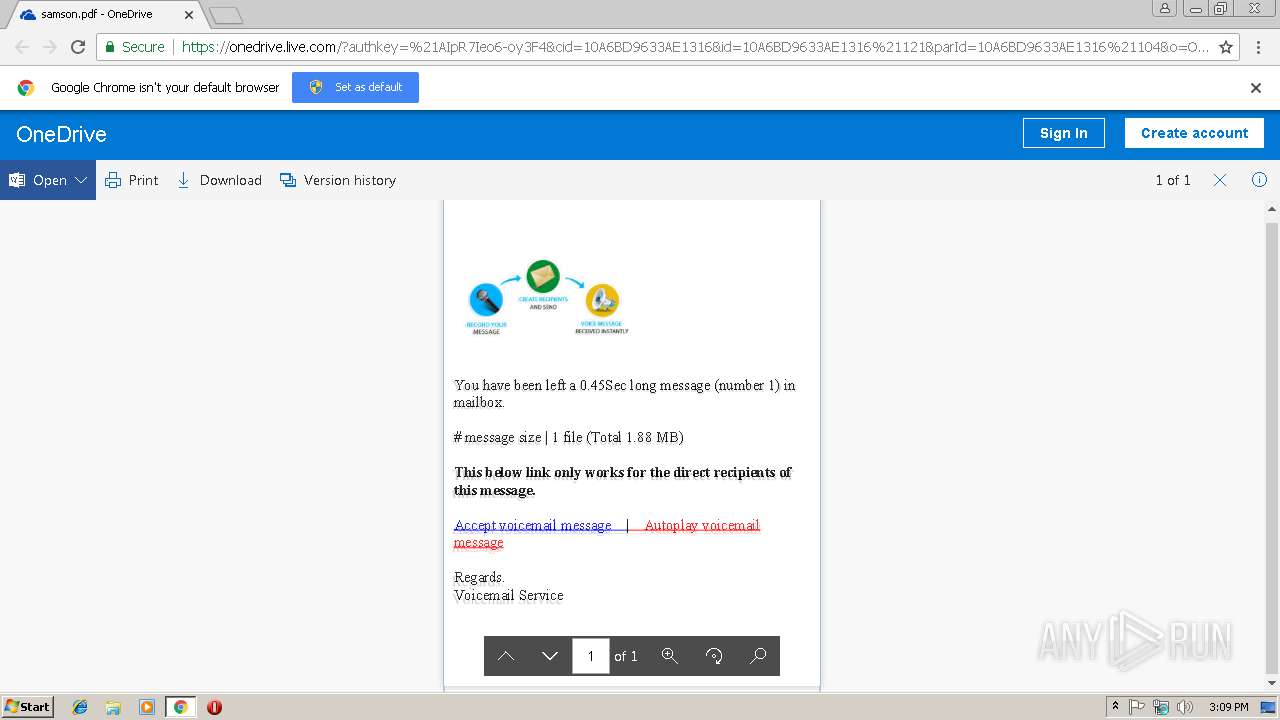
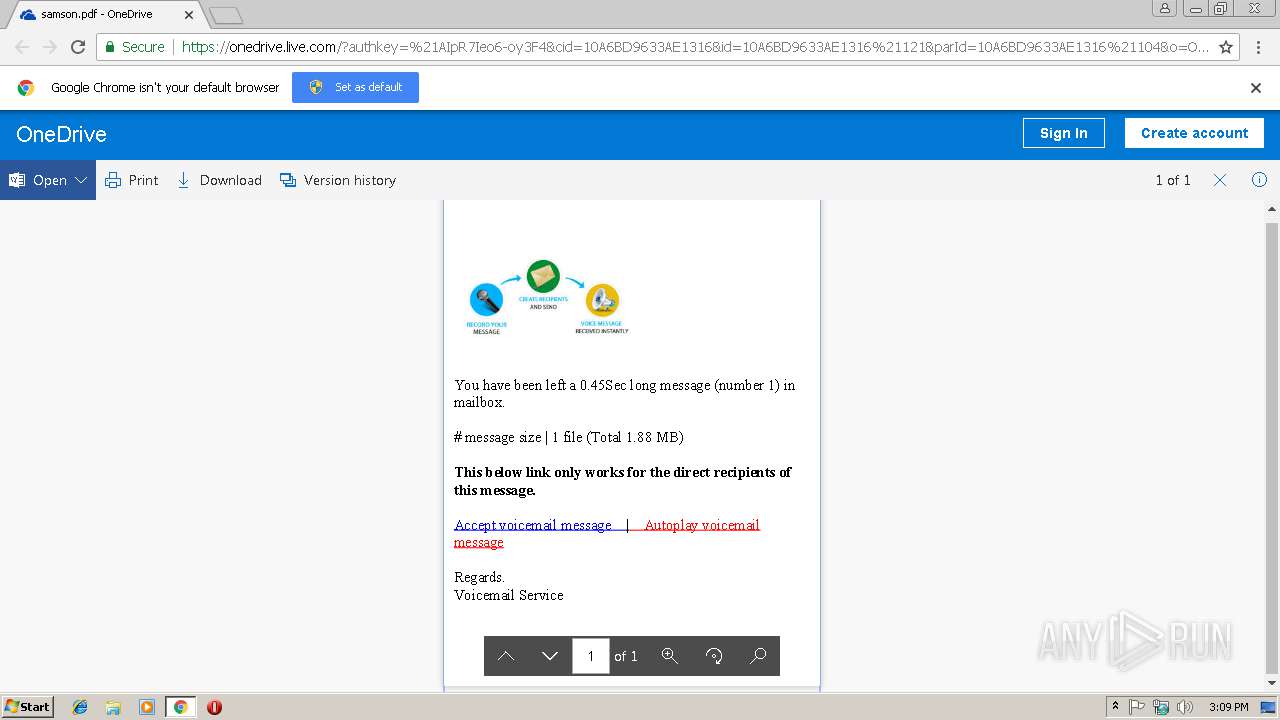
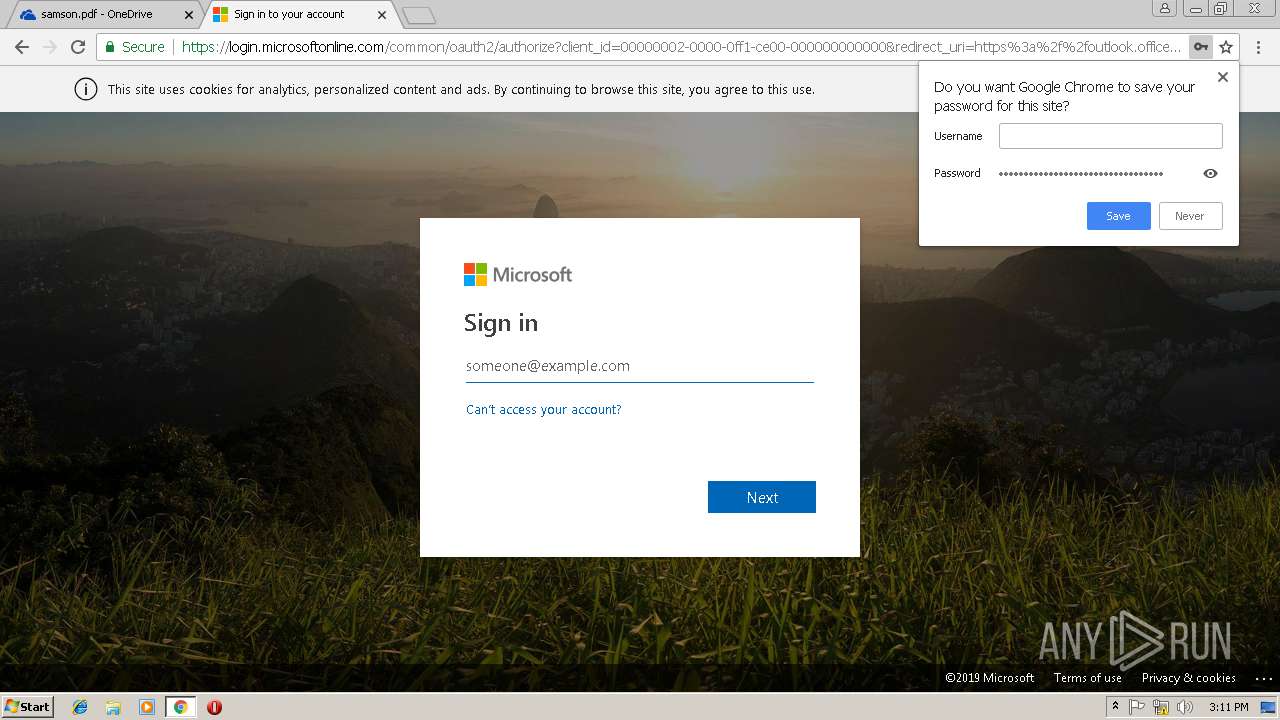
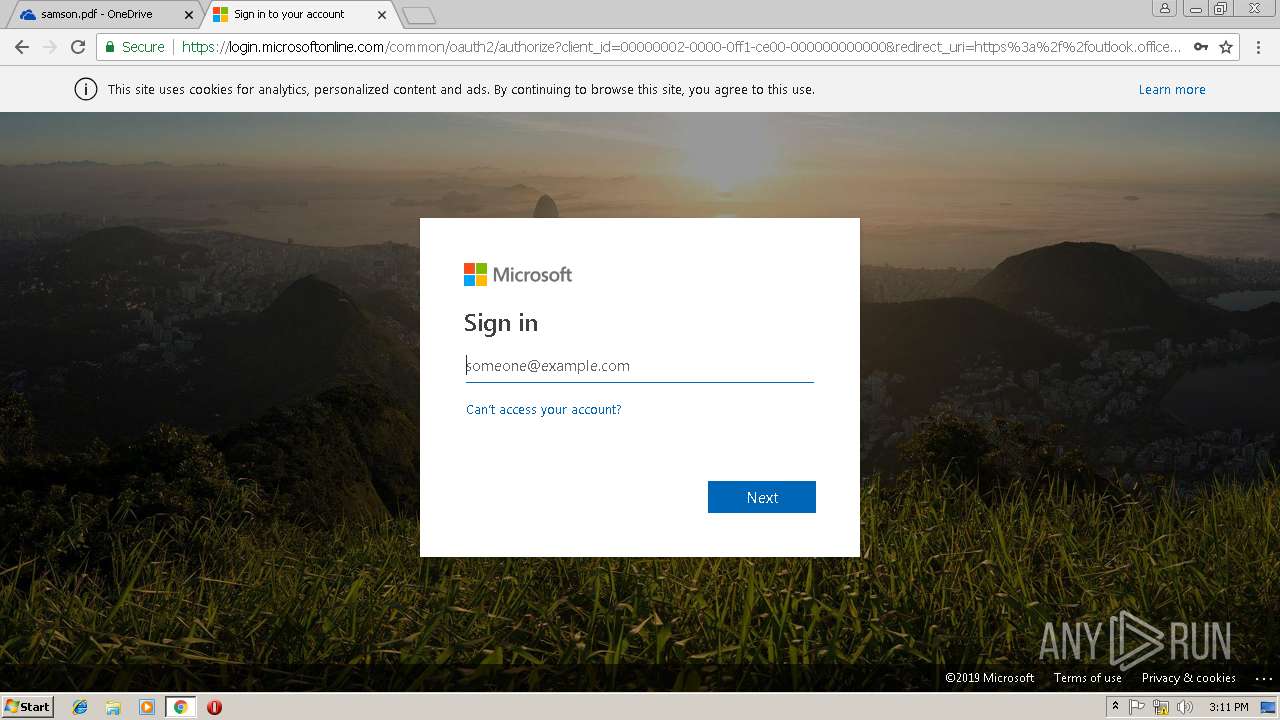
| URL: | https://1drv.ms/b/s!AhYTrjOWvaYQeYpR7Ieo6-oy3F4 |
| Full analysis: | https://app.any.run/tasks/530b0061-51c8-482a-b09f-ce7c7554adb6 |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2019, 15:09:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | EC043E7783F36BC33C206DB6C617532D |
| SHA1: | 2AEDA5EE5DD46224FC2BCFD2BA79DA56F5CADA16 |
| SHA256: | 2700C17674F666229016CDA109C16712289E4AC6A297F9BC5663B36CC8C2BD3A |
| SSDEEP: | 3:N8qDLIWKtfgfqh8i5bjR:2qXPCqi5x |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- chrome.exe (PID: 3044)
Reads settings of System Certificates
- chrome.exe (PID: 3044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
11
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=968,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=11BFF5CE3237868FC9DA1CE0606B0AEB --mojo-platform-channel-handle=1016 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=968,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=AA992EDC8AD6F48EBA1FFF1DF04D2628 --mojo-platform-channel-handle=2064 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --service-pipe-token=98A86E6E5CC476BBB1D07F820D7A7F04 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=98A86E6E5CC476BBB1D07F820D7A7F04 --renderer-client-id=4 --mojo-platform-channel-handle=1904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2924 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=968,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=6A0BDAE01A643BF5F61E2E4983C785E6 --mojo-platform-channel-handle=4164 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2968 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=C27592CE682187674A7A3447D0ADC3AC --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=C27592CE682187674A7A3447D0ADC3AC --renderer-client-id=5 --mojo-platform-channel-handle=3748 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3048 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=968,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=62D0B6B6361944D08E0C0E4A096D628B --mojo-platform-channel-handle=2380 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://1drv.ms/b/s!AhYTrjOWvaYQeYpR7Ieo6-oy3F4 | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --service-pipe-token=EB666D43CB8972D5E97992BA38D9277A --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=EB666D43CB8972D5E97992BA38D9277A --renderer-client-id=3 --mojo-platform-channel-handle=2164 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,3031516371800422712,2667241742975915268,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=9CD4831F36EF13D320A34B50ADBE7FEF --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9CD4831F36EF13D320A34B50ADBE7FEF --renderer-client-id=6 --mojo-platform-channel-handle=2408 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
550
Read events
500
Write events
47
Delete events
3
Modification events
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3044-13192643359339750 |
Value: 259 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3044-13192643359339750 |
Value: 259 | |||
| (PID) Process: | (3044) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
0
Suspicious files
61
Text files
111
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\7b24d70b-91af-4da9-b195-dea8a7c6f700.tmp | — | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ae566d00-6197-406d-88f6-52545c55f263.tmp | — | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF20ea06.TMP | text | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF20ea54.TMP | text | |
MD5:— | SHA256:— | |||
| 3044 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Thumbnails\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
74
DNS requests
41
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
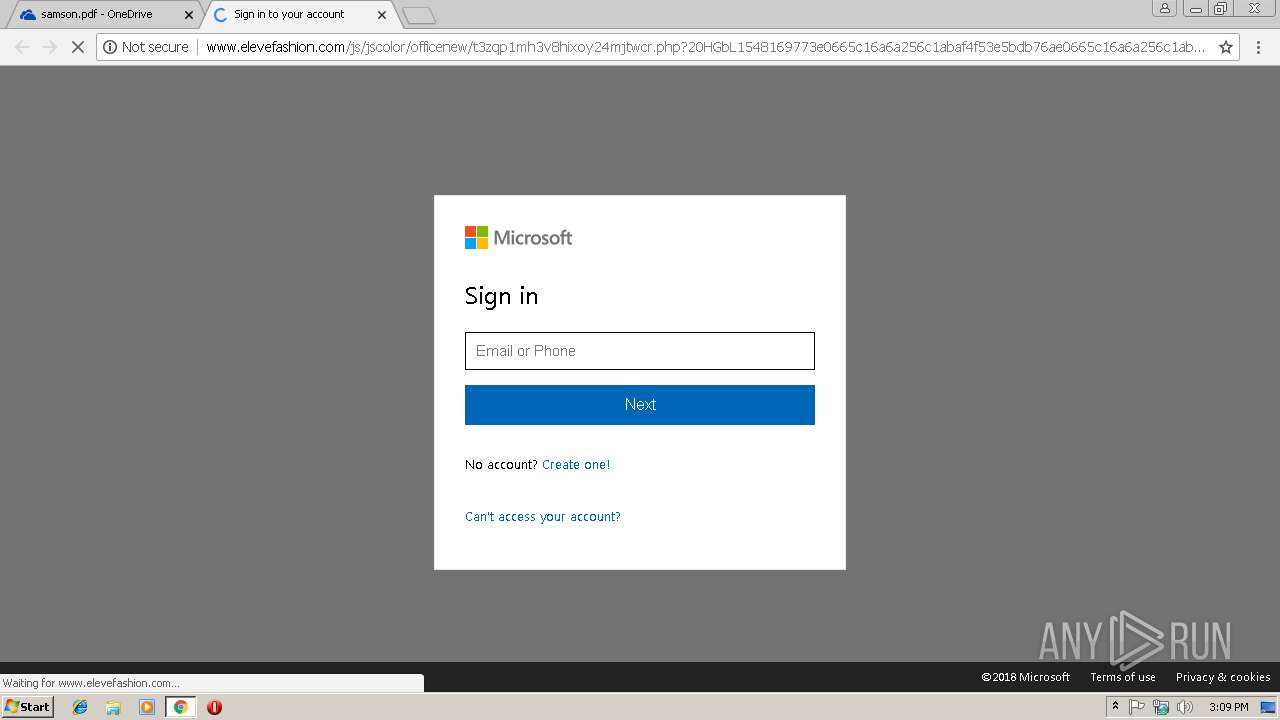
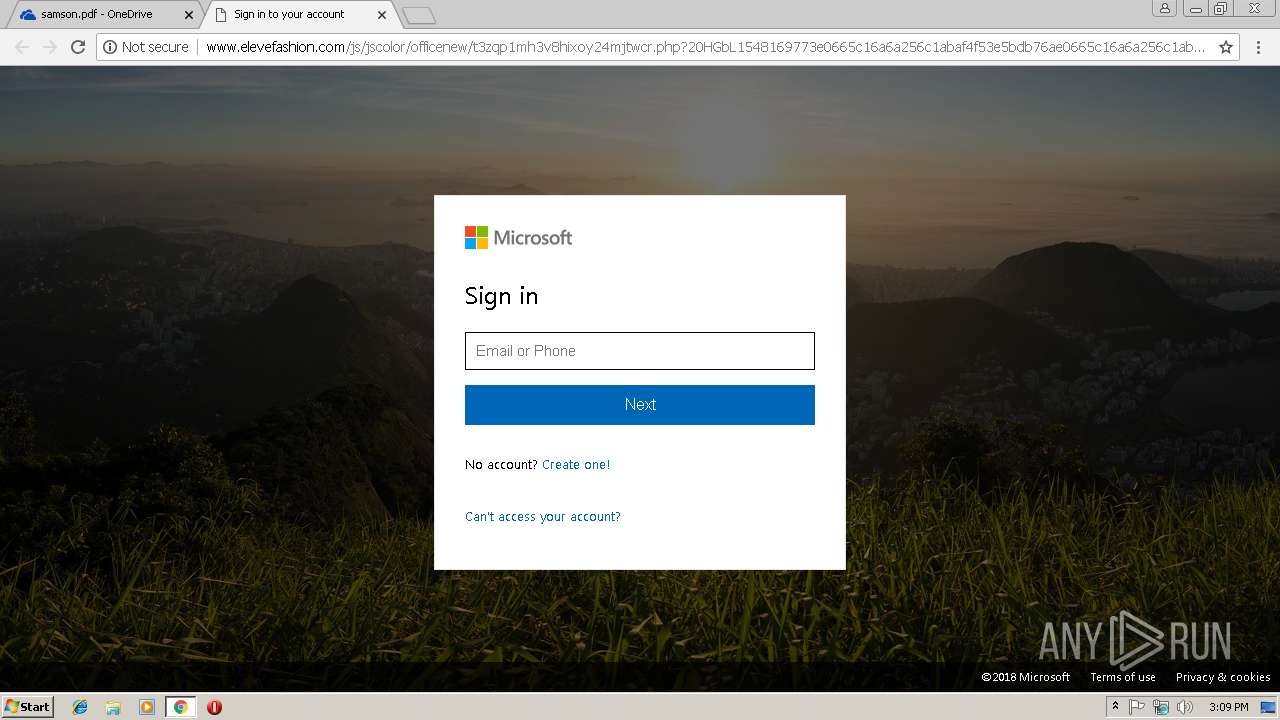
3044 | chrome.exe | GET | — | 27.254.38.17:80 | http://www.elevefashion.com/js/jscolor/officenew/images/0.jpg | TH | — | — | suspicious |
3044 | chrome.exe | GET | 200 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 55.2 Kb | whitelisted |
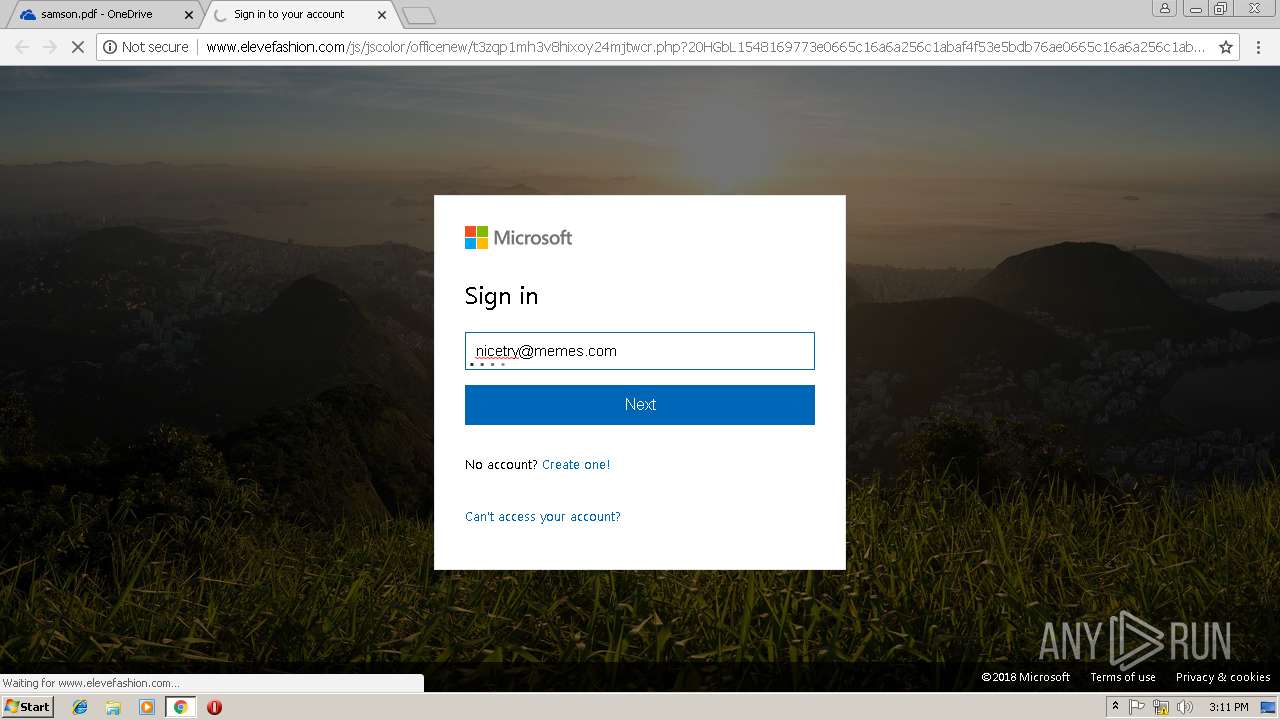
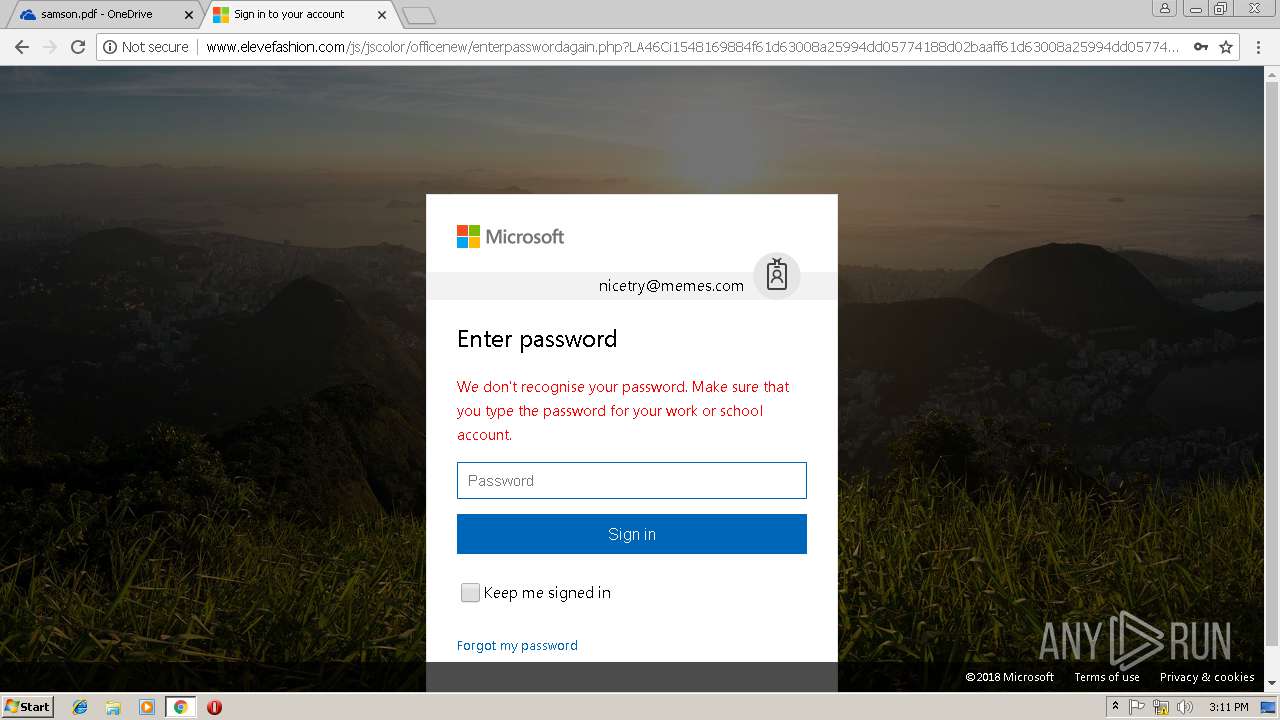
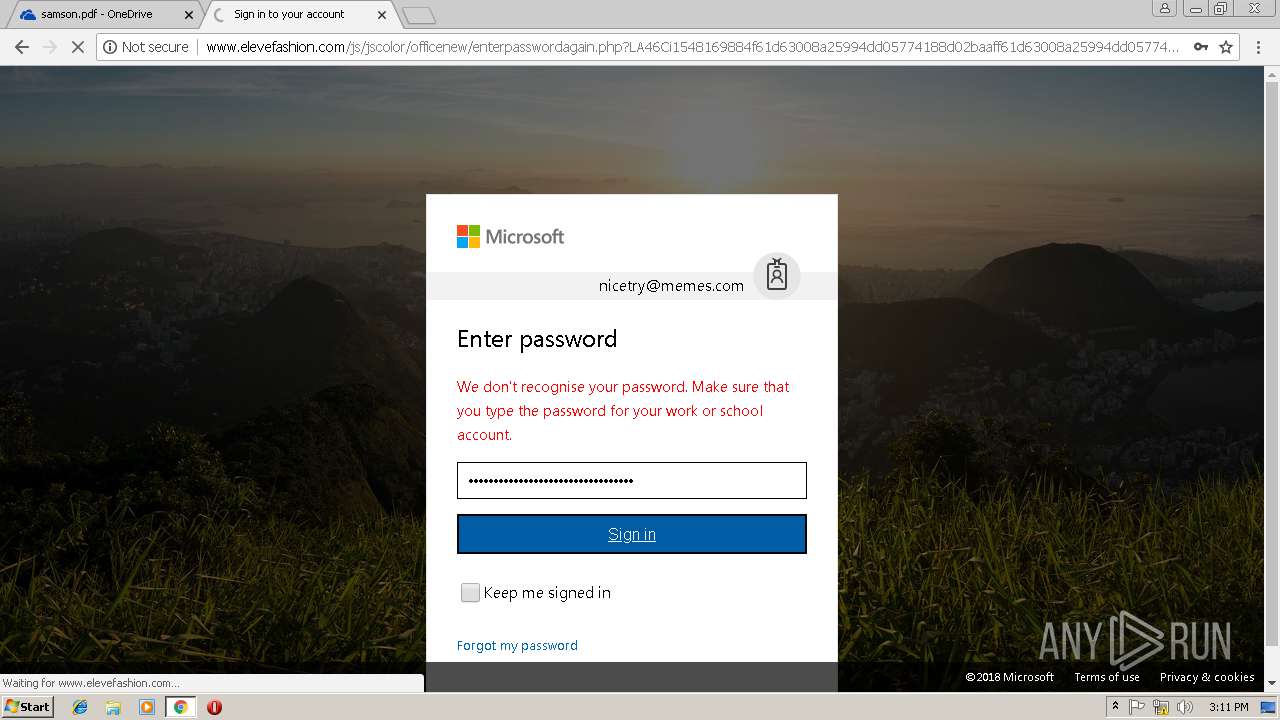
3044 | chrome.exe | GET | 302 | 27.254.38.17:80 | http://www.elevefashion.com/js/jscolor/officenew/retry.php?33b0J21548169883e46ce8e30954c72d803b5a9a391f2d5de46ce8e30954c72d803b5a9a391f2d5de46ce8e30954c72d803b5a9a391f2d5de46ce8e30954c72d803b5a9a391f2d5de46ce8e30954c72d803b5a9a391f2d5d&email=nicetry@memes.com&error=2 | TH | html | 1.15 Kb | suspicious |
3044 | chrome.exe | POST | 302 | 27.254.38.17:80 | http://www.elevefashion.com/js/jscolor/officenew/submit.php | TH | — | — | suspicious |
3044 | chrome.exe | GET | 301 | 27.254.38.17:80 | http://www.elevefashion.com/js/jscolor/officenew | TH | html | 257 b | suspicious |
3044 | chrome.exe | POST | 302 | 27.254.38.17:80 | http://www.elevefashion.com/js/jscolor/officenew/resubmit.php | TH | — | — | suspicious |
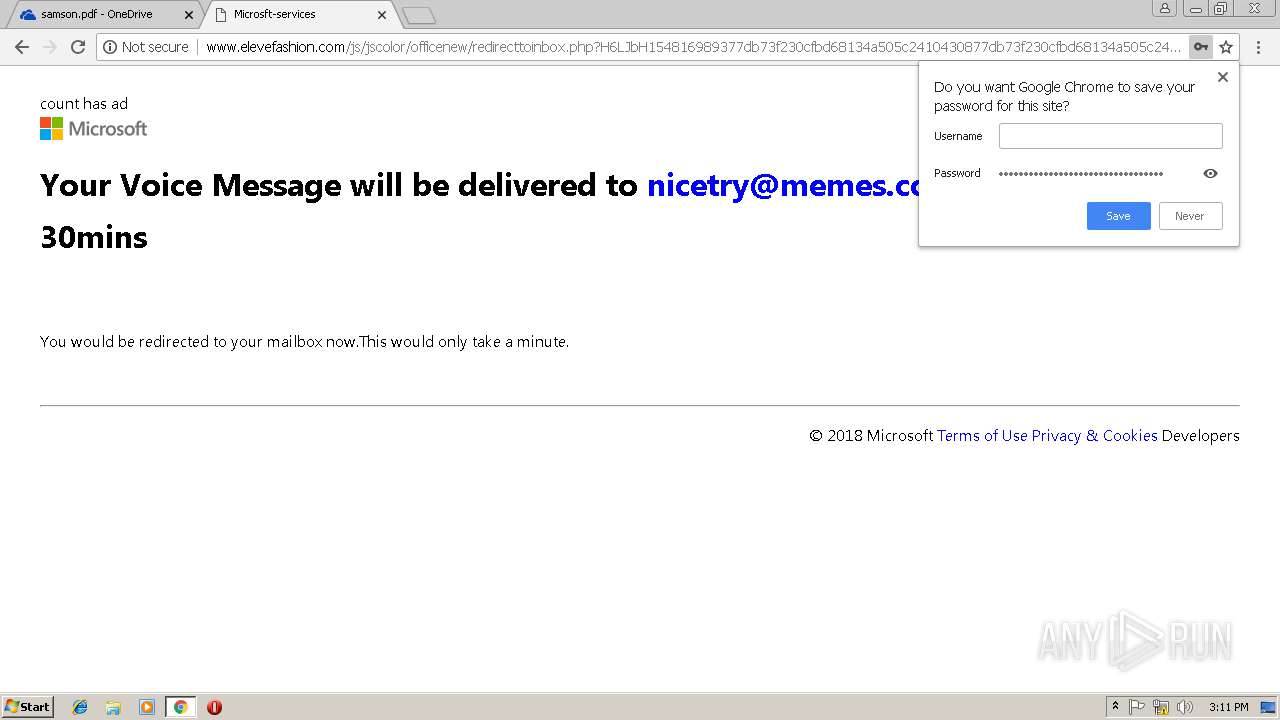
3044 | chrome.exe | GET | 200 | 27.254.38.17:80 | http://www.elevefashion.com/js/jscolor/officenew/redirecttoinbox.php?H6LJbH154816989377db73f230cfbd68134a505c2410430877db73f230cfbd68134a505c2410430877db73f230cfbd68134a505c2410430877db73f230cfbd68134a505c2410430877db73f230cfbd68134a505c24104308&email=nicetry@memes.com | TH | html | 887 b | suspicious |
3044 | chrome.exe | GET | 200 | 27.254.38.17:80 | http://www.elevefashion.com/favicon.ico | TH | image | 697 b | suspicious |
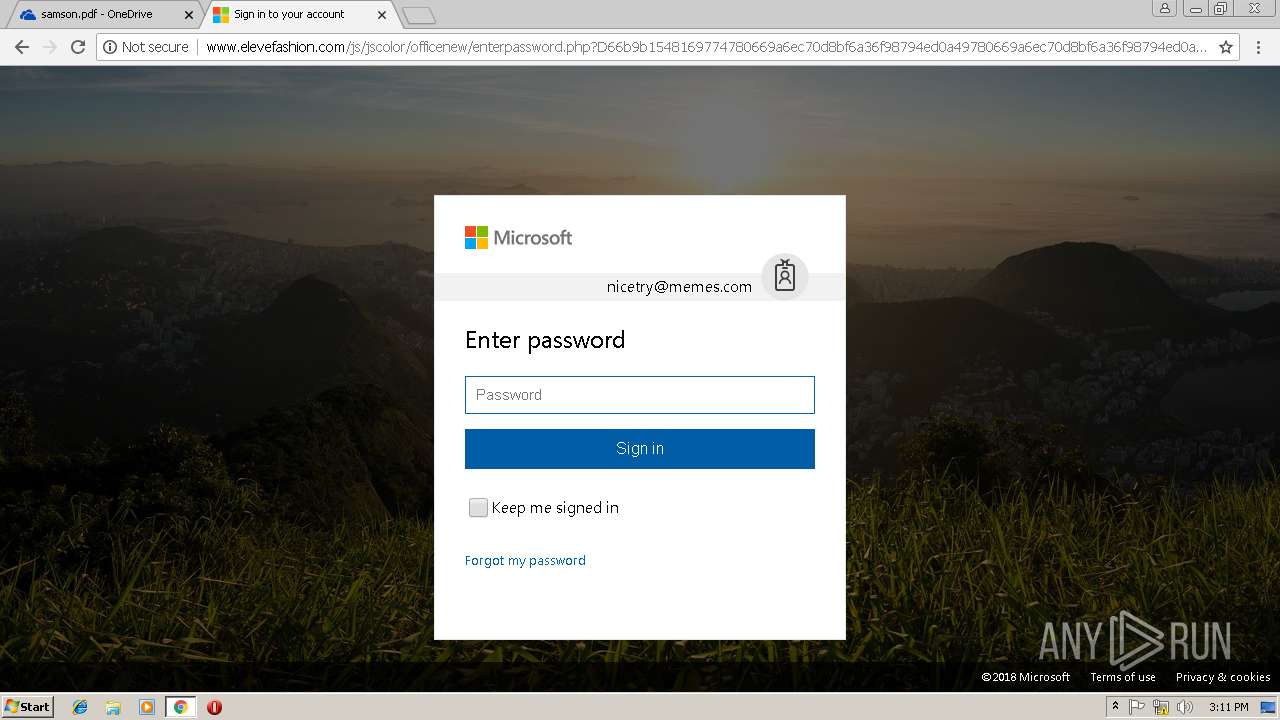
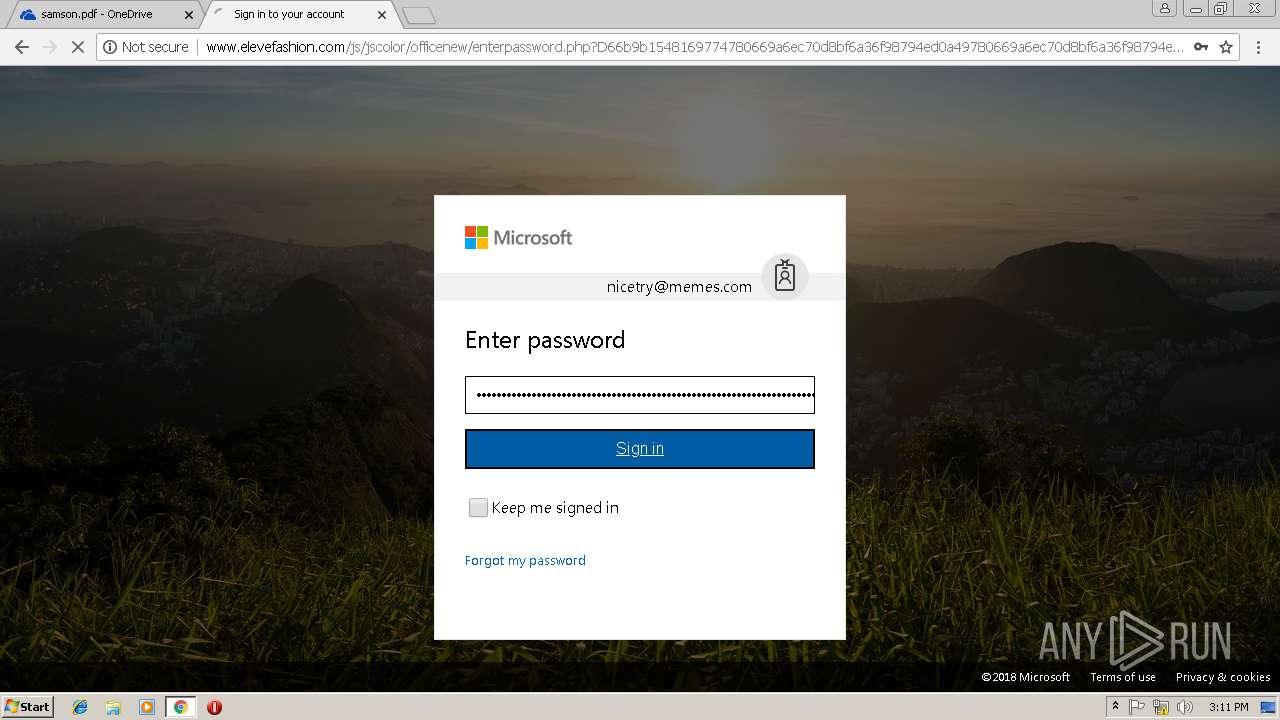
3044 | chrome.exe | POST | 200 | 27.254.38.17:80 | http://www.elevefashion.com/js/jscolor/officenew/enterpassword.php?D66b9b1548169774780669a6ec70d8bf6a36f98794ed0a49780669a6ec70d8bf6a36f98794ed0a49780669a6ec70d8bf6a36f98794ed0a49780669a6ec70d8bf6a36f98794ed0a49780669a6ec70d8bf6a36f98794ed0a49 | TH | html | 758 b | suspicious |
3044 | chrome.exe | GET | 200 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/DF3C24F9BFD666761B268073FE06D1CC8D4F82A4.crt | unknown | der | 914 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3044 | chrome.exe | 172.217.16.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3044 | chrome.exe | 216.58.208.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3044 | chrome.exe | 13.107.42.12:443 | 1drv.ms | Microsoft Corporation | US | suspicious |
3044 | chrome.exe | 172.217.23.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3044 | chrome.exe | 13.107.42.13:443 | onedrive.live.com | Microsoft Corporation | US | malicious |
3044 | chrome.exe | 2.16.186.25:443 | spoprod-a.akamaihd.net | Akamai International B.V. | — | whitelisted |
3044 | chrome.exe | 40.90.136.179:443 | skyapi.onedrive.live.com | Microsoft Corporation | US | whitelisted |
3044 | chrome.exe | 104.103.74.164:443 | static2.sharepointonline.com | Akamai Technologies, Inc. | NL | whitelisted |
3044 | chrome.exe | 104.103.82.209:443 | p.sfx.ms | Akamai Technologies, Inc. | NL | whitelisted |
3044 | chrome.exe | 52.114.32.7:443 | browser.pipe.aria.microsoft.com | Microsoft Corporation | JP | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
1drv.ms |
| shared |
accounts.google.com |
| shared |
onedrive.live.com |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
spoprod-a.akamaihd.net |
| whitelisted |
static2.sharepointonline.com |
| whitelisted |
skyapi.onedrive.live.com |
| shared |
p.sfx.ms |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
3044 | chrome.exe | A Network Trojan was detected | SC BACKDOOR TeleRAT webhook using attempt |
3044 | chrome.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
3044 | chrome.exe | A Network Trojan was detected | SC BACKDOOR TeleRAT webhook using attempt |
3044 | chrome.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
1 ETPRO signatures available at the full report