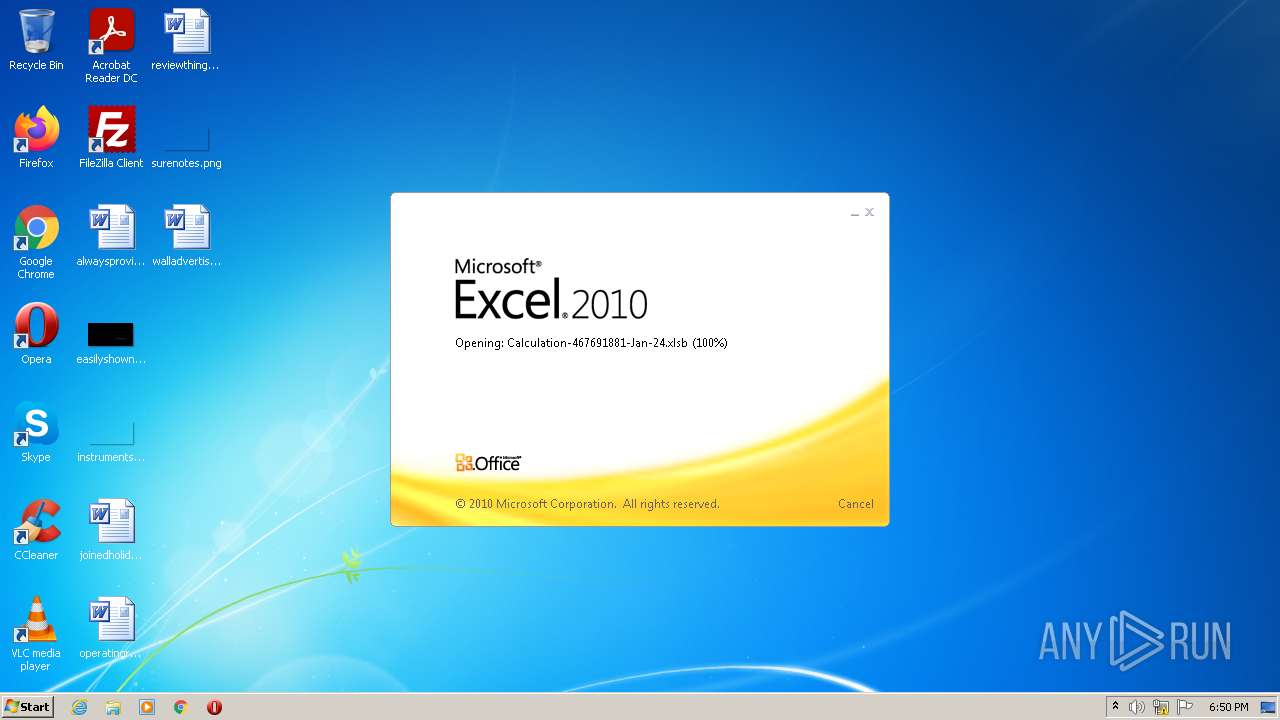
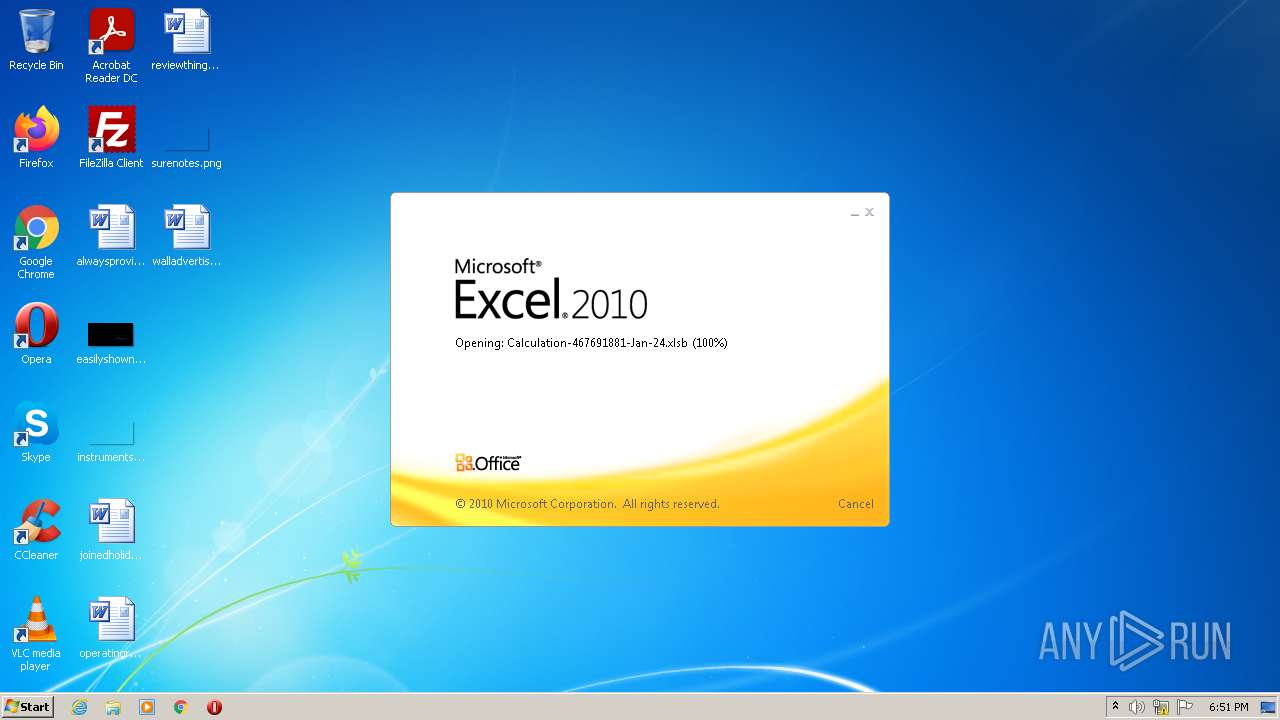
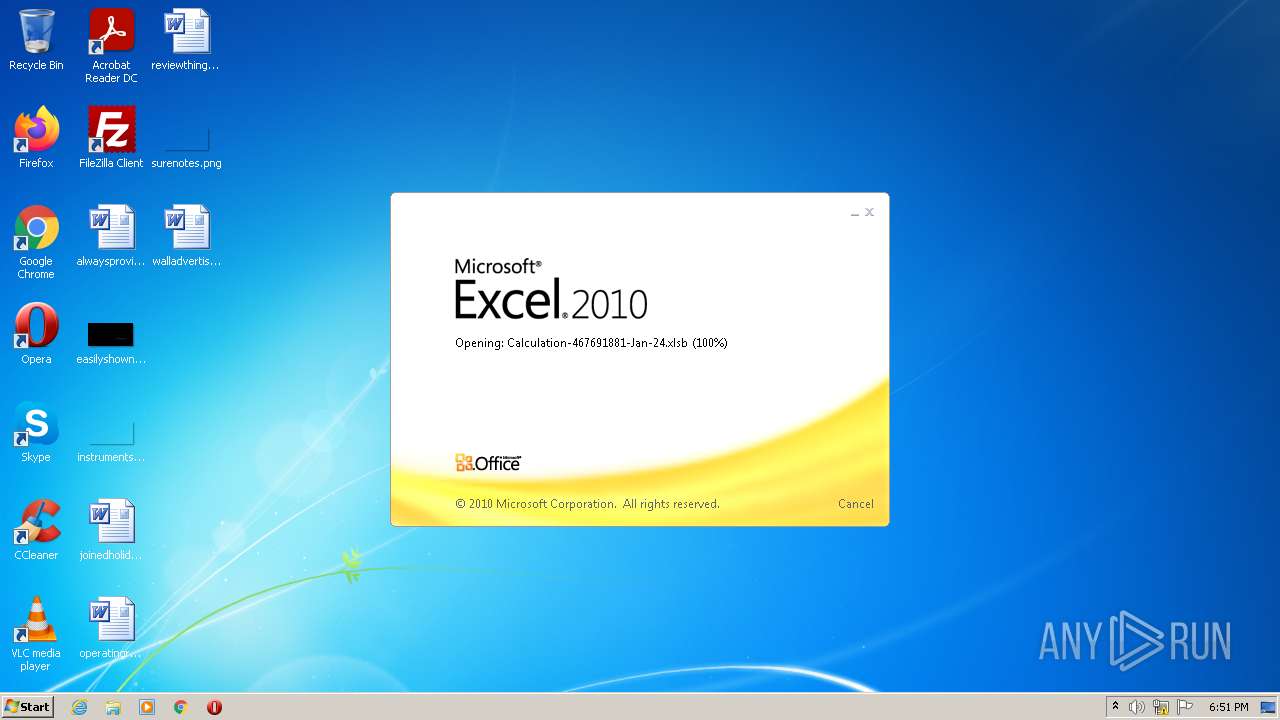
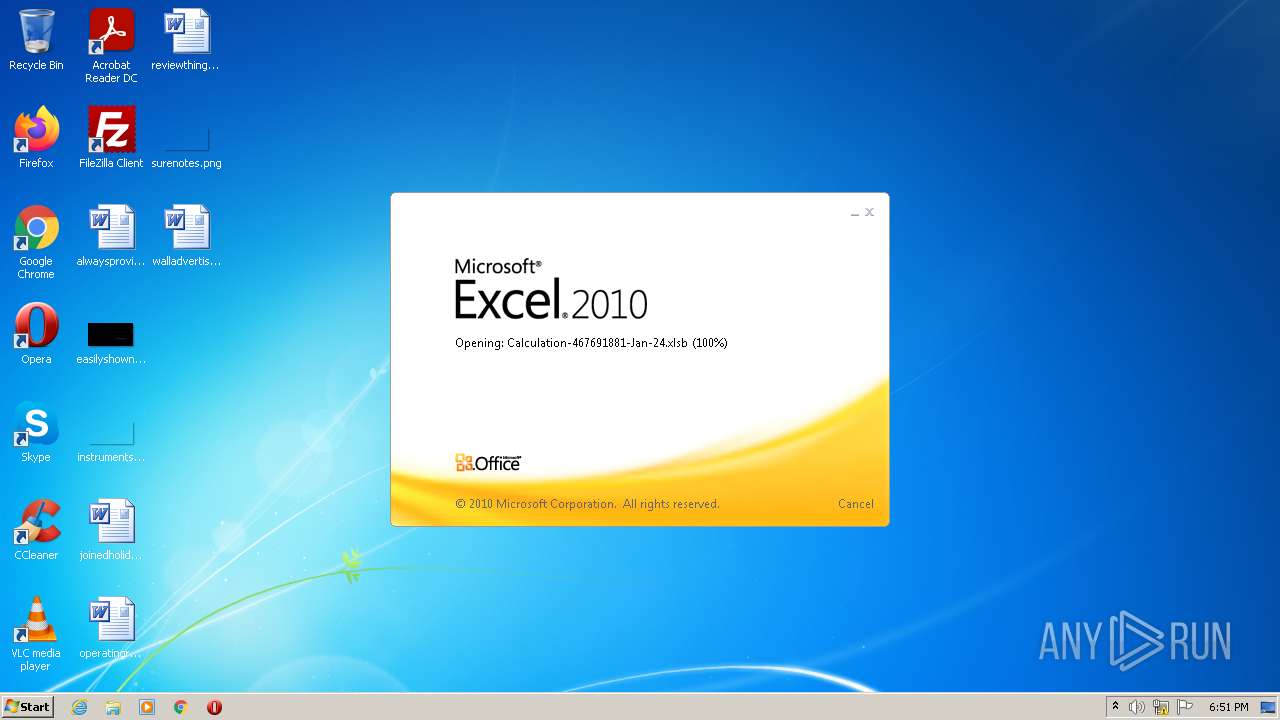
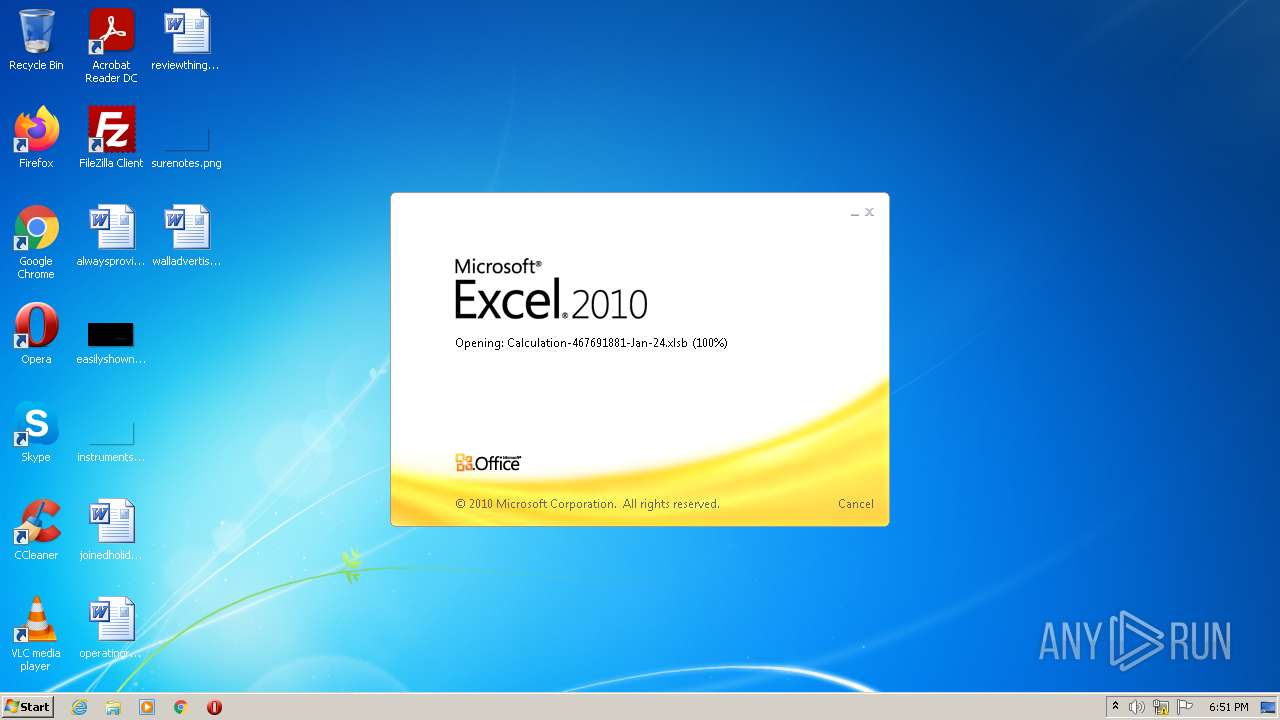
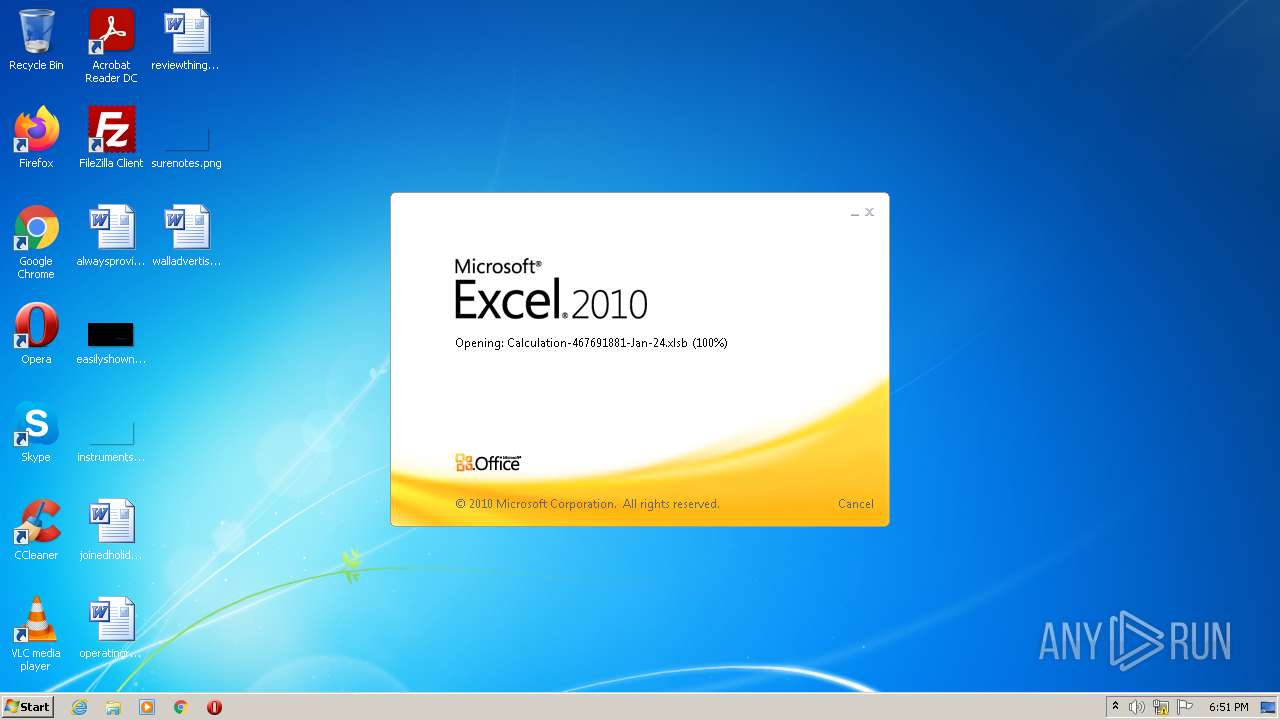
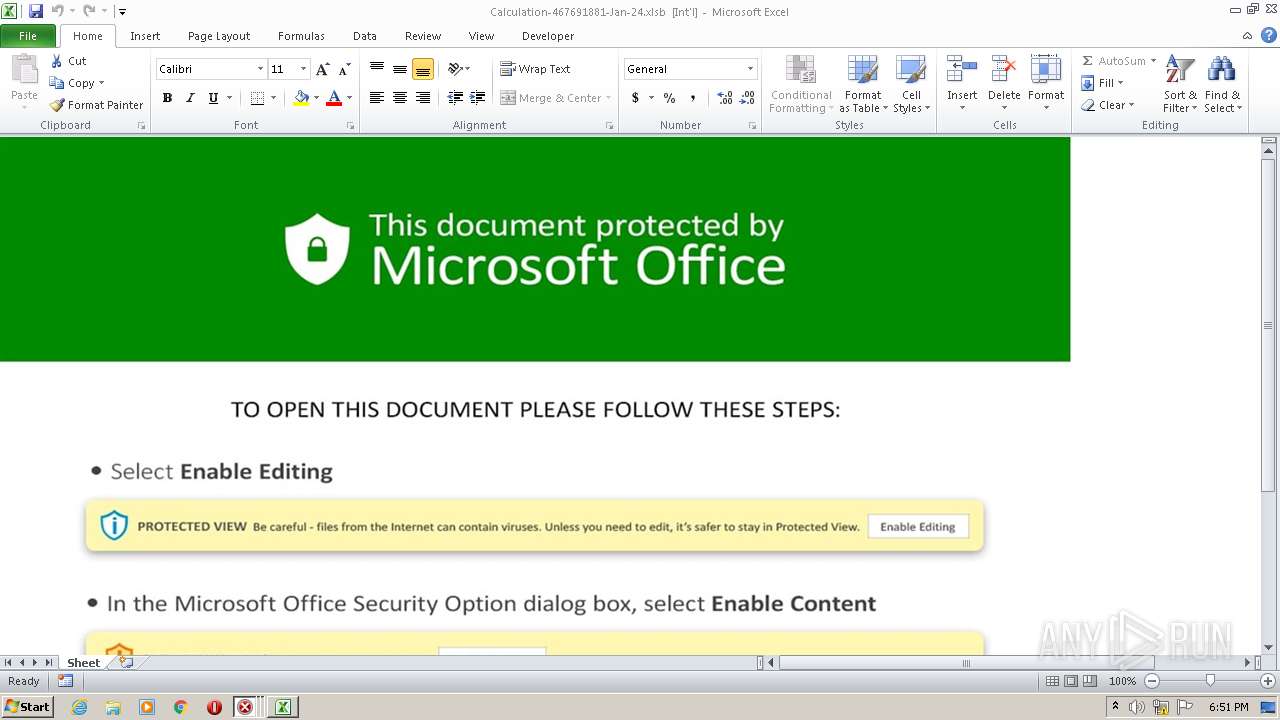
| File name: | Calculation-467691881-Jan-24.xlsb |
| Full analysis: | https://app.any.run/tasks/a330d69a-ca66-481e-98be-9013c9711bfd |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 24, 2022, 18:50:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | A7F0F37E08983068214F56F00CD07051 |
| SHA1: | 76F59592FBBA6C979A3C5AB1173FD3B94D3D3399 |
| SHA256: | 286DAA51E534EA2F4455679968A25E16DCDA1514B587444D2EFC8837DACB15B5 |
| SSDEEP: | 3072:WFwLEhWYjnsCbxKljNE5gKmFOi+uaE7O6K:WFwohtrsCbxKljDKmFOi/7Oh |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- EXCEL.EXE (PID: 1012)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 1012)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2284)
Executed via COM
- DllHost.exe (PID: 1988)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1012)
Checks supported languages
- EXCEL.EXE (PID: 1012)
- regsvr32.exe (PID: 2552)
- regsvr32.exe (PID: 292)
- regsvr32.exe (PID: 520)
- chrome.exe (PID: 2284)
- chrome.exe (PID: 1360)
- chrome.exe (PID: 3544)
- chrome.exe (PID: 3836)
- chrome.exe (PID: 1976)
- chrome.exe (PID: 2796)
- chrome.exe (PID: 3280)
- chrome.exe (PID: 2356)
- chrome.exe (PID: 2232)
- chrome.exe (PID: 3240)
- chrome.exe (PID: 3692)
- chrome.exe (PID: 2424)
- chrome.exe (PID: 3568)
- chrome.exe (PID: 2364)
- chrome.exe (PID: 3916)
- chrome.exe (PID: 516)
- chrome.exe (PID: 4020)
- chrome.exe (PID: 3200)
- chrome.exe (PID: 1928)
- chrome.exe (PID: 2892)
- chrome.exe (PID: 2540)
- chrome.exe (PID: 4036)
- chrome.exe (PID: 3440)
- chrome.exe (PID: 3464)
- chrome.exe (PID: 3976)
- DllHost.exe (PID: 1988)
- chrome.exe (PID: 3320)
Reads the computer name
- EXCEL.EXE (PID: 1012)
- chrome.exe (PID: 2284)
- chrome.exe (PID: 1976)
- chrome.exe (PID: 1360)
- chrome.exe (PID: 3544)
- chrome.exe (PID: 3568)
- chrome.exe (PID: 4020)
- chrome.exe (PID: 516)
- chrome.exe (PID: 3440)
- chrome.exe (PID: 4036)
- chrome.exe (PID: 2540)
- chrome.exe (PID: 3464)
- DllHost.exe (PID: 1988)
Reads the hosts file
- chrome.exe (PID: 2284)
- chrome.exe (PID: 1360)
Application launched itself
- chrome.exe (PID: 2284)
- chrome.exe (PID: 1976)
Manual execution by user
- chrome.exe (PID: 2284)
- chrome.exe (PID: 1976)
Reads settings of System Certificates
- chrome.exe (PID: 1360)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2284)
Reads the date of Windows installation
- chrome.exe (PID: 2540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
XML
| AppVersion: | 16.03 |
|---|---|
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| Company: | - |
| TitlesOfParts: |
|
| HeadingPairs: |
|
| ScaleCrop: | No |
| DocSecurity: | None |
| Application: | Microsoft Excel |
| ModifyDate: | 2022:01:24 08:11:53Z |
| CreateDate: | 2015:06:05 18:19:34Z |
| LastModifiedBy: | Kassa |
XMP
| Creator: | Admin1 |
|---|
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 4876 |
| ZipCompressedSize: | 649 |
| ZipCRC: | 0x7b44d919 |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0006 |
| ZipRequiredVersion: | 20 |
Total processes
74
Monitored processes
31
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | regsvr32 C:\ProgramData\VDscytujyctfjkvu1.ocx | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1052,10621083760850131610,17410926970640439766,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3212 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 520 | regsvr32 C:\ProgramData\VDscytujyctfjkvu3.ocx | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1012 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1052,10621083760850131610,17410926970640439766,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1348 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,10621083760850131610,17410926970640439766,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2888 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1988 | C:\Windows\system32\DllHost.exe /Processid:{E96767E0-7EAA-45E1-8E7D-64414AFF281A} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,10621083760850131610,17410926970640439766,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2248 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
22 321
Read events
21 953
Write events
346
Delete events
22
Modification events
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | lf> |
Value: 6C663E00F4030000010000000000000000000000 | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1012) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
142
Text files
116
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1012 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR4E4C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61EEF59D-8EC.pma | — | |
MD5:— | SHA256:— | |||
| 2796 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | — | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF138a71.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\9e96336f-3158-4283-98b4-56dc37b08e5b.tmp | text | |
MD5:— | SHA256:— | |||
| 1360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | binary | |
MD5:— | SHA256:— | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3836 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF138a80.TMP | text | |
MD5:81F483F77EE490F35306A4F94DB2286B | SHA256:82434CE3C9D13F509EBEEBE3A7A1A1DE9AB4557629D9FC855761E0CFA45E8BCE | |||
| 2284 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
36
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1360 | chrome.exe | GET | 302 | 216.239.34.21:80 | http://virustotal.com/ | US | — | — | whitelisted |
876 | svchost.exe | HEAD | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | — | — | whitelisted |
876 | svchost.exe | HEAD | 302 | 142.250.185.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | — | — | whitelisted |
876 | svchost.exe | HEAD | 200 | 74.125.108.167:80 | http://r2---sn-2gb7sn7y.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=45.86.202.16&mm=28&mn=sn-2gb7sn7y&ms=nvh&mt=1643050106&mv=m&mvi=2&pl=24&rmhost=r3---sn-2gb7sn7y.gvt1.com&shardbypass=yes | US | — | — | whitelisted |
876 | svchost.exe | GET | 206 | 74.125.108.167:80 | http://r2---sn-2gb7sn7y.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=45.86.202.16&mm=28&mn=sn-2gb7sn7y&ms=nvh&mt=1643050106&mv=m&mvi=2&pl=24&rmhost=r3---sn-2gb7sn7y.gvt1.com&shardbypass=yes | US | binary | 5.63 Kb | whitelisted |
876 | svchost.exe | GET | 206 | 74.125.108.167:80 | http://r2---sn-2gb7sn7y.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=45.86.202.16&mm=28&mn=sn-2gb7sn7y&ms=nvh&mt=1643050106&mv=m&mvi=2&pl=24&rmhost=r3---sn-2gb7sn7y.gvt1.com&shardbypass=yes | US | binary | 9.47 Kb | whitelisted |
876 | svchost.exe | GET | 206 | 74.125.108.167:80 | http://r2---sn-2gb7sn7y.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3?cms_redirect=yes&mh=8t&mip=45.86.202.16&mm=28&mn=sn-2gb7sn7y&ms=nvh&mt=1643050106&mv=m&mvi=2&pl=24&rmhost=r3---sn-2gb7sn7y.gvt1.com&shardbypass=yes | US | binary | 9.47 Kb | whitelisted |
876 | svchost.exe | GET | 302 | 142.250.185.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 576 b | whitelisted |
876 | svchost.exe | GET | 302 | 142.250.185.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 576 b | whitelisted |
876 | svchost.exe | GET | 302 | 142.250.185.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | html | 576 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1012 | EXCEL.EXE | 185.82.127.129:80 | — | Makonix SIA | SE | suspicious |
1012 | EXCEL.EXE | 101.99.95.16:80 | — | — | MY | suspicious |
1012 | EXCEL.EXE | 91.193.18.87:80 | — | — | — | suspicious |
1360 | chrome.exe | 142.250.181.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1360 | chrome.exe | 142.250.181.237:443 | accounts.google.com | Google Inc. | US | suspicious |
1360 | chrome.exe | 142.250.184.238:443 | clients2.google.com | Google Inc. | US | whitelisted |
1360 | chrome.exe | 142.250.185.100:443 | www.google.com | Google Inc. | US | whitelisted |
1360 | chrome.exe | 216.58.212.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1360 | chrome.exe | 142.250.186.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1360 | chrome.exe | 142.250.184.227:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
virustotal.com |
| whitelisted |