| File name: | 1919451179989524203815663507076221655987993950541226219603864.tgz |
| Full analysis: | https://app.any.run/tasks/96e66c11-fe78-42e1-8c71-248c15a0a089 |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2022, 20:55:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A99F49888E1F11DCC28433A74F662EEA |
| SHA1: | D93AD8F049D0461D47A95975D6B3D251E3DE6C96 |
| SHA256: | 2784876DF9372689EC7B8EF76ABE78F3BC1B9CC6BE3657318CAD346C681D4490 |
| SSDEEP: | 3072:xLQft8XmpfEt1wjSbTbihBF7buQ37nZuxanL27YTHESNuKw2V6u9BNMY:xsfGD5zihBTbcAL27YjRwK6sNMY |
MALICIOUS
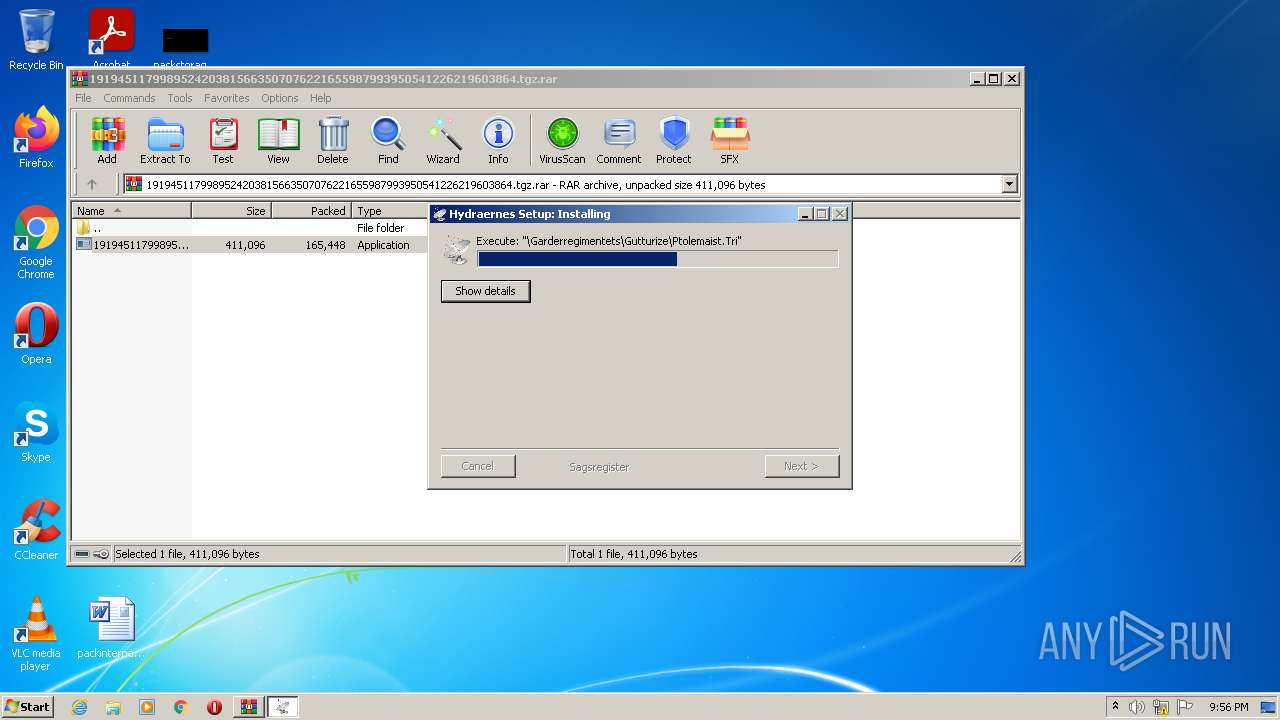
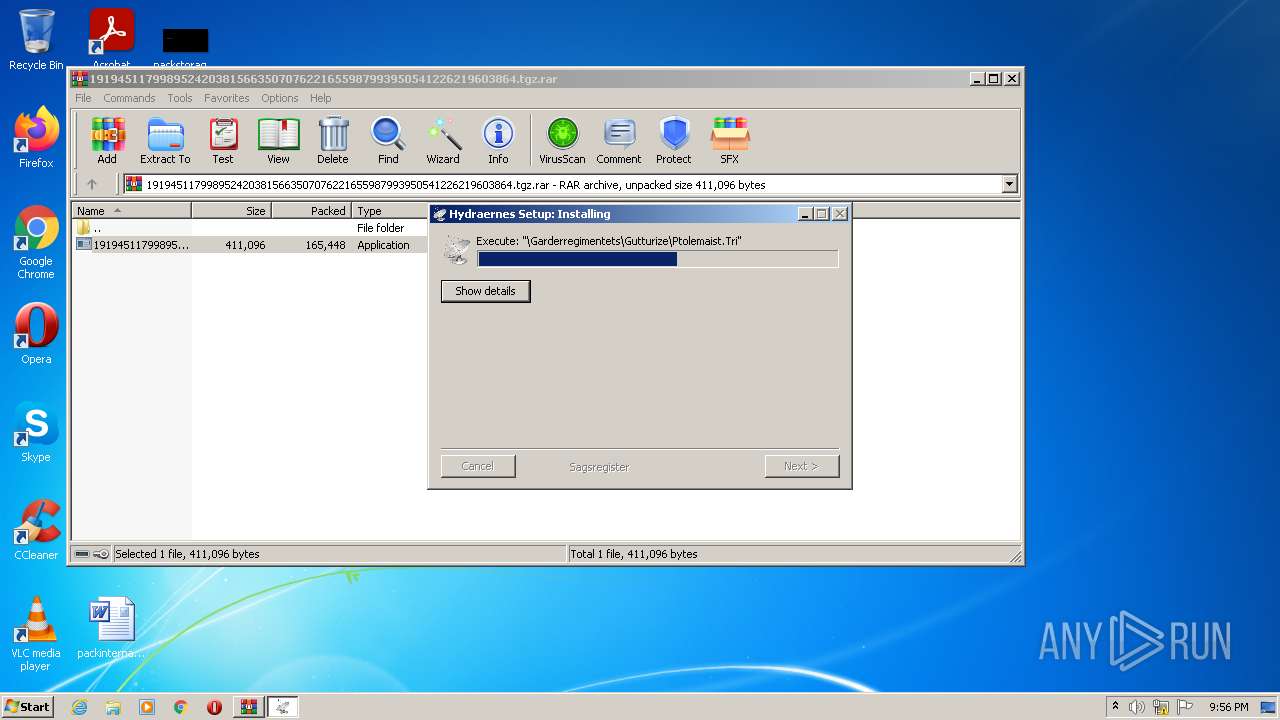
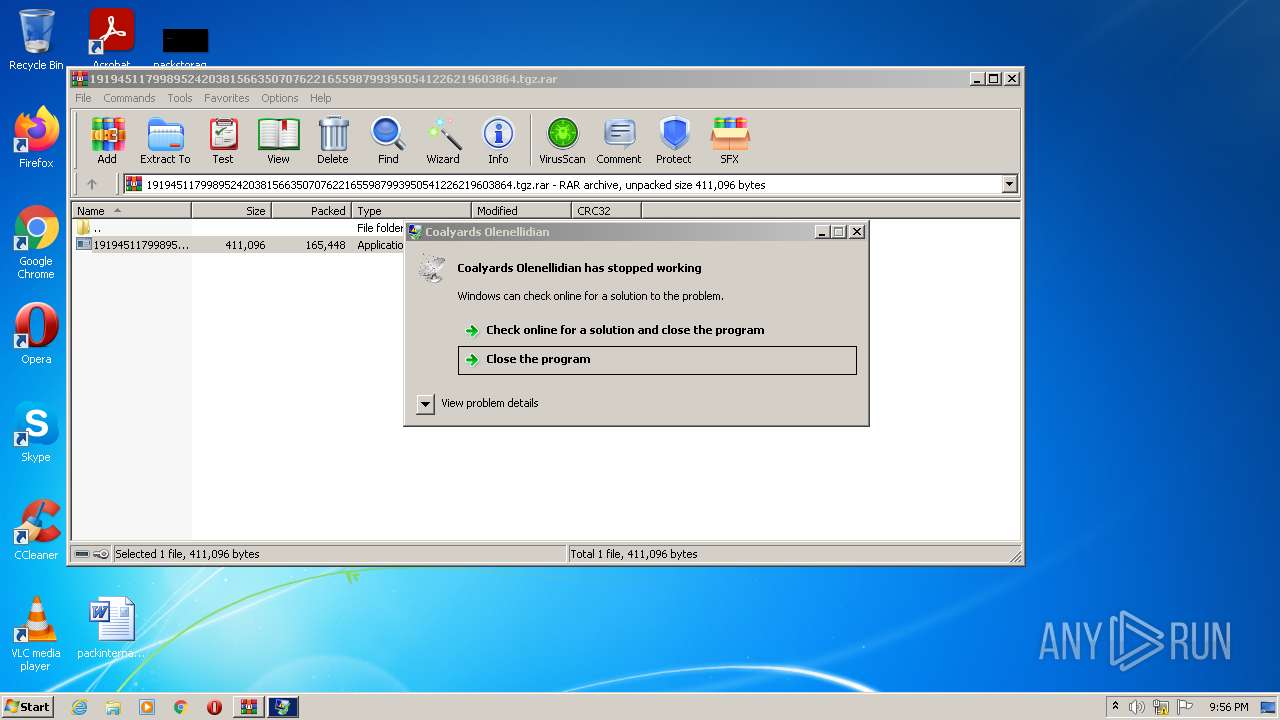
Application was dropped or rewritten from another process
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 3800)
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 2604)
Drops executable file immediately after starts
- WinRAR.exe (PID: 3044)
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 3800)
Loads dropped or rewritten executable
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 3800)
SUSPICIOUS
Checks supported languages
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 3800)
- WinRAR.exe (PID: 3044)
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 2604)
Reads the computer name
- WinRAR.exe (PID: 3044)
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 3800)
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 2604)
Executable content was dropped or overwritten
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 3800)
- WinRAR.exe (PID: 3044)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3044)
- 1919451179989524203815663507076221655987993950541226219603864.exe (PID: 3800)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
3
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2604 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3044.13247\1919451179989524203815663507076221655987993950541226219603864.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3044.13247\1919451179989524203815663507076221655987993950541226219603864.exe | WinRAR.exe | ||||||||||||
User: admin Company: Bundedes Integrity Level: MEDIUM Description: Coalyards Olenellidian Exit code: 3221225725 Modules
| |||||||||||||||
| 3044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1919451179989524203815663507076221655987993950541226219603864.tgz.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3800 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3044.12311\1919451179989524203815663507076221655987993950541226219603864.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3044.12311\1919451179989524203815663507076221655987993950541226219603864.exe | WinRAR.exe | ||||||||||||
User: admin Company: Bundedes Integrity Level: MEDIUM Description: Coalyards Olenellidian Exit code: 0 Modules
| |||||||||||||||
Total events
7 382
Read events
7 364
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1919451179989524203815663507076221655987993950541226219603864.tgz.rar | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3044.12311\1919451179989524203815663507076221655987993950541226219603864.exe | executable | |
MD5:— | SHA256:— | |||
| 3800 | 1919451179989524203815663507076221655987993950541226219603864.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Skaktposens\plaprende\Edb\Recognosce\Cancion\ArtDeco_brown_5.bmp | image | |
MD5:— | SHA256:— | |||
| 3800 | 1919451179989524203815663507076221655987993950541226219603864.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Skaktposens\plaprende\Edb\Ule\Misdepart\Gastroenterostomies.Cua | binary | |
MD5:— | SHA256:— | |||
| 3800 | 1919451179989524203815663507076221655987993950541226219603864.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Skaktposens\plaprende\Edb\Flaadeofficerernes\network-wireless-signal-weak-symbolic.symbolic.png | image | |
MD5:7A40E03256D60C255FDDE6F773C03344 | SHA256:4E771A48955E294B17A13C339DFF4154A67CE84A7C52BCCF6FE56EEAEEC392DC | |||
| 3800 | 1919451179989524203815663507076221655987993950541226219603864.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Skaktposens\plaprende\Edb\Flaadeofficerernes\surreverence.Van | text | |
MD5:— | SHA256:— | |||
| 3044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3044.13247\1919451179989524203815663507076221655987993950541226219603864.exe | executable | |
MD5:— | SHA256:— | |||
| 3800 | 1919451179989524203815663507076221655987993950541226219603864.exe | C:\Users\admin\Documents\Paaskrifternes.ini | text | |
MD5:— | SHA256:— | |||
| 3800 | 1919451179989524203815663507076221655987993950541226219603864.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Skaktposens\plaprende\Edb\Flaadeofficerernes\weather-few-clouds-symbolic.svg | image | |
MD5:3AF5AFFF134750B10F9B491591A8F7A2 | SHA256:E5EC423B37F0BF203CEB9B8E3DA6A7F1F3491A15C732B3CA58E38C0503FC14DA | |||
| 3800 | 1919451179989524203815663507076221655987993950541226219603864.exe | C:\Users\admin\AppData\Local\Temp\nsr67E6.tmp\System.dll | executable | |
MD5:17ED1C86BD67E78ADE4712BE48A7D2BD | SHA256:BD046E6497B304E4EA4AB102CAB2B1F94CE09BDE0EEBBA4C59942A732679E4EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1600 | WerFault.exe | 20.189.173.20:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.microsoft.com |
| whitelisted |