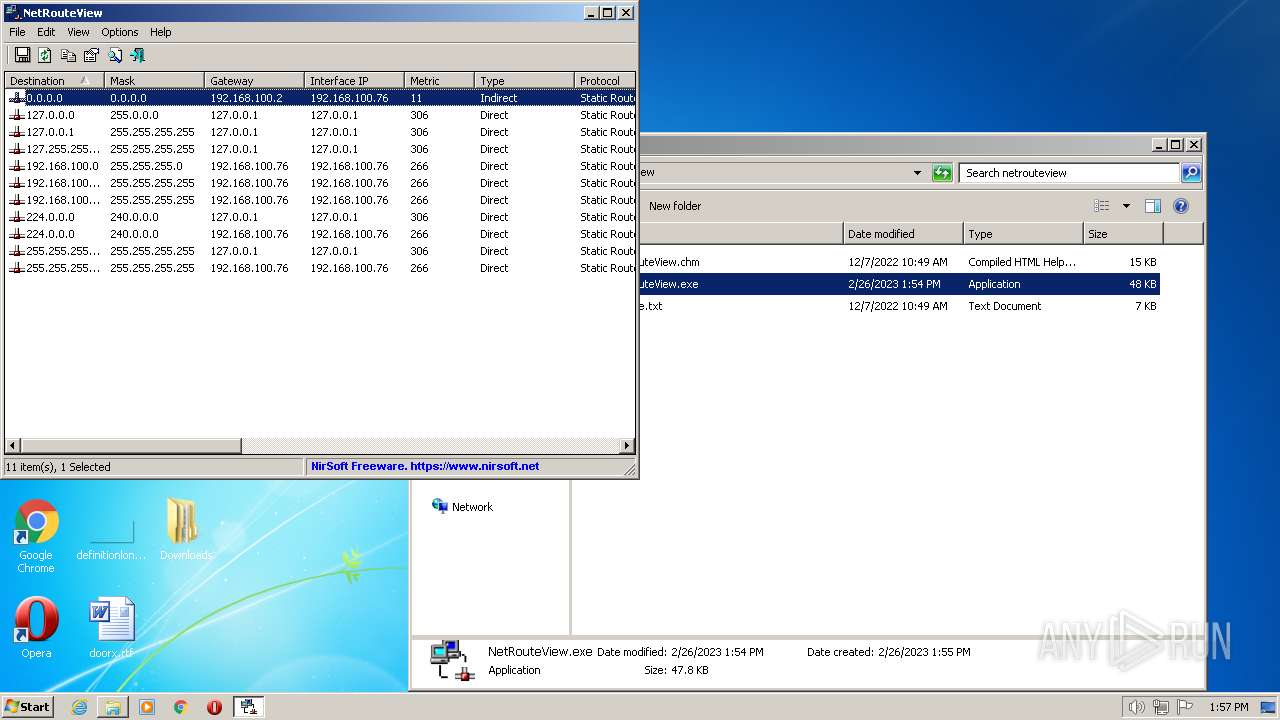
- NetRouteView.exe (PID: 3872)
- VNCPassView.exe (PID: 4040)
- RouterPassView.exe (PID: 2184)
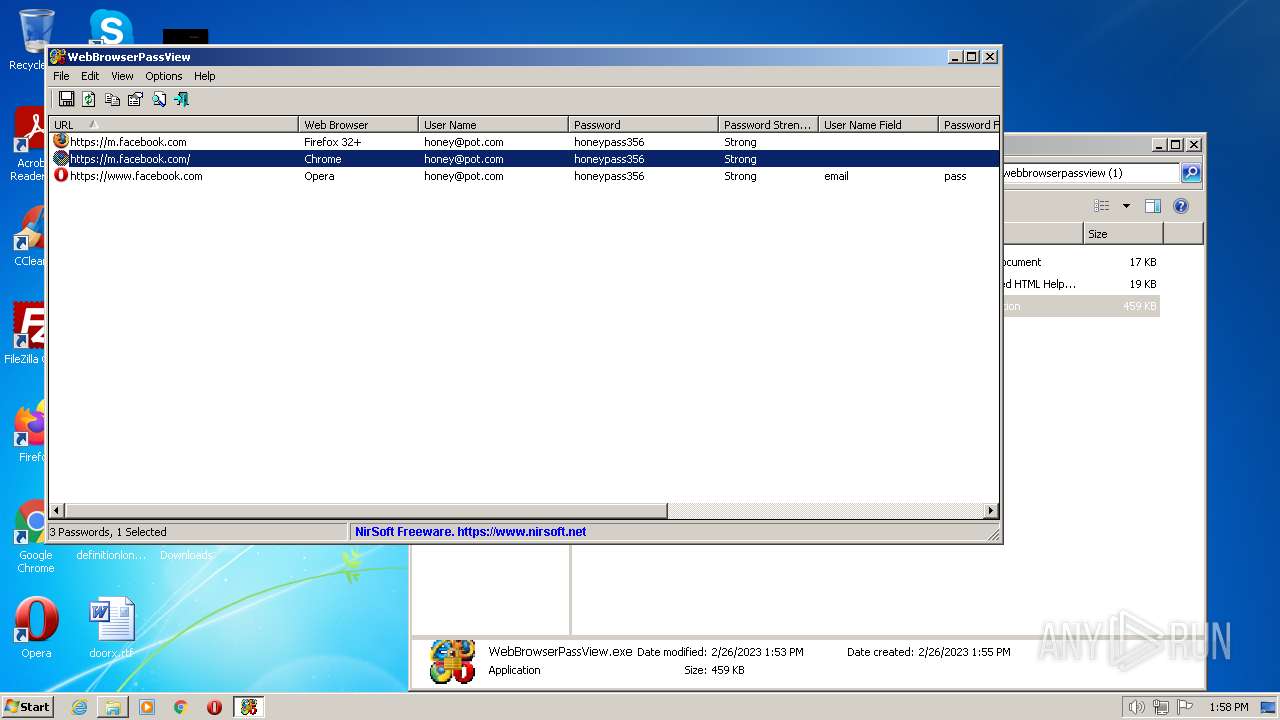
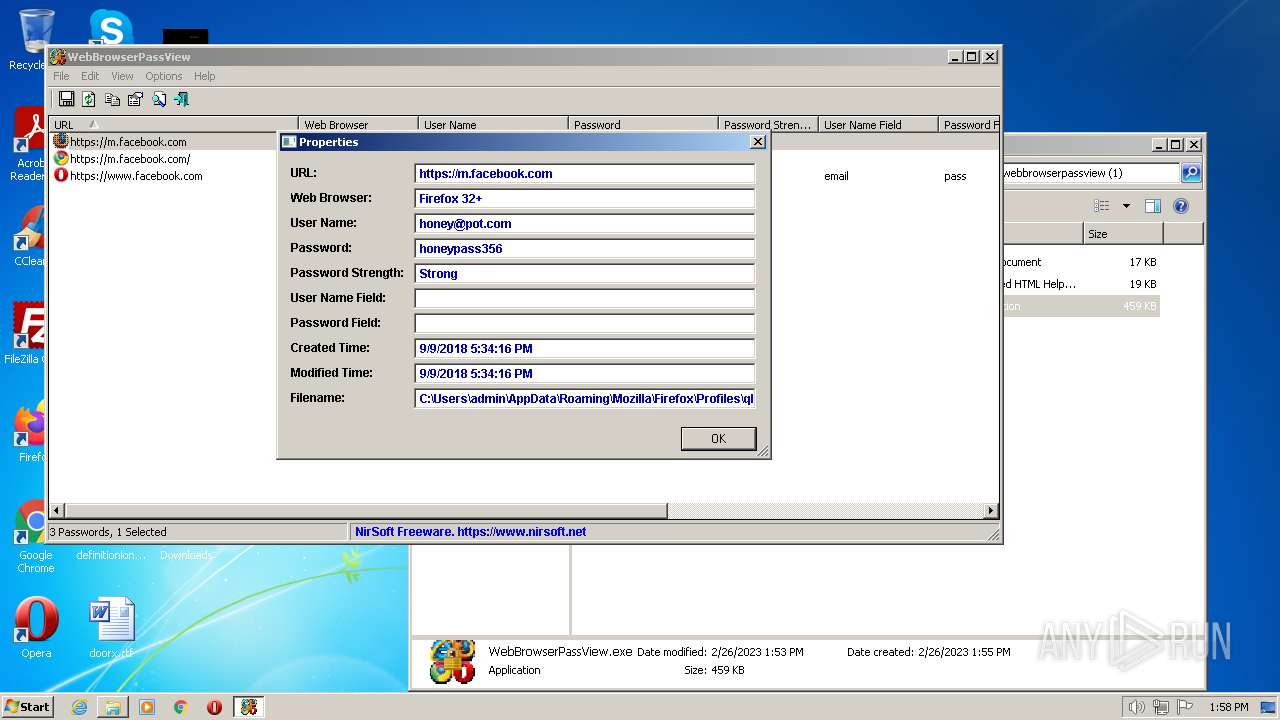
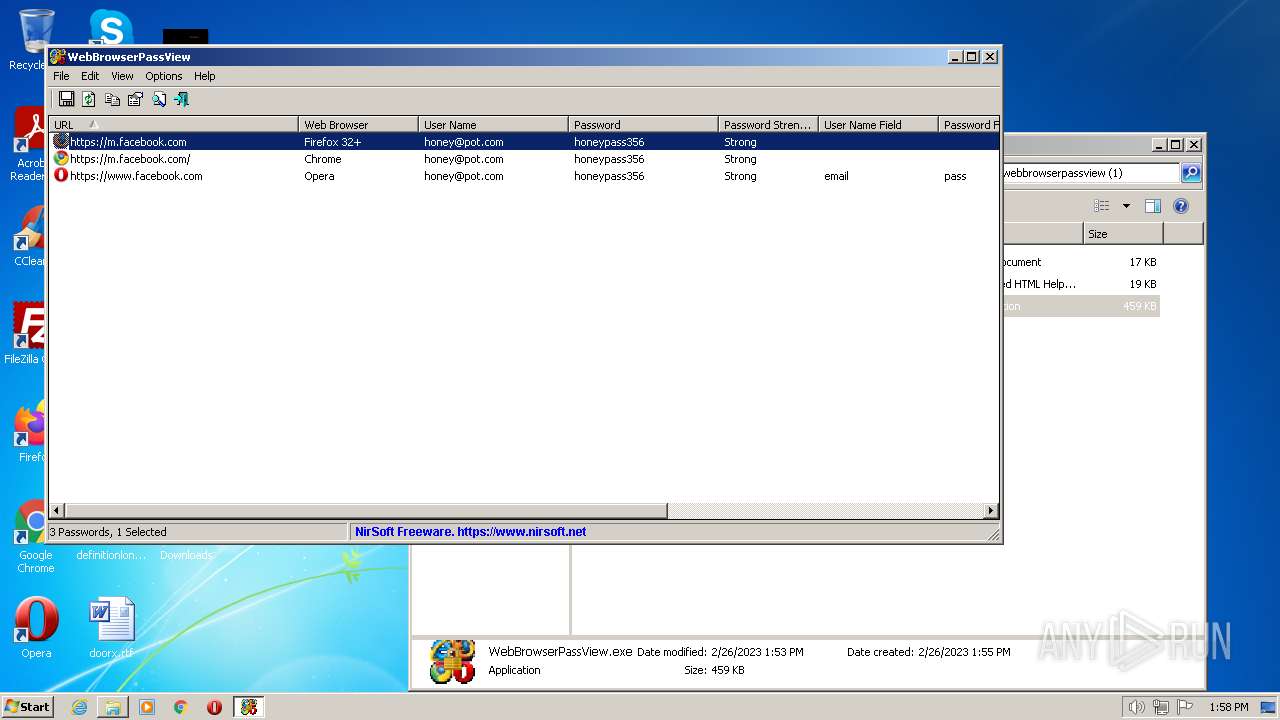
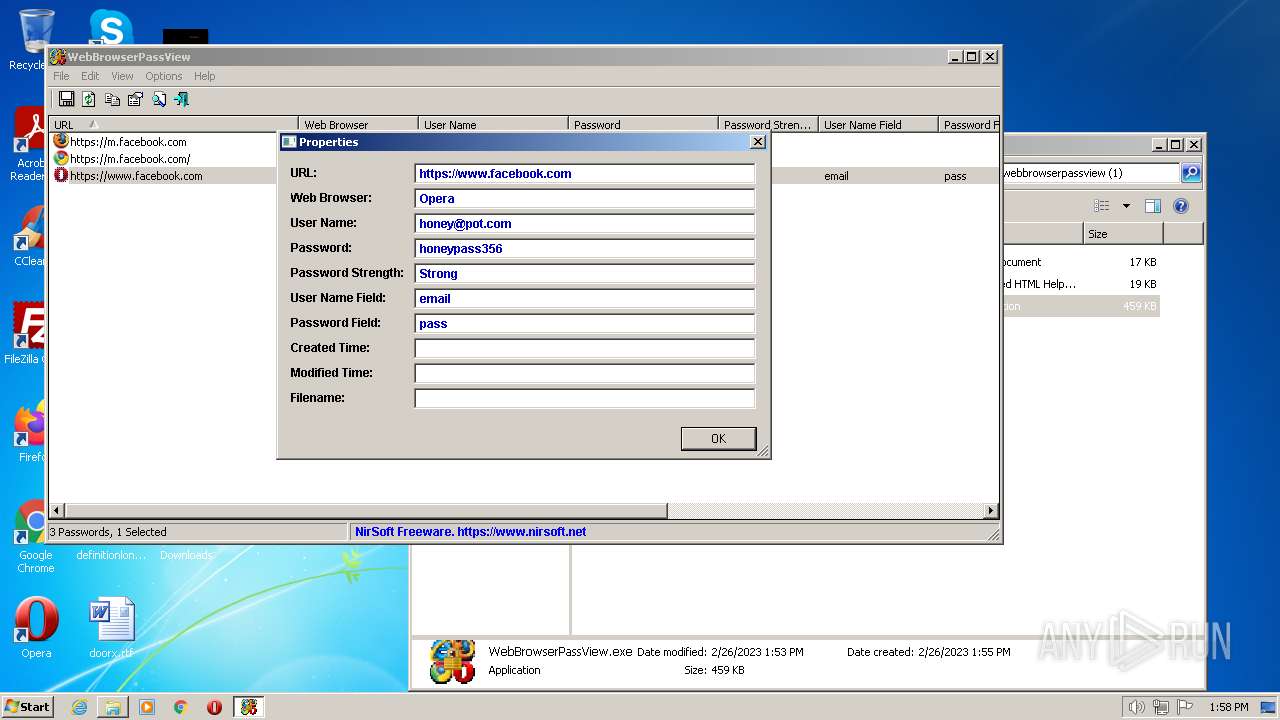
- WebBrowserPassView.exe (PID: 2492)
- mailpv.exe (PID: 1836)
Actions looks like stealing of personal data
- mailpv.exe (PID: 1836)
- WebBrowserPassView.exe (PID: 2492)
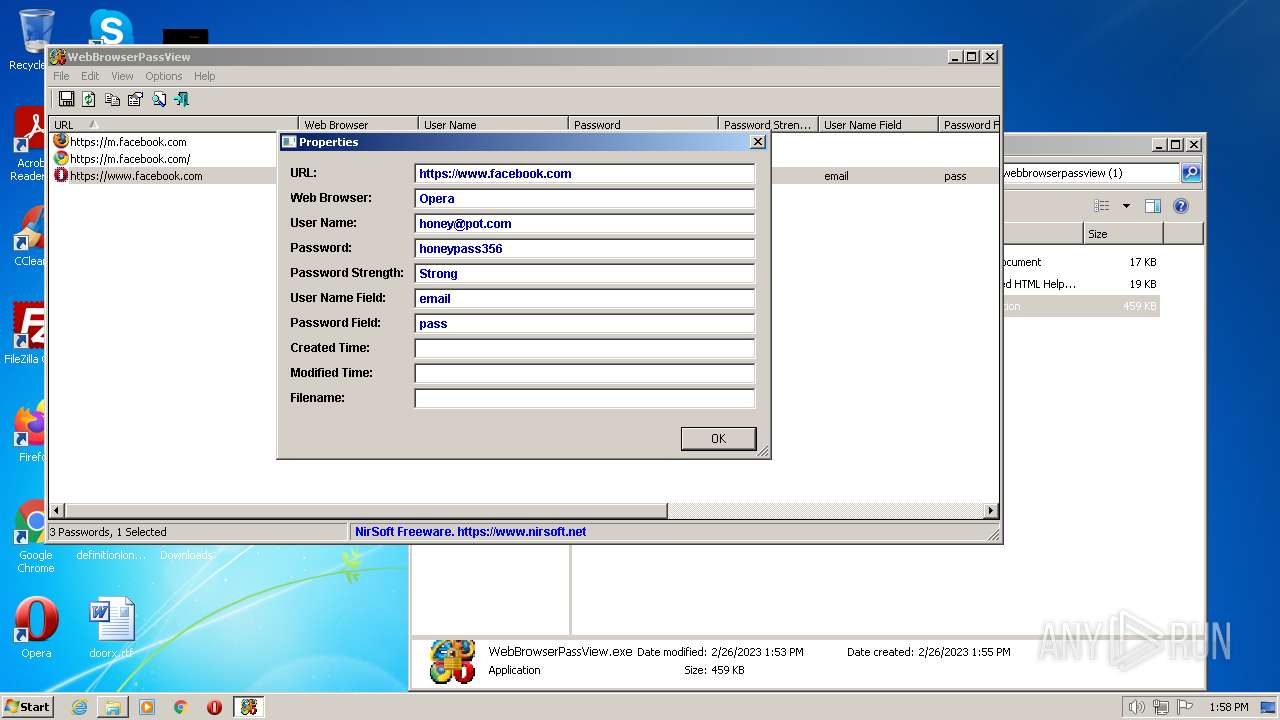
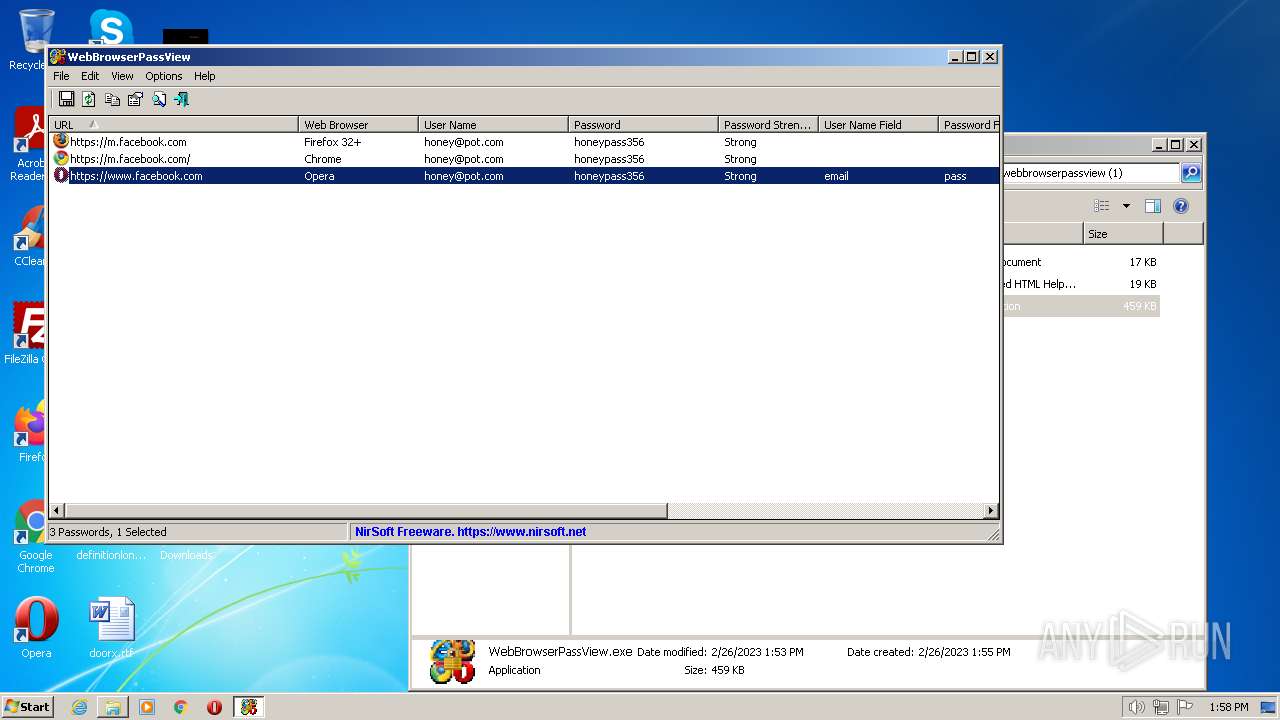
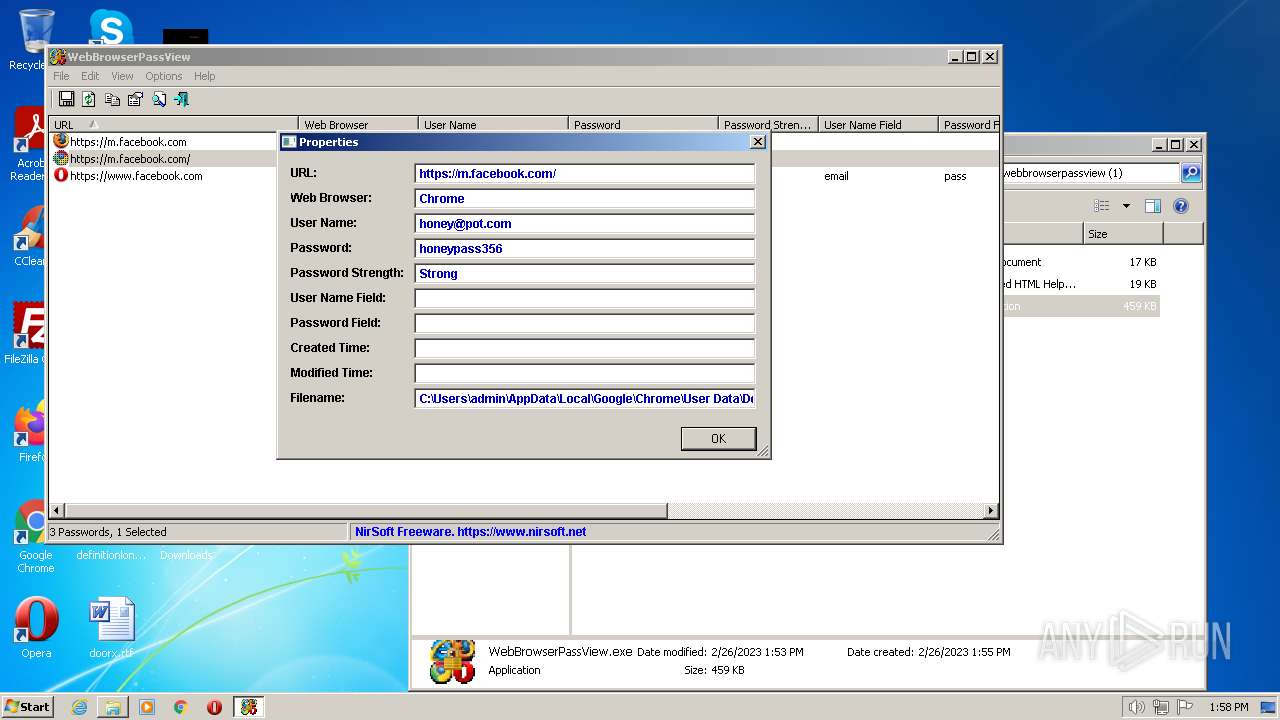
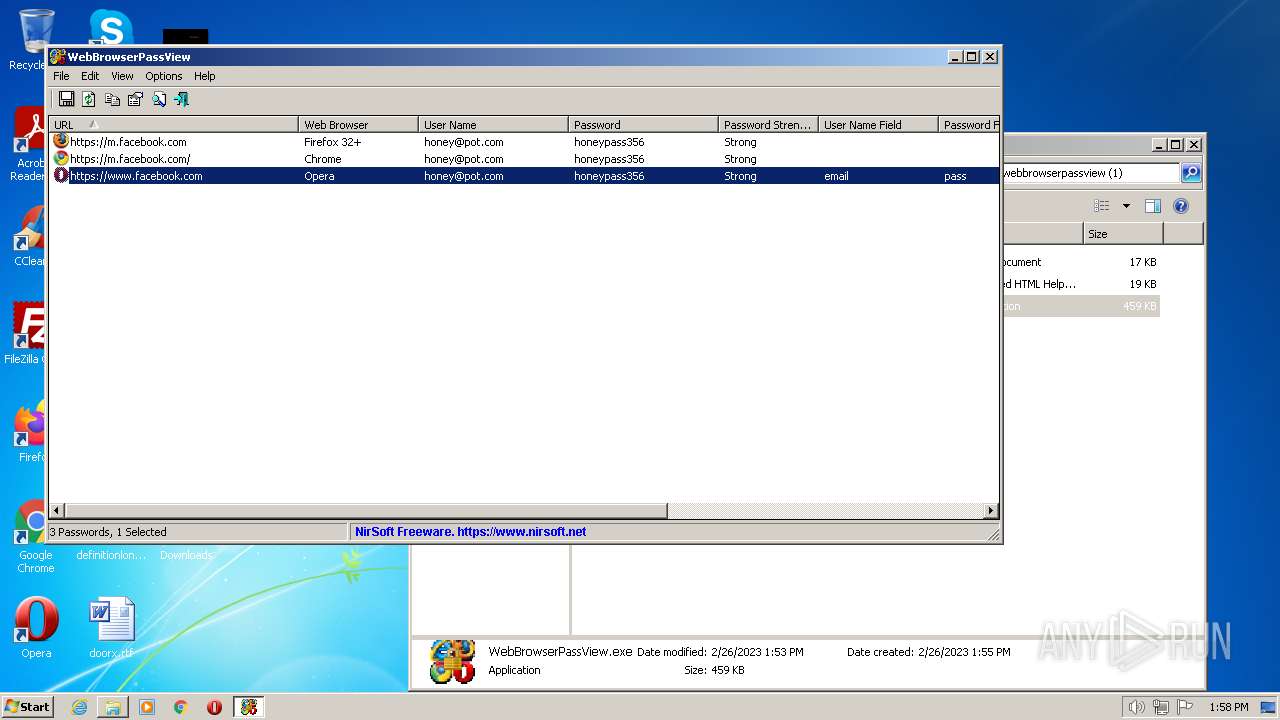
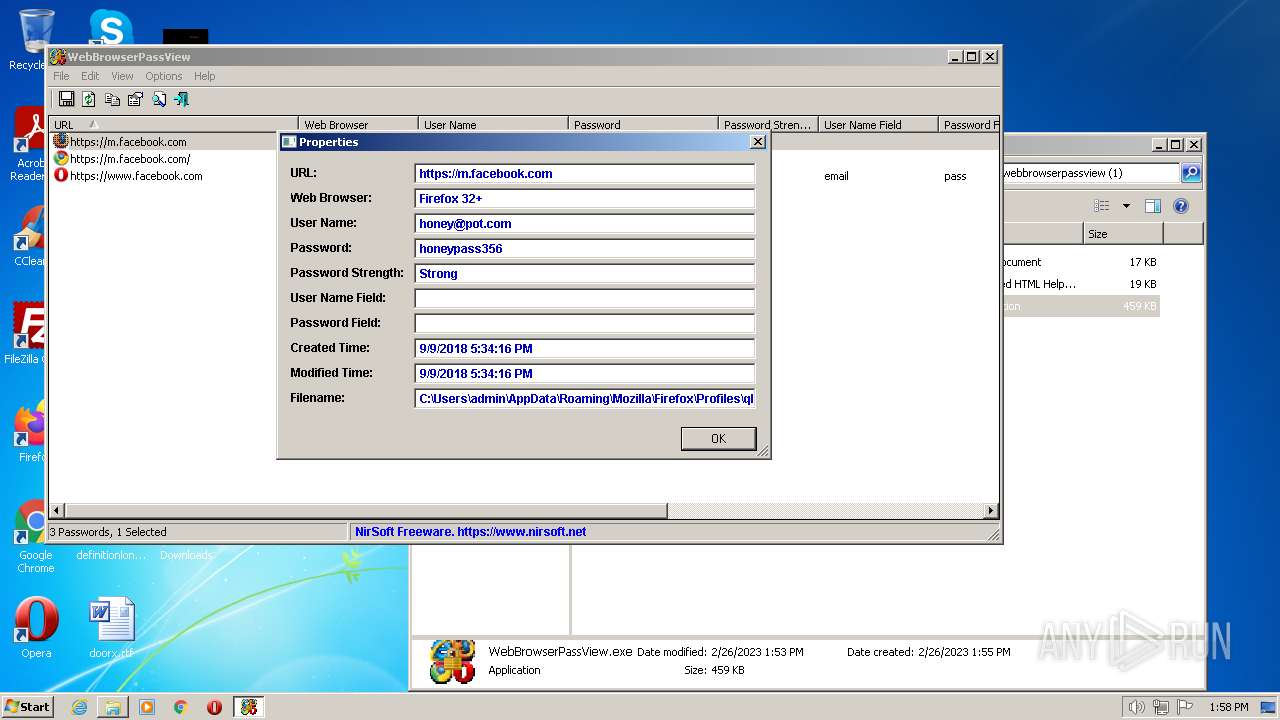
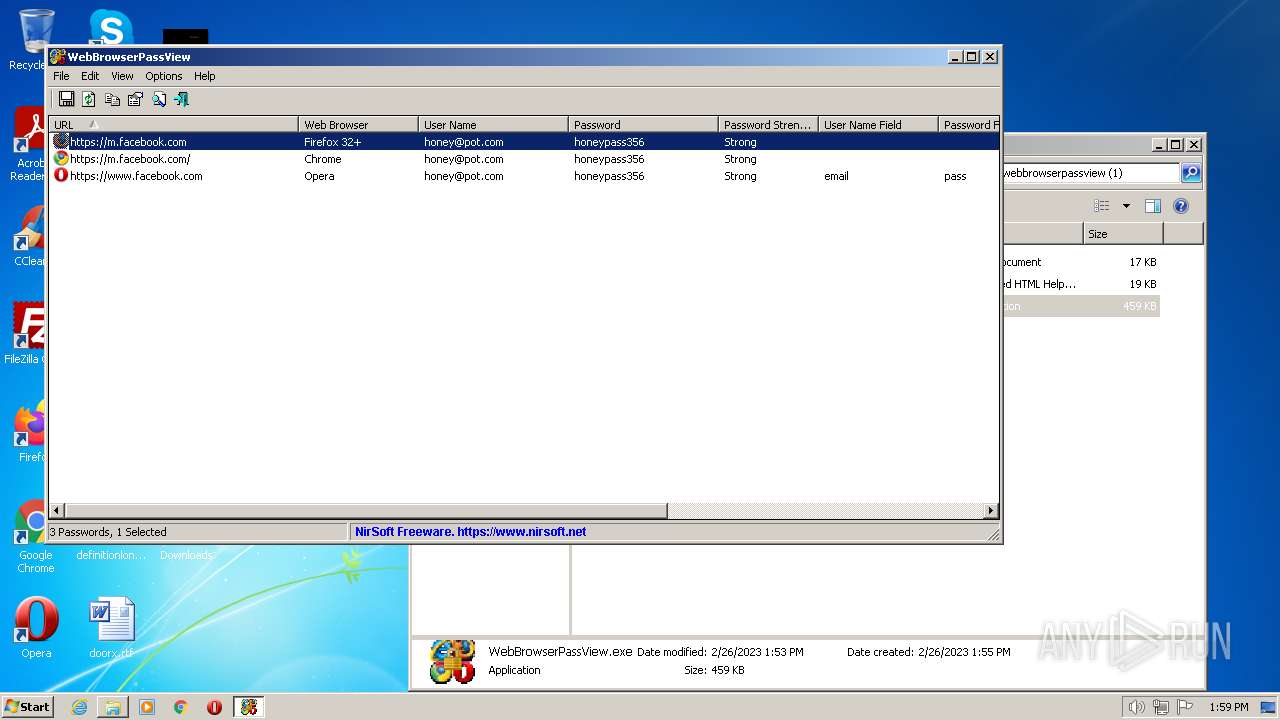
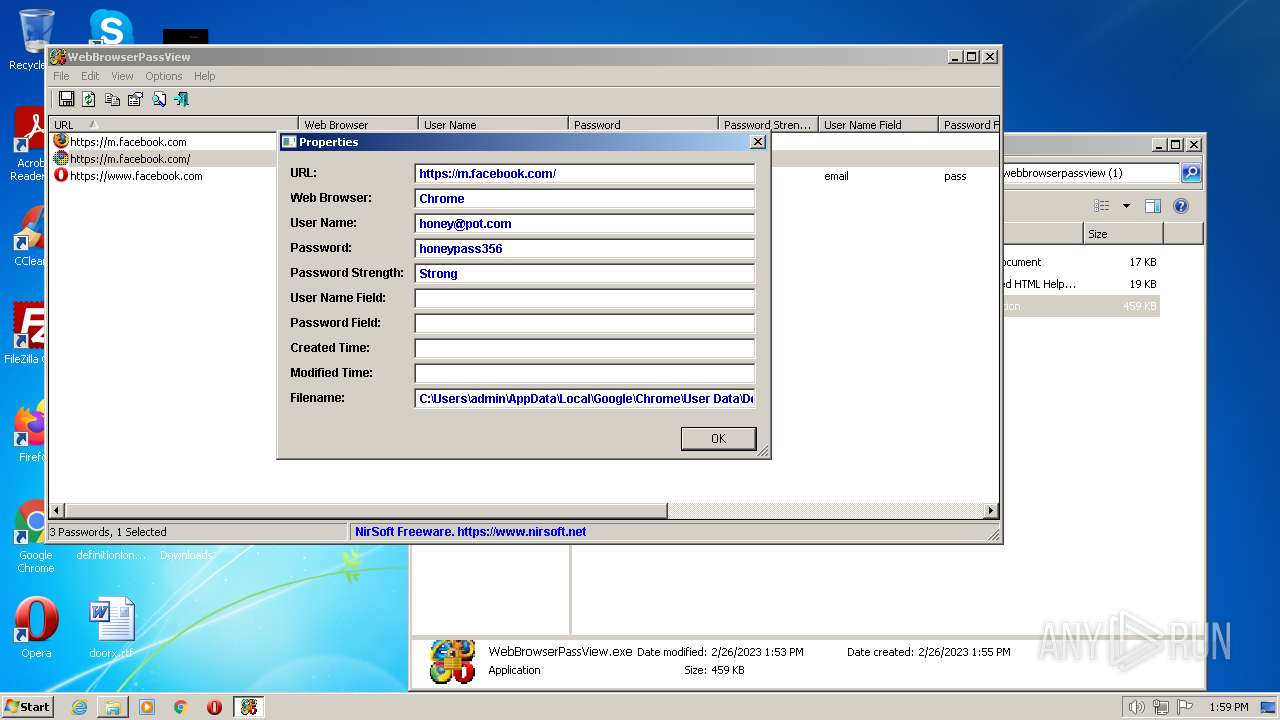
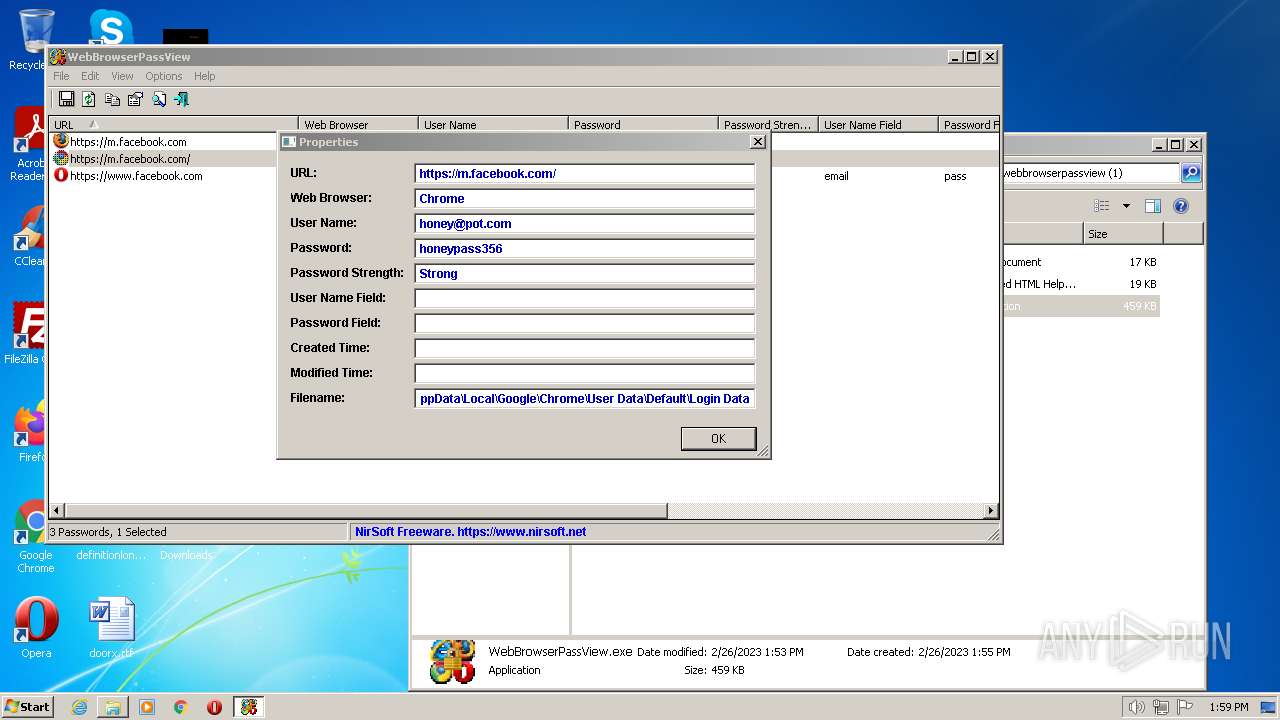
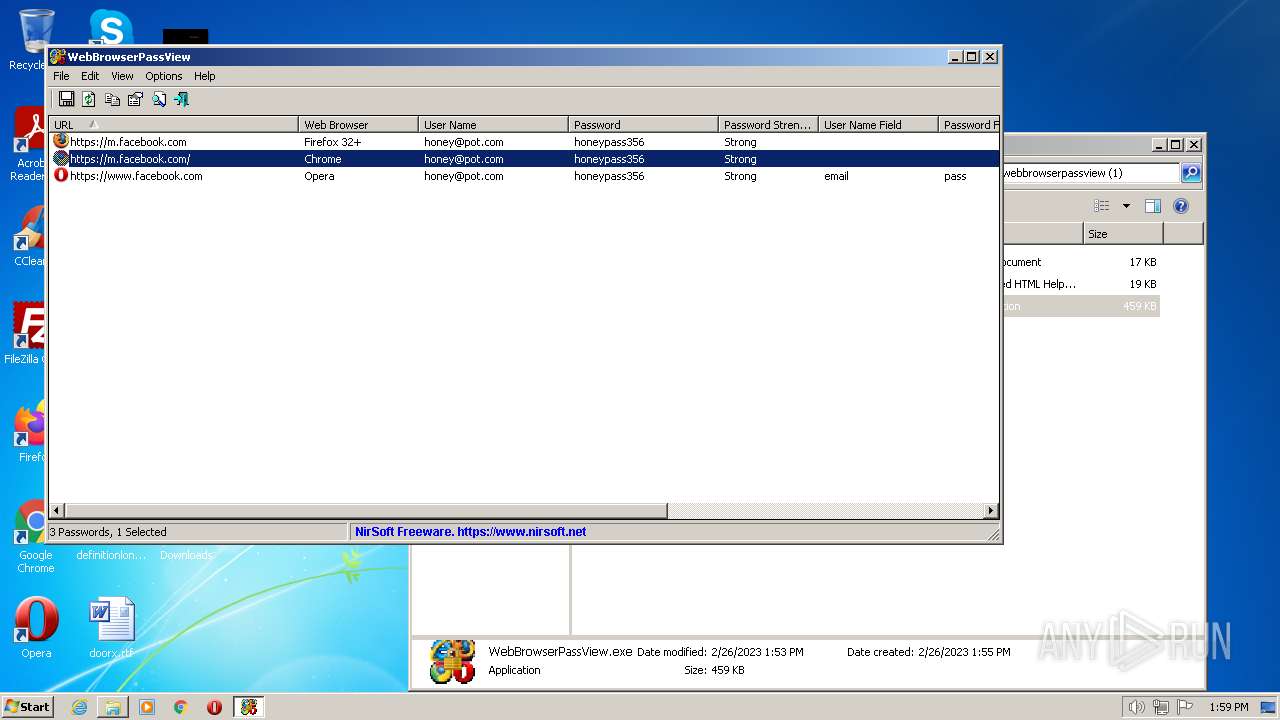
Steals credentials from Web Browsers
- WebBrowserPassView.exe (PID: 2492)
SUSPICIOUS
No suspicious indicators.INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 832)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 832)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 832)
Manual execution by a user
- BulletsPassView.exe (PID: 3380)
- Dialupass.exe (PID: 1772)
- Dialupass.exe (PID: 2420)
- NOTEPAD.EXE (PID: 116)
- NetRouteView.exe (PID: 3872)
- RouterPassView.exe (PID: 2184)
- WebBrowserPassView.exe (PID: 2492)
- VNCPassView.exe (PID: 4040)
- mailpv.exe (PID: 1836)
Reads the computer name
- BulletsPassView.exe (PID: 3380)
- mailpv.exe (PID: 1836)
- NetRouteView.exe (PID: 3872)
- RouterPassView.exe (PID: 2184)
- WebBrowserPassView.exe (PID: 2492)
- Dialupass.exe (PID: 1772)
Reads the machine GUID from the registry
- BulletsPassView.exe (PID: 3380)
- RouterPassView.exe (PID: 2184)
- WebBrowserPassView.exe (PID: 2492)
Checks supported languages
- BulletsPassView.exe (PID: 3380)
- NetRouteView.exe (PID: 3872)
- RouterPassView.exe (PID: 2184)
- WebBrowserPassView.exe (PID: 2492)
- VNCPassView.exe (PID: 4040)
- mailpv.exe (PID: 1836)
- Dialupass.exe (PID: 1772)
The process checks LSA protection
- BulletsPassView.exe (PID: 3380)
- RouterPassView.exe (PID: 2184)
- WebBrowserPassView.exe (PID: 2492)
Create files in a temporary directory
- WebBrowserPassView.exe (PID: 2492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | bulletspassview/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2023:02:26 22:52:10 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
62
Monitored processes
10
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Downloads\bulletspassview\readme.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 832 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Downloads.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1772 | "C:\Users\admin\Desktop\Downloads\dialupass\Dialupass.exe" | C:\Users\admin\Desktop\Downloads\dialupass\Dialupass.exe | Explorer.EXE | ||||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: Dialup/VPN Password Recovery Exit code: 0 Version: 3.61 Modules
| |||||||||||||||
| 1836 | "C:\Users\admin\Desktop\Downloads\mailpv\mailpv.exe" | C:\Users\admin\Desktop\Downloads\mailpv\mailpv.exe | Explorer.EXE | ||||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: Email Password-Recovery Exit code: 0 Version: 1.92 Modules
| |||||||||||||||
| 2184 | "C:\Users\admin\Desktop\Downloads\routerpassview\RouterPassView.exe" | C:\Users\admin\Desktop\Downloads\routerpassview\RouterPassView.exe | — | Explorer.EXE | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: Decrypts Router files. Exit code: 0 Version: 1.90 Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Desktop\Downloads\dialupass\Dialupass.exe" | C:\Users\admin\Desktop\Downloads\dialupass\Dialupass.exe | — | Explorer.EXE | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: Dialup/VPN Password Recovery Exit code: 3221226540 Version: 3.61 Modules
| |||||||||||||||
| 2492 | "C:\Users\admin\Desktop\Downloads\webbrowserpassview (1)\WebBrowserPassView.exe" | C:\Users\admin\Desktop\Downloads\webbrowserpassview (1)\WebBrowserPassView.exe | Explorer.EXE | ||||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: Web Browser Password Viewer Exit code: 0 Version: 2.12 Modules
| |||||||||||||||
| 3380 | "C:\Users\admin\Desktop\Downloads\bulletspassview\BulletsPassView.exe" | C:\Users\admin\Desktop\Downloads\bulletspassview\BulletsPassView.exe | — | Explorer.EXE | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: BulletsPassView Exit code: 0 Version: 1.32 Modules
| |||||||||||||||
| 3872 | "C:\Users\admin\Desktop\Downloads\netrouteview\NetRouteView.exe" | C:\Users\admin\Desktop\Downloads\netrouteview\NetRouteView.exe | — | Explorer.EXE | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: NetRouteView Exit code: 0 Version: 1.40 Modules
| |||||||||||||||
| 4040 | "C:\Users\admin\Desktop\Downloads\vncpassview\VNCPassView.exe" | C:\Users\admin\Desktop\Downloads\vncpassview\VNCPassView.exe | — | Explorer.EXE | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: VNCPassView Exit code: 0 Version: 1.05 Modules
| |||||||||||||||
Total events
4 448
Read events
4 340
Write events
106
Delete events
2
Modification events
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Downloads.zip | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
14
Suspicious files
0
Text files
28
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\bulletspassview\BulletsPassView.chm | chm | |
MD5:C957F7AB8D05FABAC84EF239FB36CB29 | SHA256:32F9F133832ADC8116F5A588D35CA4F036B7E435E9AEEADE48B3A823DA56372F | |||
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\routerpassview\RouterPassView.exe | executable | |
MD5:10D1D830605DB00287A616674EF9154A | SHA256:3EE00A42A65D2DF9EE571875A11F53B56C8494E90E1E8E60E128AABDB56399C8 | |||
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\mailpv\mailpv.exe | executable | |
MD5:FC3B93E042DE5FA569A8379D46BCE506 | SHA256:5BE325905DF8AAB7089AB2348D89343F55A2F88DADD75DE8F382E8FA026451BD | |||
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\mailpv\mailpv.chm | chm | |
MD5:31C9D2793D5B4DA033E503B3BF792986 | SHA256:18E9B39AB7C27EA80C6B76FC04881A5348DE491AB22ABE65A6BDB7254E23D5D1 | |||
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\netrouteview\NetRouteView.chm | chm | |
MD5:2796B30E29DA8C23BFA1AD0A99069645 | SHA256:A12F91F814E68A2755D8DCC64C74E44C0E1CA760DEA7CC542A12B53A4DEC488C | |||
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\netrouteview\NetRouteView.exe | executable | |
MD5:3F748C7C4B4ABB3CD90102E483F4D3C6 | SHA256:0E2F08388AD562273807A89851D8216FFB59A00D5A8656A9F8500CC554150CD4 | |||
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\routerpassview\readme.txt | text | |
MD5:3D6396871CEA91F3CC414A5F2F8DC799 | SHA256:61139AC2986742DE0C9F906EF247677E2E82DC6056F2891D4730CA42F621FF9B | |||
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\vncpassview\readme.txt | text | |
MD5:52C8CD031FB75AEBCF8A5F1AC597F9DA | SHA256:63CD2E9DA2F437EE3C7D7D9F7DEBB282ECC908F2E6F5AD7FEDC8EC571272E312 | |||
| 2492 | WebBrowserPassView.exe | C:\Users\admin\AppData\Local\Temp\bhv5156.tmp | — | |
MD5:— | SHA256:— | |||
| 832 | WinRAR.exe | C:\Users\admin\Desktop\Downloads\webbrowserpassview (1)\readme.txt | text | |
MD5:DFF7CBF7A7A6FC115C45D8E384FFCA0F | SHA256:496794C2682DE2961E0D48EC79DB5511F9274AC06405A40F64BE927DE89E05FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report