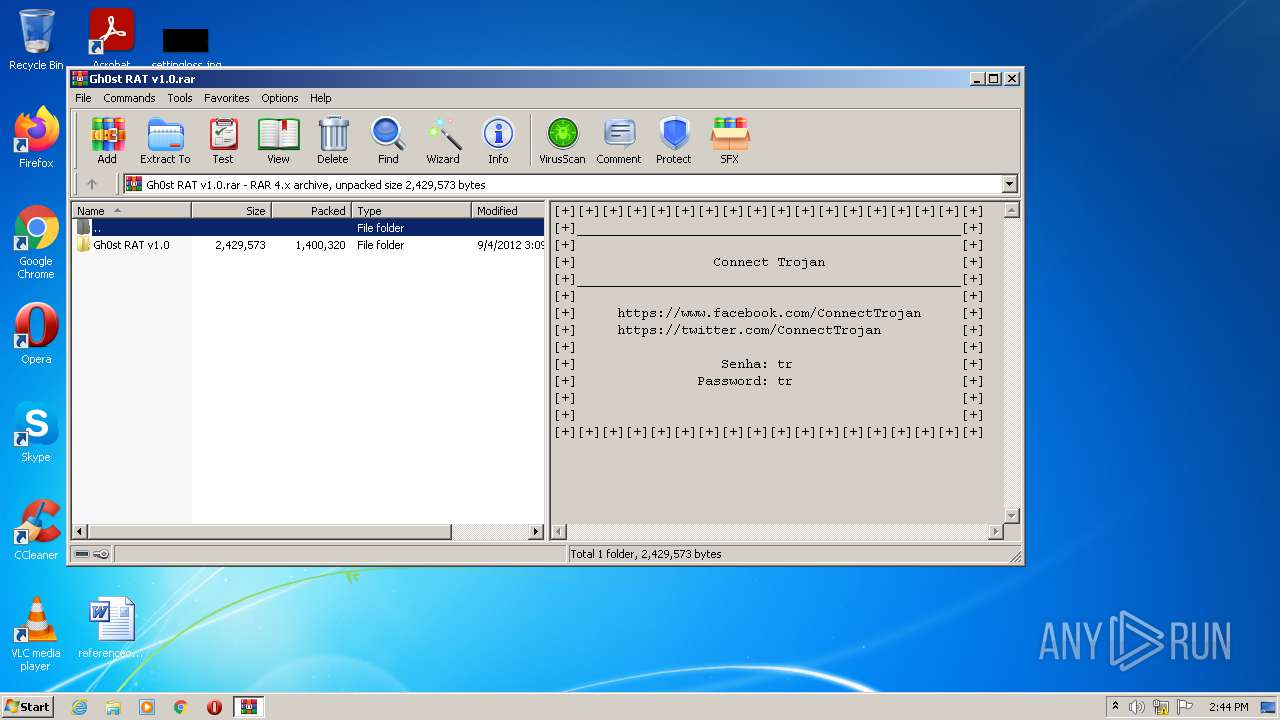
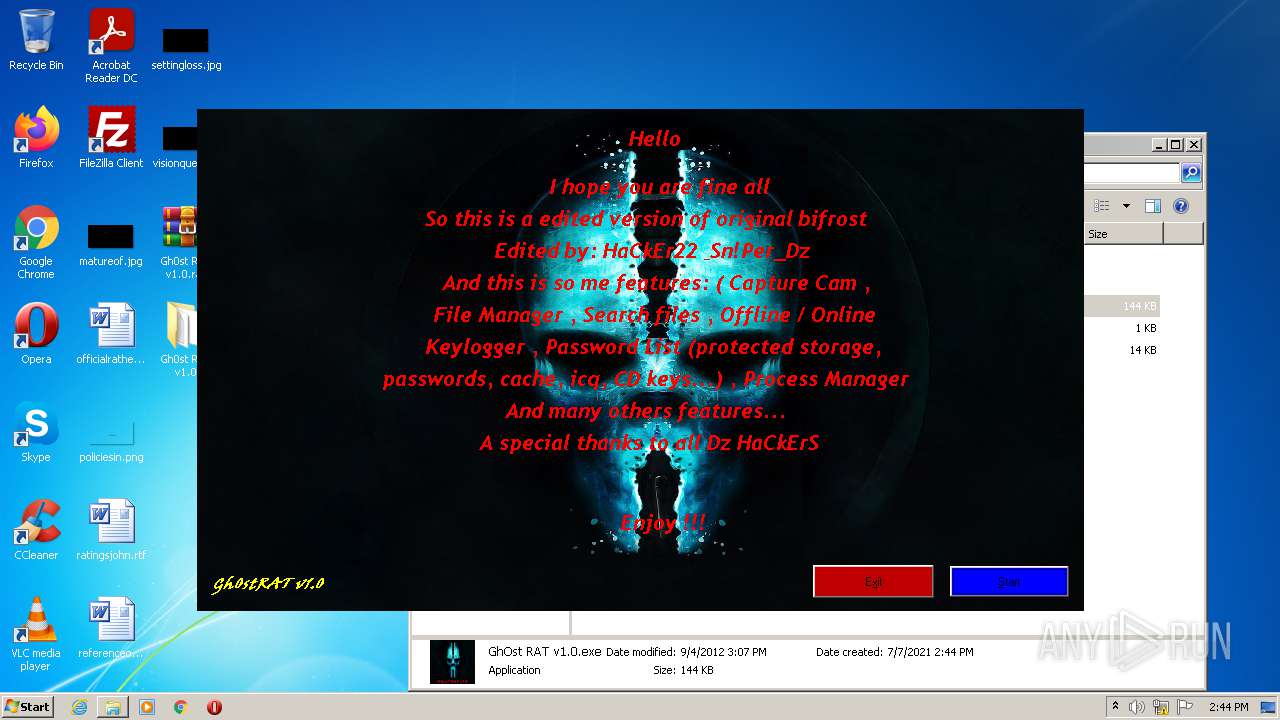
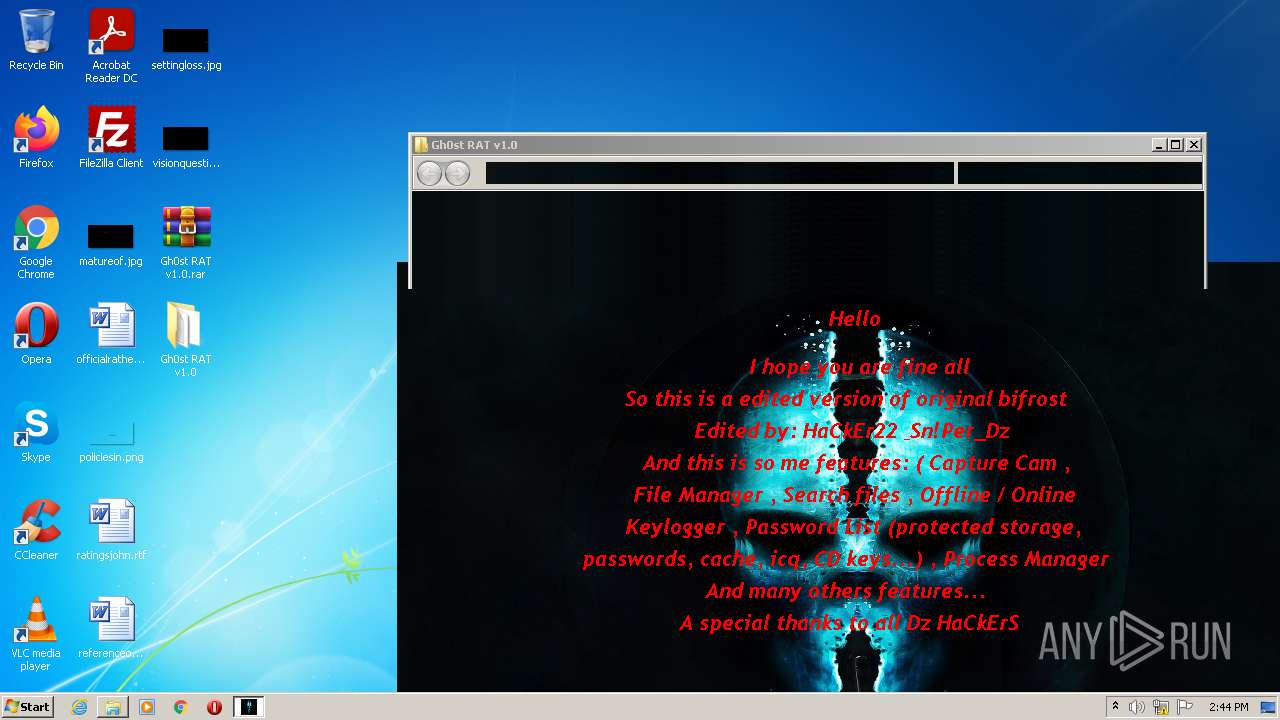
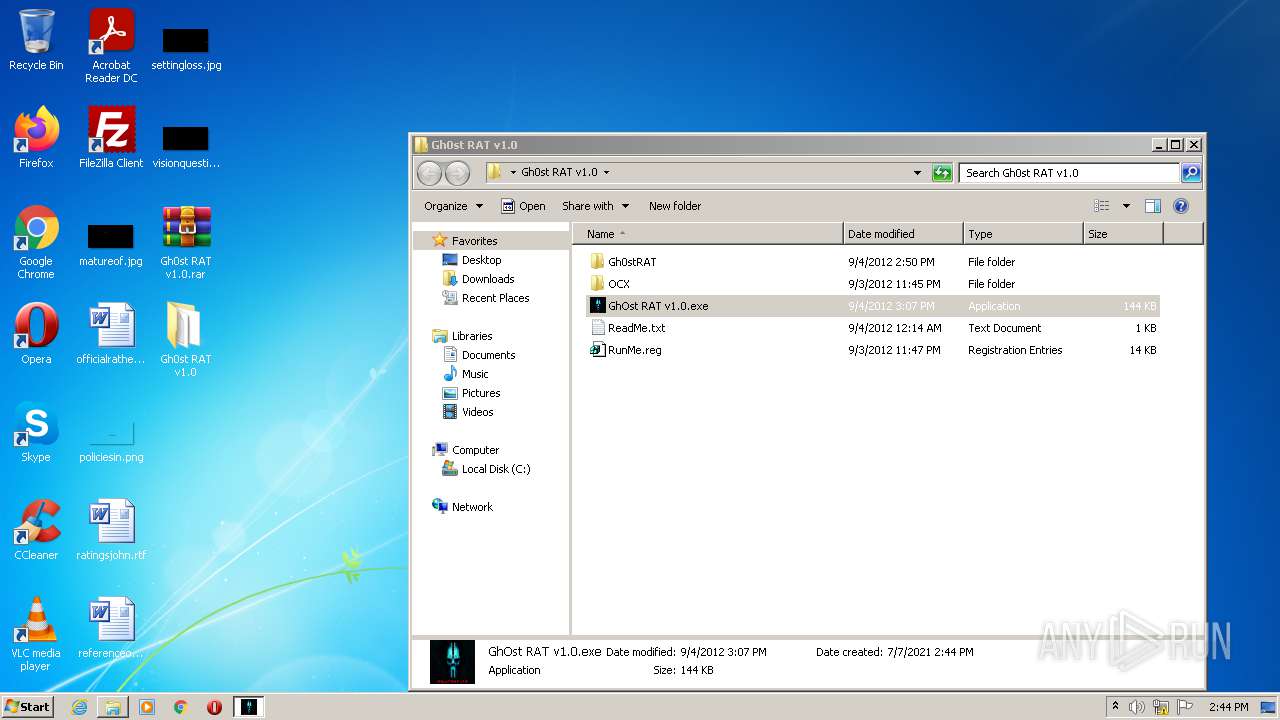
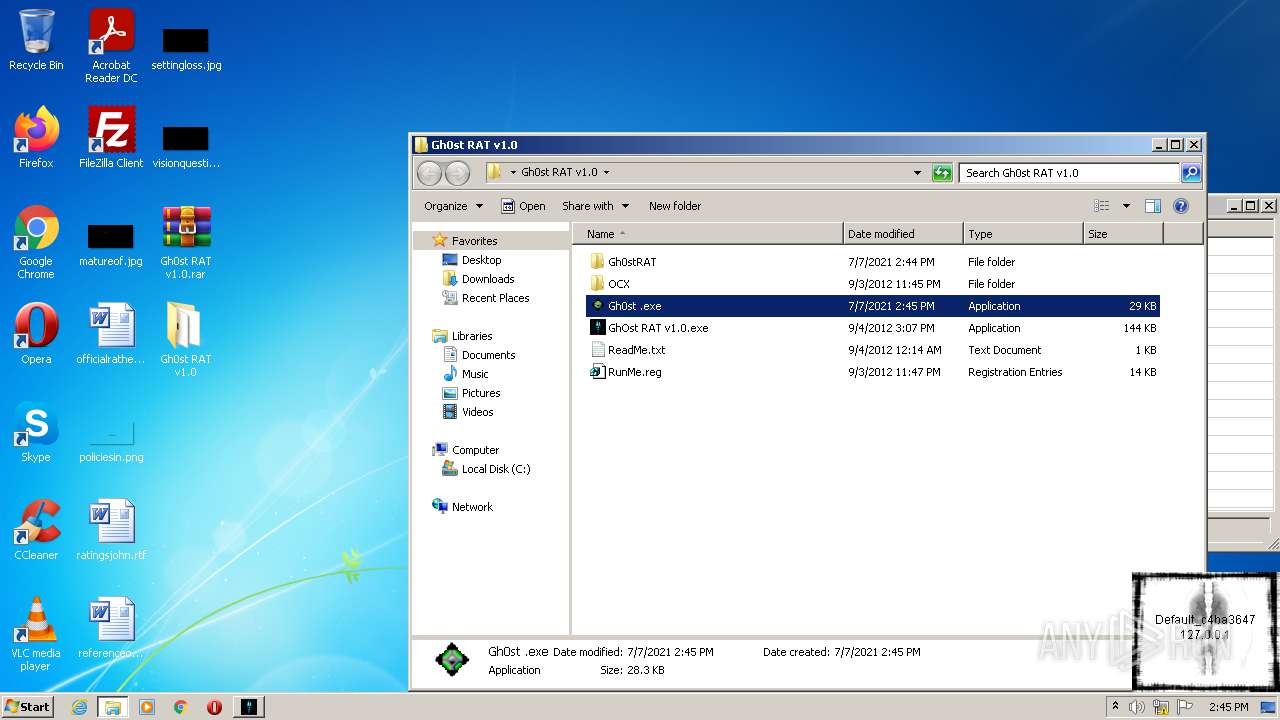
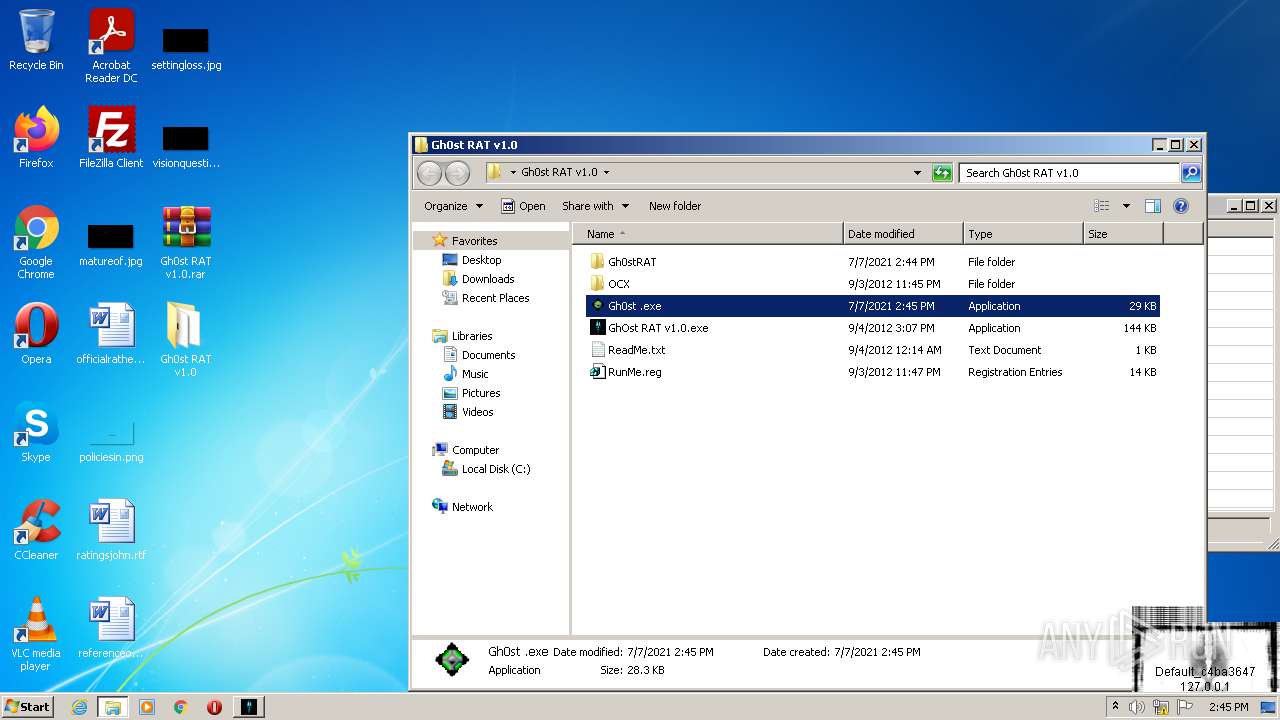
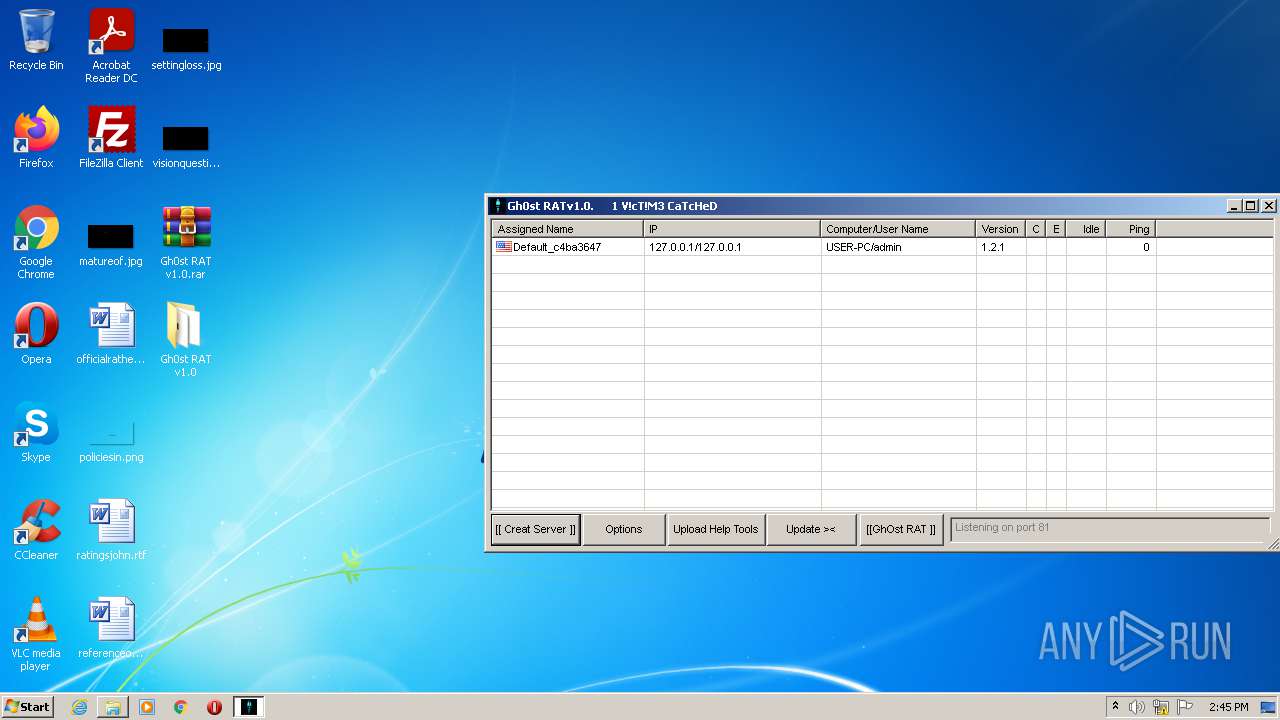
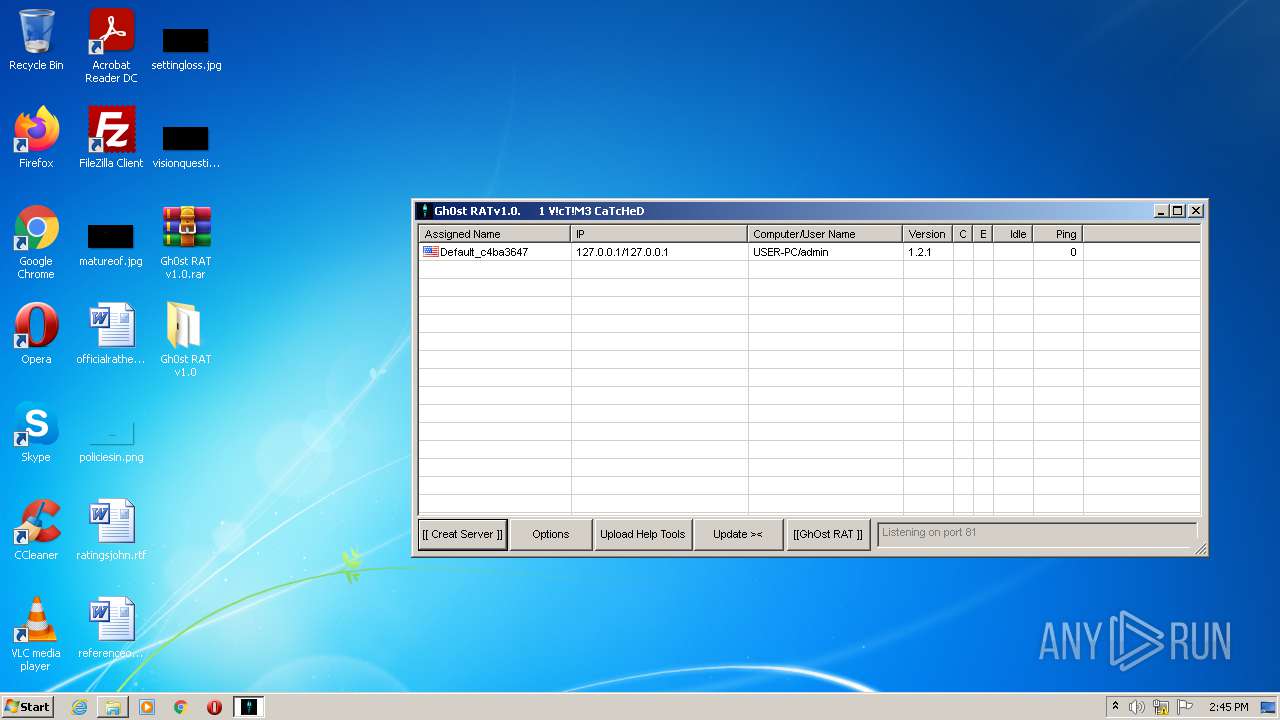
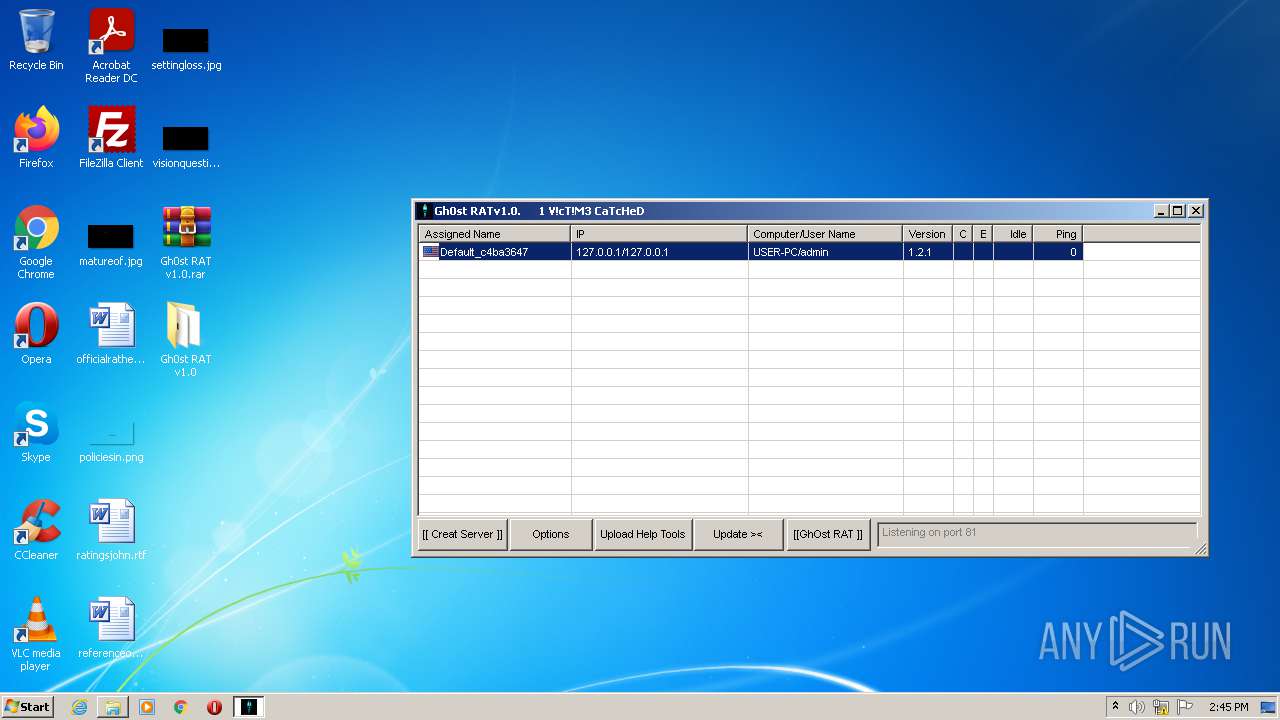
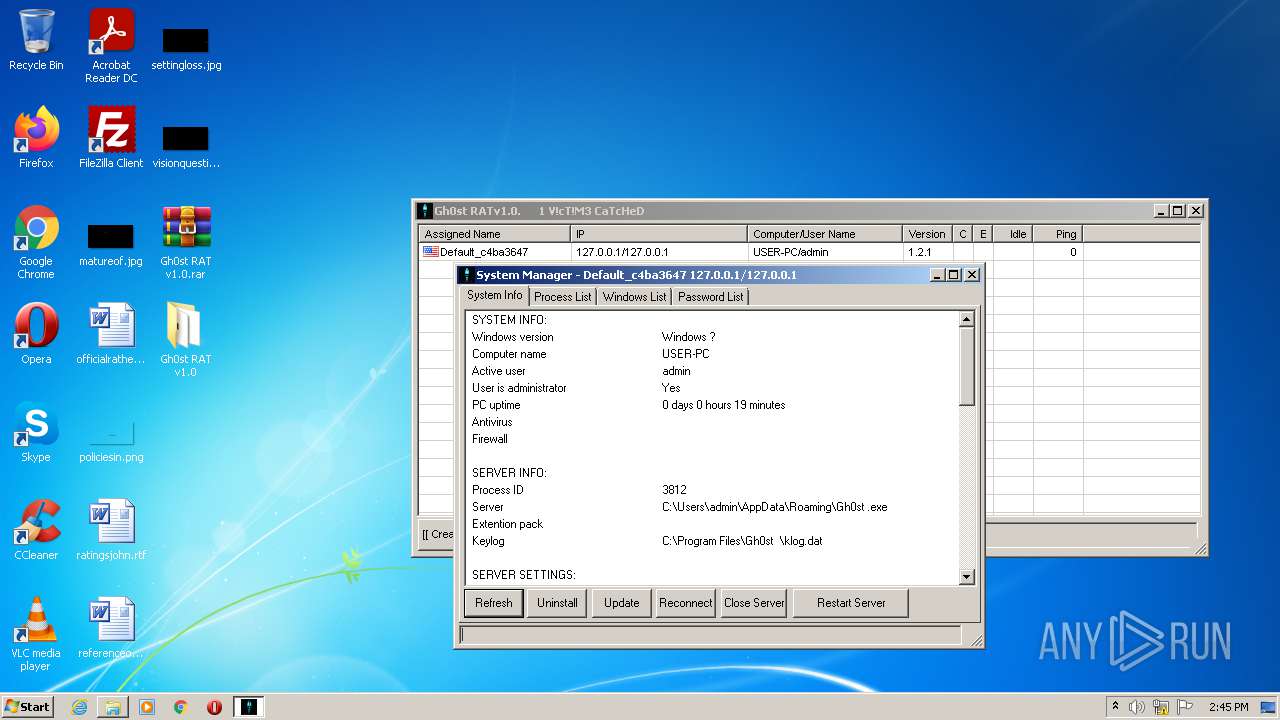
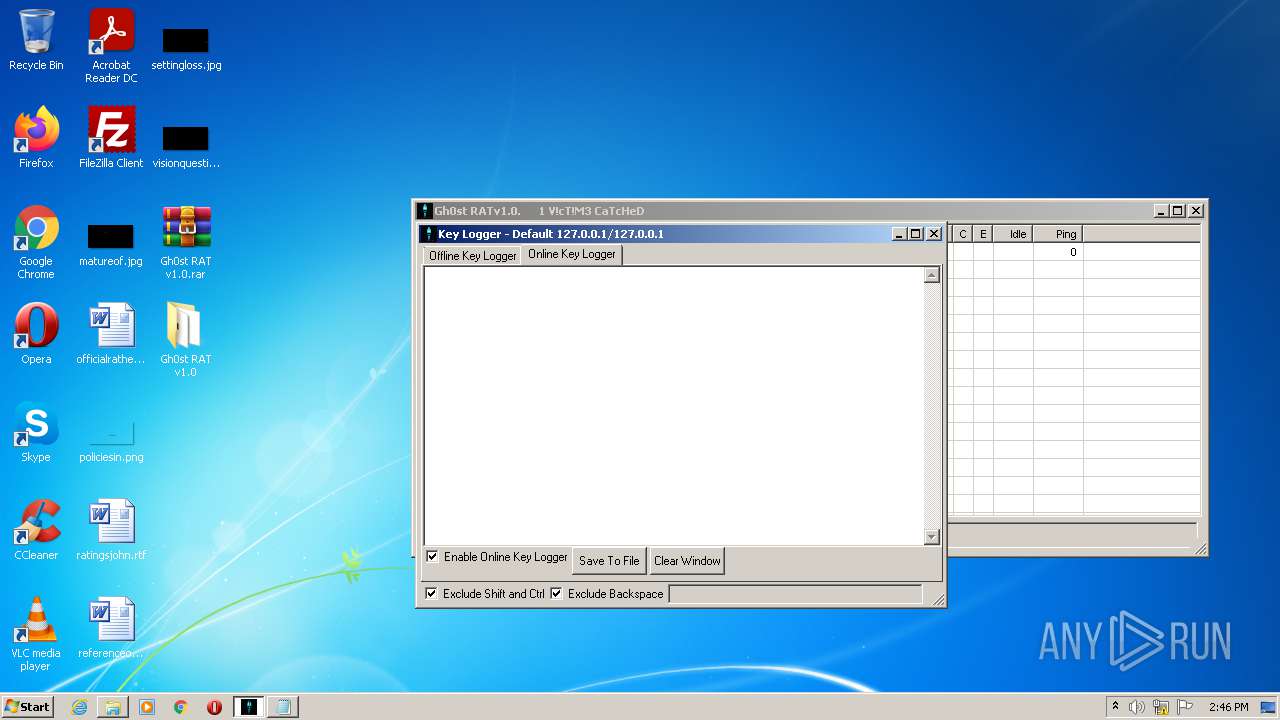
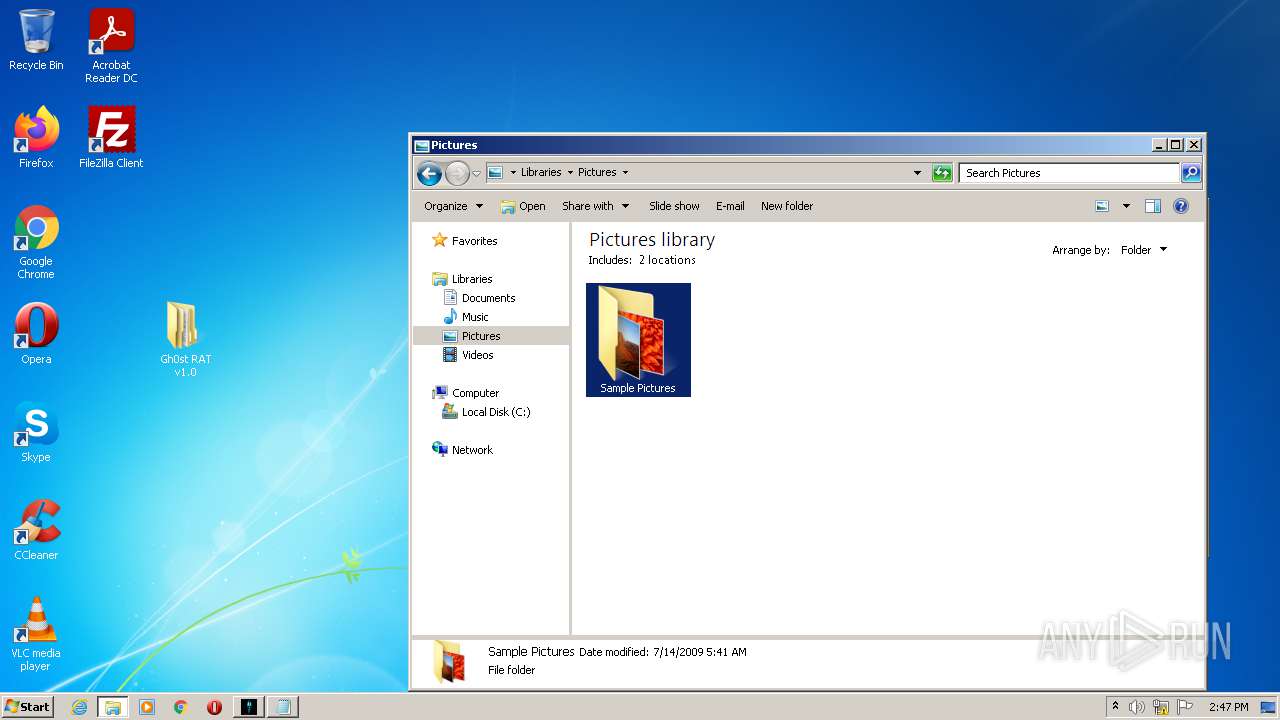
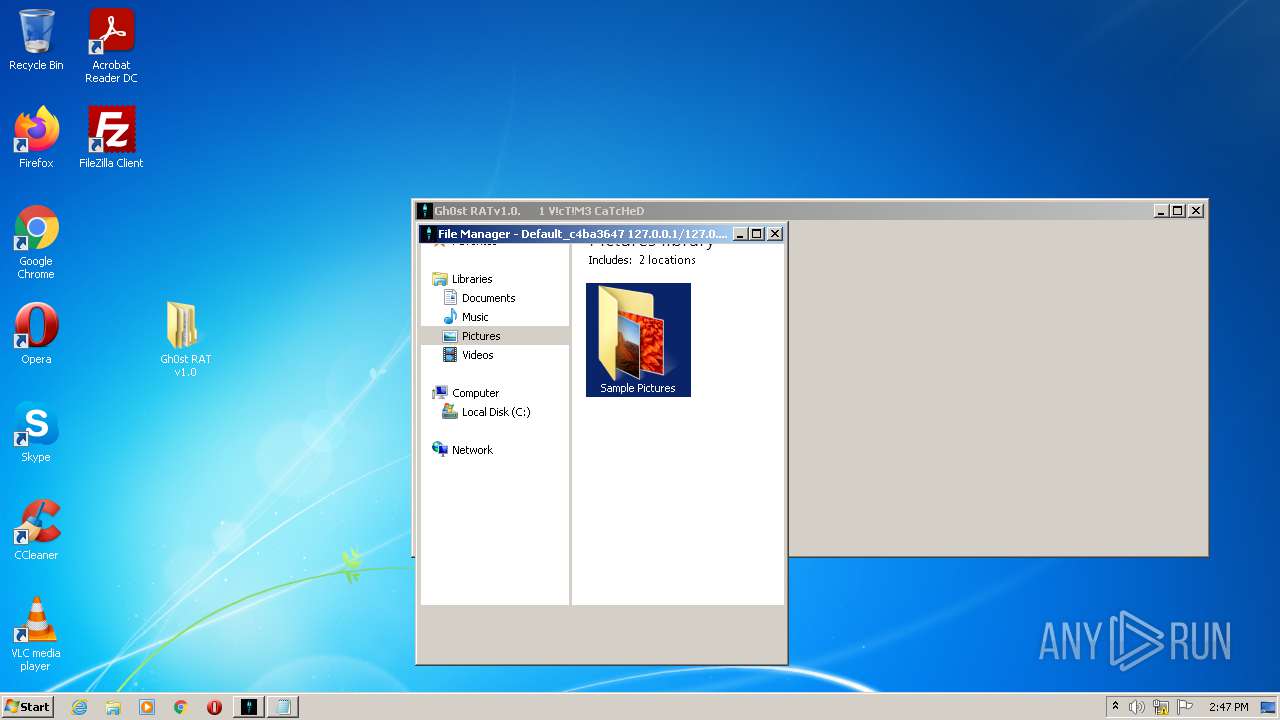
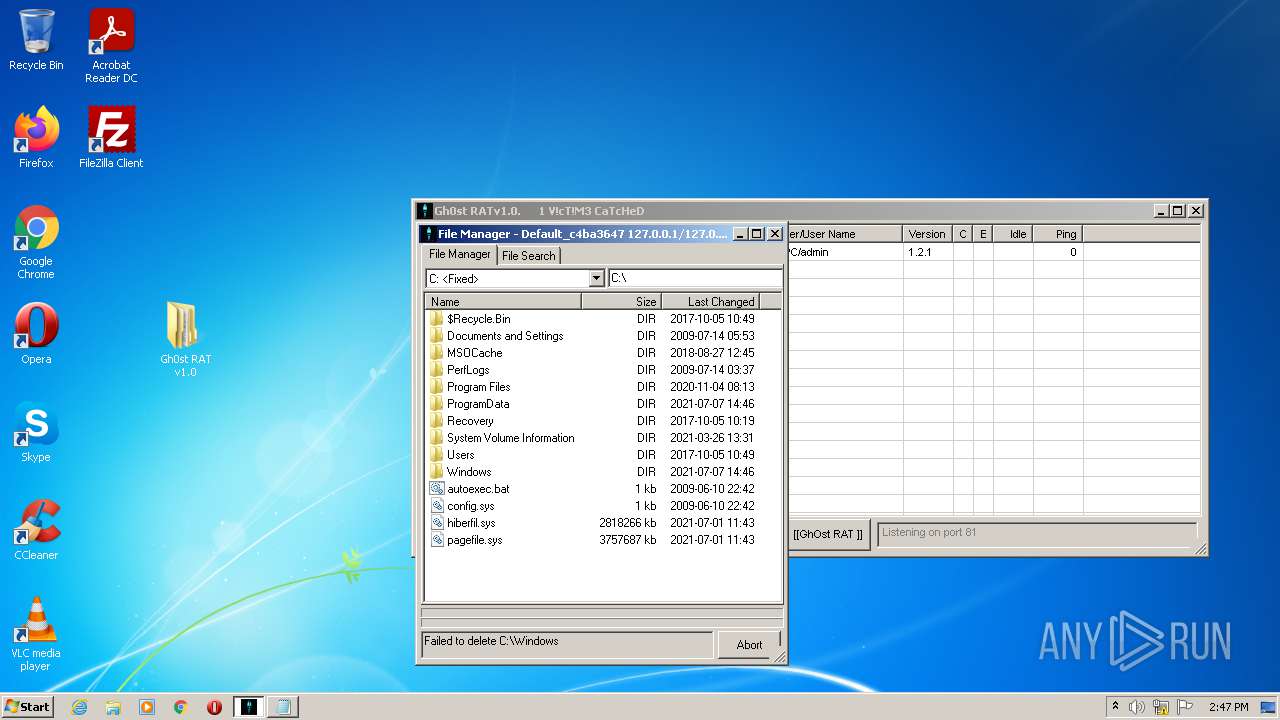
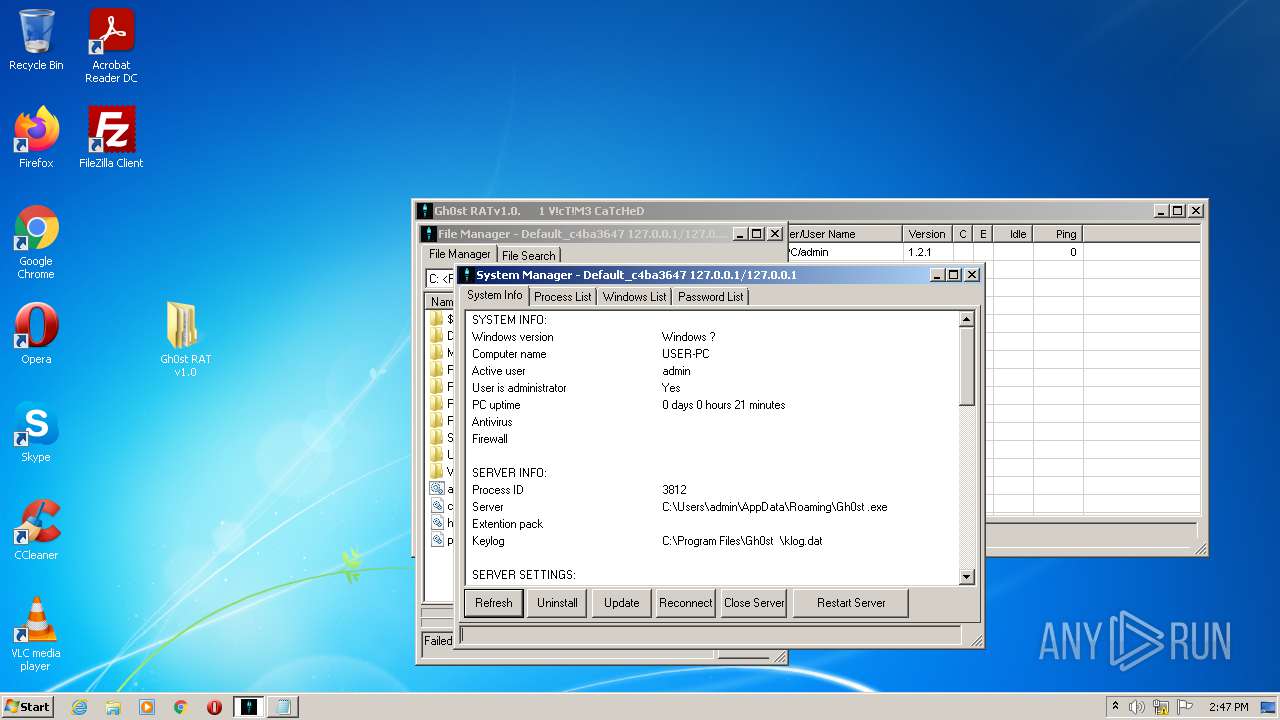
| File name: | Gh0st RAT v1.0.rar |
| Full analysis: | https://app.any.run/tasks/2581a017-1c57-457b-b5f5-fdc9686e9820 |
| Verdict: | Malicious activity |
| Analysis date: | July 07, 2021, 13:44:05 |
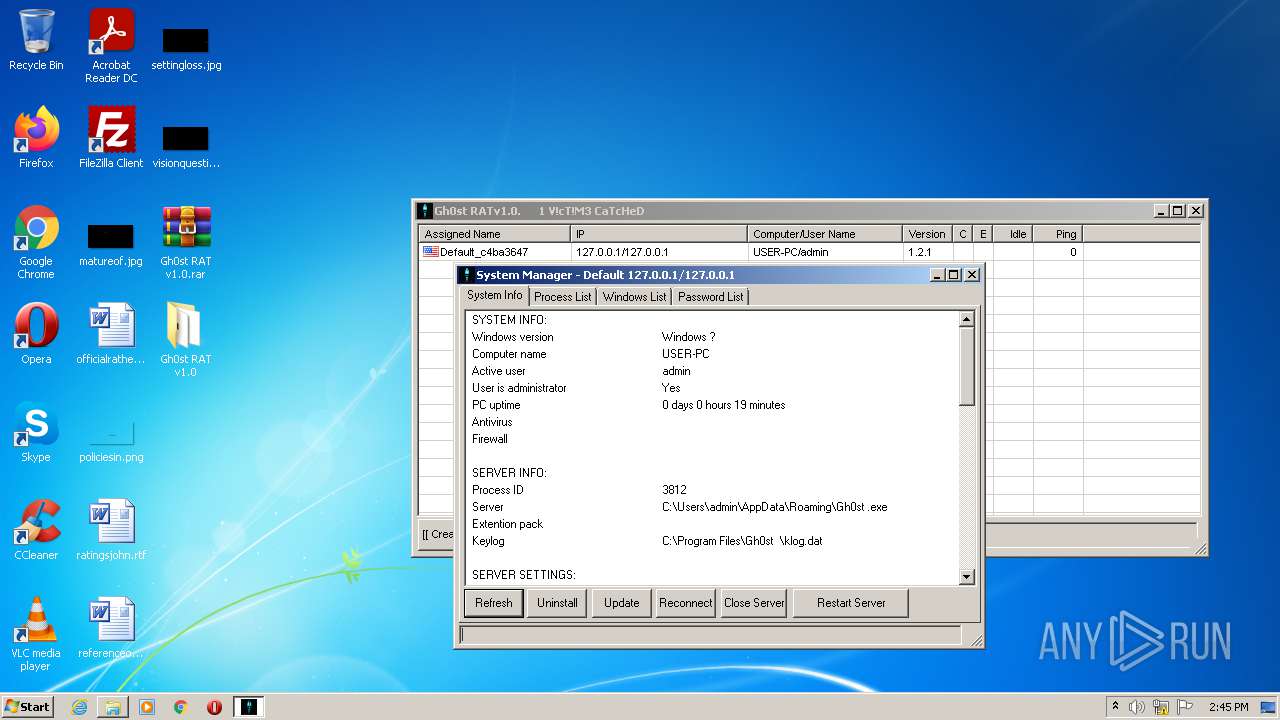
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: FirstVolume |
| MD5: | EF0A7CC5BF13D3569867A20F56682313 |
| SHA1: | 949FEA6951EF022B06B91E52BE9876D9852AD40F |
| SHA256: | 285F1196492FC129D454A28FB59B3FB93AAC7DA90EC3557EE99936C7A43C7151 |
| SSDEEP: | 24576:+CB4tisXpW7wtTY7F1/qzt0nHItGrBmNpEuLPfg/nh9Djoo33Sb/G:+CBmJs7F1yuotGC3uht3iq |
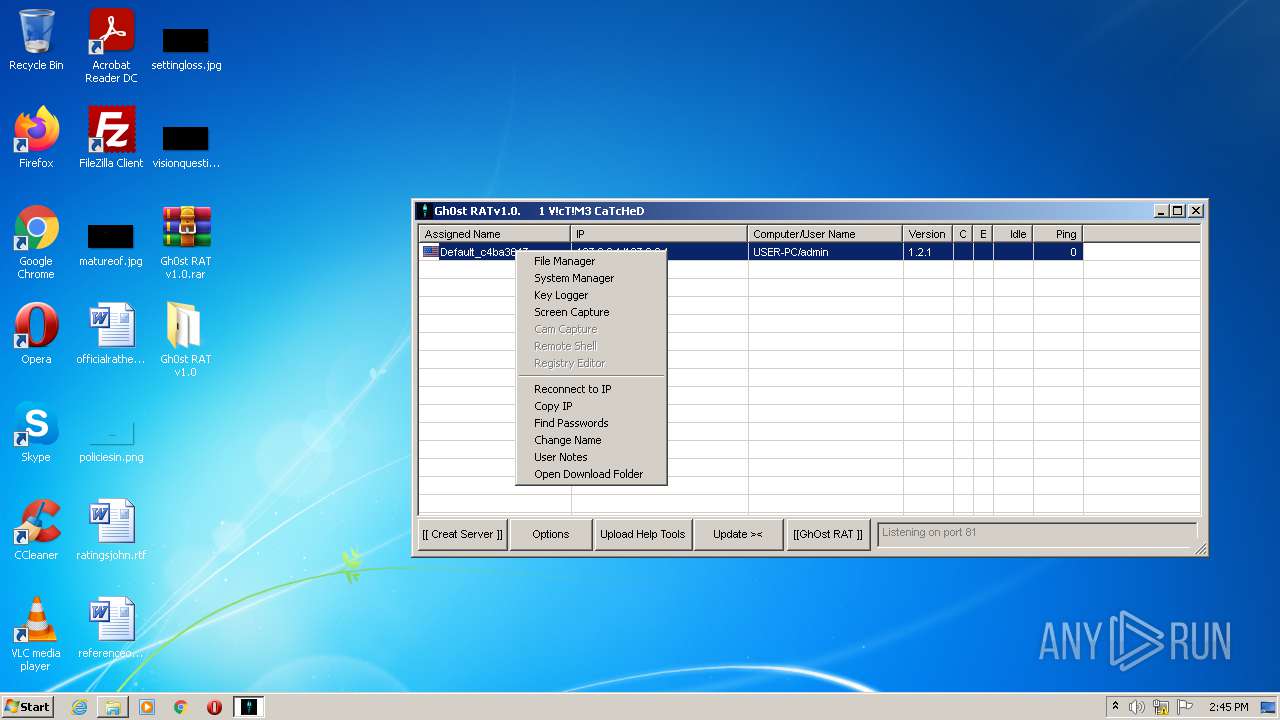
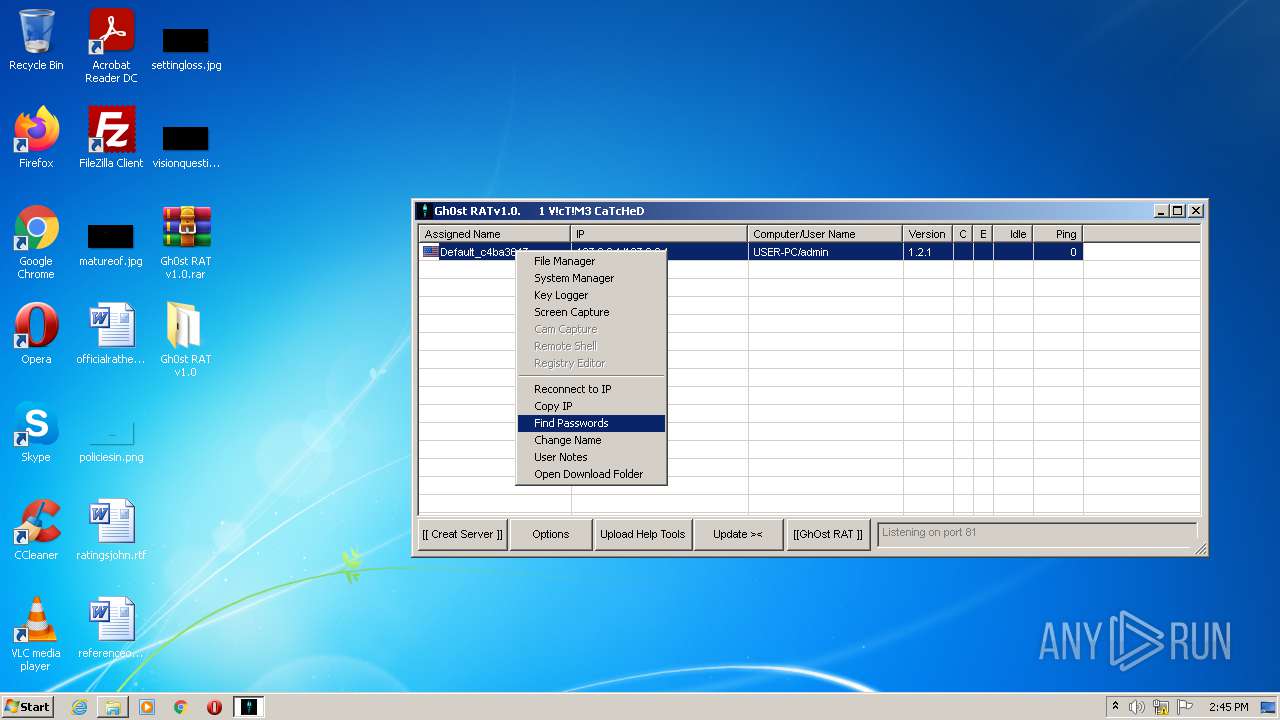
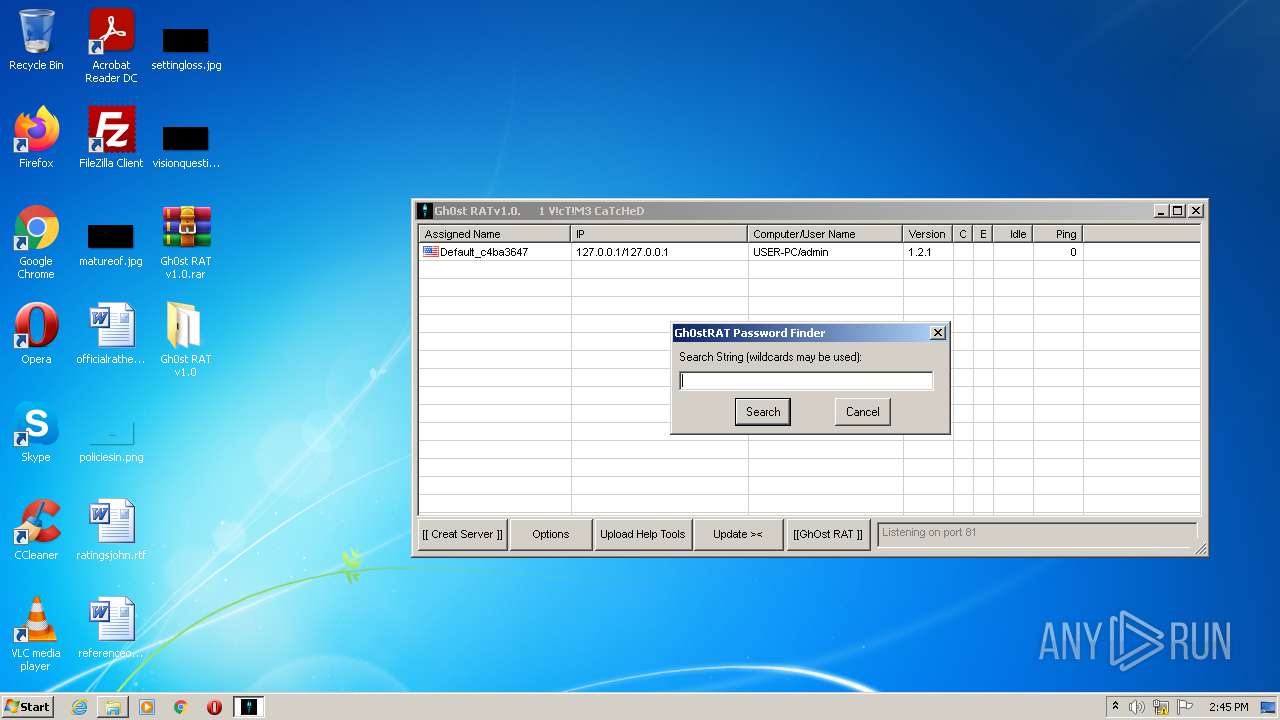
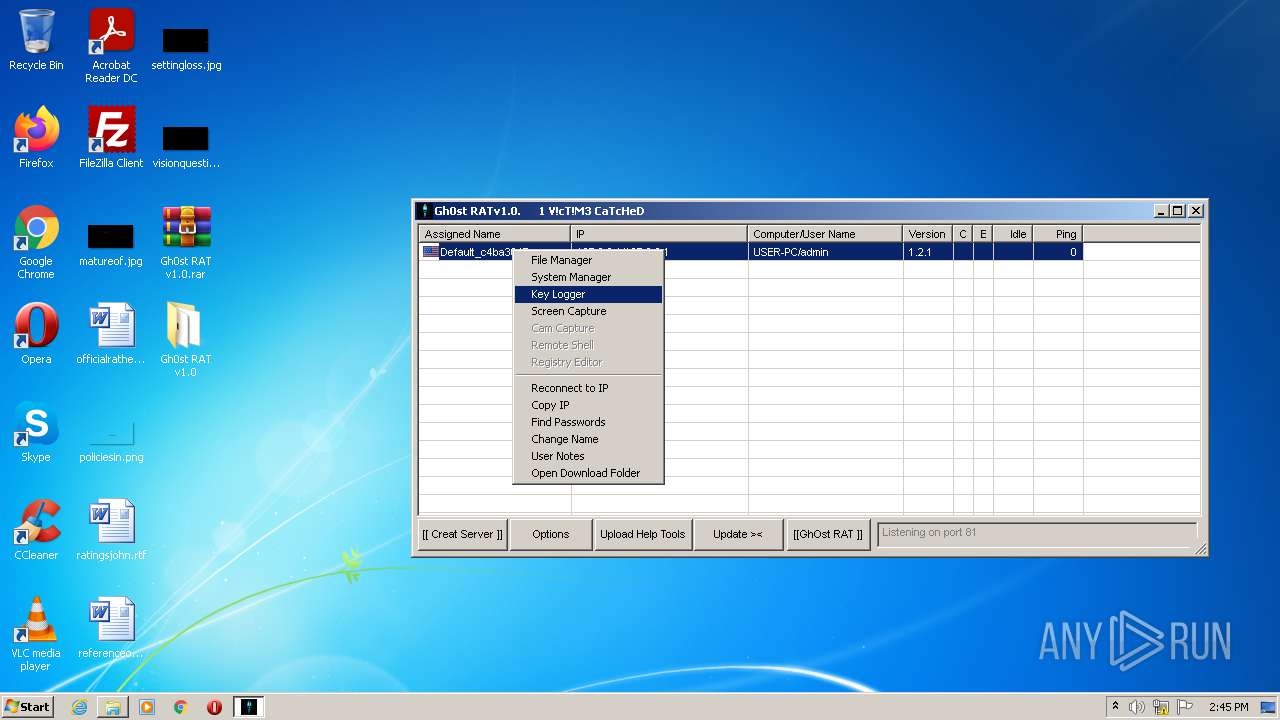
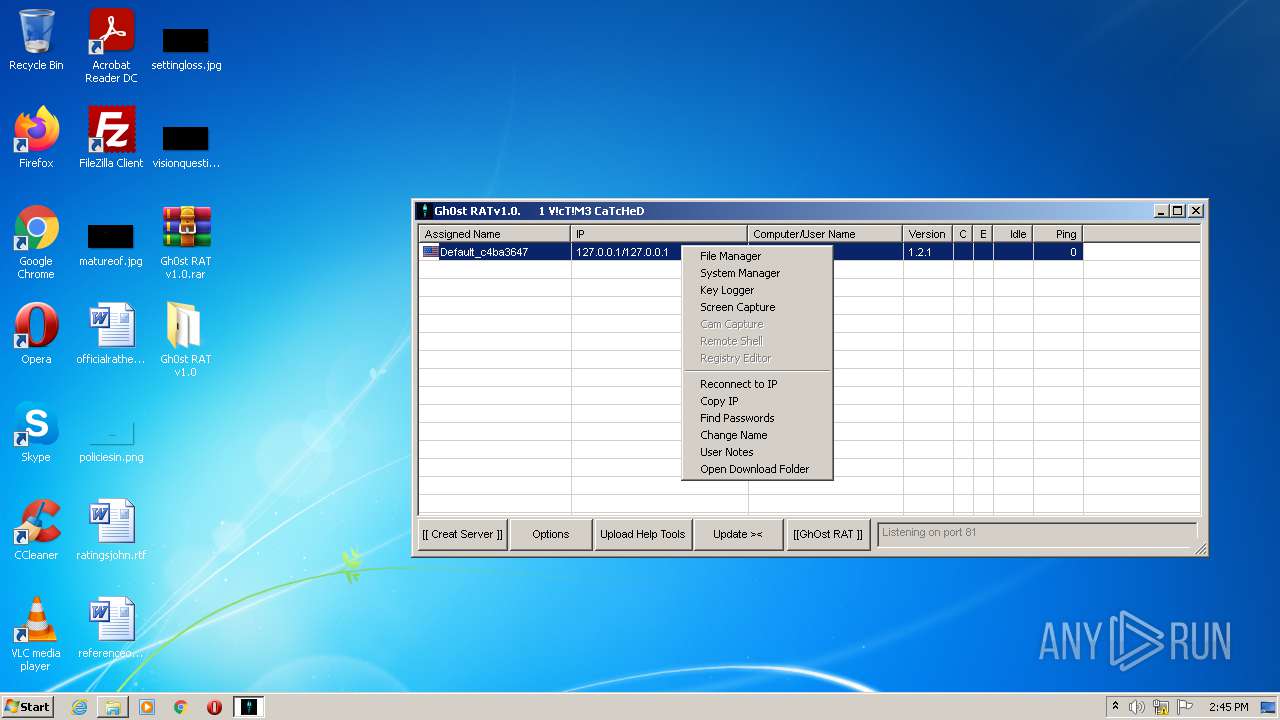
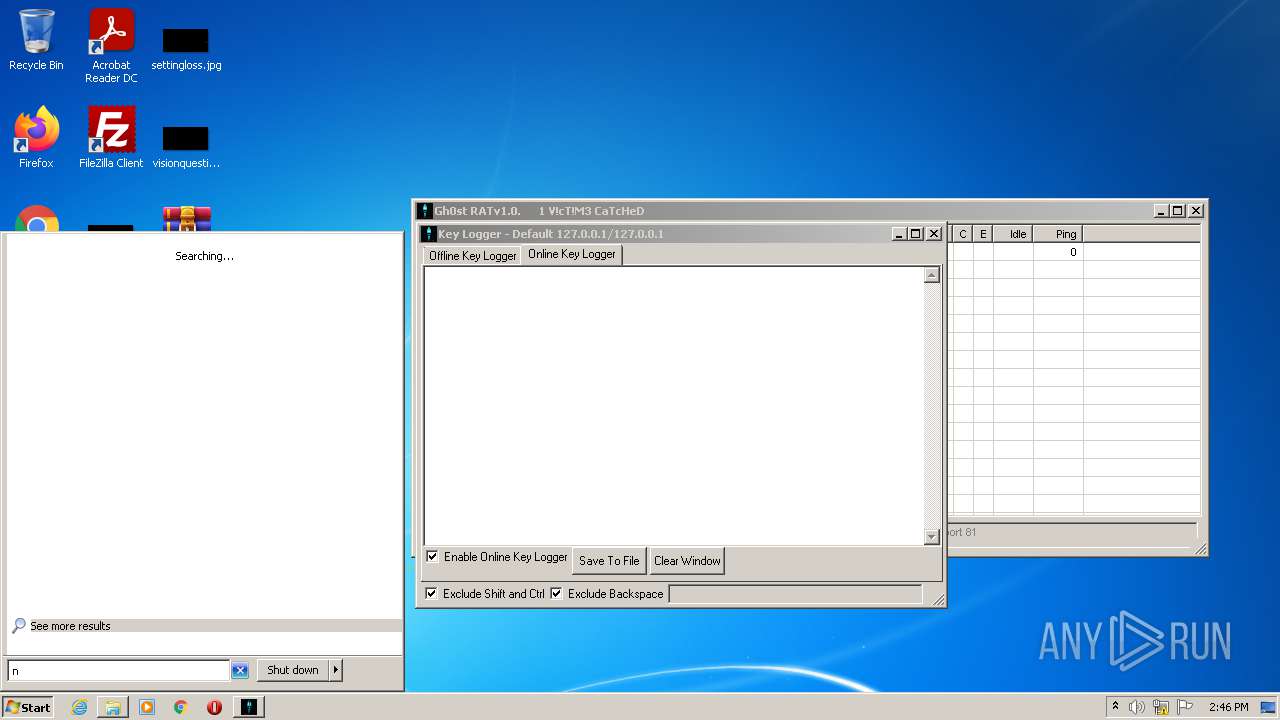
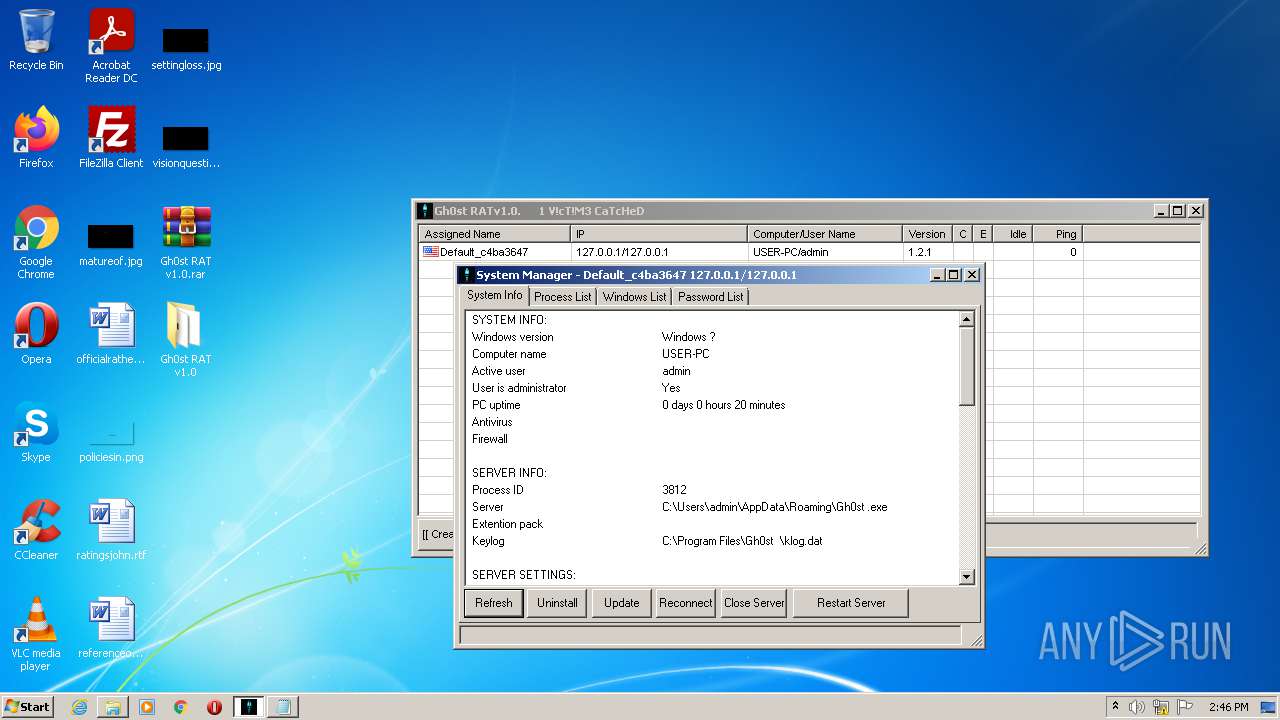
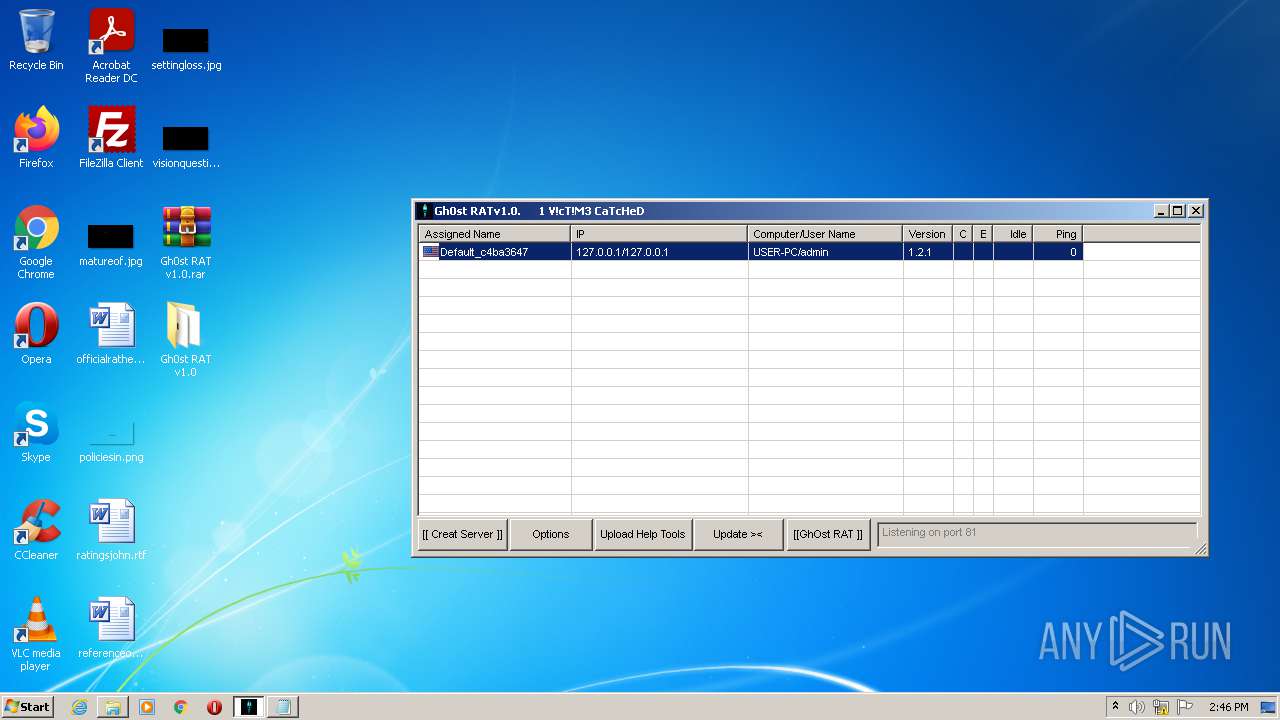
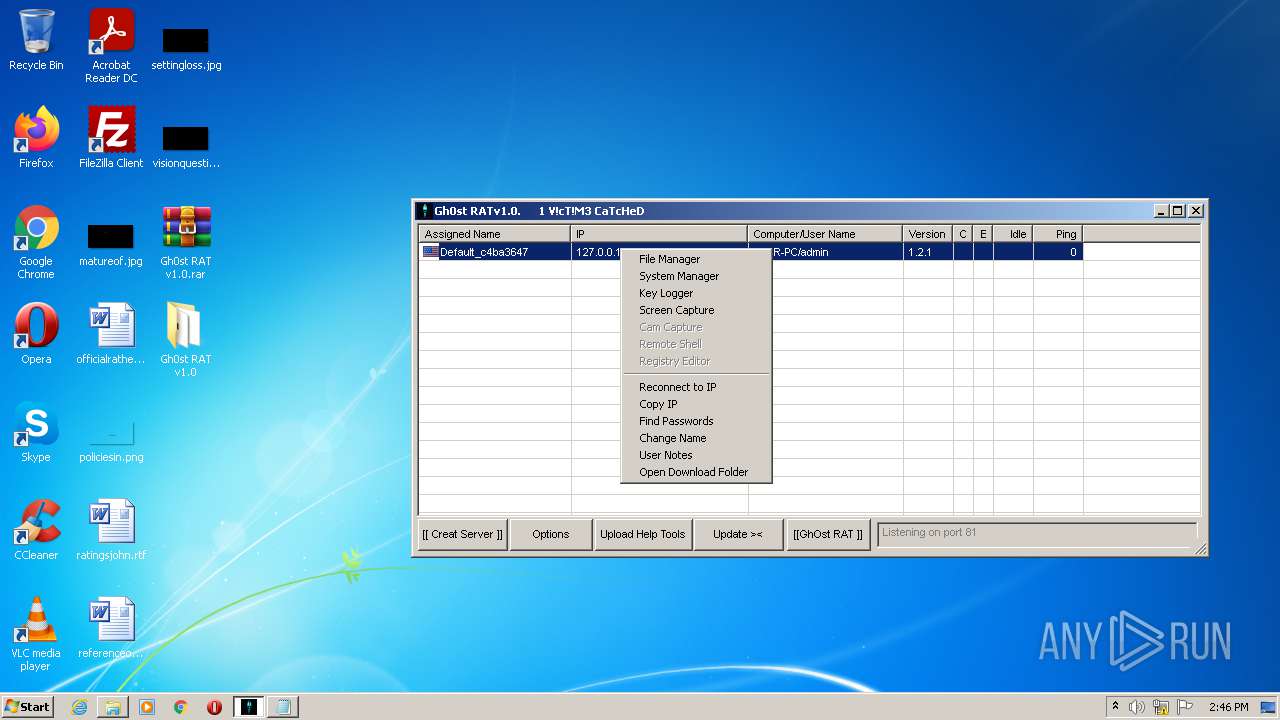
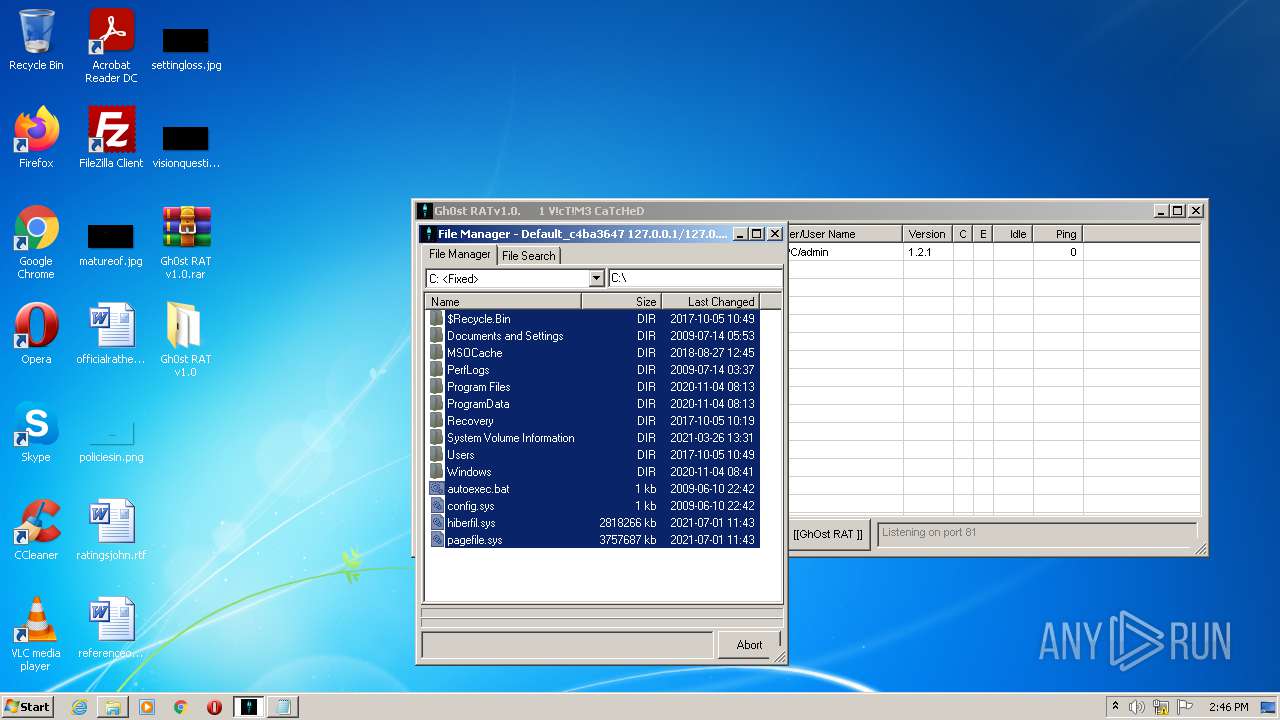
MALICIOUS
Application was dropped or rewritten from another process
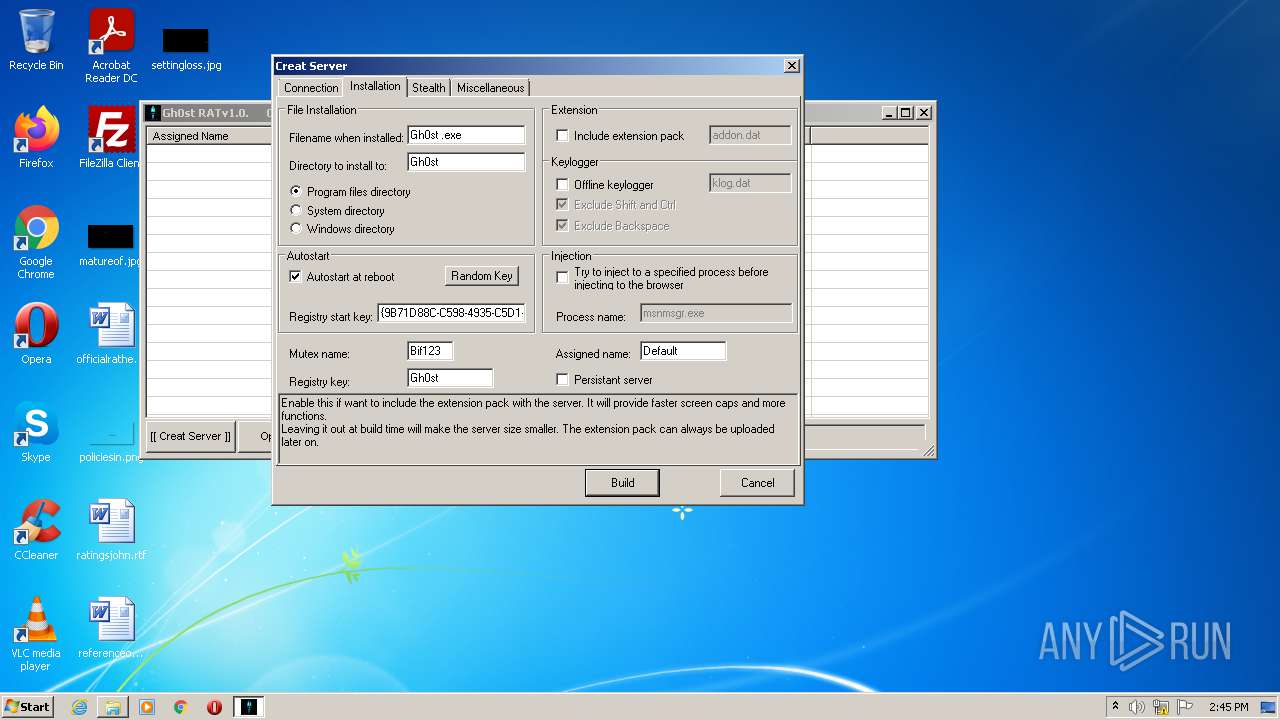
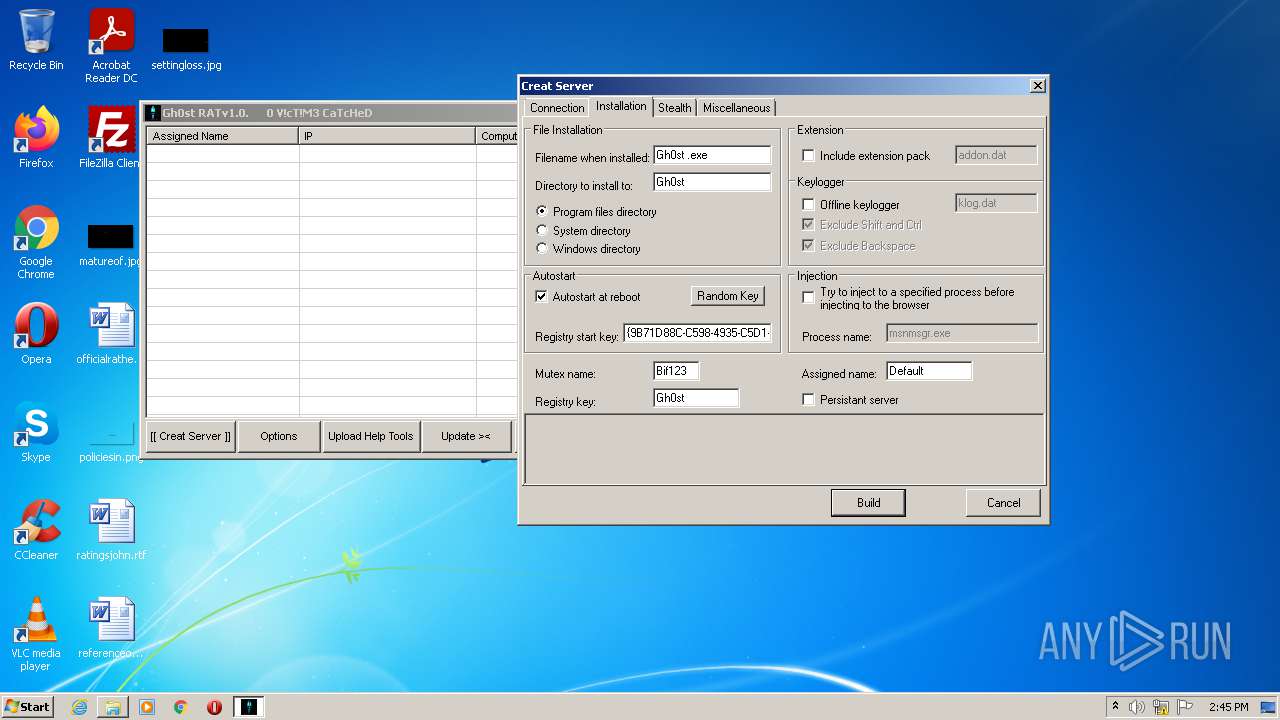
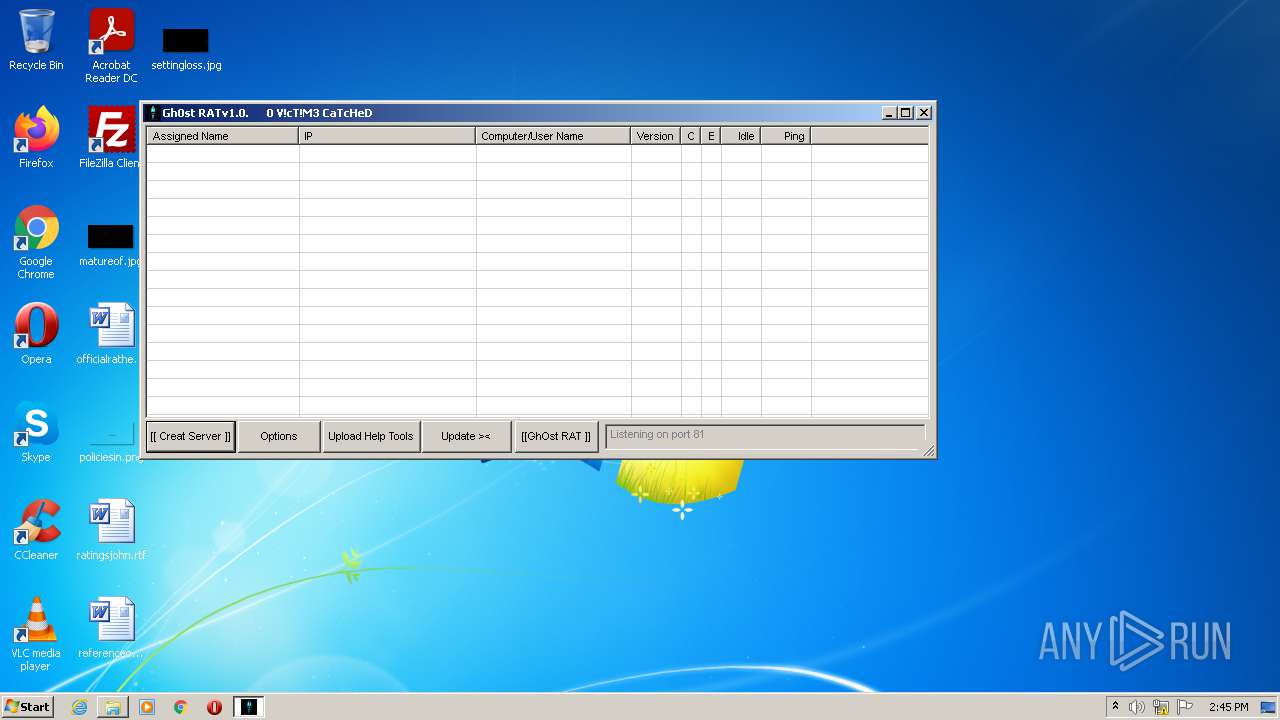
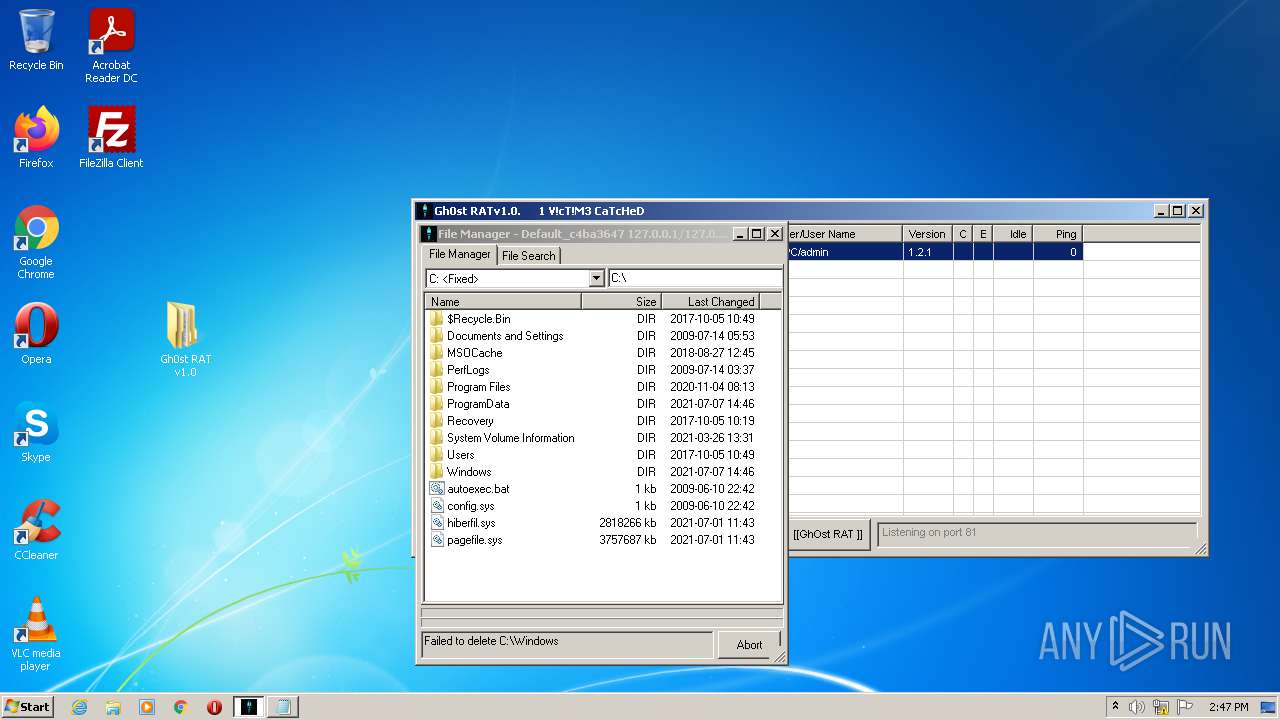
- GhOst RAT v1.0.exe (PID: 2828)
- Gh0stRAT.exe (PID: 3652)
- Gh0st .exe (PID: 4056)
Runs injected code in another process
- Gh0st .exe (PID: 4056)
- iexplore.exe (PID: 3812)
Application was injected by another process
- Explorer.EXE (PID: 1896)
Changes the autorun value in the registry
- Explorer.EXE (PID: 1896)
Drops executable file immediately after starts
- Explorer.EXE (PID: 1896)
SUSPICIOUS
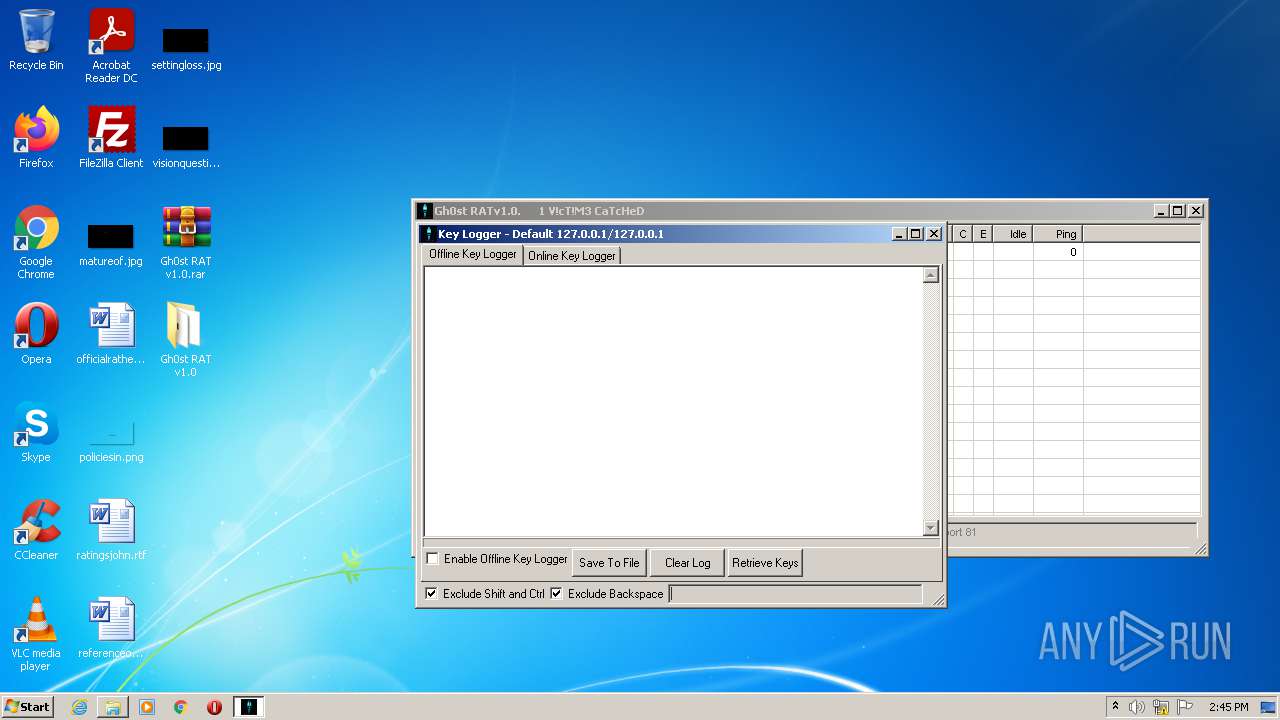
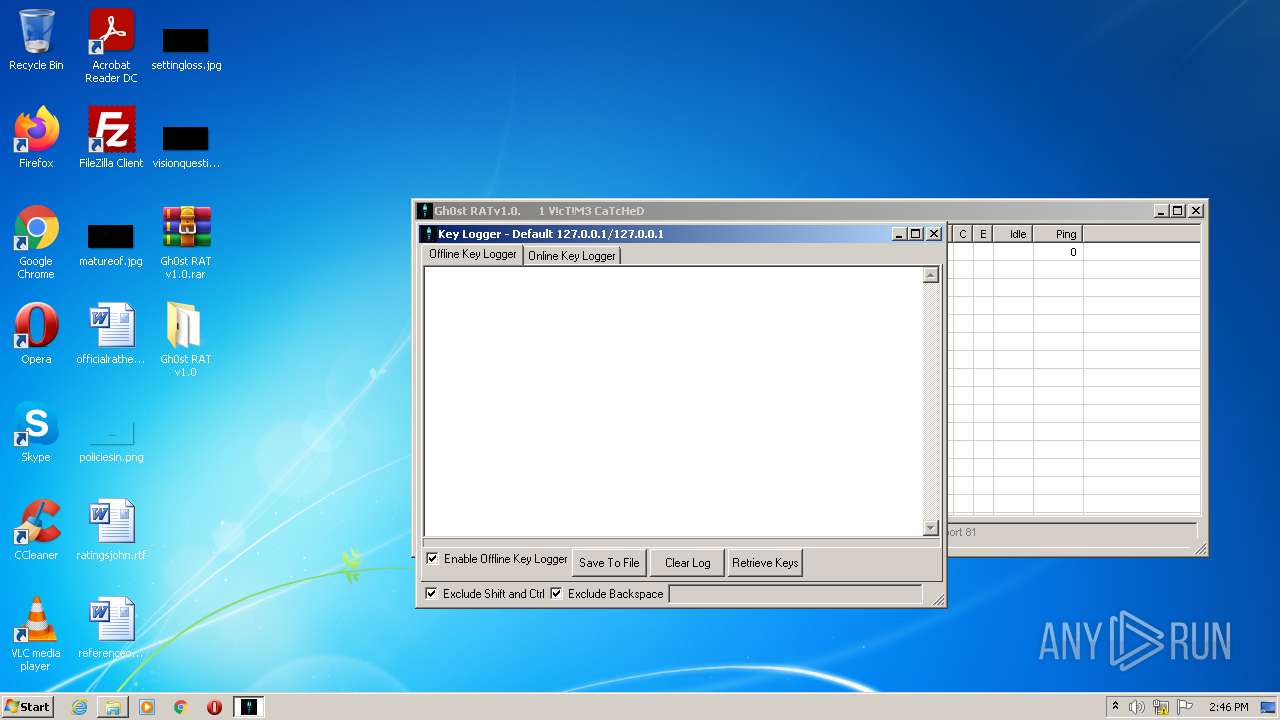
Reads the computer name
- WinRAR.exe (PID: 1164)
- Gh0stRAT.exe (PID: 3652)
Checks supported languages
- WinRAR.exe (PID: 1164)
- GhOst RAT v1.0.exe (PID: 2828)
- Gh0stRAT.exe (PID: 3652)
- Gh0st .exe (PID: 4056)
- Explorer.EXE (PID: 1896)
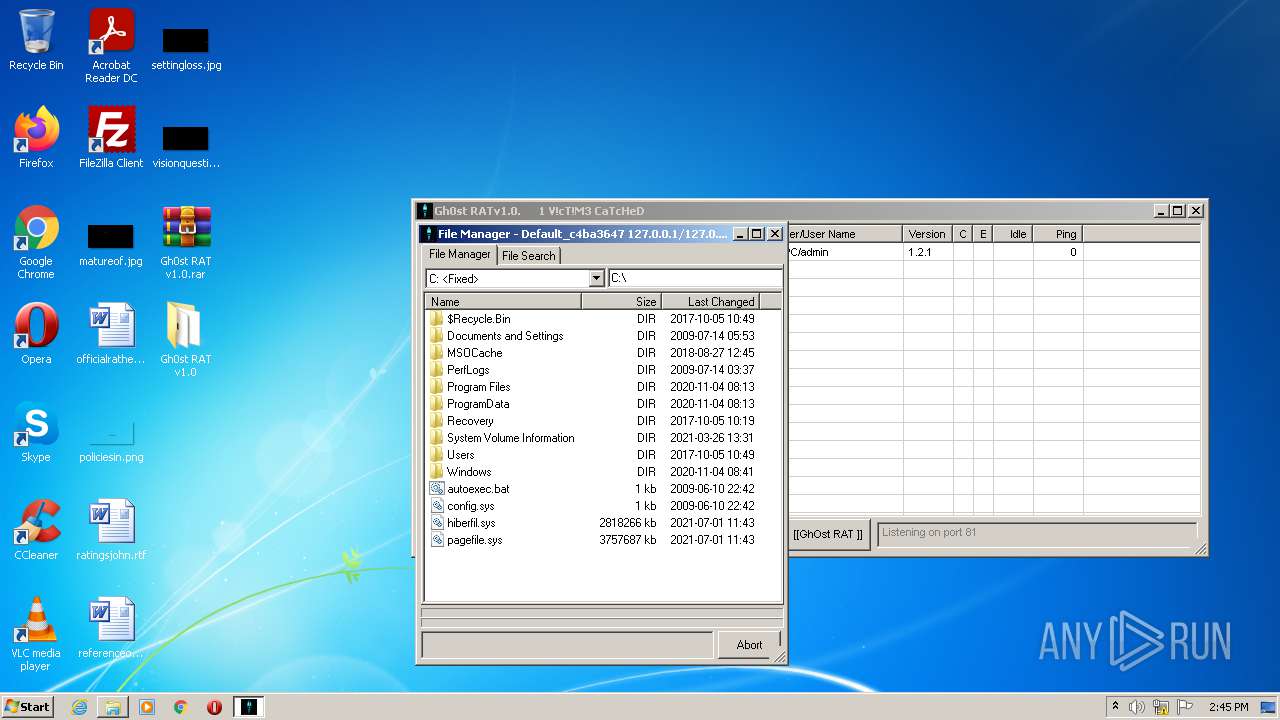
Creates files in the user directory
- Explorer.EXE (PID: 1896)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1164)
- Gh0stRAT.exe (PID: 3652)
- Explorer.EXE (PID: 1896)
Drops a file with too old compile date
- WinRAR.exe (PID: 1164)
- Gh0stRAT.exe (PID: 3652)
- Explorer.EXE (PID: 1896)
Starts Internet Explorer
- Explorer.EXE (PID: 1896)
Reads default file associations for system extensions
- Gh0stRAT.exe (PID: 3652)
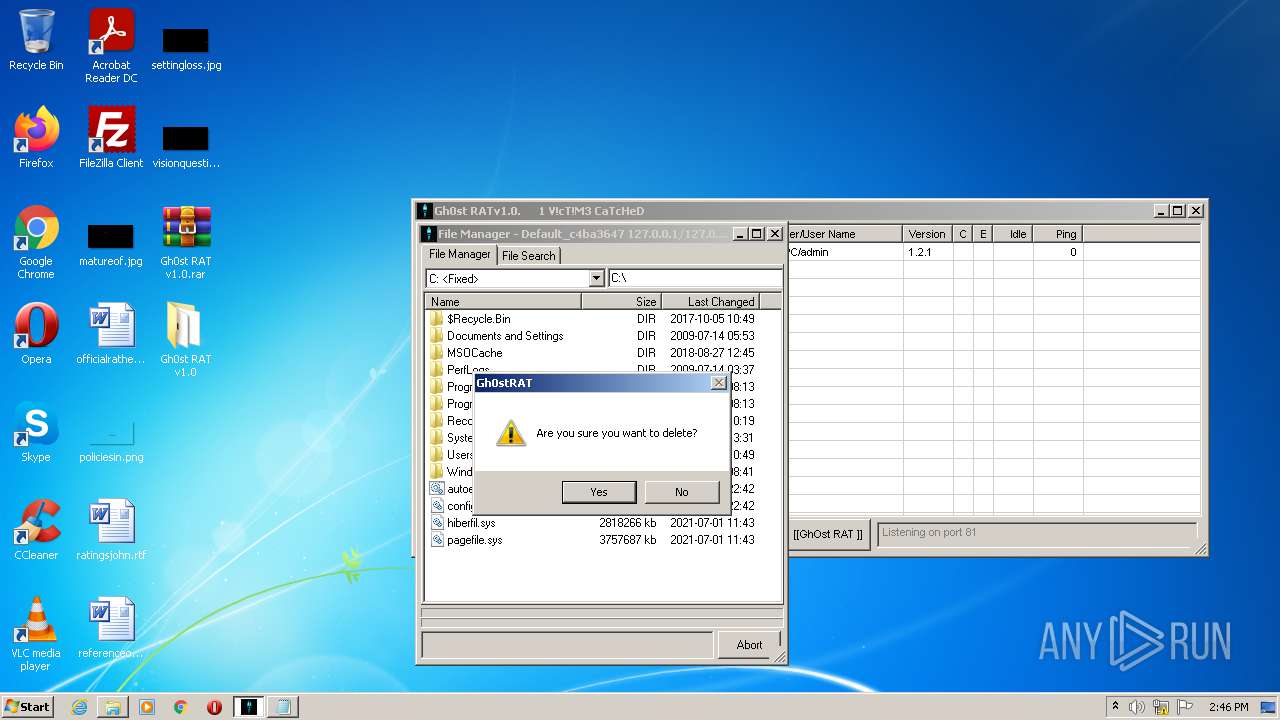
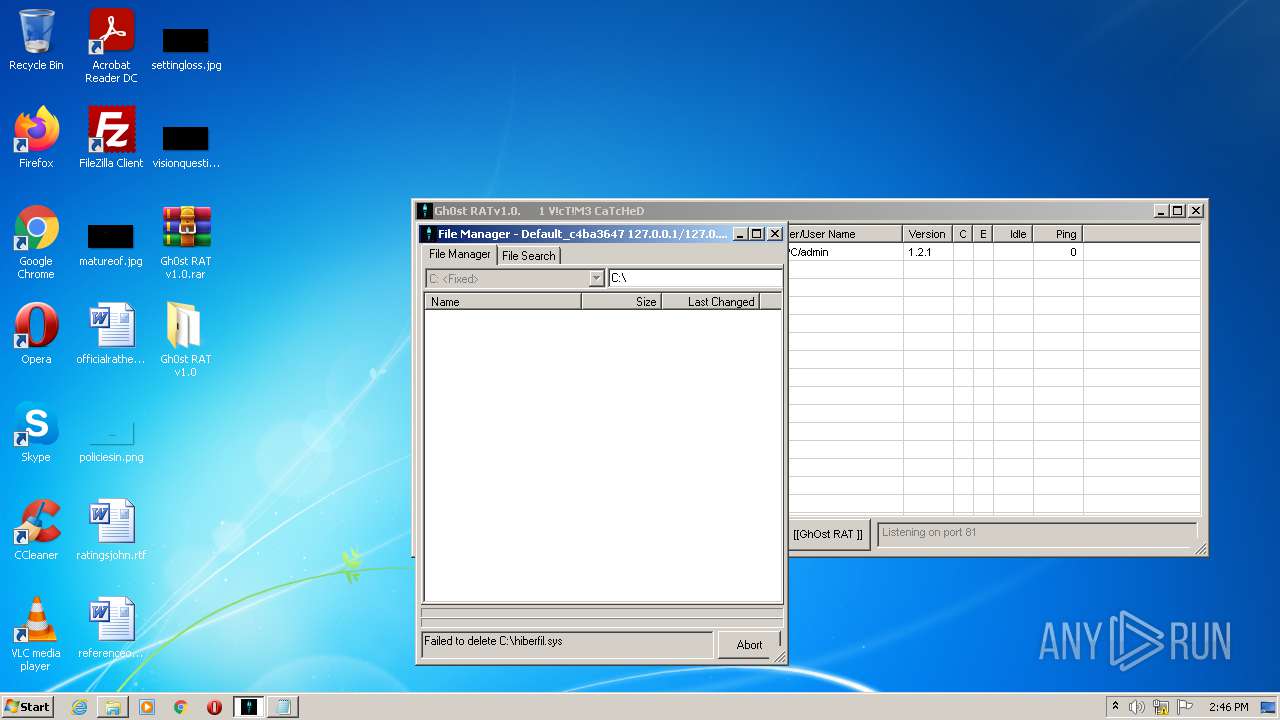
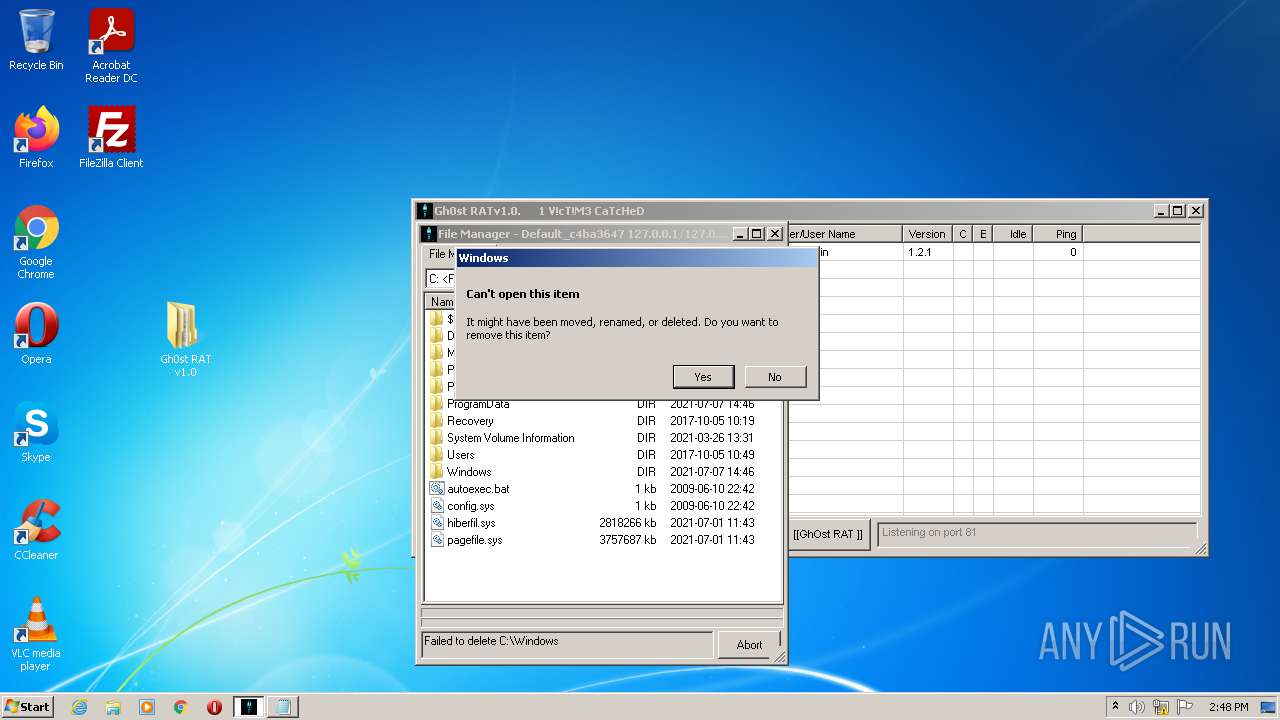
Removes files from Windows directory
- iexplore.exe (PID: 3812)
INFO
Checks supported languages
- NOTEPAD.EXE (PID: 2160)
- iexplore.exe (PID: 3812)
- notepad.exe (PID: 1844)
Manual execution by user
- NOTEPAD.EXE (PID: 2160)
- GhOst RAT v1.0.exe (PID: 2828)
- Gh0st .exe (PID: 4056)
- iexplore.exe (PID: 3812)
- notepad.exe (PID: 1844)
Reads the computer name
- iexplore.exe (PID: 3812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
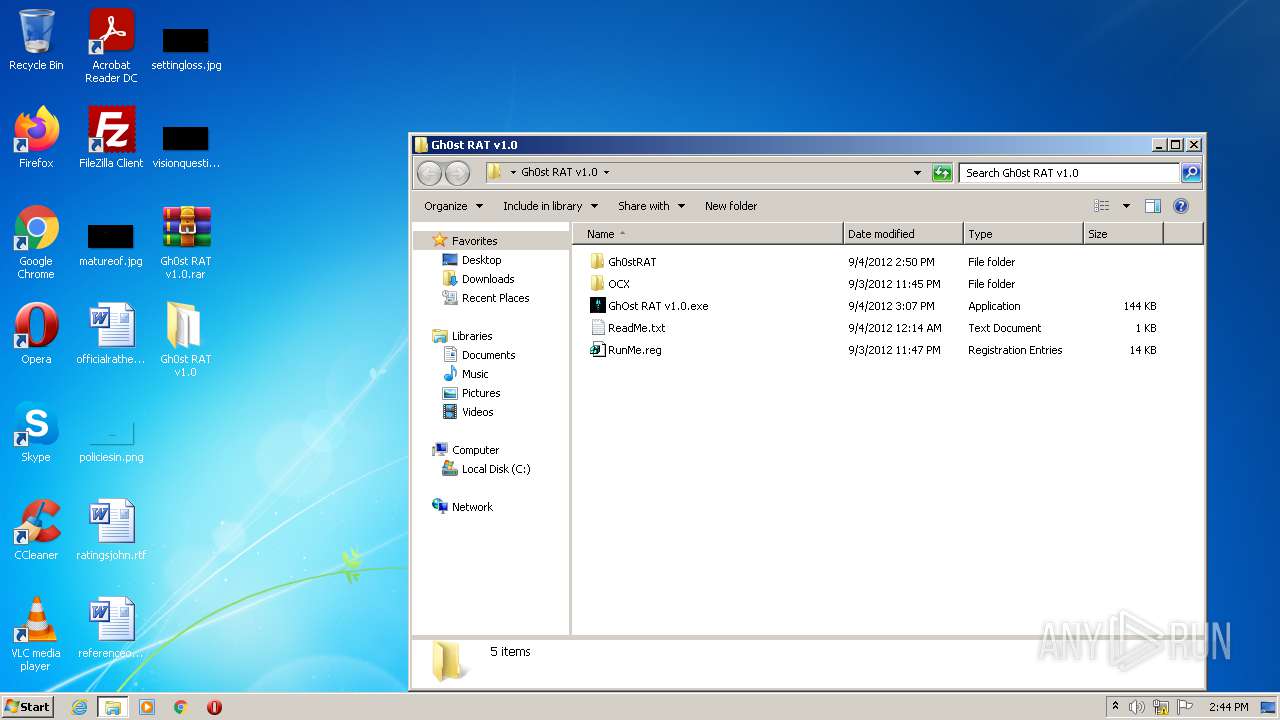
| ArchivedFileName: | Gh0st RAT v1.0\Gh0stRAT\Gh0stRAT.exe |
|---|---|
| PackingMethod: | Normal |
| ModifyDate: | 2012:09:03 23:33:09 |
| OperatingSystem: | Win32 |
| UncompressedSize: | 1843200 |
| CompressedSize: | 1131206 |
Total processes
45
Monitored processes
8
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Gh0st RAT v1.0.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1844 | "C:\Windows\system32\notepad.exe" | C:\Windows\system32\notepad.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1896 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2160 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Gh0st RAT v1.0\ReadMe.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
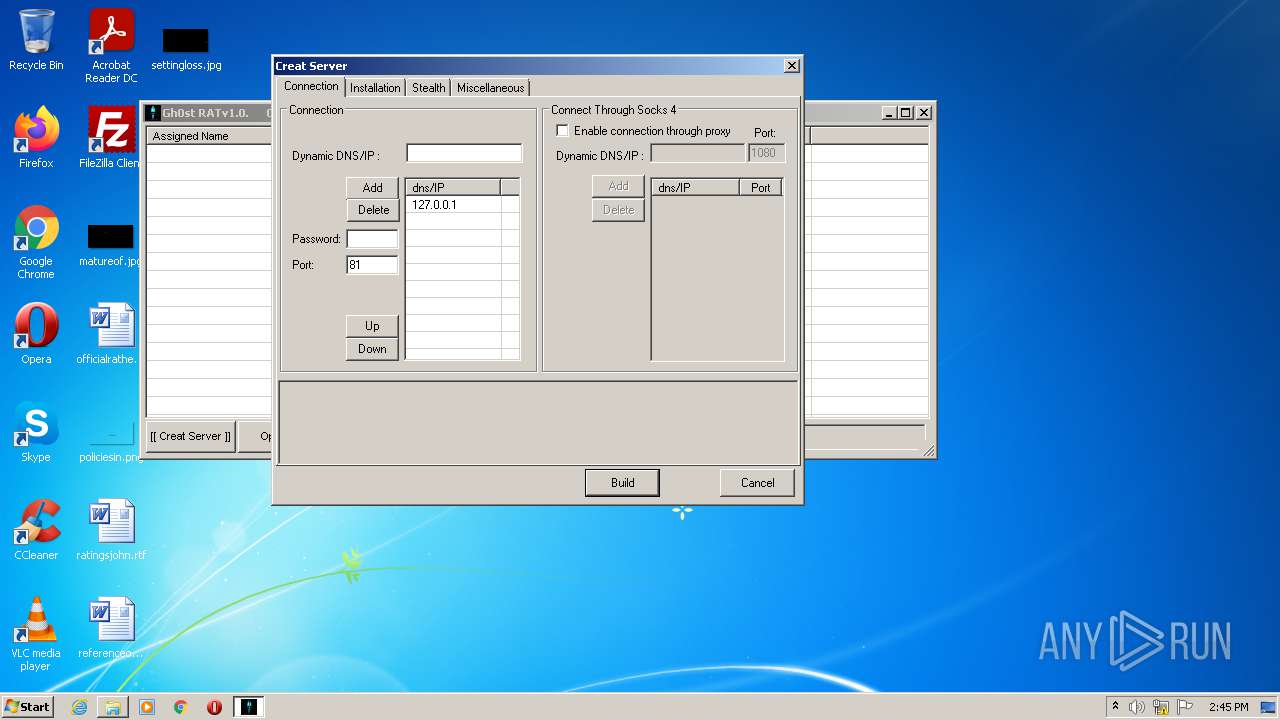
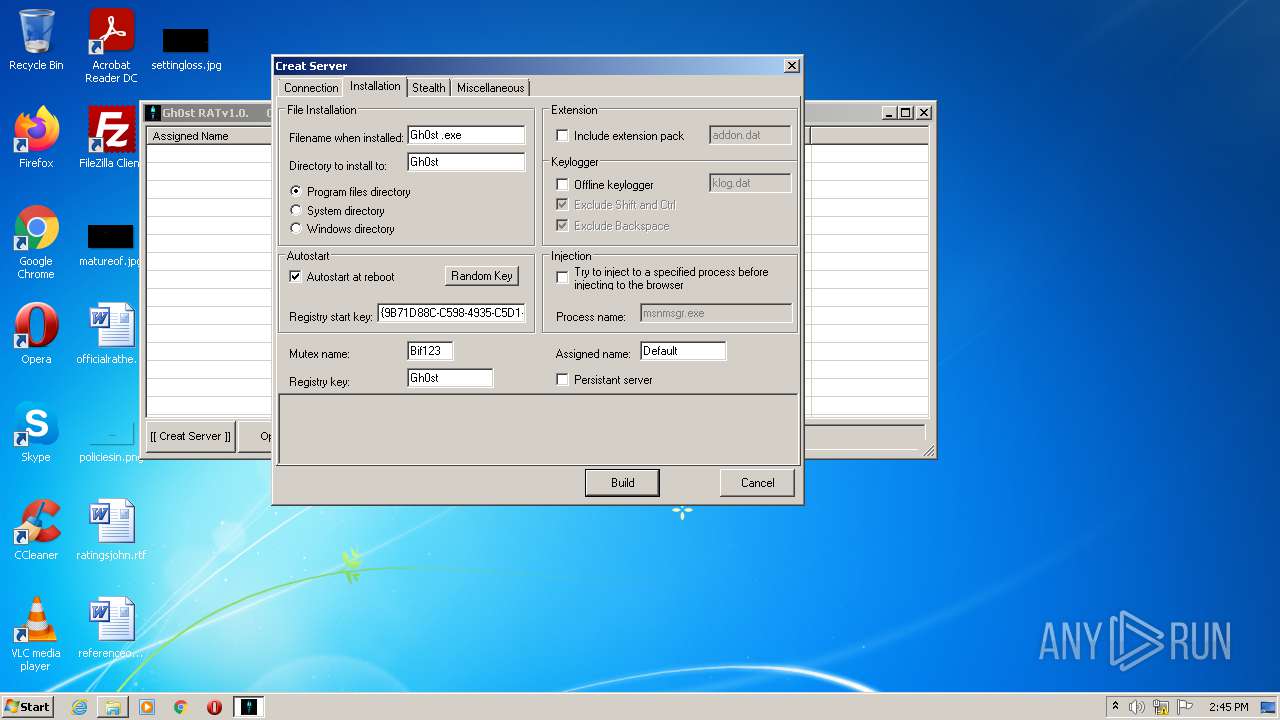
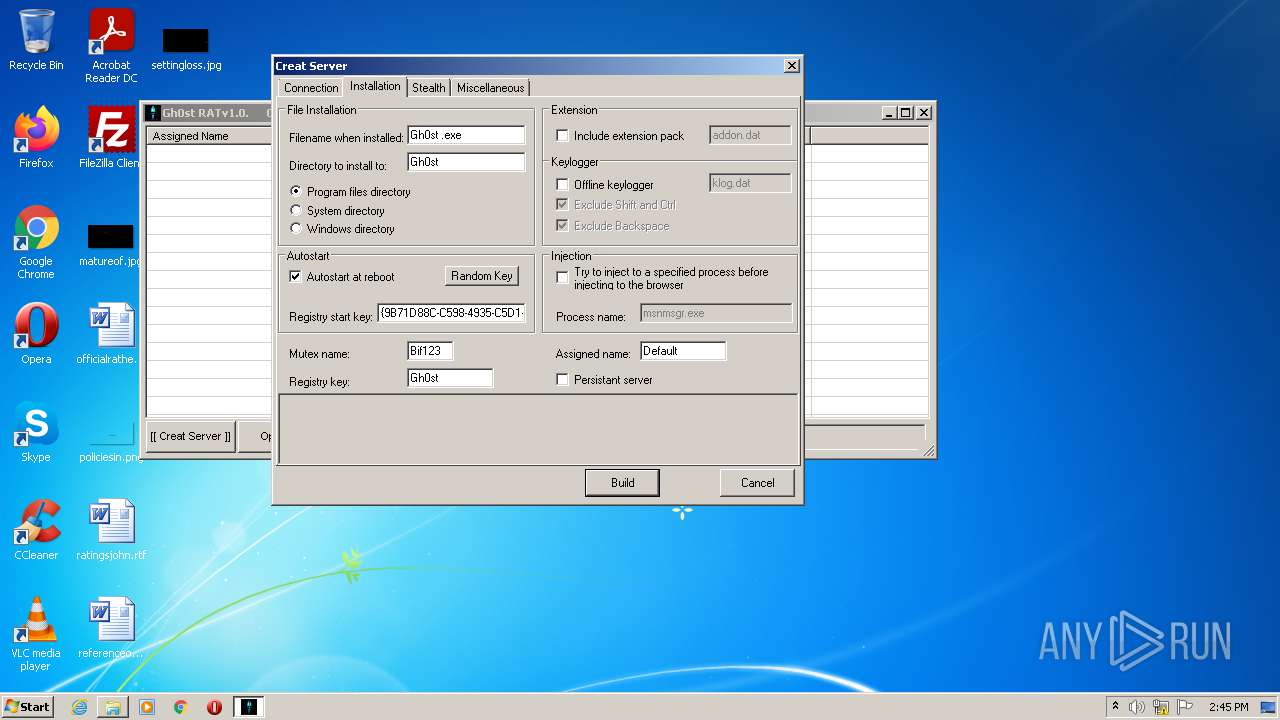
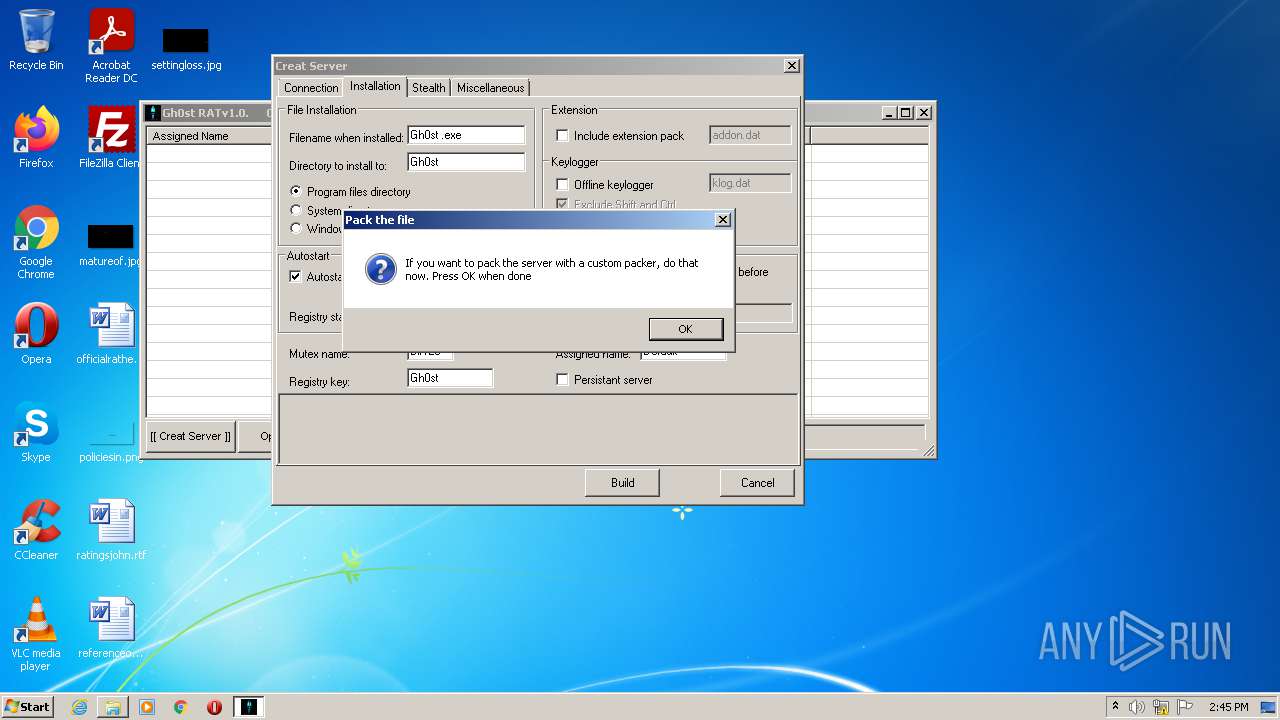
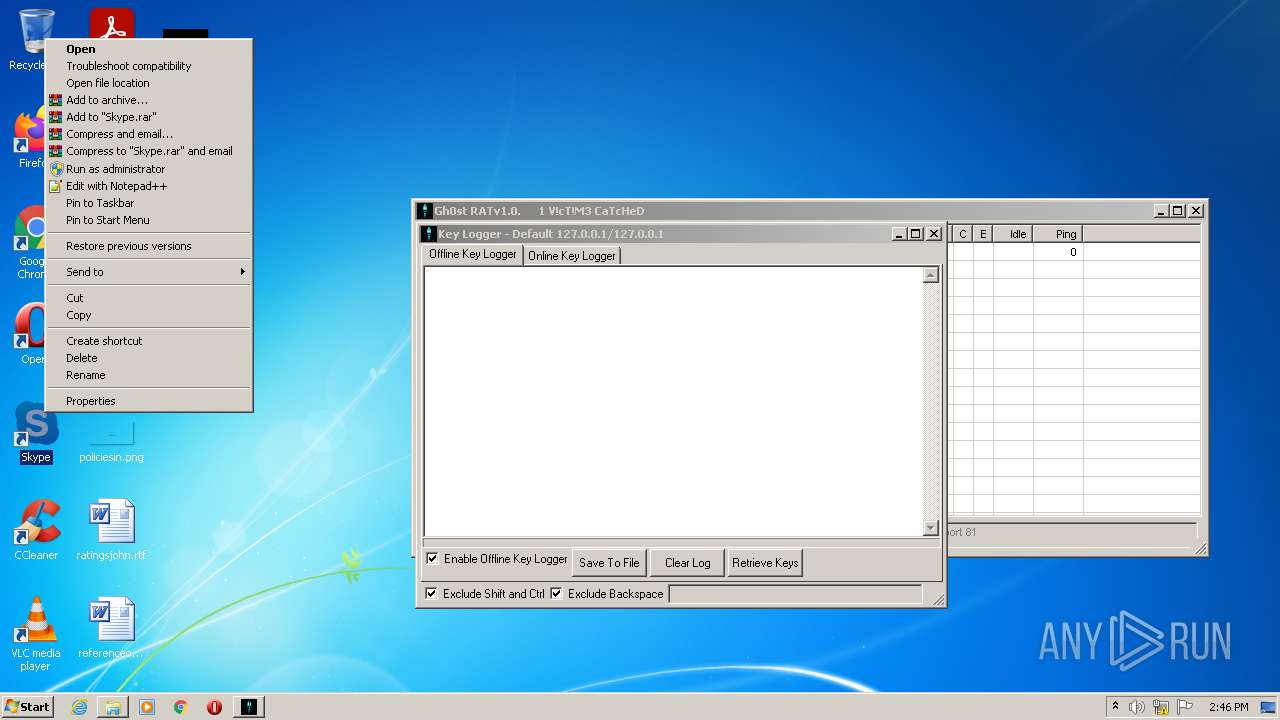
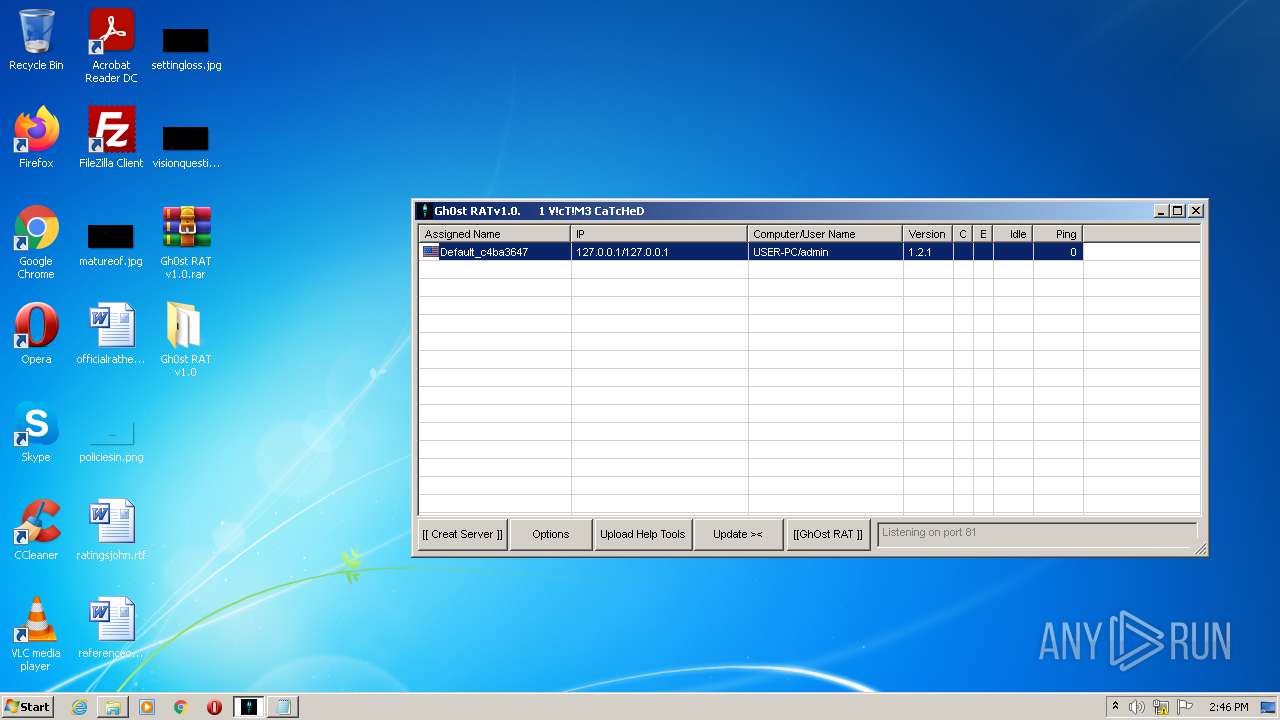
| 2828 | "C:\Users\admin\Desktop\Gh0st RAT v1.0\GhOst RAT v1.0.exe" | C:\Users\admin\Desktop\Gh0st RAT v1.0\GhOst RAT v1.0.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Dz_force TEAm Integrity Level: MEDIUM Description: Gh0stRAT v1.0 Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3652 | "C:\Users\admin\Desktop\Gh0st RAT v1.0\Gh0stRAT\Gh0stRAT.exe" | C:\Users\admin\Desktop\Gh0st RAT v1.0\Gh0stRAT\Gh0stRAT.exe | GhOst RAT v1.0.exe | ||||||||||||
User: admin Company: https://www.facebook.com/HaCkIngIsOurBlOod Integrity Level: MEDIUM Description: Gh0stRAT v1.0 Exit code: 0 Version: 1, 0, 0, 0 Modules
| |||||||||||||||
| 3812 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4056 | "C:\Users\admin\Desktop\Gh0st RAT v1.0\Gh0st .exe" | C:\Users\admin\Desktop\Gh0st RAT v1.0\Gh0st .exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
14 483
Read events
13 557
Write events
926
Delete events
0
Modification events
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Gh0st RAT v1.0.rar | |||
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1164) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1896) Explorer.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
6
Suspicious files
5
Text files
2
Unknown types
8
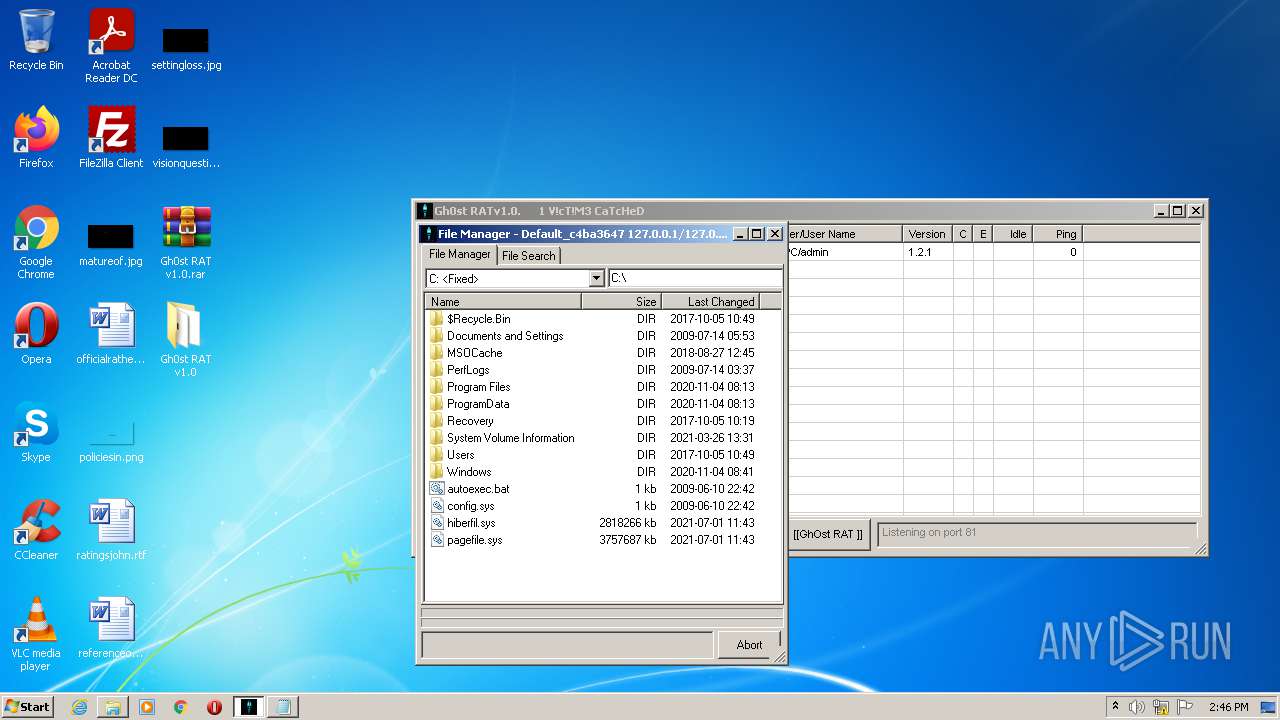
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1896 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 1896 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\Gh0st RAT v1.0\ReadMe.txt | text | |
MD5:— | SHA256:— | |||
| 1896 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\918e0ecb43d17e23.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 1896 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Gh0st RAT v1.0.lnk | lnk | |
MD5:— | SHA256:— | |||
| 1896 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Gh0st .exe | executable | |
MD5:— | SHA256:— | |||
| 1896 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Gh0st RAT v1.0.rar.lnk | lnk | |
MD5:— | SHA256:— | |||
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\Gh0st RAT v1.0\RunMe.reg | text | |
MD5:— | SHA256:— | |||
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\Gh0st RAT v1.0\OCX\actskin4.ocx | executable | |
MD5:— | SHA256:— | |||
| 1896 | Explorer.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\ReadMe.txt.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report