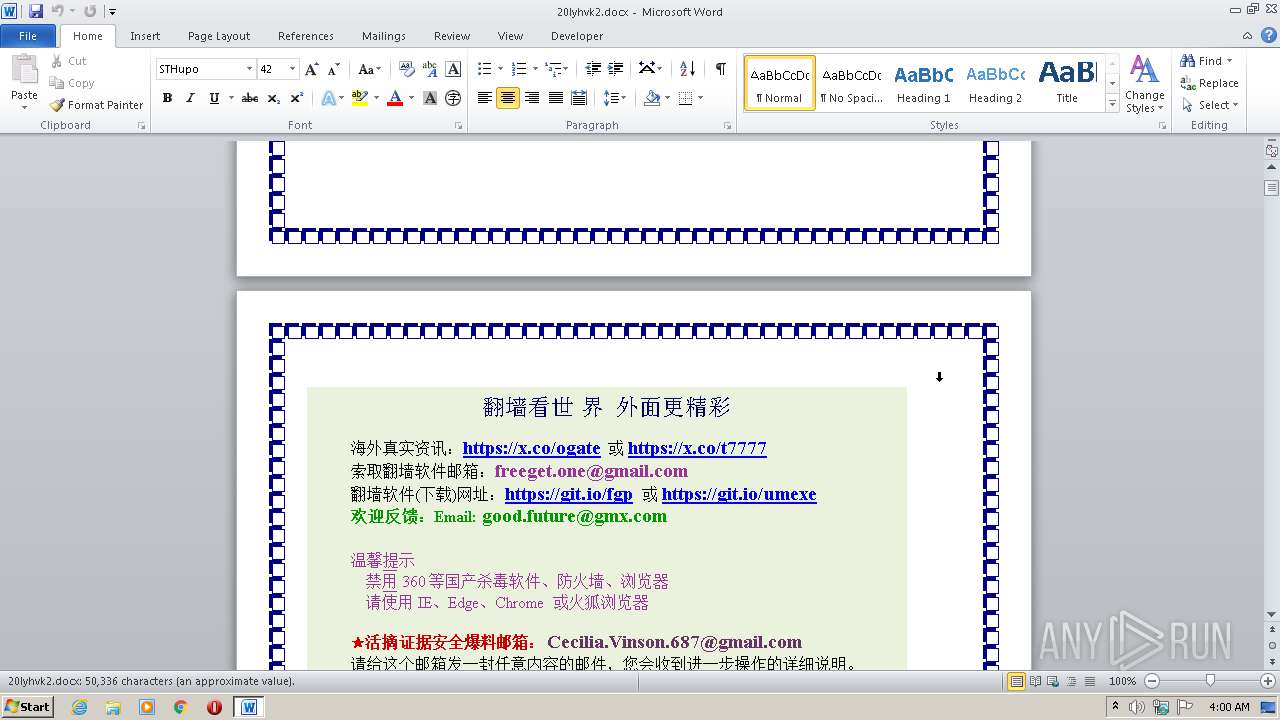
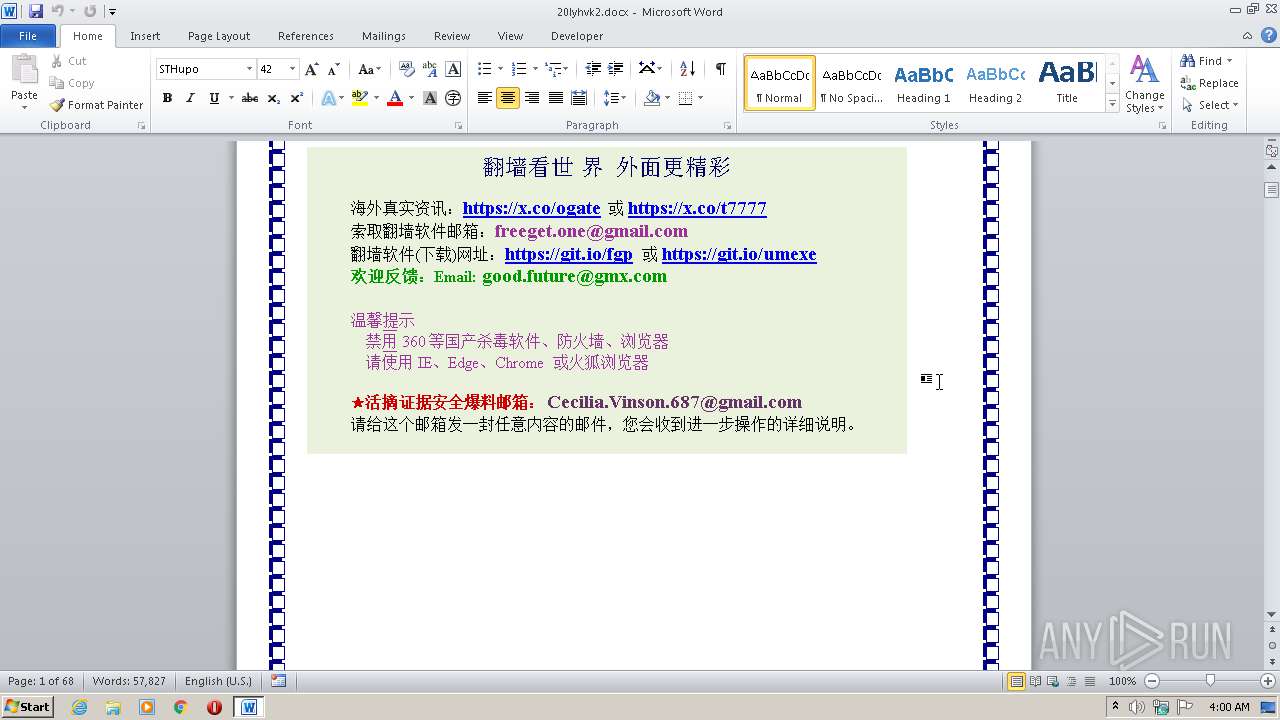
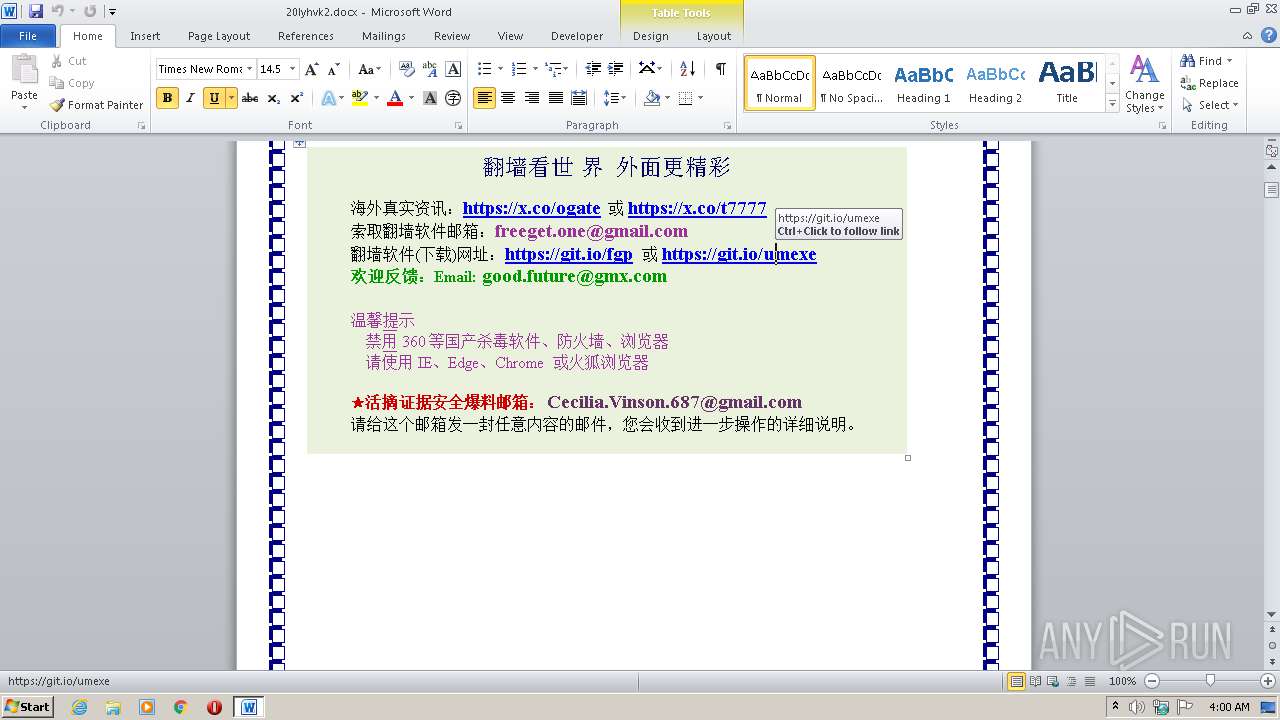
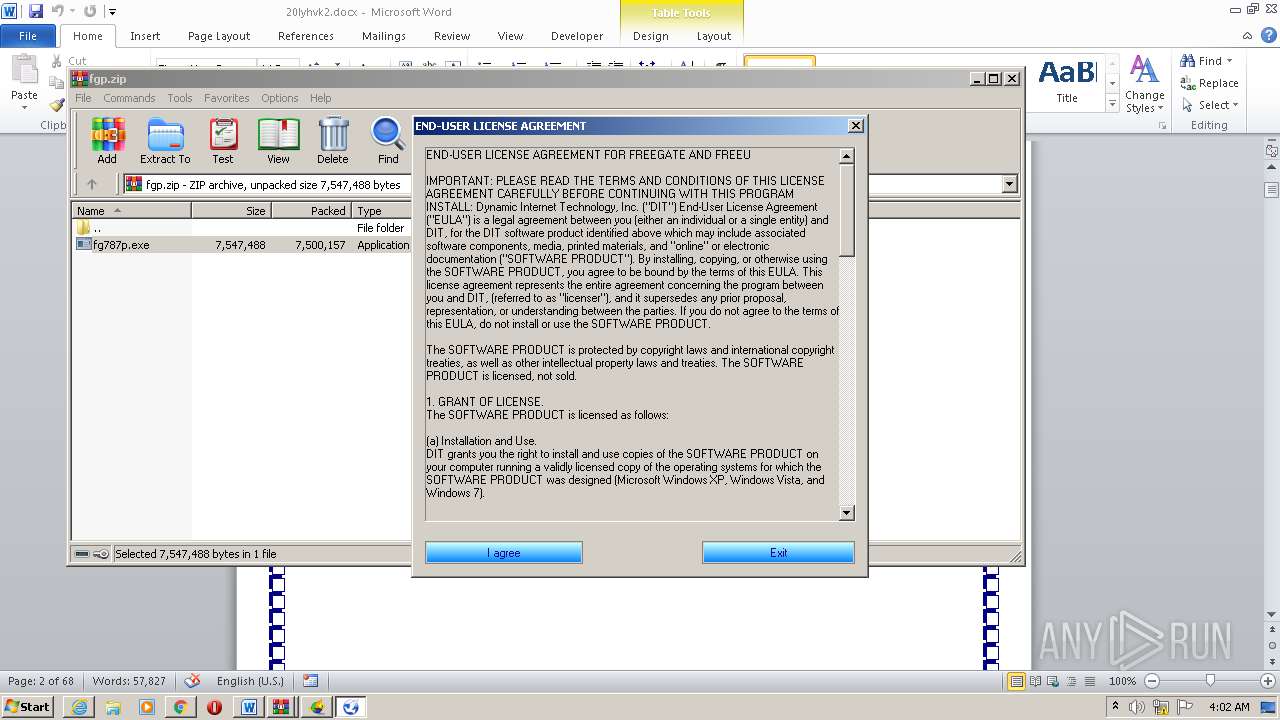
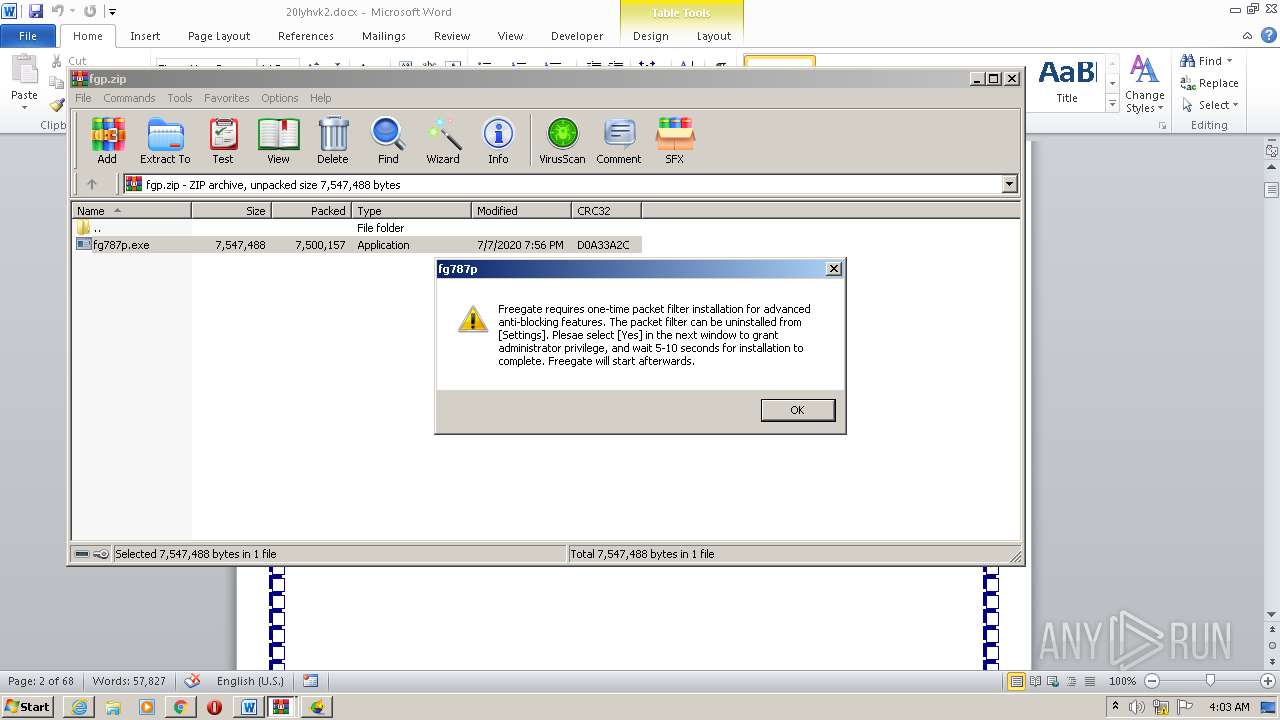
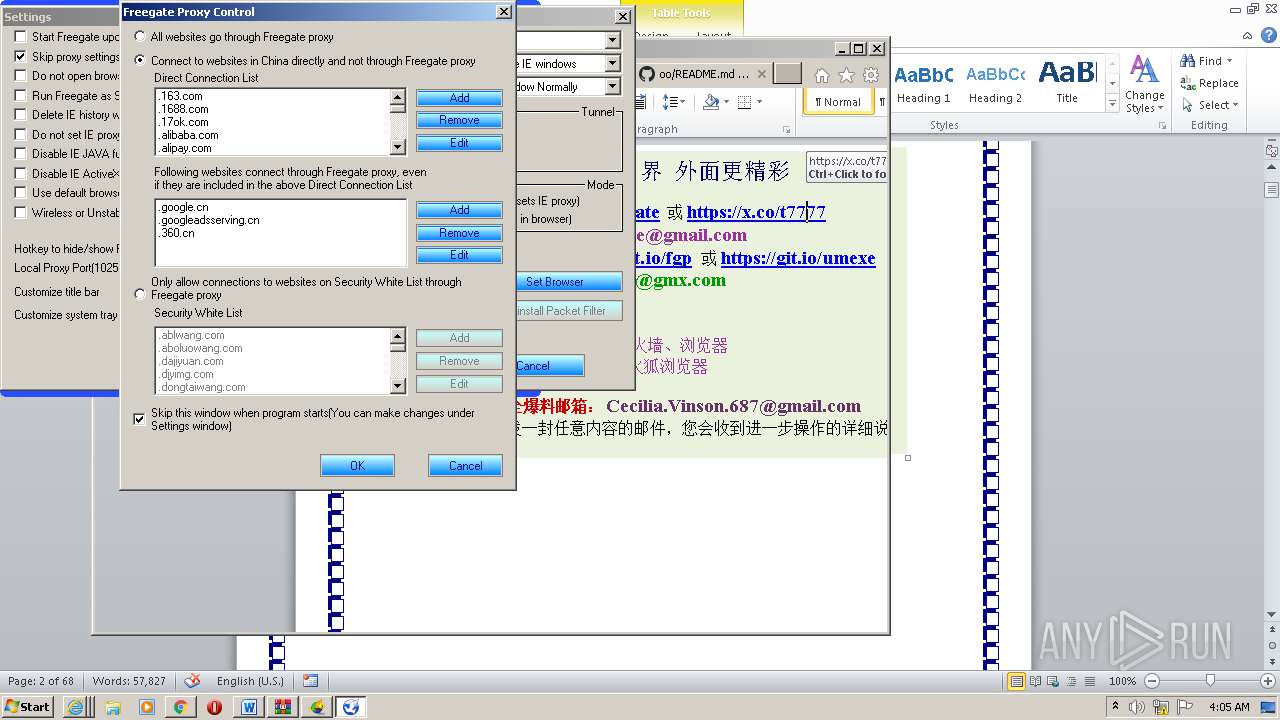
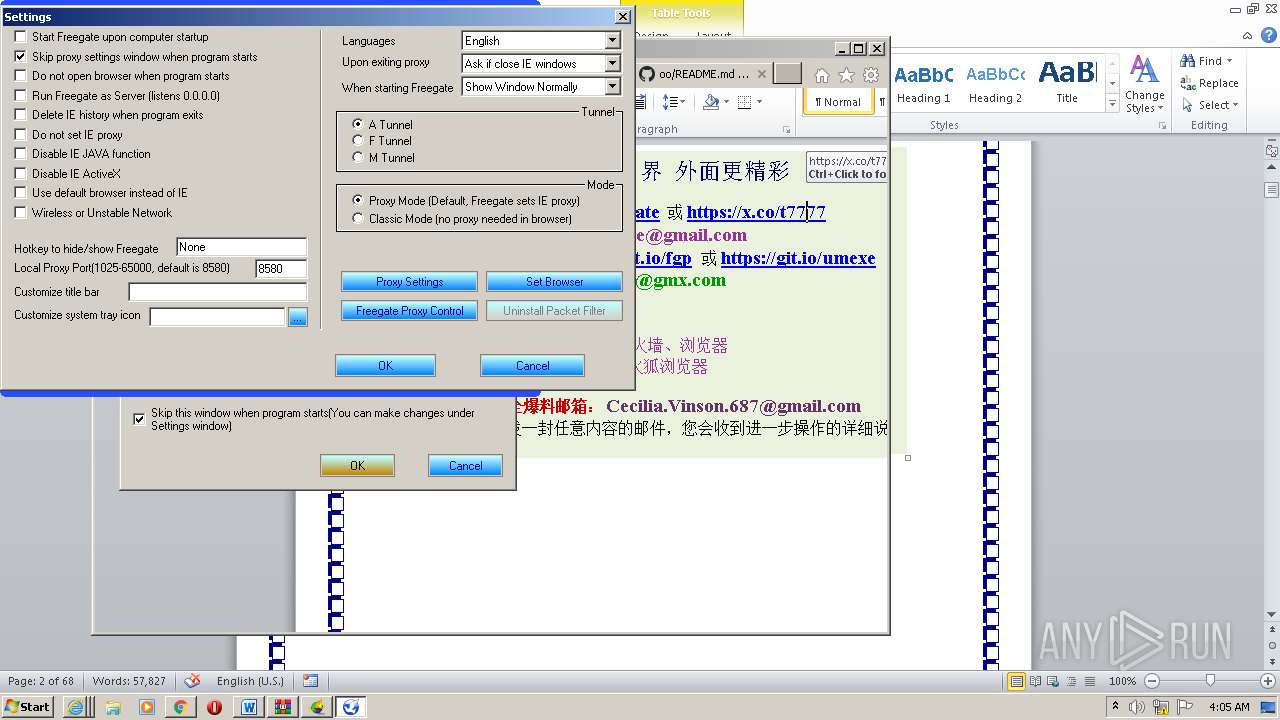
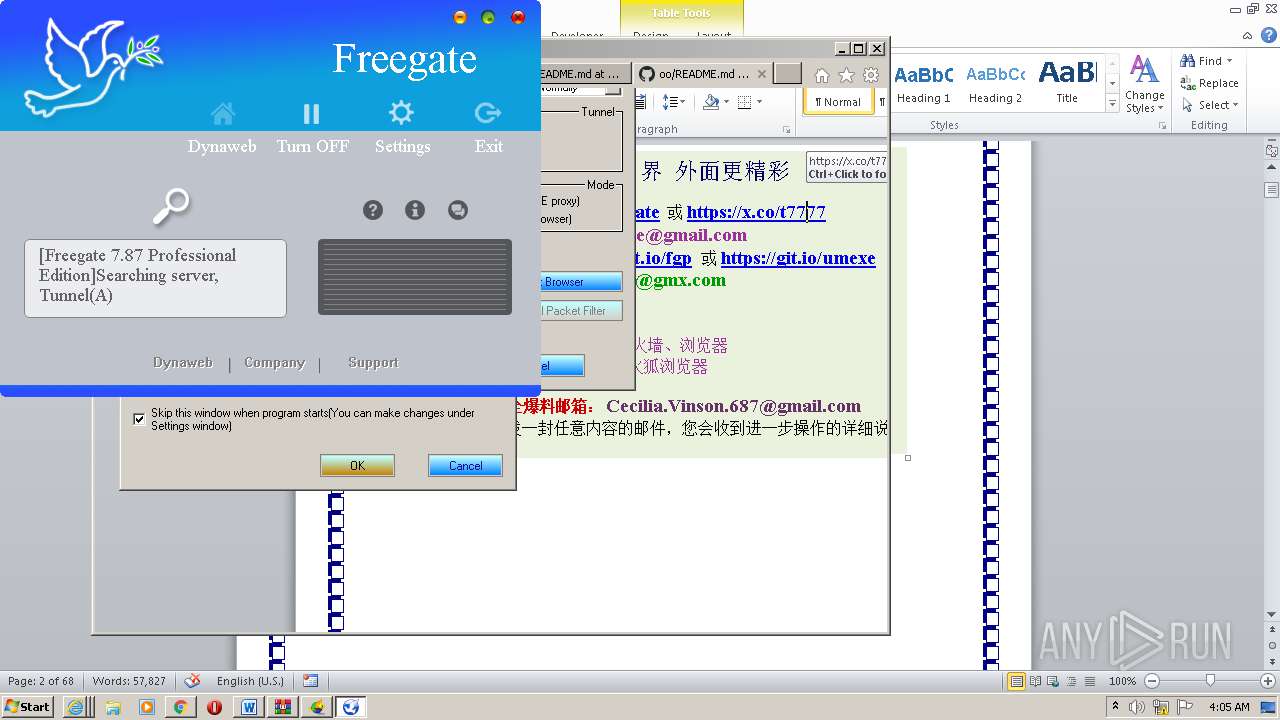
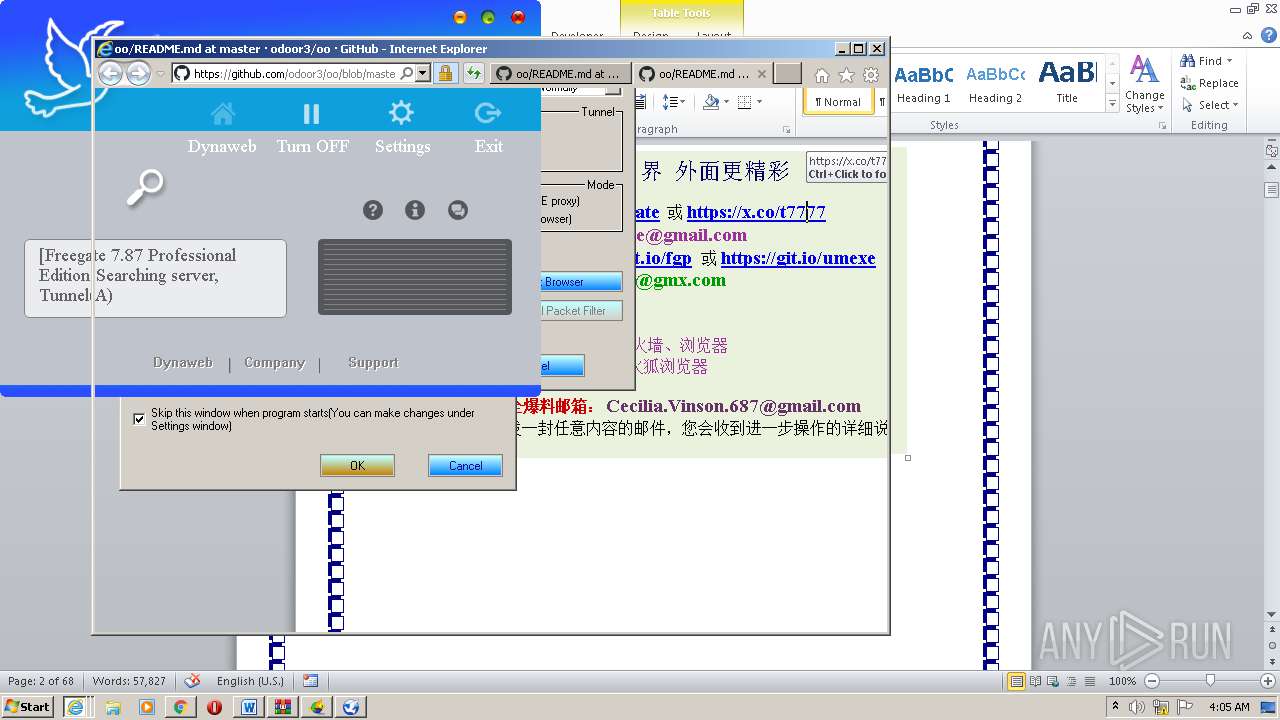
| File name: | 20lyhvk2.docx |
| Full analysis: | https://app.any.run/tasks/f8daacb9-d9fa-4d8f-bff7-5f4f4aae9138 |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2020, 03:00:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
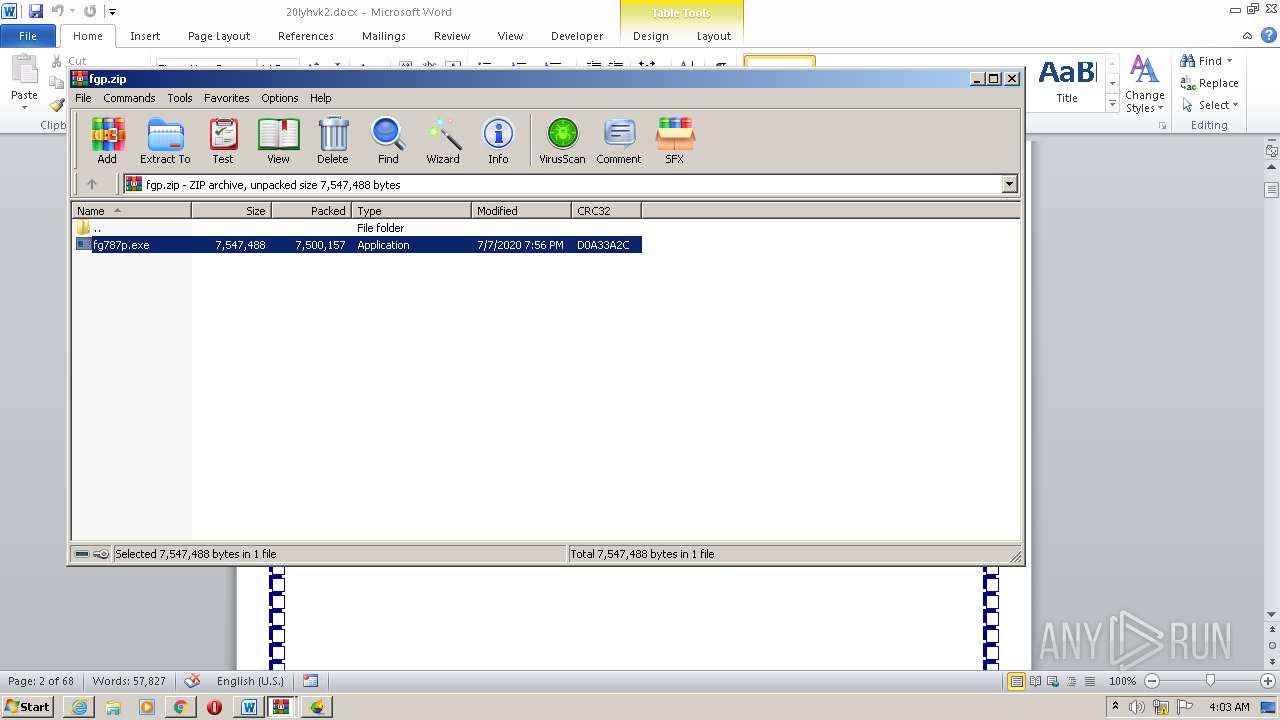
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 25C2D3489105F9DE292822E0F7351F55 |
| SHA1: | CAD3EECE0F63D196DF7EEEE2FA13025D89AFAB8E |
| SHA256: | 27AA9D080C31365ACEDF43D603B3997D15730C13EDA323ED3EF4152E54579E38 |
| SSDEEP: | 12288:3I2fETt7e/a4fj8ltgOfF+ew9GMWnyVLJ9gf1yN8D1tskoS2Q:4METt6C4bwtgc+Z9QOd9m4C7oS2Q |
MALICIOUS
Application was dropped or rewritten from another process
- u.exe (PID: 2376)
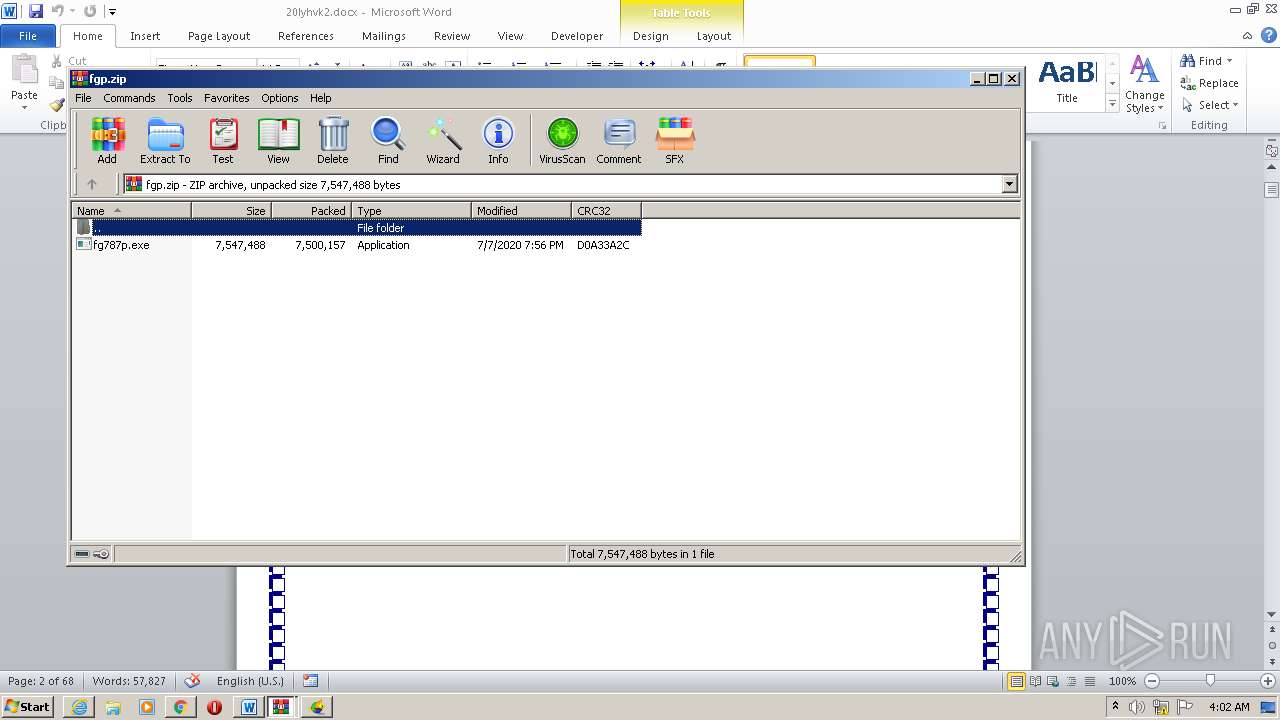
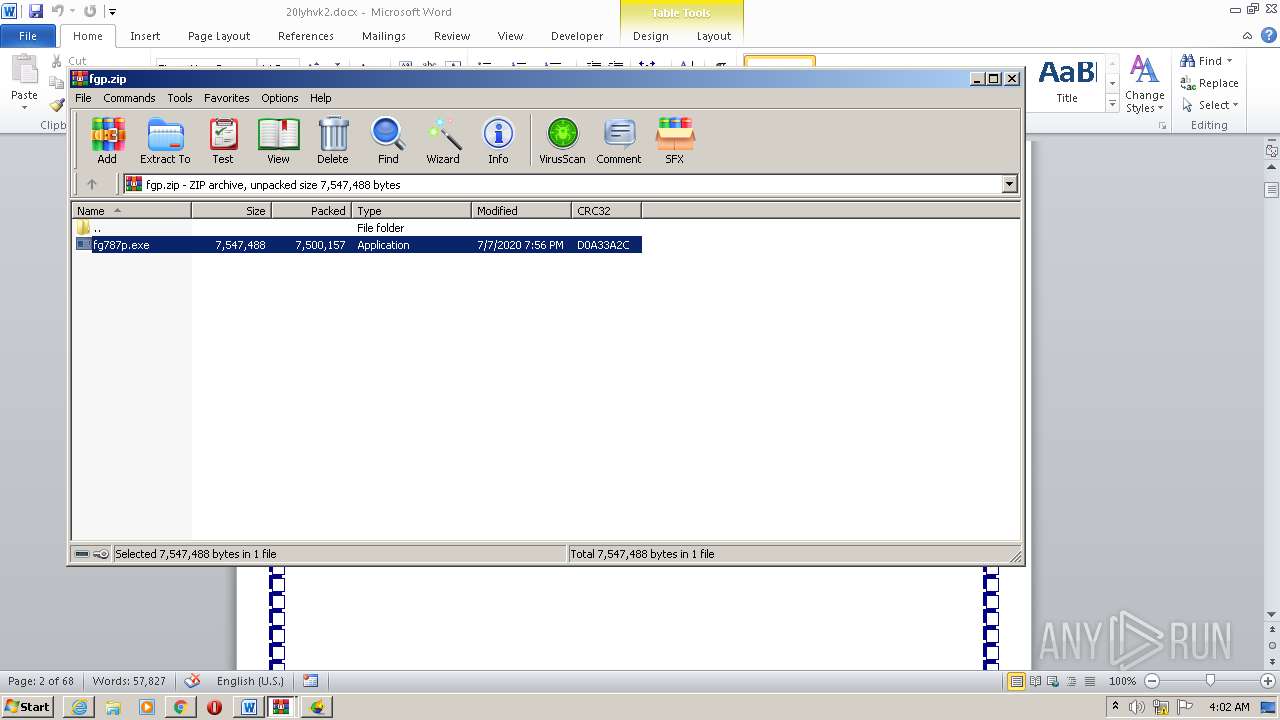
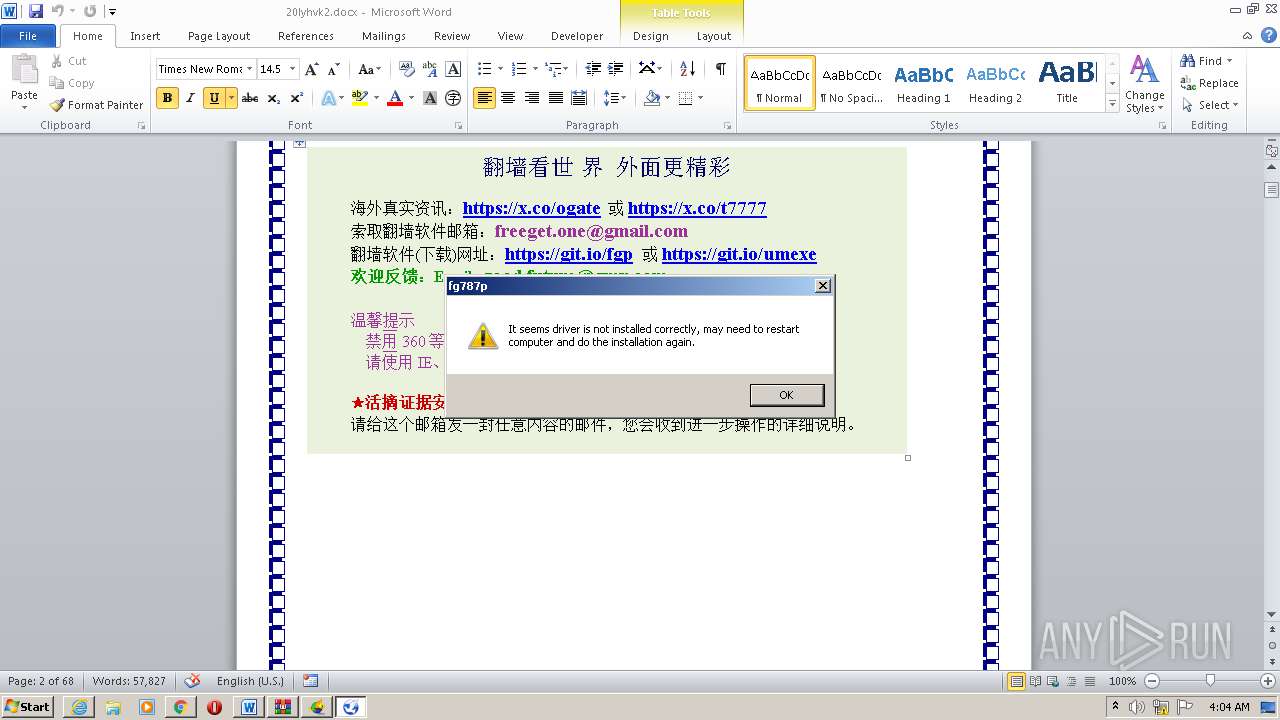
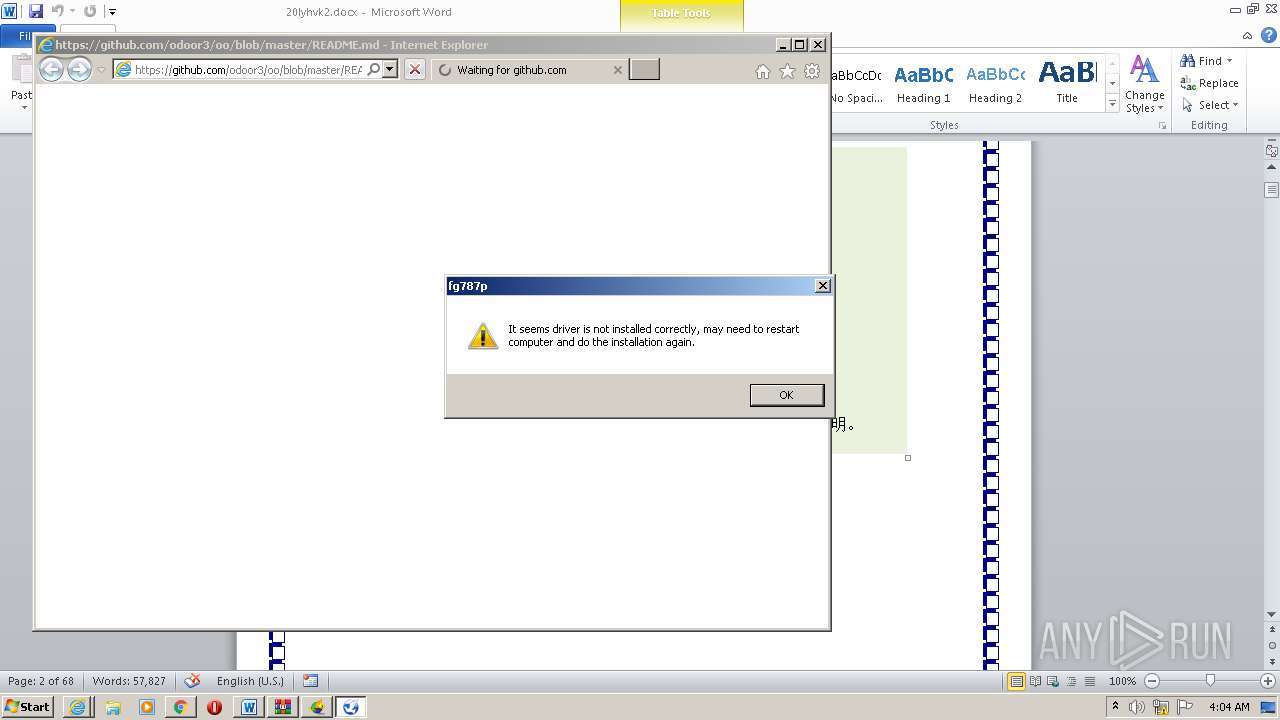
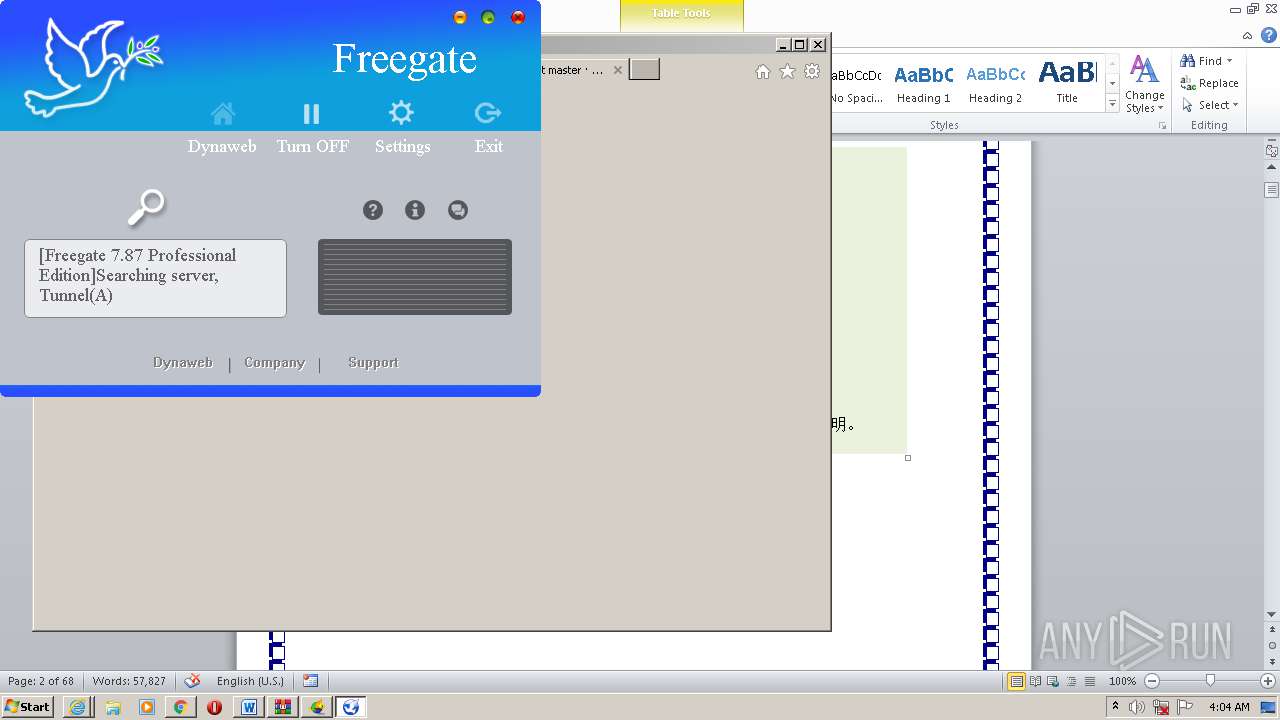
- fg787p.exe (PID: 2624)
- u1902.exe (PID: 1700)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2268)
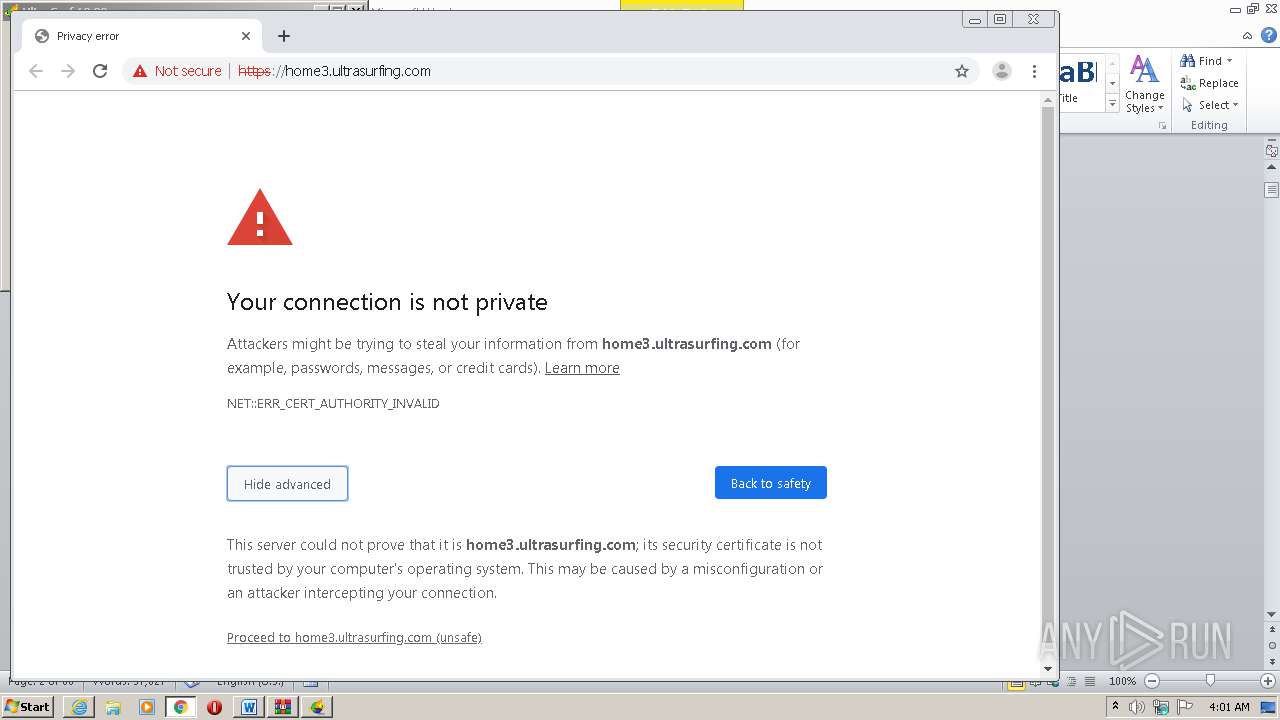
Changes internet zones settings
- u1902.exe (PID: 1700)
Changes settings of System certificates
- certutil.exe (PID: 3124)
- msiexec.exe (PID: 2680)
SUSPICIOUS
Starts Internet Explorer
- WINWORD.EXE (PID: 2268)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4072)
- WinRAR.exe (PID: 3452)
- fg787p.exe (PID: 2624)
- msiexec.exe (PID: 2680)
- netcfg.exe (PID: 340)
- DrvInst.exe (PID: 2984)
- u1902.exe (PID: 1700)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3760)
Reads Internet Cache Settings
- fg787p.exe (PID: 2624)
- DllHost.exe (PID: 3772)
- u1902.exe (PID: 1700)
Starts Microsoft Installer
- fg787p.exe (PID: 2624)
Creates files in the Windows directory
- certutil.exe (PID: 3124)
- DrvInst.exe (PID: 2984)
- netcfg.exe (PID: 340)
Removes files from Windows directory
- certutil.exe (PID: 3124)
- DrvInst.exe (PID: 2984)
- netcfg.exe (PID: 340)
Executed via COM
- DrvInst.exe (PID: 2984)
- DllHost.exe (PID: 3772)
Creates files in the driver directory
- DrvInst.exe (PID: 2984)
- netcfg.exe (PID: 340)
Executed as Windows Service
- vssvc.exe (PID: 3428)
Adds / modifies Windows certificates
- msiexec.exe (PID: 2680)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2268)
Reads Internet Cache Settings
- WINWORD.EXE (PID: 2268)
- iexplore.exe (PID: 2212)
- iexplore.exe (PID: 1508)
- iexplore.exe (PID: 3336)
- iexplore.exe (PID: 2844)
Changes internet zones settings
- iexplore.exe (PID: 2212)
Reads settings of System Certificates
- WINWORD.EXE (PID: 2268)
- chrome.exe (PID: 3804)
- iexplore.exe (PID: 2212)
- iexplore.exe (PID: 1508)
Creates files in the user directory
- WINWORD.EXE (PID: 2268)
- iexplore.exe (PID: 2212)
- iexplore.exe (PID: 2844)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2212)
Application launched itself
- chrome.exe (PID: 3760)
- iexplore.exe (PID: 2212)
- msiexec.exe (PID: 2680)
Reads the hosts file
- chrome.exe (PID: 3804)
- chrome.exe (PID: 3760)
Creates files in the program directory
- msiexec.exe (PID: 2680)
Adds / modifies Windows certificates
- DrvInst.exe (PID: 2984)
- iexplore.exe (PID: 2212)
Changes settings of System certificates
- DrvInst.exe (PID: 2984)
- iexplore.exe (PID: 2212)
Searches for installed software
- DrvInst.exe (PID: 2984)
Reads internet explorer settings
- WINWORD.EXE (PID: 2268)
- iexplore.exe (PID: 3456)
- iexplore.exe (PID: 2844)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3428)
Creates a software uninstall entry
- msiexec.exe (PID: 2680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:07:12 19:42:11 |
| ZipCRC: | 0x24cd2445 |
| ZipCompressedSize: | 475 |
| ZipUncompressedSize: | 979 |
| ZipFileName: | docProps/app.xml |
XML
| Template: | Normal |
|---|---|
| TotalEditTime: | 1.8 hours |
| Pages: | 65 |
| Words: | 9018 |
| Characters: | 51409 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 428 |
| Paragraphs: | 120 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 60307 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| LastModifiedBy: | Anxin Lin |
| RevisionNumber: | 55 |
| CreateDate: | 2020:07:04 23:51:00Z |
| ModifyDate: | 2020:07:07 03:39:00Z |
XMP
| Creator: | Irene |
|---|
Total processes
100
Monitored processes
54
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 340 | "C:\Windows\system32\netcfg.exe" -v -l "C:\Program Files\Windows Packet Filter\drivers\ndisrd_lwf.inf" -c s -i nt_ndisrd | C:\Windows\system32\netcfg.exe | MsiExec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WinPE network installer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | C:\Windows\system32\MsiExec.exe -Embedding D0C1FCD0592E031BAA5FDD276E96BA27 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,6971488429021650105,3900874987105638998,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4580304189386257354 --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4260 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,6971488429021650105,3900874987105638998,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17548726521316444015 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3872 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1508 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2212 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
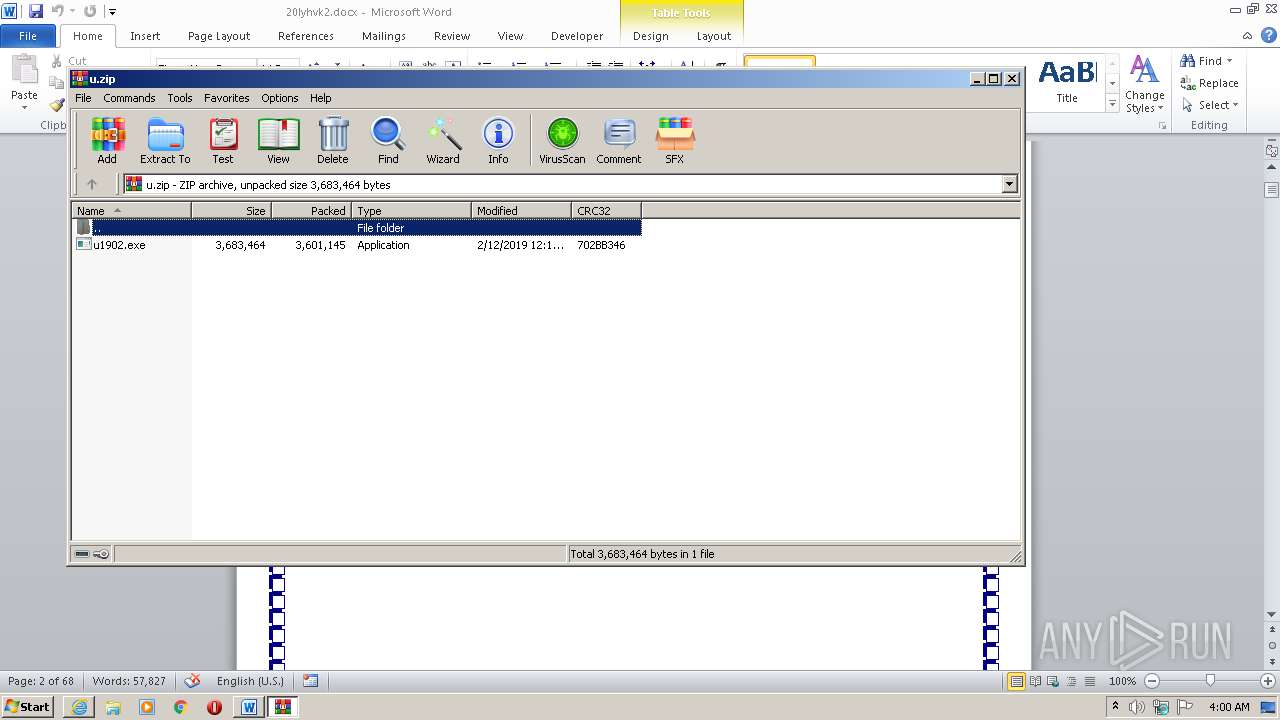
| 1700 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.8160\u1902.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4072.8160\u1902.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1044,6971488429021650105,3900874987105638998,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1031724019740052778 --mojo-platform-channel-handle=3832 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,6971488429021650105,3900874987105638998,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2287885617531399150 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4780 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
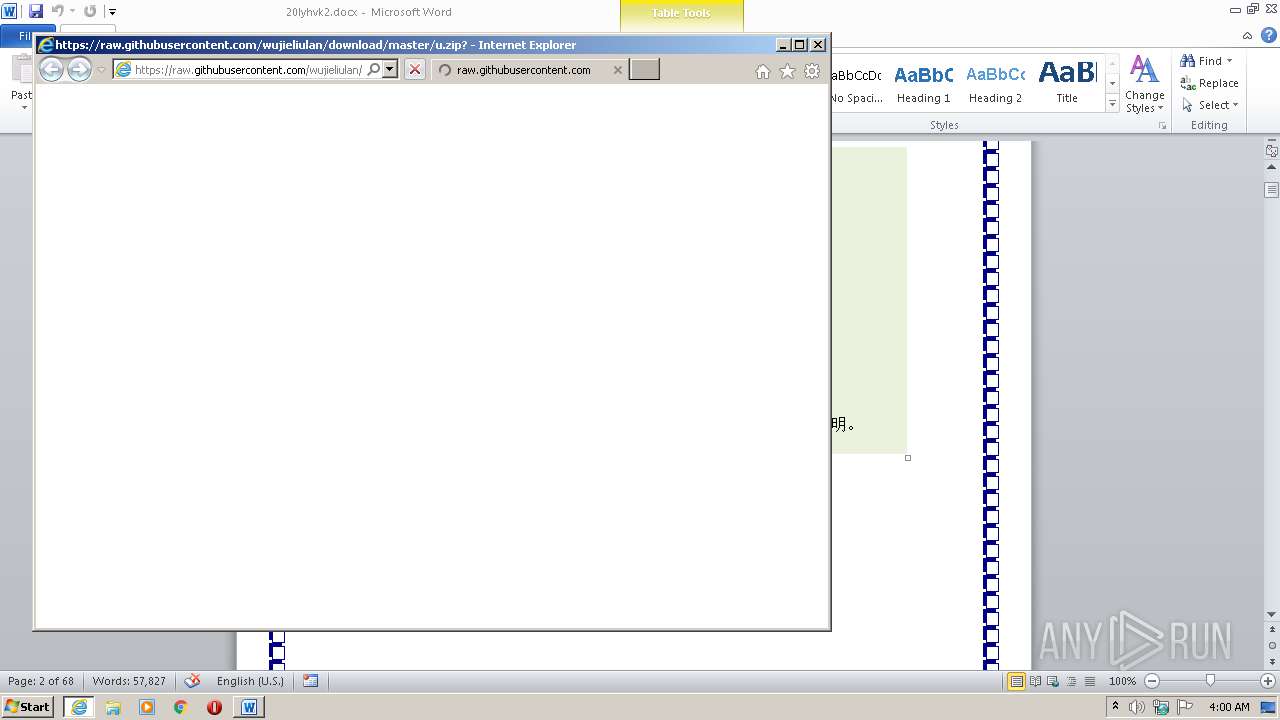
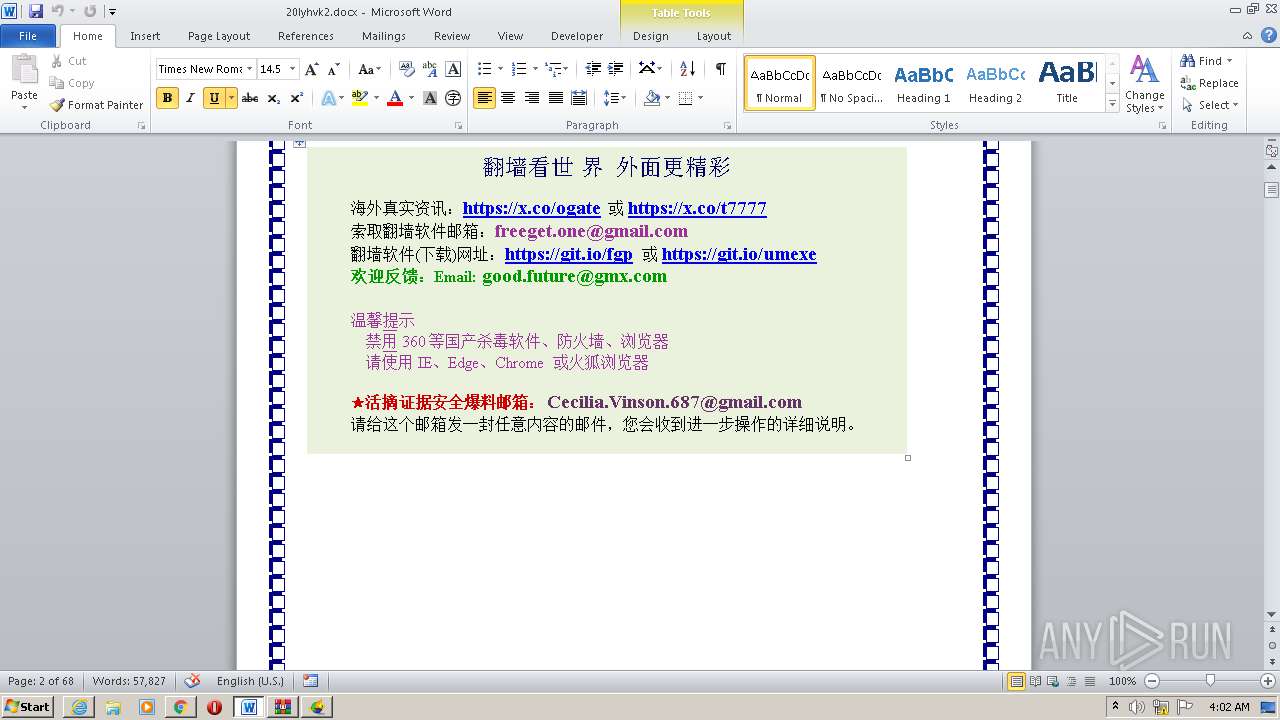
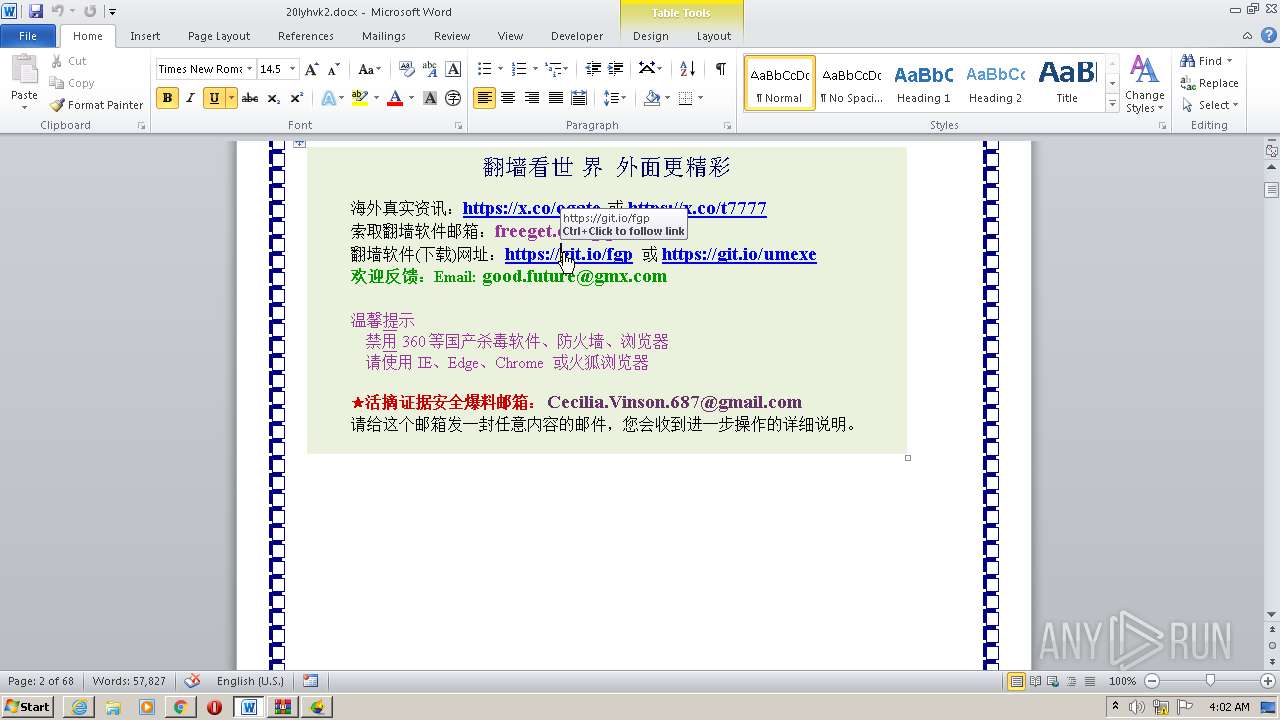
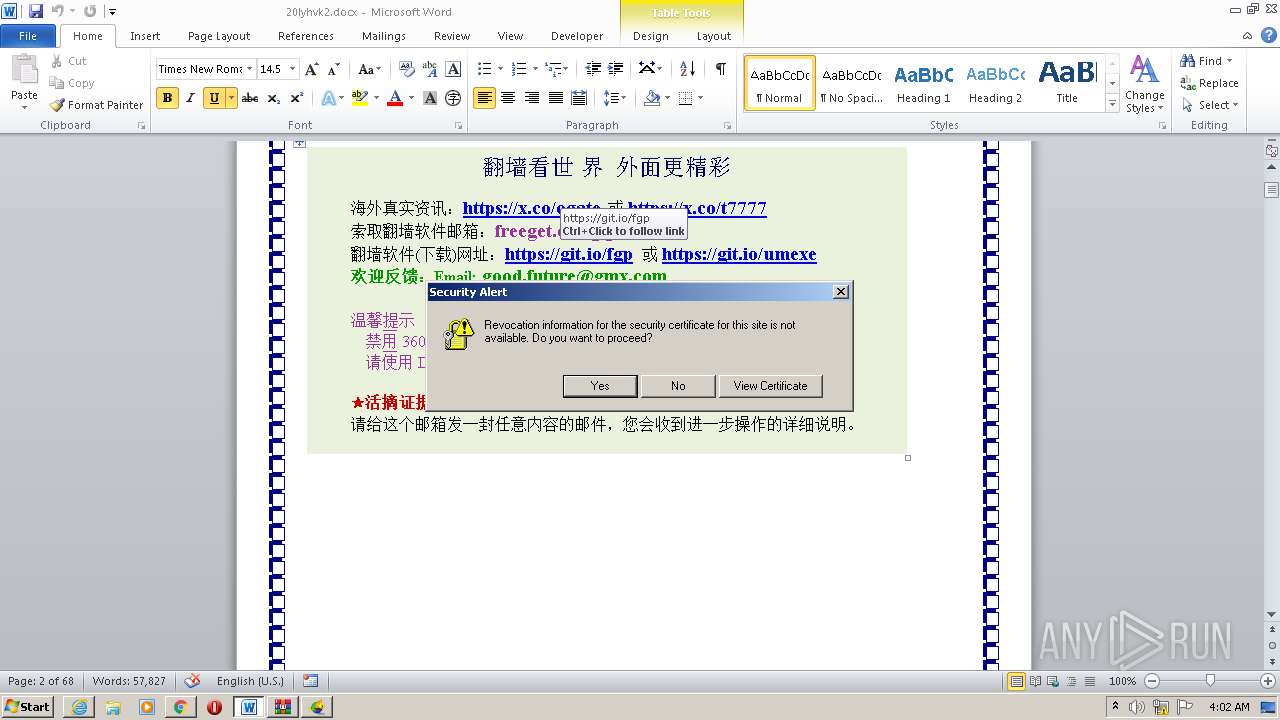
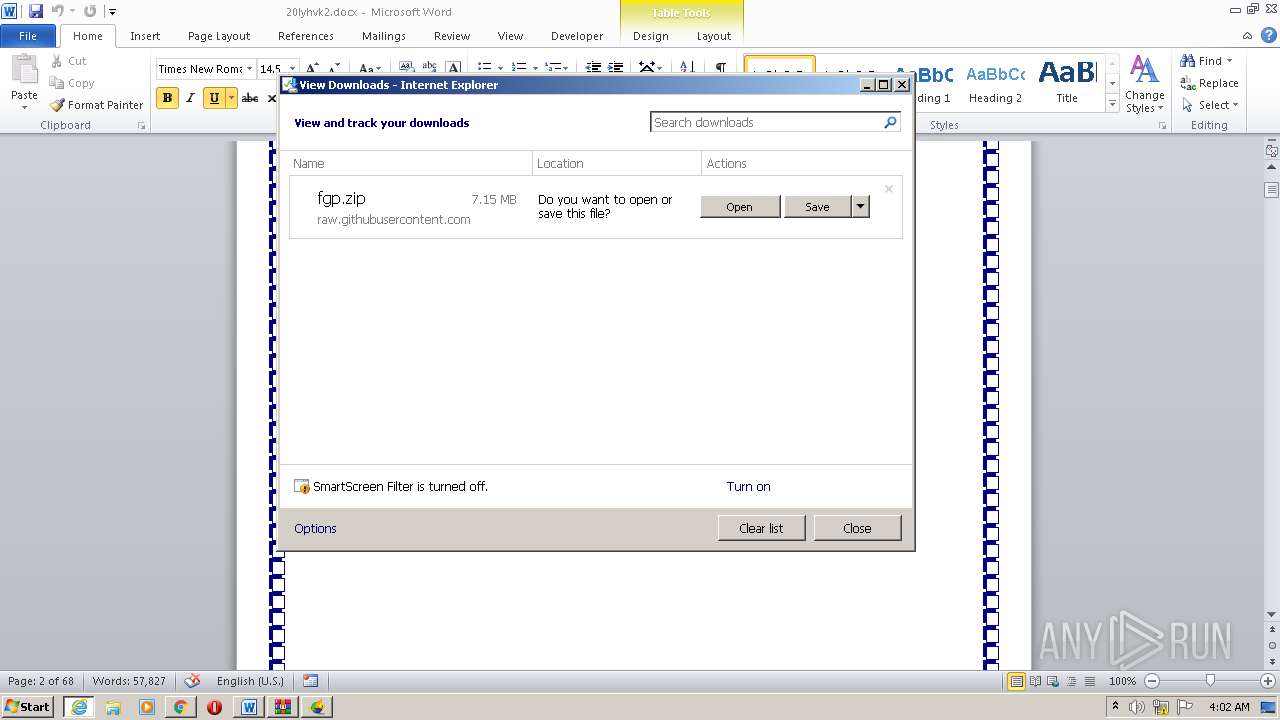
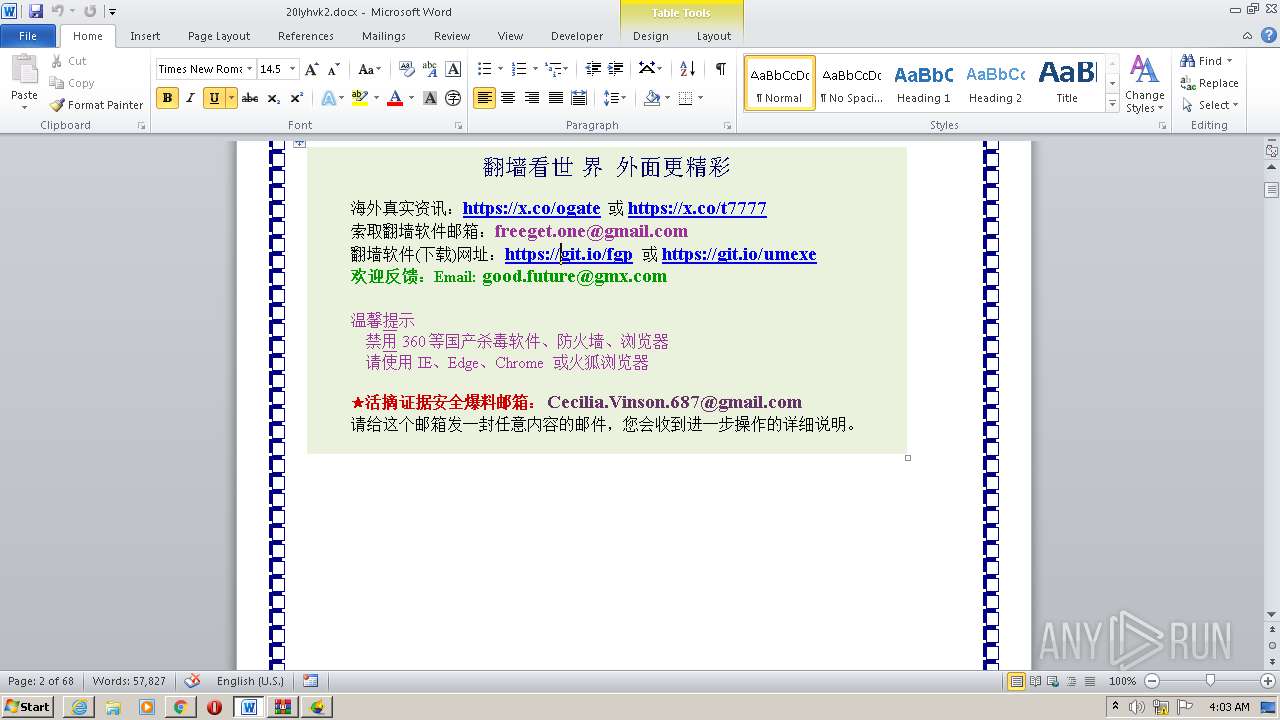
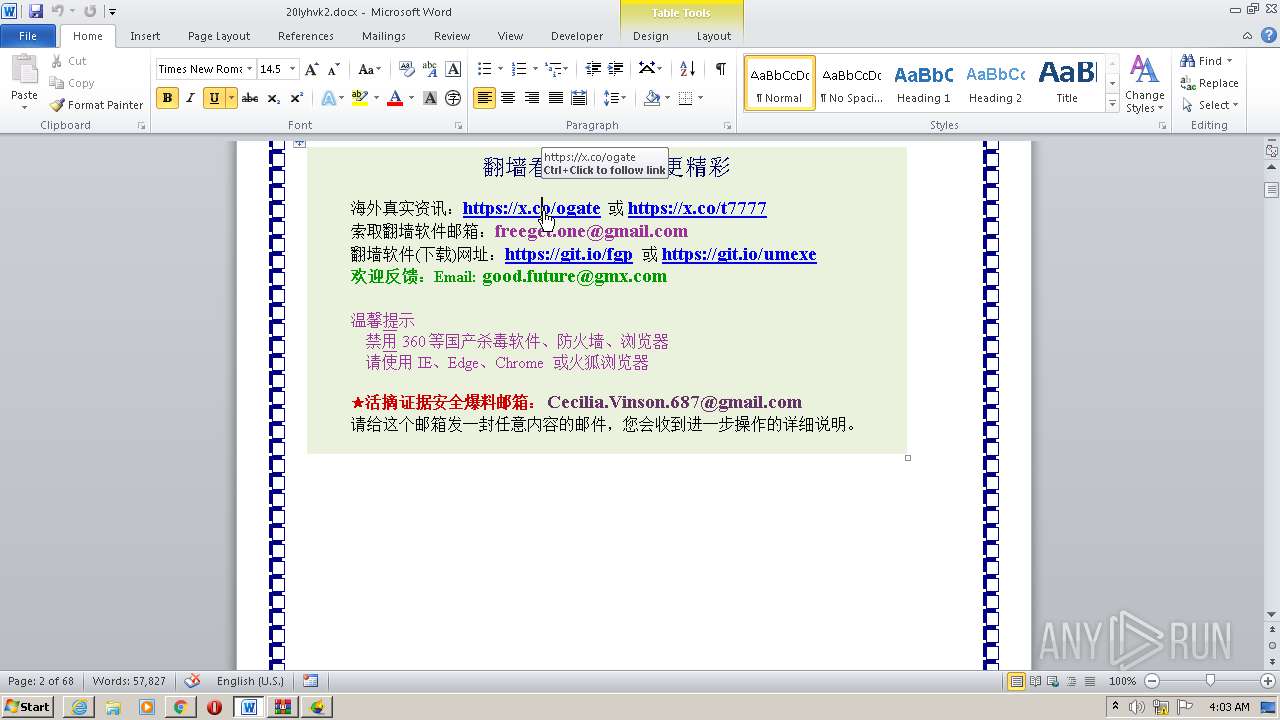
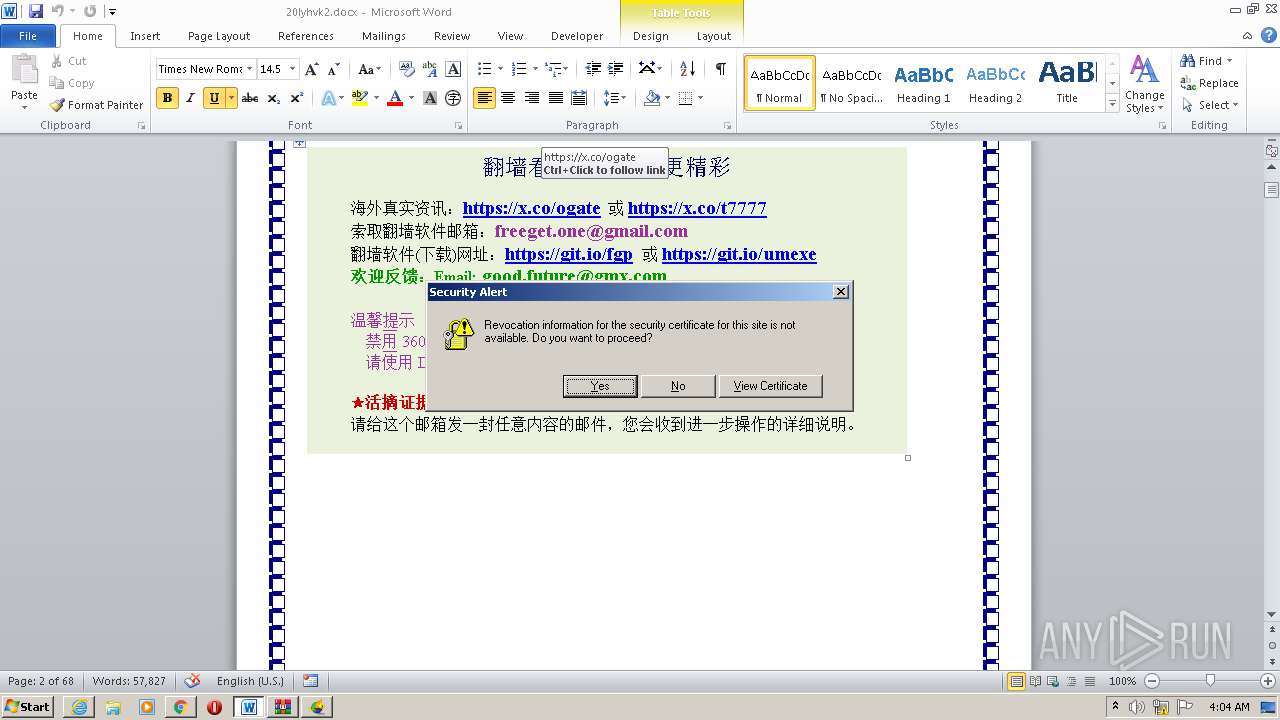
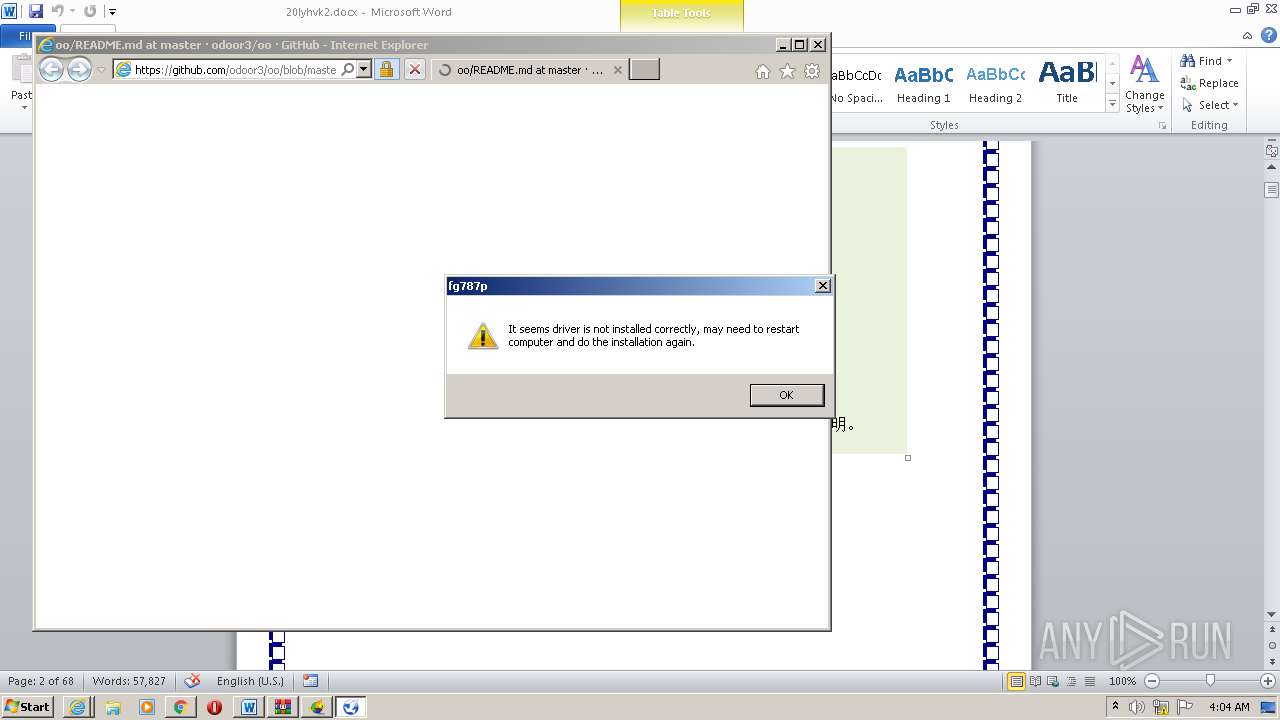
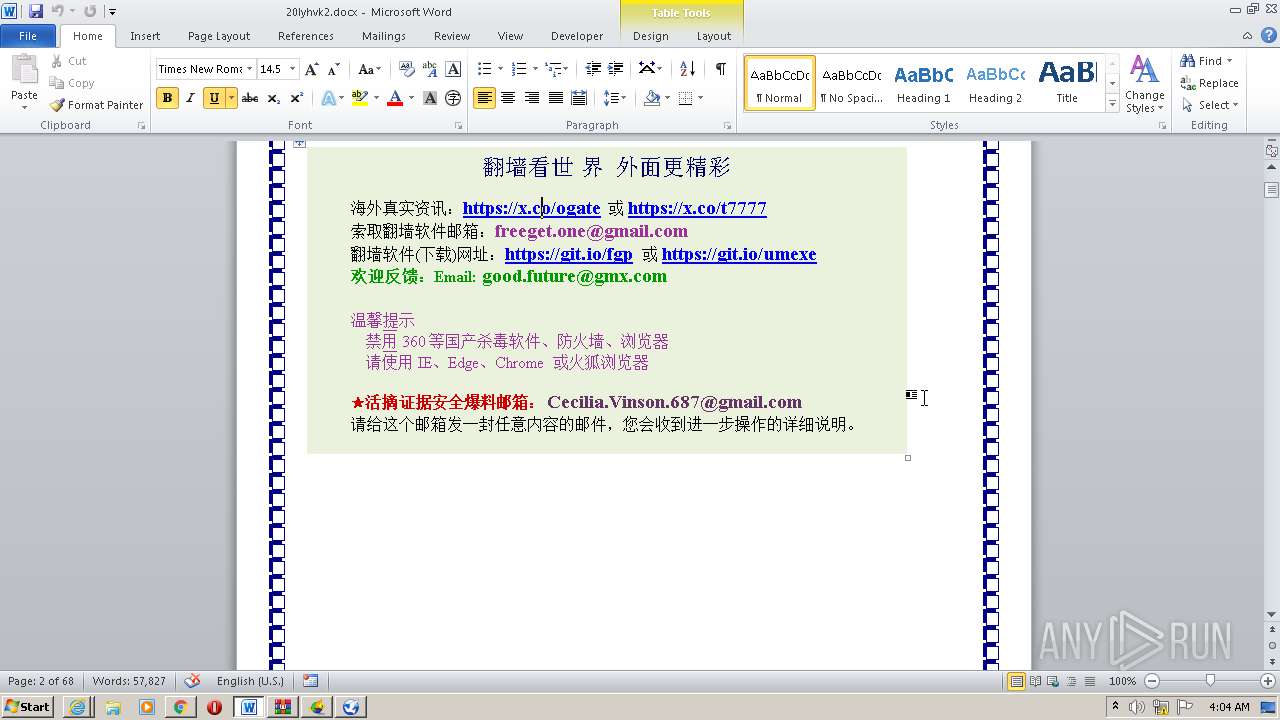
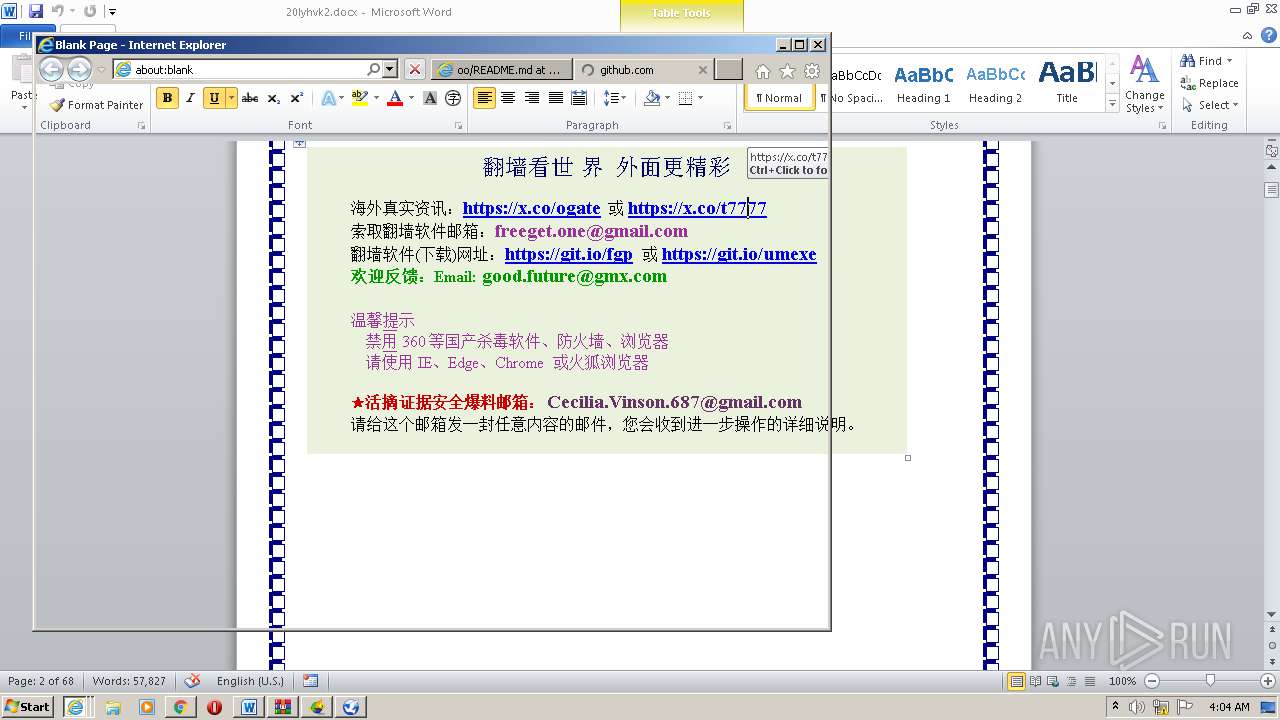
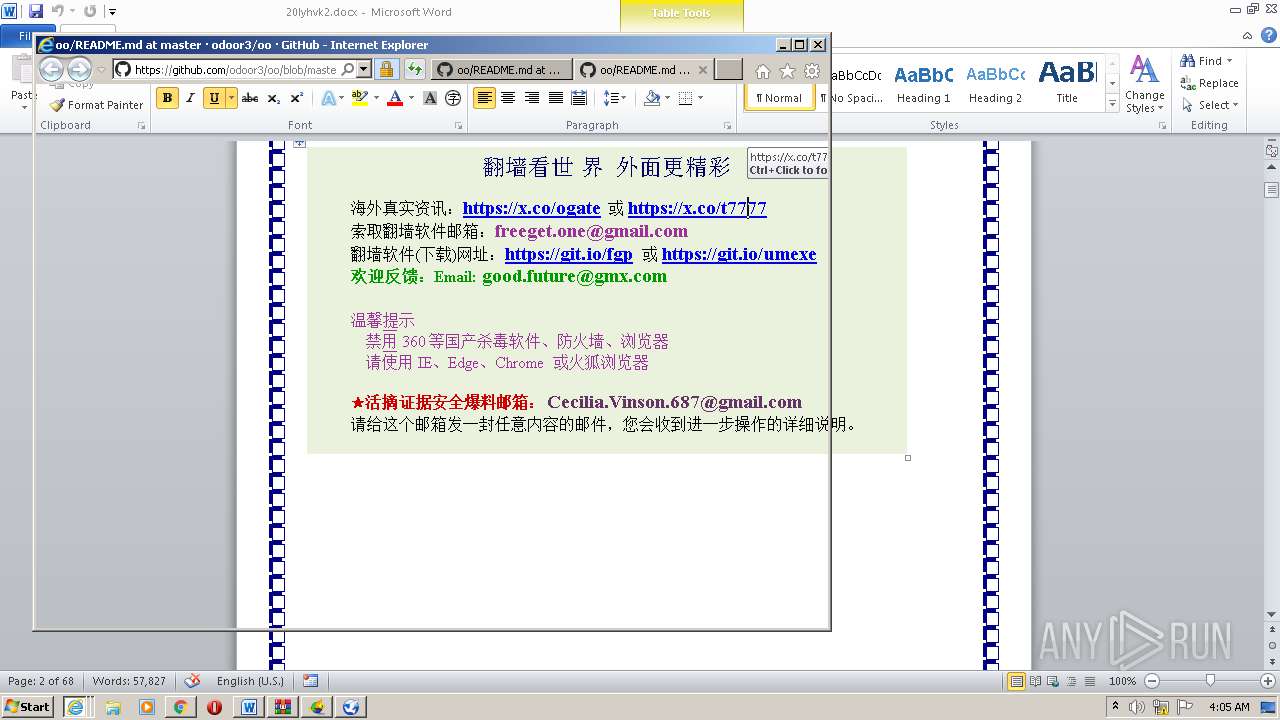
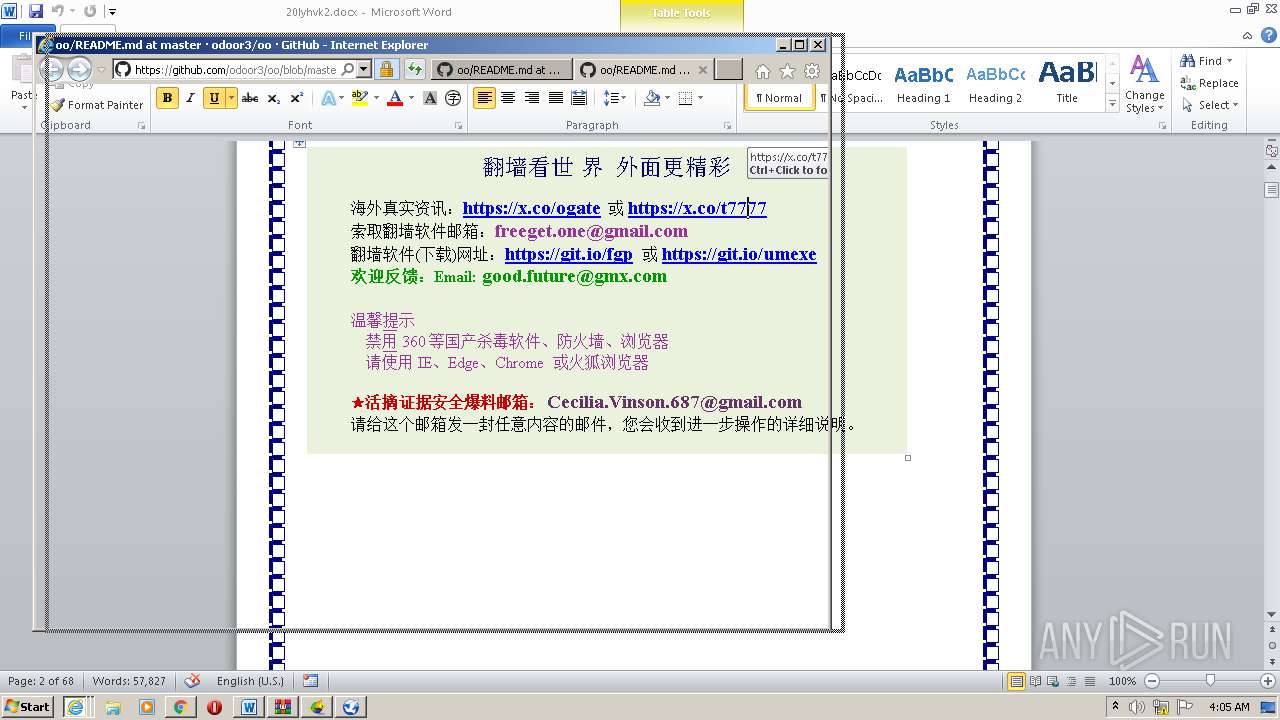
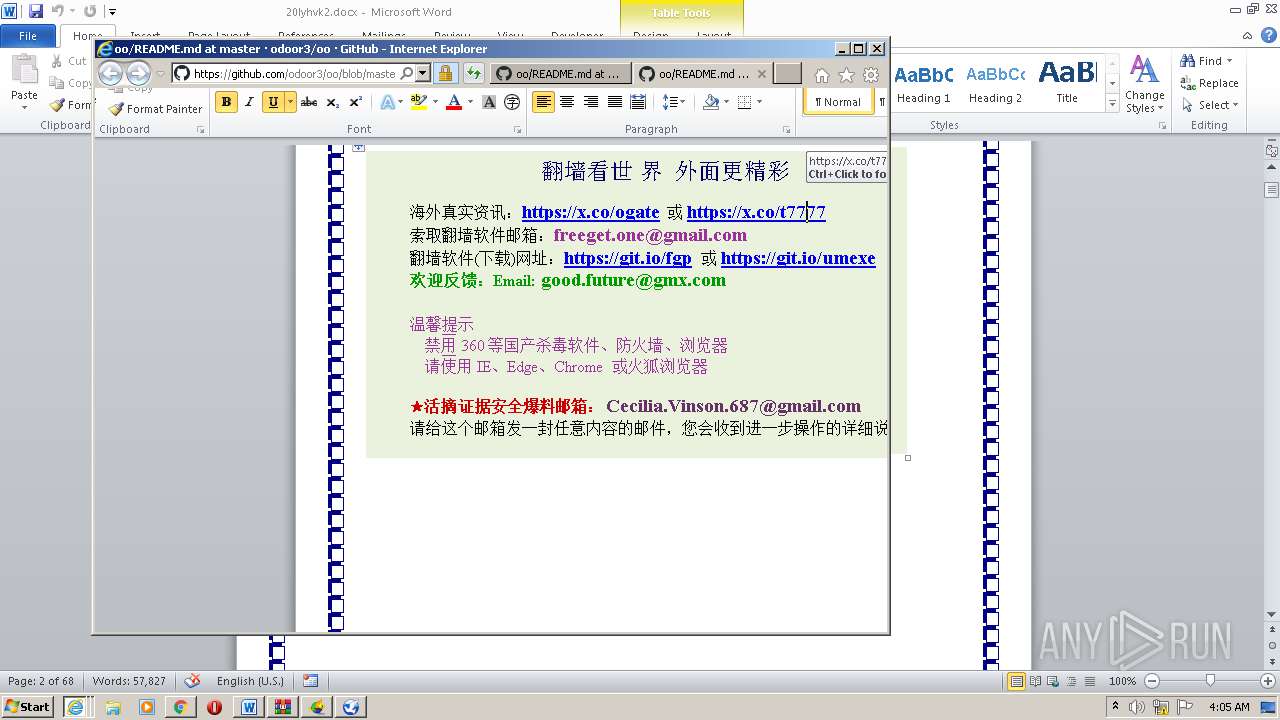
| 1816 | "C:\Program Files\Internet Explorer\iexplore.exe" https://raw.githubusercontent.com/freegate-release/website/gh-pages/files/fgp.zip | C:\Program Files\Internet Explorer\iexplore.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,6971488429021650105,3900874987105638998,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4735728212494482450 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2592 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
13 838
Read events
4 713
Write events
6 910
Delete events
2 215
Modification events
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | a=9 |
Value: 613D3900DC080000010000000000000000000000 | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2268) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
13
Suspicious files
142
Text files
413
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2268 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7541.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2268 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CabC314.tmp | — | |
MD5:— | SHA256:— | |||
| 2268 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\TarC315.tmp | — | |
MD5:— | SHA256:— | |||
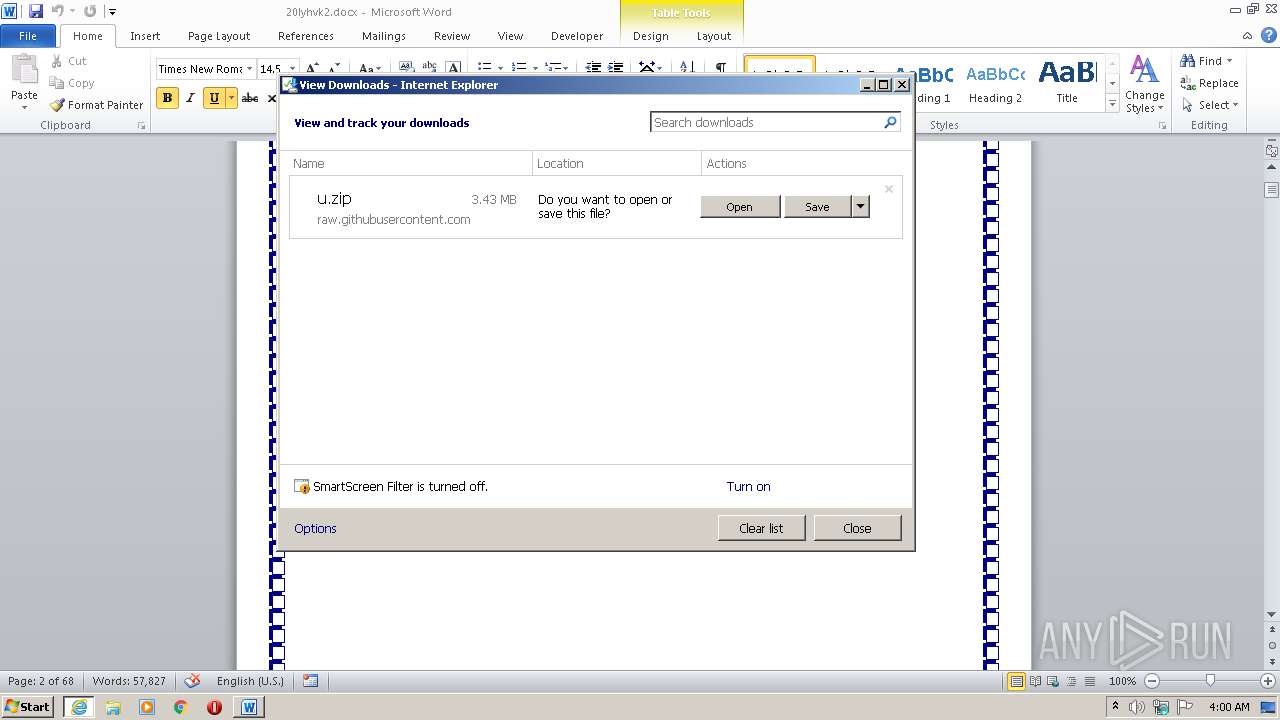
| 2268 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\u[1].zip | — | |
MD5:— | SHA256:— | |||
| 1508 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabCD35.tmp | — | |
MD5:— | SHA256:— | |||
| 1508 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabCD36.tmp | — | |
MD5:— | SHA256:— | |||
| 1508 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarCD38.tmp | — | |
MD5:— | SHA256:— | |||
| 1508 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarCD37.tmp | — | |
MD5:— | SHA256:— | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF42990D098C0FB127.TMP | — | |
MD5:— | SHA256:— | |||
| 2212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\u.zip.hh7zvw8.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
10
DNS requests
23
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2268 | WINWORD.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
2268 | WINWORD.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEA7DhnK6vbZVWuDNUnGhjDo%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2268 | WINWORD.EXE | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2268 | WINWORD.EXE | 151.101.0.133:443 | raw.githubusercontent.com | Fastly | US | malicious |
1508 | iexplore.exe | 151.101.0.133:443 | raw.githubusercontent.com | Fastly | US | malicious |
2376 | u.exe | 152.199.19.161:443 | do.skype.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2376 | u.exe | 72.52.87.179:443 | — | Hurricane Electric, Inc. | US | suspicious |
2376 | u.exe | 45.95.98.179:443 | — | — | — | unknown |
2268 | WINWORD.EXE | 3.230.235.205:443 | git.io | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
git.io |
| shared |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
do.skype.com |
| whitelisted |
github.com |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars0.githubusercontent.com |
| whitelisted |
avatars1.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
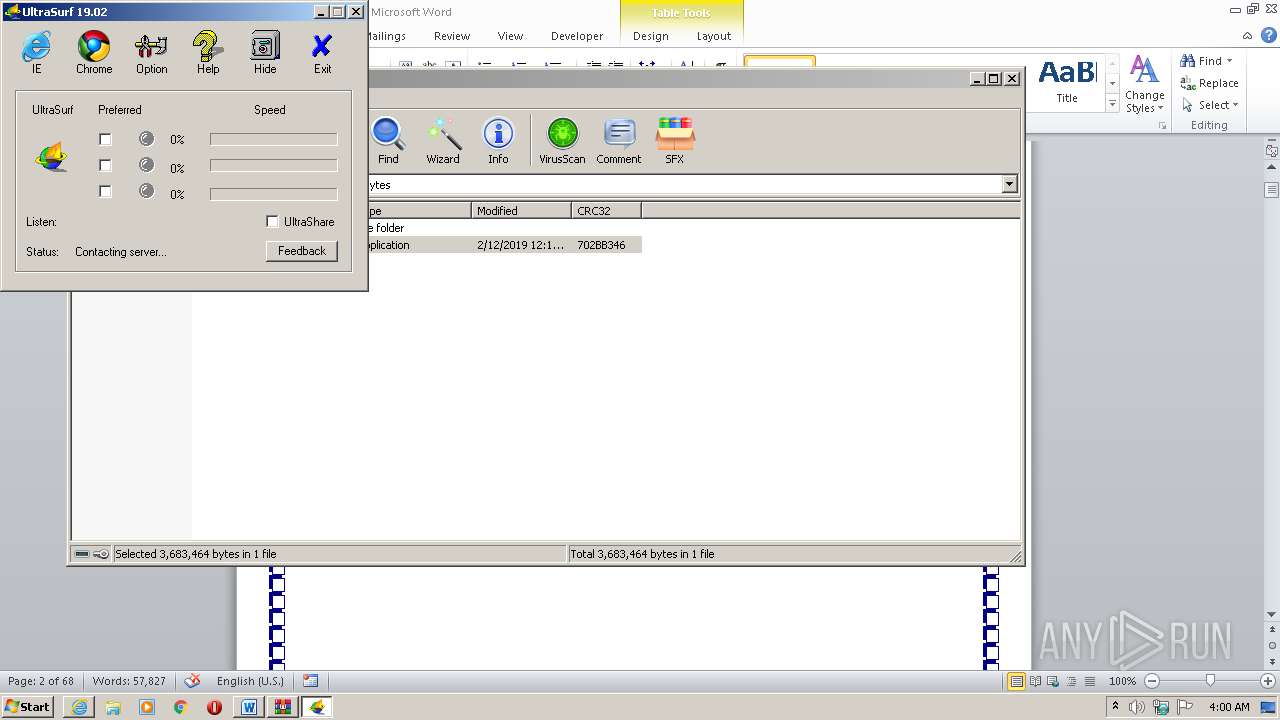
2376 | u.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Possible JA3 UltraSurf Proxy Anonymizer |
2376 | u.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Possible JA3 UltraSurf Proxy Anonymizer |
2376 | u.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] Possible JA3 UltraSurf Proxy Anonymizer |