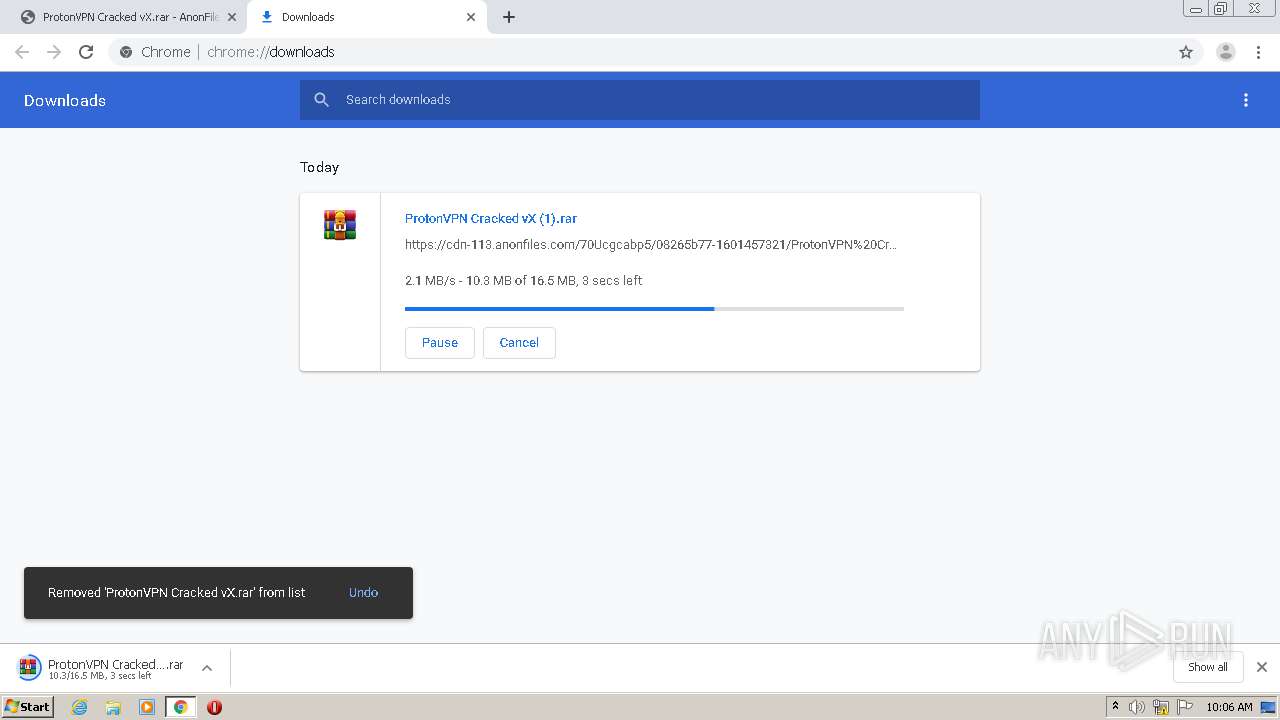
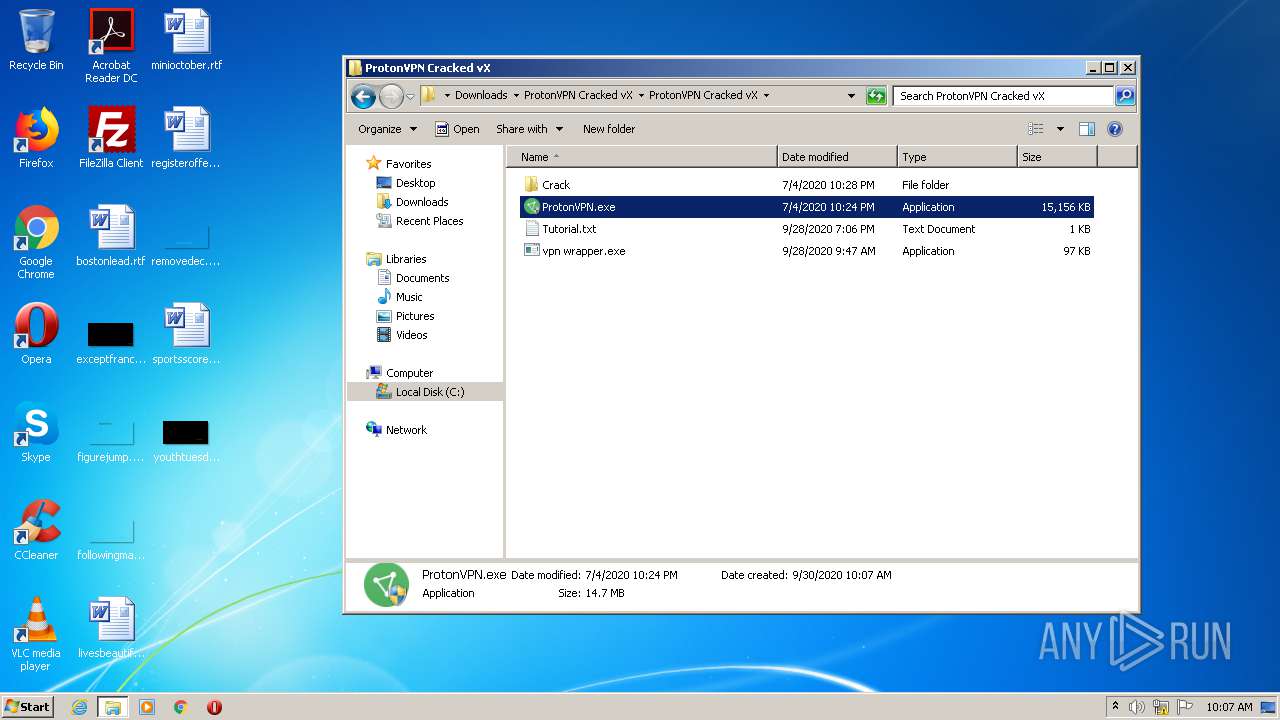
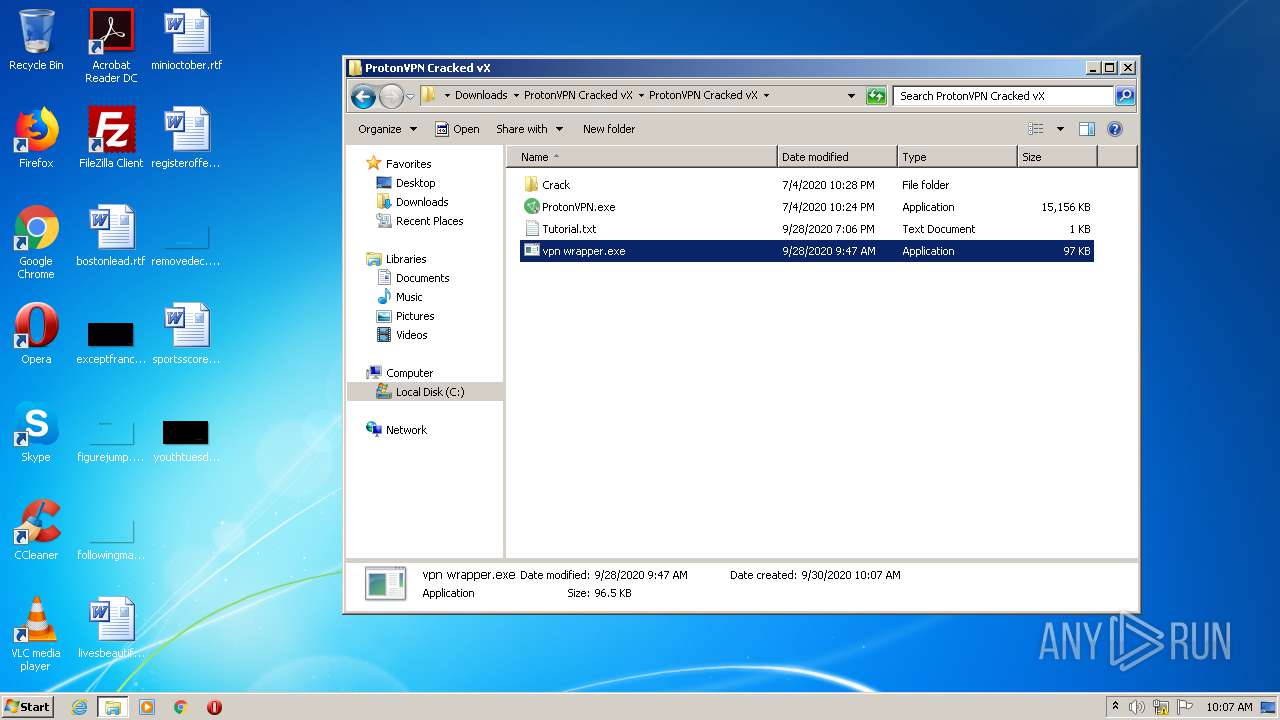
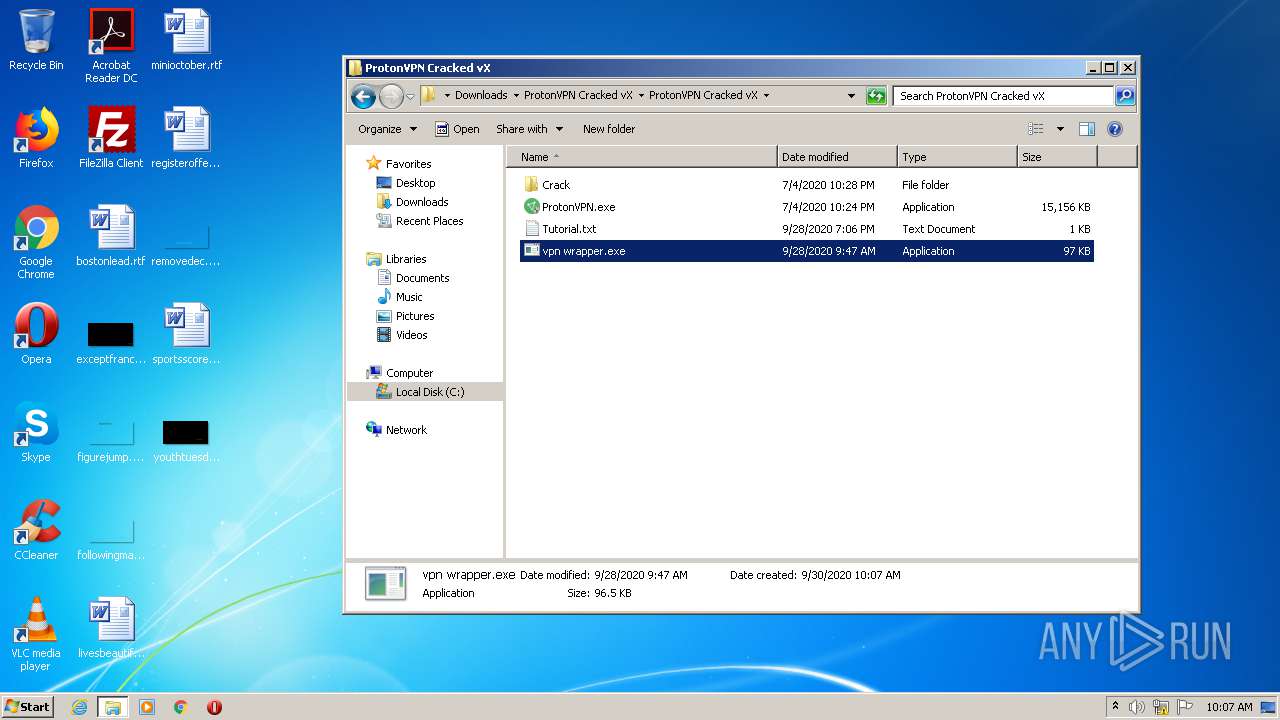
| URL: | https://anonfiles.com/70Ucgcabp5/ProtonVPN_Cracked_vX_rar |
| Full analysis: | https://app.any.run/tasks/d35065d2-271f-4e88-b61c-21ea7420d806 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 09:05:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A0DD71B5C4C74440C58402925F654991 |
| SHA1: | CC1092ACB645C67CCAC0053333CB0B6DD4CA0EE5 |
| SHA256: | 277B33E3B1121EF61B139B1C1A5D251D1684AF7CA7F0675A4B495F7858C48CF9 |
| SSDEEP: | 3:N8M2bzofzhQwUX:2M2b0KwO |
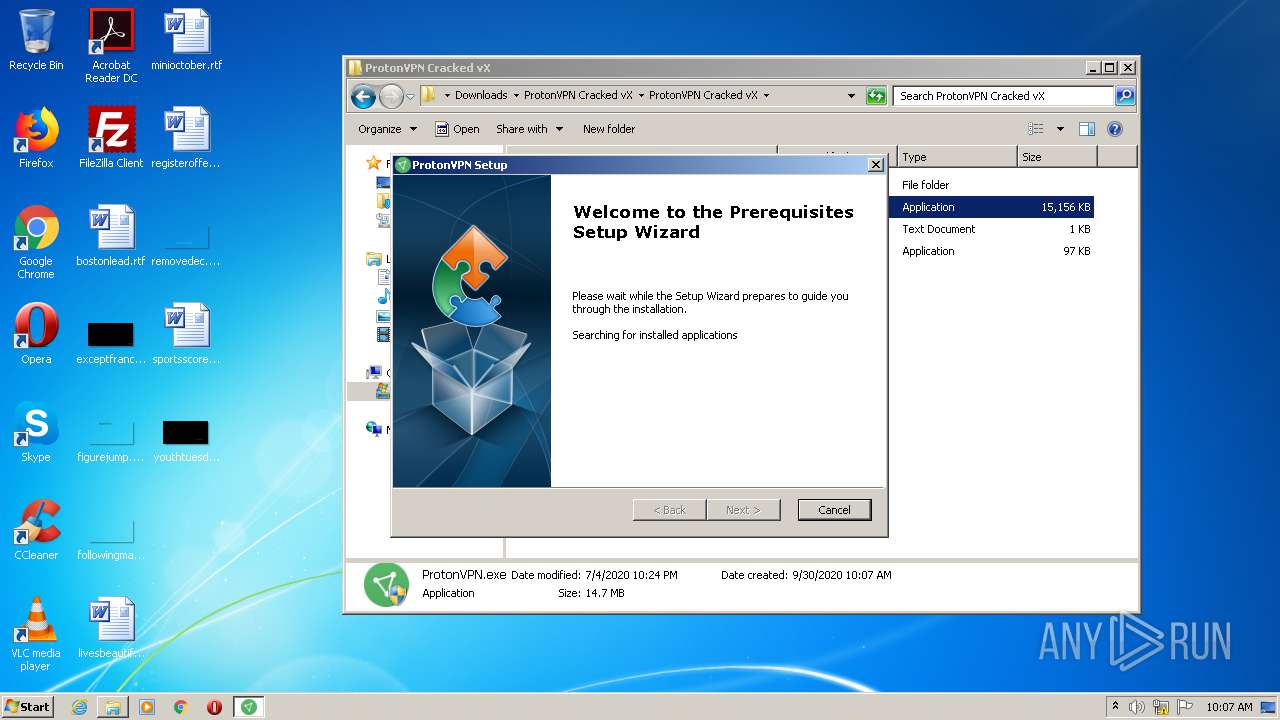
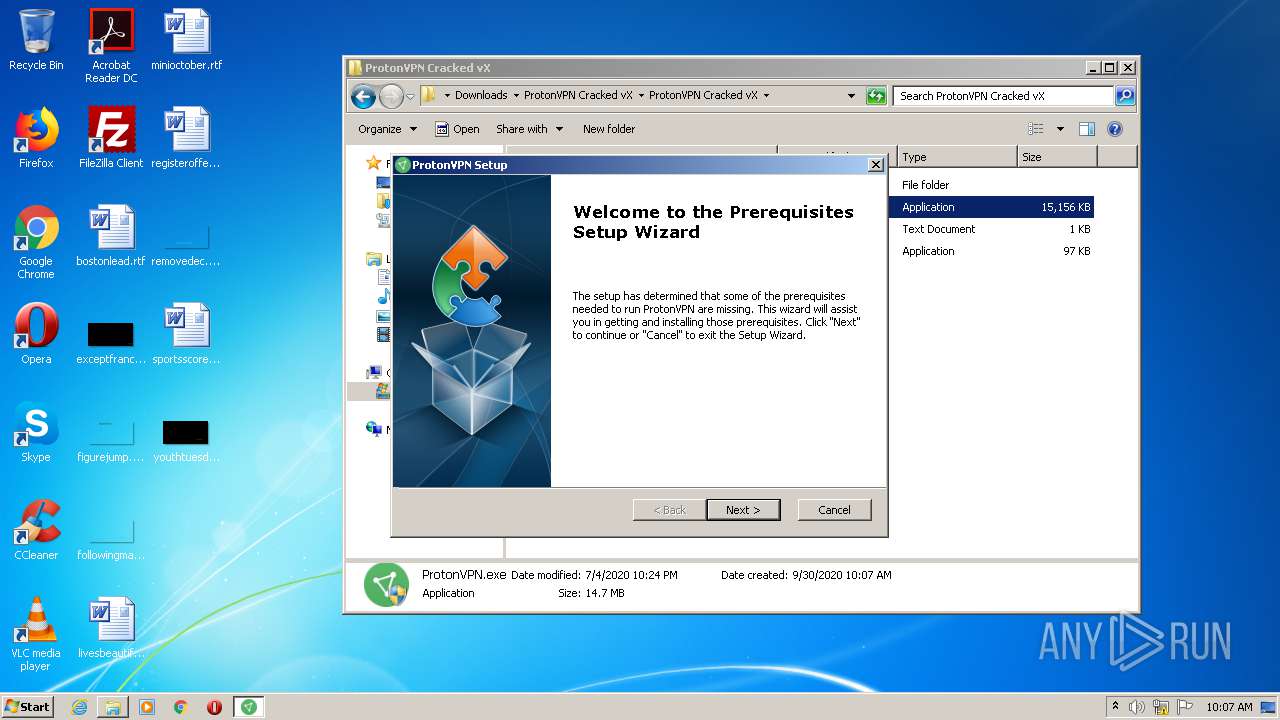
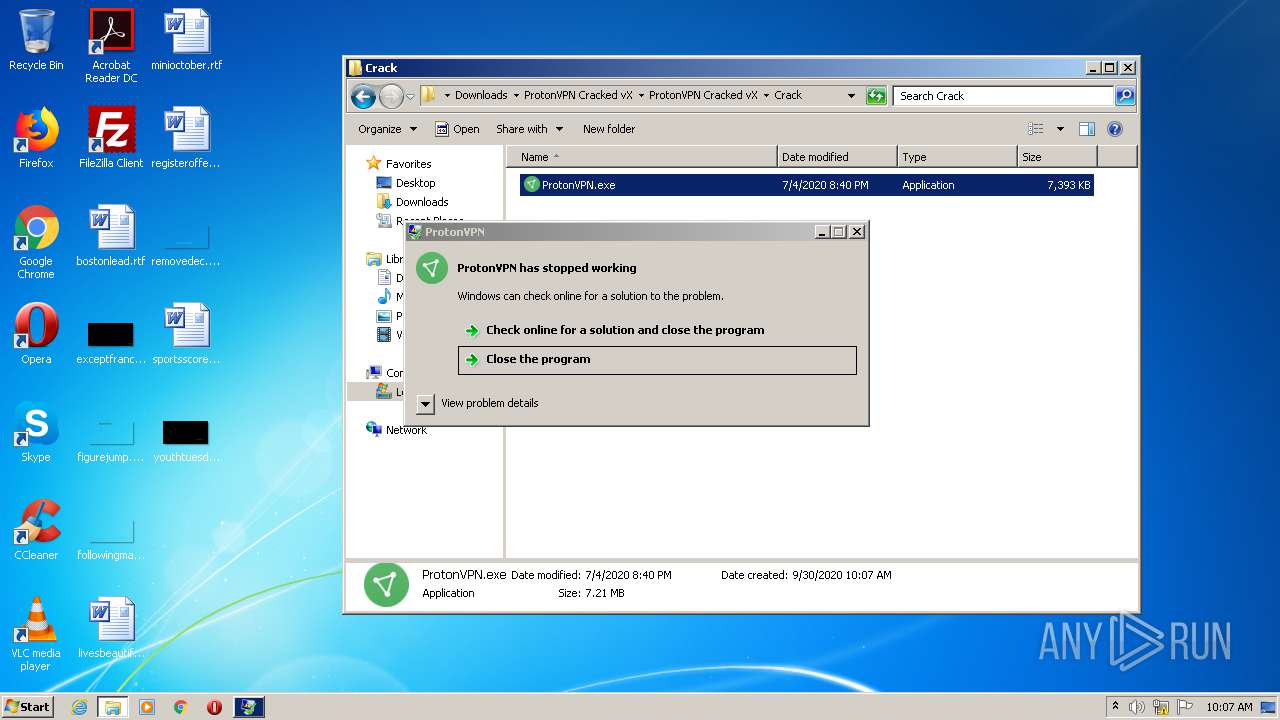
MALICIOUS
Application was dropped or rewritten from another process
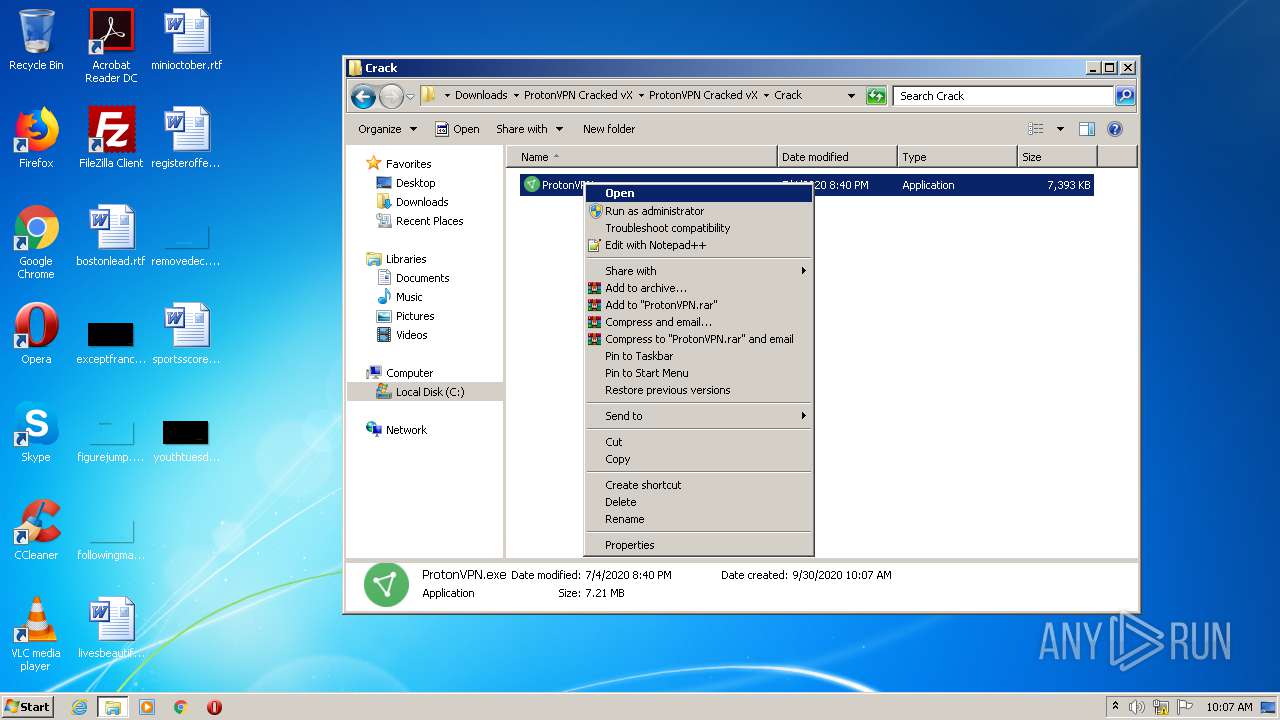
- ProtonVPN.exe (PID: 2424)
- ProtonVPN.exe (PID: 3828)
- vpn wrapper.exe (PID: 3036)
- ProtonVPN.exe (PID: 3172)
- vpn wrapper.exe (PID: 3528)
Changes settings of System certificates
- ProtonVPN.exe (PID: 3828)
Loads dropped or rewritten executable
- ProtonVPN.exe (PID: 3828)
Loads the Task Scheduler DLL interface
- MsiExec.exe (PID: 3208)
- ProtonVPN.exe (PID: 3828)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3424)
- ProtonVPN.exe (PID: 3828)
Adds / modifies Windows certificates
- ProtonVPN.exe (PID: 3828)
Reads Environment values
- MsiExec.exe (PID: 3208)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 3008)
- cmd.exe (PID: 3428)
Starts CMD.EXE for commands execution
- ProtonVPN.exe (PID: 3828)
INFO
Application launched itself
- chrome.exe (PID: 2408)
- msiexec.exe (PID: 2616)
Reads the hosts file
- chrome.exe (PID: 2400)
- chrome.exe (PID: 2408)
Reads Internet Cache Settings
- chrome.exe (PID: 2408)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3424)
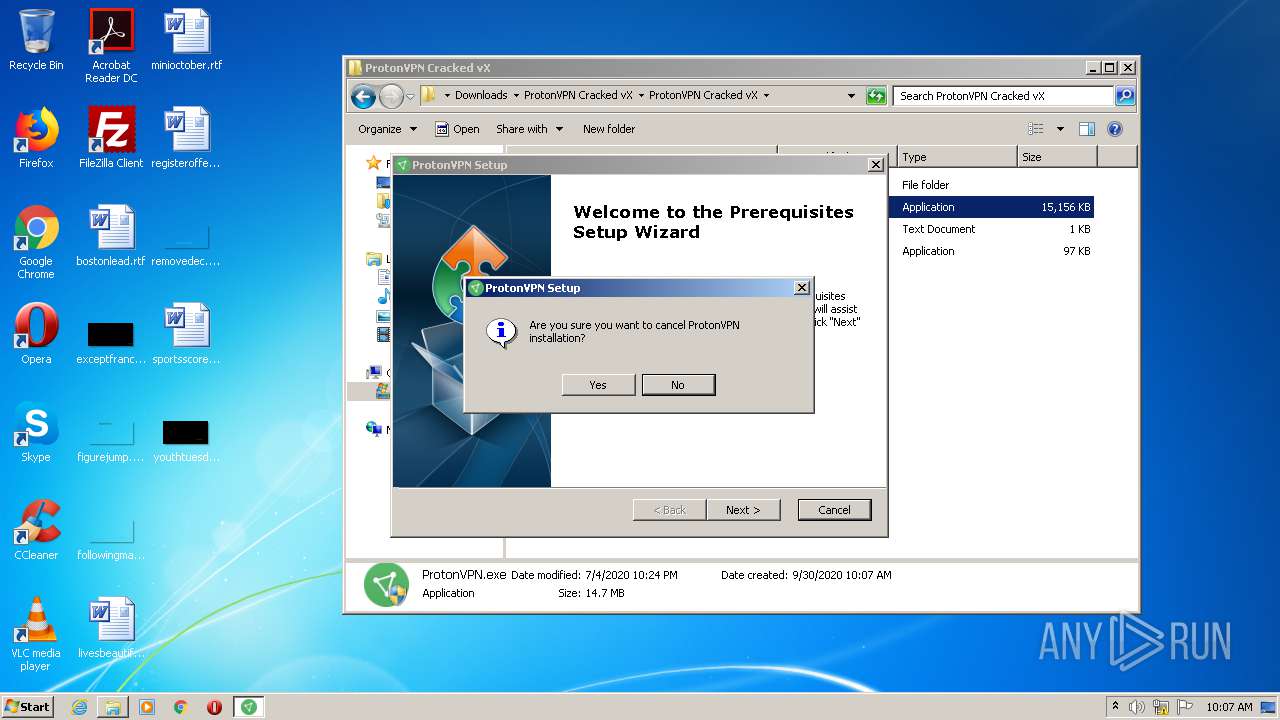
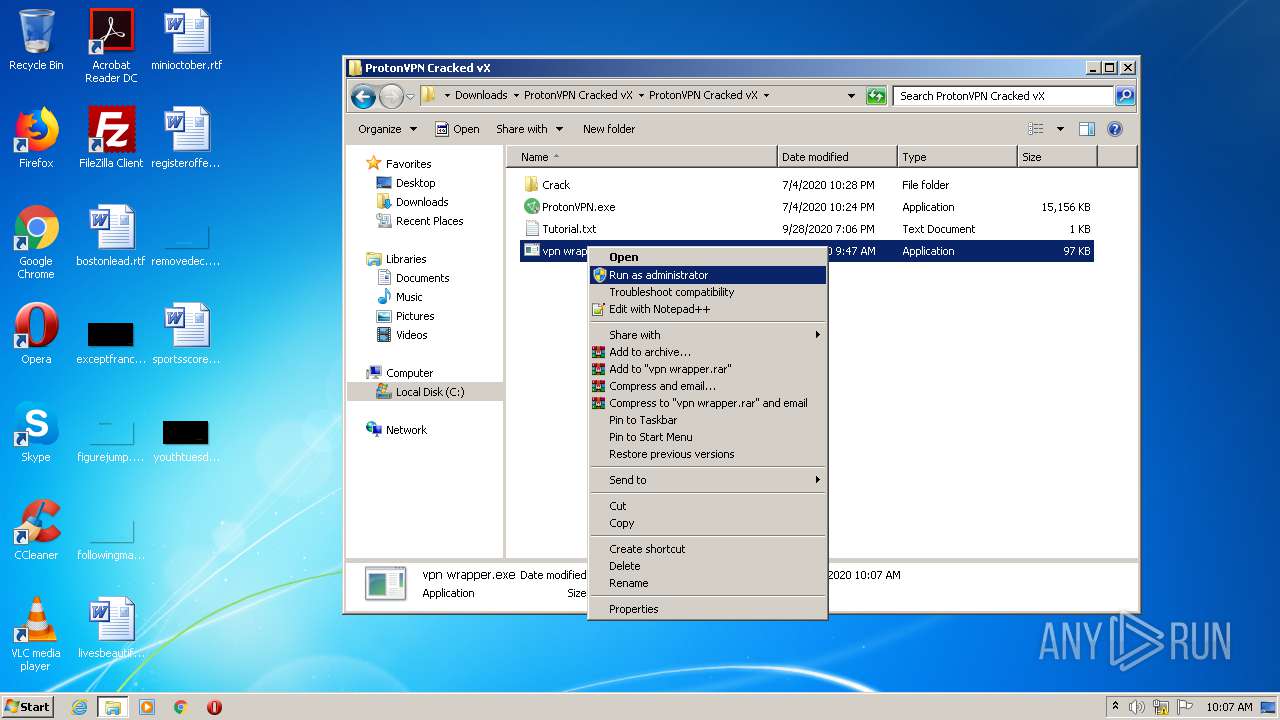
Manual execution by user
- WinRAR.exe (PID: 3424)
- ProtonVPN.exe (PID: 3828)
- ProtonVPN.exe (PID: 2424)
- ProtonVPN.exe (PID: 3172)
- vpn wrapper.exe (PID: 3528)
- vpn wrapper.exe (PID: 3036)
Reads settings of System Certificates
- ProtonVPN.exe (PID: 3828)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
36
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | FindStr "KB2992611" | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,14180777060144869701,17544777938815243426,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6868995792677569275 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3068 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,14180777060144869701,17544777938815243426,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15929183599745490011 --mojo-platform-channel-handle=3856 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 892 | wmic qfe get hotfixid | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1036,14180777060144869701,17544777938815243426,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=7755361088232678721 --mojo-platform-channel-handle=1052 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1856 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,14180777060144869701,17544777938815243426,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=5653267691472824764 --mojo-platform-channel-handle=1304 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,14180777060144869701,17544777938815243426,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2934647022524411427 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2496 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2104 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,14180777060144869701,17544777938815243426,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15370672278048759922 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2244 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,14180777060144869701,17544777938815243426,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14857022217532018066 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2624 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 546
Read events
1 405
Write events
136
Delete events
5
Modification events
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (960) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2408-13245930316388500 |
Value: 259 | |||
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3228-13245745346152343 |
Value: 0 | |||
| (PID) Process: | (2408) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
10
Suspicious files
48
Text files
119
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F744A4D-968.pma | — | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\5af4aef4-c16a-4140-8392-1a4b9a2f54d2.tmp | — | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000046.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF227980.TMP | text | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF2279af.TMP | text | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2408 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
33
DNS requests
16
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2400 | chrome.exe | 172.217.22.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2400 | chrome.exe | 172.64.139.6:443 | anonfiles.com | Cloudflare Inc | US | suspicious |
2400 | chrome.exe | 172.217.16.205:443 | accounts.google.com | Google Inc. | US | whitelisted |
2400 | chrome.exe | 13.226.155.124:443 | counterry.club | — | US | whitelisted |
2400 | chrome.exe | 143.204.94.127:443 | providentsopport.site | — | US | unknown |
2400 | chrome.exe | 217.64.149.25:443 | cdn-113.anonfiles.com | — | IR | unknown |
2400 | chrome.exe | 13.225.73.42:443 | www.xvbelink.com | — | US | suspicious |
2400 | chrome.exe | 216.58.206.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2400 | chrome.exe | 216.58.210.14:443 | clients2.google.com | Google Inc. | US | whitelisted |
2400 | chrome.exe | 172.217.23.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
anonfiles.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
vjs.zencdn.net |
| whitelisted |
djv99sxoqpv11.cloudfront.net |
| shared |
baconaces.pro |
| shared |
counterry.club |
| whitelisted |
leneshedhous.club |
| suspicious |
providentsopport.site |
| whitelisted |
cdn-113.anonfiles.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2400 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM CLOSEWAIT FIN out of window |