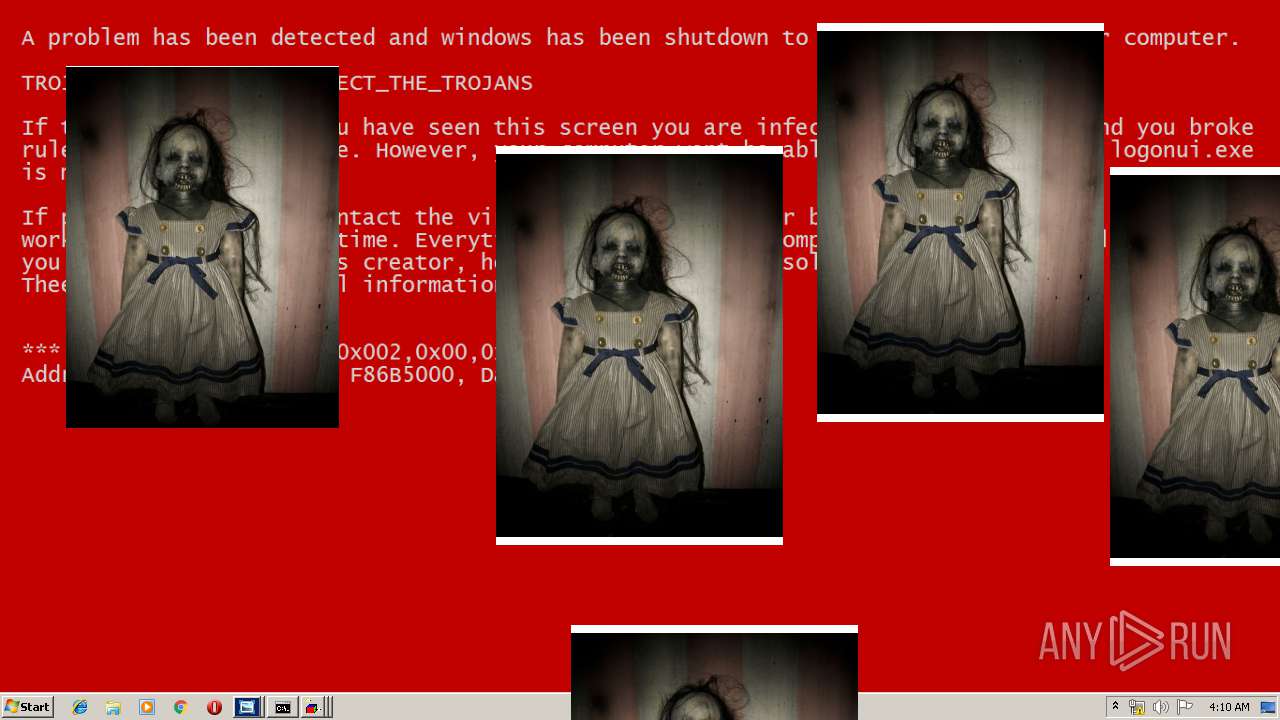
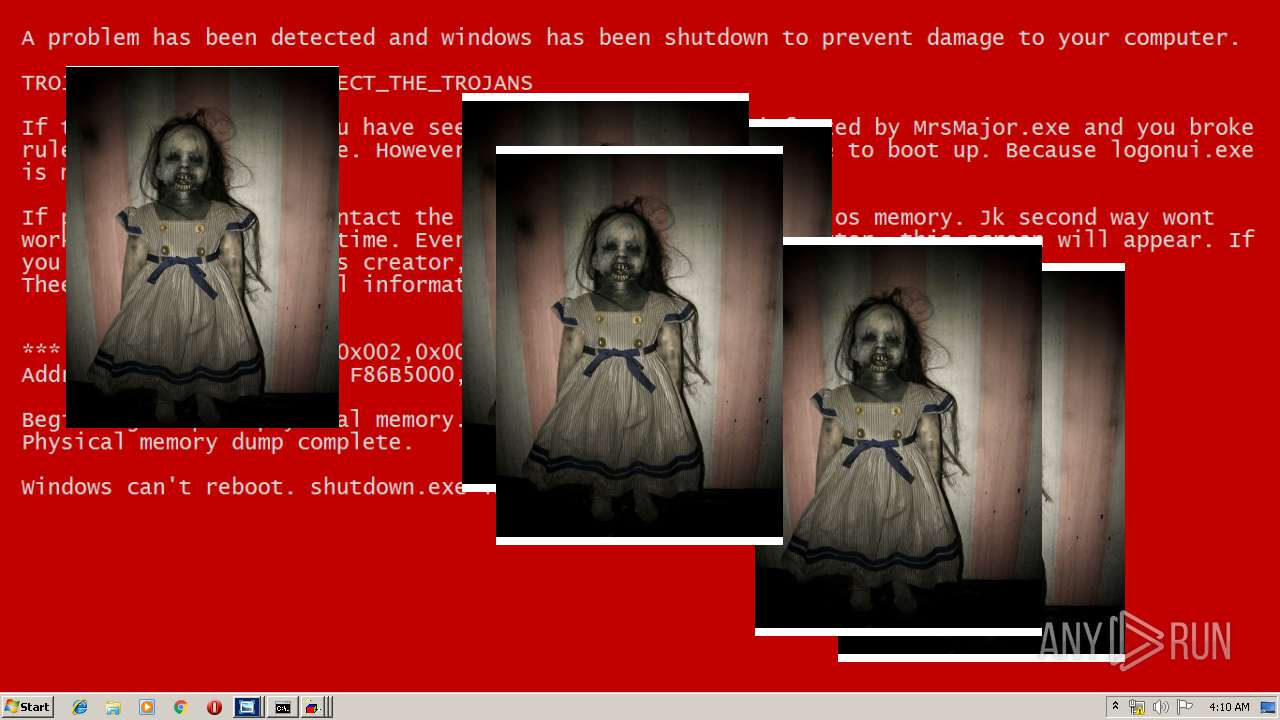
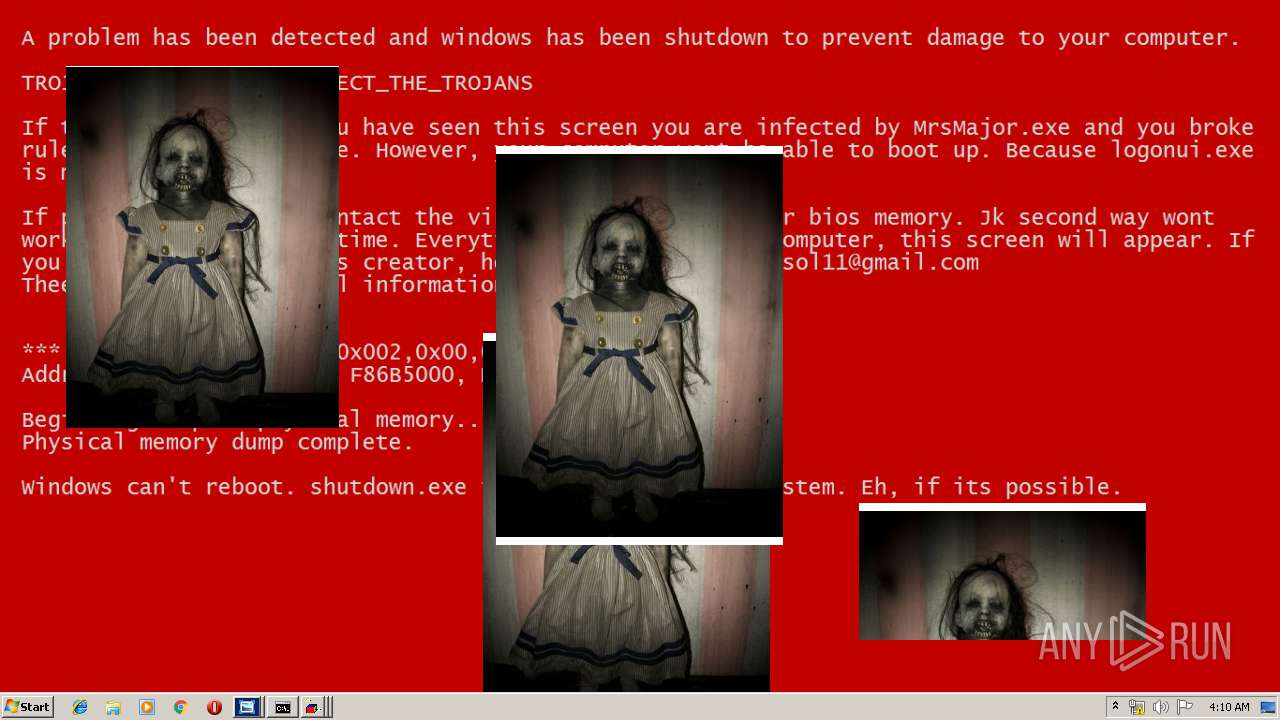
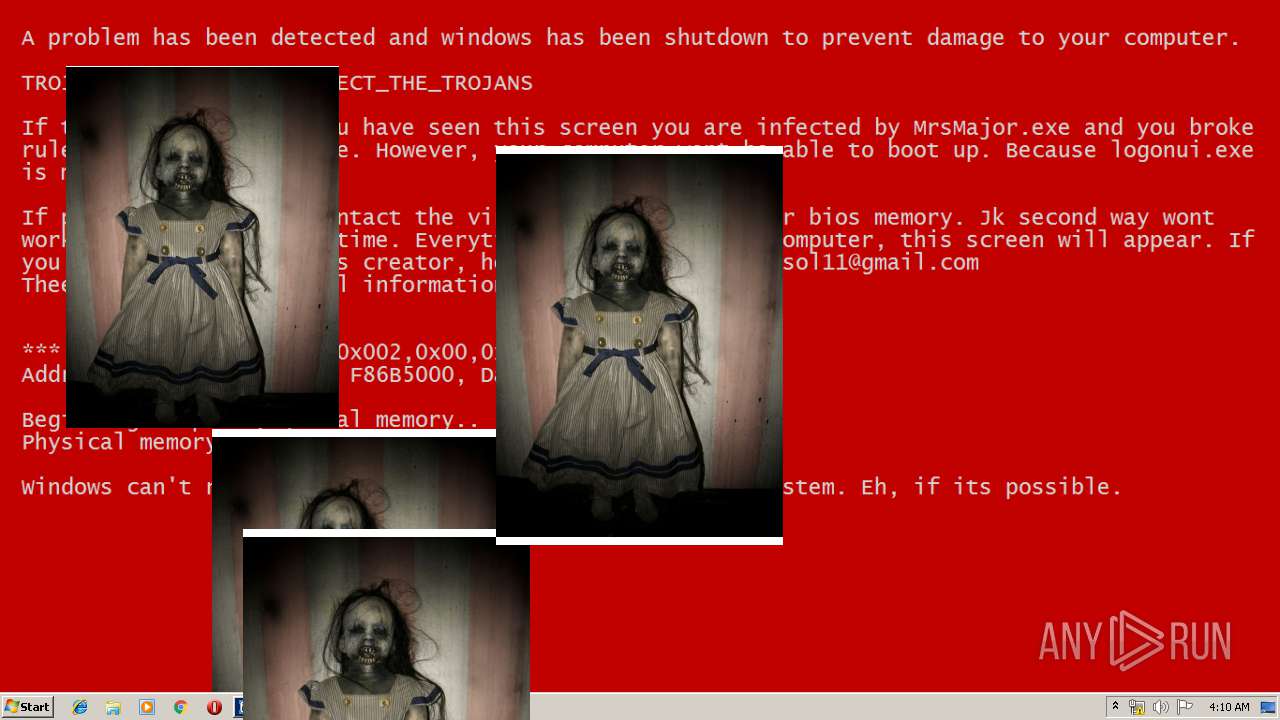
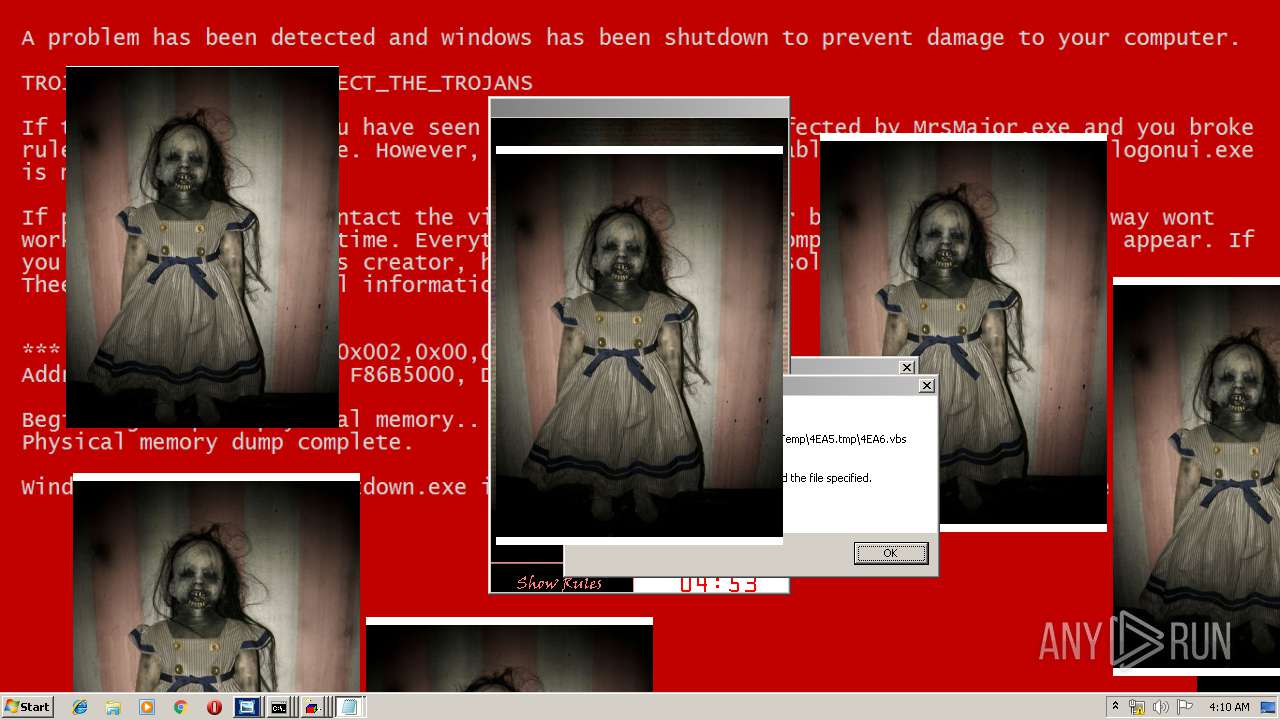
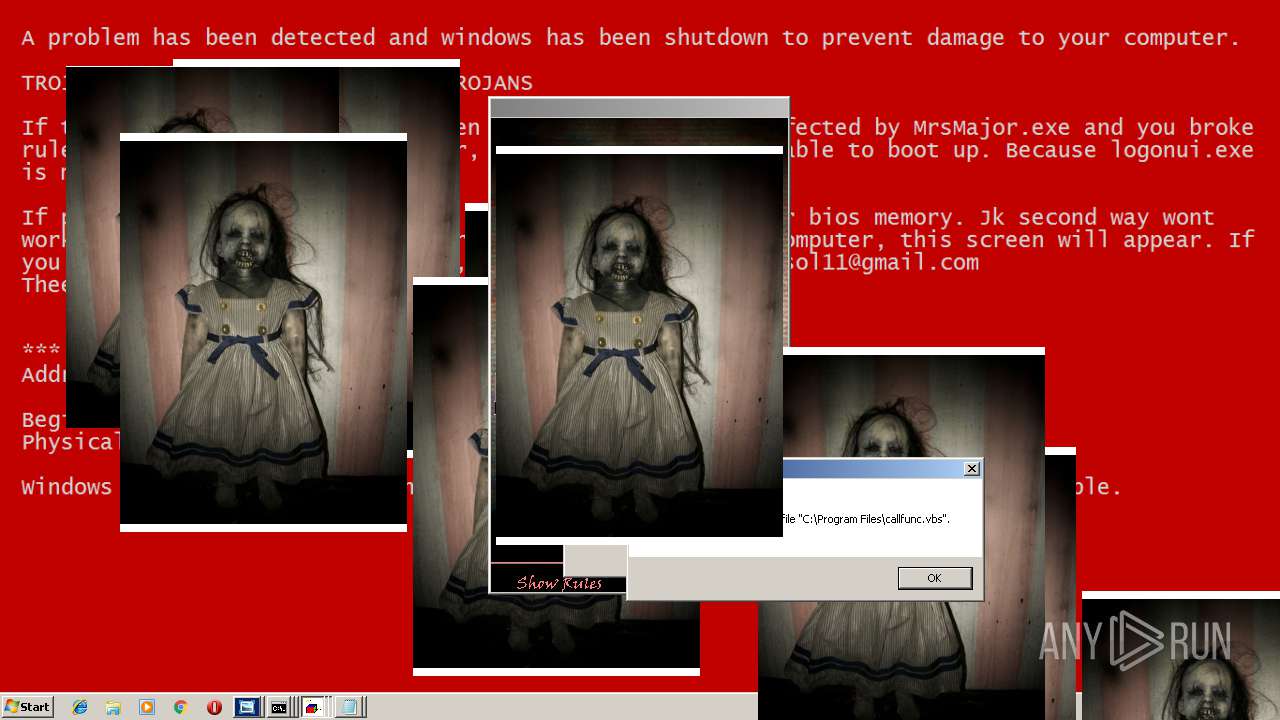
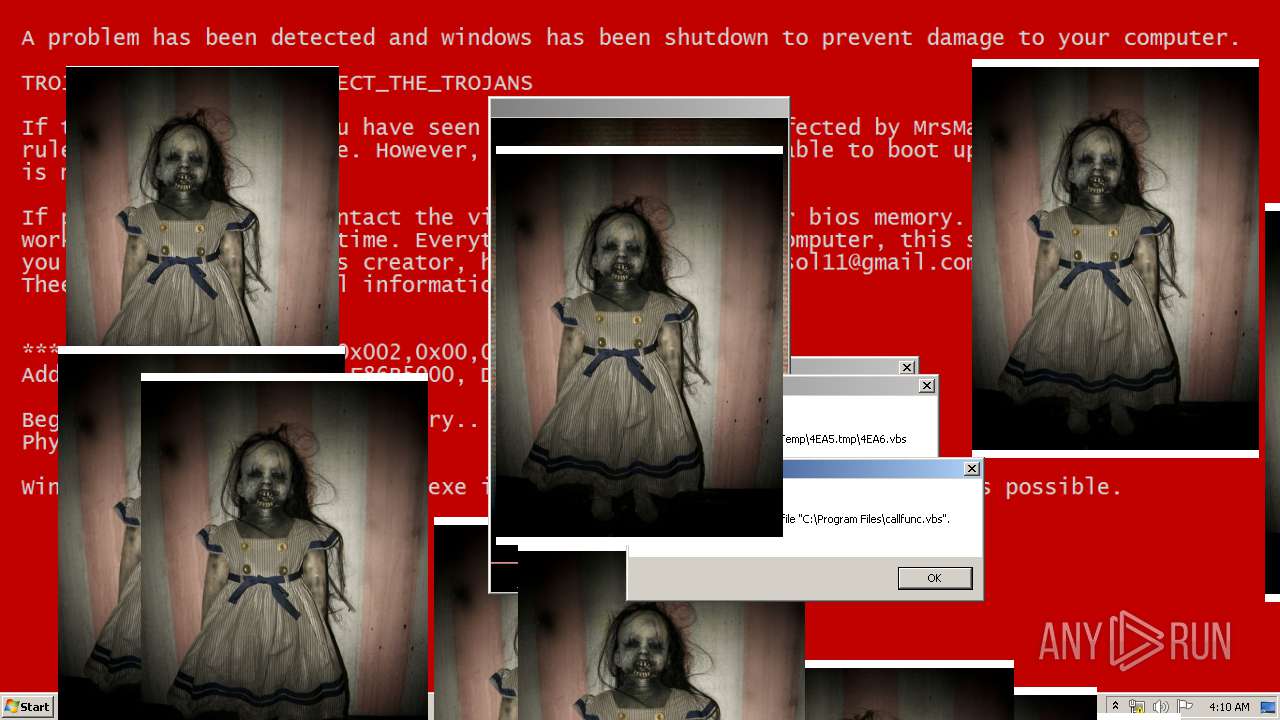
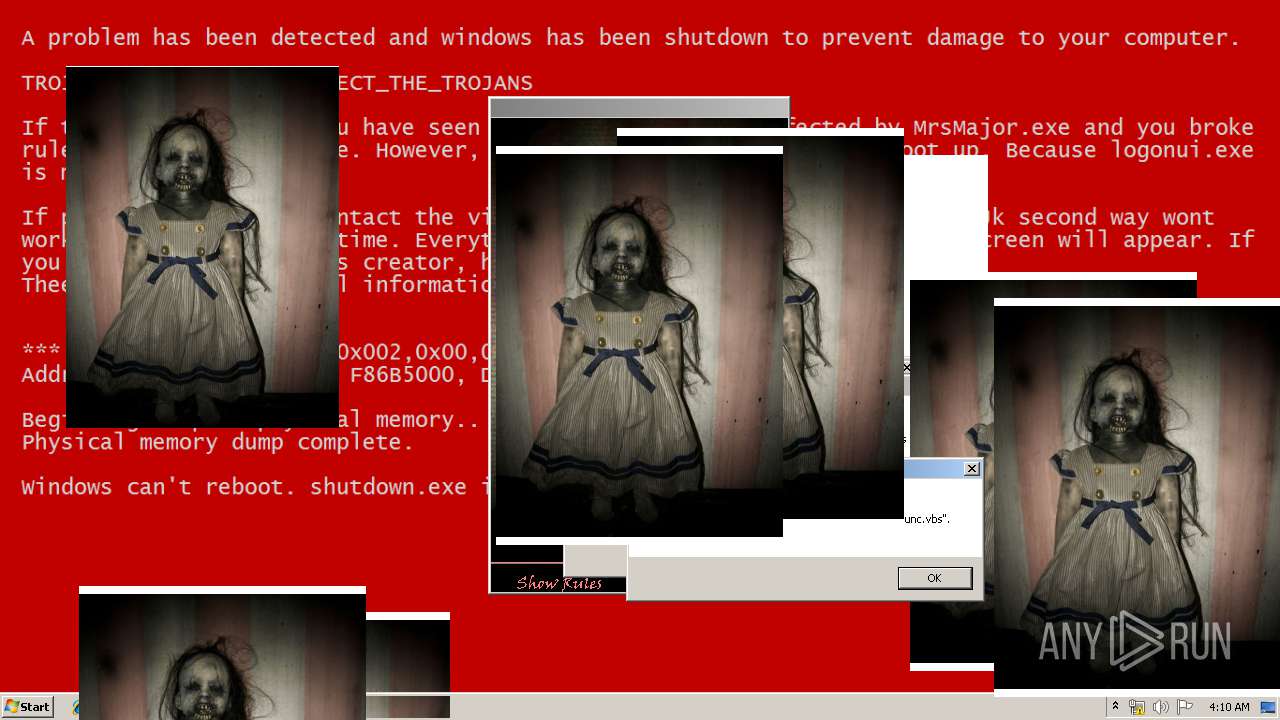
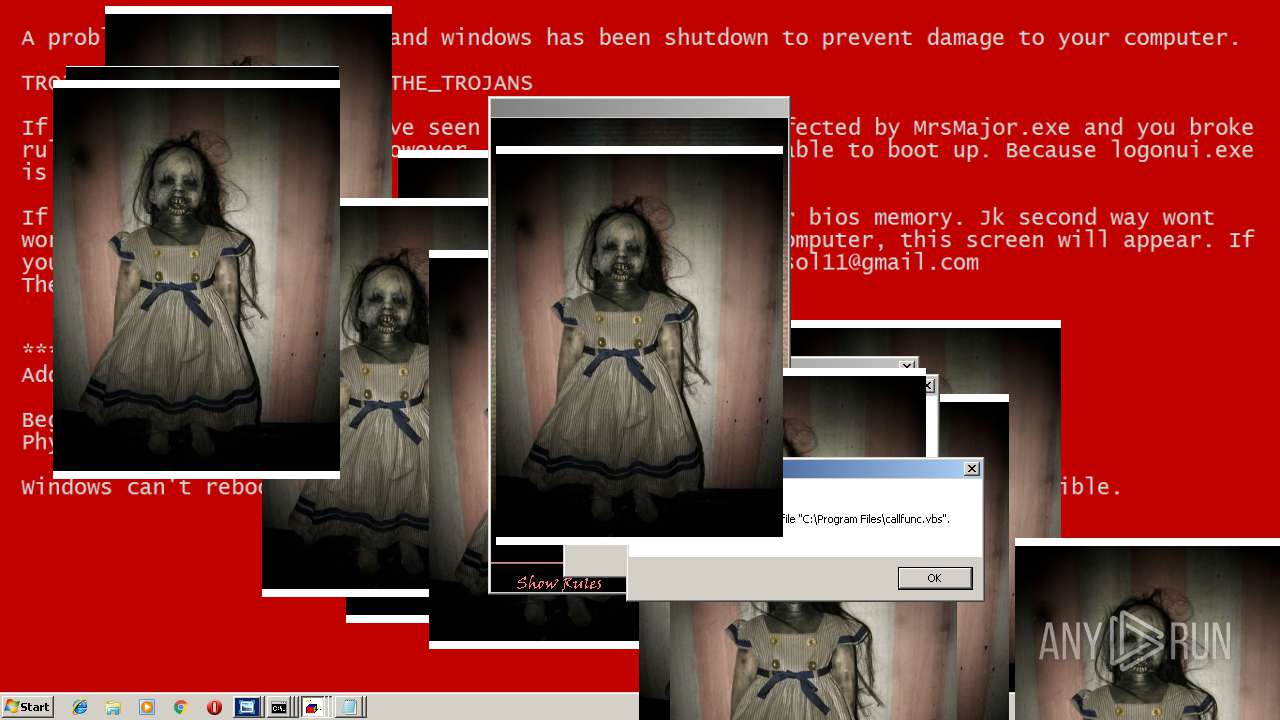
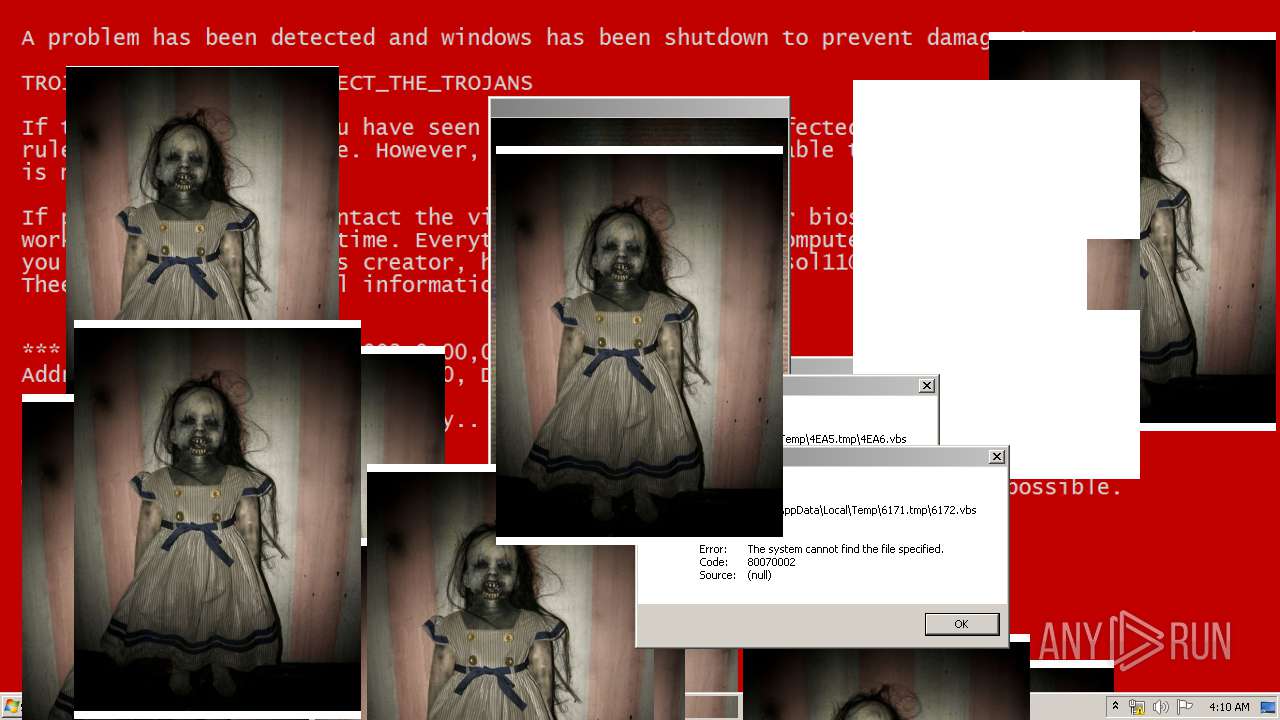
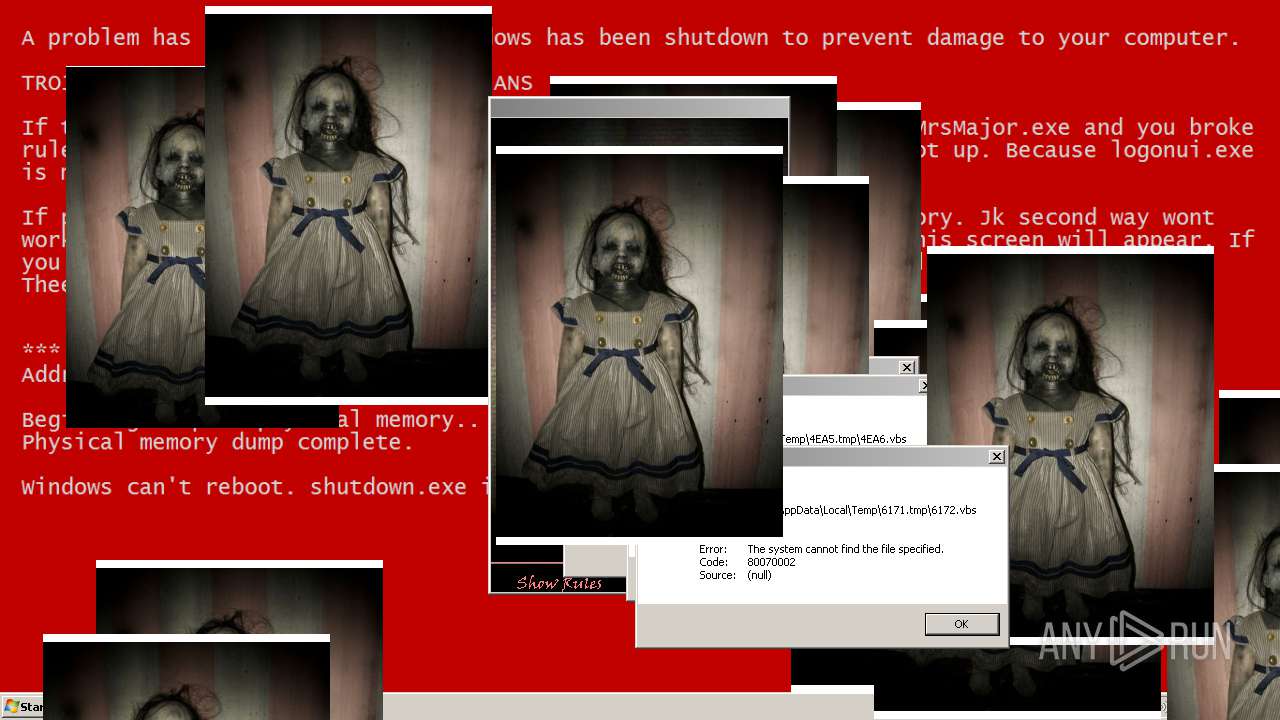
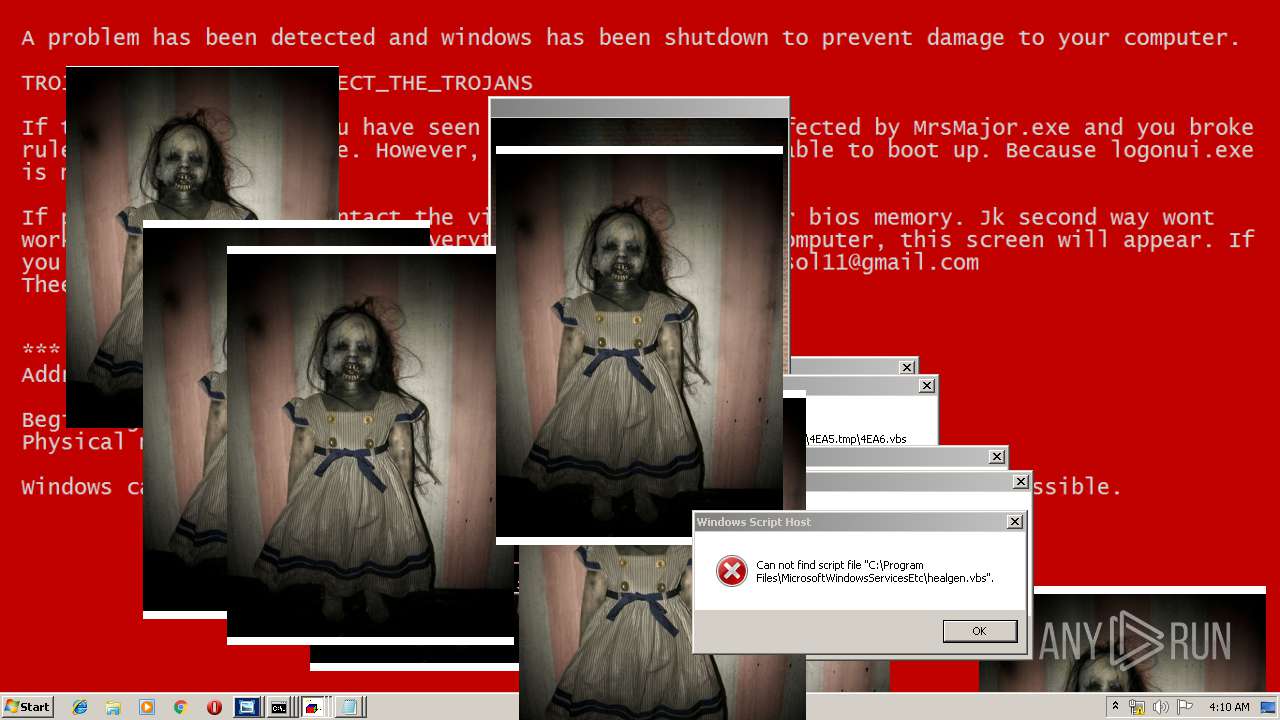
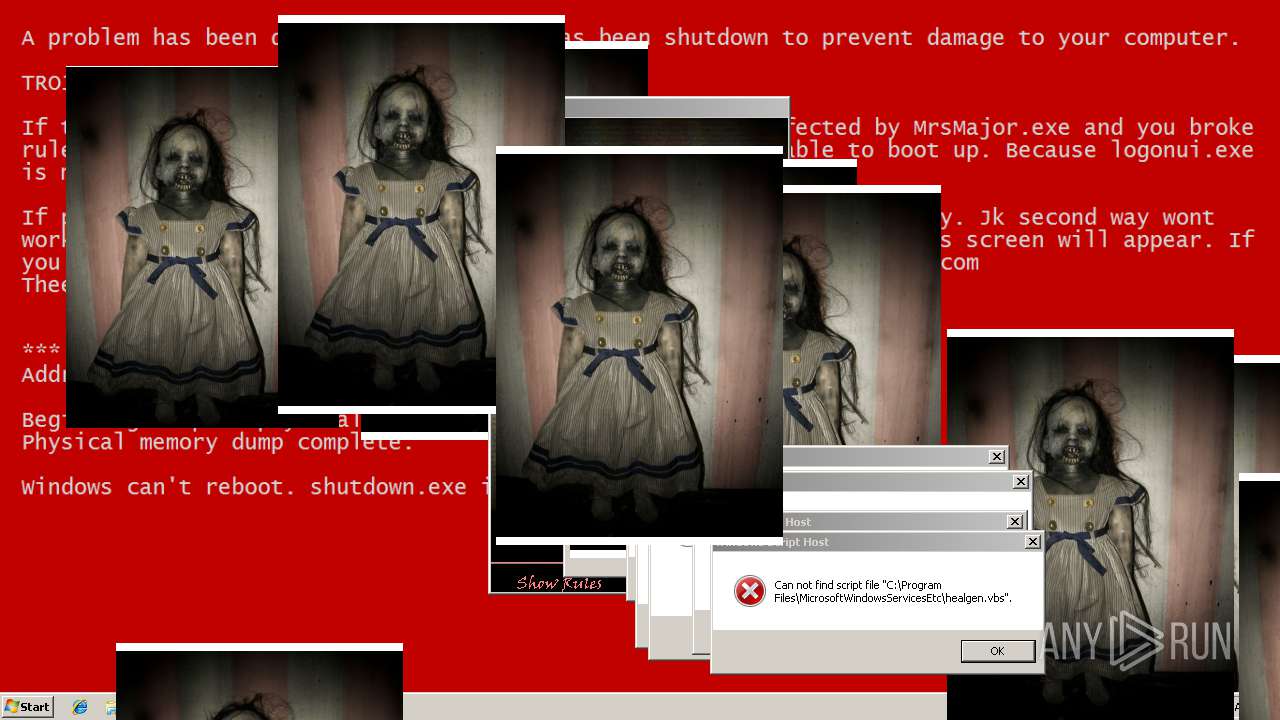
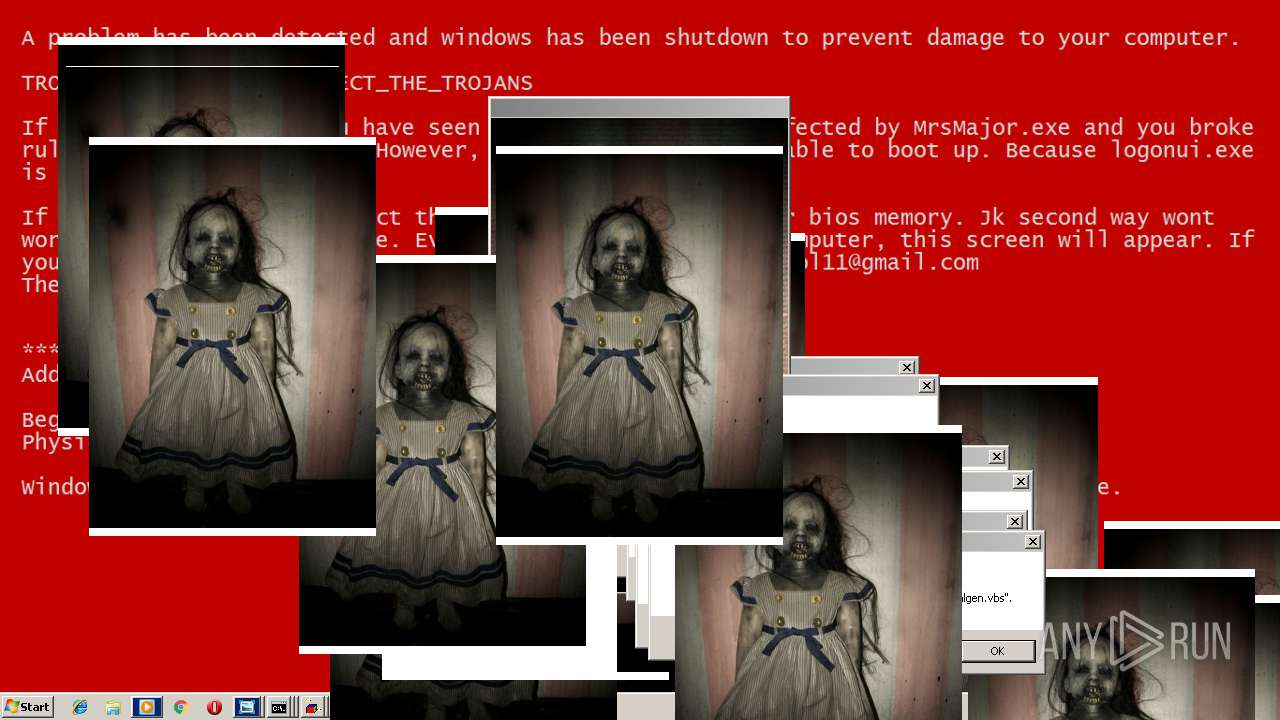
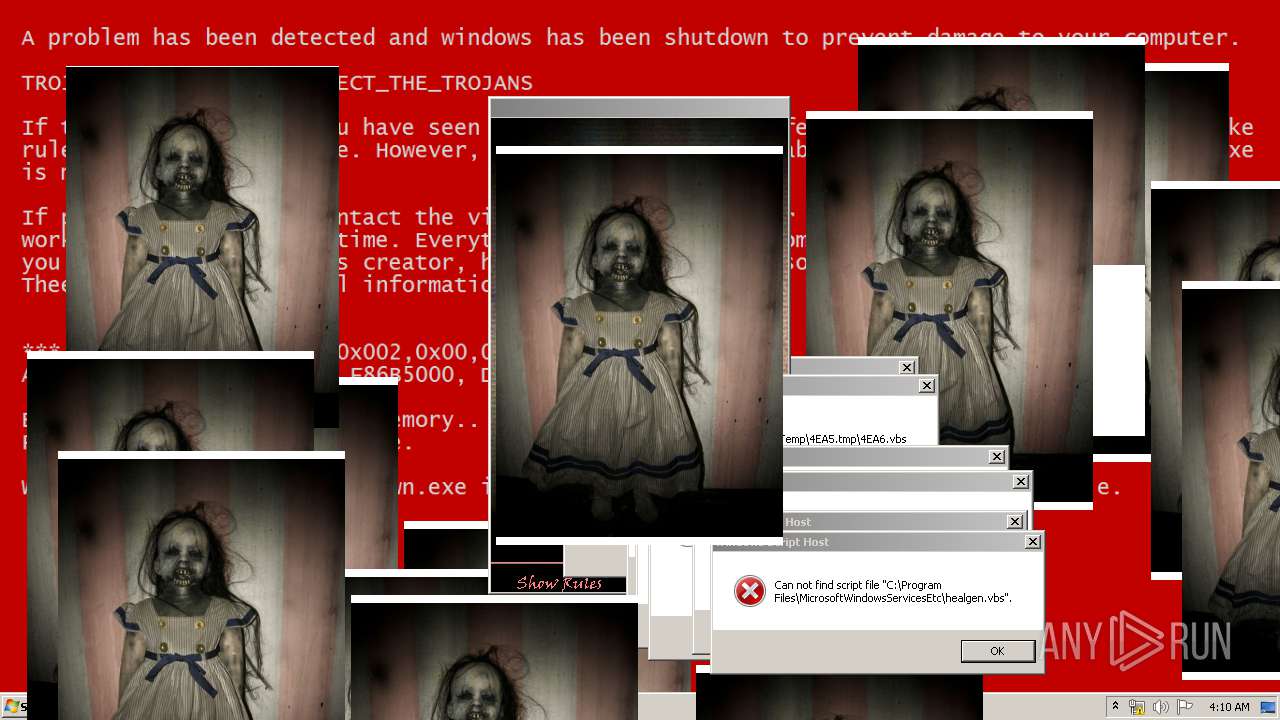
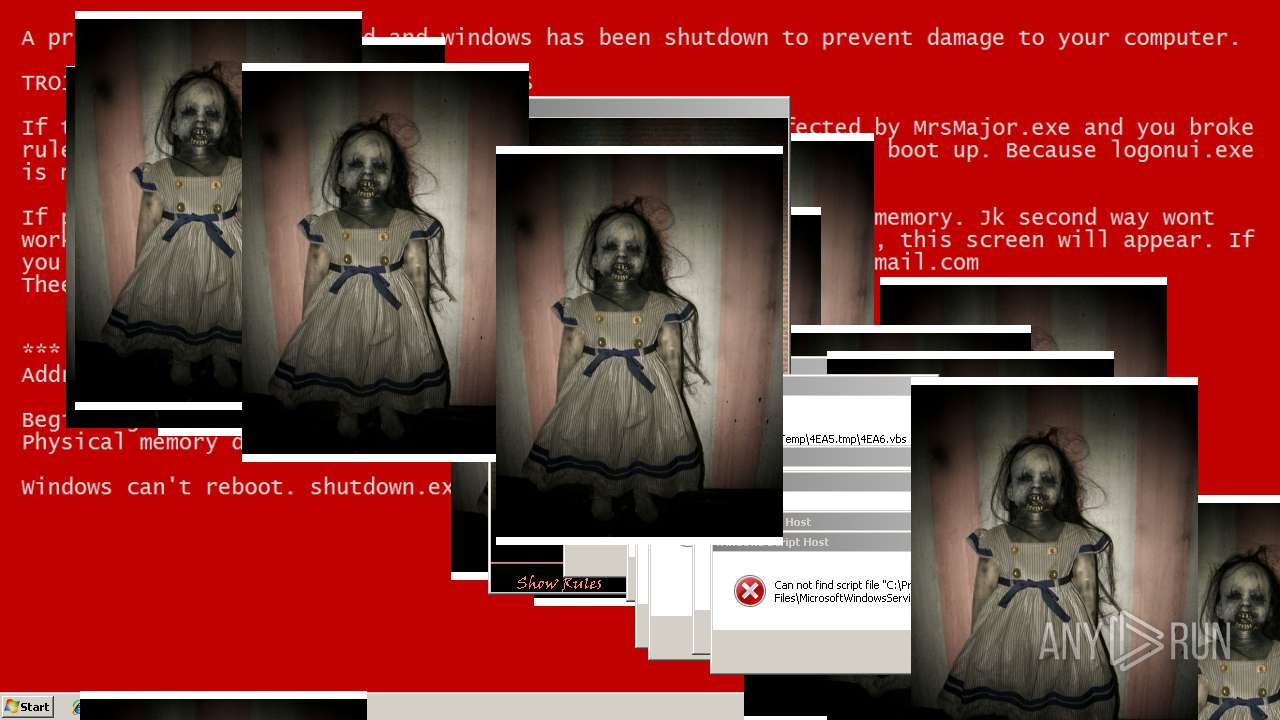
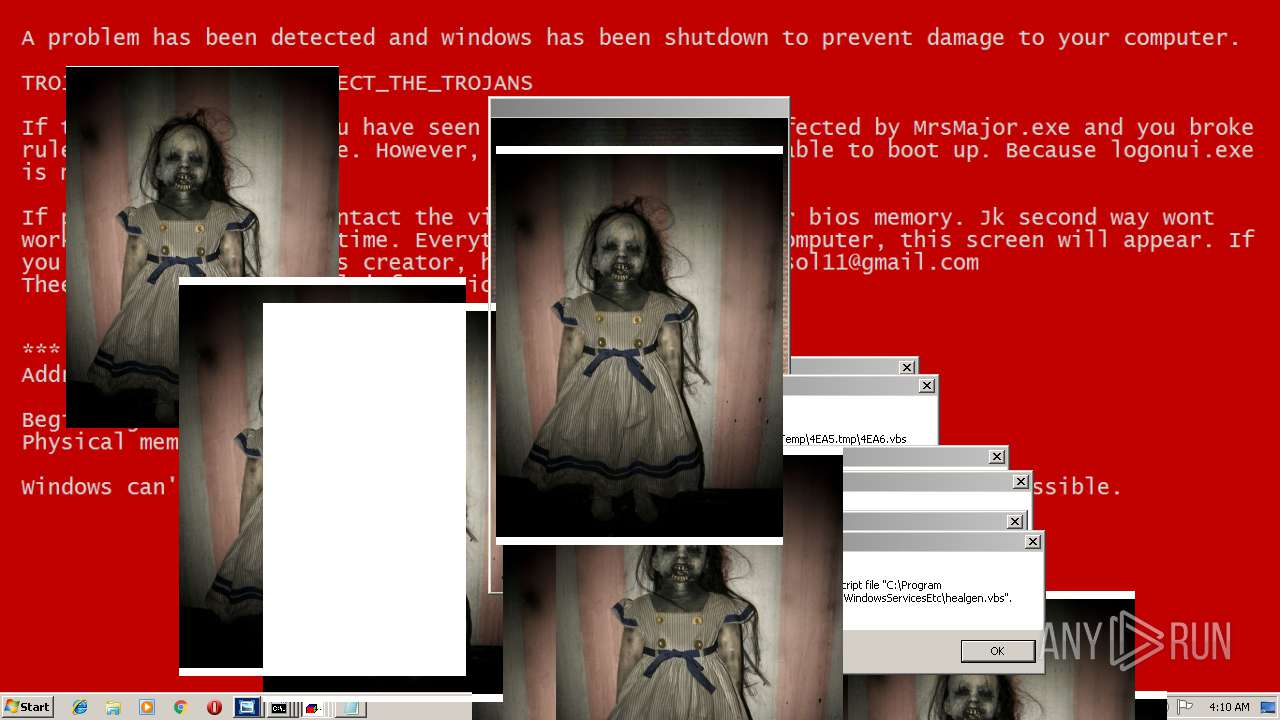
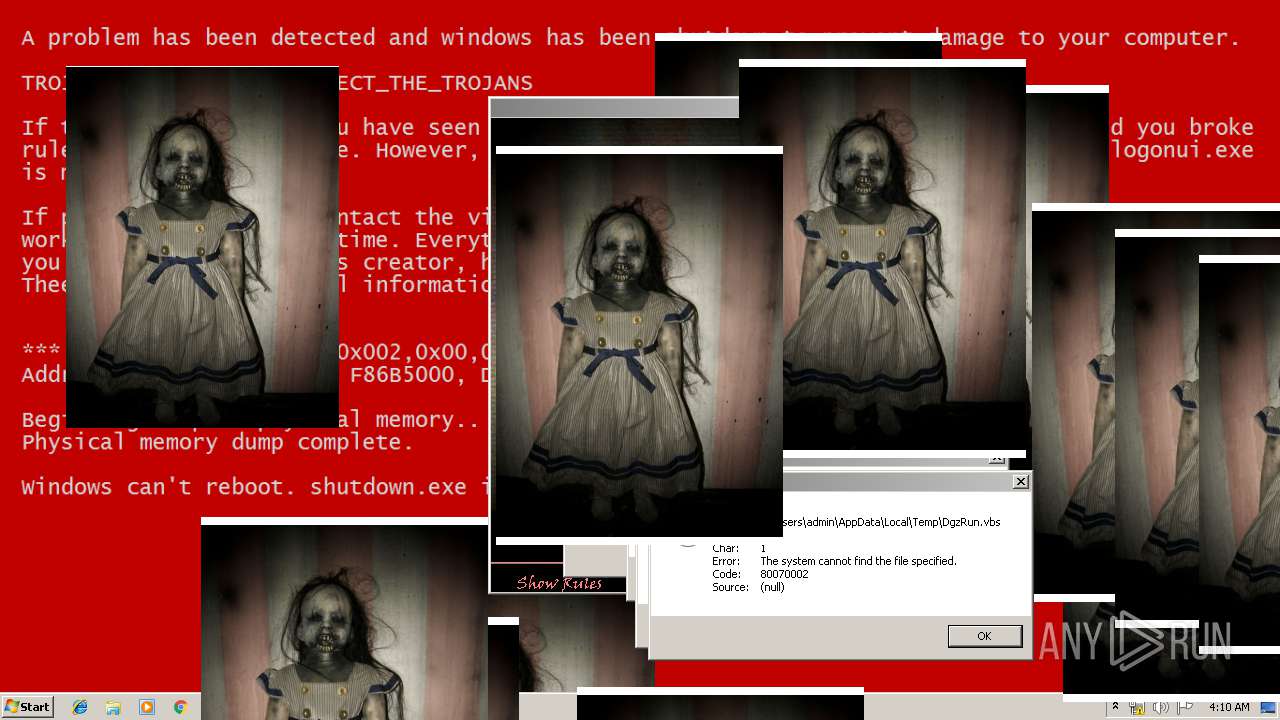
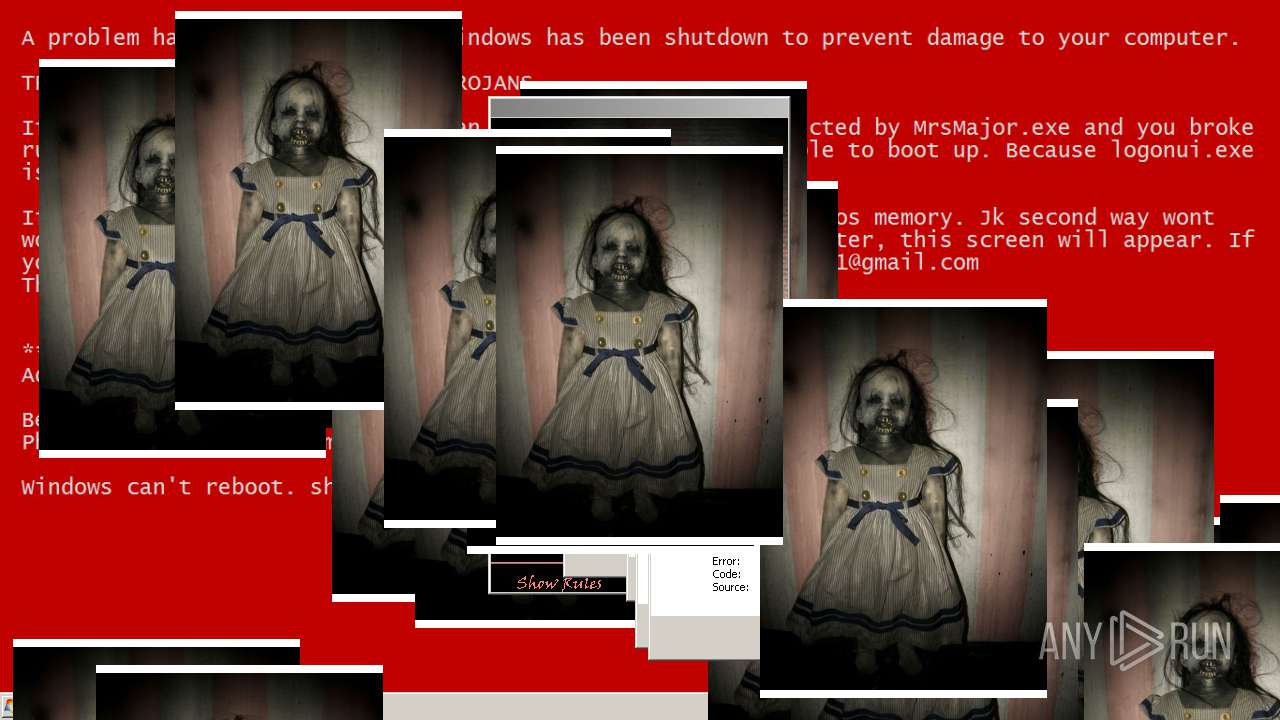
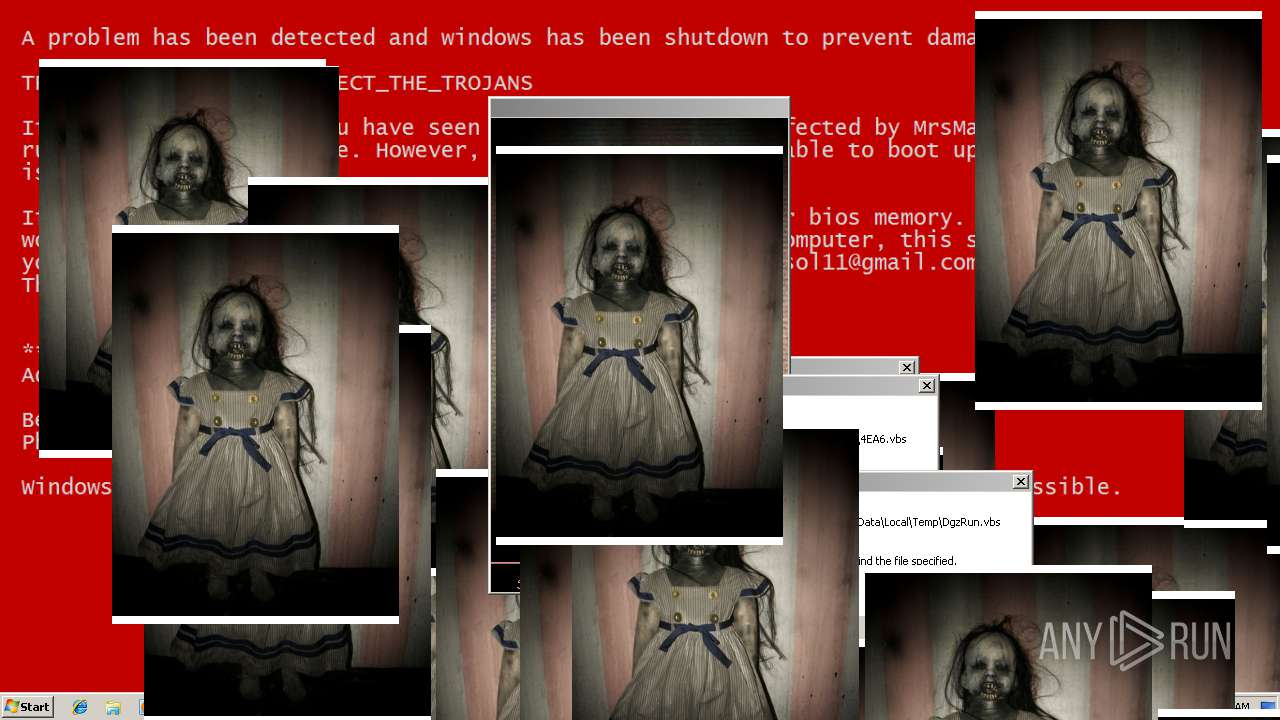
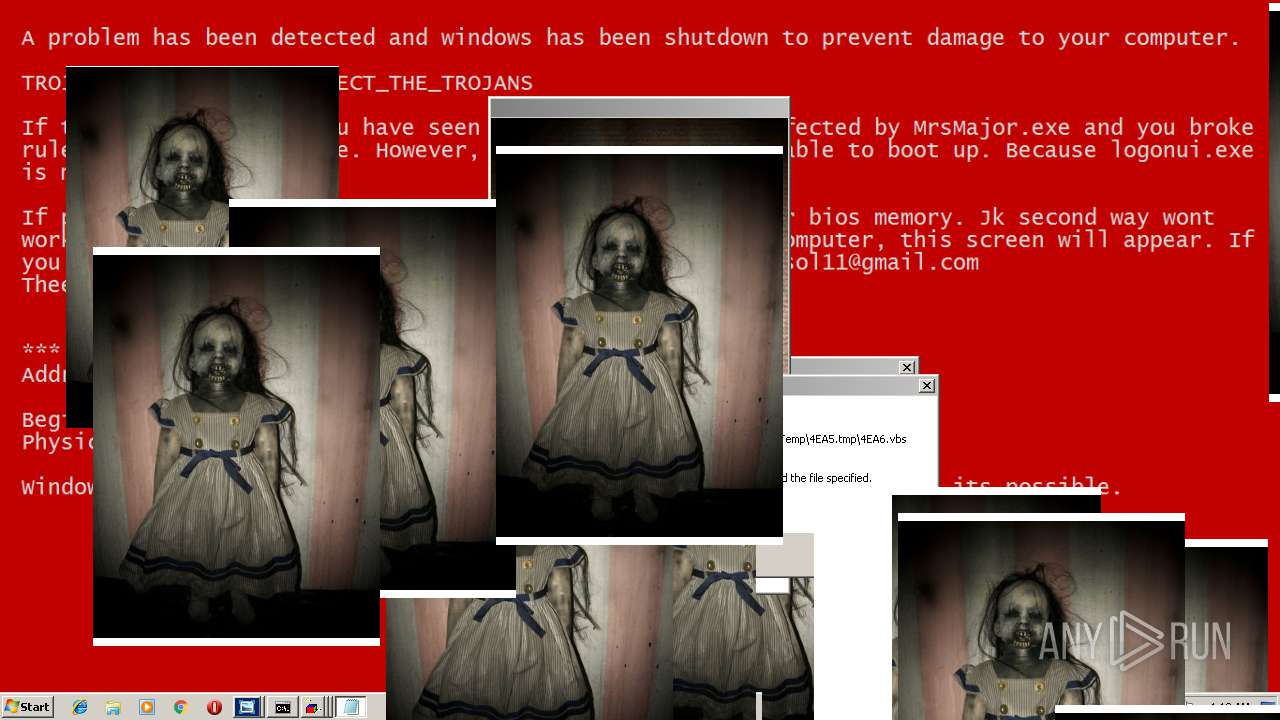
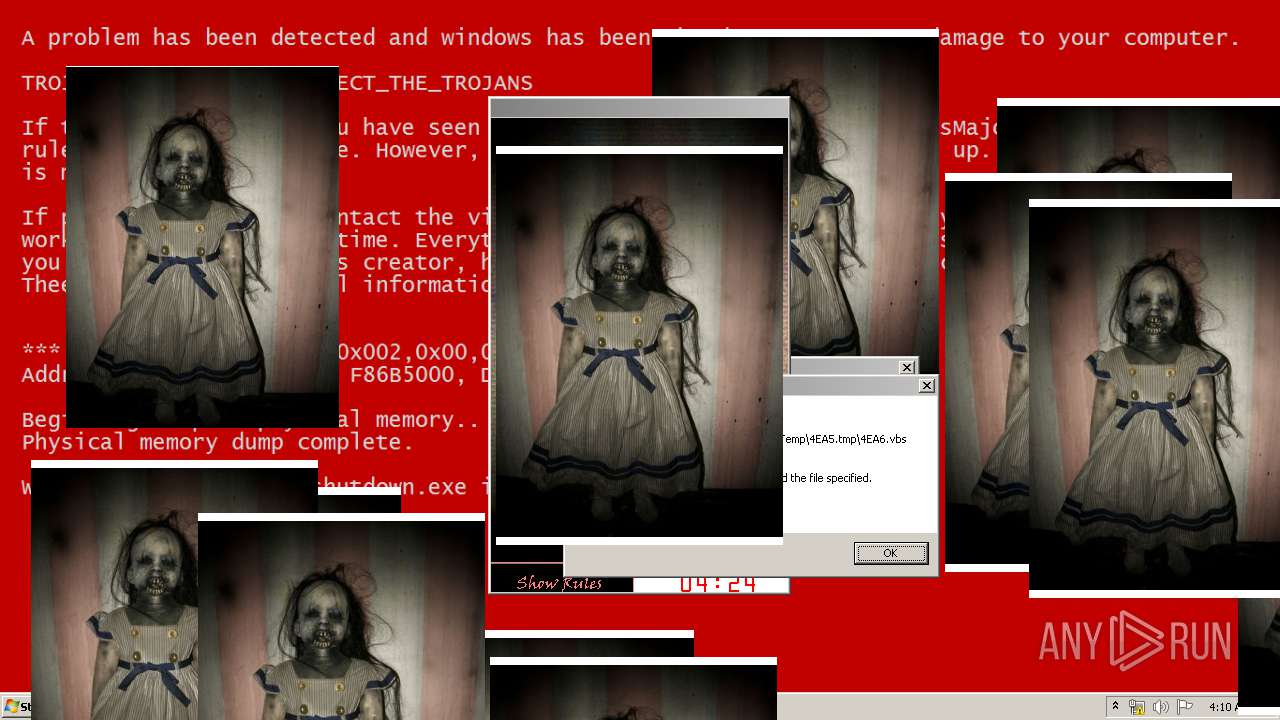
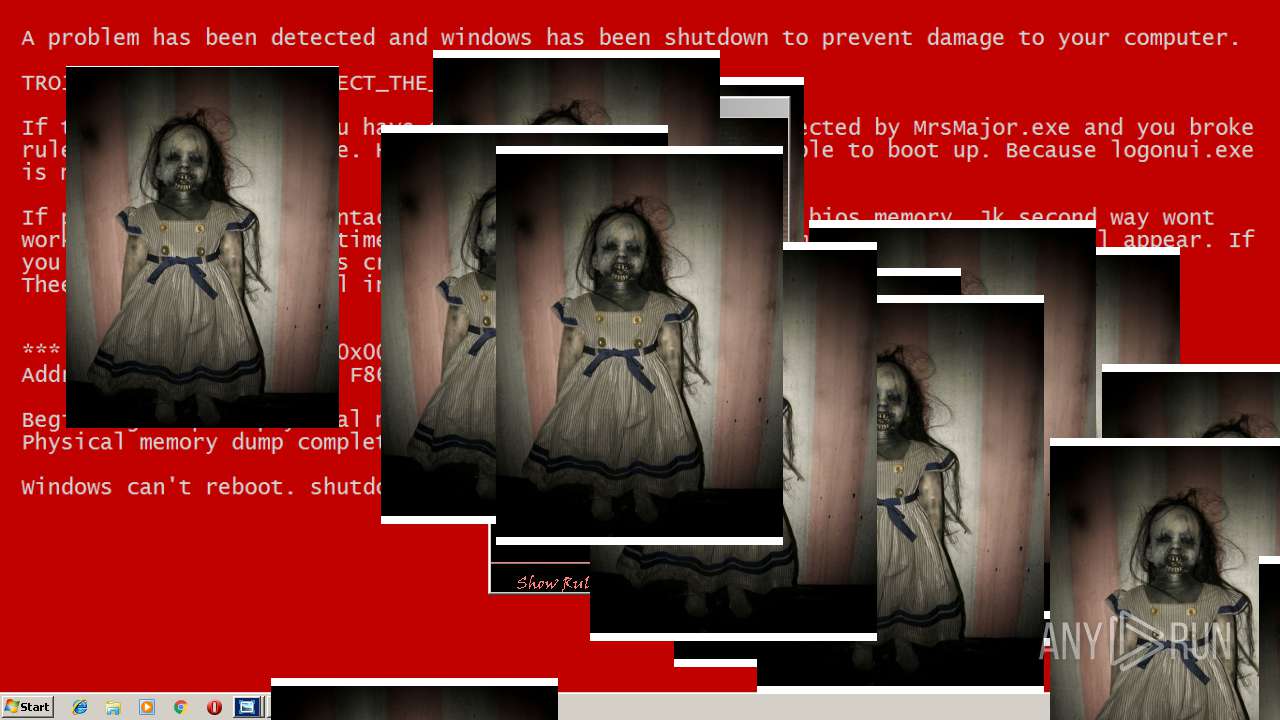
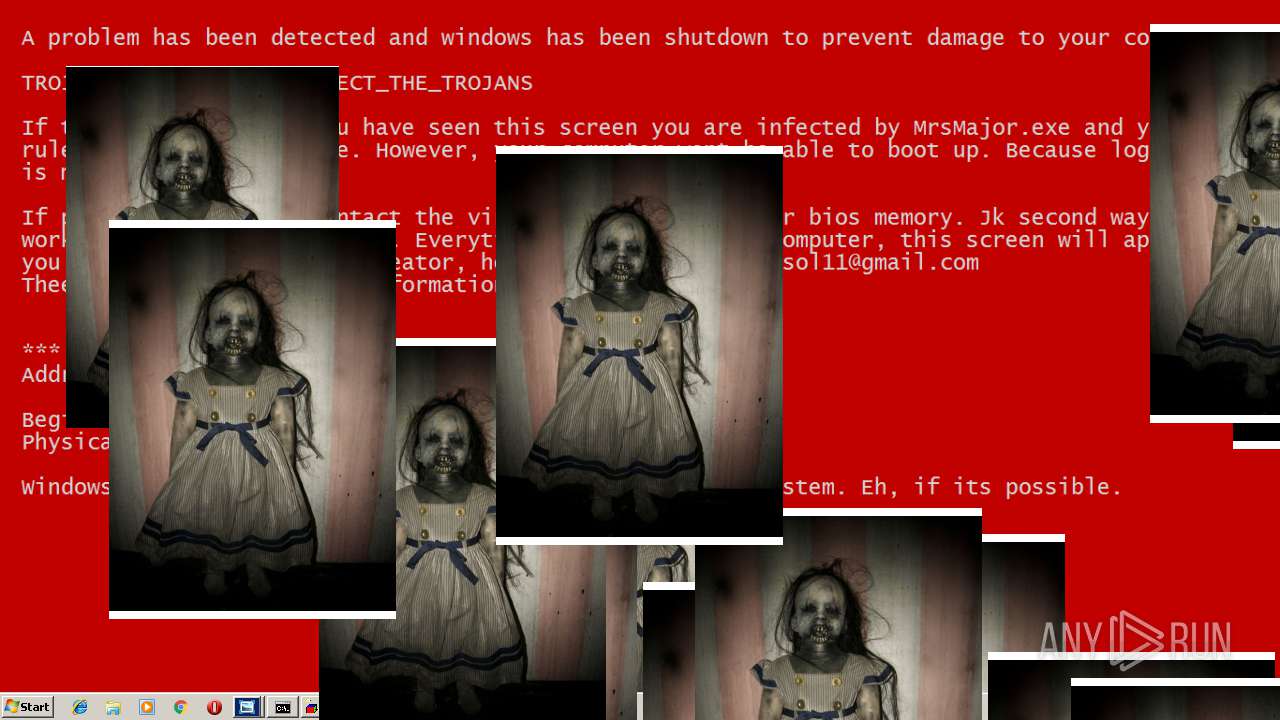
| File name: | Test.exe |
| Full analysis: | https://app.any.run/tasks/bc1e2159-b0ea-4763-a59e-134cac97ecc5 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2019, 03:09:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C55A7051AD16A380F811AC27172626AD |
| SHA1: | 21065853915127F3ABDE6DE2B0812DE2BED4FF1C |
| SHA256: | 27256EEA20C2C78C47FF3065234A47E2D8A6F2BDBDC2994416A35C0462195281 |
| SSDEEP: | 196608:L0ptmTLSdWuRc+F/vzCbAnMNVcnYNAXKgIKDG8J1uzPECyQ5GnwjTnBSalqt7FoU:LmtmawuRcurGIYNCiQ1F/3wjzUano7JN |
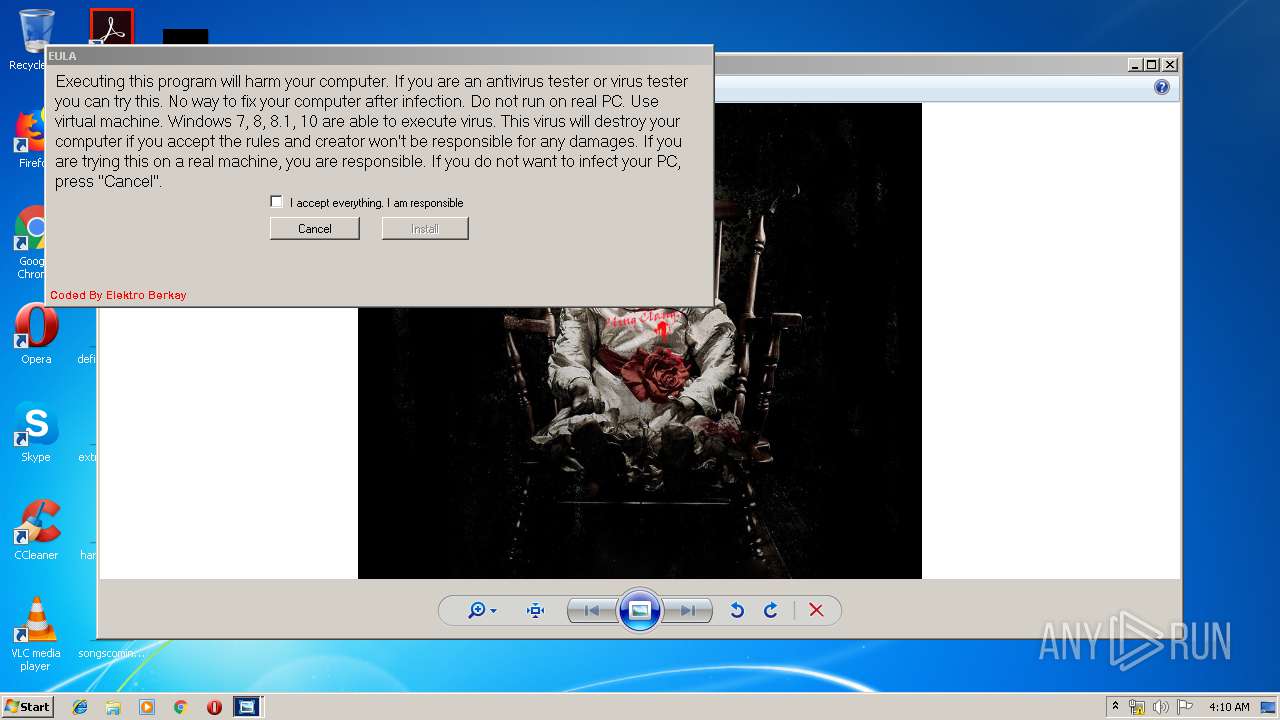
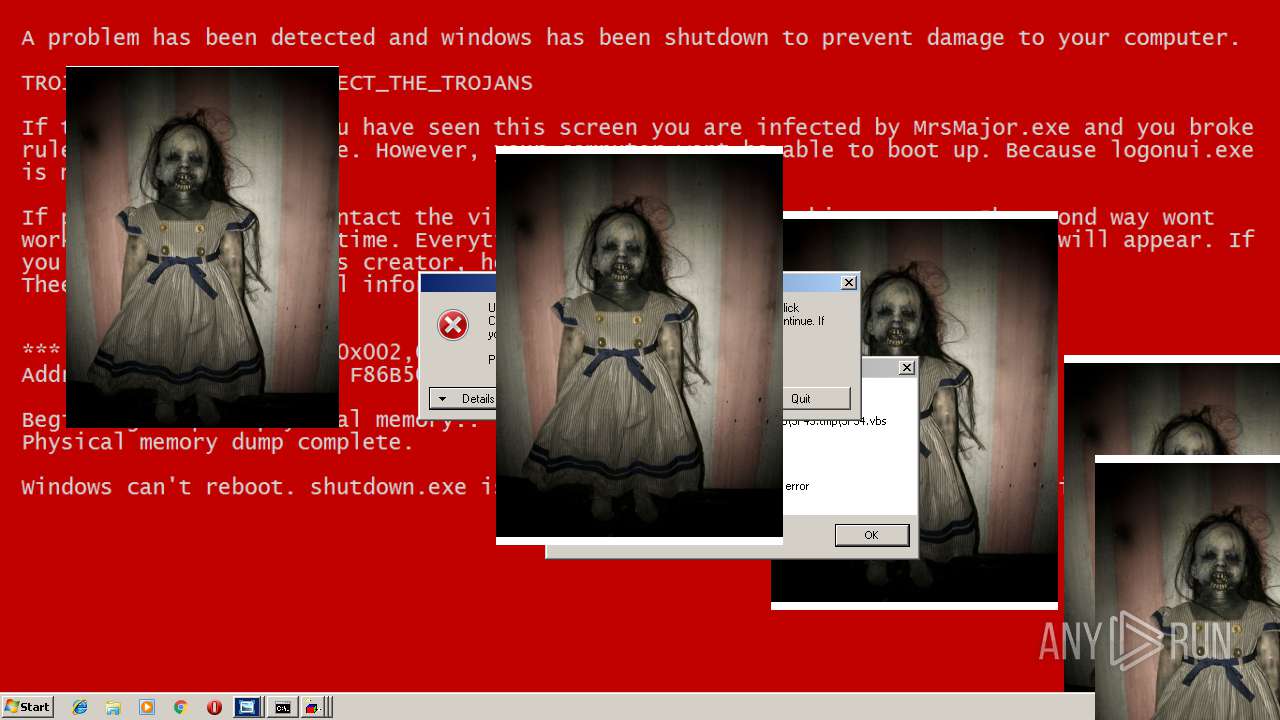
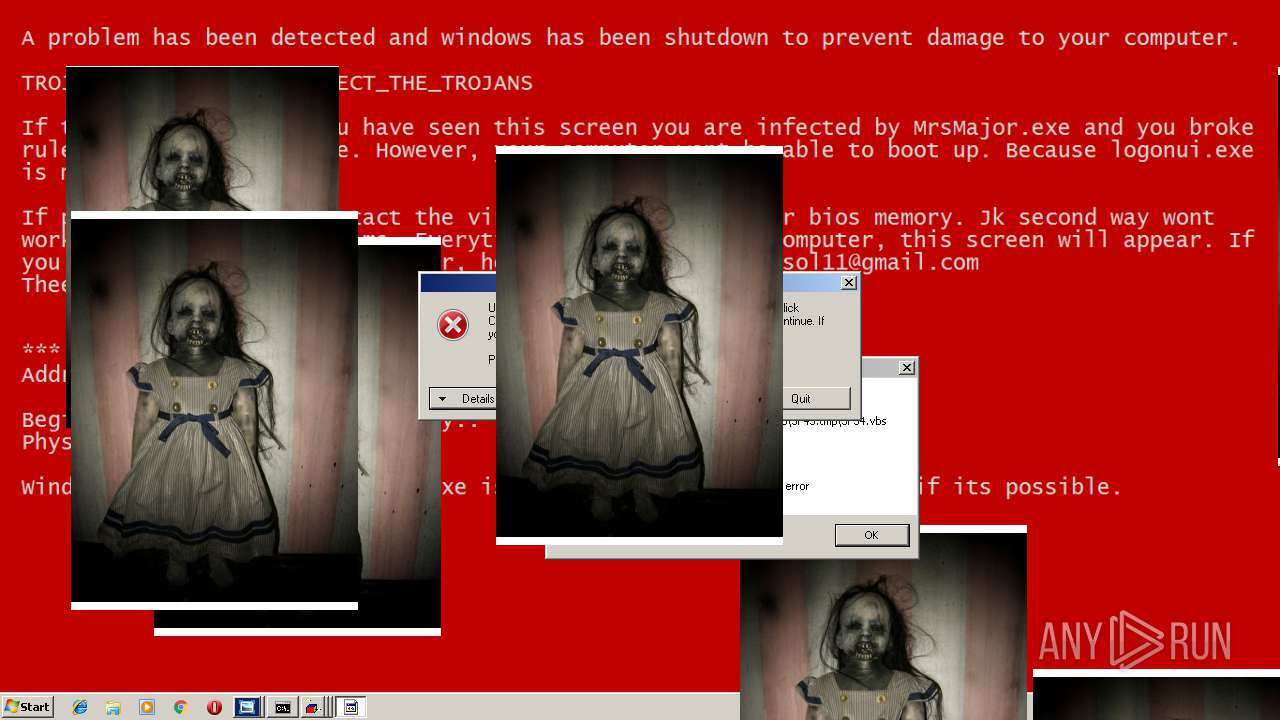
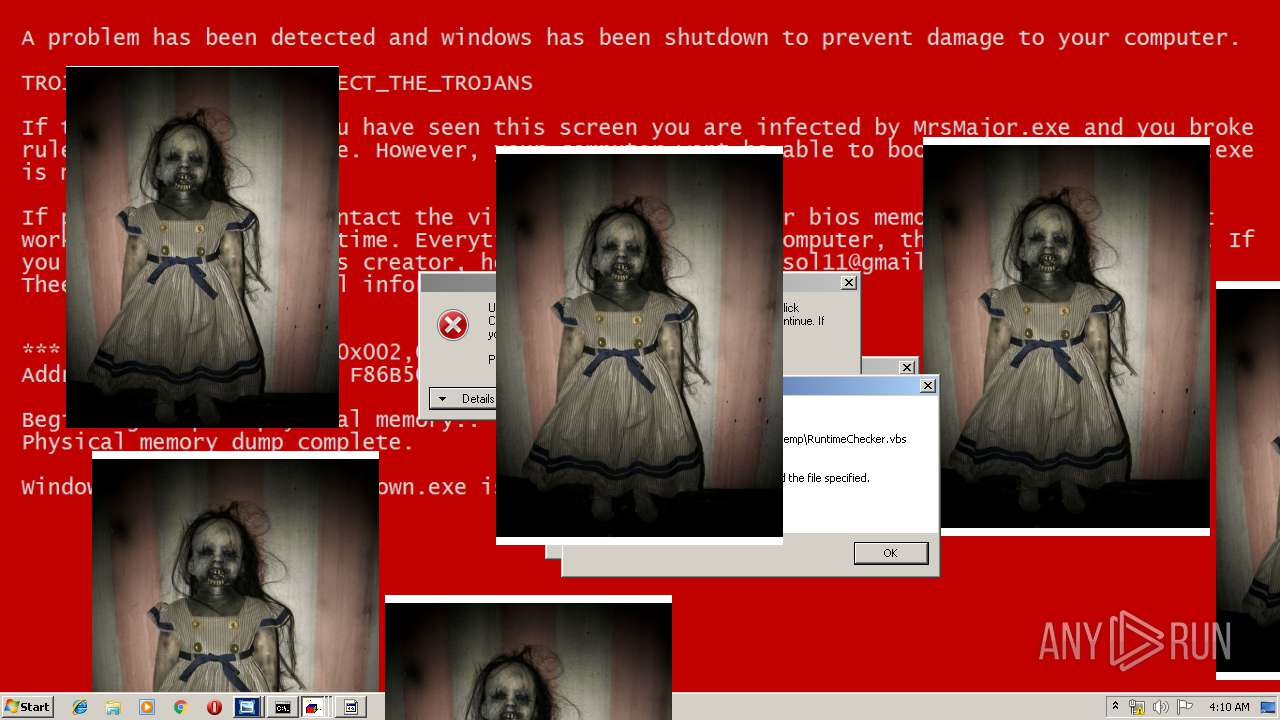
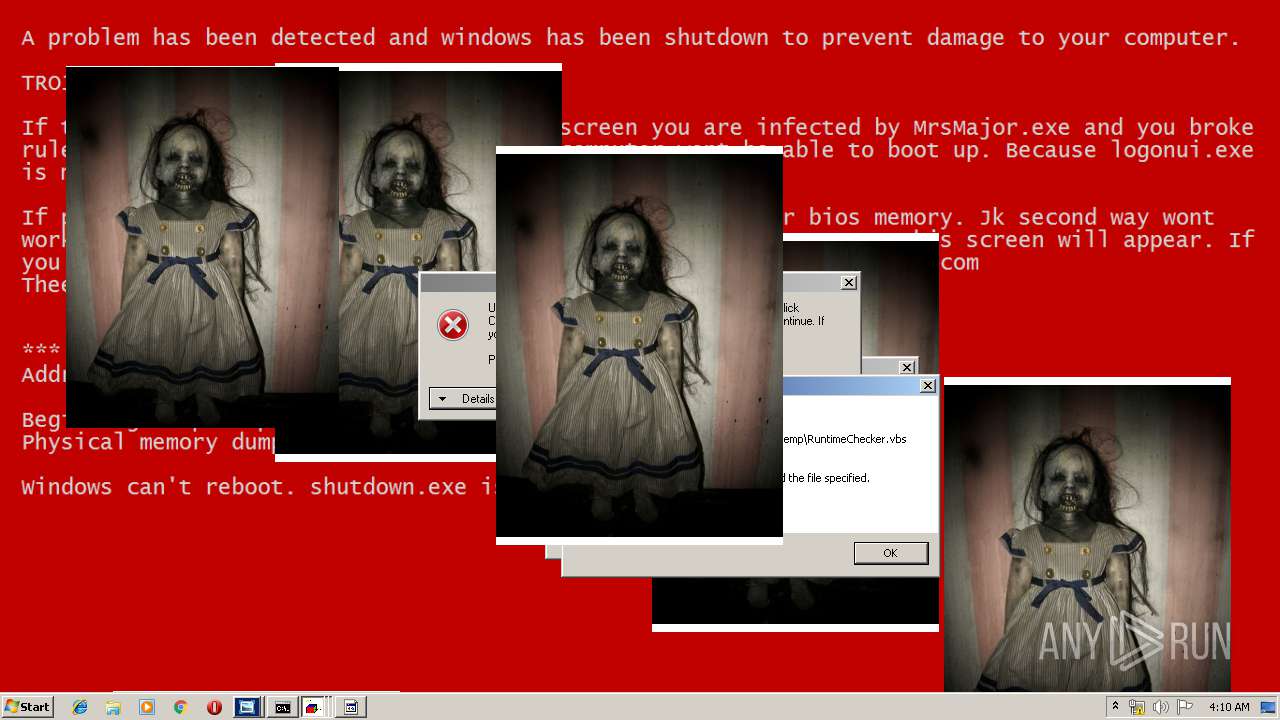
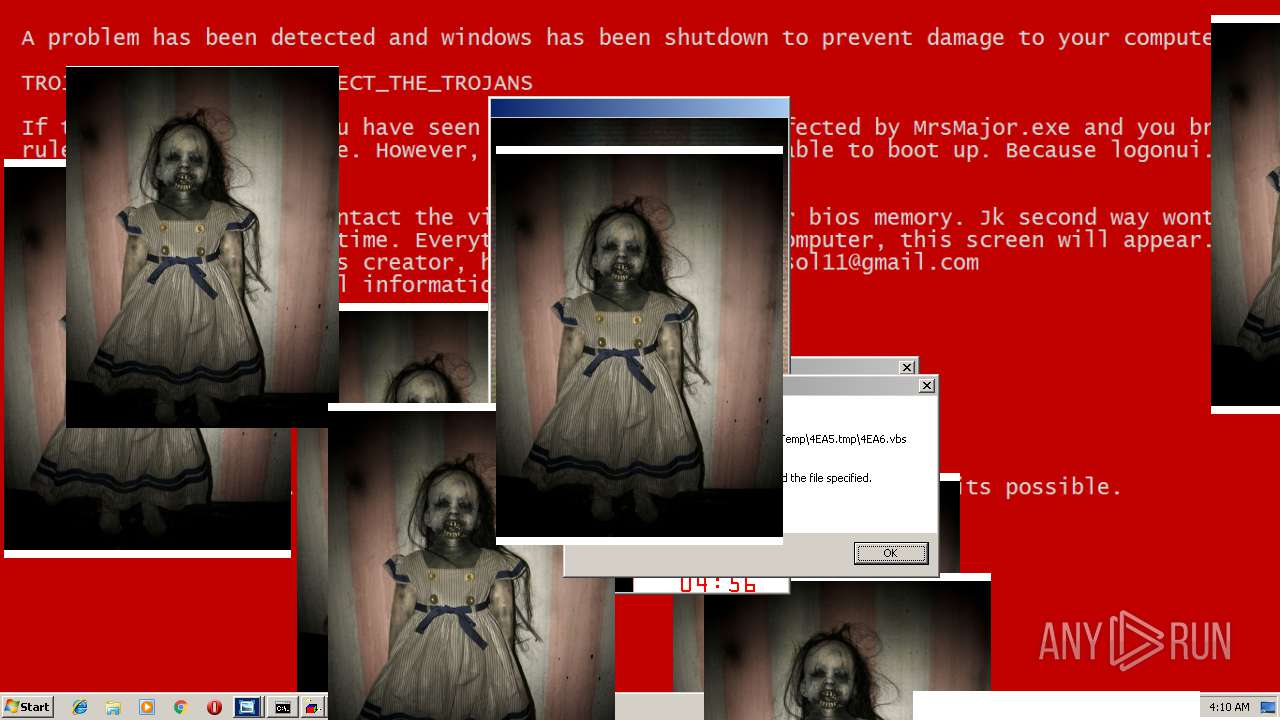
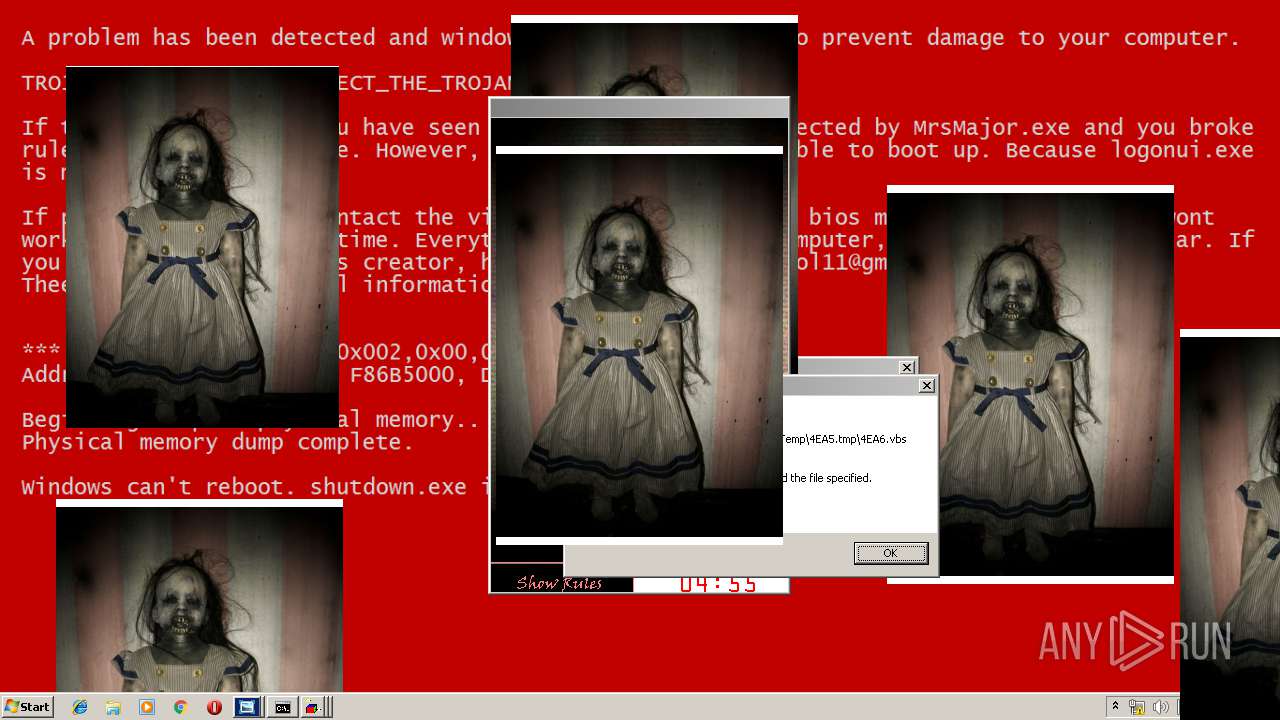
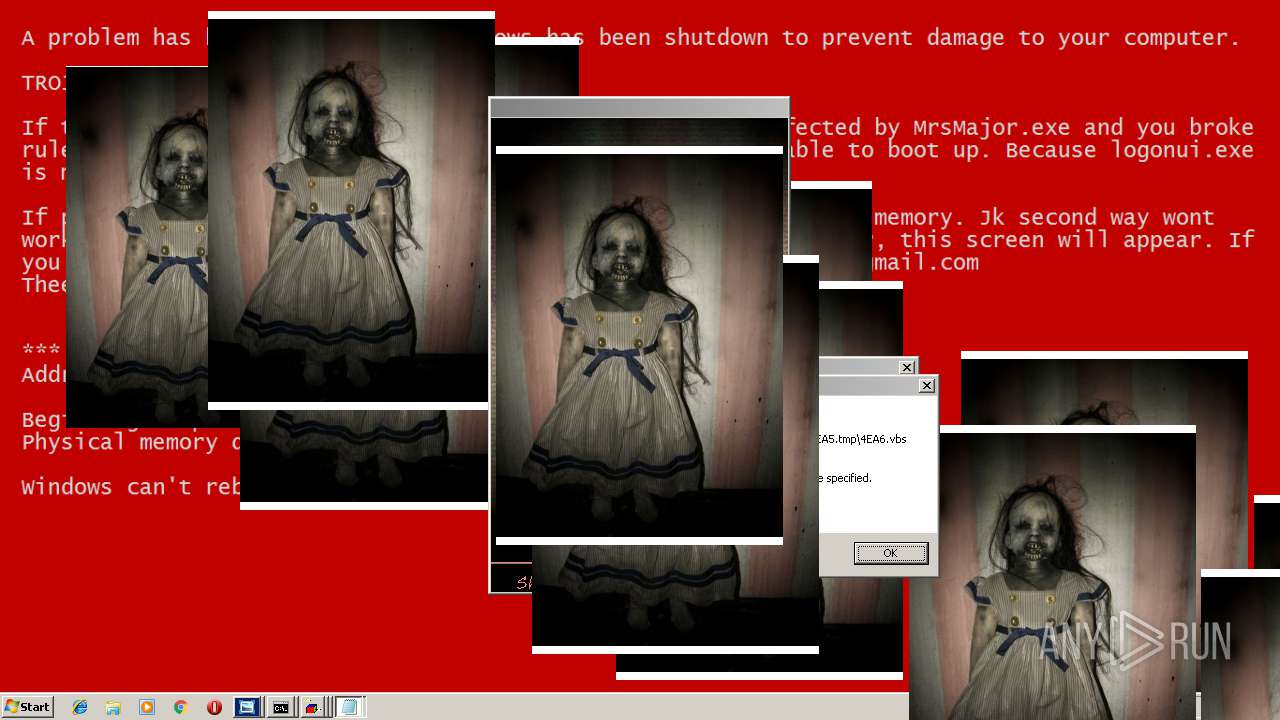
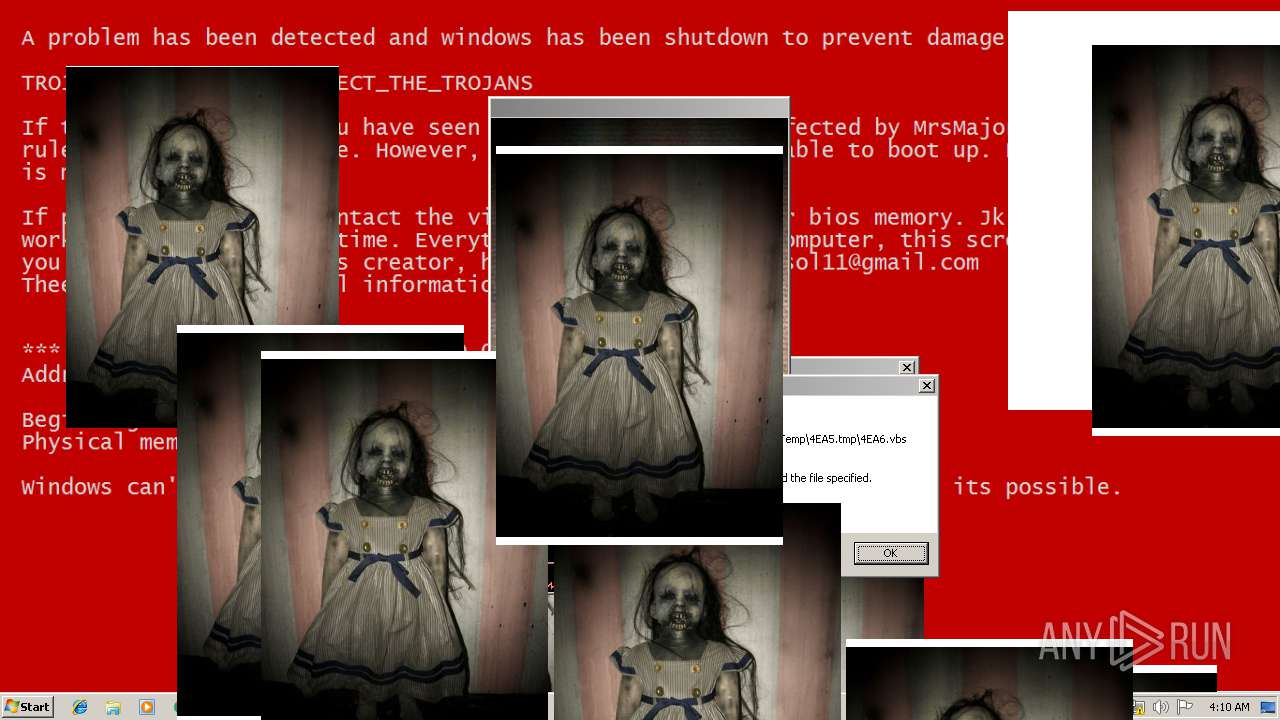
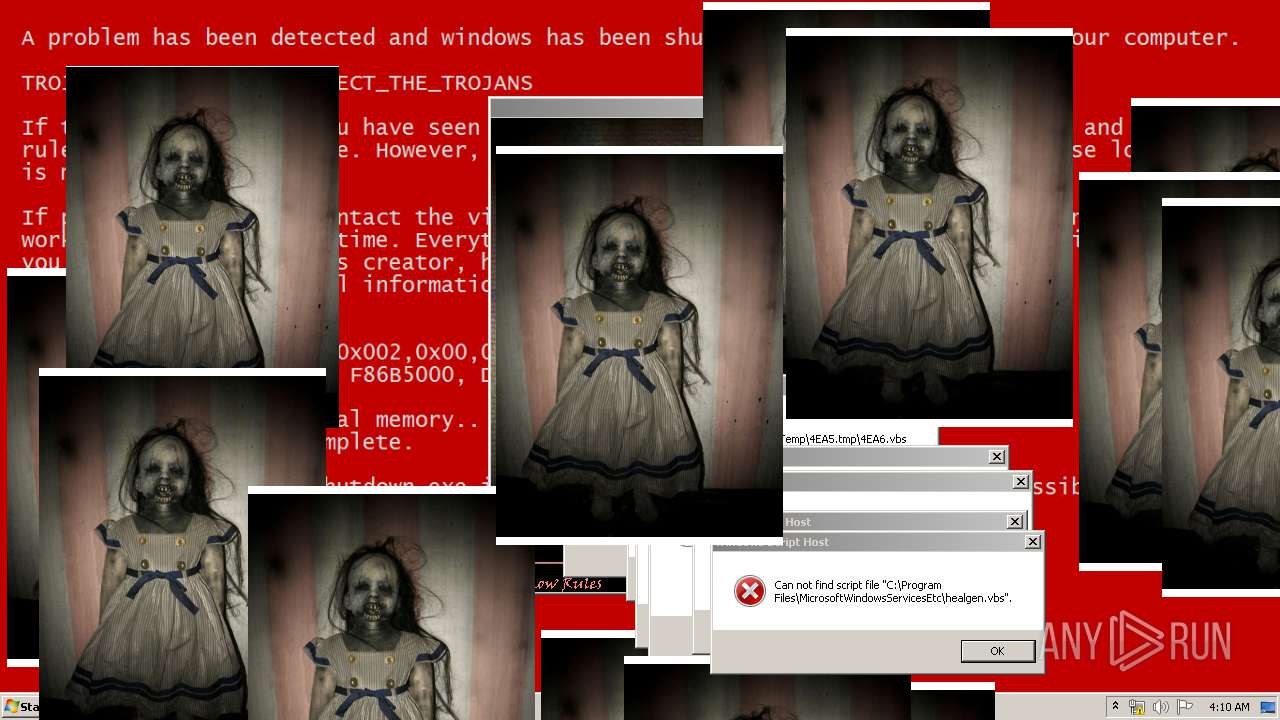
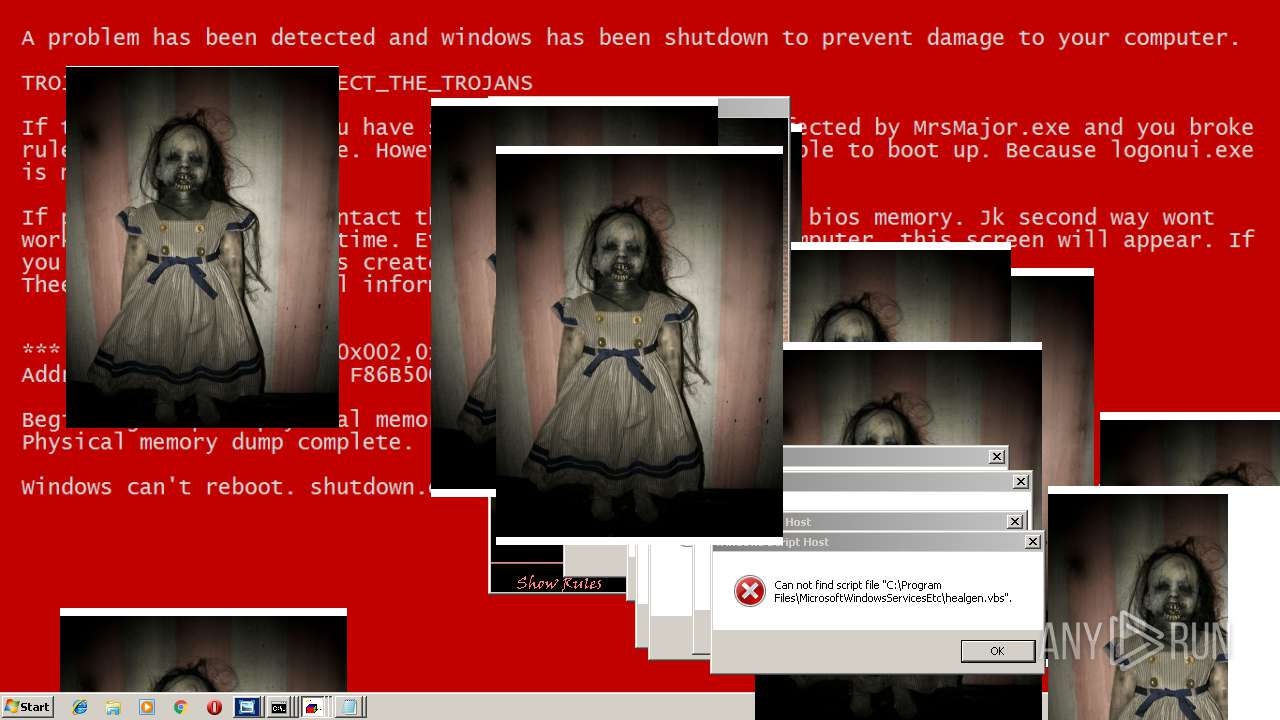
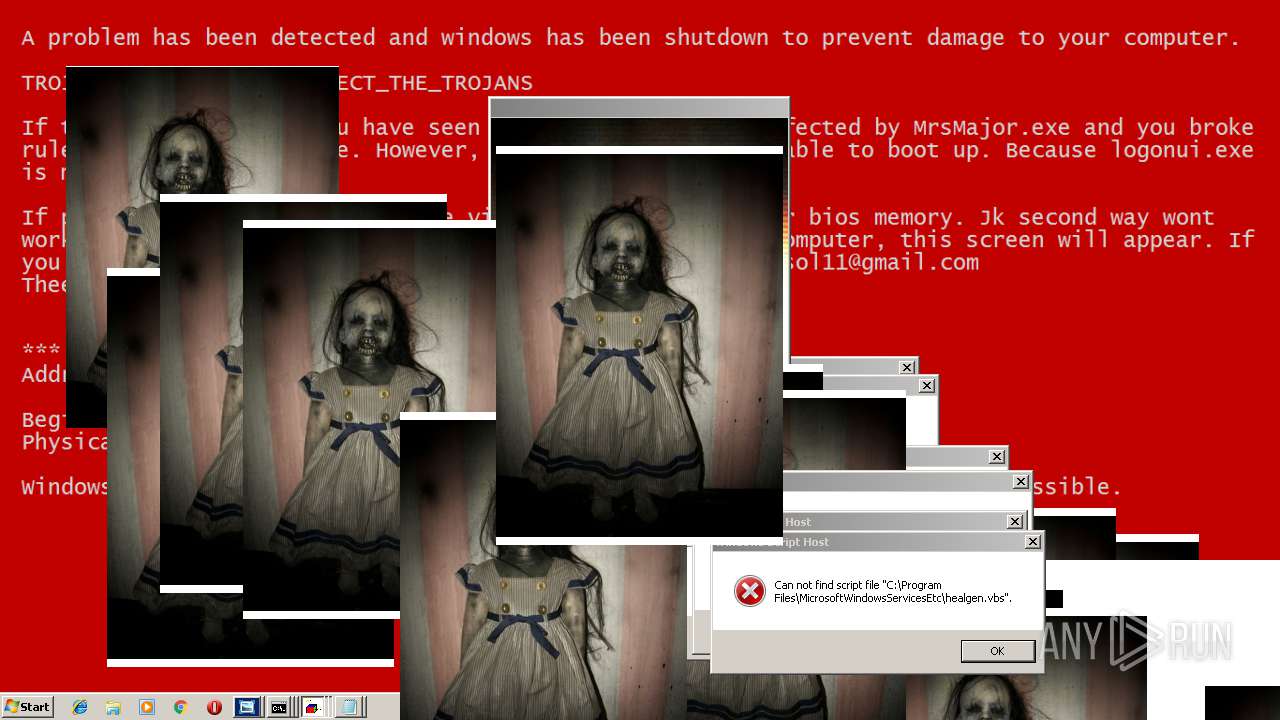
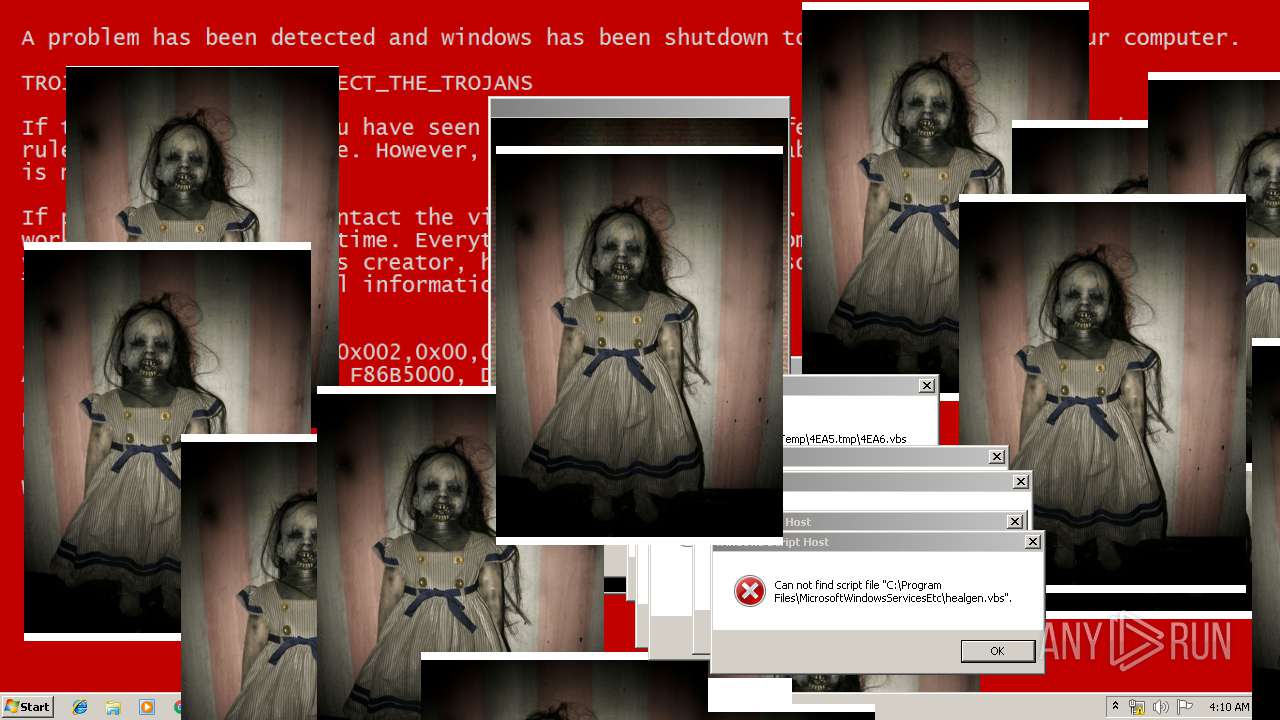
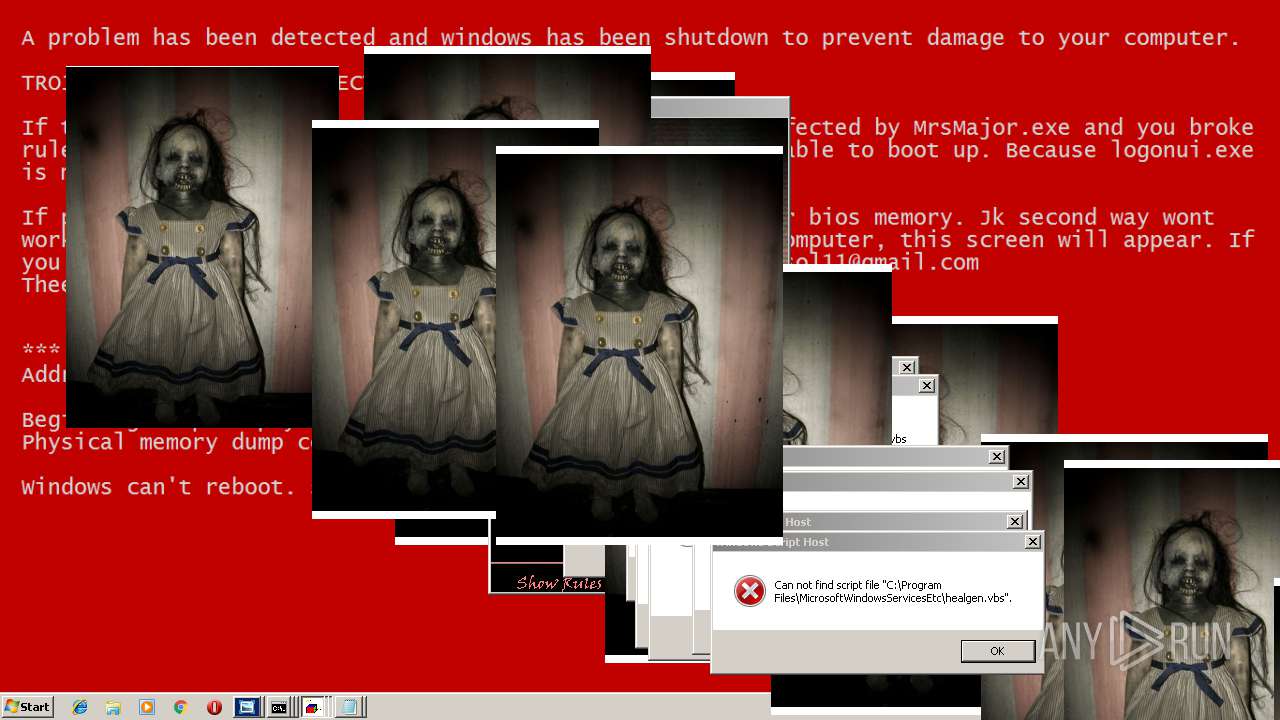
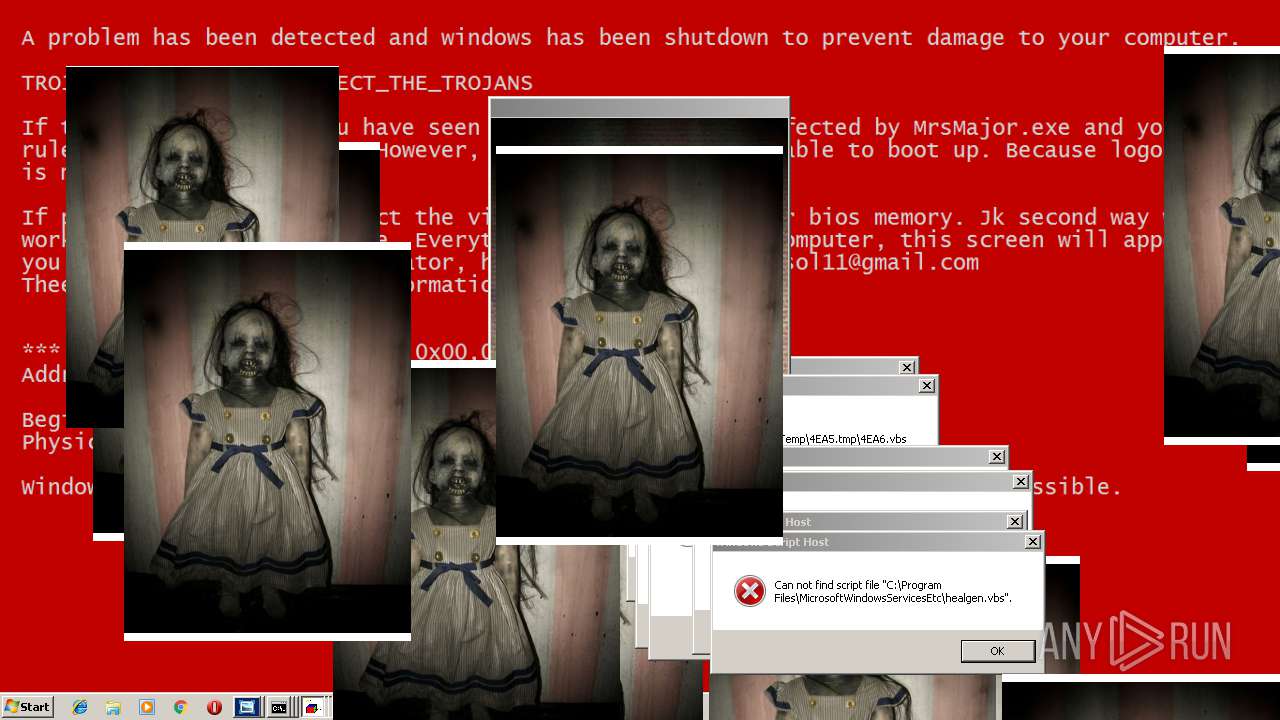
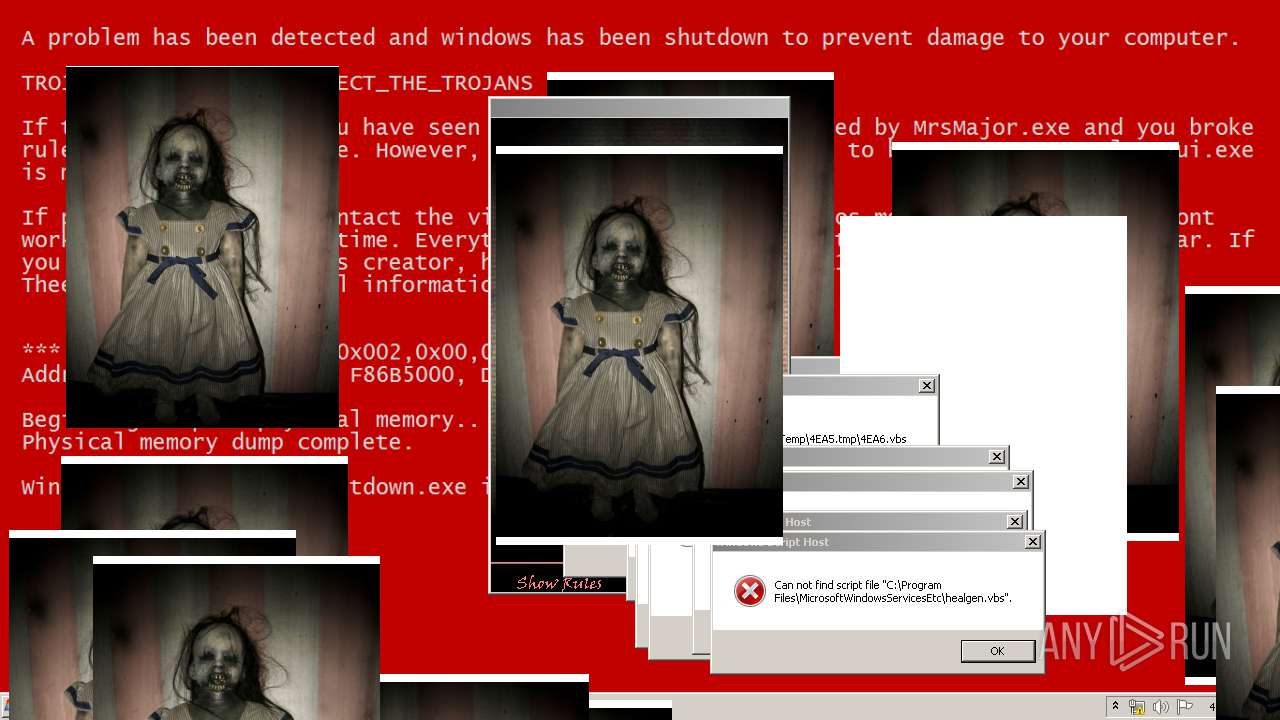
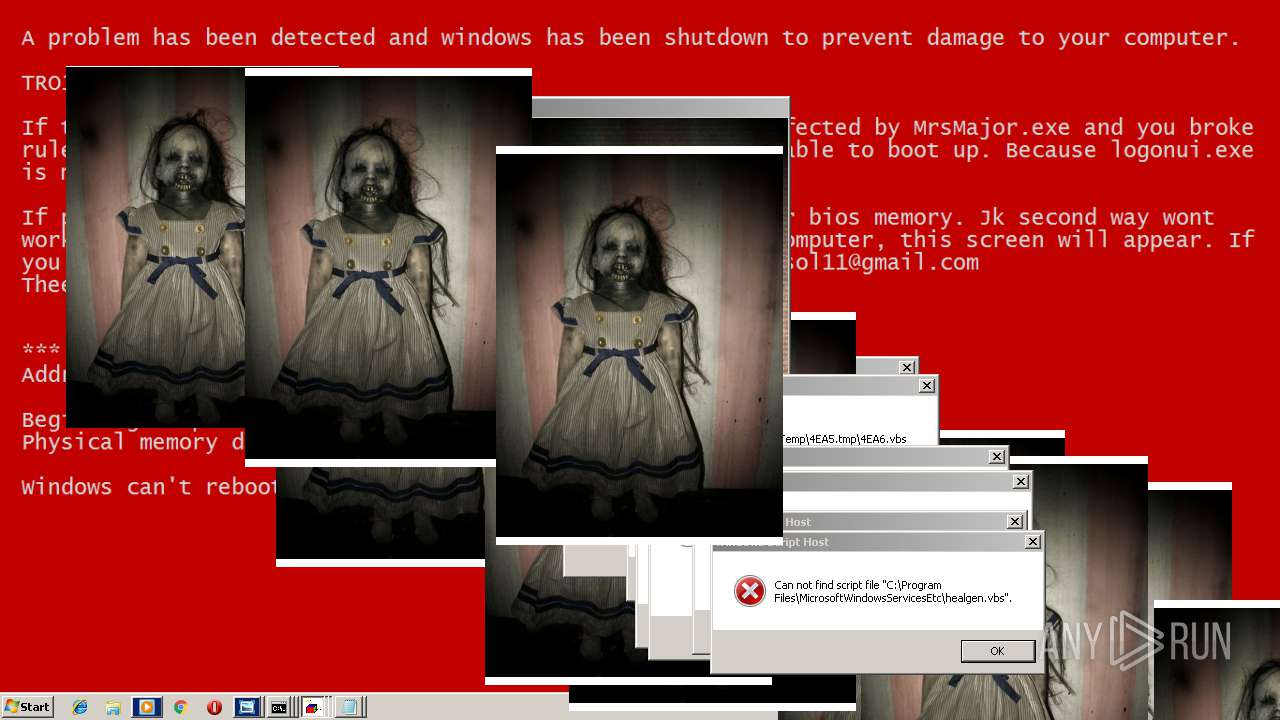
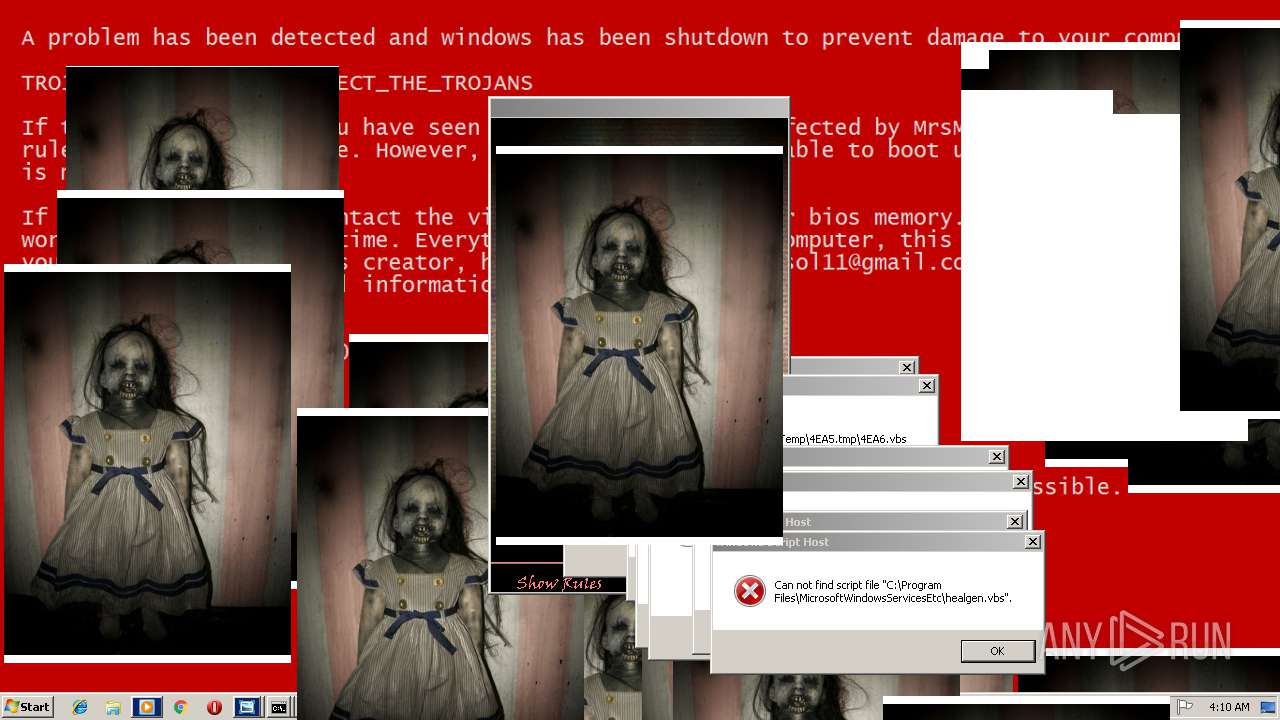
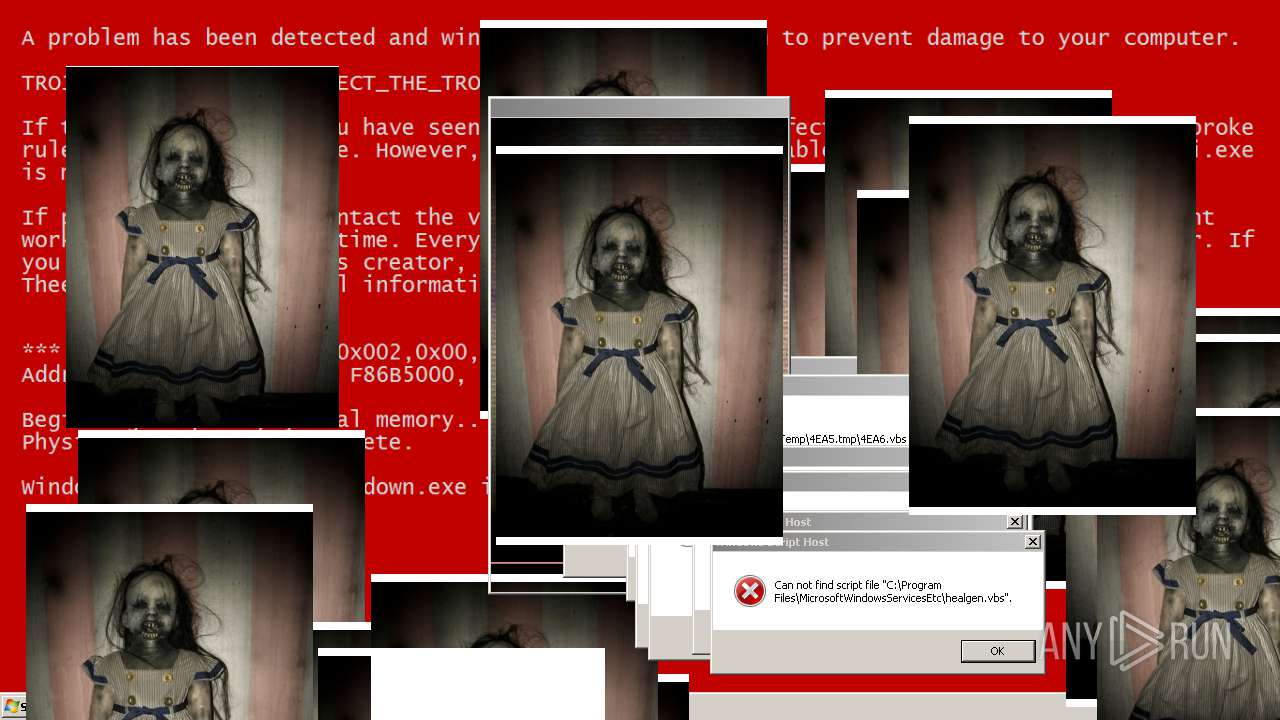
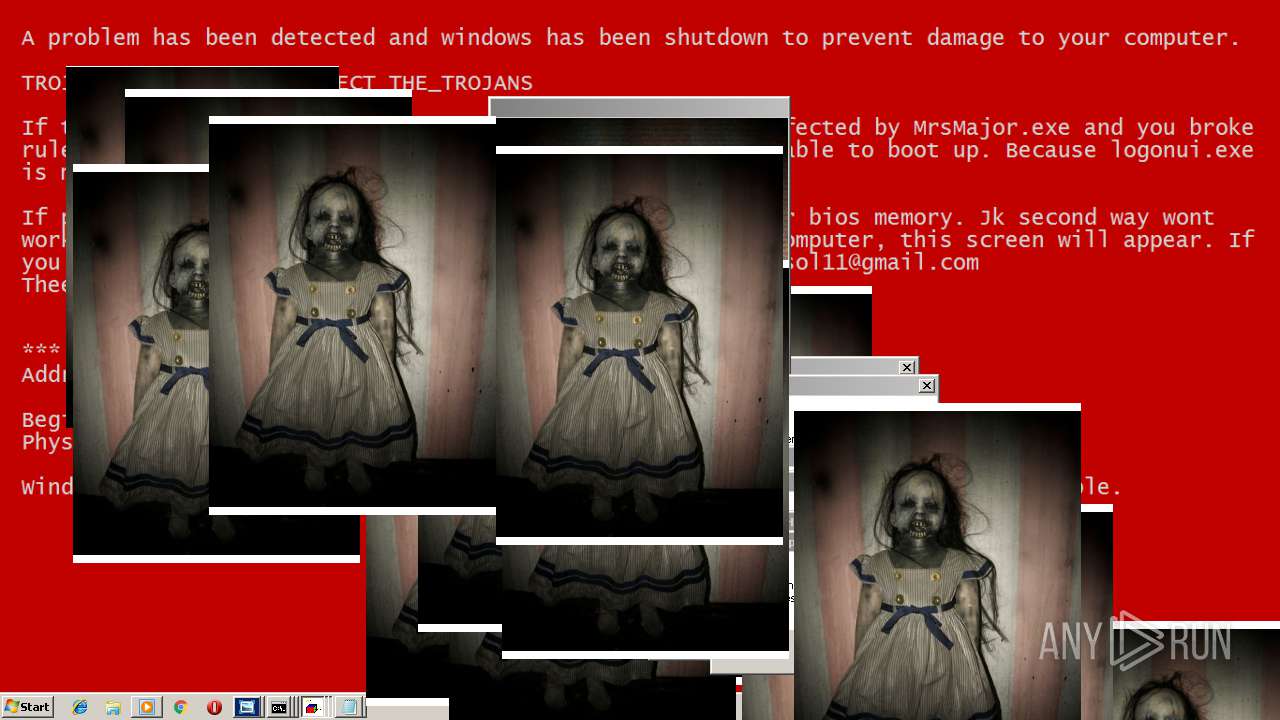
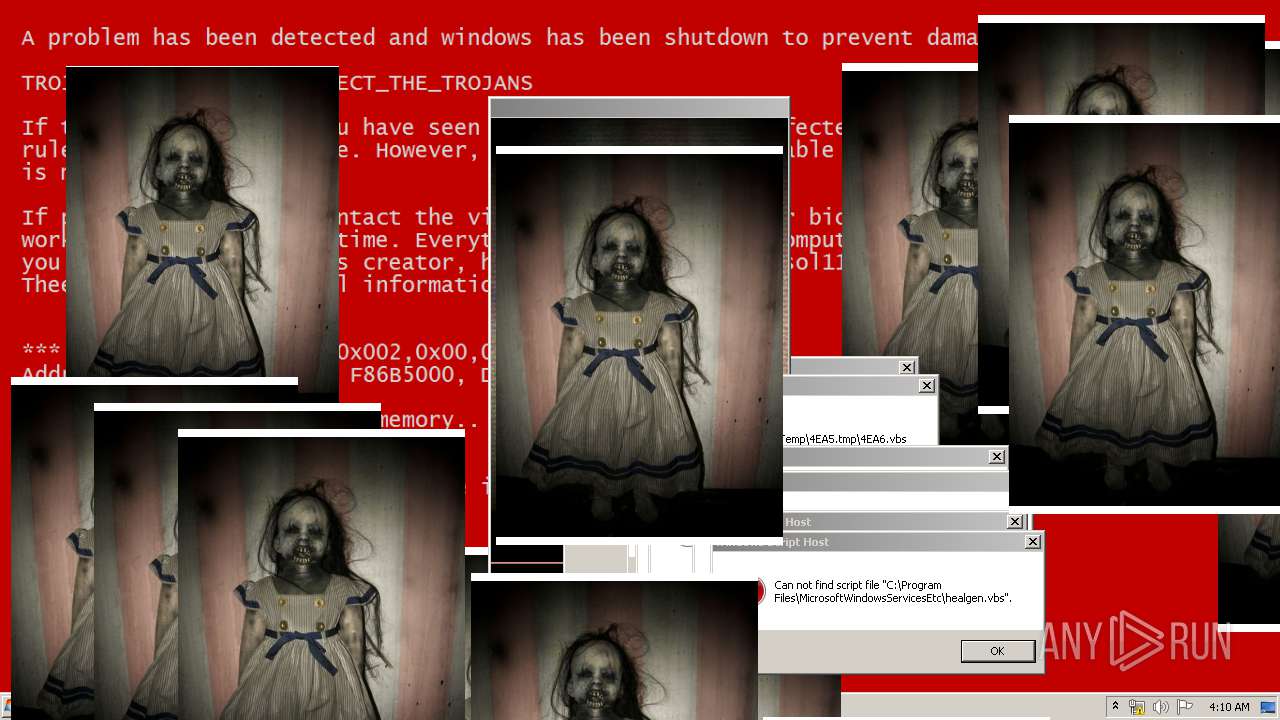
MALICIOUS
Application was dropped or rewritten from another process
- runner32s.exe (PID: 1512)
- runner32s.exe (PID: 2288)
- RuntimeChecker.exe (PID: 2904)
- rsod.exe (PID: 1760)
- WinScrew.exe (PID: 1872)
- eula32.exe (PID: 3700)
- runner32s.exe (PID: 3568)
- RuntimeChecker.exe (PID: 2772)
- WinScrew.exe (PID: 284)
- majordared.exe (PID: 2588)
- runner32s.exe (PID: 3208)
- BossDaMajor.exe (PID: 2720)
- runner32s.exe (PID: 1824)
- BossDaMajor.exe (PID: 772)
- majorsod.exe (PID: 2296)
- majorlist.exe (PID: 3228)
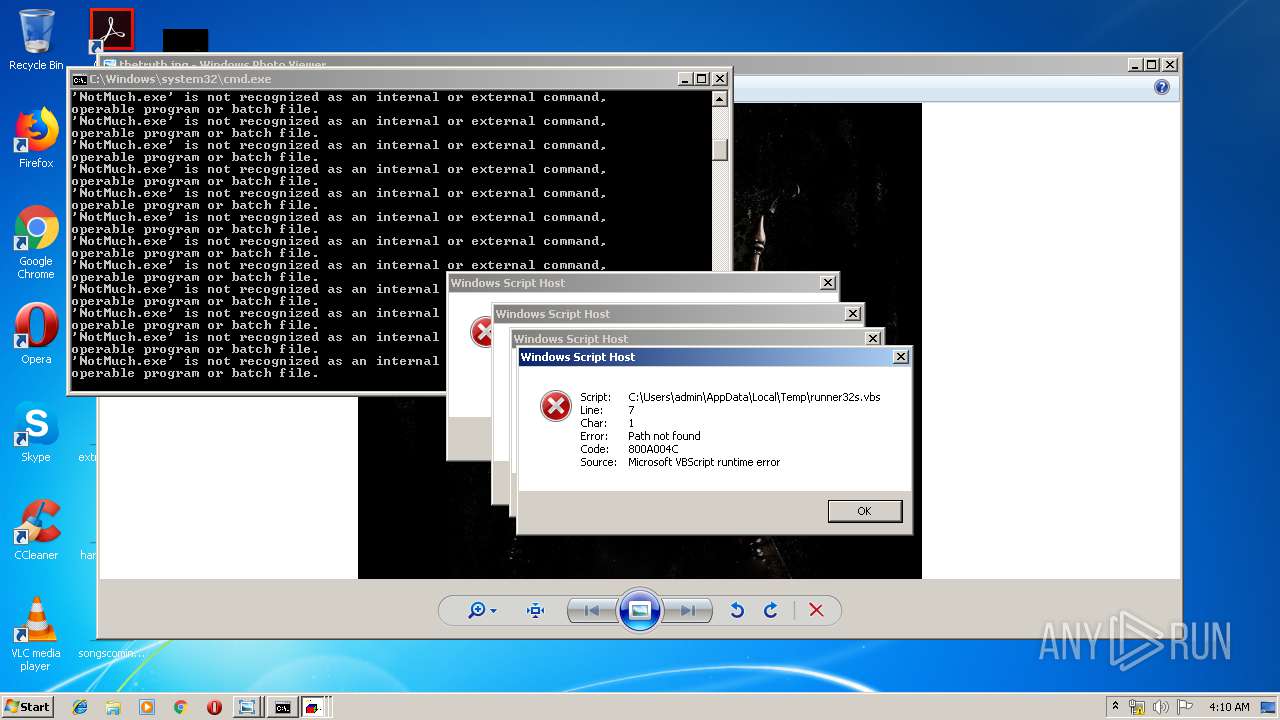
- NotMuch.exe (PID: 2836)
- Major.exe (PID: 3872)
- breakrule.exe (PID: 2604)
- GetReady.exe (PID: 3512)
- bsod.exe (PID: 1336)
- majorlist.exe (PID: 1864)
- Major.exe (PID: 3824)
- GetReady.exe (PID: 1412)
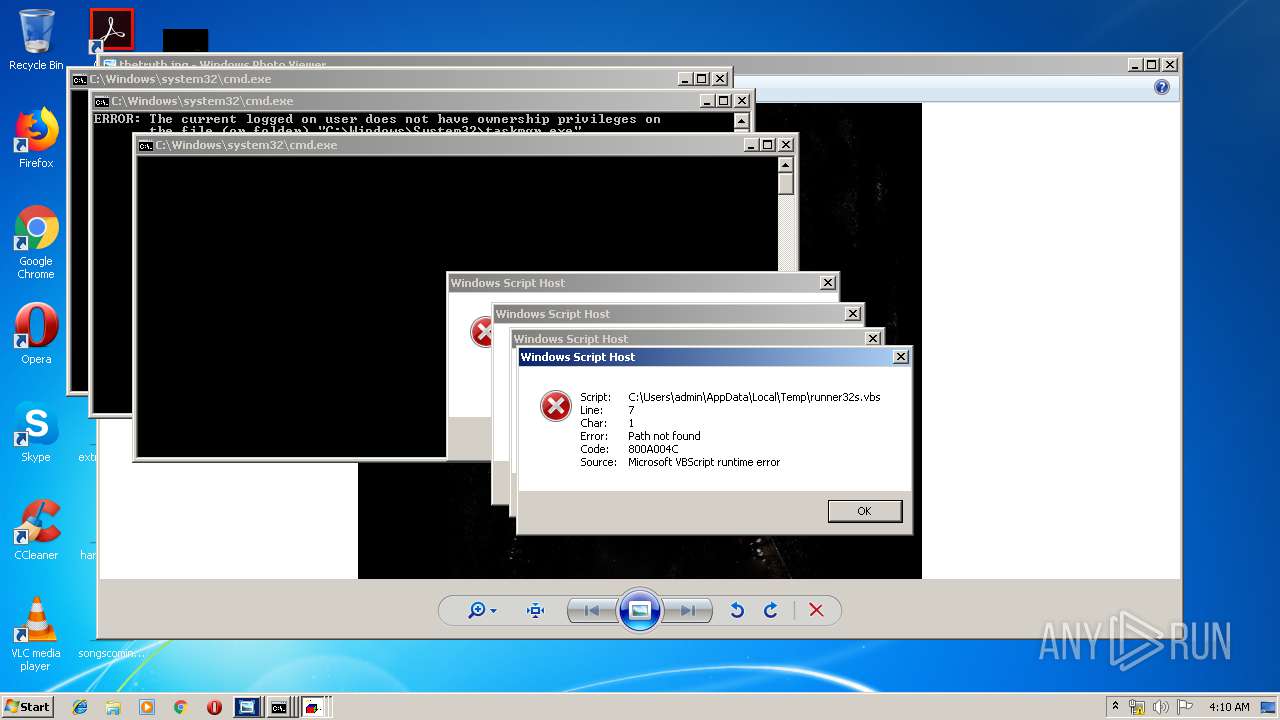
Uses TASKKILL.EXE to kill security tools
- cmd.exe (PID: 3788)
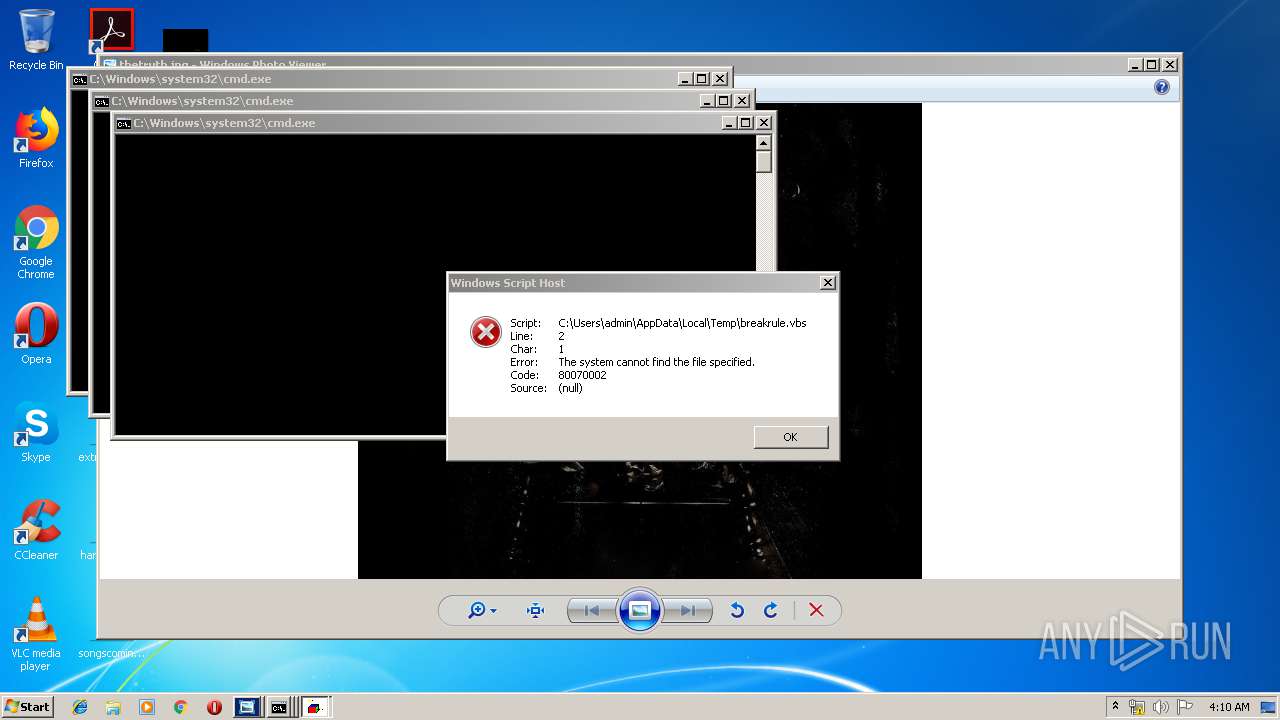
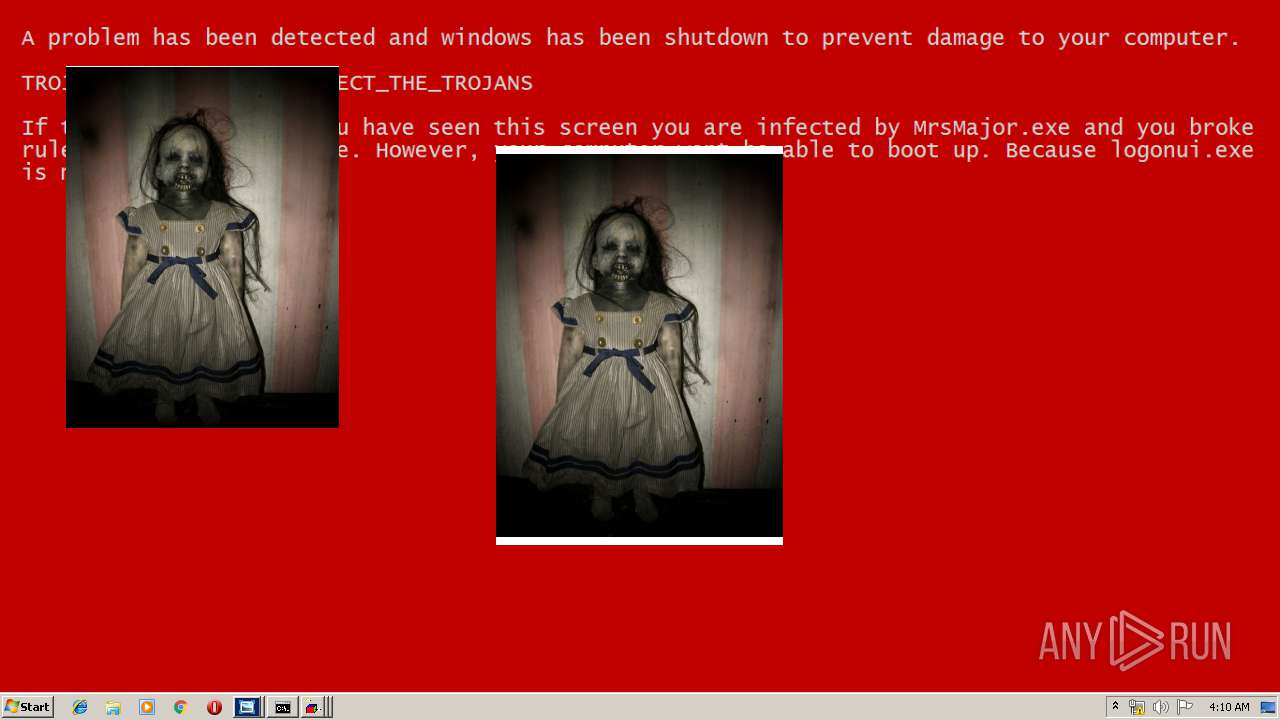
Task Manager has been disabled (taskmgr)
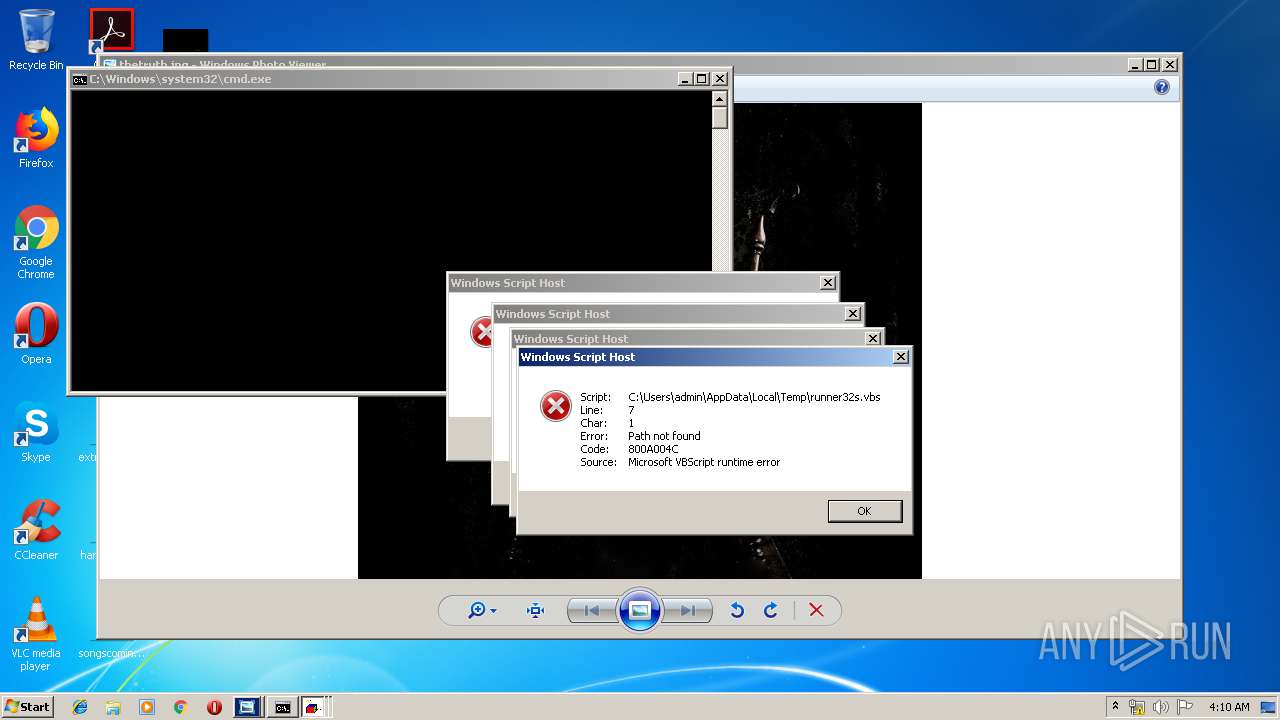
- wscript.exe (PID: 1532)
Disables registry editing tools (regedit)
- wscript.exe (PID: 1532)
Changes the login/logoff helper path in the registry
- wscript.exe (PID: 1532)
SUSPICIOUS
Executable content was dropped or overwritten
- Test.exe (PID: 2976)
- BossDaMajor.exe (PID: 772)
- wscript.exe (PID: 3892)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 3580)
- Test.exe (PID: 2976)
- WScript.exe (PID: 3076)
- WinScrew.exe (PID: 284)
- WScript.exe (PID: 2520)
- majorlist.exe (PID: 3228)
- GetReady.exe (PID: 3512)
- wscript.exe (PID: 2056)
- majorlist.exe (PID: 1864)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 728)
- cmd.exe (PID: 3868)
- cmd.exe (PID: 2544)
- cmd.exe (PID: 3400)
Executes scripts
- Test.exe (PID: 2976)
- runner32s.exe (PID: 3568)
- RuntimeChecker.exe (PID: 2904)
- BossDaMajor.exe (PID: 772)
- runner32s.exe (PID: 3208)
- majorsod.exe (PID: 2296)
- breakrule.exe (PID: 2604)
- cmd.exe (PID: 3556)
- wscript.exe (PID: 3892)
- WScript.exe (PID: 3332)
- Major.exe (PID: 3824)
- WScript.exe (PID: 1412)
Executed via COM
- DllHost.exe (PID: 2128)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 3788)
Application launched itself
- wscript.exe (PID: 3892)
- WScript.exe (PID: 3332)
- WScript.exe (PID: 1412)
Creates files in the program directory
- wscript.exe (PID: 3892)
- wscript.exe (PID: 1532)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3788)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:09:30 20:01:44+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 190976 |
| InitializedDataSize: | 372224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d549 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-Sep-2018 18:01:44 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000120 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 30-Sep-2018 18:01:44 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0002E924 | 0x0002EA00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.69845 |
.rdata | 0x00030000 | 0x00009A8C | 0x00009C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.13014 |
.data | 0x0003A000 | 0x000203A0 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.23545 |
.gfids | 0x0005B000 | 0x000000E8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.09308 |
.rsrc | 0x0005C000 | 0x0002EA7B | 0x0002EC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.8984 |
.reloc | 0x0008B000 | 0x00001FDC | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.67876 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.10026 | 2216 | UNKNOWN | English - United States | RT_ICON |
3 | 5.25868 | 3752 | UNKNOWN | English - United States | RT_ICON |
4 | 5.02609 | 1128 | UNKNOWN | English - United States | RT_ICON |
5 | 5.18109 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 5.04307 | 9640 | UNKNOWN | English - United States | RT_ICON |
7 | 3.23498 | 564 | UNKNOWN | German - Germany | RT_STRING |
8 | 3.21532 | 616 | UNKNOWN | German - Germany | RT_STRING |
9 | 3.20126 | 604 | UNKNOWN | German - Germany | RT_STRING |
10 | 3.20175 | 416 | UNKNOWN | German - Germany | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
166
Monitored processes
103
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Windows\system32\wscript.exe" C:\Users\admin\AppData\Local\Temp\3F43.tmp\3F54.vbs | C:\Windows\system32\wscript.exe | — | runner32s.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 284 | "C:\Users\admin\AppData\Local\Temp\WinScrew.exe" | C:\Users\admin\AppData\Local\Temp\WinScrew.exe | Test.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1251649031 Modules
| |||||||||||||||
| 344 | taskkill /f /im eset.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 3221225794 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | takeown /f sethc.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Takes ownership of a file Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 596 | takeown /f sethc.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 644 | taskkill /f /im dllhost.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 3221225794 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 728 | cmd /c ""C:\Users\admin\AppData\Local\Temp\WinScrew.bat" " | C:\Windows\system32\cmd.exe | — | Test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 772 | "C:\Users\admin\AppData\Local\Temp\BossDaMajor.exe" | C:\Users\admin\AppData\Local\Temp\BossDaMajor.exe | Test.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 868 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\fexec.vbs" | C:\Windows\System32\WScript.exe | — | Test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1073807364 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1000 | "C:\Windows\System32\cmd.exe" /c cd\&cd "Program Files"&cd MicrosoftWindowsServicesEtc&RuntimeChecker.exe | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 126
Read events
3 001
Write events
125
Delete events
0
Modification events
| (PID) Process: | (2976) Test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2976) Test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2976) Test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {FFE2A43C-56B9-4BF5-9A79-CC6D4285608A} {00000122-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000007EC1B089B90ED501 | |||
| (PID) Process: | (2976) Test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Test.exe | |||
| (PID) Process: | (2128) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (3568) runner32s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3568) runner32s.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2520) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2520) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3580) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
16
Suspicious files
0
Text files
107
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\eula32.exe | executable | |
MD5:— | SHA256:— | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\BossDaMajor.exe | executable | |
MD5:38FF71C1DEE2A9ADD67F1EDB1A30FF8C | SHA256:730A41A7656F606A22E9F0D68782612D6E00AB8CFE1260160B9E0B00BC2E442A | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\breakrule.exe | executable | |
MD5:BCB0AC4822DE8AEB86EA8A83CD74D7CA | SHA256:5EAFEBD52FBF6D0E8ABD0CC9BF42D36E5B6E4D85B8EBE59F61C9F2D6DCCC65E4 | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\WinScrew.bat | text | |
MD5:04067CA733EE8B2AB2F068EDC8B75A0F | SHA256:3AEF33C03777ABE62FEEF0A840AC6A087CAAFC05ADFE801464FD1C52EAC656A0 | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\xRun.vbs | text | |
MD5:26EC8D73E3F6C1E196CC6E3713B9A89F | SHA256:ED588FA361979F7F9C6DBB4E6A1AE6E075F2DB8D79EA6CA2007BA8E3423671B0 | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\checker.bat | text | |
MD5:F59801D5C49713770BDB2F14EFF34E2F | SHA256:3382484B5A6A04D05500E7622DA37C1FFAEF3A1343395942BC7802BF2A19B53F | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\WinScrew.exe | executable | |
MD5:1AAAFEDD9F259ACCA75708F4AF10B5BE | SHA256:429E01B0E06B02A55BAFB1527629F8D4C5F64D9B21AC9F81484A3928FDCE6DC9 | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\bsod.exe | executable | |
MD5:8F6A3B2B1AF3A4AACD8DF1734D250CFE | SHA256:6581EEAB9FD116662B4CA73F6EF00FB96E0505D01CFB446EE4B32BBDEEFE1361 | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\xRunReg.vbs | text | |
MD5:8267192F547F8914FF36EFF80CA3F402 | SHA256:CDD4F356CA256C707960BC42B97649111A830E6F951CA6A3CF80853E3C342947 | |||
| 2976 | Test.exe | C:\Users\admin\AppData\Local\Temp\AppKill.bat | text | |
MD5:D4E987817D2E5D6ED2C12633D6F11101 | SHA256:5549670EF8837C6E3C4E496C1EA2063670618249D4151DEA4D07D48AB456690C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report