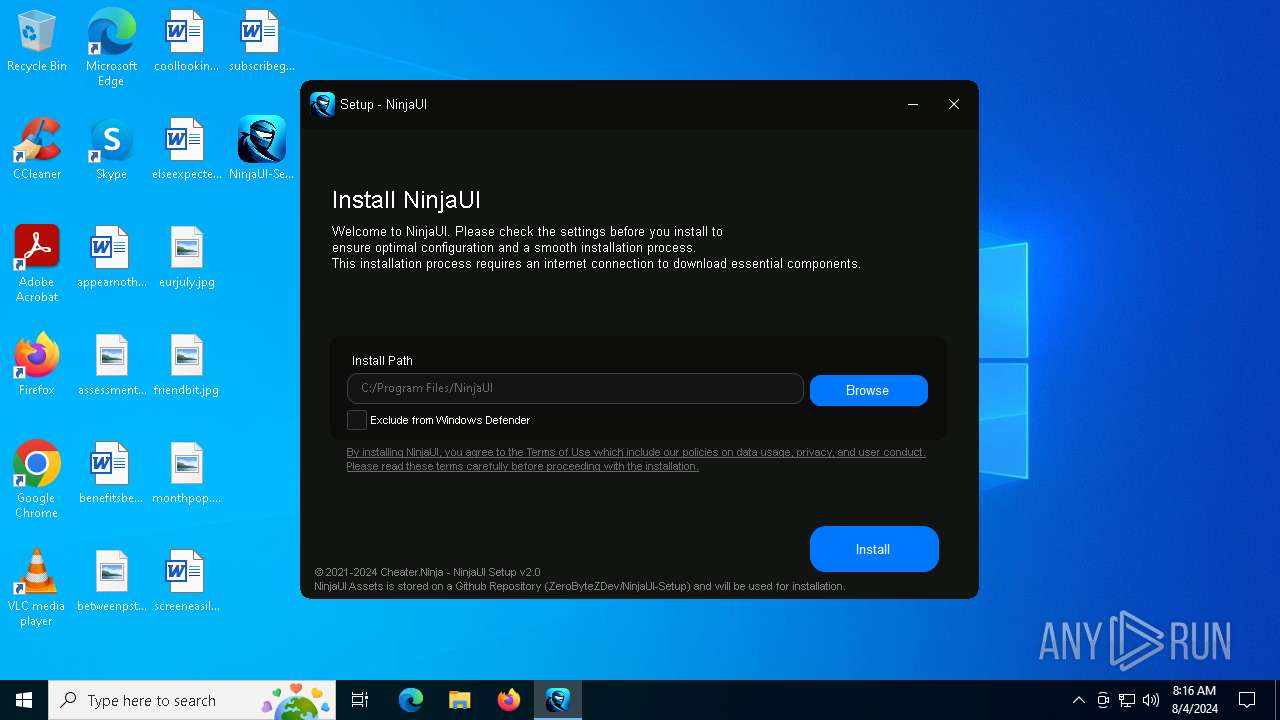
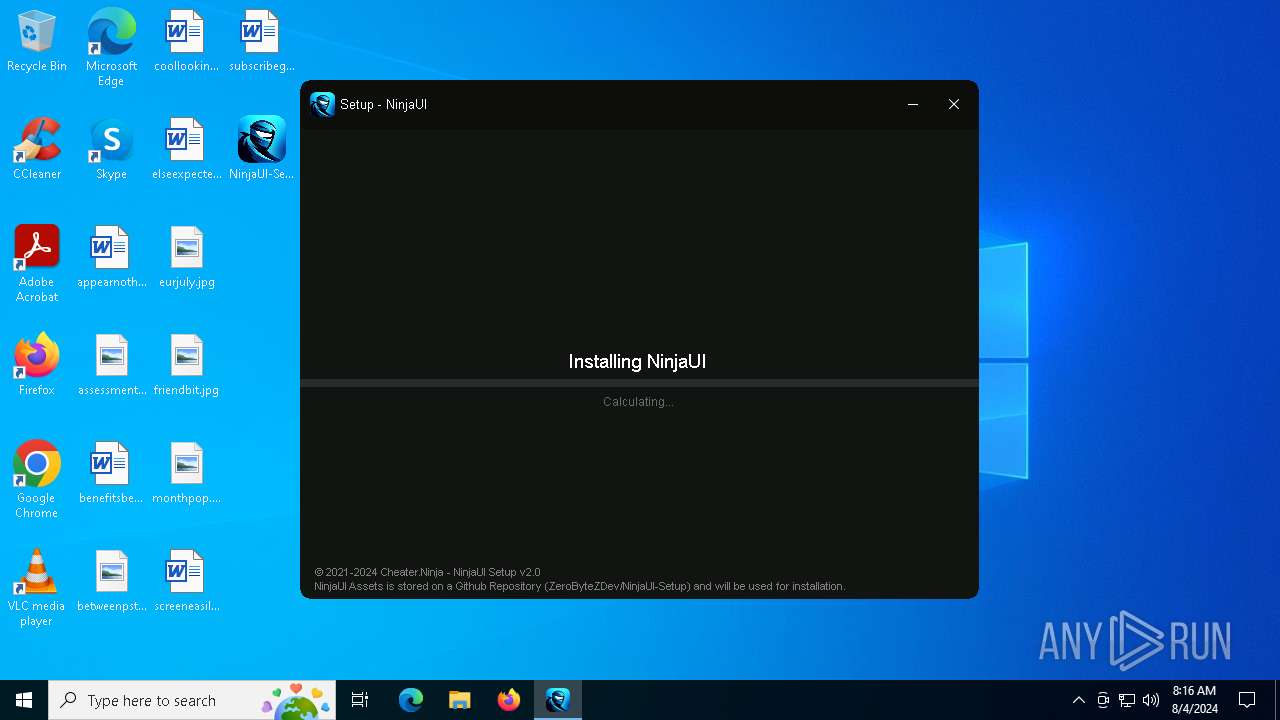
| File name: | NinjaUI-Setup-v2.0.exe |
| Full analysis: | https://app.any.run/tasks/431e1547-acce-41c1-ba04-bfab8934993d |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2024, 08:16:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | AAA0815A139A84B11E846705E05BC814 |
| SHA1: | 77D07CC005E031A6782F6AB7D44A30E035F68FE7 |
| SHA256: | 284FF705A6CD2A91A146DC23E70967E12E6EF18A01DD9013CFE05A2B16FBAE68 |
| SSDEEP: | 49152:L0eMNSUY82nPHX297MLqZAE8fczoJqVl/wdIDjCnHXfQTNLvbuyYWW7NkfUM7MH7:AeMNxgo7MEAnioeDDjC3fYNLvYbN9O9Y |
MALICIOUS
Drops the executable file immediately after the start
- NinjaUI-Setup-v2.0.exe (PID: 6496)
- NinjaUI-Setup.exe (PID: 6584)
SUSPICIOUS
Reads security settings of Internet Explorer
- NinjaUI-Setup-v2.0.exe (PID: 6496)
- NinjaUI-Setup.exe (PID: 6584)
Reads the date of Windows installation
- NinjaUI-Setup-v2.0.exe (PID: 6496)
- NinjaUI-Setup.exe (PID: 6584)
Executable content was dropped or overwritten
- NinjaUI-Setup-v2.0.exe (PID: 6496)
- NinjaUI-Setup.exe (PID: 6584)
There is functionality for taking screenshot (YARA)
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI.exe (PID: 5040)
INFO
Reads the computer name
- NinjaUI-Setup-v2.0.exe (PID: 6496)
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI.exe (PID: 5040)
Checks supported languages
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI-Setup-v2.0.exe (PID: 6496)
- NinjaUI.exe (PID: 5040)
Create files in a temporary directory
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI-Setup-v2.0.exe (PID: 6496)
Process checks computer location settings
- NinjaUI-Setup-v2.0.exe (PID: 6496)
- NinjaUI-Setup.exe (PID: 6584)
Reads Environment values
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI.exe (PID: 5040)
Reads the machine GUID from the registry
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI.exe (PID: 5040)
Checks proxy server information
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI.exe (PID: 5040)
Reads the software policy settings
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI.exe (PID: 5040)
Creates files in the program directory
- NinjaUI-Setup.exe (PID: 6584)
- NinjaUI.exe (PID: 5040)
Disables trace logs
- NinjaUI.exe (PID: 5040)
- NinjaUI-Setup.exe (PID: 6584)
Potential library load (Base64 Encoded 'LoadLibrary')
- NinjaUI.exe (PID: 5040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:03 07:51:24+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 167936 |
| InitializedDataSize: | 344064 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16f40 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
121
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5040 | "C:\Program Files\NinjaUI\NinjaUI.exe" | C:\Program Files\NinjaUI\NinjaUI.exe | NinjaUI-Setup.exe | ||||||||||||
User: admin Company: NinjaUI Software Integrity Level: HIGH Description: NinjaUI Version: 1.0.0.0 Modules
| |||||||||||||||
| 6496 | "C:\Users\admin\Desktop\NinjaUI-Setup-v2.0.exe" | C:\Users\admin\Desktop\NinjaUI-Setup-v2.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6536 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\NinjaUI-Setup.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\NinjaUI-Setup.exe | — | NinjaUI-Setup-v2.0.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6584 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\NinjaUI-Setup.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\NinjaUI-Setup.exe | NinjaUI-Setup-v2.0.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
13 202
Read events
13 149
Write events
53
Delete events
0
Modification events
| (PID) Process: | (6496) NinjaUI-Setup-v2.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6496) NinjaUI-Setup-v2.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6496) NinjaUI-Setup-v2.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6496) NinjaUI-Setup-v2.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6584) NinjaUI-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6584) NinjaUI-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\NinjaUI-Setup_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6584) NinjaUI-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\NinjaUI-Setup_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6584) NinjaUI-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\NinjaUI-Setup_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6584) NinjaUI-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\NinjaUI-Setup_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6584) NinjaUI-Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\NinjaUI-Setup_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
11
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6584 | NinjaUI-Setup.exe | C:\Program Files\NinjaUI\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 6584 | NinjaUI-Setup.exe | C:\Users\admin\Desktop\NinjaUI.lnk | binary | |
MD5:1DADC9FF396F11825D7C0FB39CC870E4 | SHA256:C3B1285C9D24B11331E5F294C4AB9D2FBE2FB8E1A94890445E3083E0ABAF735D | |||
| 6496 | NinjaUI-Setup-v2.0.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Guna.UI2.dll | executable | |
MD5:C97F23B52087CFA97985F784EA83498F | SHA256:E658E8A5616245DBE655E194B59F1BB704AAEAFBD0925D6EEBBE70555A638CDD | |||
| 6584 | NinjaUI-Setup.exe | C:\Program Files\NinjaUI\NinjaLLInjector32.exe | executable | |
MD5:A4395C6BD025D170812F12C0A474E856 | SHA256:CD7CEC5AAE1B795E5AD194AF84F213B130EC4F20D45E07CECADAEC3D0EAC8FC7 | |||
| 6584 | NinjaUI-Setup.exe | C:\Users\admin\AppData\Local\Temp\NinjaUI-Package.zip | compressed | |
MD5:4EBB8DD530E3C0C2571658597D18B7C1 | SHA256:D898B08598967AE908E44F7E08750DC9ACCFB718E9F4C6AF42CA75C6757E1E84 | |||
| 6584 | NinjaUI-Setup.exe | C:\Program Files\NinjaUI\DiscordRPC.dll | executable | |
MD5:3956130E36754F184A0443C850F708F8 | SHA256:25C39F91F737D80040C72C9E3F95DB0FECE1C9653F501828ADC16CFB1EC59D26 | |||
| 6584 | NinjaUI-Setup.exe | C:\Program Files\NinjaUI\Guna.UI2.dll | executable | |
MD5:C97F23B52087CFA97985F784EA83498F | SHA256:E658E8A5616245DBE655E194B59F1BB704AAEAFBD0925D6EEBBE70555A638CDD | |||
| 6584 | NinjaUI-Setup.exe | C:\Program Files\NinjaUI\NinjaLLInjector64.exe | executable | |
MD5:AA0FBEFD978B88384A9F822858877357 | SHA256:F09C016D88F126C2866FFFF522716328F250AF1D9F0708F1EFEEADCD2DB4C5EB | |||
| 6496 | NinjaUI-Setup-v2.0.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\NinjaUI-Setup.exe | executable | |
MD5:BA506F8678F4D9FBB99DDA4BEACDB7F3 | SHA256:293CBE499C9225CD140993E77C42F76A2F06EF0B59739659B3C1BAB727D5750F | |||
| 6584 | NinjaUI-Setup.exe | C:\Program Files\NinjaUI\Updater.exe | executable | |
MD5:73DF0068DDE63CCCFC8424C9CA9FB1AA | SHA256:B52D263B4A9E8AC042C1DF90743DD23F9EA9EABD2630AF6302285268D181A296 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
20
DNS requests
8
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 104.26.12.77:443 | https://api.ninjaui.net/?getSettings&token=12d4f735e6b341d2a7f5b6545c89d7cfc1ae86a2f12e9e0c7b5e67c9fa1e7bcd | unknown | text | 646 b | unknown |
— | — | POST | 200 | 172.67.68.3:443 | https://api.ninjaui.net/ | unknown | binary | 44 b | unknown |
— | — | GET | 200 | 172.67.68.3:443 | https://ninjaui.net/ | unknown | html | 76.3 Kb | unknown |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/ZeroByteZDev/NinjaUI-FIles/main/NinjaUI2-Package.zip | unknown | compressed | 1.42 Mb | unknown |
— | — | GET | 200 | 104.26.12.77:443 | https://ninjaui.net/ | unknown | html | 76.3 Kb | unknown |
— | — | POST | 400 | 104.26.13.77:443 | https://auth.ninjaui.net/ | unknown | binary | 51 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5600 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1248 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5600 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6584 | NinjaUI-Setup.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
ninjaui.net |
| unknown |
api.ninjaui.net |
| unknown |
auth.ninjaui.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Potentially Bad Traffic | ET HUNTING Terse Request for Zip File (GET) |