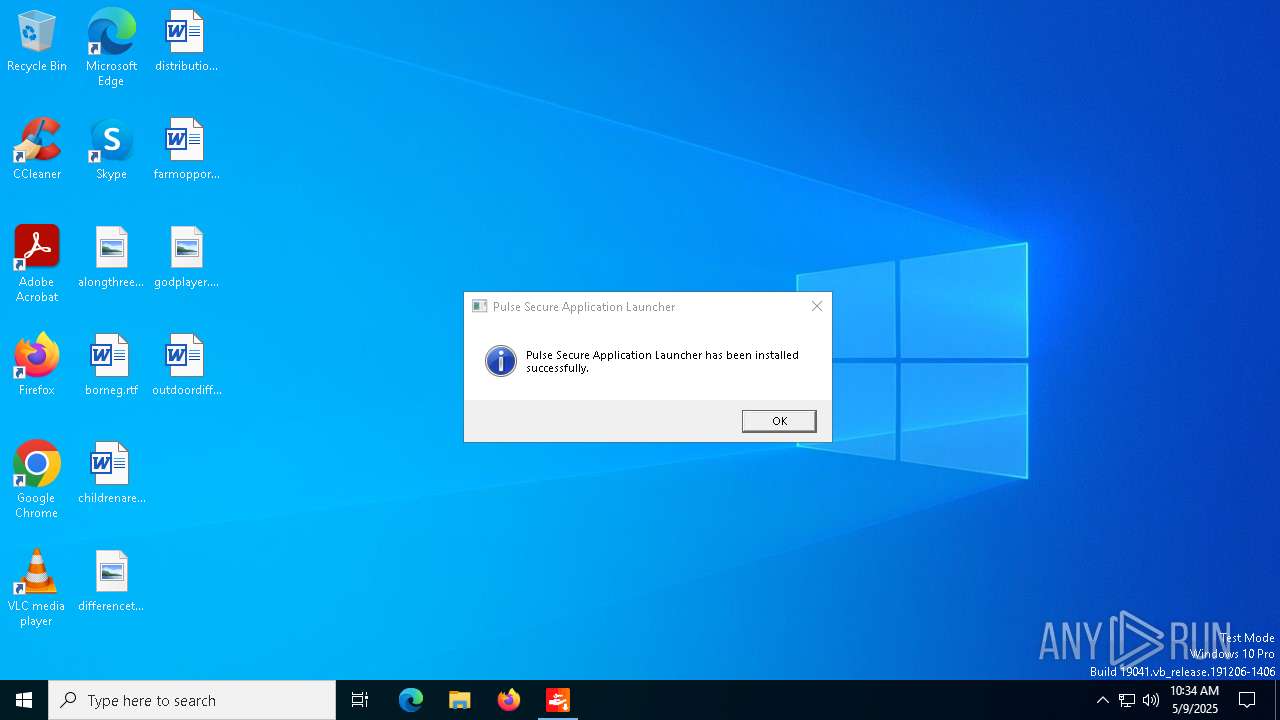
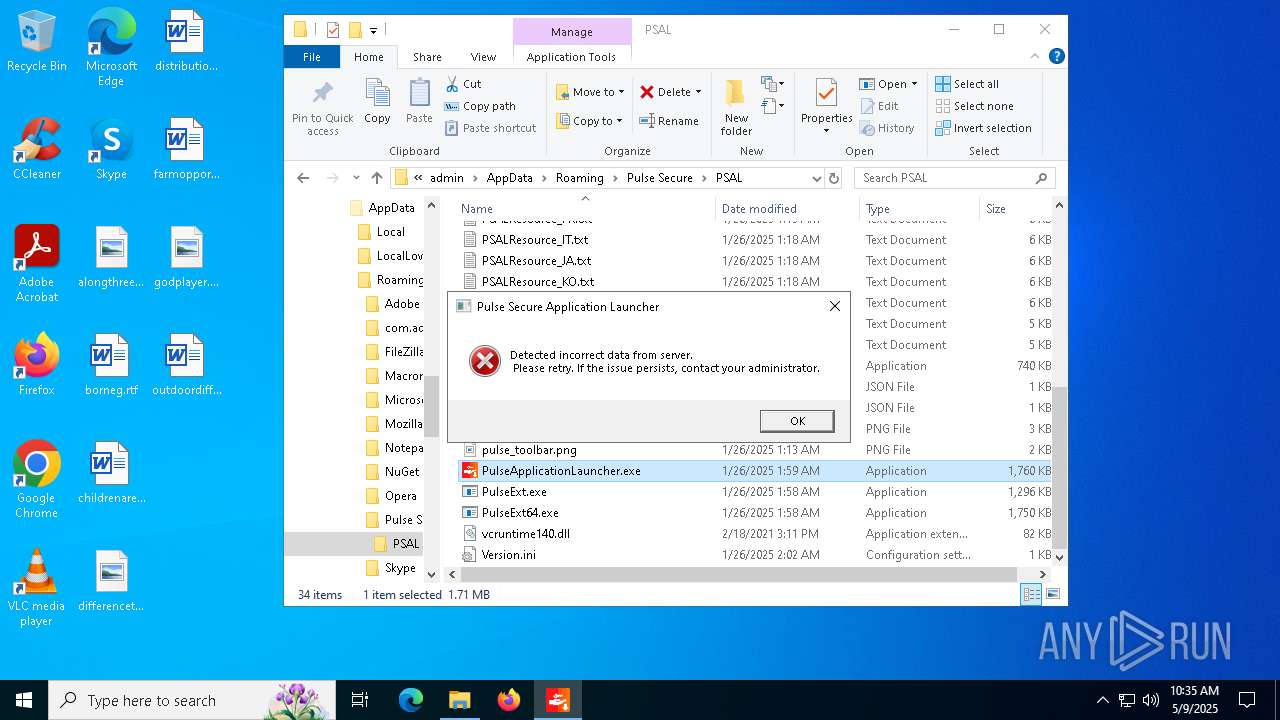
| File name: | PulseSecureAppLauncher__2_.msi |
| Full analysis: | https://app.any.run/tasks/207d364c-92a4-4229-82d4-da3f7cfa2796 |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 10:33:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Pulse Application Launcher, Author: Ivanti, Inc., Keywords: Installer, Comments: This installer database contains the logic and data required to install Pulse Application Launcher., Template: Intel;1033, Revision Number: {18C4DC19-FD03-42A0-A147-A118C14E5649}, Create Time/Date: Sun Jan 26 10:02:38 2025, Last Saved Time/Date: Sun Jan 26 10:02:38 2025, Number of Pages: 300, Number of Words: 10, Name of Creating Application: Windows Installer XML Toolset (3.14.1.8722), Security: 2 |
| MD5: | 71FE673B9DDFC3BBBB147F6B62A61676 |
| SHA1: | 0D4E891F7D12ABB9896E66C641AD973BE8A0076D |
| SHA256: | 2713771C9745B6A83054F8FBAAB849D2A9BFC5AA56C2084744E222312E16402D |
| SSDEEP: | 98304:Y4cKw4sWD5azOy5Jb5lMuopg7e9XeTRJcQKMAxbrCTrjCe/YvAW3skgwKmIRXt/L:MOnccJSbH8wky |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 2392)
- msiexec.exe (PID: 7348)
The process drops C-runtime libraries
- msiexec.exe (PID: 2392)
- msiexec.exe (PID: 7348)
Executes as Windows Service
- VSSVC.exe (PID: 7436)
INFO
Creates files or folders in the user directory
- msiexec.exe (PID: 2392)
Checks supported languages
- msiexec.exe (PID: 7348)
The sample compiled with english language support
- msiexec.exe (PID: 2392)
- msiexec.exe (PID: 7348)
Checks proxy server information
- msiexec.exe (PID: 2392)
Reads the computer name
- msiexec.exe (PID: 7348)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2392)
Reads the software policy settings
- msiexec.exe (PID: 2392)
Manages system restore points
- SrTasks.exe (PID: 8112)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7348)
Manual execution by a user
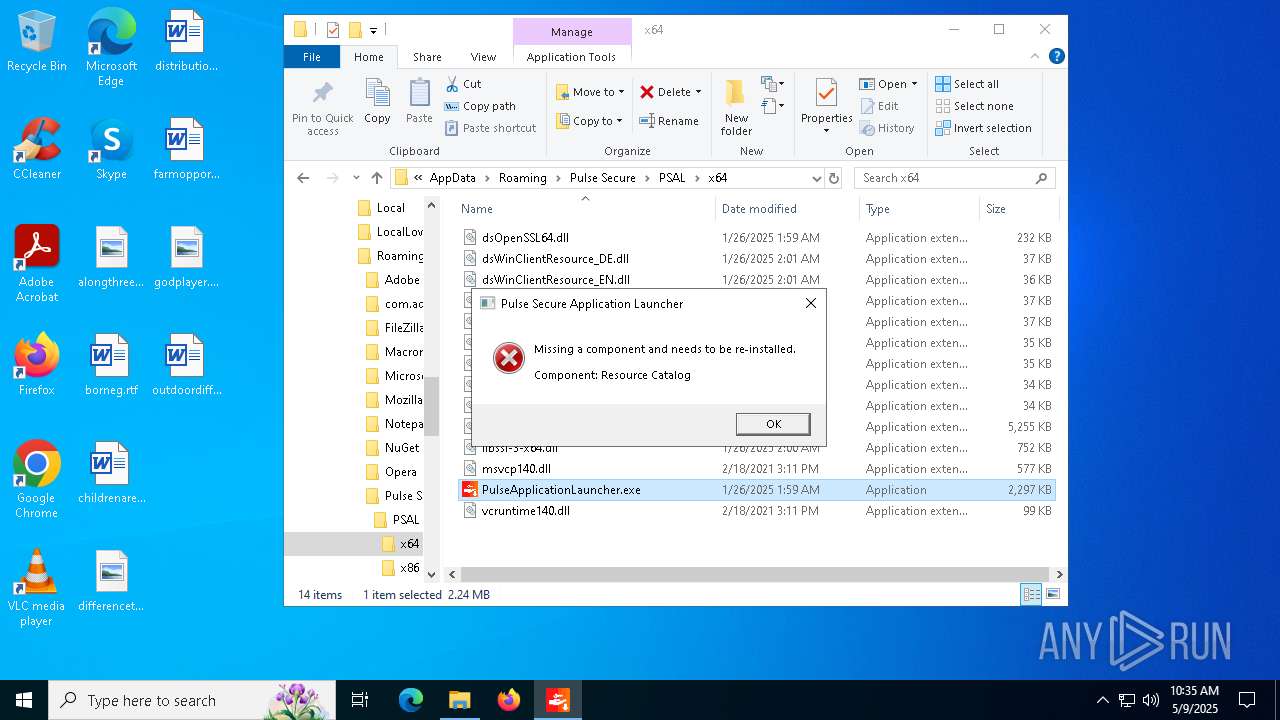
- PulseApplicationLauncher.exe (PID: 4932)
- PulseApplicationLauncher.exe (PID: 6112)
- mspaint.exe (PID: 7948)
- mspaint.exe (PID: 8072)
- PulseApplicationLauncher.exe (PID: 6004)
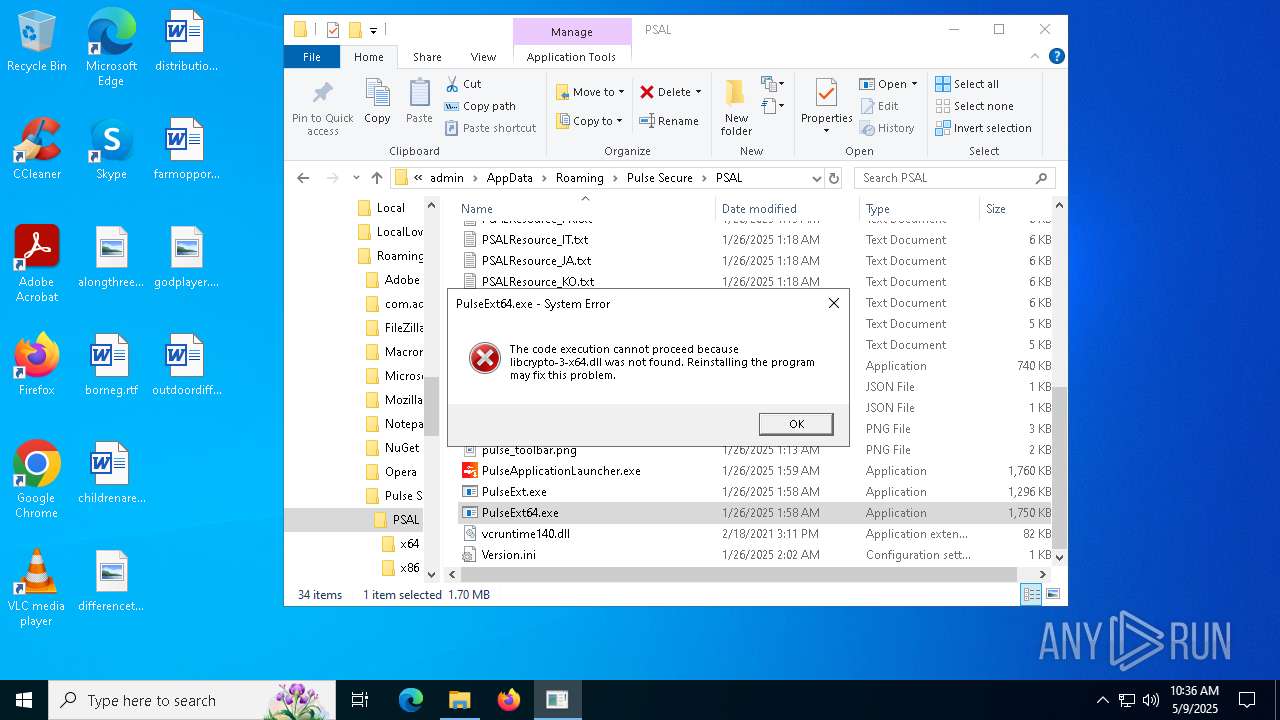
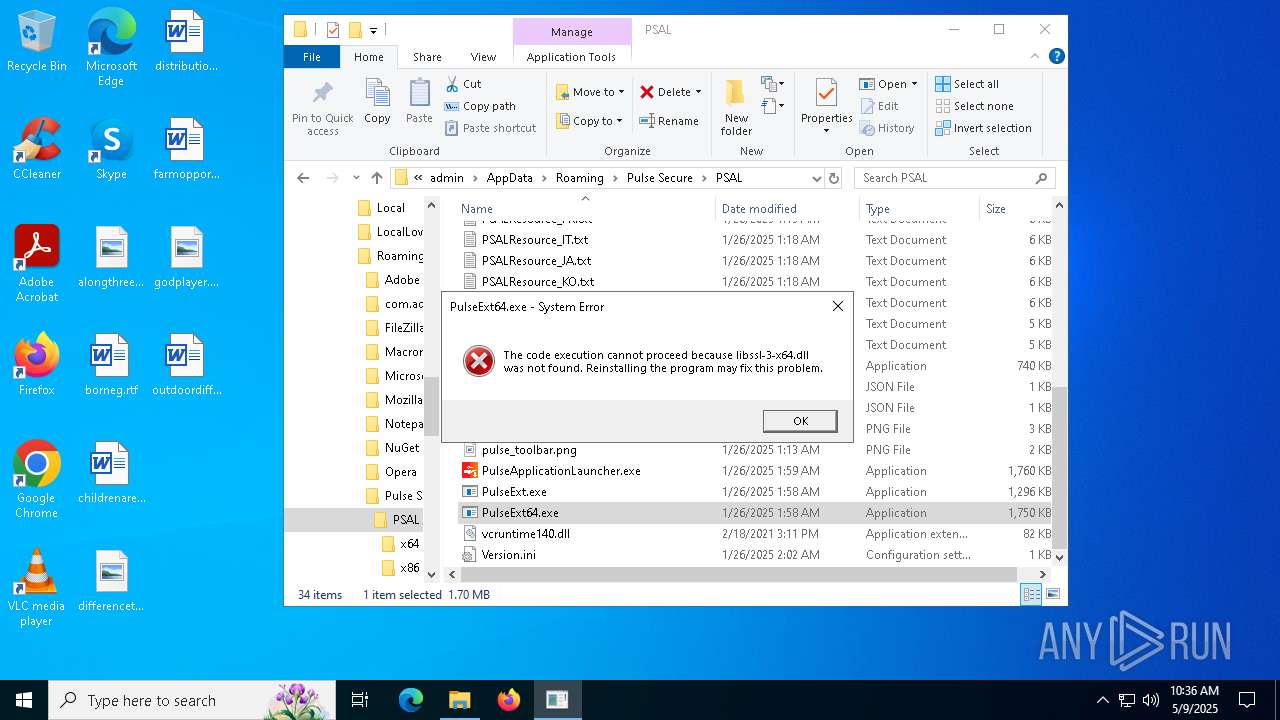
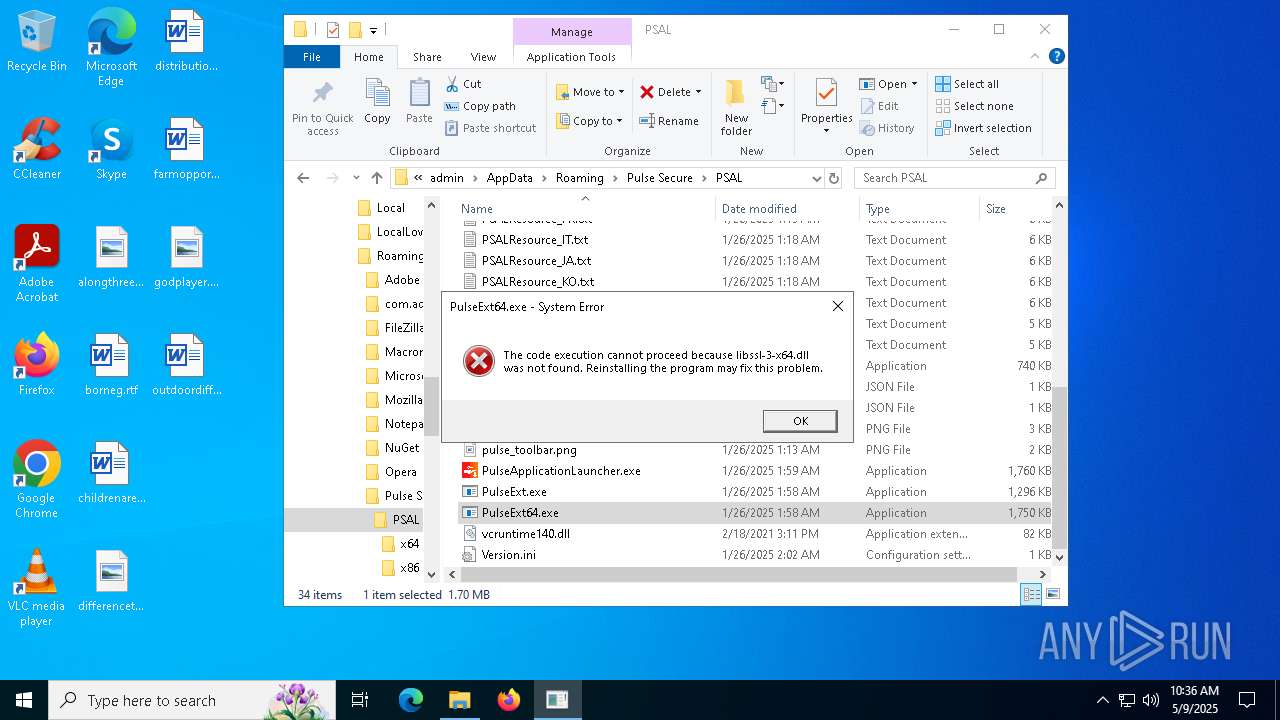
- PulseExt64.exe (PID: 8016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Pulse Application Launcher |
| Author: | Ivanti, Inc. |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Pulse Application Launcher. |
| Template: | Intel;1033 |
| RevisionNumber: | {18C4DC19-FD03-42A0-A147-A118C14E5649} |
| CreateDate: | 2025:01:26 10:02:38 |
| ModifyDate: | 2025:01:26 10:02:38 |
| Pages: | 300 |
| Words: | 10 |
| Software: | Windows Installer XML Toolset (3.14.1.8722) |
| Security: | Read-only recommended |
Total processes
154
Monitored processes
17
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Users\admin\AppData\Roaming\Pulse Secure\PSAL\PulseApplicationLauncher.exe" PSALInstallFinished | C:\Users\admin\AppData\Roaming\Pulse Secure\PSAL\PulseApplicationLauncher.exe | — | msiexec.exe | |||||||||||
User: admin Company: Ivanti, Inc. Integrity Level: MEDIUM Description: Pulse Secure Application Launcher Exit code: 0 Version: 22, 8, 1, 31437 Modules
| |||||||||||||||
| 2392 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\PulseSecureAppLauncher__2_.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | C:\Windows\syswow64\MsiExec.exe -Embedding 70733B233D8086965D2A1EF206E2D2B7 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | "C:\Users\admin\AppData\Roaming\Pulse Secure\PSAL\PulseApplicationLauncher.exe" | C:\Users\admin\AppData\Roaming\Pulse Secure\PSAL\PulseApplicationLauncher.exe | — | explorer.exe | |||||||||||
User: admin Company: Ivanti, Inc. Integrity Level: MEDIUM Description: Pulse Secure Application Launcher Exit code: 4294967295 Version: 22, 8, 1, 31437 Modules
| |||||||||||||||
| 6004 | "C:\Users\admin\AppData\Roaming\Pulse Secure\PSAL\x64\PulseApplicationLauncher.exe" | C:\Users\admin\AppData\Roaming\Pulse Secure\PSAL\x64\PulseApplicationLauncher.exe | — | explorer.exe | |||||||||||
User: admin Company: Ivanti, Inc. Integrity Level: MEDIUM Description: Pulse Secure Application Launcher Exit code: 4294967295 Version: 22, 8, 1, 31437 Modules
| |||||||||||||||
| 6112 | "C:\Users\admin\AppData\Roaming\Pulse Secure\PSAL\PulseApplicationLauncher.exe" | C:\Users\admin\AppData\Roaming\Pulse Secure\PSAL\PulseApplicationLauncher.exe | — | explorer.exe | |||||||||||
User: admin Company: Ivanti, Inc. Integrity Level: MEDIUM Description: Pulse Secure Application Launcher Exit code: 4294967295 Version: 22, 8, 1, 31437 Modules
| |||||||||||||||
| 7228 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7284 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7348 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 827
Read events
12 482
Write events
325
Delete events
20
Modification events
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000002B427DBCDC0DB01B41C0000E81C0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000002B427DBCDC0DB01B41C0000E81C0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000032F877DBCDC0DB01B41C0000E81C0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000032F877DBCDC0DB01B41C0000E81C0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000003FBF7CDBCDC0DB01B41C0000E81C0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000024227FDBCDC0DB01B41C0000E81C0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000BC9510DCCDC0DB01B41C0000E81C0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7348) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000037F912DCCDC0DB01B41C0000701D0000E80300000100000000000000000000007EC5E6FCDC69B04791746B2B7EB0241800000000000000000000000000000000 | |||
| (PID) Process: | (7436) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000AD4021DCCDC0DB010C1D0000941D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
46
Suspicious files
26
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7348 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7348 | msiexec.exe | C:\Windows\Installer\11216f.msi | — | |
MD5:— | SHA256:— | |||
| 2392 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:686040315D8A2A17B240A4179326B9F3 | SHA256:EF6CEB5A39CD94686F8DB3CFAA8BD5D21F95195930E7BF022FFDA7E7F10DC7DA | |||
| 2392 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_5860AD8F4270EFB91F3E5FD27AAAAB78 | binary | |
MD5:3F3ECE1C7C48D29AA2D6C62ED04A32BD | SHA256:17339D2CEBD169B8C68A53F05F7E12AD44948B7FC799E4C7A565C155D69D86AA | |||
| 7348 | msiexec.exe | C:\Windows\Installer\MSI2363.tmp | executable | |
MD5:8EDC1557E9FC7F25F89AD384D01BCEC4 | SHA256:78860E15E474CC2AF7AD6E499A8971B6B8197AFB8E49A1B9EAAA392E4378F3A5 | |||
| 2392 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:38ACD0885B0AA5A49C1B1353579CE9C6 | SHA256:C358A1830CDE9F3F8D50A35D83737B0549FF1DC284DCCE8DA13CAF77DE9F8975 | |||
| 2392 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:9C77E3AAA9BD13C4B91BB1099CF7F3D3 | SHA256:B17D6168DA07E0D0D242DD239D432F7060F499EDD0E1883F56152411004C627B | |||
| 2392 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:1234AC9D296D681660B46A30D9335457 | SHA256:5CDE7FFEF4C91362E0A7D6263A5EC98326BBD1612BA819F10262A8EB6BFFA326 | |||
| 7348 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{fce6c57e-69dc-47b0-9174-6b2b7eb02418}_OnDiskSnapshotProp | binary | |
MD5:BDDE8149F6049F356DF81EA4DA191809 | SHA256:C57D7814D40ACB00D68AA8D2A08D99DAE34BAB1CABA546F645A408E8F42F1265 | |||
| 2392 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_5860AD8F4270EFB91F3E5FD27AAAAB78 | binary | |
MD5:A68AC81D6A2665C82319A1DB71873F31 | SHA256:2E9596822AB2F327D34290934458194B8AFA4760C07C7A2C98D3609501BA1EF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
46
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.147.64:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2392 | msiexec.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
2392 | msiexec.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
2392 | msiexec.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEApZrg126rO1sbd16expp%2FI%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8044 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8044 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.17.147.64:80 | crl.microsoft.com | Akamai International B.V. | CZ | whitelisted |
— | — | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2392 | msiexec.exe | 2.16.38.4:80 | ocsp.digicert.com | AKAMAI-AS | ES | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.16.38.4:80 | ocsp.digicert.com | AKAMAI-AS | ES | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |