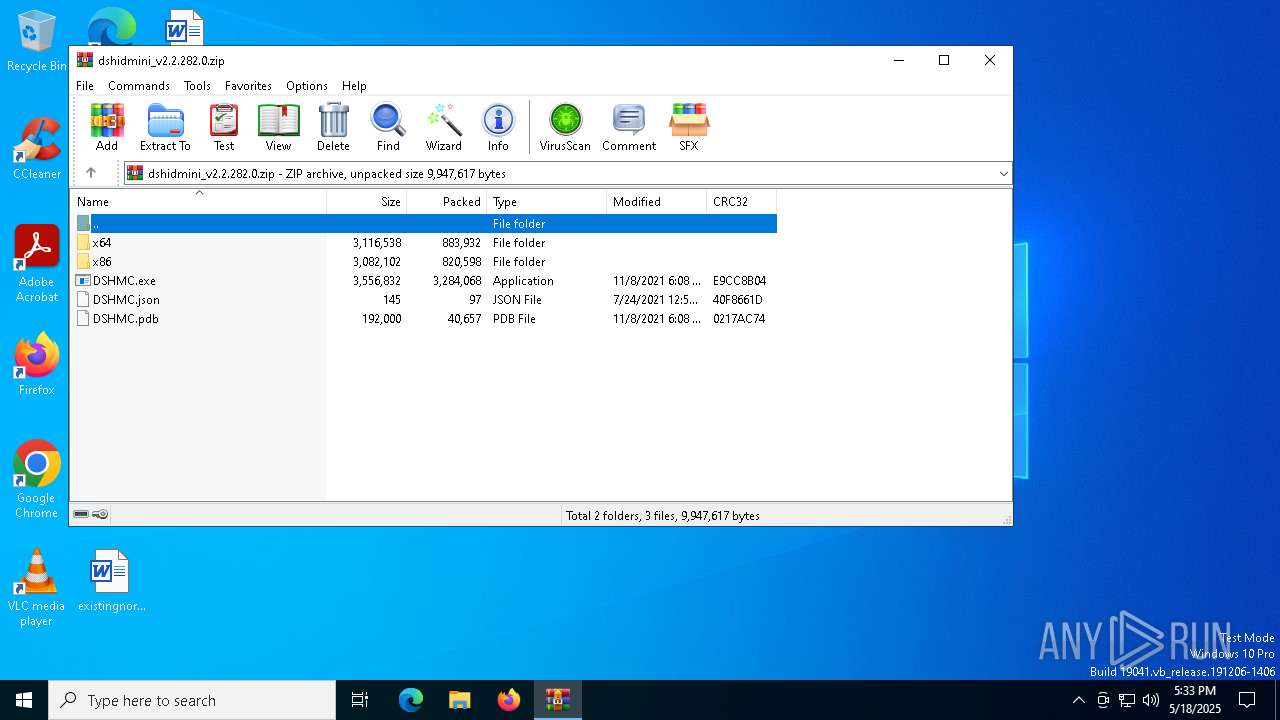
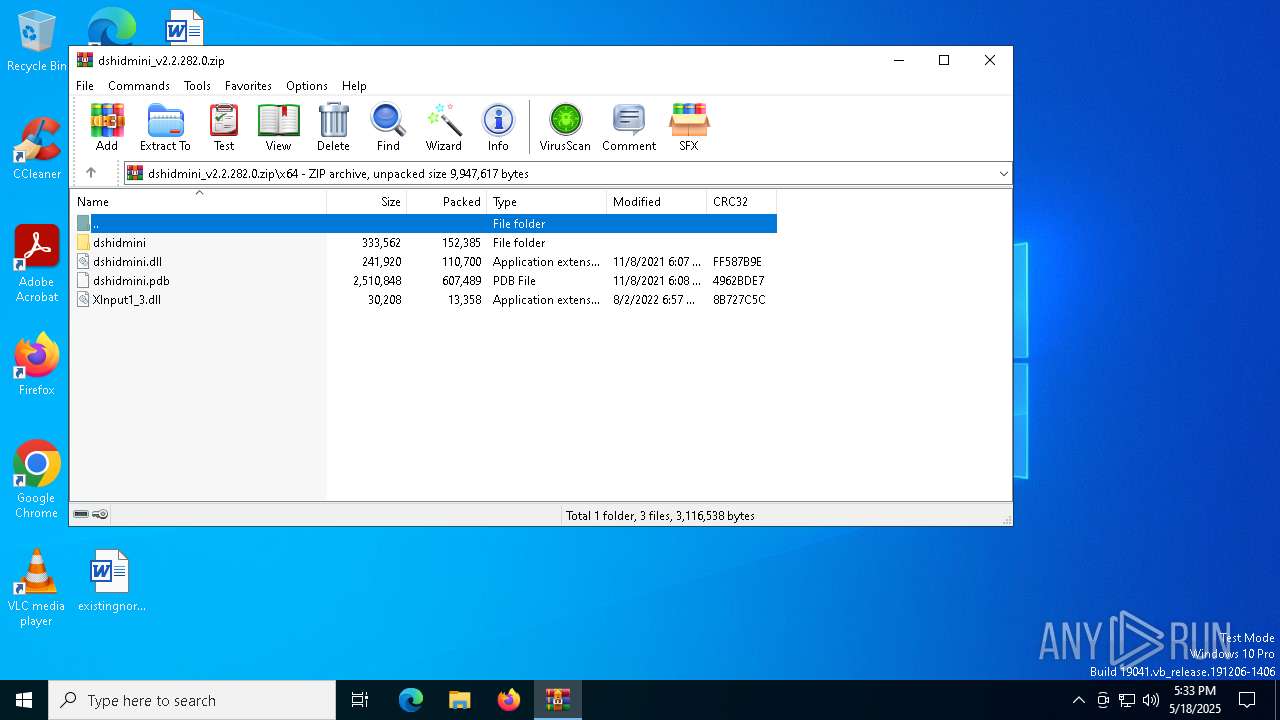
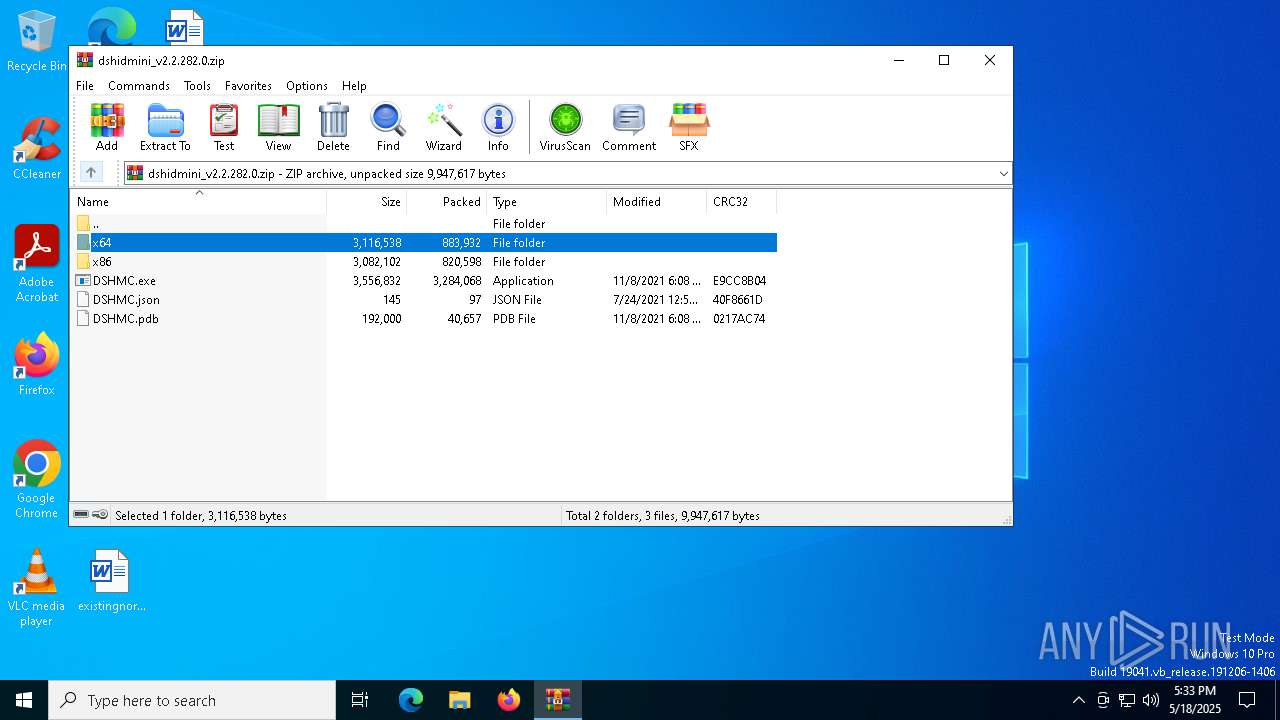
| File name: | dshidmini_v2.2.282.0.zip |
| Full analysis: | https://app.any.run/tasks/feb75065-c4c3-4961-bd23-99985e77445d |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 17:33:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 821E201A124350D183FC6F7EA9EC463F |
| SHA1: | 3E4AA8CE9378C1562E361F4AEA1389C2EC3C64D6 |
| SHA256: | 27FCDC6C92D661A101CEBCBE5E673E620F7723DDEE4092D894D275AF91A8A06A |
| SSDEEP: | 98304:z9bV28rYvl8jrom2/FHkepfk1R4V5vYCuWGp3ZGvfnRHXubd3wVMJ241o9+bryiE:EJgbZSnF8wL |
MALICIOUS
No malicious indicators.SUSPICIOUS
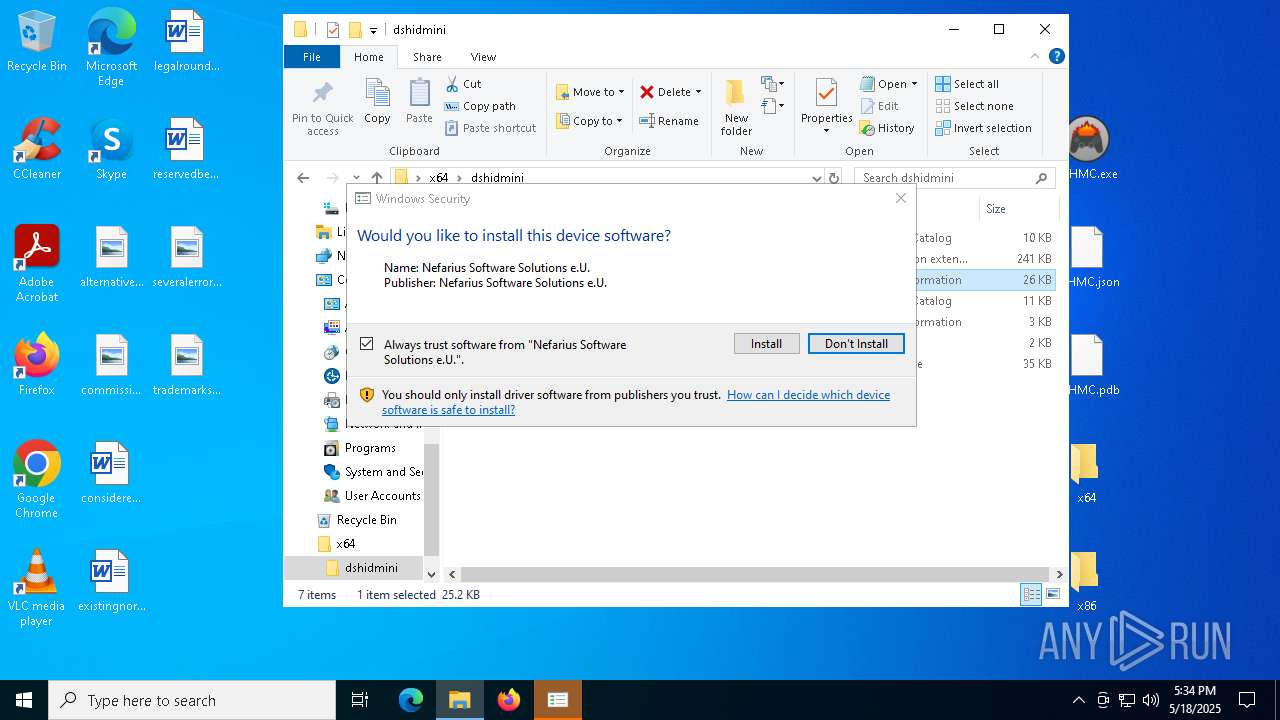
Drops a system driver (possible attempt to evade defenses)
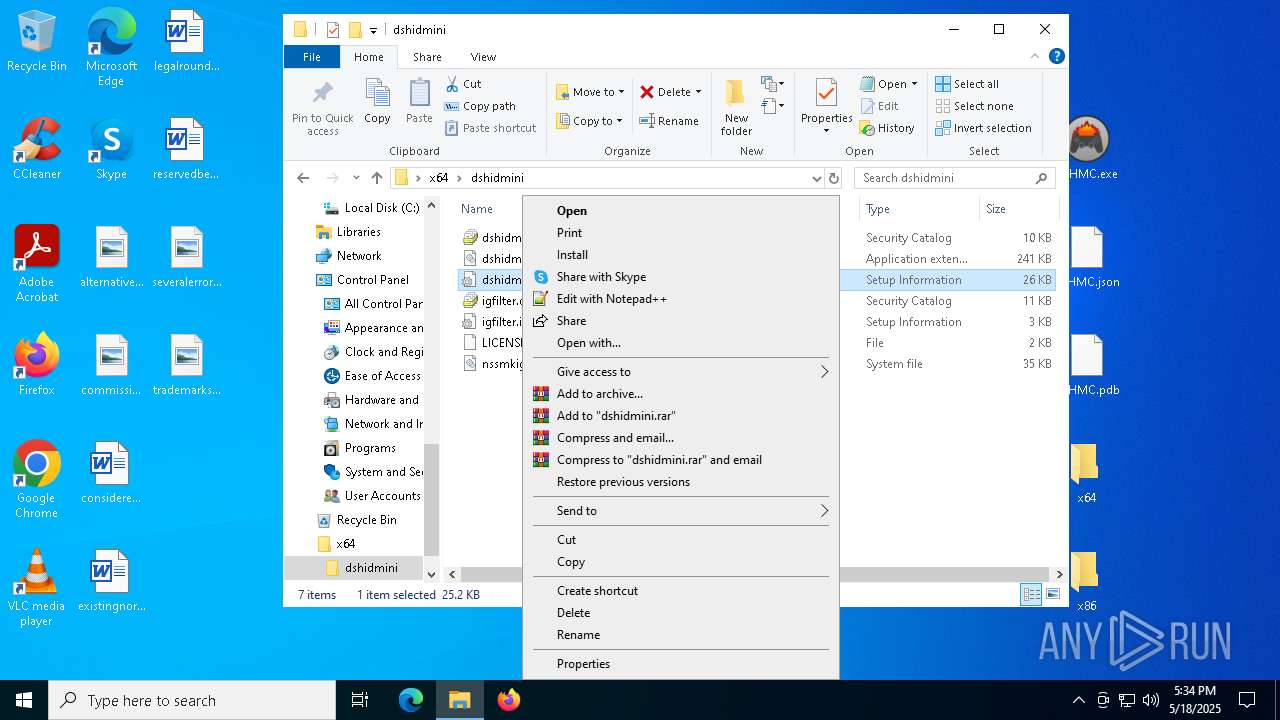
- WinRAR.exe (PID: 6040)
Executable content was dropped or overwritten
- InfDefaultInstall.exe (PID: 5260)
- drvinst.exe (PID: 6080)
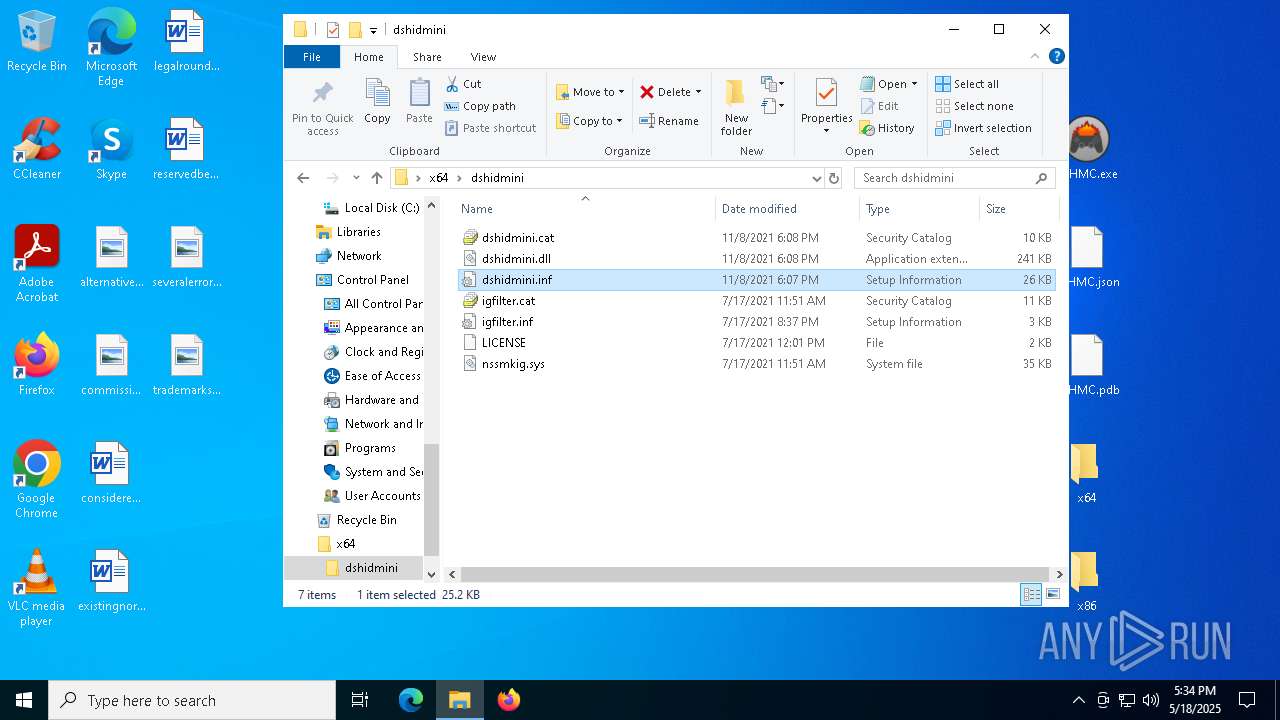
Creates files in the driver directory
- drvinst.exe (PID: 6080)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6040)
- InfDefaultInstall.exe (PID: 5260)
- drvinst.exe (PID: 6080)
Manual execution by a user
- InfDefaultInstall.exe (PID: 5260)
- InfDefaultInstall.exe (PID: 6676)
Create files in a temporary directory
- InfDefaultInstall.exe (PID: 5260)
Checks supported languages
- drvinst.exe (PID: 6080)
Reads the software policy settings
- drvinst.exe (PID: 6080)
- rundll32.exe (PID: 736)
Reads the machine GUID from the registry
- drvinst.exe (PID: 6080)
Reads the computer name
- drvinst.exe (PID: 6080)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 736)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:11:08 18:08:22 |
| ZipCRC: | 0xe9cc8b04 |
| ZipCompressedSize: | 3284068 |
| ZipUncompressedSize: | 3556832 |
| ZipFileName: | DSHMC.exe |
Total processes
136
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | rundll32.exe C:\WINDOWS\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{88d715f4-ec00-8947-964a-2c86ca30c3c8} Global\{045da93a-0d9b-a141-aedd-d01d2f9e7dd6} C:\WINDOWS\System32\DriverStore\Temp\{7dccc8de-66a2-c94c-bd3d-09fa0f4de331}\dshidmini.inf C:\WINDOWS\System32\DriverStore\Temp\{7dccc8de-66a2-c94c-bd3d-09fa0f4de331}\dshidmini.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
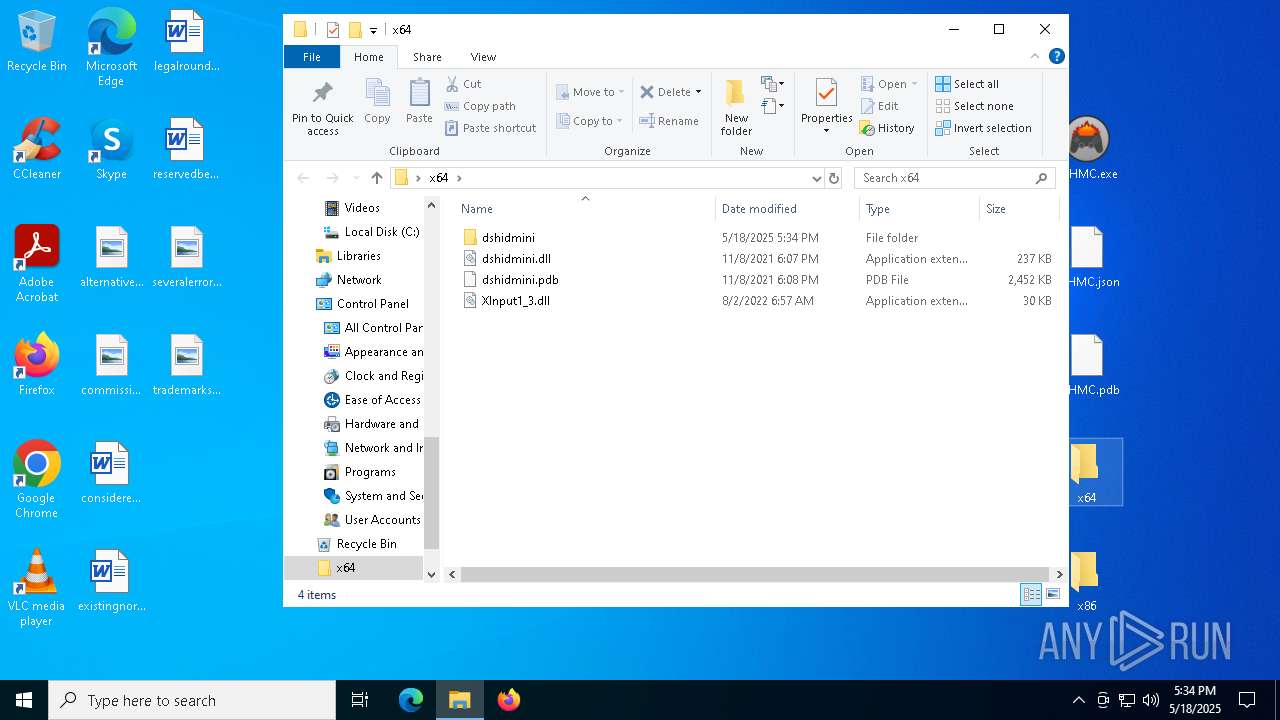
| 5260 | "C:\WINDOWS\System32\InfDefaultInstall.exe" "C:\Users\admin\Desktop\x64\dshidmini\dshidmini.inf" | C:\Windows\System32\InfDefaultInstall.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: INF Default Install Version: 5.2.3668.0 Modules
| |||||||||||||||
| 6040 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\dshidmini_v2.2.282.0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6080 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{7337e31a-0e6e-7e42-a7d5-eb2bf6022fc8}\dshidmini.inf" "9" "4e5cb8d47" "00000000000001E0" "WinSta0\Default" "00000000000001F0" "208" "C:\Users\admin\Desktop\x64\dshidmini" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6676 | "C:\WINDOWS\System32\InfDefaultInstall.exe" "C:\Users\admin\Desktop\x64\dshidmini\dshidmini.inf" | C:\Windows\System32\InfDefaultInstall.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: INF Default Install Exit code: 3221226540 Version: 5.2.3668.0 Modules
| |||||||||||||||
Total events
10 730
Read events
10 700
Write events
30
Delete events
0
Modification events
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\dshidmini_v2.2.282.0.zip | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6040) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
14
Suspicious files
19
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\x64\dshidmini\dshidmini.dll | executable | |
MD5:CE1BA56FD413818C5EDE3E4FC9138321 | SHA256:C5FE1228126E1384B8EBAAFB7AE253007BB1484624DB6F7EBEBA9FE3F6B338F1 | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\DSHMC.pdb | binary | |
MD5:92A54B0D173CBA8483D92B1B59875602 | SHA256:B837D2FFD9DE52E8CFCA49B5960D468CC8C73951B3F580D9C68F44299B0C1C75 | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\x64\dshidmini\dshidmini.inf | binary | |
MD5:FCFEE1D3202BAB69D68A1F8A3CAD4742 | SHA256:1490B82EA99509C9BF18605C3245D9B572D9C69EF7819F8E4D43BBC66F7FDFA5 | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\x64\dshidmini\dshidmini.cat | binary | |
MD5:77CD0EEFC220429AEA7F2457EC29F324 | SHA256:08A0123C8DCD5A04C7A7639210784DAB83692967EB053E664C6380F4F6F76327 | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\x64\XInput1_3.dll | executable | |
MD5:F2DA09030A83DC3A5F44E0E3D30C6B87 | SHA256:79DA6F81B877DCBDCC234E7158191D6555D0C56EE69329641FD051551EB5F770 | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\x64\dshidmini.pdb | binary | |
MD5:EF4F2A74F44BBB4EC7758B32EB4DB89F | SHA256:BE1AE0483D9D4512543258D195777A523052AF8D60E73D22383F5CAE2FBB903C | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\x64\dshidmini.dll | executable | |
MD5:590DAEBA78F0E711FCFF5C784FC6EE98 | SHA256:CACD7E2ABE5955C8EADF0C80AC72C4B2741BBE84522E88C14336D155A343EEBC | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\x64\dshidmini\igfilter.inf | binary | |
MD5:F4EACD01294A9ED7C482C193C3B3B3B7 | SHA256:765B40637270F4361FCB3F231626C9D14C989EF0D8BC63FB76BC7F47DF99ABD3 | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\x64\dshidmini\LICENSE | text | |
MD5:AC2529ED2F45E675368CB56112C18F71 | SHA256:C868DF89B6321BD7BF291B45FA6D8A0436F7053883C68EBAF0545ED98A2C7025 | |||
| 6040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6040.45143\DSHMC.json | text | |
MD5:4CB66DF591A9DF32444B2D46A03B592E | SHA256:74151CFAD882CEB1A8D540A8C6CA8453DF59BF99D3011963C711D351DE82E00C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4272 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4272 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4272 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |