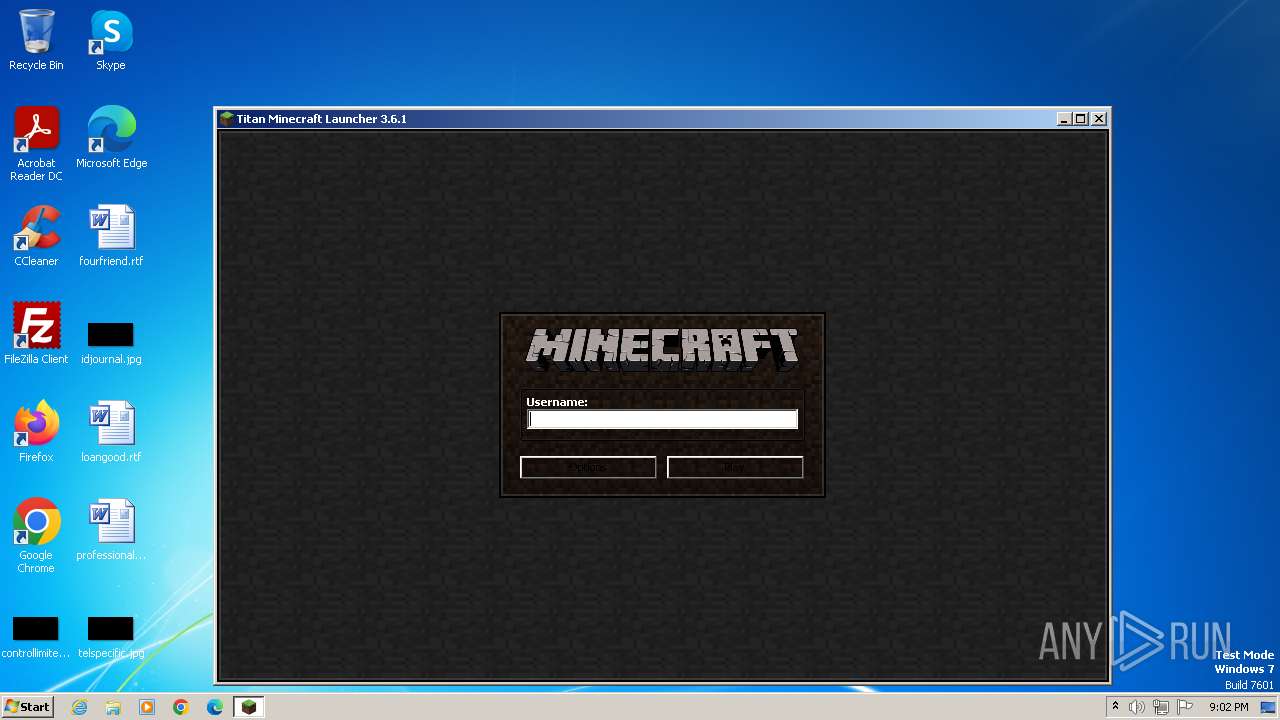
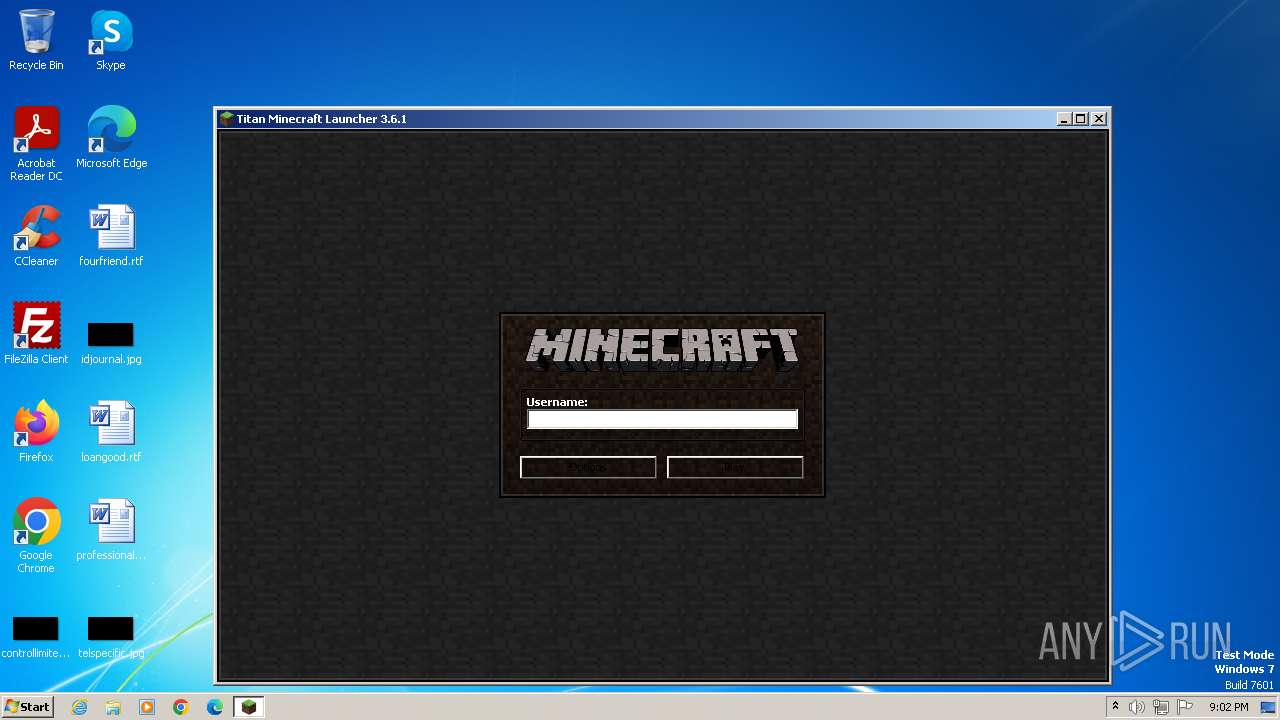
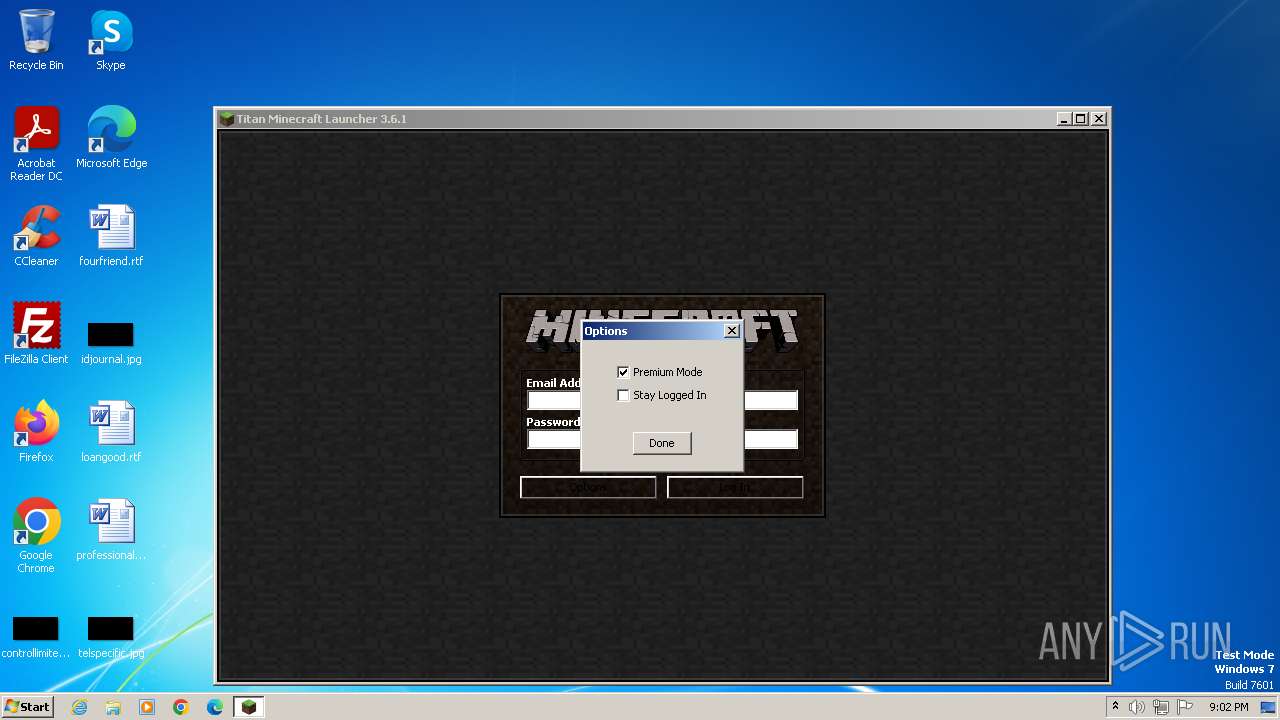
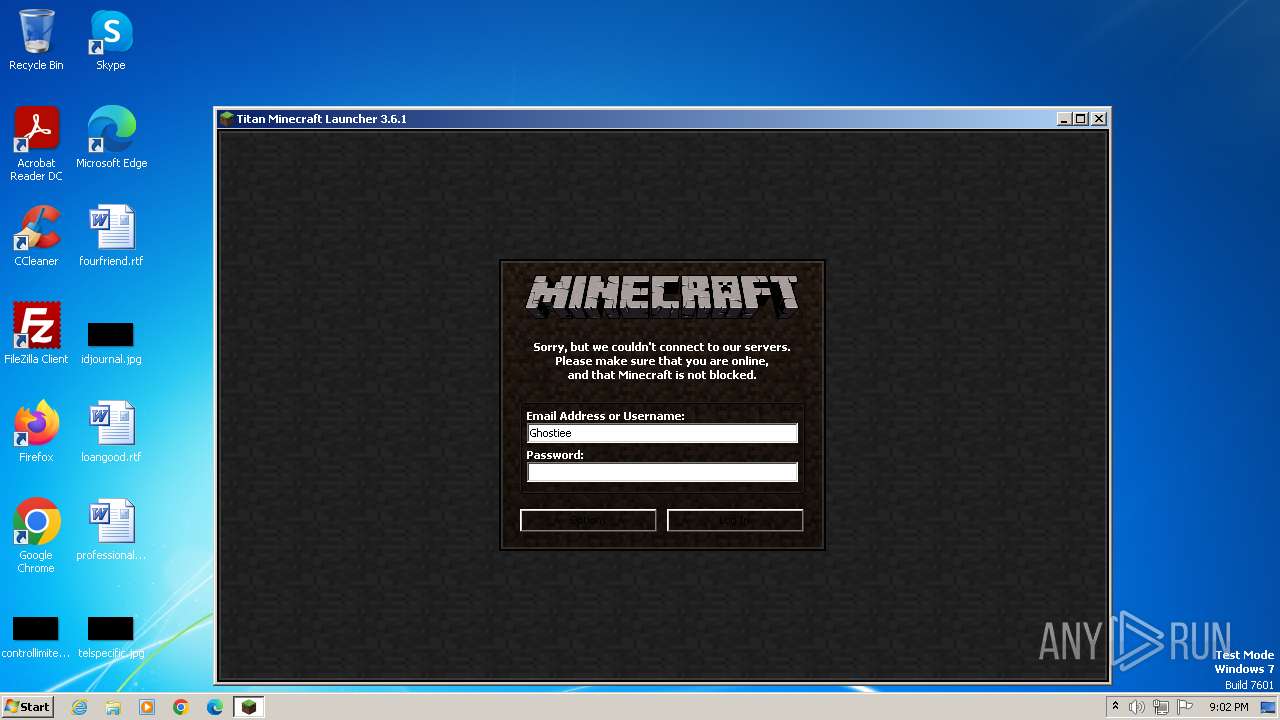
| File name: | Minecraft Launcher.exe |
| Full analysis: | https://app.any.run/tasks/db8a95e4-eb0a-41a3-a0ce-67492b96f6ef |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2024, 20:01:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 689568710A8AB5C54DCBA95ACD2E3B53 |
| SHA1: | 9739DB03DA71E8B79B7CECAF8908975D37A26A73 |
| SHA256: | 28148908BEFB0382C4C3F629C1A5F9A4F93B09855968E444DE78D95C6DAD86A4 |
| SSDEEP: | 49152:7NY/oae1UgHrnRAST8XrhaRY0T+nqO4P4dj:q/BWrn3T8hiVT+ne4dj |
MALICIOUS
Drops the executable file immediately after the start
- Minecraft Launcher.exe (PID: 3980)
SUSPICIOUS
Checks for Java to be installed
- Minecraft Launcher.exe (PID: 3980)
INFO
Checks supported languages
- Minecraft Launcher.exe (PID: 3980)
- wmpnscfg.exe (PID: 1200)
- javaw.exe (PID: 3996)
Reads the computer name
- javaw.exe (PID: 3996)
- wmpnscfg.exe (PID: 1200)
Creates files in the program directory
- javaw.exe (PID: 3996)
Reads the machine GUID from the registry
- javaw.exe (PID: 3996)
Manual execution by a user
- wmpnscfg.exe (PID: 1200)
Create files in a temporary directory
- javaw.exe (PID: 3996)
Creates files or folders in the user directory
- javaw.exe (PID: 3996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:10:07 02:28:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.22 |
| CodeSize: | 18432 |
| InitializedDataSize: | 18432 |
| UninitializedDataSize: | 36864 |
| EntryPoint: | 0x1290 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.6.1.0 |
| ProductVersionNumber: | 3.6.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Titan Launcher |
| FileDescription: | 1.10.2 Minecraft Launcher |
| FileVersion: | 3.6.1 |
| InternalName: | Minecraft Launcher |
| LegalCopyright: | Titan Launcher |
| OriginalFileName: | Minecraft Launcher.exe |
| ProductName: | Titan Launcher |
| ProductVersion: | 3.6.1 |
Total processes
36
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1200 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Users\admin\AppData\Local\Temp\Minecraft Launcher.exe" | C:\Users\admin\AppData\Local\Temp\Minecraft Launcher.exe | — | explorer.exe | |||||||||||
User: admin Company: Titan Launcher Integrity Level: MEDIUM Description: 1.10.2 Minecraft Launcher Exit code: 0 Version: 3.6.1 Modules
| |||||||||||||||
| 3996 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -Xms256m -Xmx512m -jar "C:\Users\admin\AppData\Local\Temp\Minecraft Launcher.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | Minecraft Launcher.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 4044 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 274
Read events
1 272
Write events
2
Delete events
0
Modification events
| (PID) Process: | (3996) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
0
Suspicious files
0
Text files
8
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3996 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:C18BB554E1B562F9CE80F2D1CC37E184 | SHA256:28AD335F95E22F482C0D95EF6A43DED9552910F2A3707243EAA741179EC83A1F | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio7879701710485251460.tmp | image | |
MD5:CB2666EAE03572A523CE8EAD1EB45134 | SHA256:7BC1CC5F09034D3CA71B5F23AF0E83A2B681E90F5B986DE3748D555F527251B4 | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\servers.dat | binary | |
MD5:A0A1E0A23EDA0BF2961BD8E8F7D84C87 | SHA256:89C9E9B9DCE117D9B281679023CFBBECF3460BD49B84E2B2F8E35FC72F2C482D | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\launcher_profiles.json | binary | |
MD5:368652291BE13D72F17AE4D77744FF03 | SHA256:E9CEF0BBF7CB7BE34B677E59249C9675153A9A86C534FD542CB5535F3F669620 | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio2643308680113793621.tmp | image | |
MD5:91D3708A258E5F789E2AE888CF68F66F | SHA256:0AD2672561C2BA4E86C38702682BD84D720351F3E5C4CA232F0043AAB7FA8B28 | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\minecraft launcher\options.json | binary | |
MD5:B9CF32949297936C8EDE369A16865831 | SHA256:4420CB57C8D4ADB8D867534F258D16D5BB7621D04A2C710CC94CBCA9F8D4E7C1 | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio20268339865476803.tmp | image | |
MD5:D141CC8E71A3351F1AACB88A74B45FA4 | SHA256:2788675E062E1111EAD50A9A05971A7C11FE6246A89F571CF9F59ED68C72BB17 | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8115520951713233464.tmp | image | |
MD5:D141CC8E71A3351F1AACB88A74B45FA4 | SHA256:2788675E062E1111EAD50A9A05971A7C11FE6246A89F571CF9F59ED68C72BB17 | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio5106826260152362584.tmp | image | |
MD5:E7E38B97A9FE7E0BB219AAF28BB750B7 | SHA256:99EDDE5742D3F824EB8F1EA03CCBDB969A04F94235CAE509644A442F8EBB039E | |||
| 3996 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8853323843133515070.tmp | image | |
MD5:D141CC8E71A3351F1AACB88A74B45FA4 | SHA256:2788675E062E1111EAD50A9A05971A7C11FE6246A89F571CF9F59ED68C72BB17 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
5
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3996 | javaw.exe | 162.125.66.15:443 | dl.dropboxusercontent.com | DROPBOX | DE | malicious |
3996 | javaw.exe | 49.13.77.253:80 | titanindex.net | Hetzner Online GmbH | DE | unknown |
3996 | javaw.exe | 54.231.229.232:443 | s3.amazonaws.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl.dropboxusercontent.com |
| shared |
titanindex.net |
| unknown |
dl.dropbox.com |
| shared |
s3.amazonaws.com |
| shared |
authserver.mojang.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3996 | javaw.exe | Misc activity | ET INFO DropBox User Content Domain (dl .dropboxusercontent .com in TLS SNI) |