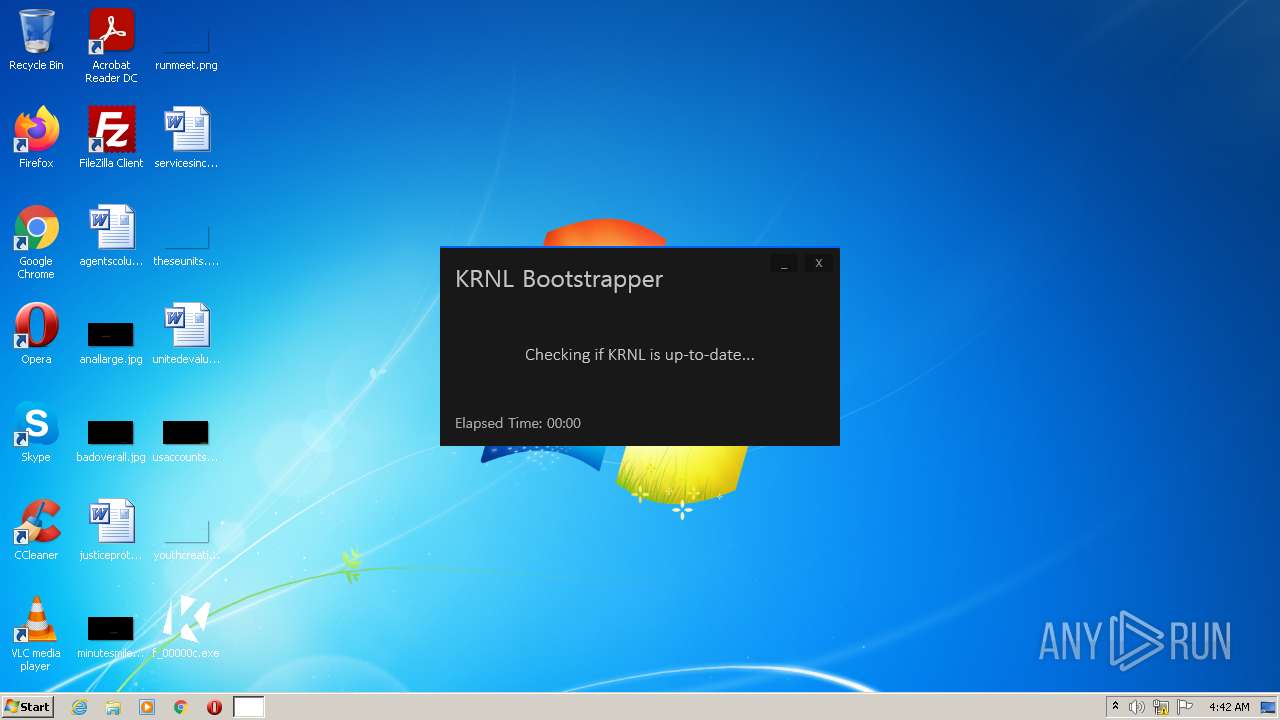
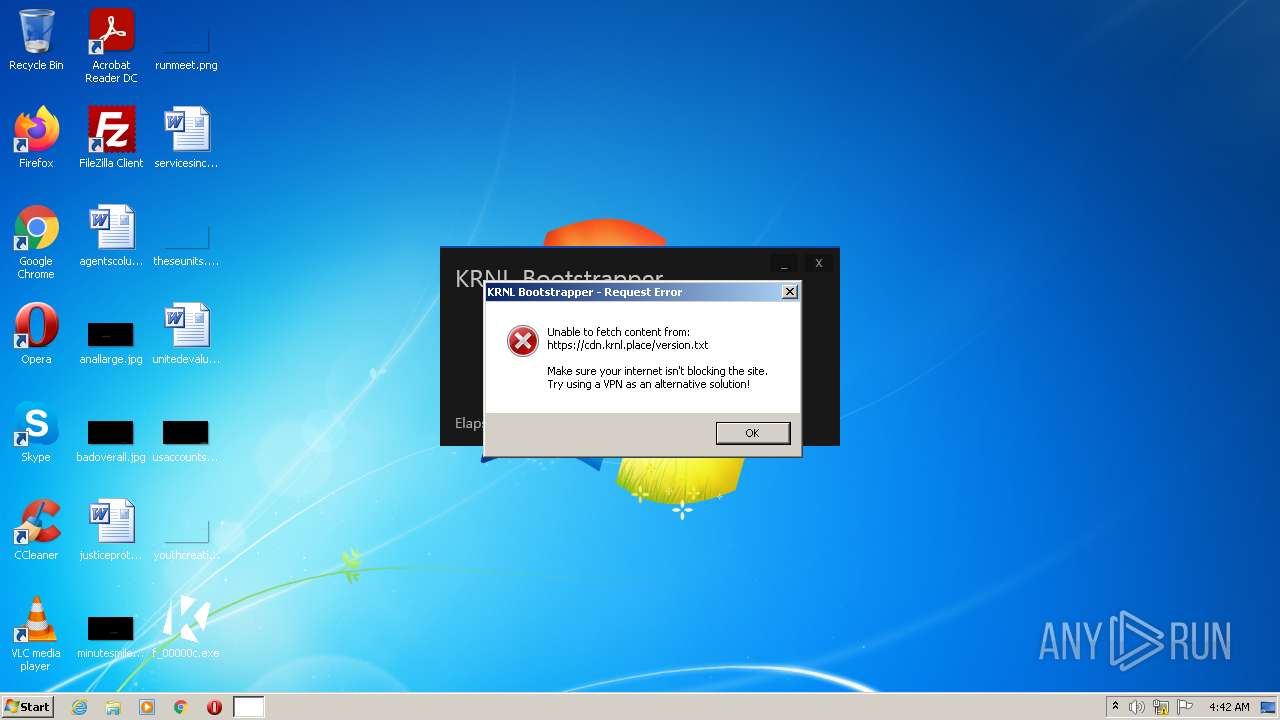
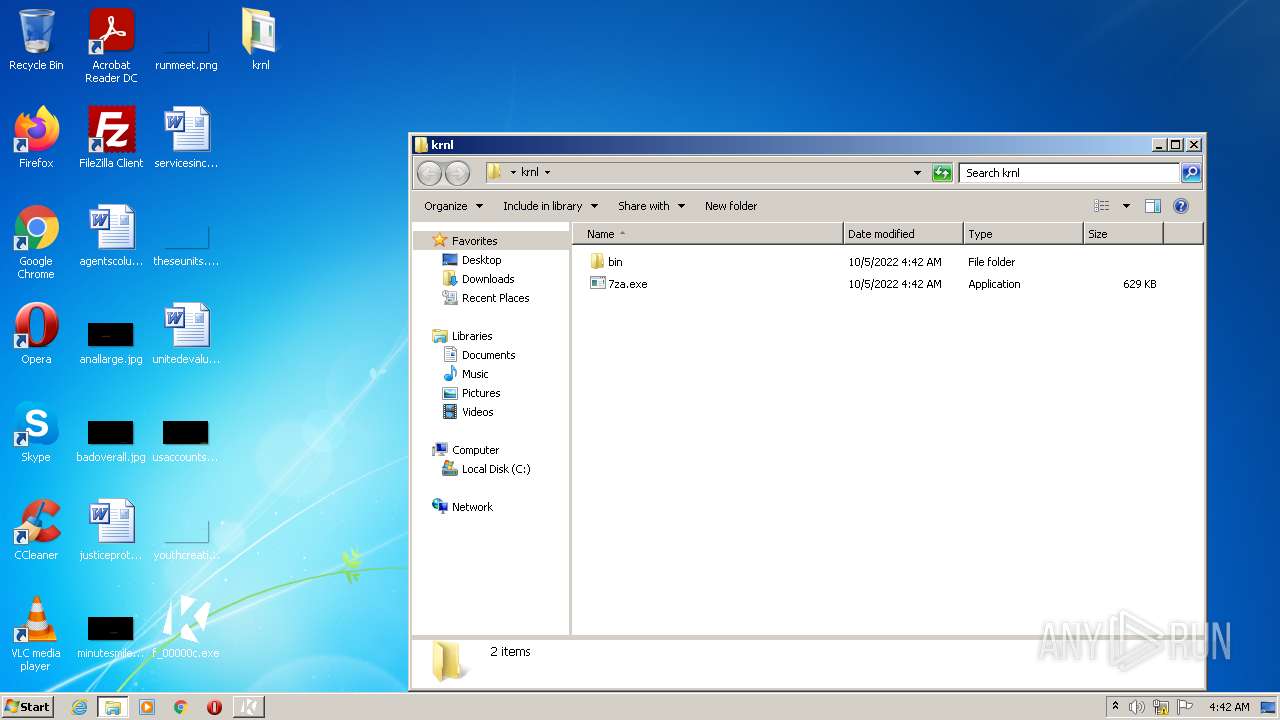
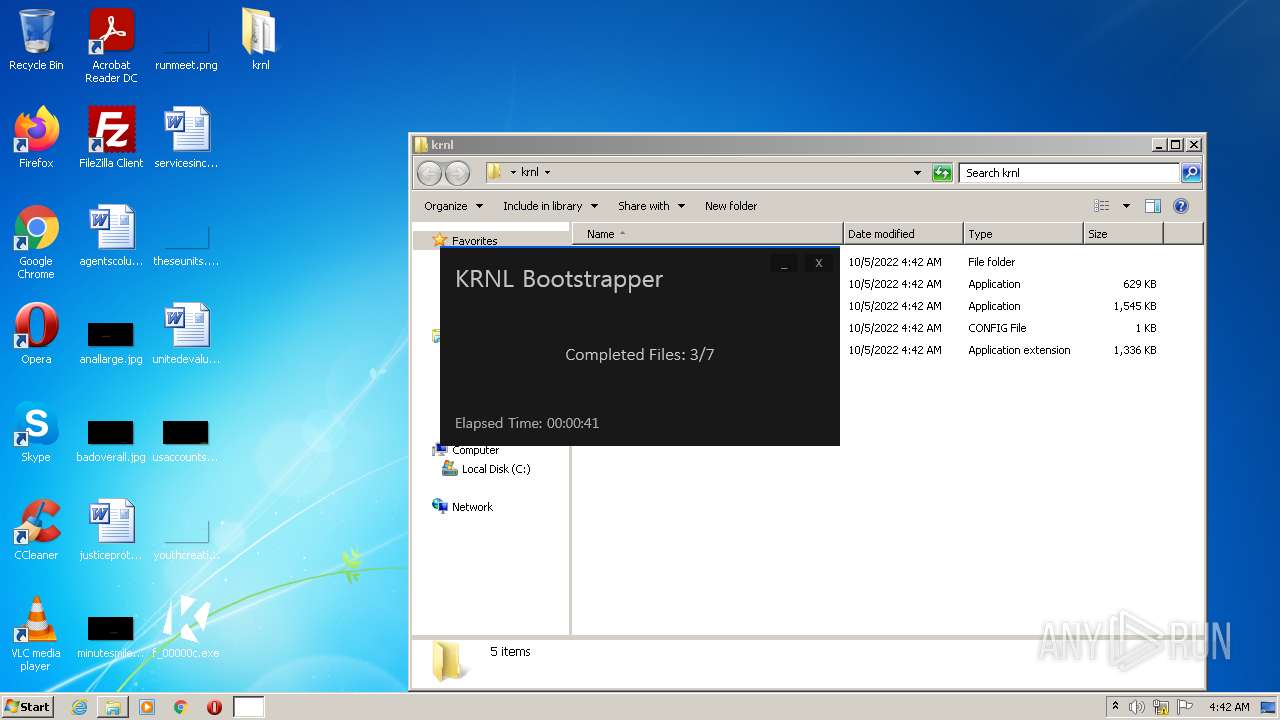
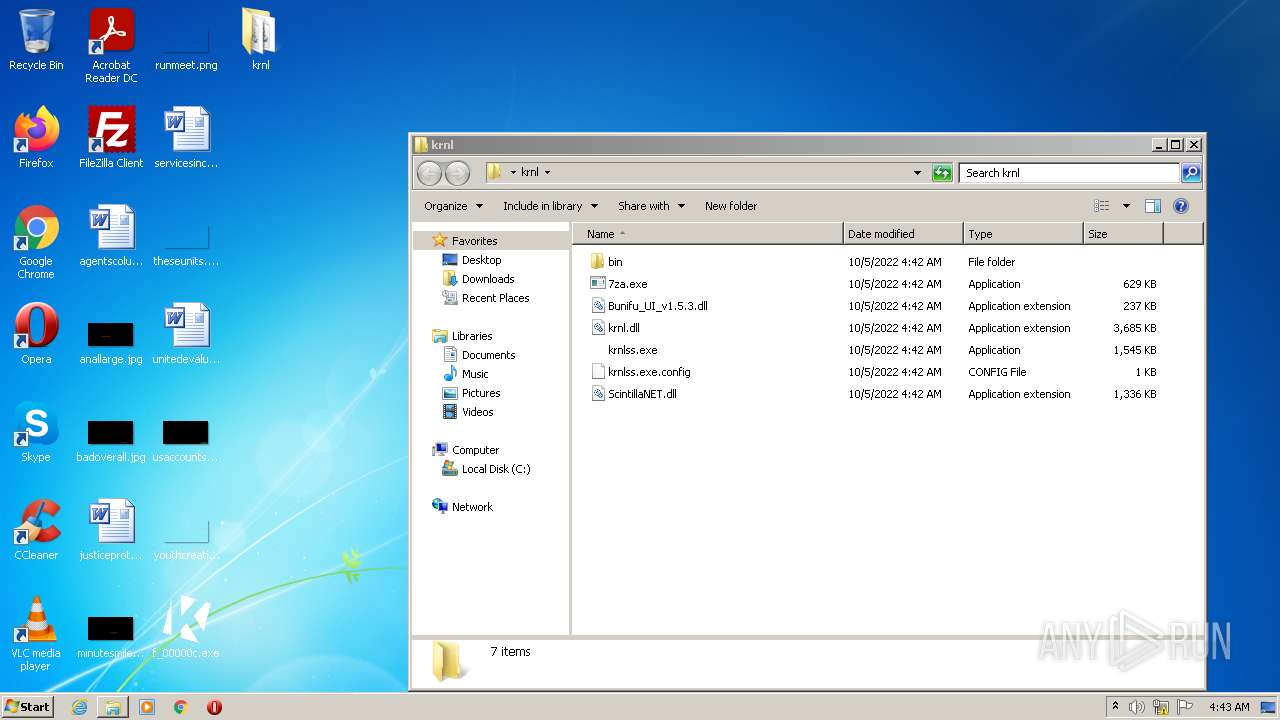
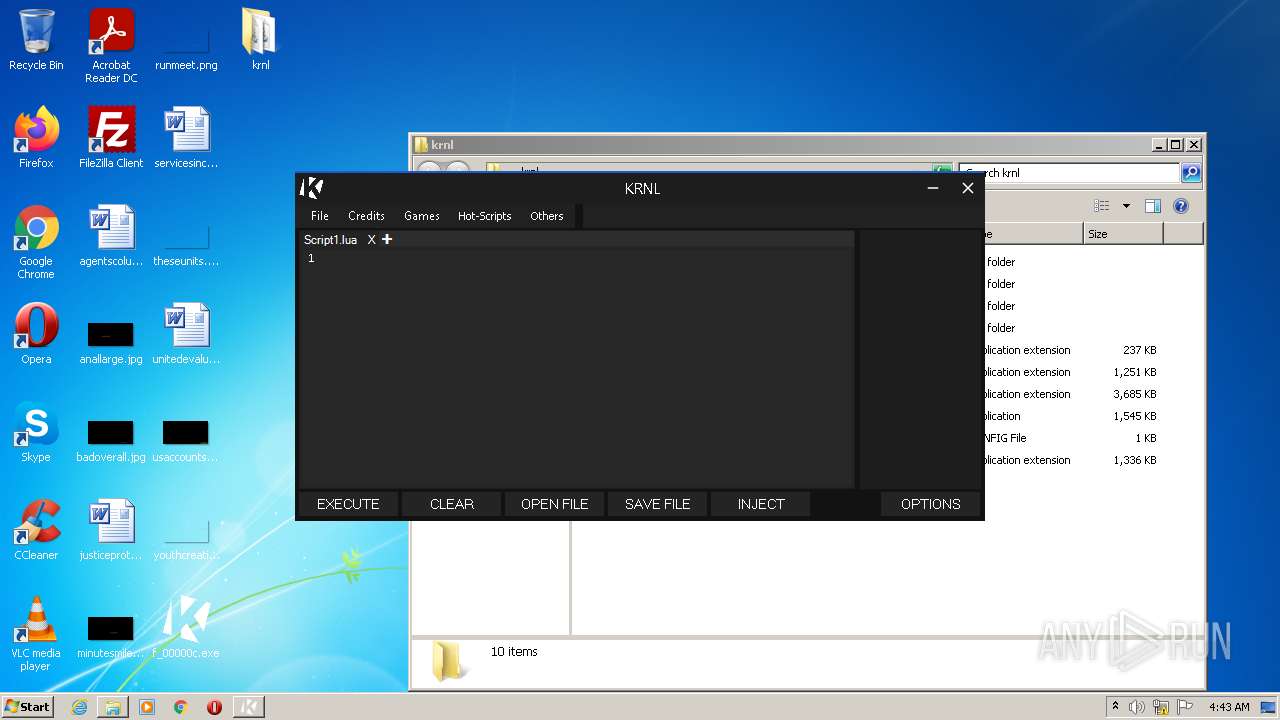
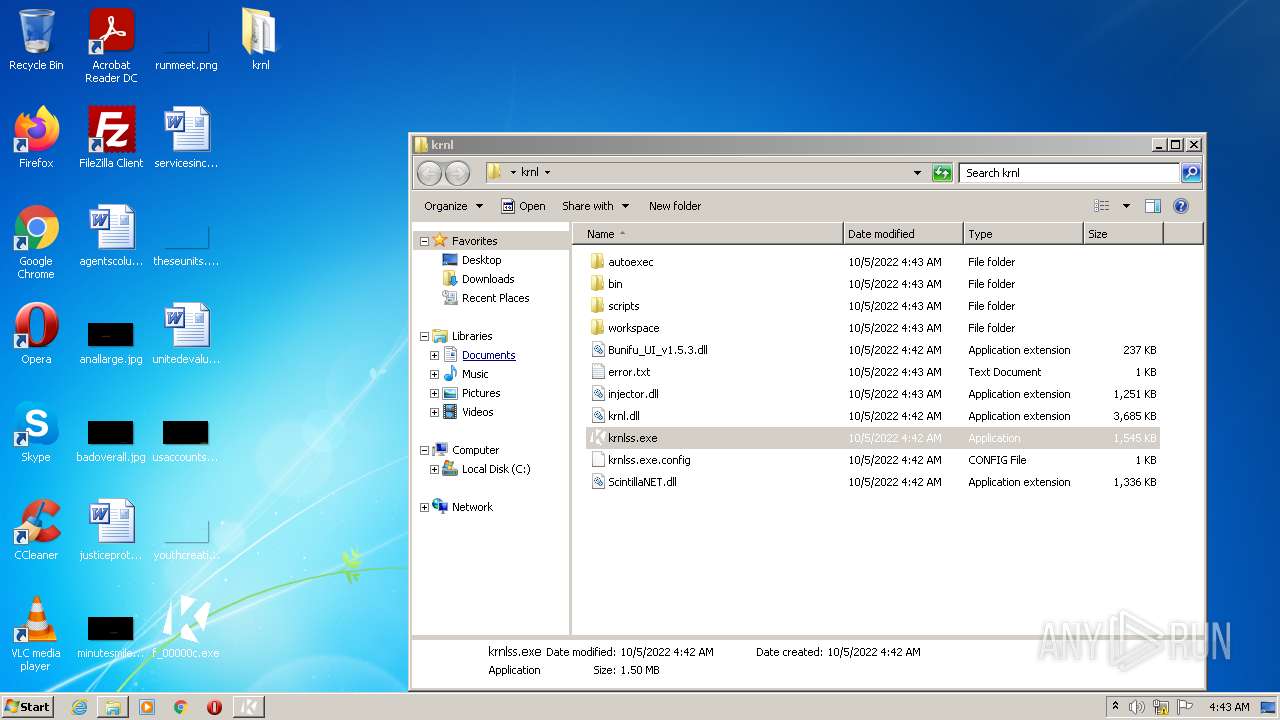
| File name: | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\f_00000c |
| Full analysis: | https://app.any.run/tasks/601a4882-d4fe-4c42-ba24-6cfc96d632b0 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2022, 03:42:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | F14153BBD95FC26D9CCEA77C49CF09B9 |
| SHA1: | CB59F900711EA751C4322B4DAB50FA2C0EE70B33 |
| SHA256: | 27EAB496D0B63D52C18CEE063110D9D479523B58426BFCB58E420A5CAE087C54 |
| SSDEEP: | 12288:aBVCrK2jsP3zv+FSF68GANNhWLS0B6L+FOCN+AzrnxdanvzFzho:SU7ecSgL6y+gk+rnxdarFu |
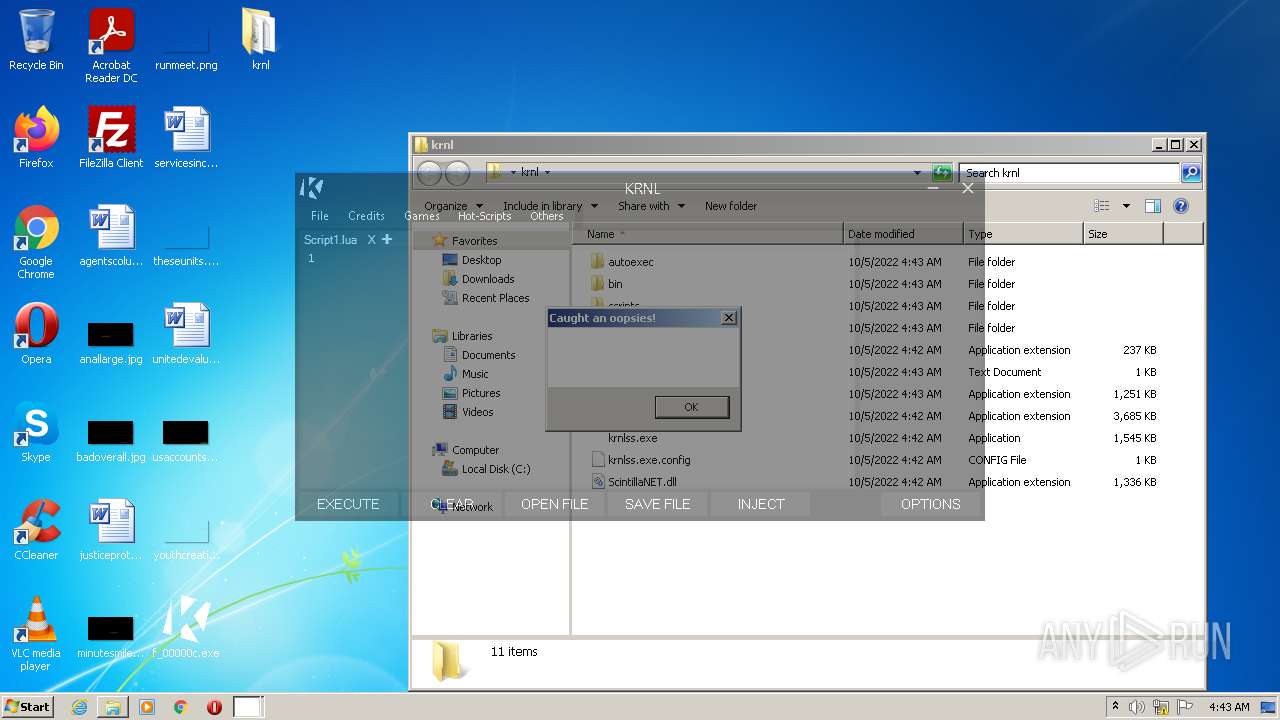
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3720)
- krnlss.exe (PID: 3676)
- krnlss.exe (PID: 1308)
- WerFault.exe (PID: 1144)
- WerFault.exe (PID: 2828)
- krnlss.exe (PID: 4004)
- WerFault.exe (PID: 1640)
Application was dropped or rewritten from another process
- 7za.exe (PID: 1176)
- 7za.exe (PID: 3792)
- krnlss.exe (PID: 3676)
- krnlss.exe (PID: 1308)
- krnlss.exe (PID: 4004)
SUSPICIOUS
Reads Environment values
- f_00000c.exe (PID: 3052)
- krnlss.exe (PID: 3676)
- krnlss.exe (PID: 1308)
- krnlss.exe (PID: 4004)
Reads the computer name
- f_00000c.exe (PID: 3052)
- 7za.exe (PID: 1176)
- 7za.exe (PID: 3792)
- krnlss.exe (PID: 3676)
- krnlss.exe (PID: 1308)
- krnlss.exe (PID: 4004)
Checks supported languages
- f_00000c.exe (PID: 3052)
- 7za.exe (PID: 1176)
- 7za.exe (PID: 3792)
- krnlss.exe (PID: 3676)
- krnlss.exe (PID: 1308)
- krnlss.exe (PID: 4004)
INFO
Reads the computer name
- WISPTIS.EXE (PID: 3688)
- WerFault.exe (PID: 2828)
- WerFault.exe (PID: 1144)
- WerFault.exe (PID: 1640)
Checks supported languages
- WISPTIS.EXE (PID: 3688)
- WerFault.exe (PID: 2828)
- WerFault.exe (PID: 1144)
- WerFault.exe (PID: 1640)
Reads settings of System Certificates
- f_00000c.exe (PID: 3052)
- krnlss.exe (PID: 3676)
- krnlss.exe (PID: 1308)
- krnlss.exe (PID: 4004)
Checks Windows Trust Settings
- krnlss.exe (PID: 3676)
- krnlss.exe (PID: 1308)
- krnlss.exe (PID: 4004)
Manual execution by user
- krnlss.exe (PID: 1308)
- krnlss.exe (PID: 4004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2093-Aug-30 18:10:57 |
| Debug artifacts: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | krnl_bootstrapper |
| FileVersion: | 1.0.0.0 |
| InternalName: | krnl_bootstrapper.exe |
| LegalCopyright: | Copyright © 2022 |
| LegalTrademarks: | - |
| OriginalFilename: | krnl_bootstrapper.exe |
| ProductName: | krnl_bootstrapper |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 3 |
| TimeDateStamp: | 2093-Aug-30 18:10:57 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 8192 | 939412 | 939520 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.5376 |
.rsrc | 950272 | 256216 | 256512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.20735 |
.reloc | 1212416 | 12 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 1.16474 | 254536 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.01924 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
1 (#2) | 3.26862 | 860 | UNKNOWN | UNKNOWN | RT_VERSION |
1 (#3) | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
58
Monitored processes
12
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1144 | C:\Windows\system32\WerFault.exe -u -p 1308 -s 1600 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1176 | "C:\Users\admin\Desktop\krnl\7za.exe" x "C:\Users\admin\Desktop\krnl\bin\src.7z" -o"C:\Users\admin\Desktop\krnl\bin" -aoa -bsp1 | C:\Users\admin\Desktop\krnl\7za.exe | — | f_00000c.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 15.14 Modules
| |||||||||||||||
| 1308 | "C:\Users\admin\Desktop\krnl\krnlss.exe" | C:\Users\admin\Desktop\krnl\krnlss.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3762504530 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1640 | C:\Windows\system32\WerFault.exe -u -p 4004 -s 1596 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2828 | C:\Windows\system32\WerFault.exe -u -p 3676 -s 1696 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3052 | "C:\Users\admin\Desktop\f_00000c.exe" | C:\Users\admin\Desktop\f_00000c.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: krnl_bootstrapper Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3676 | "C:\Users\admin\Desktop\krnl\krnlss.exe" | C:\Users\admin\Desktop\krnl\krnlss.exe | f_00000c.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3762504530 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3688 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\SYSTEM32\WISPTIS.EXE | f_00000c.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 24 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3720 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3792 | "C:\Users\admin\Desktop\krnl\7za.exe" x "C:\Users\admin\Desktop\krnl\bin\Monaco.zip" -o"C:\Users\admin\Desktop\krnl\bin" -aoa -bsp1 | C:\Users\admin\Desktop\krnl\7za.exe | — | f_00000c.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 15.14 Modules
| |||||||||||||||
Total events
14 480
Read events
14 326
Write events
154
Delete events
0
Modification events
| (PID) Process: | (3052) f_00000c.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: f_00000c.exe | |||
| (PID) Process: | (3052) f_00000c.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3052) f_00000c.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3052) f_00000c.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3052) f_00000c.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3688) WISPTIS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: WISPTIS.EXE | |||
| (PID) Process: | (3688) WISPTIS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Wisp\Touch |
| Operation: | write | Name: | TouchGate |
Value: 1 | |||
| (PID) Process: | (3688) WISPTIS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Wisp\MultiTouch |
| Operation: | write | Name: | MultiTouchEnabled |
Value: 1 | |||
| (PID) Process: | (3688) WISPTIS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Wisp\Pen\SysEventParameters |
| Operation: | write | Name: | FlickMode |
Value: 1 | |||
| (PID) Process: | (3688) WISPTIS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Wisp\Pen\SysEventParameters |
| Operation: | write | Name: | TouchFlickTolerance |
Value: 50 | |||
Executable files
137
Suspicious files
3
Text files
45
Unknown types
66
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3052 | f_00000c.exe | C:\Users\admin\Desktop\krnl\bin\src.7z | — | |
MD5:— | SHA256:— | |||
| 1176 | 7za.exe | C:\Users\admin\Desktop\krnl\bin\src\CefSharp.BrowserSubprocess.Core.pdb | — | |
MD5:— | SHA256:— | |||
| 1176 | 7za.exe | C:\Users\admin\Desktop\krnl\bin\src\CefSharp.Core.pdb | — | |
MD5:— | SHA256:— | |||
| 1176 | 7za.exe | C:\Users\admin\Desktop\krnl\bin\src\CefSharp.OffScreen.pdb | pdb | |
MD5:5E67005702F401904BEB30FF08DABA06 | SHA256:5583B83CF52ADF789CA846BF467CEB65FA73236100C41EE4E21A12BEE993B457 | |||
| 1176 | 7za.exe | C:\Users\admin\Desktop\krnl\bin\src\CefSharp.pdb | pdb | |
MD5:CA5A17CFB5EEE0AA89B9AE2E5D9A411D | SHA256:47A9B9C9EC218CB60A5BA66FC8F54999A33F3DED58CEBCE632E15AE0DF0A1D49 | |||
| 1176 | 7za.exe | C:\Users\admin\Desktop\krnl\bin\src\CefSharp.Test.dll.config | xml | |
MD5:08D8F7932F150D4B62650FAB6D43B4E3 | SHA256:5EA532A66EA3003A3821141E3438840FAC452DFF4308F43C7CBC16623E0C3FC2 | |||
| 1176 | 7za.exe | C:\Users\admin\Desktop\krnl\bin\src\CefSharp.BrowserSubprocess.pdb | pdb | |
MD5:8500C8EAEDF45493B8469F25C71E4A1E | SHA256:C4EE78C4DBCCF4A1A1E389BC0702F4EC9E1FAE92A2710CCA0D28C18BE2D93A62 | |||
| 3052 | f_00000c.exe | C:\Users\admin\Desktop\krnl\krnlss.exe | executable | |
MD5:4D7C519CC2127F785D13694D7A281F33 | SHA256:6DA486F47B7CDC5F54BAD208AE48A25E3F1827FED64D1455C9D986B68D37F7B5 | |||
| 1176 | 7za.exe | C:\Users\admin\Desktop\krnl\bin\src\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 1176 | 7za.exe | C:\Users\admin\Desktop\krnl\bin\src\CefSharp.OffScreen.xml | xml | |
MD5:AD52F4620459C39EA85569D4EFB27B1C | SHA256:53B310365455C68CC7344171FADCFAC4907549BC4F96215253D6E495324730A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3052 | f_00000c.exe | 51.178.133.139:443 | cdn.krnl.place | OVH SAS | FR | unknown |
3052 | f_00000c.exe | 188.114.96.3:443 | k-storage.com | CLOUDFLARENET | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.krnl.place |
| suspicious |
k-storage.com |
| malicious |
dns.msftncsi.com |
| shared |