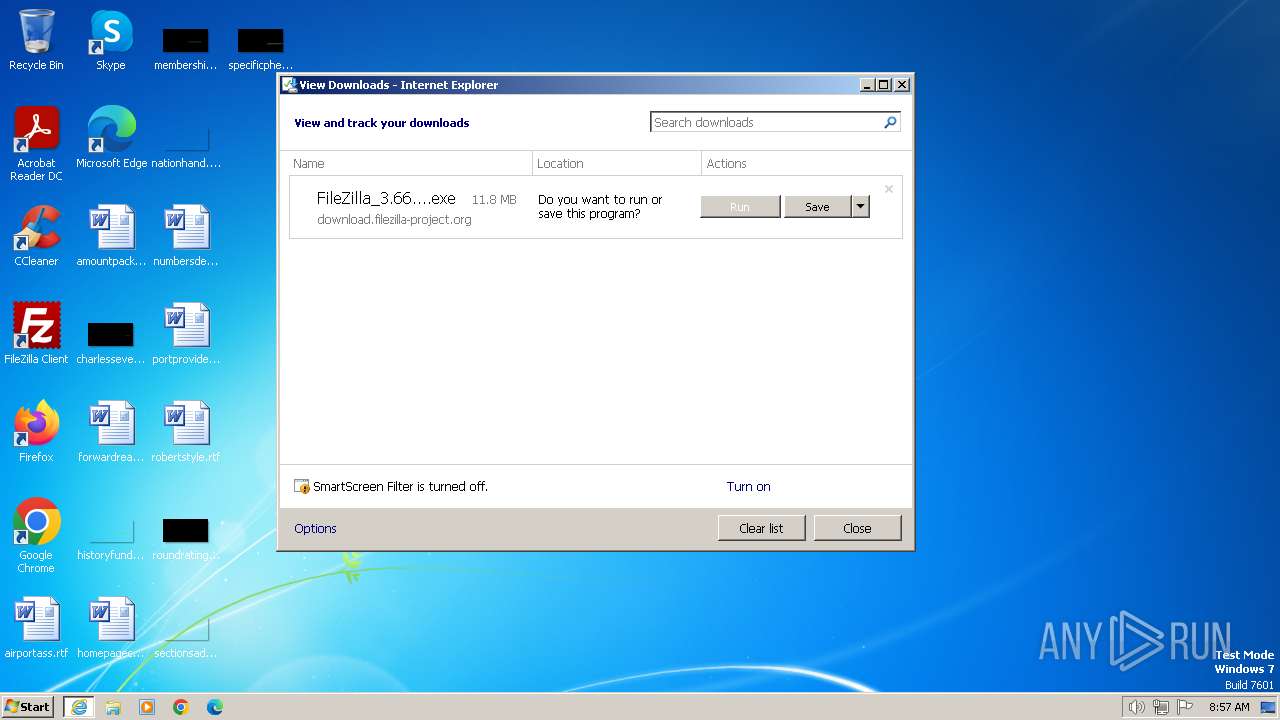
| URL: | https://download.filezilla-project.org/client/FileZilla_3.66.5_win64_sponsored-setup.exe |
| Full analysis: | https://app.any.run/tasks/5bb5d7a7-eea9-4c06-a317-3f8c07d88b77 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2024, 08:57:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F3EC0D003484A481AEB2C5DD0FE9124D |
| SHA1: | F390B225EC491BBE33344E3D9C74F6AEA4945A67 |
| SHA256: | 285A00669044B5ADBF394F57AA584F498C15DDAE593611BA9527EB214D4EA98B |
| SSDEEP: | 3:N8SElQw0EIVEjR+XKdpJEpjXLd6Wg5kIWARAkA:2SKHJRhKNXnOrAkA |
MALICIOUS
Drops the executable file immediately after the start
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
- uninstall.exe (PID: 2256)
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
SUSPICIOUS
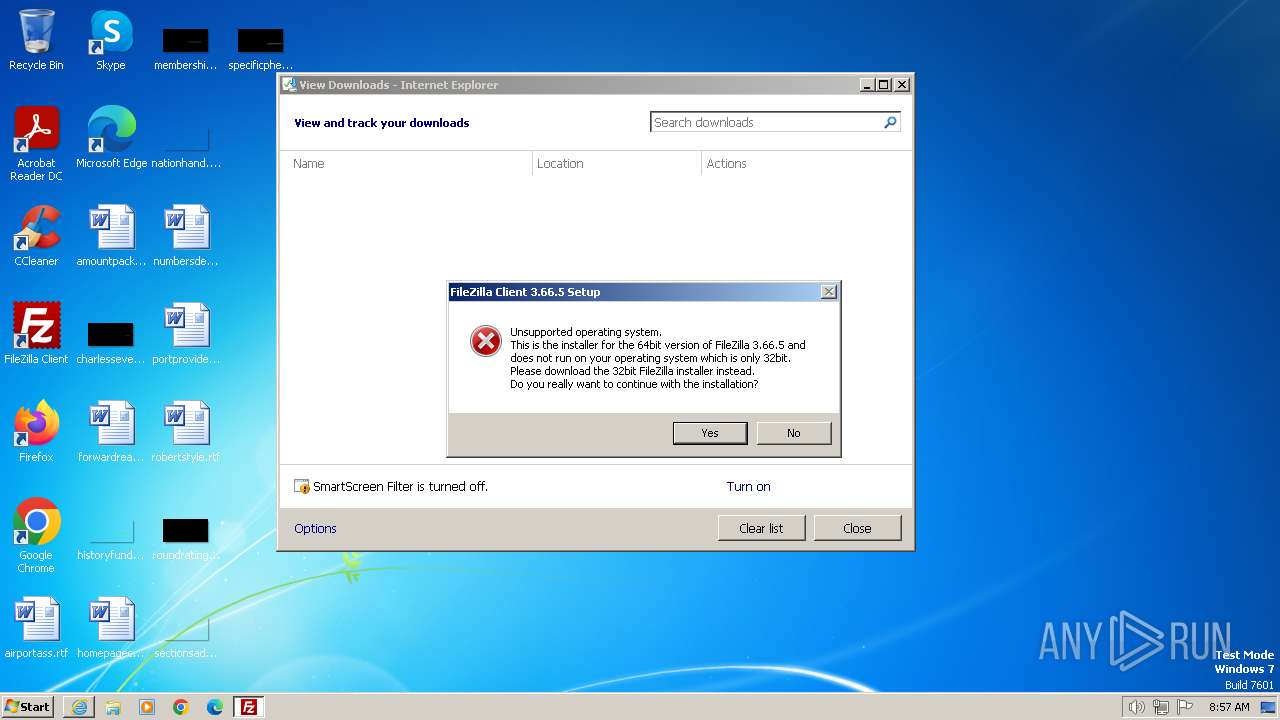
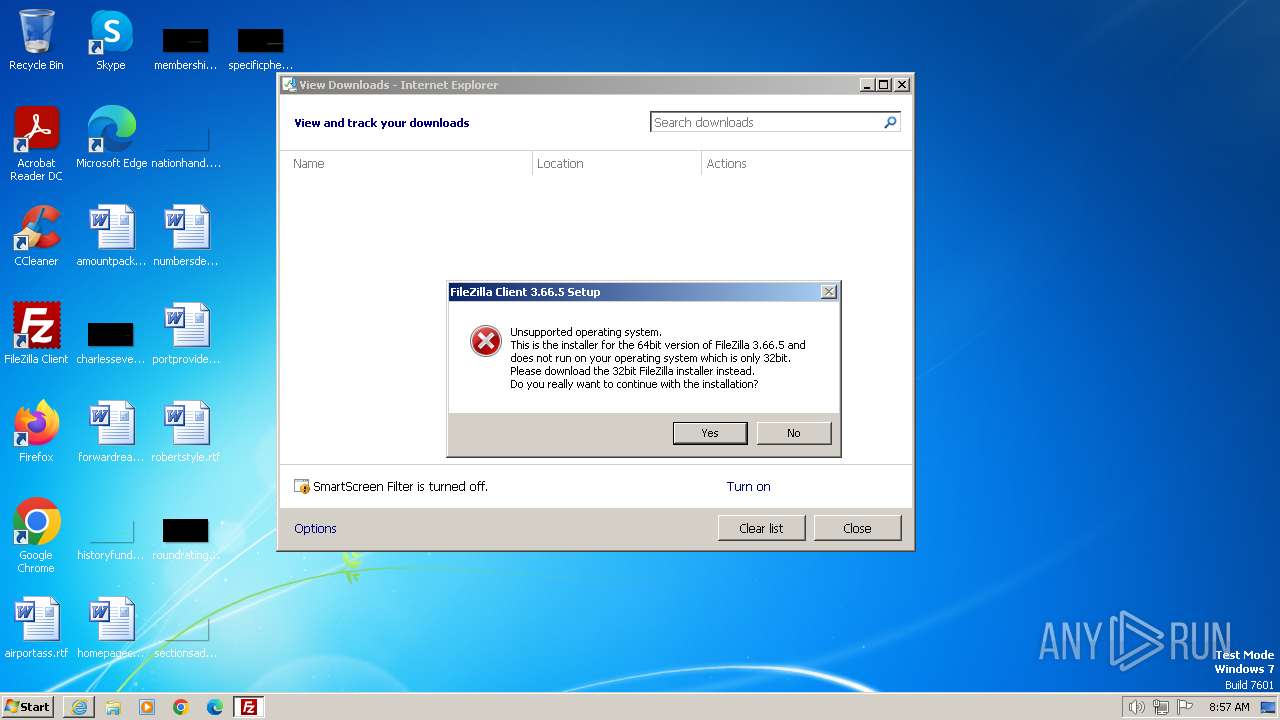
The process creates files with name similar to system file names
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
- uninstall.exe (PID: 2256)
Malware-specific behavior (creating "System.dll" in Temp)
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
- uninstall.exe (PID: 2256)
Executable content was dropped or overwritten
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
- uninstall.exe (PID: 2256)
Application launched itself
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
Searches for installed software
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
Creates/Modifies COM task schedule object
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
Creates a software uninstall entry
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
Reads the Internet Settings
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
Reads security settings of Internet Explorer
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
INFO
Application launched itself
- iexplore.exe (PID: 1384)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1384)
The process uses the downloaded file
- iexplore.exe (PID: 1384)
Drops the executable file immediately after the start
- iexplore.exe (PID: 1384)
- iexplore.exe (PID: 3536)
Checks supported languages
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
- uninstall.exe (PID: 2256)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3536)
- iexplore.exe (PID: 1384)
Reads the computer name
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
- uninstall.exe (PID: 2256)
Create files in a temporary directory
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 3992)
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
- uninstall.exe (PID: 2256)
Creates files in the program directory
- FileZilla_3.66.5_win64_sponsored-setup.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
46
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1384 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://download.filezilla-project.org/client/FileZilla_3.66.5_win64_sponsored-setup.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\FileZilla_3.66.5_win64_sponsored-setup.exe" /UAC:13010A /NCRC | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\FileZilla_3.66.5_win64_sponsored-setup.exe | FileZilla_3.66.5_win64_sponsored-setup.exe | ||||||||||||
User: admin Company: Tim Kosse Integrity Level: HIGH Description: FileZilla FTP Client Exit code: 0 Version: 3.66.5 Modules
| |||||||||||||||
| 2256 | "C:\Program Files\FileZilla FTP Client\uninstall.exe" /frominstall /keepstartmenudir _?=C:\Program Files\FileZilla FTP Client | C:\Program Files\FileZilla FTP Client\uninstall.exe | FileZilla_3.66.5_win64_sponsored-setup.exe | ||||||||||||
User: admin Company: Tim Kosse Integrity Level: HIGH Description: FileZilla FTP Client Exit code: 0 Version: 3.65.0 Modules
| |||||||||||||||
| 3536 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1384 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3992 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\FileZilla_3.66.5_win64_sponsored-setup.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\FileZilla_3.66.5_win64_sponsored-setup.exe | iexplore.exe | ||||||||||||
User: admin Company: Tim Kosse Integrity Level: MEDIUM Description: FileZilla FTP Client Exit code: 0 Version: 3.66.5 Modules
| |||||||||||||||
Total events
24 758
Read events
24 583
Write events
131
Delete events
44
Modification events
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 708424688 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31088822 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31088822 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1384) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
39
Suspicious files
45
Text files
692
Unknown types
94
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabF79E.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:3A602C206D3F484389E05D24B8422773 | SHA256:96F0D49C3F1FC4437946EAC6AB92BA24E238C3549F8260D91F37109321EF27AB | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabF7DF.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarF7E0.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\FileZilla_3.66.5_win64_sponsored-setup[1].exe | executable | |
MD5:51E25DADD5FEBD0094DFB2DC0D0619CA | SHA256:BB991F73865238058EC5F56CF508668B202B56D9434043D5F7E9BD9BE4F5AEED | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarF79F.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 1384 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{67DF3AED-CCA9-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:7818DC81F9ACC2BD31D5EB577C8A0EB7 | SHA256:8AAF7842D26DB181A168FC0FE80BB81089F0F8DCCD6DB953044DB6823E359124 | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E7B1F943988F21AD31846EC9C7BF45B9 | SHA256:4B3497EACC7D0736F73790125A752C9D2835EECC7AF3629506833FB1E899E9EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
16
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3536 | iexplore.exe | GET | 304 | 23.32.238.217:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5b0325f31ae0f9b6 | unknown | — | — | unknown |
3536 | iexplore.exe | GET | 304 | 23.32.238.217:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
3536 | iexplore.exe | GET | 200 | 23.32.238.217:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0302b3af7cdfdbed | unknown | compressed | 65.2 Kb | unknown |
3536 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3536 | iexplore.exe | GET | 200 | 23.32.238.217:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?dfd57d13c28afd30 | unknown | compressed | 65.2 Kb | unknown |
1384 | iexplore.exe | GET | 304 | 23.32.238.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9aee5c2adfb08fdb | unknown | — | — | unknown |
1384 | iexplore.exe | GET | 304 | 23.32.238.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?76ad697231f9b13b | unknown | — | — | unknown |
1384 | iexplore.exe | GET | 304 | 23.32.238.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d416ea50f343b89b | unknown | — | — | unknown |
1384 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3536 | iexplore.exe | 49.12.121.47:443 | download.filezilla-project.org | Hetzner Online GmbH | DE | unknown |
3536 | iexplore.exe | 23.32.238.217:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3536 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
1384 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
1384 | iexplore.exe | 23.32.238.240:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1384 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.filezilla-project.org |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |