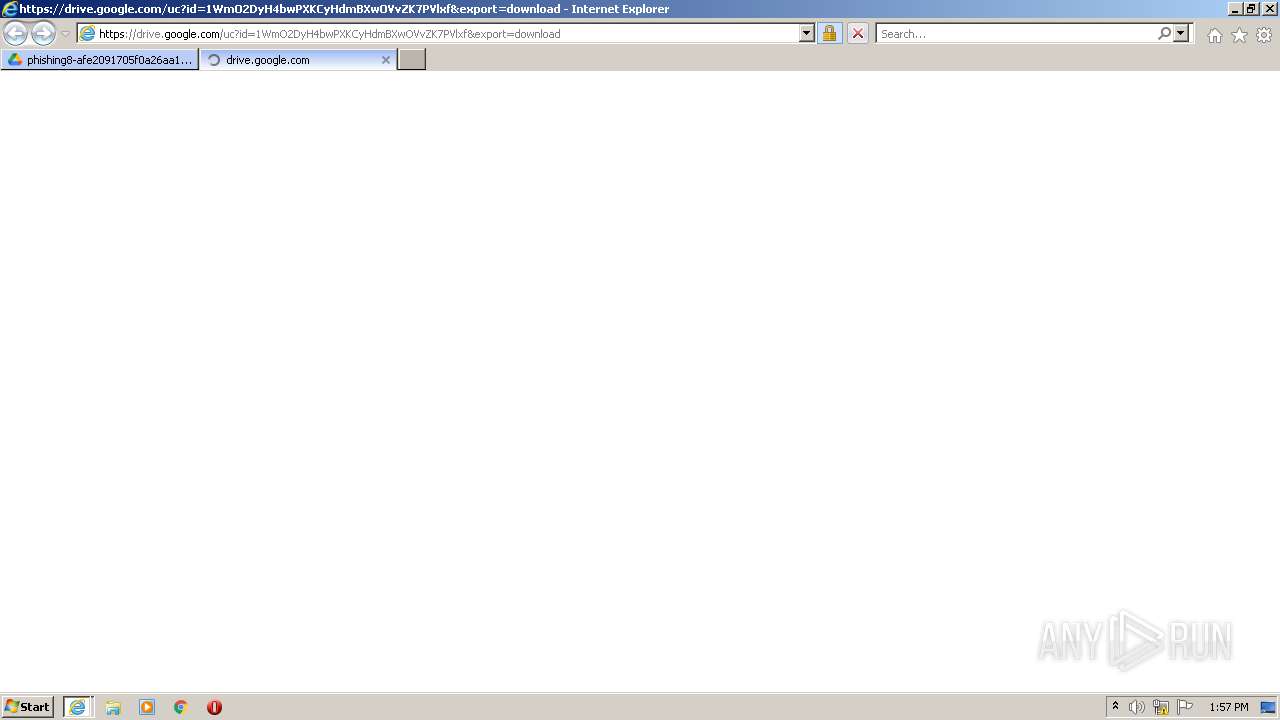
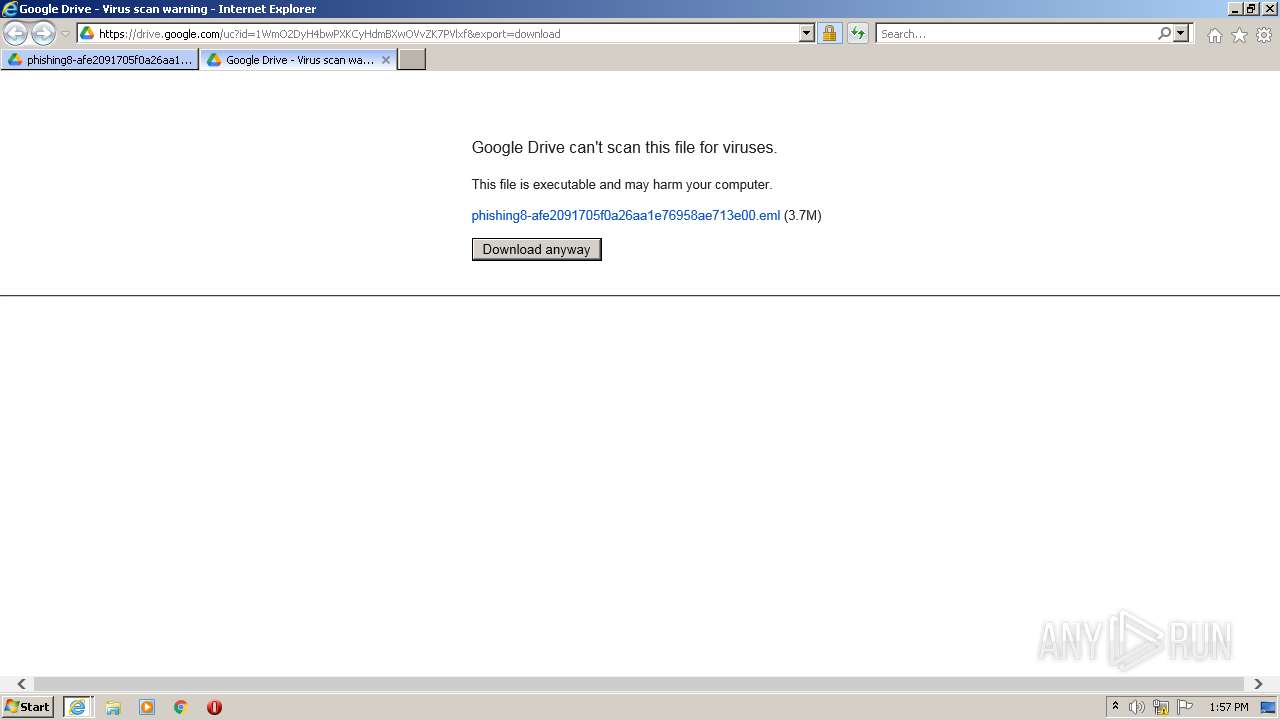
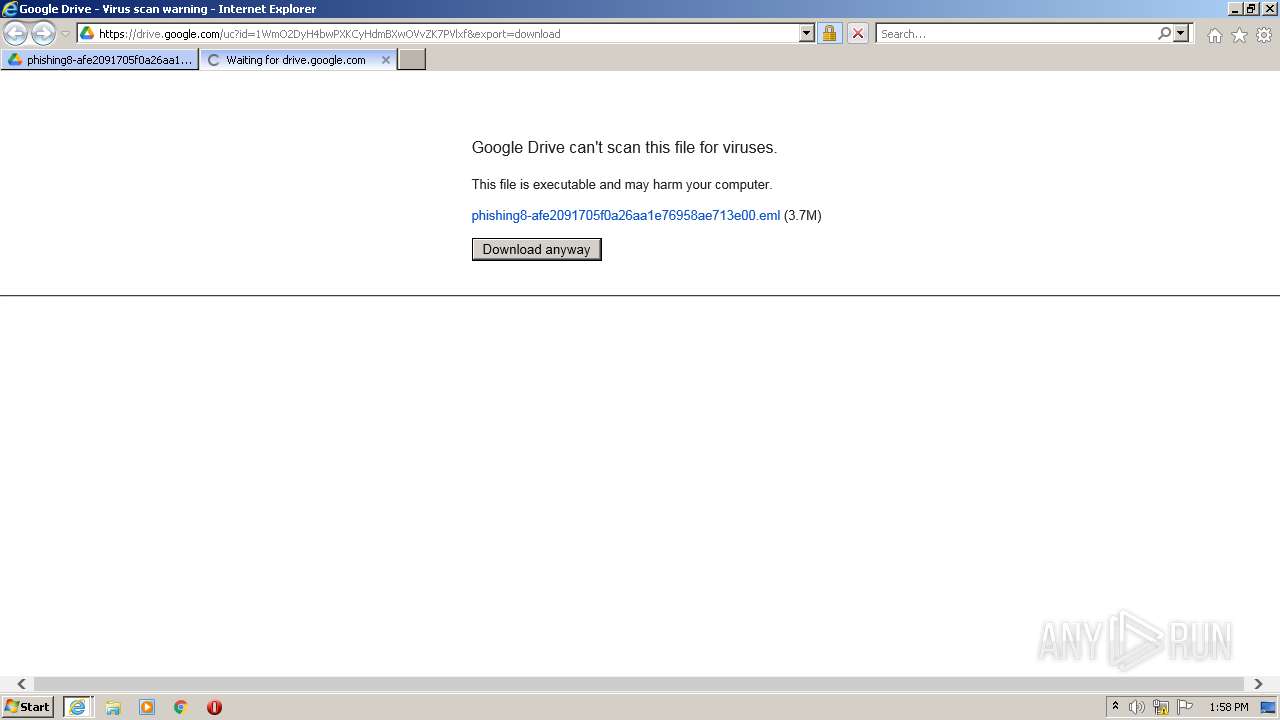
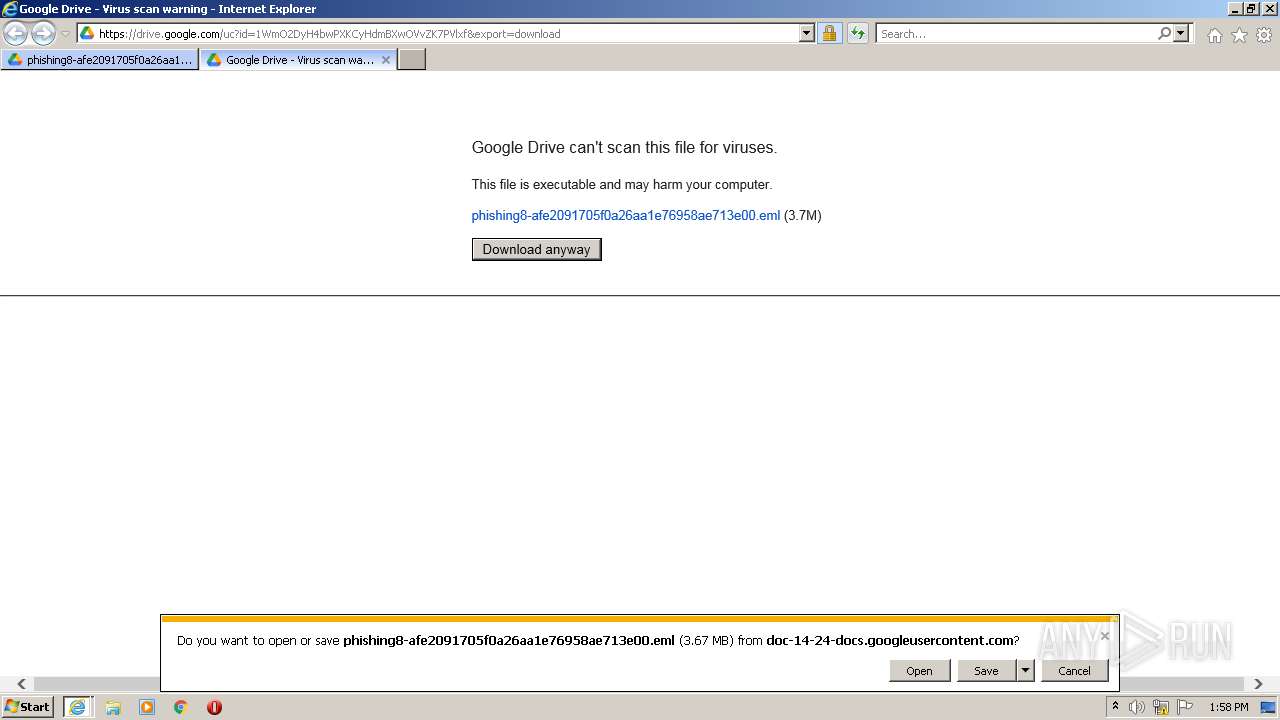
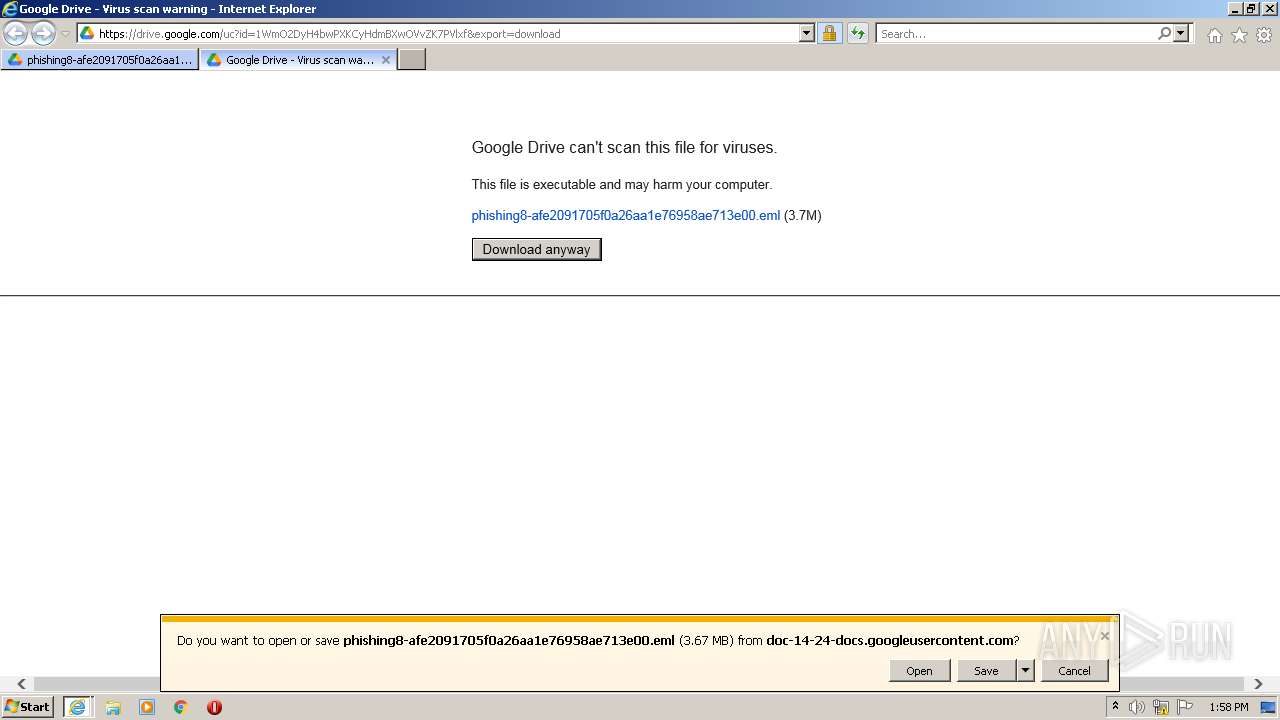
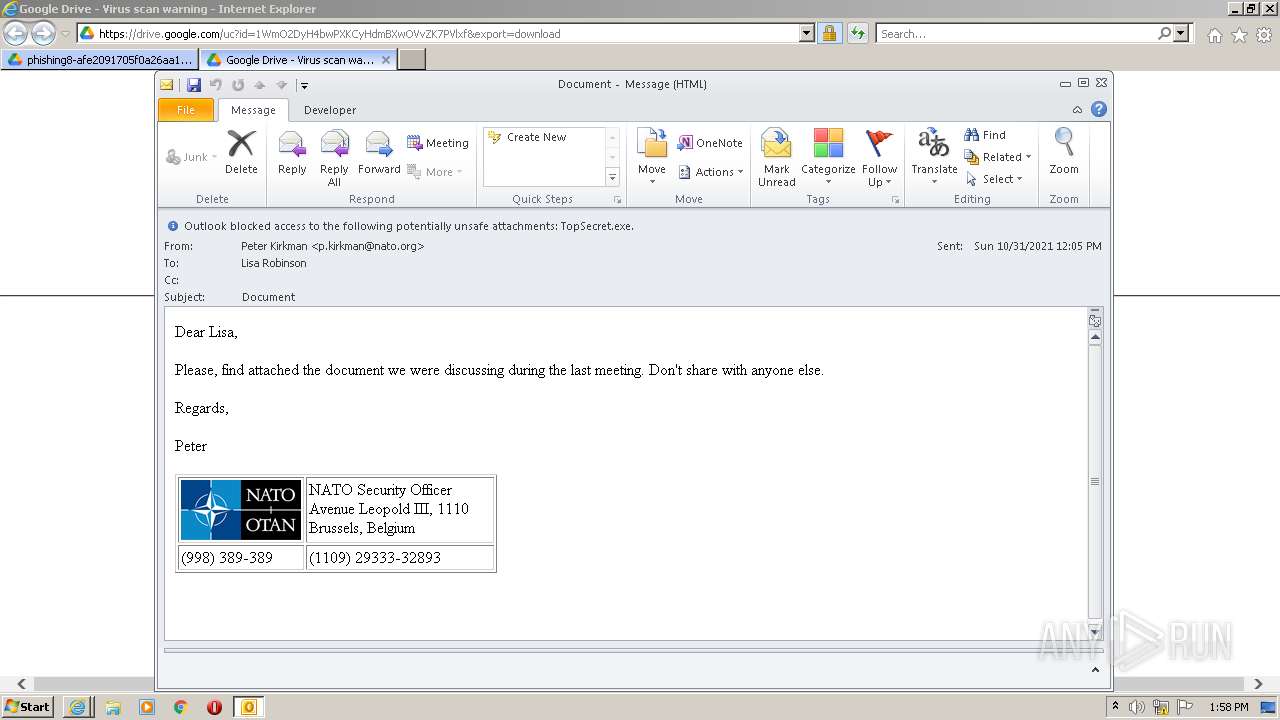
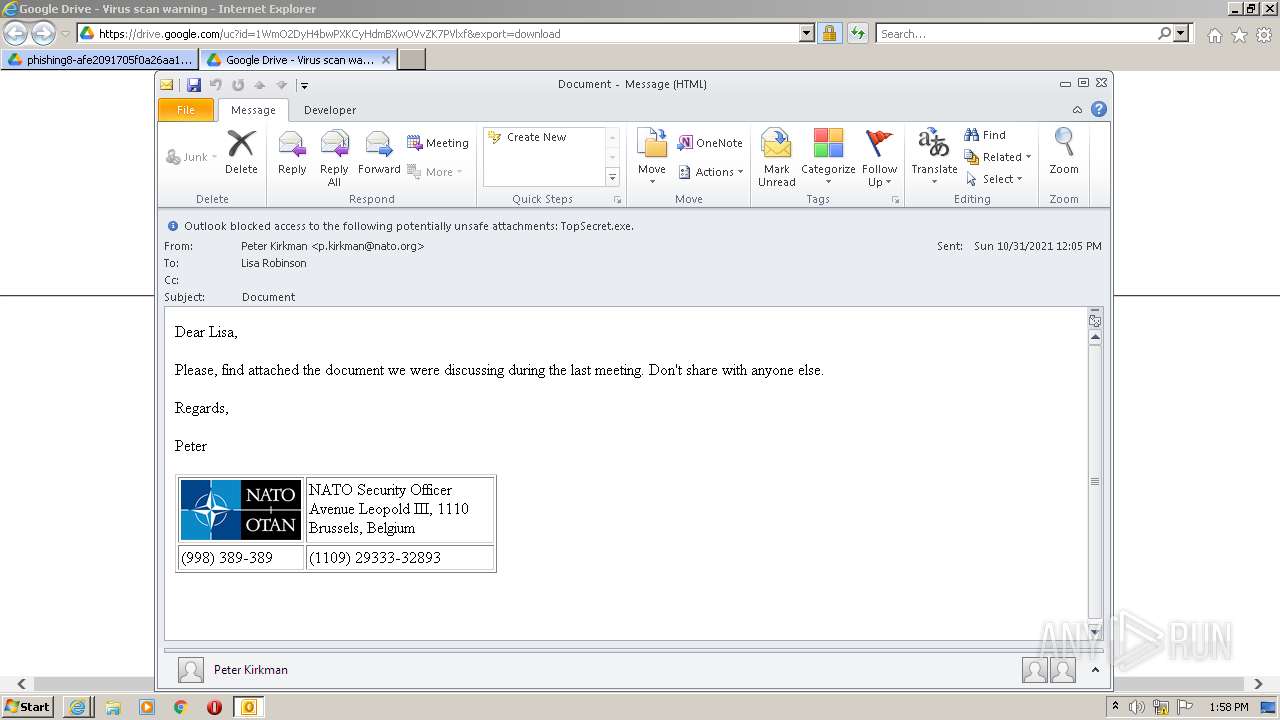
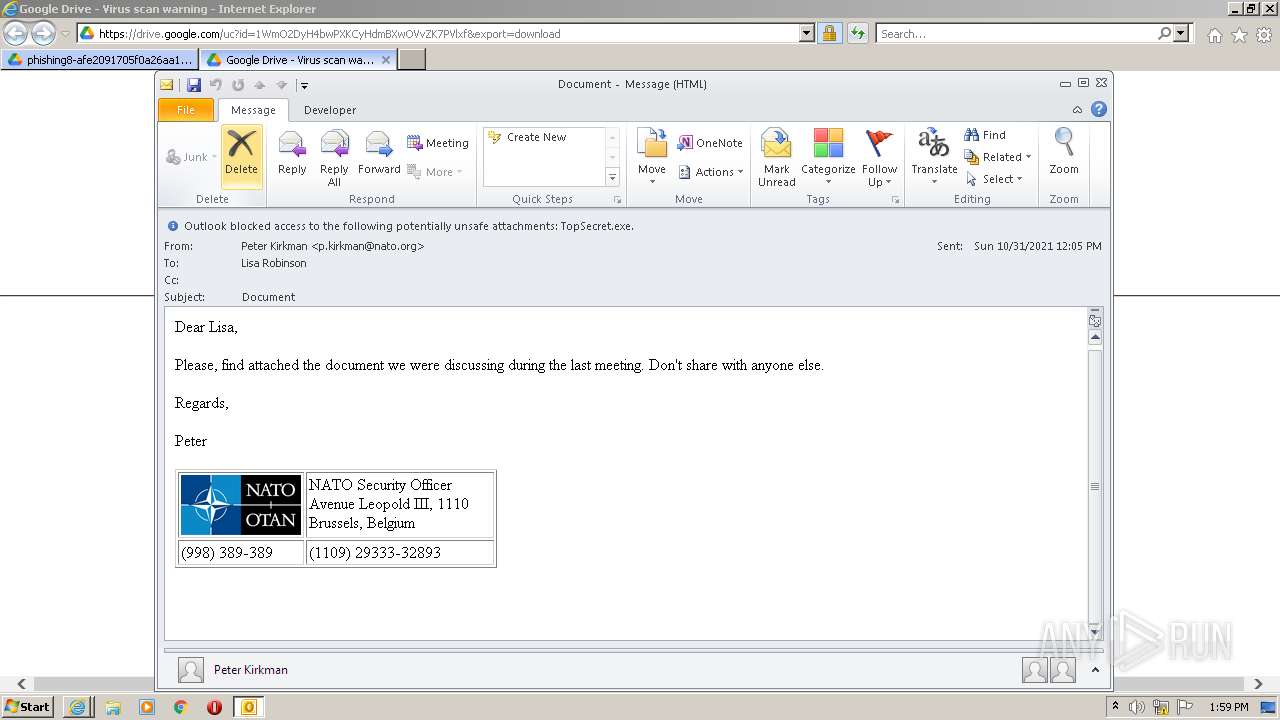
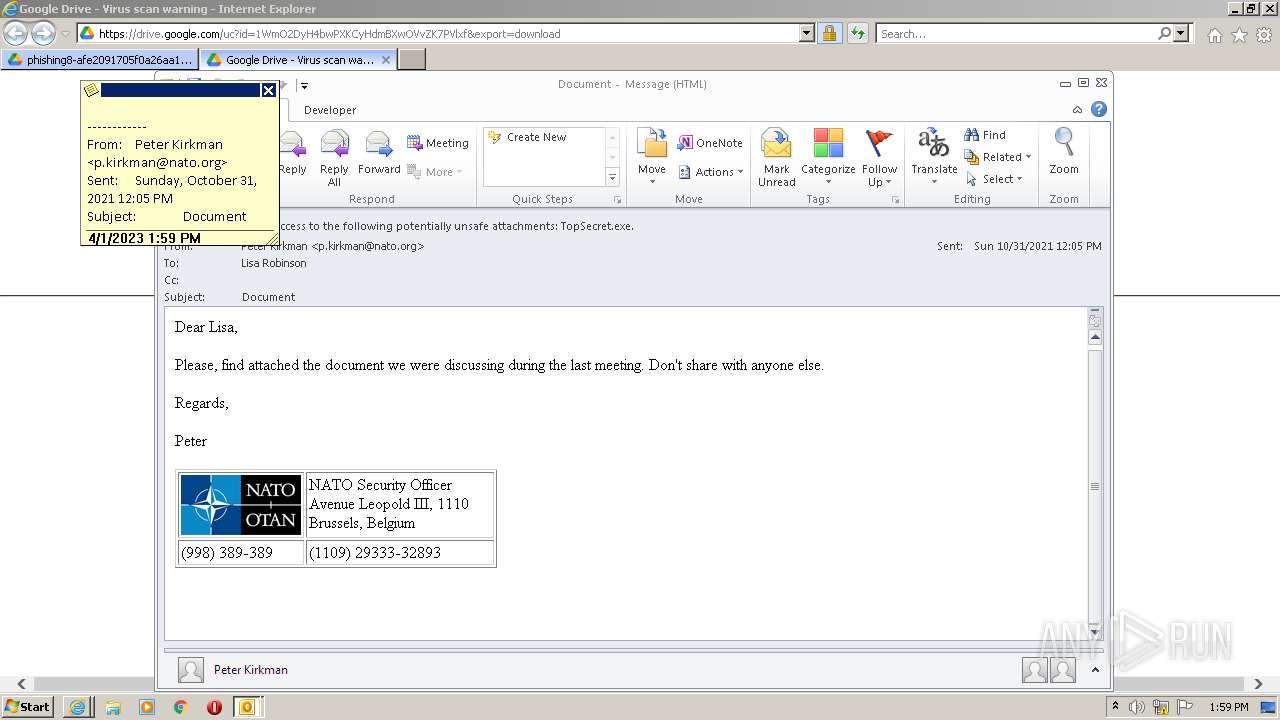
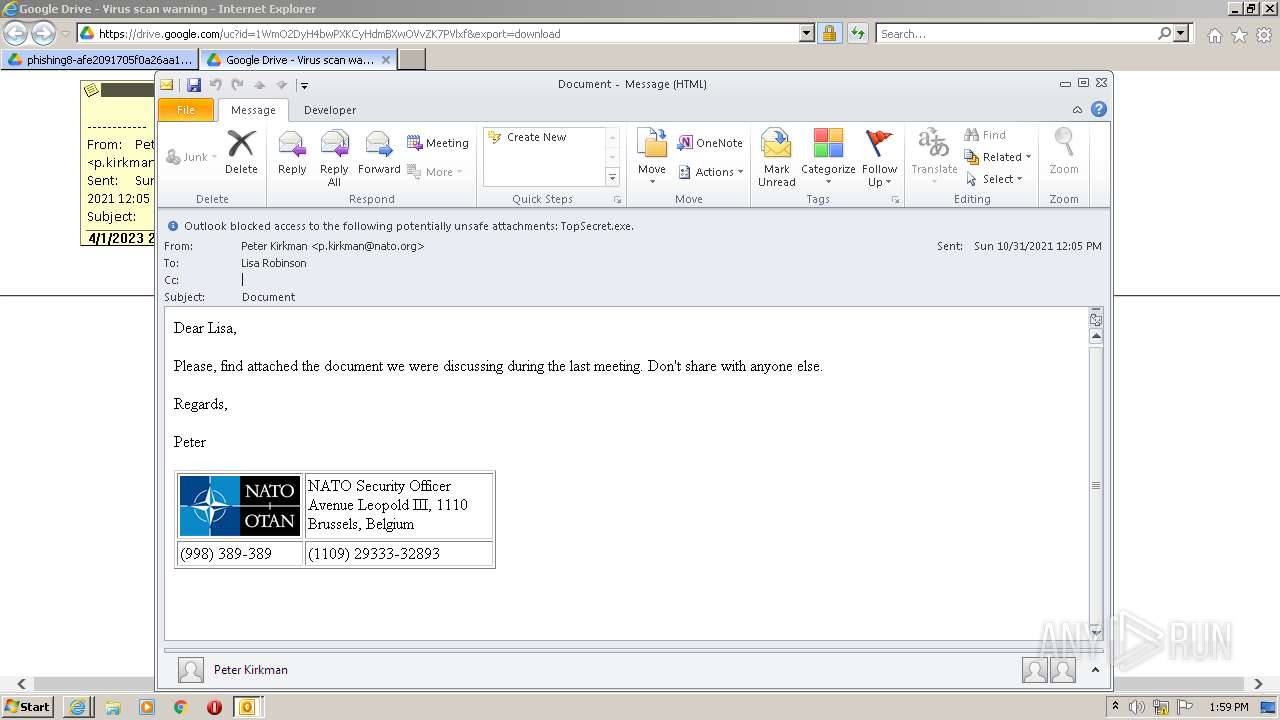
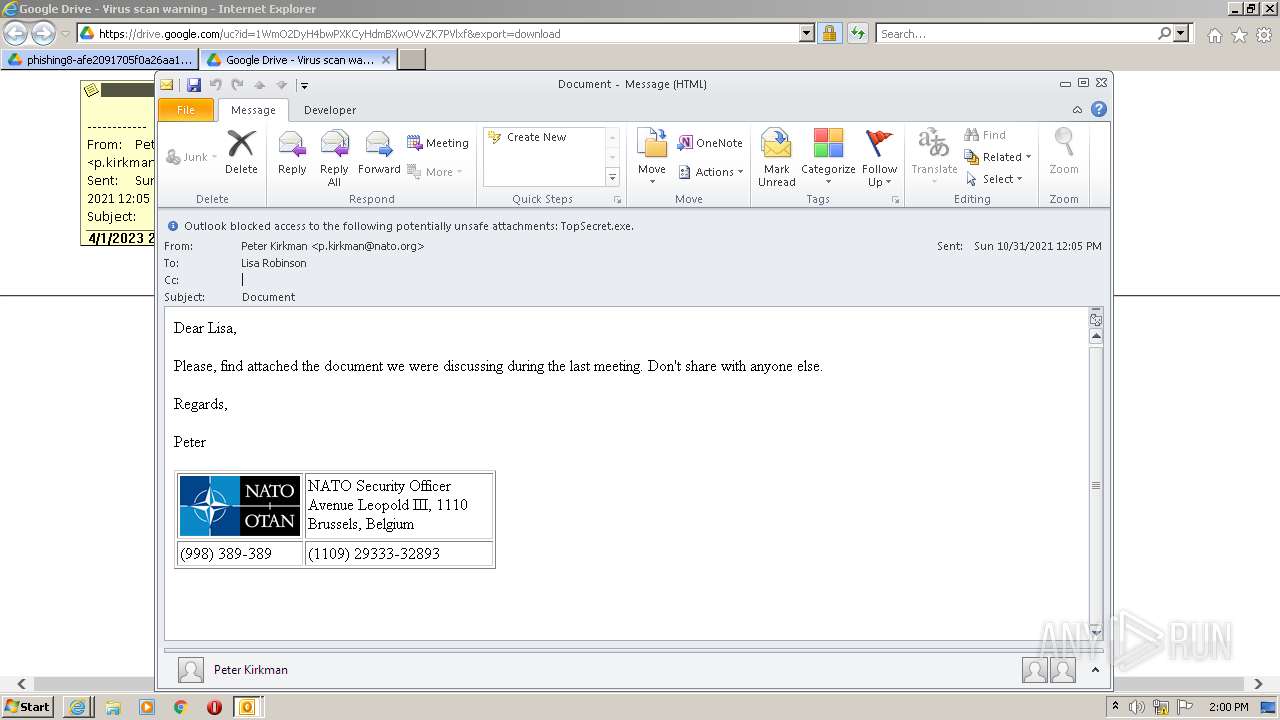
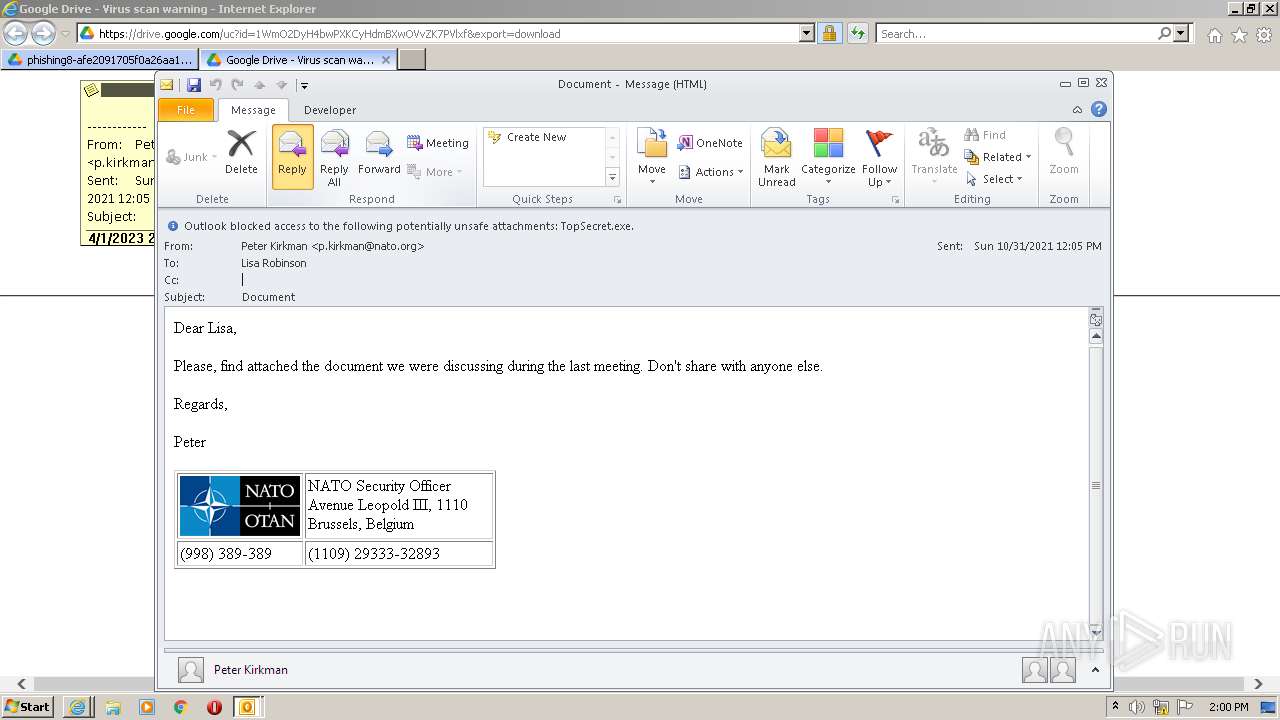
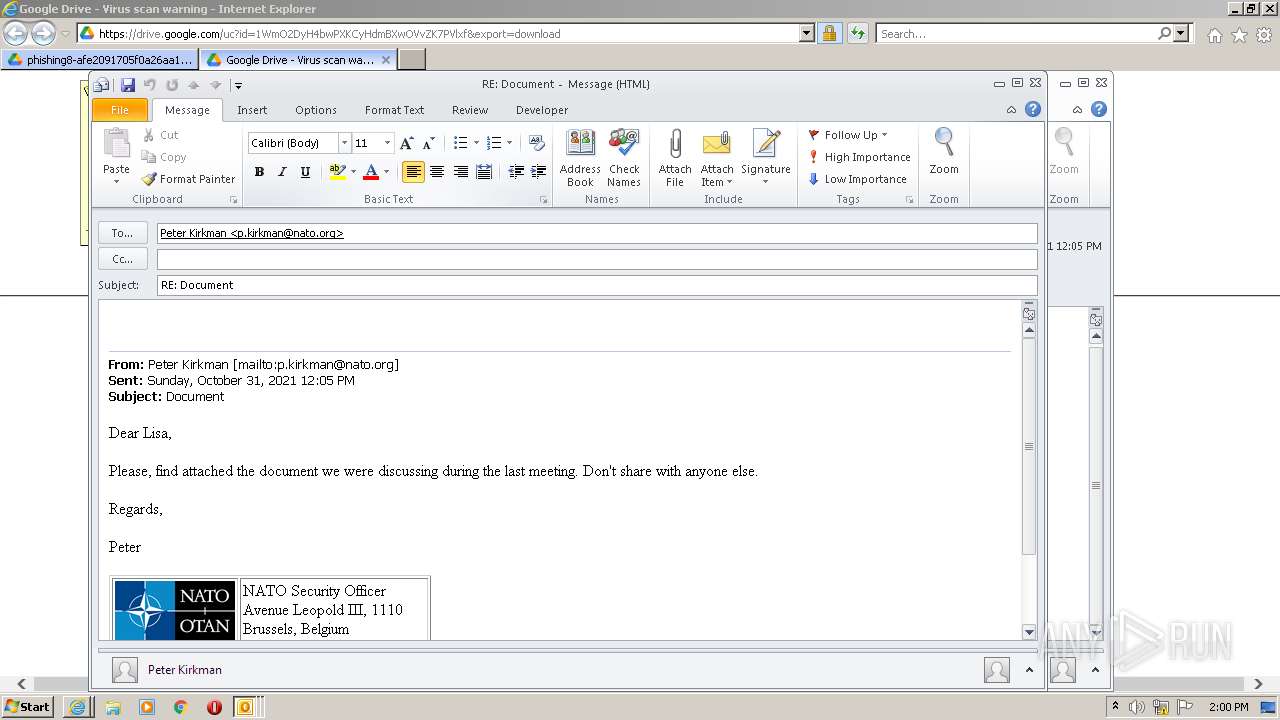
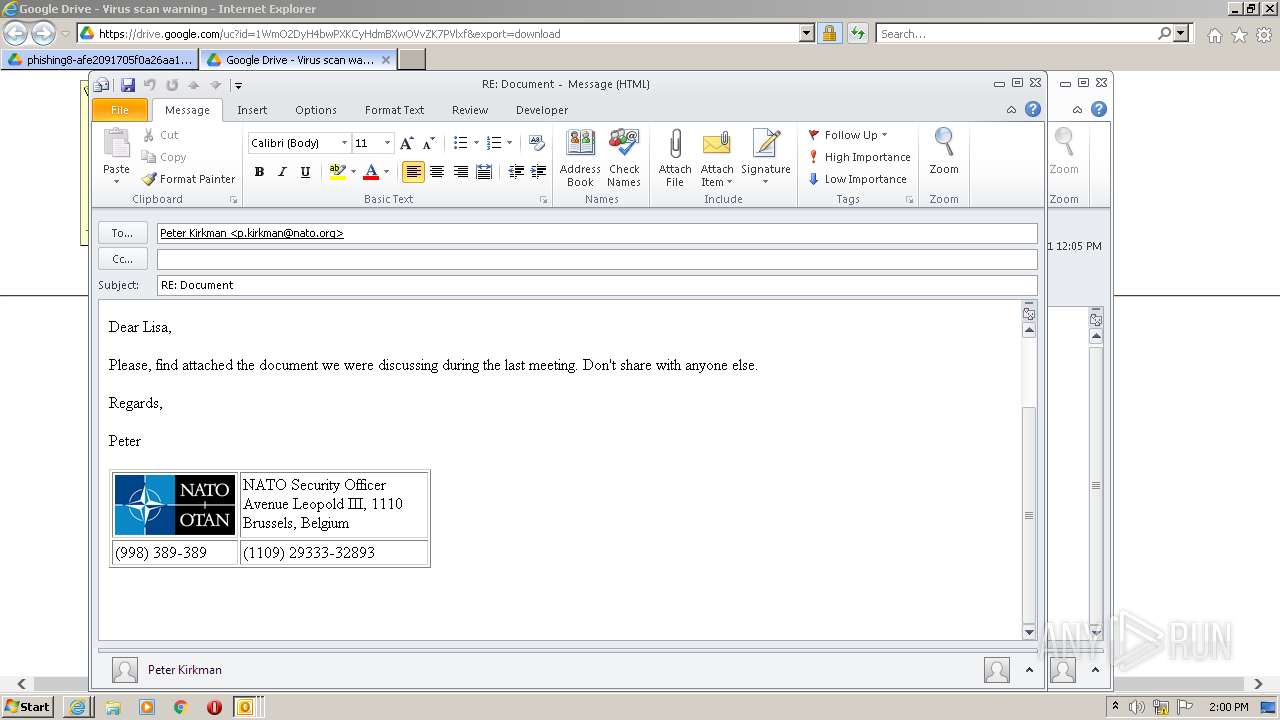
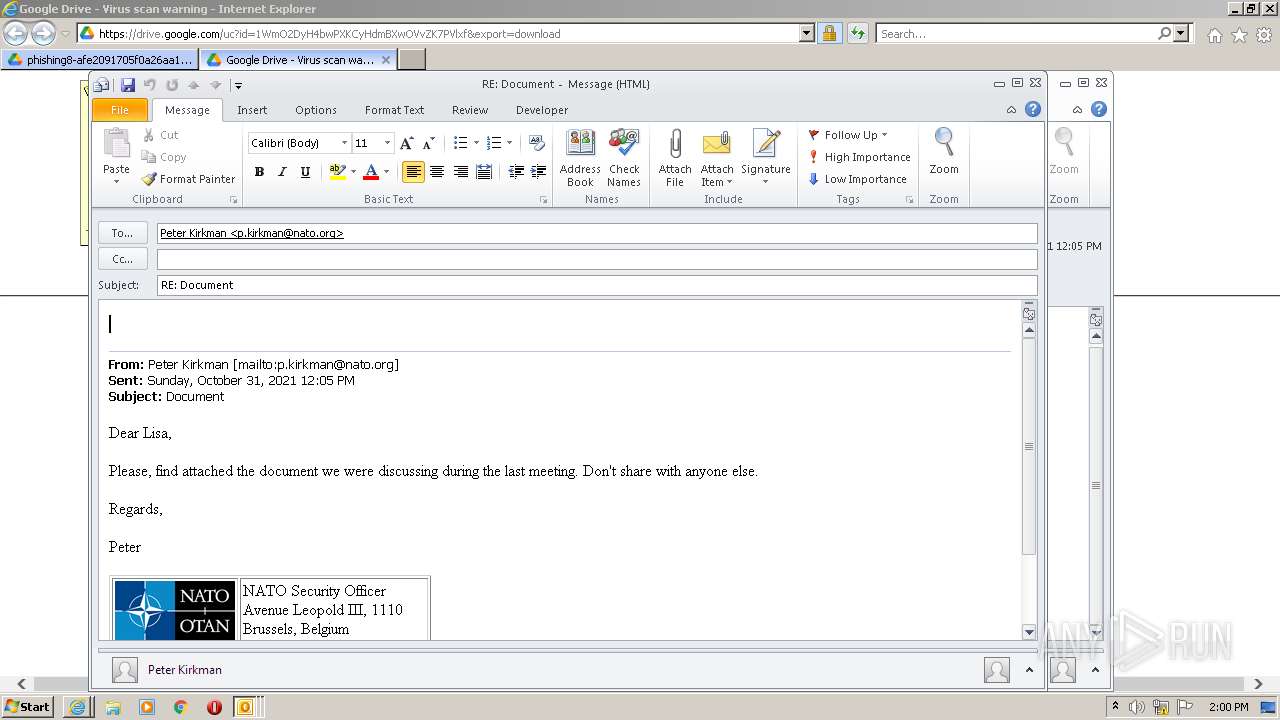
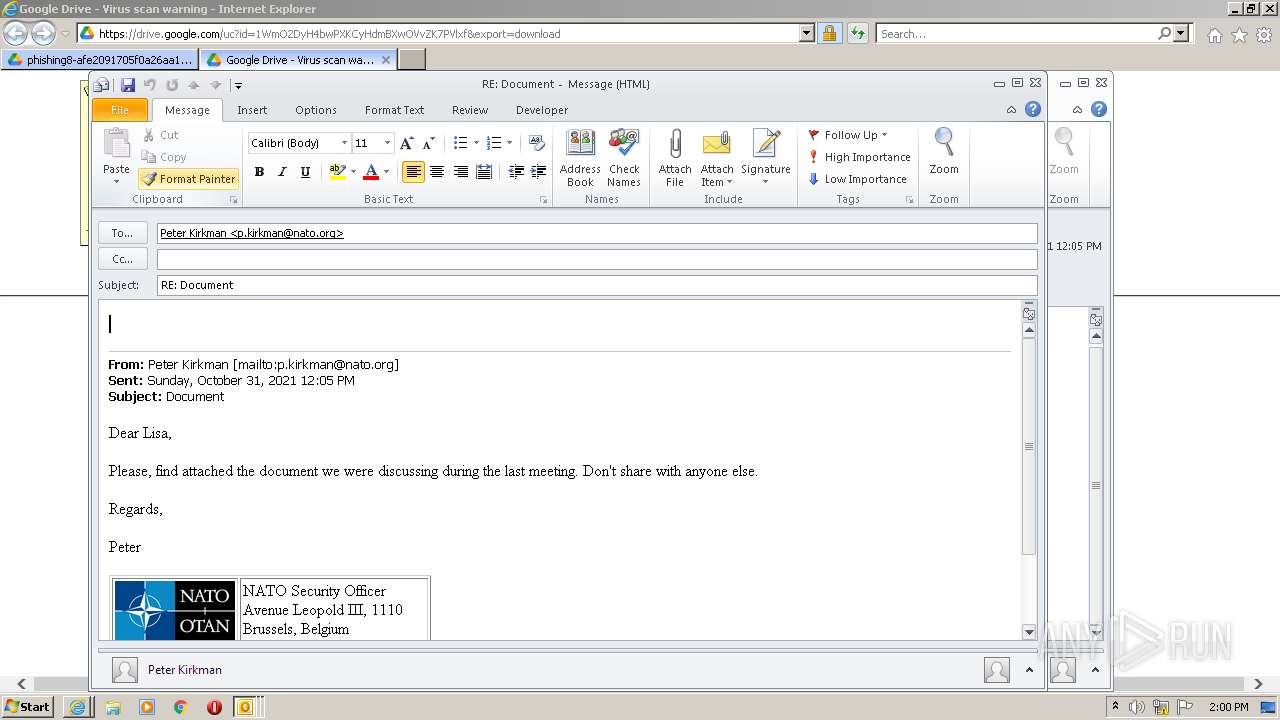
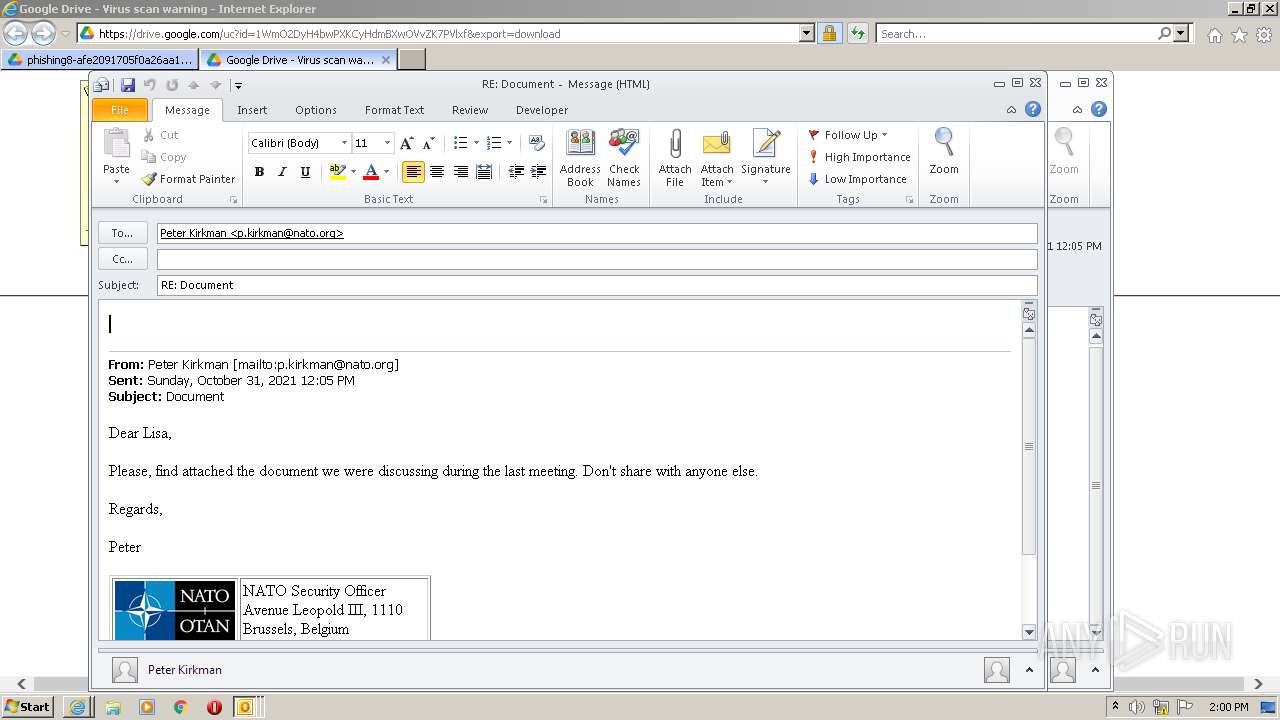
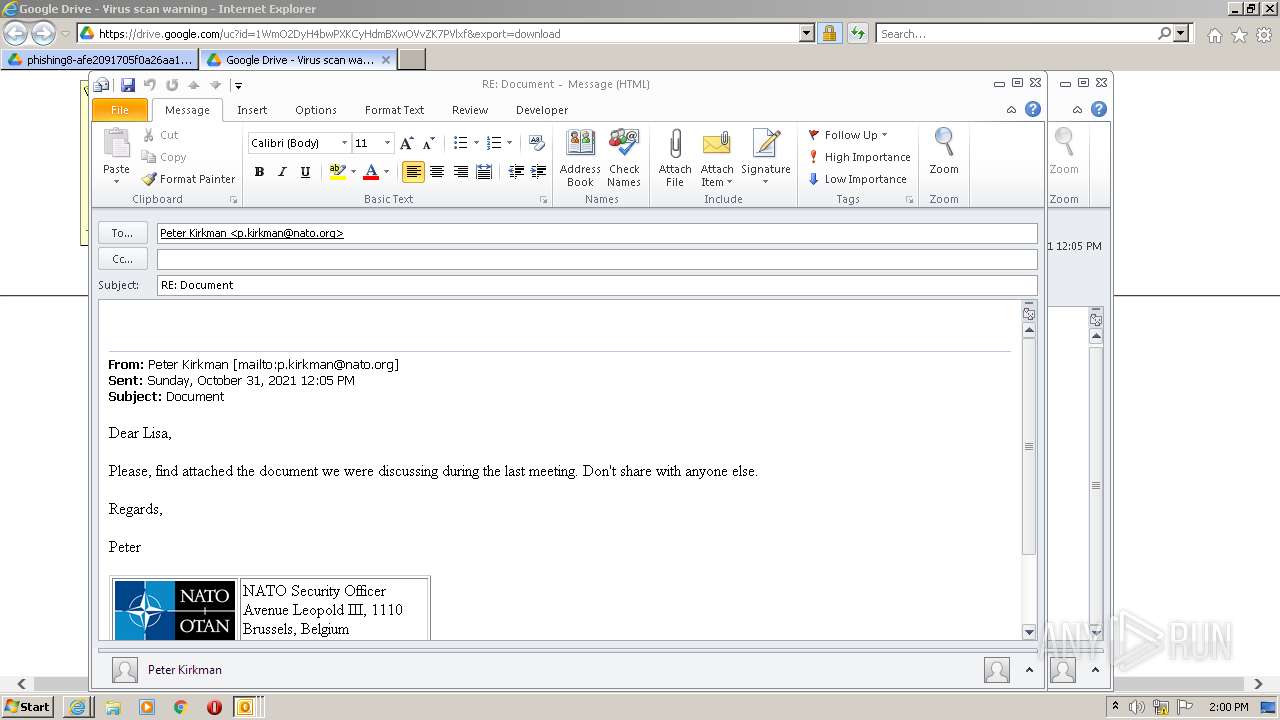
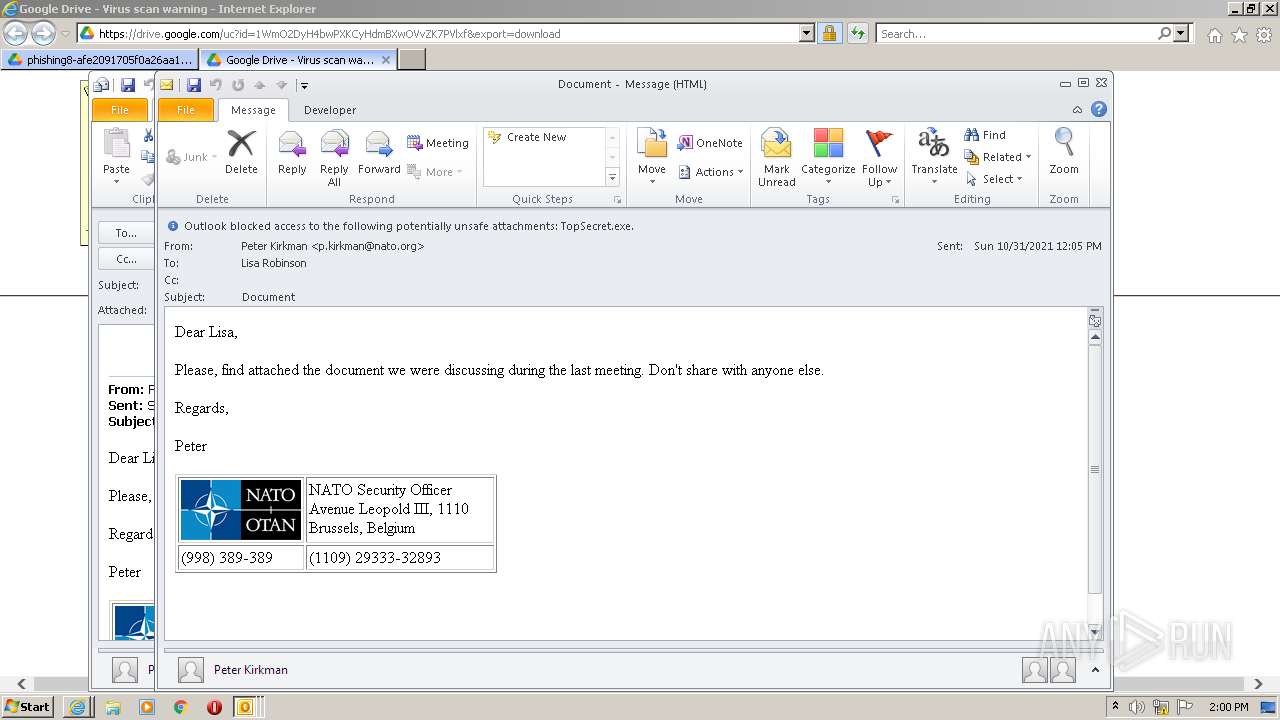
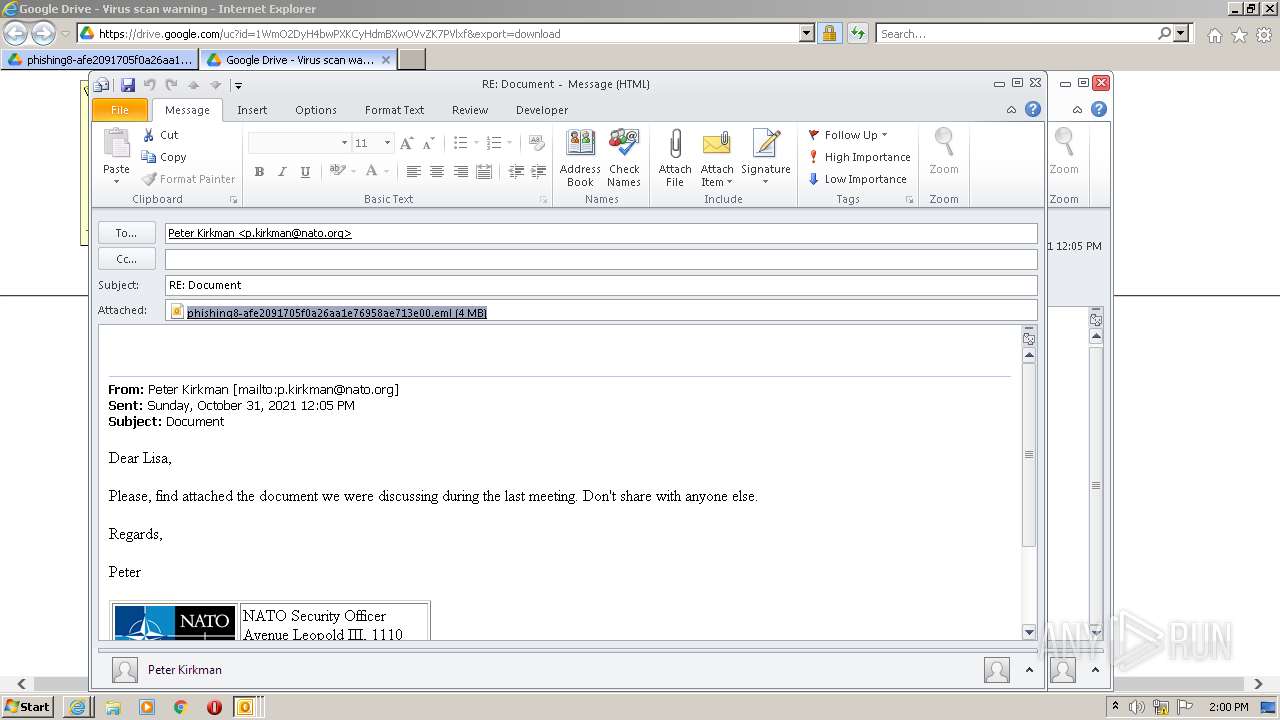
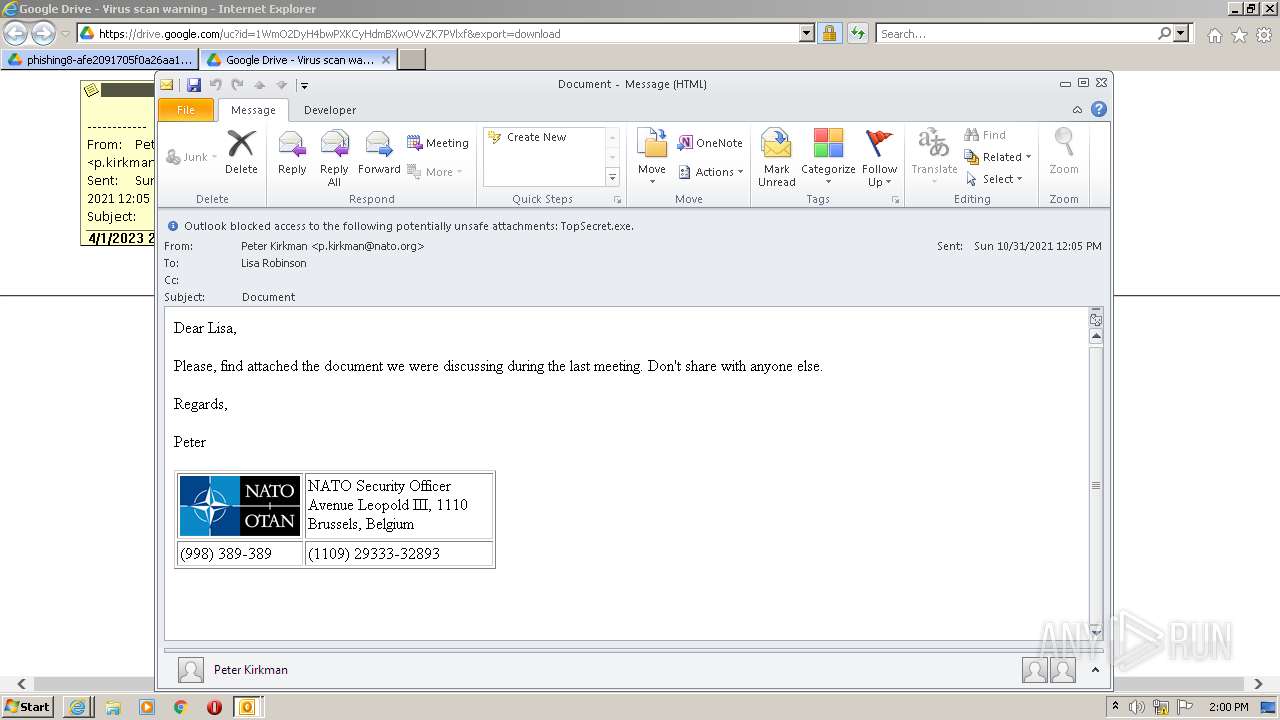
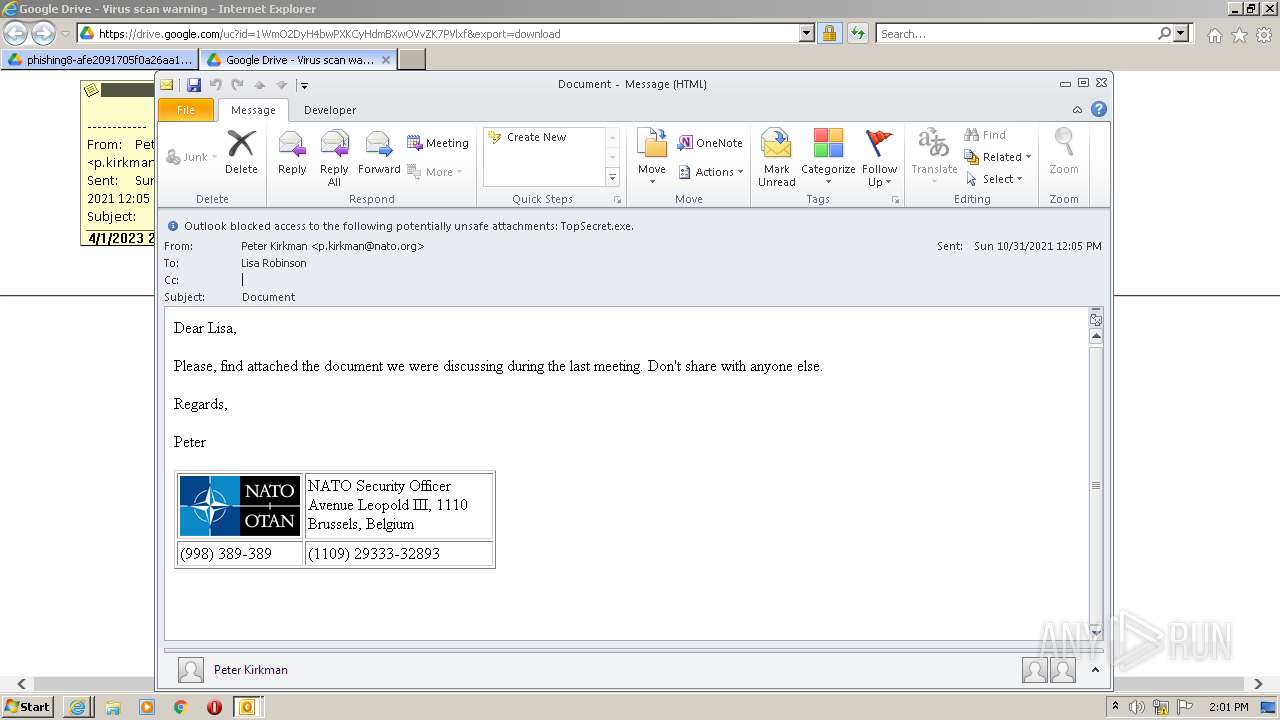
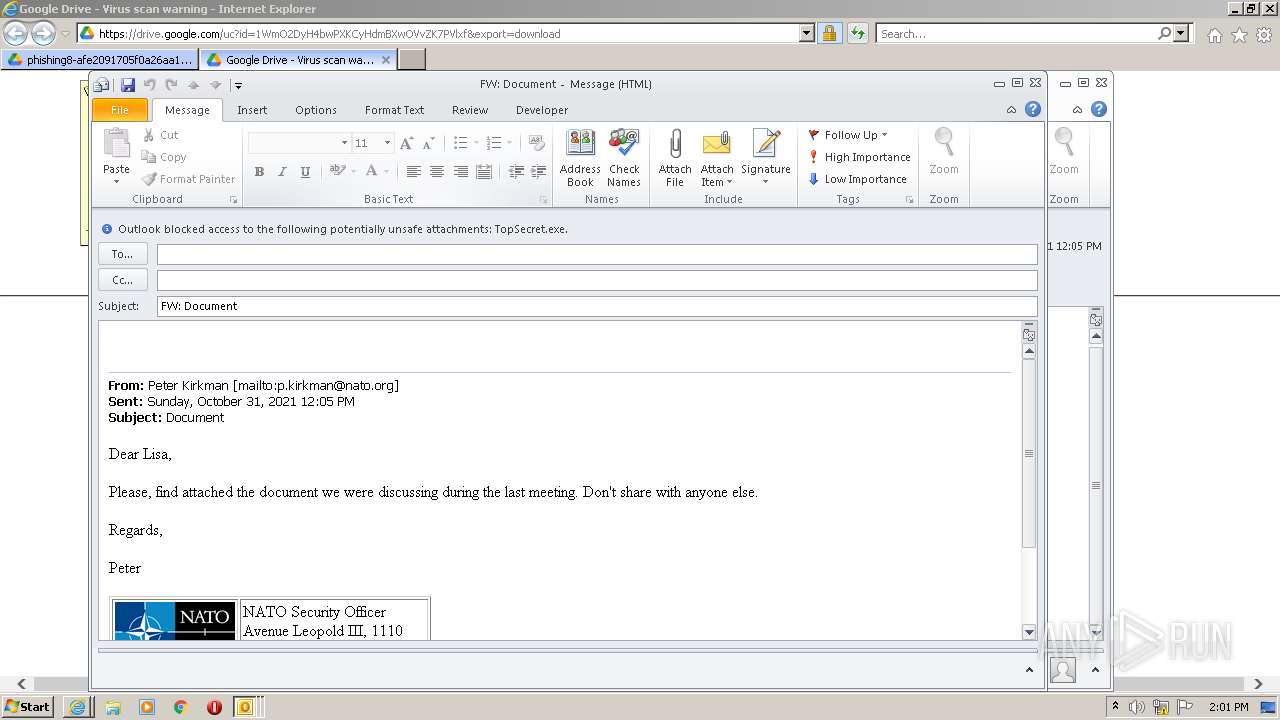
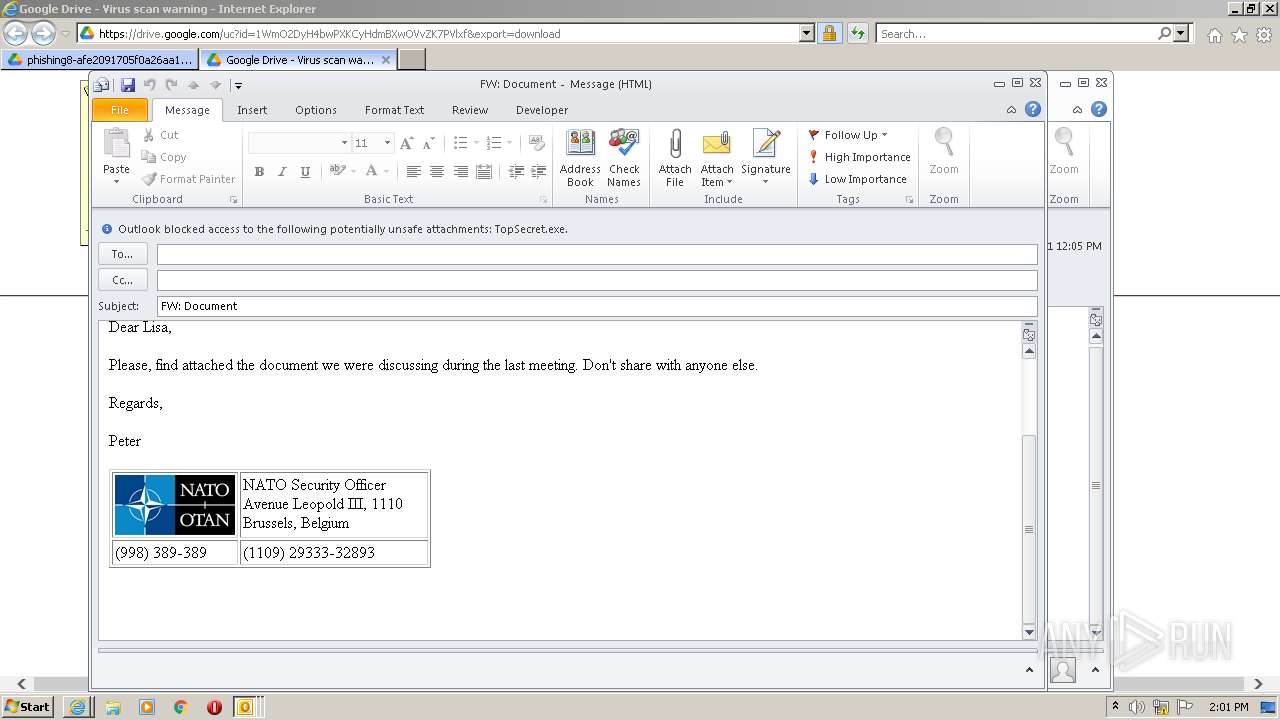
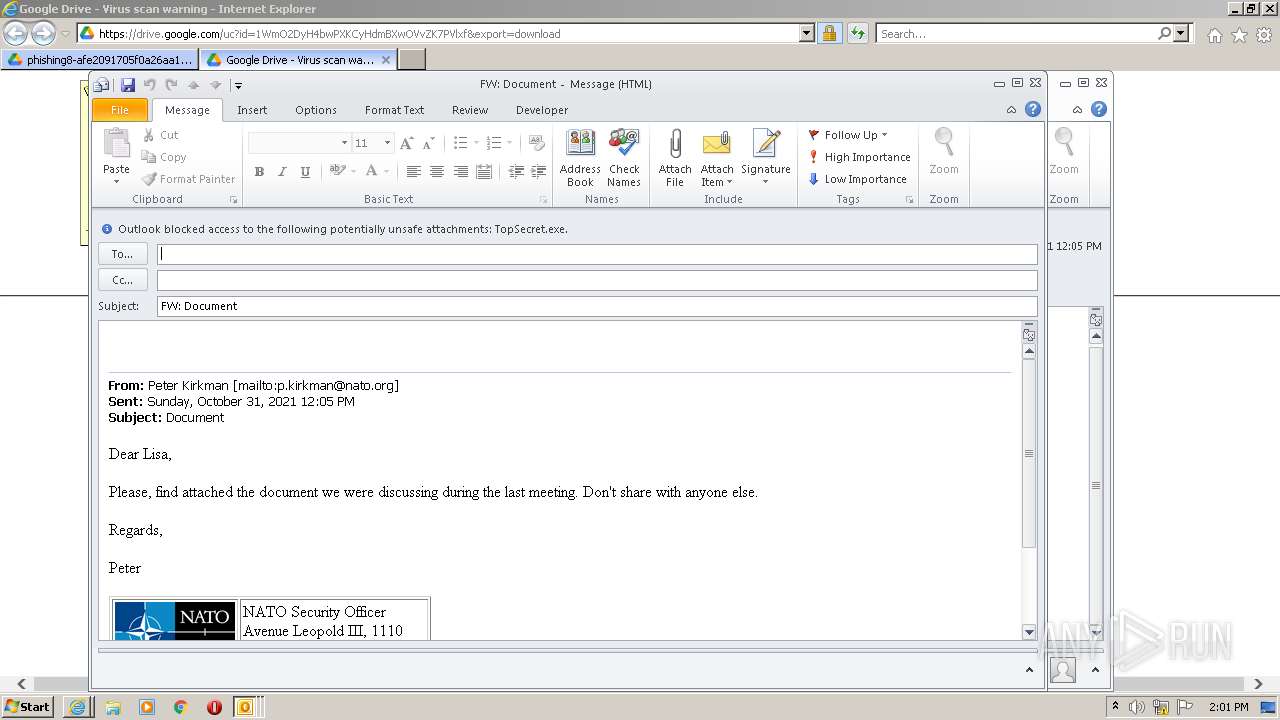
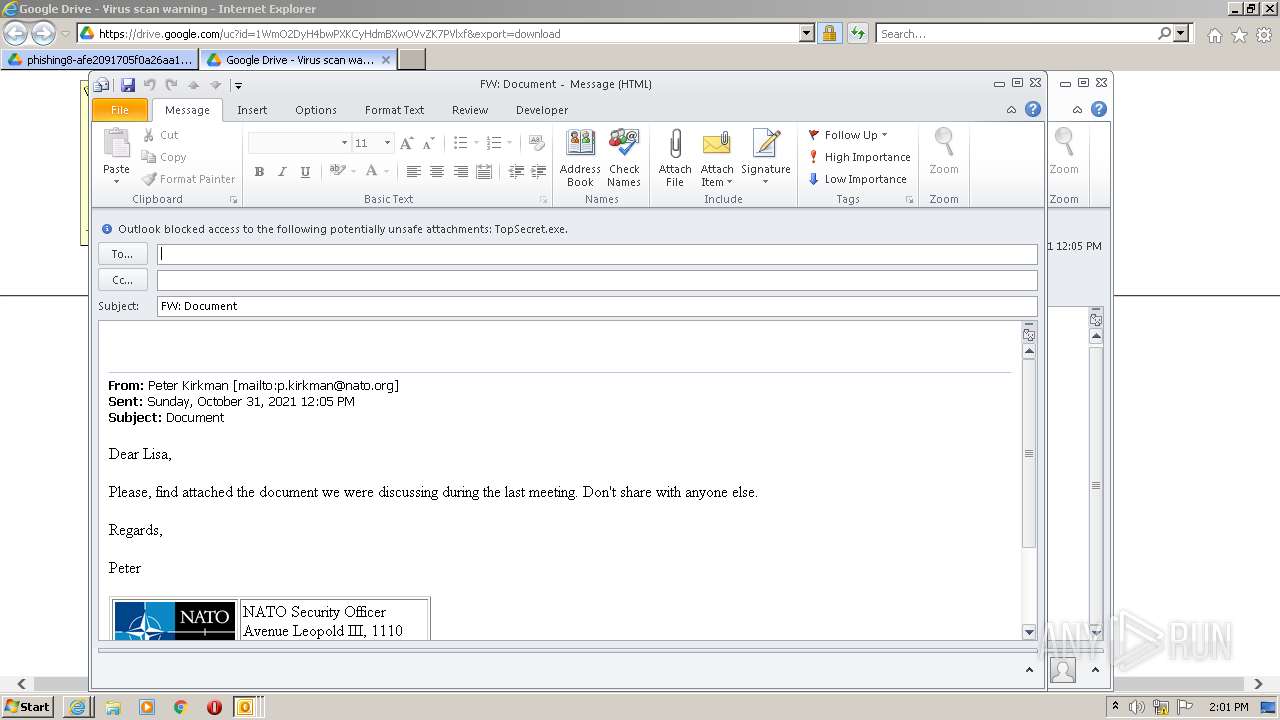
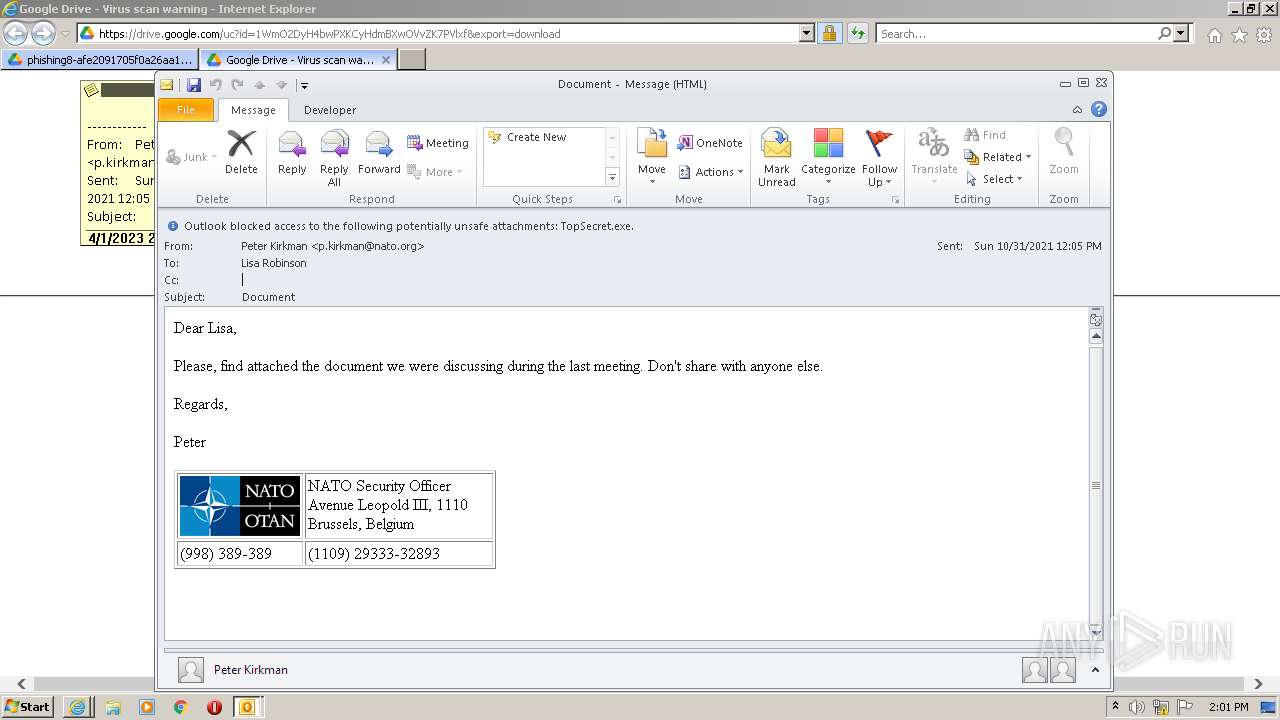
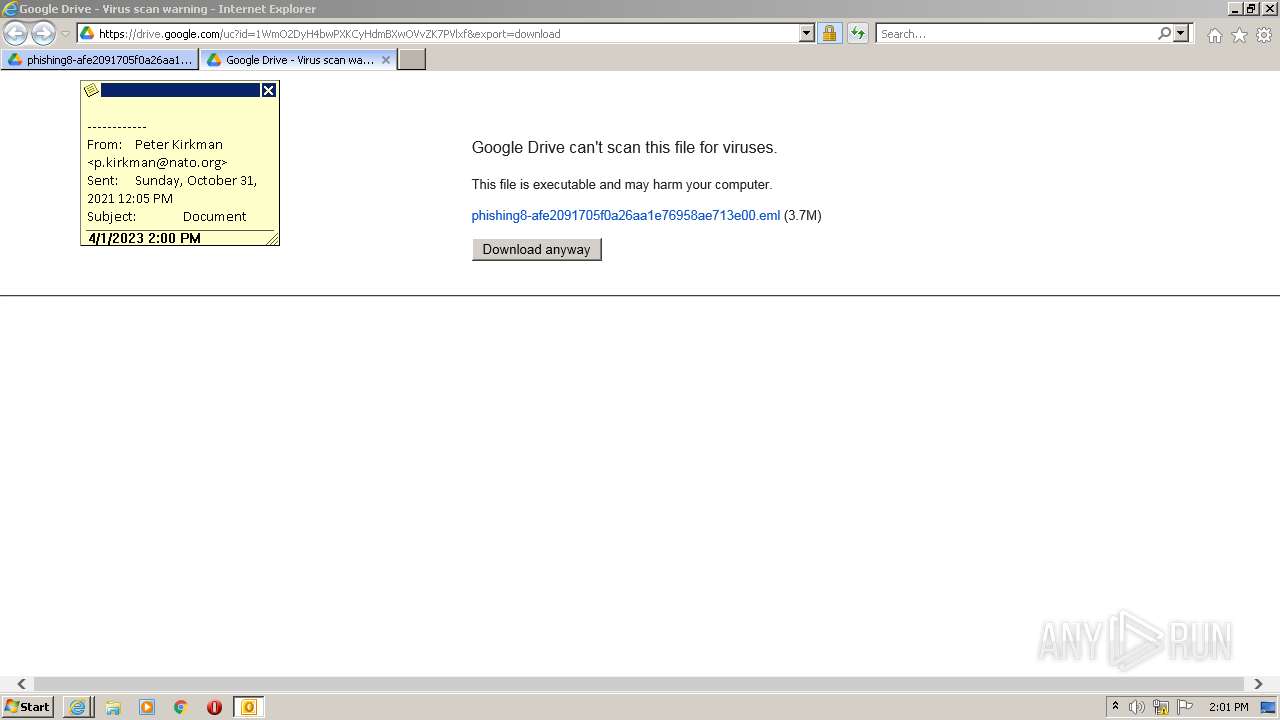
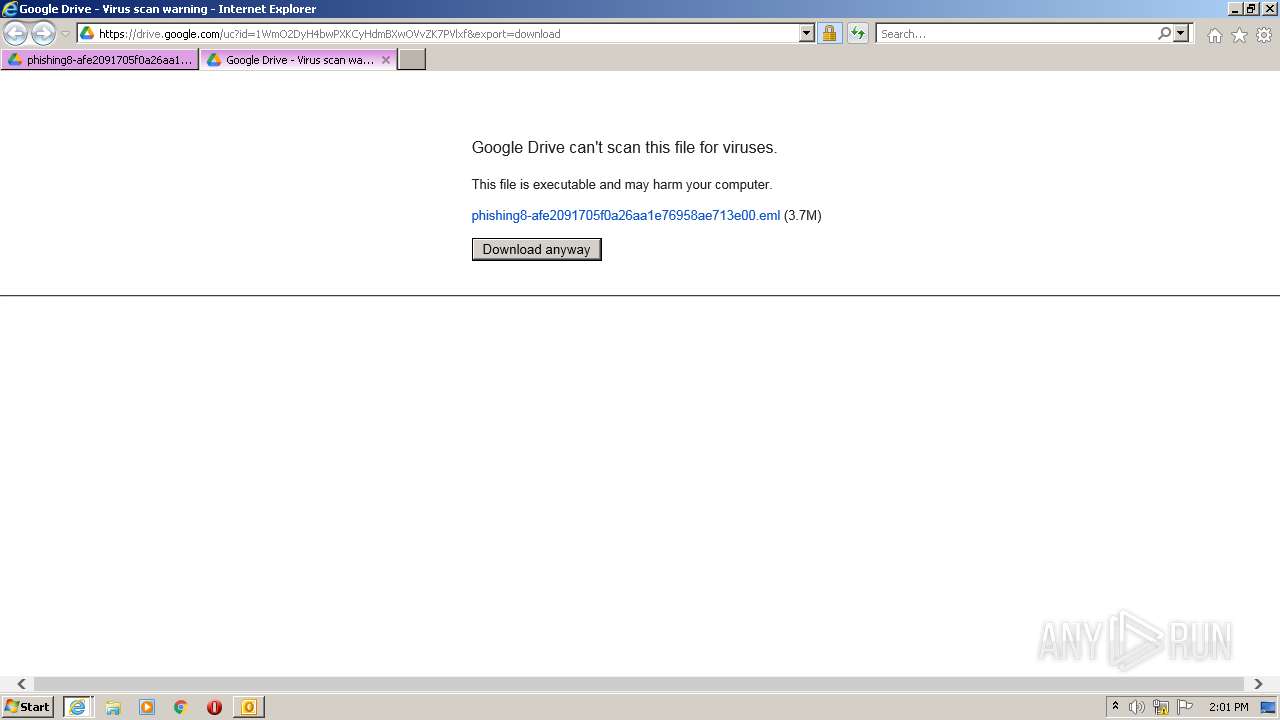
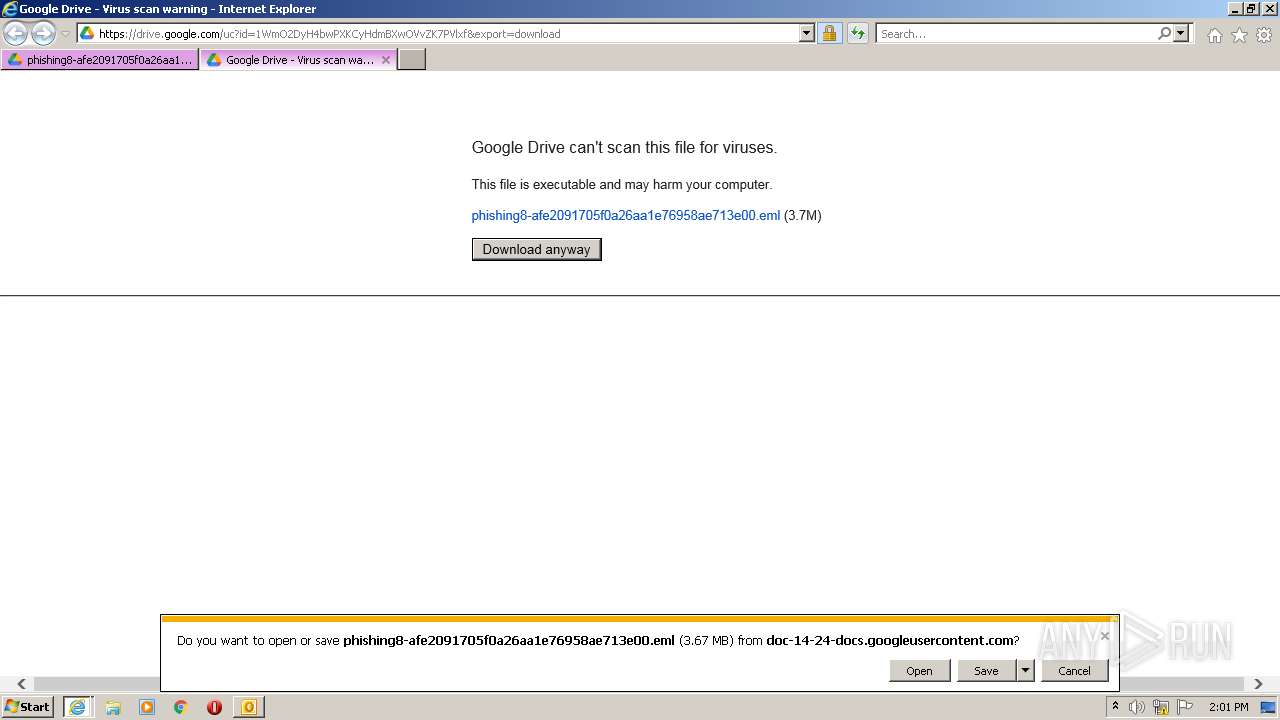
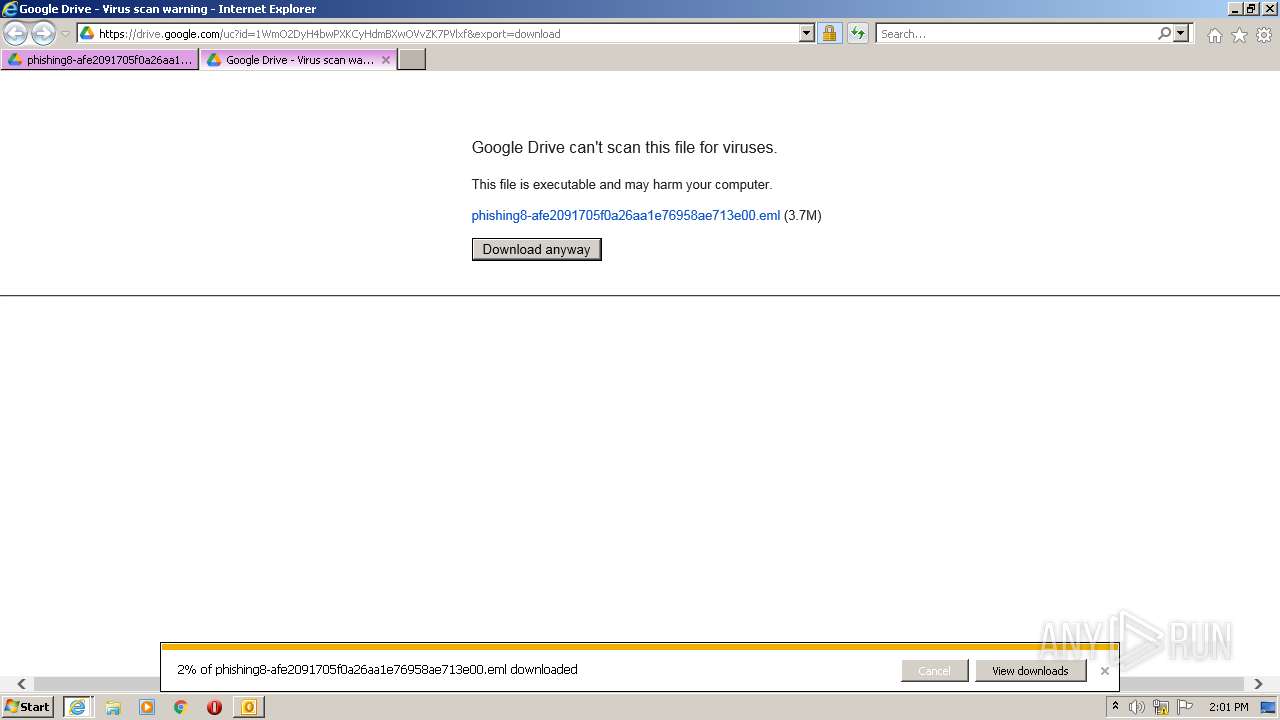
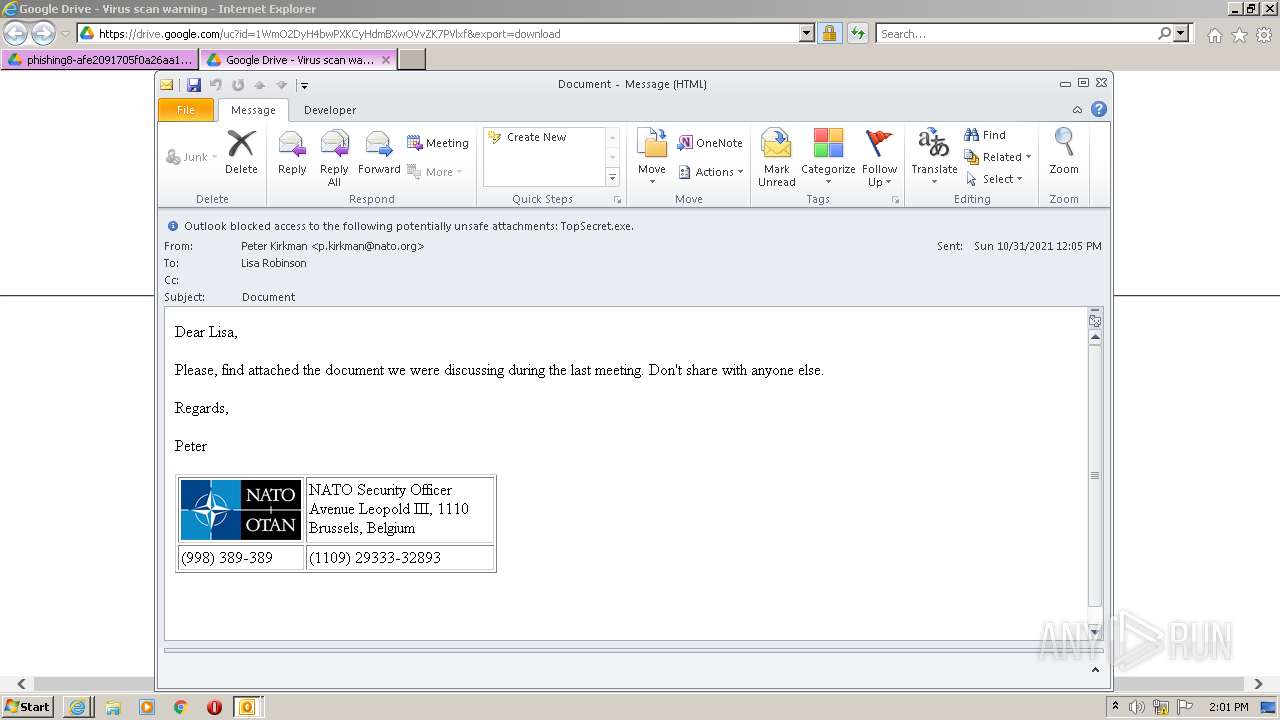
| URL: | https://drive.google.com/file/d/1WmO2DyH4bwPXKCyHdmBXwOVvZK7PVlxf/ |
| Full analysis: | https://app.any.run/tasks/68c49737-edb3-471f-83c8-eed11af8cc62 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 12:56:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 7D603F0A339F1320C7A4D218EF16E3EF |
| SHA1: | EF7D032B7B16EFFA2A72C0DF03EEB01AC43293A9 |
| SHA256: | 27978AE14EA7FDAD1F947B9517C3FB3D381A8E13EFC892A0C2D28F4893E5AAAB |
| SSDEEP: | 3:N8PMMtZJuloIIA7ctHSKn:2AJSoKn |
MALICIOUS
Unusual execution from MS Office
- OUTLOOK.EXE (PID: 3324)
SUSPICIOUS
Searches for installed software
- OUTLOOK.EXE (PID: 3324)
Reads the Internet Settings
- OUTLOOK.EXE (PID: 3324)
Detected use of alternative data streams (AltDS)
- OUTLOOK.EXE (PID: 3324)
Application launched itself
- OUTLOOK.EXE (PID: 3324)
Reads Microsoft Outlook installation path
- OUTLOOK.EXE (PID: 3324)
INFO
Application launched itself
- iexplore.exe (PID: 2680)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3324)
- OUTLOOK.EXE (PID: 2448)
- OUTLOOK.EXE (PID: 4016)
The process checks LSA protection
- OUTLOOK.EXE (PID: 3324)
Reads the computer name
- OUTLOOK.EXE (PID: 3324)
Reads the machine GUID from the registry
- OUTLOOK.EXE (PID: 3324)
Checks supported languages
- OUTLOOK.EXE (PID: 3324)
- OUTLOOK.EXE (PID: 2448)
- OUTLOOK.EXE (PID: 4016)
Create files in a temporary directory
- OUTLOOK.EXE (PID: 3324)
- iexplore.exe (PID: 2680)
Process checks computer location settings
- OUTLOOK.EXE (PID: 3324)
Checks proxy server information
- OUTLOOK.EXE (PID: 3324)
The process uses the downloaded file
- iexplore.exe (PID: 2680)
- OUTLOOK.EXE (PID: 3324)
Creates files or folders in the user directory
- OUTLOOK.EXE (PID: 3324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1364 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2680 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
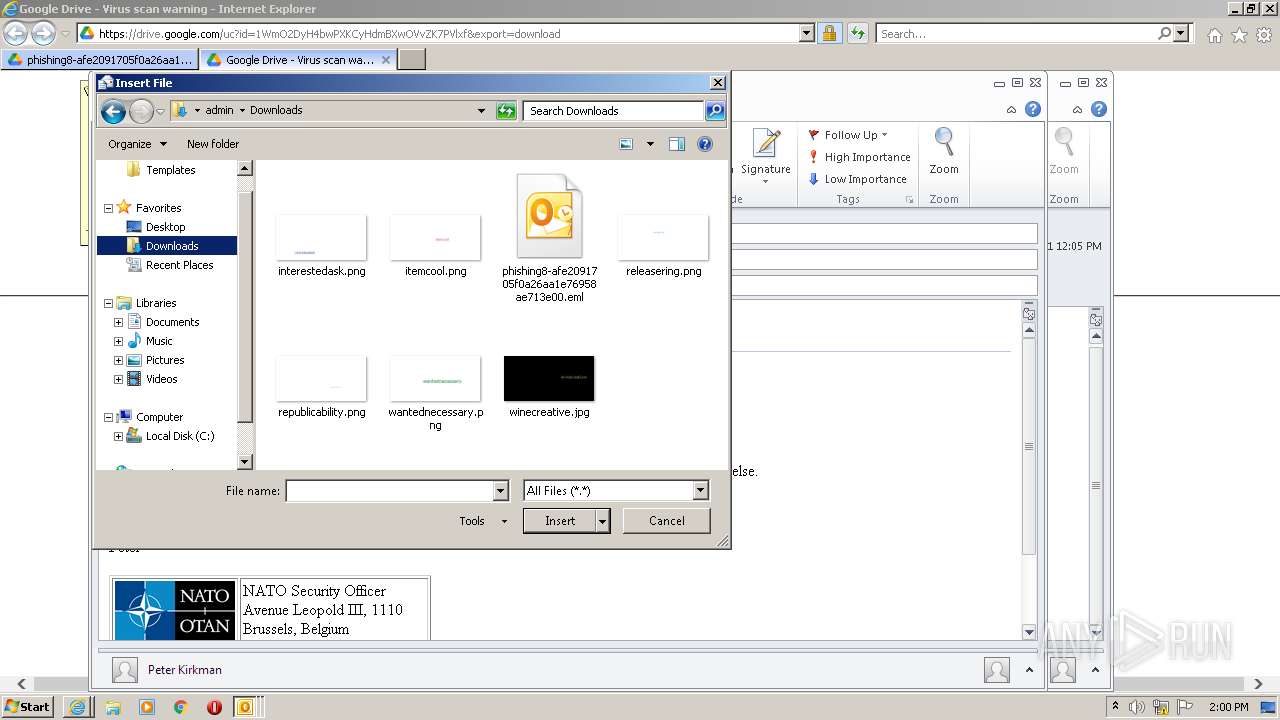
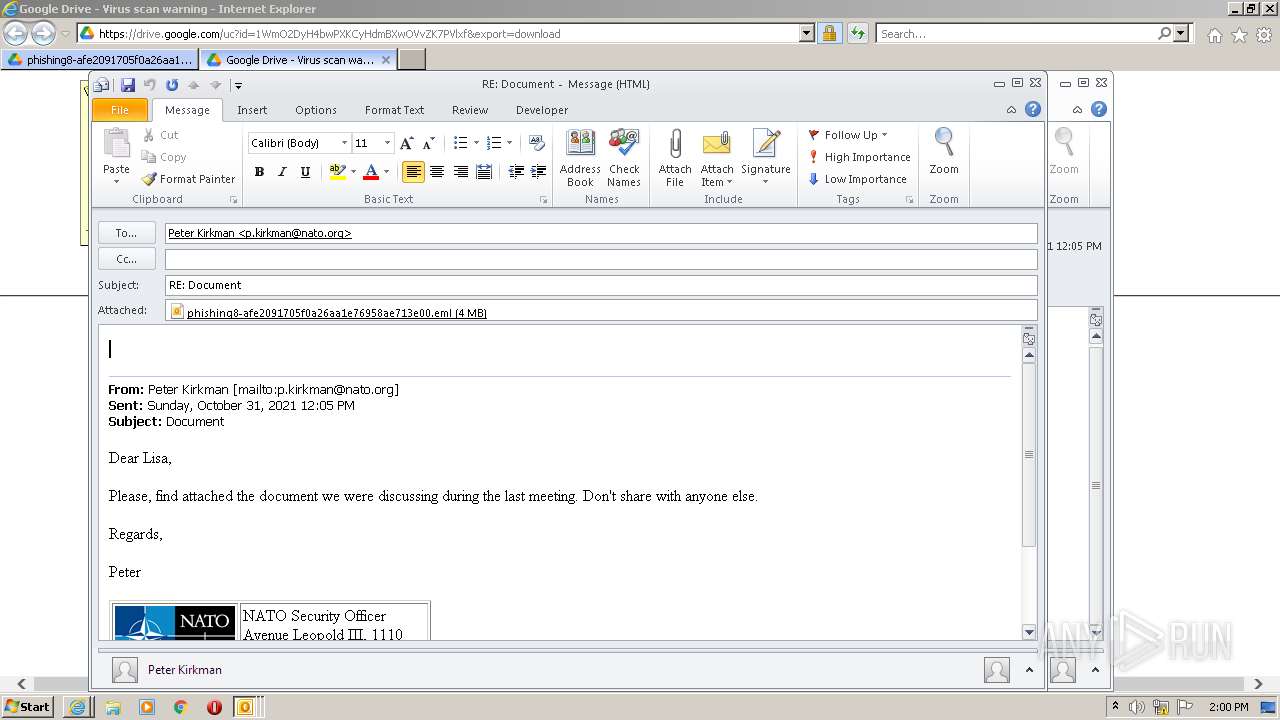
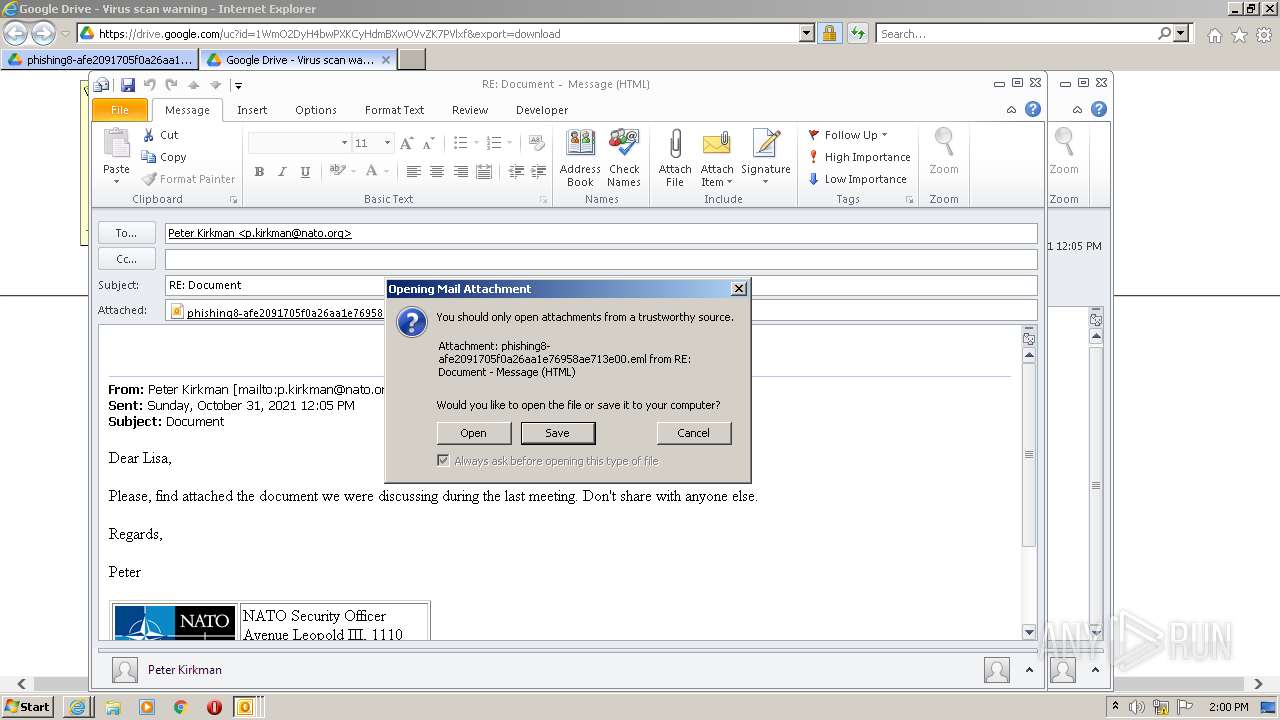
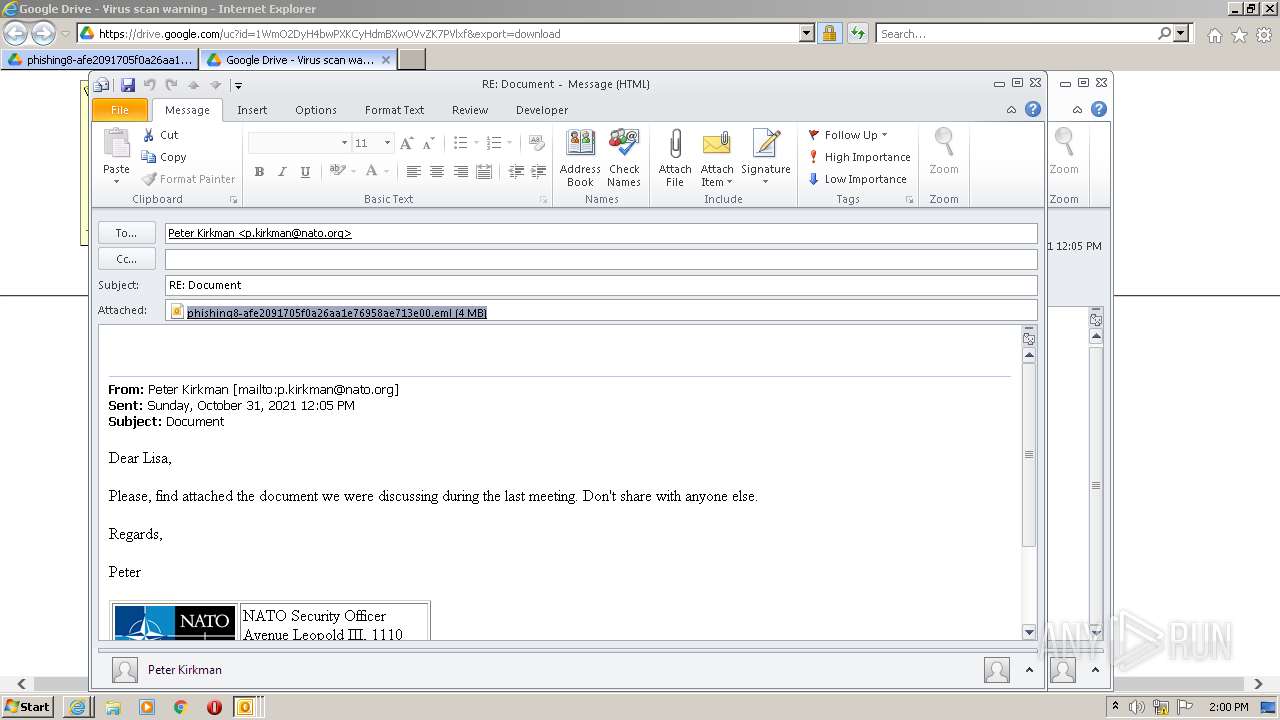
| 2448 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\433SGH8P\phishing8-afe2091705f0a26aa1e76958ae713e00.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2680 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://drive.google.com/file/d/1WmO2DyH4bwPXKCyHdmBXwOVvZK7PVlxf/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3324 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\Downloads\phishing8-afe2091705f0a26aa1e76958ae713e00.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 4016 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\phishing8-afe2091705f0a26aa1e76958ae713e00.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
55 028
Read events
53 452
Write events
1 504
Delete events
72
Modification events
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2680) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
46
Text files
112
Unknown types
50
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2680 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 2680 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1364 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 1364 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 1364 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E87CE99F124623F95572A696C80EFCAF_F21BF538BAEA56C2FC86EE4A4D9AD2BF | binary | |
MD5:— | SHA256:— | |||
| 1364 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:— | SHA256:— | |||
| 1364 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E87CE99F124623F95572A696C80EFCAF_F21BF538BAEA56C2FC86EE4A4D9AD2BF | der | |
MD5:— | SHA256:— | |||
| 1364 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\VH9PT0D7.txt | text | |
MD5:— | SHA256:— | |||
| 1364 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\edit[1].htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
56
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3324 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
1364 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEX8DsGwm267CjwDOorEaJk%3D | US | der | 471 b | whitelisted |
2680 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1364 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFwMawXF47e0CuAYa1GCMjM%3D | US | der | 471 b | whitelisted |
1364 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
1364 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGuOw5S%2FgZeuCs2W38ctSDs%3D | US | der | 471 b | whitelisted |
2680 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
1364 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCAnAYBLgi%2BghKCkyxZyQ88 | US | der | 472 b | whitelisted |
2680 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
1364 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDP0V3EgcJtXxJEXyOb6vmJ | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2680 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2680 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 142.250.181.238:443 | drive.google.com | GOOGLE | US | whitelisted |
1364 | iexplore.exe | 142.250.181.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1364 | iexplore.exe | 142.250.185.67:443 | www.gstatic.com | GOOGLE | US | whitelisted |
1364 | iexplore.exe | 216.58.212.170:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
1364 | iexplore.exe | 142.250.181.227:443 | ocsp.pki.goog | GOOGLE | US | whitelisted |
— | — | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
— | — | 142.250.184.238:443 | apis.google.com | GOOGLE | US | whitelisted |
— | — | 216.58.212.174:443 | play.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
drive.google.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |