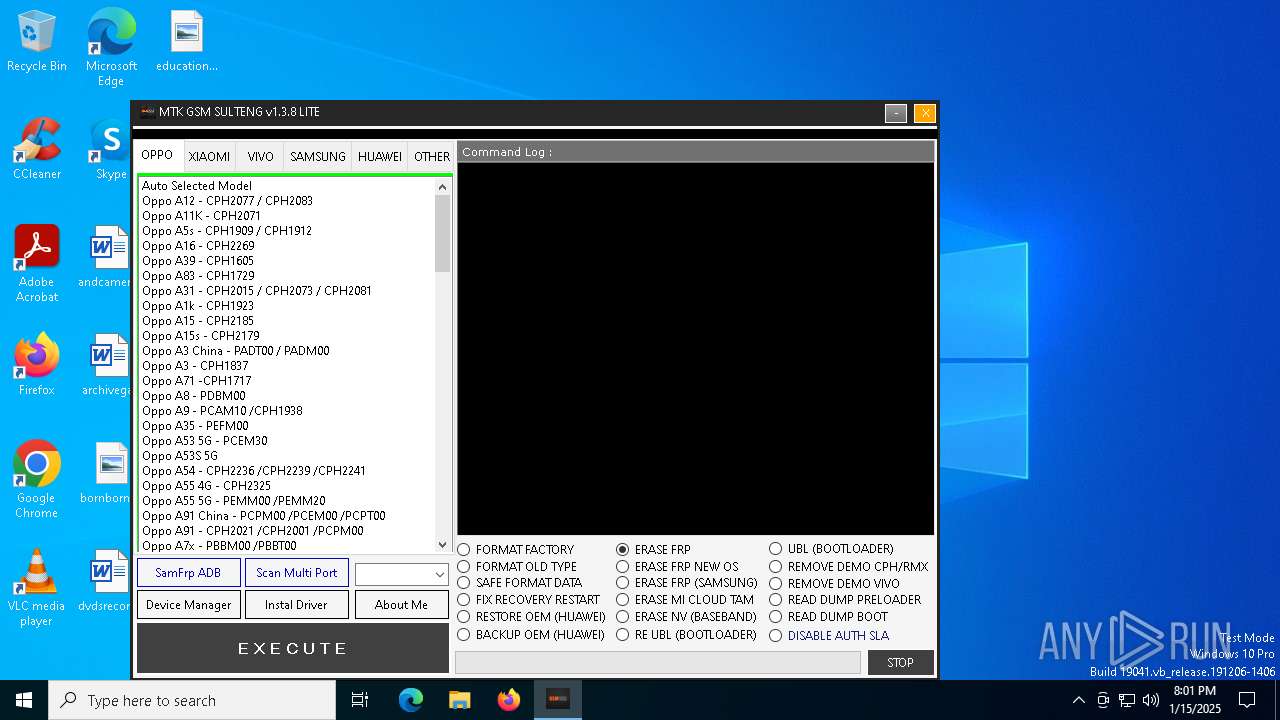
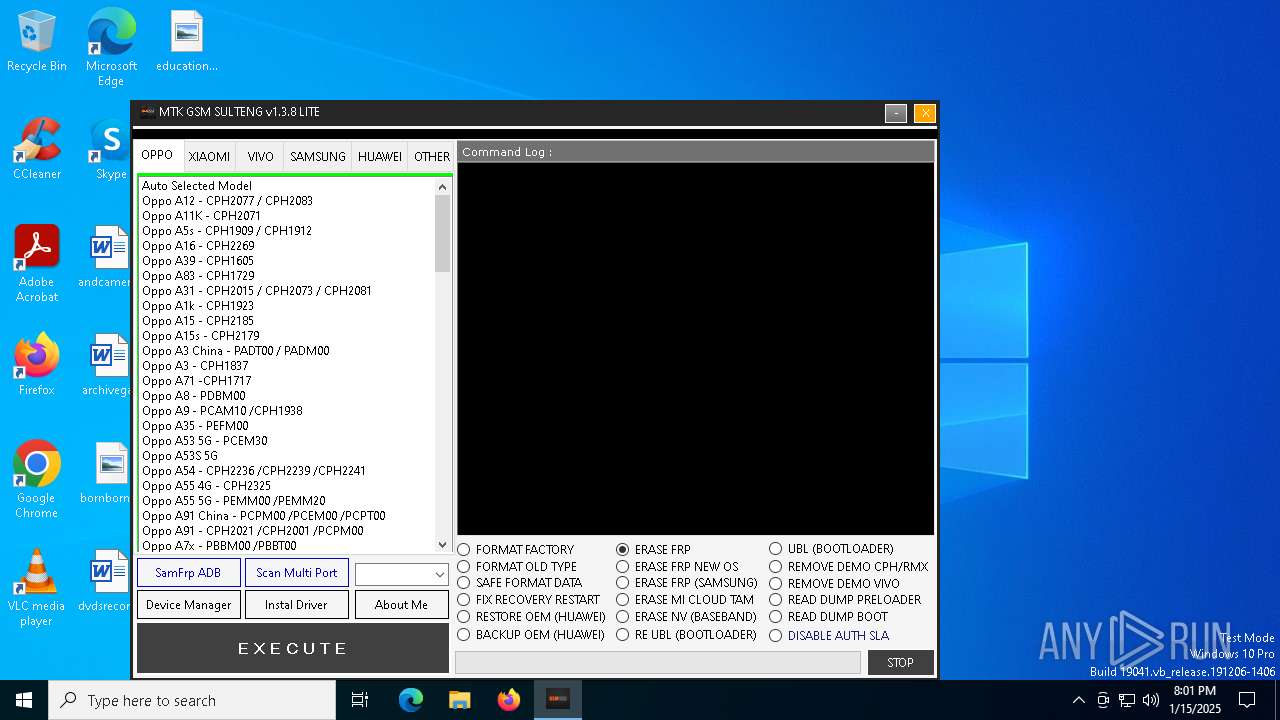
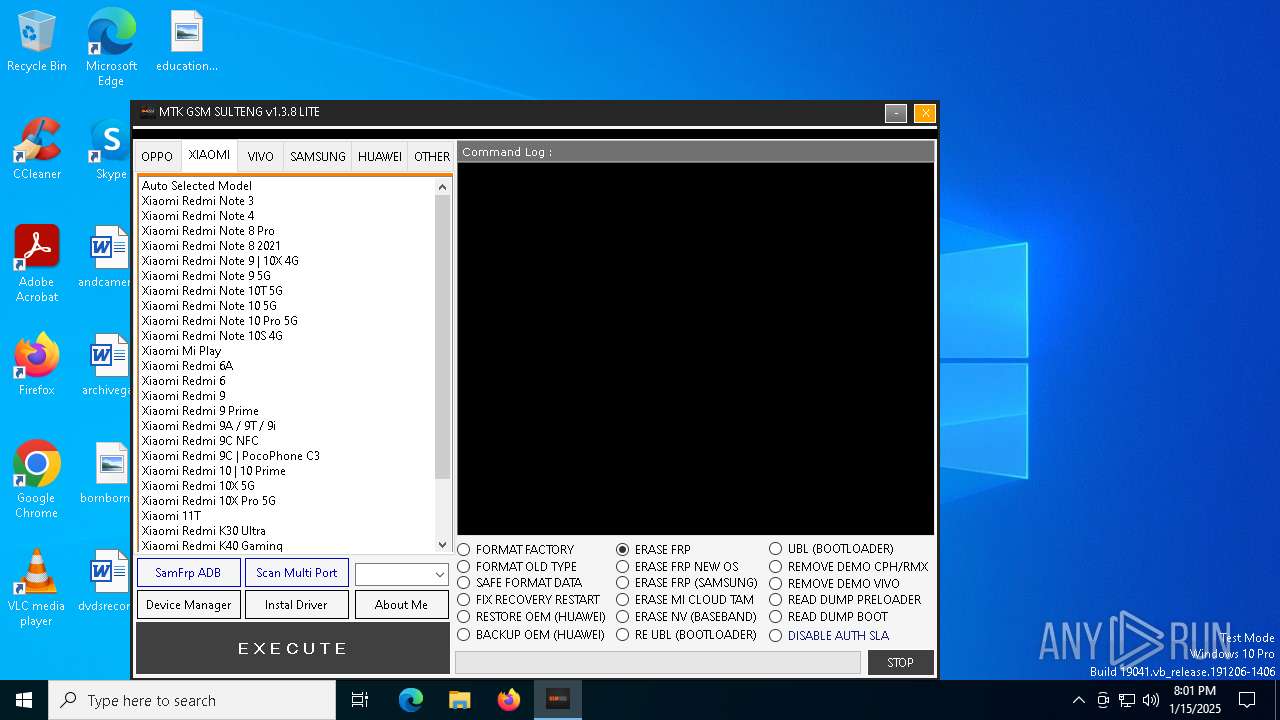
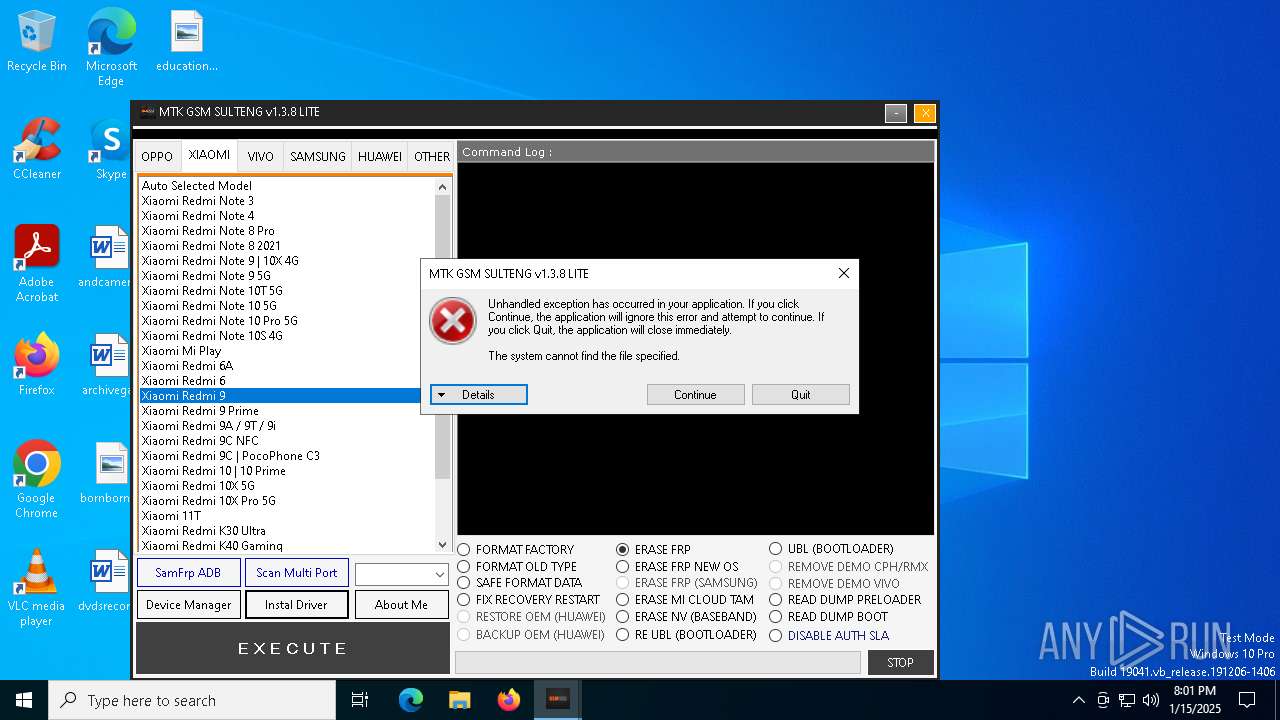
| File name: | MTK GSM Sulteng V1.3.8.exe |
| Full analysis: | https://app.any.run/tasks/de50c2fd-4d3d-4026-a9df-eb22f011cc49 |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2025, 20:00:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 9D66C5E252CA880DC38DB7FF9B10C244 |
| SHA1: | 06D695197C191287642D3E7F4AF241B1A846CD79 |
| SHA256: | 27B01A5CF26B5D1979FA96A2F775EC26F2DA18912228E92F3AA0CE8DF64777CD |
| SSDEEP: | 3072:4H04aPpohcjPxbmbE2aokr+VbbxMbb+UbbbnLxPtcc+bYaBzb2Z54rR9lKBvAfIM:hOgO8+JDfz |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- WinRAR.exe (PID: 6232)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6232)
Starts CMD.EXE for commands execution
- MTK GSM Sulteng V1.3.8.exe (PID: 3988)
Reads security settings of Internet Explorer
- MTK GSM Sulteng V1.3.8.exe (PID: 3988)
Loads Python modules
- python.exe (PID: 1200)
- python.exe (PID: 7088)
Executes as Windows Service
- VSSVC.exe (PID: 6820)
INFO
Checks supported languages
- MTK GSM Sulteng V1.3.8.exe (PID: 6972)
- MTK GSM Sulteng V1.3.8.exe (PID: 3988)
- msiexec.exe (PID: 3208)
Reads the machine GUID from the registry
- MTK GSM Sulteng V1.3.8.exe (PID: 6972)
Reads the computer name
- MTK GSM Sulteng V1.3.8.exe (PID: 6972)
- MTK GSM Sulteng V1.3.8.exe (PID: 3988)
- msiexec.exe (PID: 3208)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6232)
Manual execution by a user
- WinRAR.exe (PID: 6232)
- MTK GSM Sulteng V1.3.8.exe (PID: 3988)
The process uses the downloaded file
- WinRAR.exe (PID: 6232)
The sample compiled with english language support
- WinRAR.exe (PID: 6232)
Python executable
- python.exe (PID: 1200)
- python.exe (PID: 7088)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1296)
Creates files or folders in the user directory
- msiexec.exe (PID: 1296)
Process checks computer location settings
- MTK GSM Sulteng V1.3.8.exe (PID: 3988)
Reads the software policy settings
- msiexec.exe (PID: 1296)
Checks proxy server information
- msiexec.exe (PID: 1296)
Manages system restore points
- SrTasks.exe (PID: 1476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:05:13 16:34:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 329728 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5262e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft |
| FileDescription: | MTK_UNIVERSAL_V3 |
| FileVersion: | 1.0.0.0 |
| InternalName: | MTK_UNIVERSAL_V3.exe |
| LegalCopyright: | Copyright © Microsoft 2021 |
| OriginalFileName: | MTK_UNIVERSAL_V3.exe |
| ProductName: | MTK_UNIVERSAL_V3 |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
135
Monitored processes
15
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1200 | data\python data\mtk e frp | C:\Users\admin\Desktop\MTK GSM Sulteng V1.3.8\data\python.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 4294967295 Version: 3.10.0rc2 Modules
| |||||||||||||||
| 1296 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\Desktop\MTK GSM Sulteng V1.3.8\data\driver.msi" | C:\Windows\SysWOW64\msiexec.exe | MTK GSM Sulteng V1.3.8.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1602 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1476 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3640 | "cmd.exe" data\python data\mtk da seccfg unlock | C:\Windows\SysWOW64\cmd.exe | — | MTK GSM Sulteng V1.3.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3988 | "C:\Users\admin\Desktop\MTK GSM Sulteng V1.3.8\MTK GSM Sulteng V1.3.8.exe" | C:\Users\admin\Desktop\MTK GSM Sulteng V1.3.8\MTK GSM Sulteng V1.3.8.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: MTK_UNIVERSAL_V3 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5256 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5472 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5652 | "cmd.exe" data\python data\mtk e frp | C:\Windows\SysWOW64\cmd.exe | — | MTK GSM Sulteng V1.3.8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 384
Read events
22 189
Write events
186
Delete events
9
Modification events
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MTK GSM Sulteng V1.3.8.rar | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFAE000000710000006E0400005A020000 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
54
Suspicious files
1 123
Text files
321
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\.vs\mtk\v16\Browse.VC.db | binary | |
MD5:30FB835DD3F1E9A074F00F6818166C03 | SHA256:B9573CCAC1EA44B53C368CB81F3CB105B90118A31263804DE54B0C20EC3485CA | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\AdbWinApi.dll.dat | executable | |
MD5:ED5A809DC0024D83CBAB4FB9933D598D | SHA256:D60103A5E99BC9888F786EE916F5D6E45493C3247972CB053833803DE7E95CF9 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\colorama\__pycache__\ansitowin32.cpython-310.pyc | binary | |
MD5:D2EC821664E5F50CF53C5A649B0B863A | SHA256:94BAA81EE0FABE91CD4A87D63C58B58CFF0F9ED382CF95431EA12CE60210C80F | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\AdbWinApi.dll | executable | |
MD5:C0271C6AA30C74CBB63BE0E0ADFDCF71 | SHA256:D9588BABF213AA15043FF7A1E2ED5D986103B0EA012110F9118F2C9B2482C5A5 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\AdbWinUsbApi.dll | executable | |
MD5:0E24119DAF1909E398FA1850B6112077 | SHA256:25207C506D29C4E8DCEB61B4BD50E8669BA26012988A43FBF26A890B1E60FC97 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\colorama\__pycache__\initialise.cpython-310.pyc | binary | |
MD5:64CB911D239A5F00BEBFE0F740753FCC | SHA256:2B0E7AB1BAF704A223467982568CB60A7DBC55F3452030BB6B6AE44AF2AAAA9A | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\colorama\ansitowin32.py | text | |
MD5:CC62E5B793FABB96B5A3B89F5B3FF3F5 | SHA256:C95EC212609BD7D3239C928E0D9104BCC1FF7E76C98709E9CE8E2CC59B865E60 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\.gitignore | text | |
MD5:7A423E56842E461A40E8CDEF6178BF96 | SHA256:438462707B14D46E5E34295DA1D356D393A618C5378DAA084ACE88ADD1A18B69 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\api-ms-win-core-path-l1-1-0.dll | executable | |
MD5:0ED28B807ADB89AA37F9B3C057134F4A | SHA256:745C3AA5871AF101B3B023A948FB0CC73904235085F011C9906A5804D5D71584 | |||
| 6232 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6232.13280\MTK GSM Sulteng V1.3.8\data\.vs\mtk12\v16\.suo | binary | |
MD5:701646FDF8644321064E418595ABA5CA | SHA256:922F04DB3D9D2892DC0B51CAFBF79B591FC809D21F1C20ED41D22A41BE8E389C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
43
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.17:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6464 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6200 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6200 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1296 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHwbNTVK59t050FfEWnKa6g%3D | unknown | — | — | unknown |
1296 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHwbNTVK59t050FfEWnKa6g%3D | unknown | — | — | unknown |
1296 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://rb.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTDRSYViRCZTxmZjLENmnwVjLly9QQU1MAGIknrOUvdk%2BJcobhHdglyA1gCEF0QyxjrOnkAh4OrdHf50xk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.17:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5564 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |