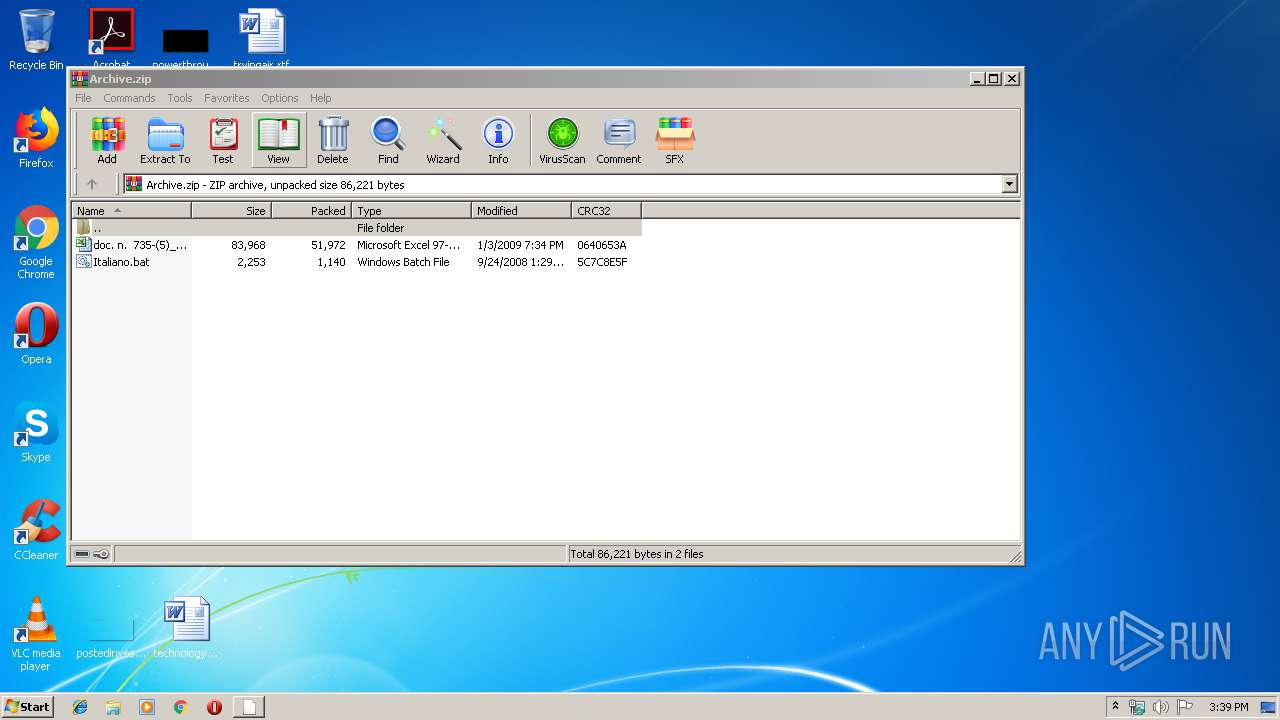
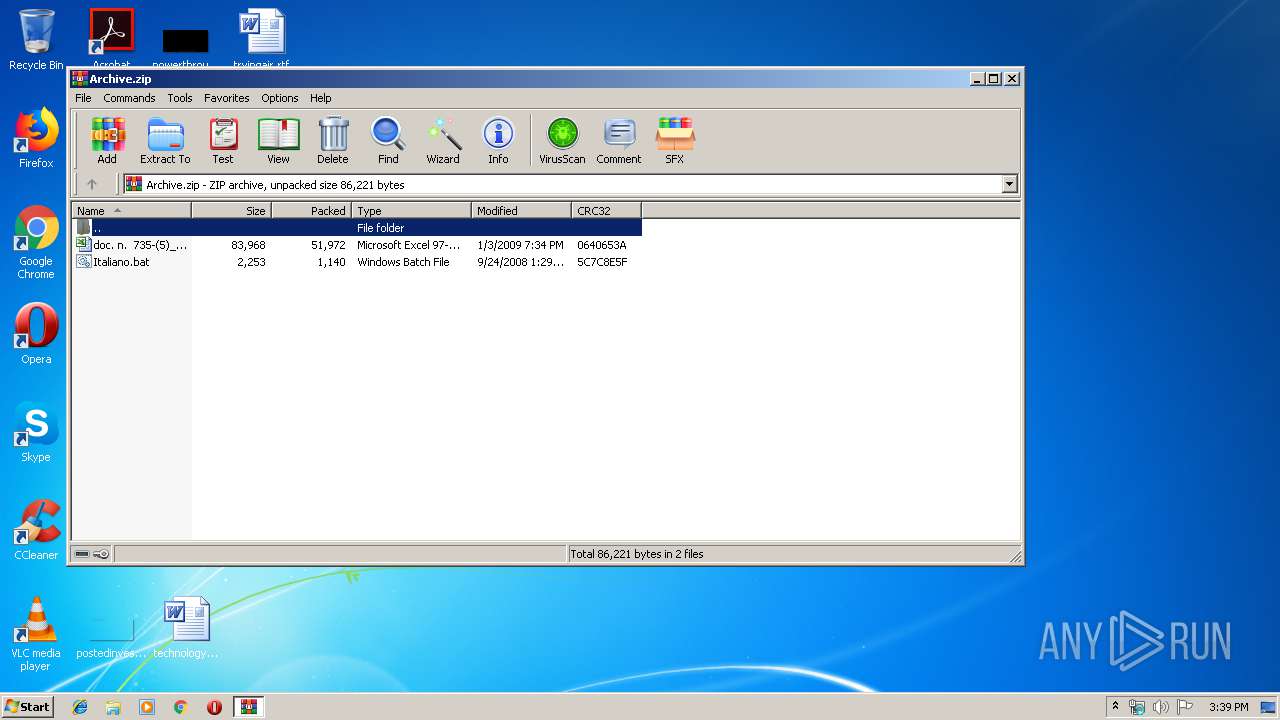
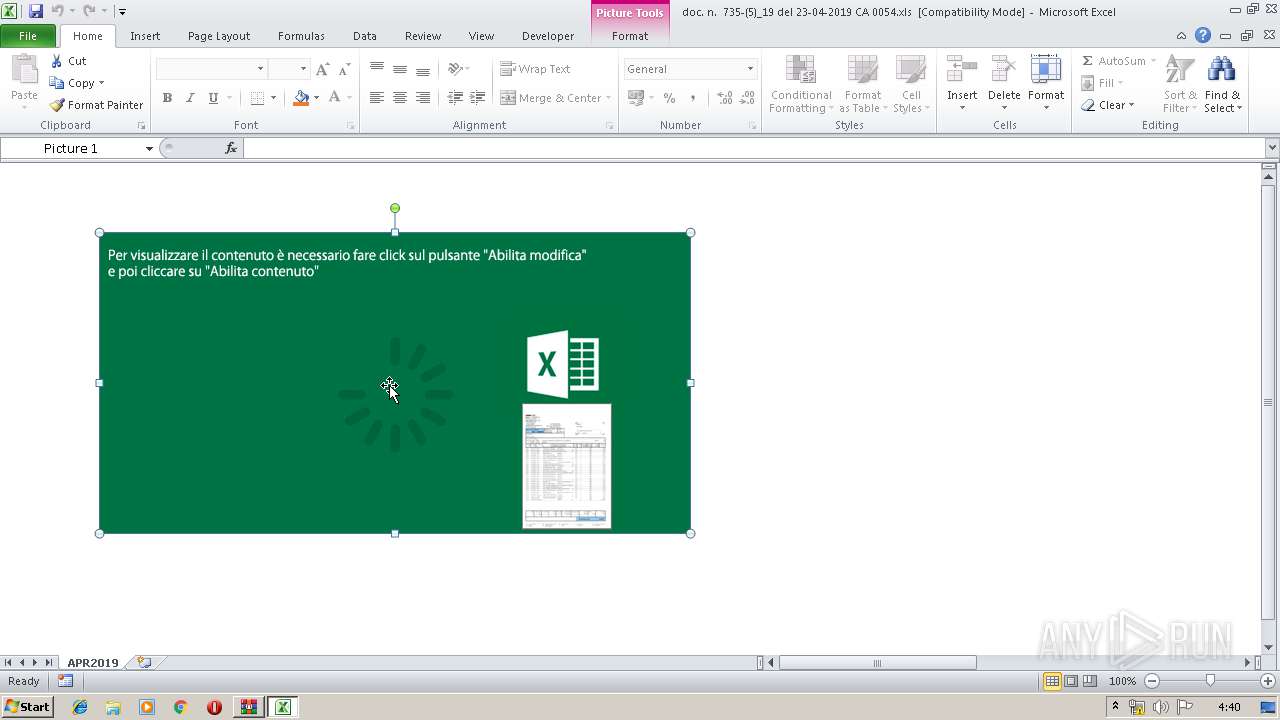
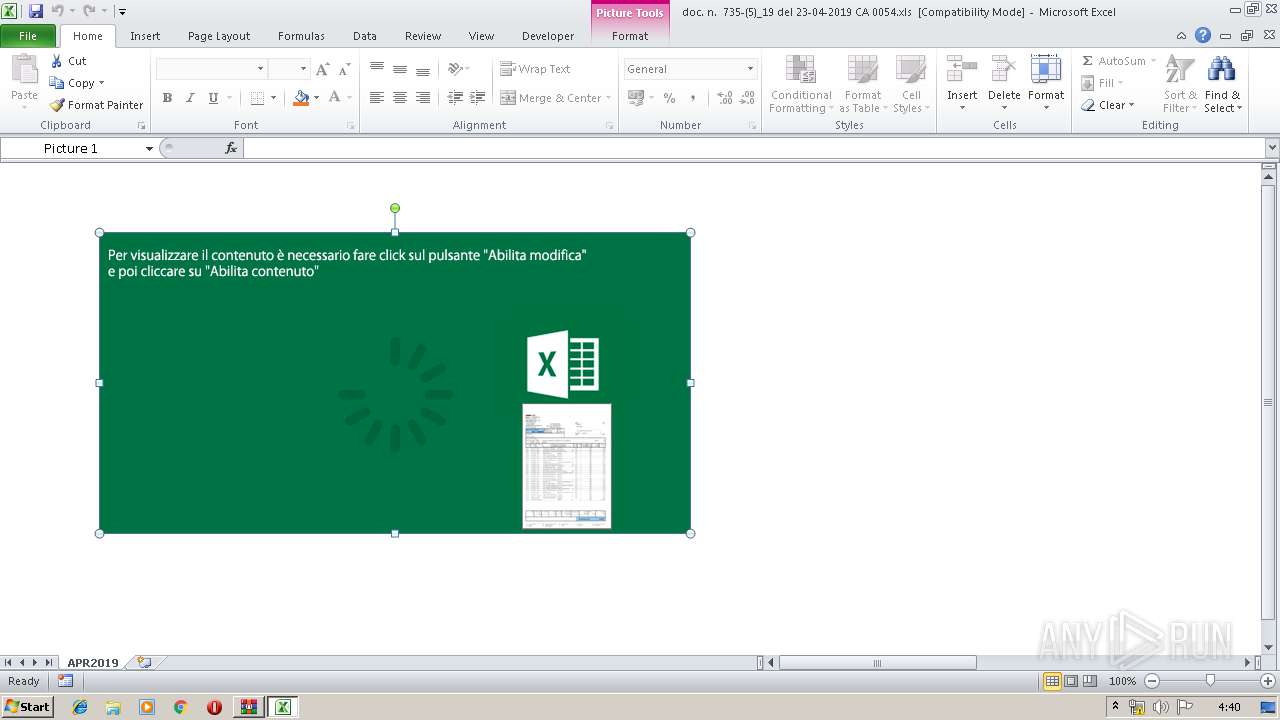
| File name: | Archive.zip |
| Full analysis: | https://app.any.run/tasks/a48ad189-409c-4791-9b0d-300a8ab3692c |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 14:38:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 916A8D4DBB024E76000A0B11BF297DA2 |
| SHA1: | 9A7B75DAEED84BD1C3180E7B05EE4FAEA8A1138D |
| SHA256: | 285170BABB05D05FFFA8702D442643DD0884E136D26704C3852AA6FFE001A2EA |
| SSDEEP: | 1536:gaMSJ+zrIg3w8RviIuko75jM6cgF1bhthGpyyz:gbzrIYwPIHcQ6VF1NGz |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 3816)
- EXCEL.EXE (PID: 3856)
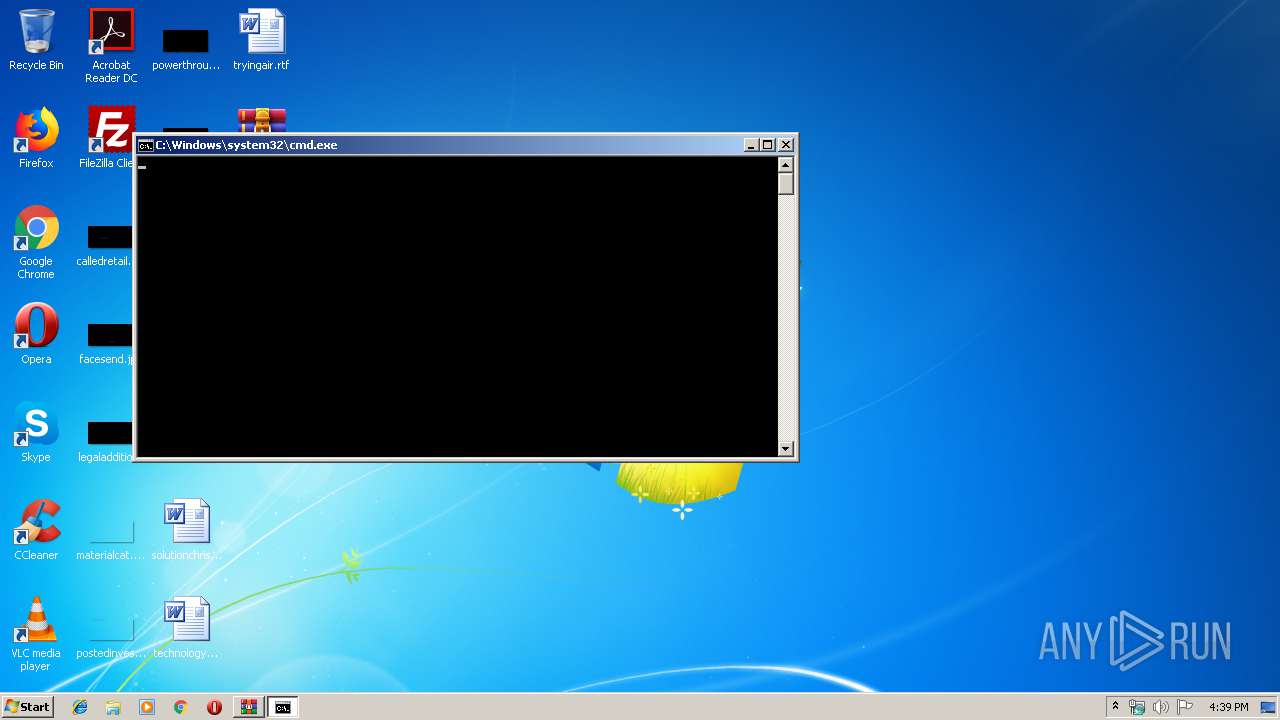
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3816)
- EXCEL.EXE (PID: 3856)
Executes PowerShell scripts
- cmD.exe (PID: 4088)
- cmD.exe (PID: 3900)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmD.exe (PID: 4088)
- cmD.exe (PID: 3900)
Creates files in the user directory
- powershell.exe (PID: 608)
- powershell.exe (PID: 3336)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3816)
- EXCEL.EXE (PID: 3856)
Creates files in the user directory
- EXCEL.EXE (PID: 3816)
- EXCEL.EXE (PID: 3856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2008:09:24 13:29:15 |
| ZipCRC: | 0x5c7c8e5f |
| ZipCompressedSize: | 1140 |
| ZipUncompressedSize: | 2253 |
| ZipFileName: | Italiano.bat |
Total processes
56
Monitored processes
15
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Windows\regedit.exe" /s "C:\Users\admin\AppData\Local\Temp\decoded" | C:\Windows\regedit.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 608 | pOwerShEll -exeCutioNp bypASs -nOprOFIle -NOnIntE -WinD hidDEN ${execUTIonCOnteXt}.InvokeCoMmAnd.InVokEsCripT( ${iNput} ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2104 | certutil /decode "C:\Users\admin\AppData\Local\Temp\b64" "C:\Users\admin\AppData\Local\Temp\decoded" | C:\Windows\system32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2832 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Archive.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2920 | cmd /c ""C:\Users\admin\Desktop\Italiano.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3032 | regedit.exe /s "C:\Users\admin\AppData\Local\Temp\decoded" | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3076 | C:\Windows\system32\cmd.exe /S /D /c" EchO/^&( $Env:COMSPec[4,15,25]-jOiN'') (NEw-oBJEct IO.COMpREsSION.DeflAtEsTREAm( [syStem.Io.MeMoRysTrEaM] [conVeRt]::FROMbasE64sTrINg( '' ), [SYsTeM.io.coMPReSsIoN.COmPreSsIOnModE]::deCOmPreSS )^| fOReAch-OBjECt{NEw-oBJEct iO.stREAmREADeR( $_,[TexT.eNCoDiNg]::aSCiI )}).readtOEnd() " | C:\Windows\system32\cmd.exe | — | cmD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3336 | pOwerShEll -exeCutioNp bypASs -nOprOFIle -NOnIntE -WinD hidDEN ${execUTIonCOnteXt}.InvokeCoMmAnd.InVokEsCripT( ${iNput} ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3508 | "C:\Windows\regedit.exe" /s "C:\Users\admin\AppData\Local\Temp\decoded" | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3552 | C:\Windows\system32\cmd.exe /S /D /c" EchO/^&( $Env:COMSPec[4,15,25]-jOiN'') (NEw-oBJEct IO.COMpREsSION.DeflAtEsTREAm( [syStem.Io.MeMoRysTrEaM] [conVeRt]::FROMbasE64sTrINg( '' ), [SYsTeM.io.coMPReSsIoN.COmPreSsIOnModE]::deCOmPreSS )^| fOReAch-OBjECt{NEw-oBJEct iO.stREAmREADeR( $_,[TexT.eNCoDiNg]::aSCiI )}).readtOEnd() " | C:\Windows\system32\cmd.exe | — | cmD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 771
Read events
1 528
Write events
220
Delete events
23
Modification events
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Archive.zip | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
0
Suspicious files
6
Text files
11
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3816 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR41BF.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 608 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JCIX6XLVOT5RAAJ9Z4BQ.temp | — | |
MD5:— | SHA256:— | |||
| 3816 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFC85DAC1BFB406524.TMP | — | |
MD5:— | SHA256:— | |||
| 3816 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF7DBACBDE6DDBDEAA.TMP | — | |
MD5:— | SHA256:— | |||
| 3856 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRE4C1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3336 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\M6T2AYVRG5UXQQ1CNHEH.temp | — | |
MD5:— | SHA256:— | |||
| 2832 | WinRAR.exe | C:\Users\admin\Desktop\Italiano.bat | text | |
MD5:— | SHA256:— | |||
| 3856 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\doc. n. 735-(5)_19 del 23-04-2019 CA 0054.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
| 608 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 608 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1349fd.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report