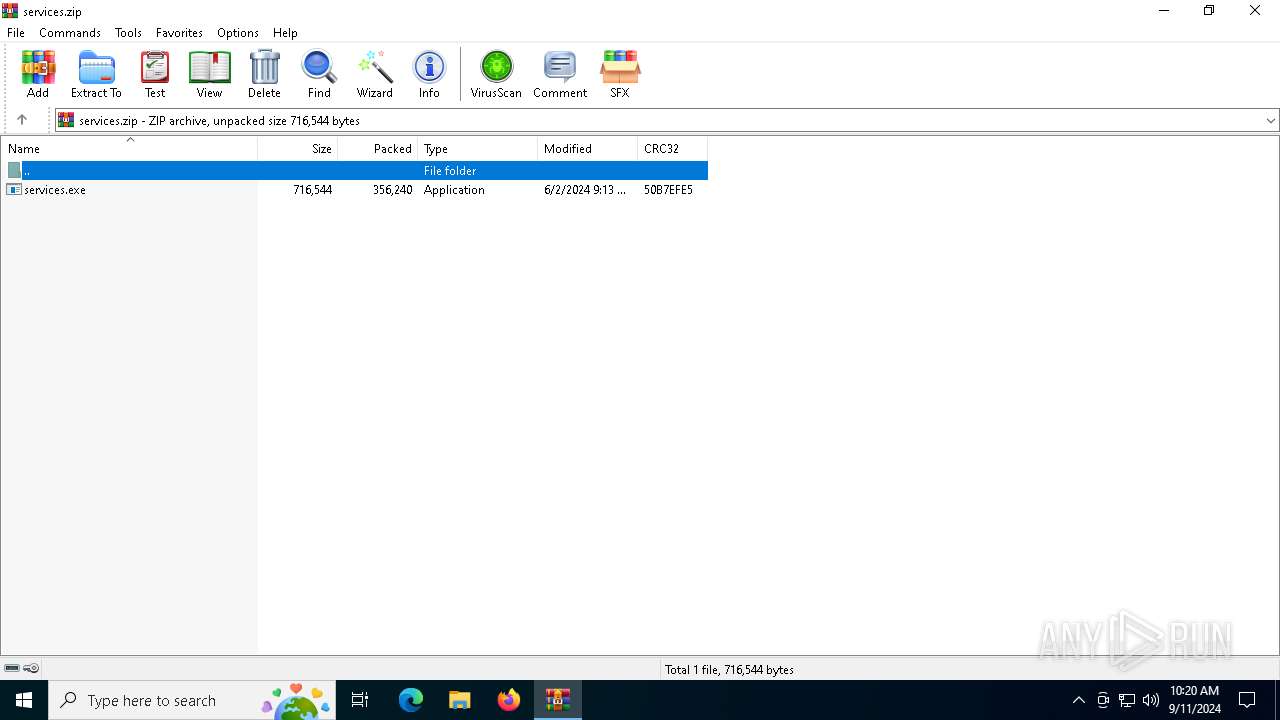
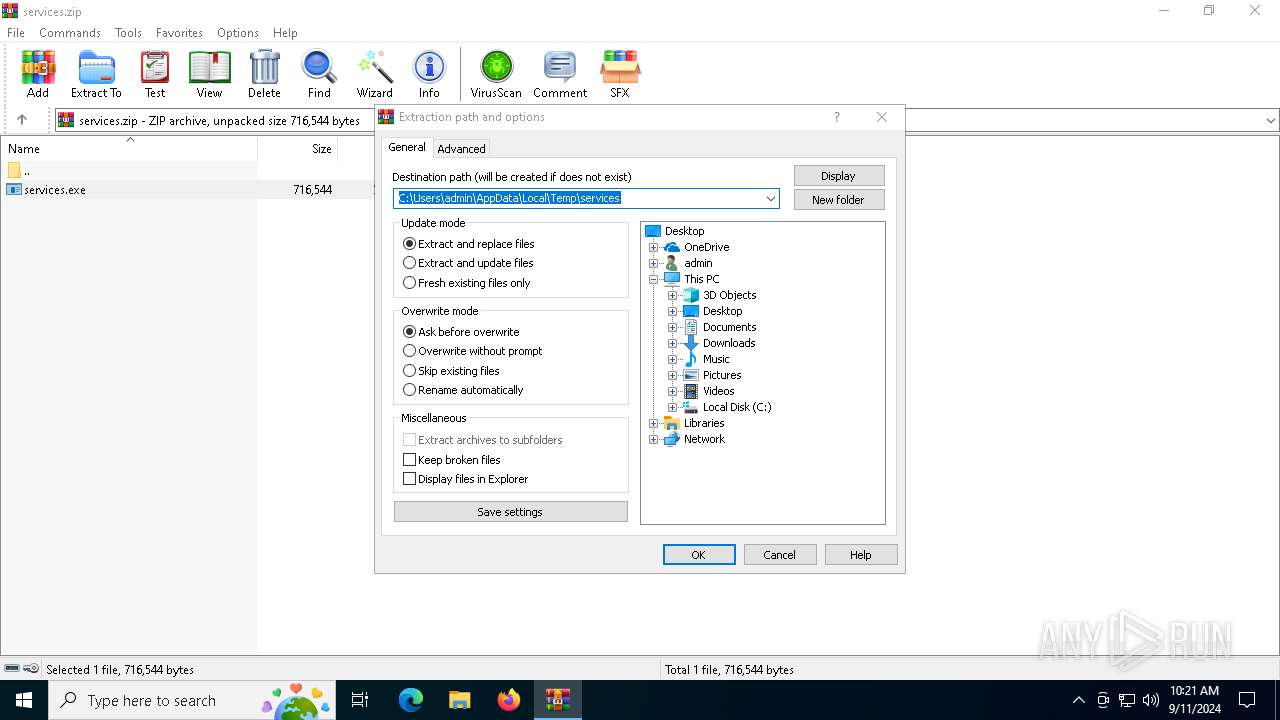
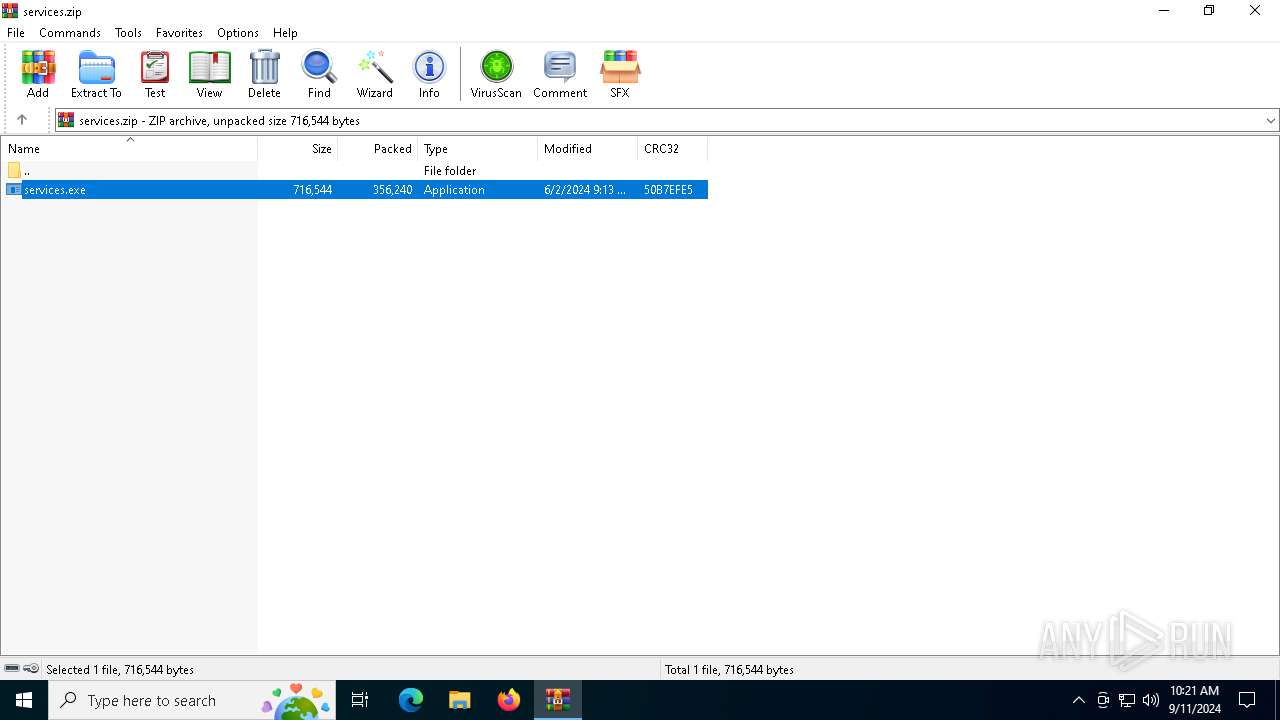
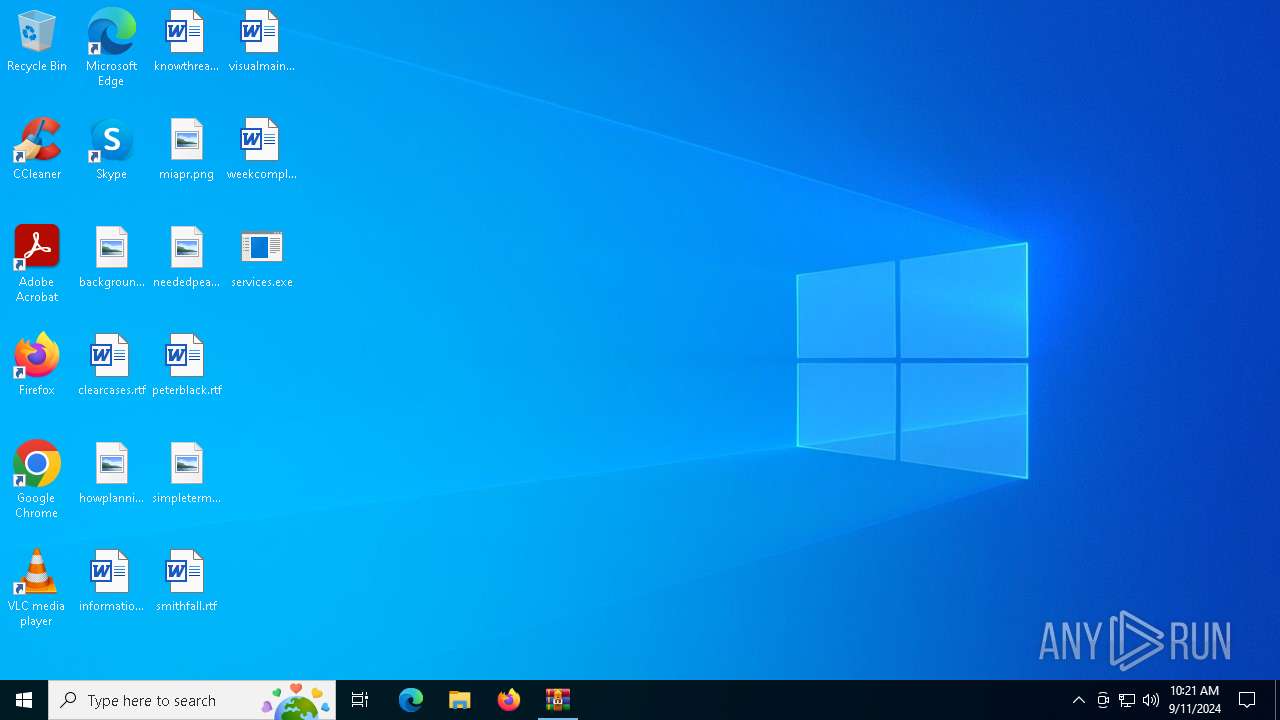
| File name: | services.zip |
| Full analysis: | https://app.any.run/tasks/8f86e599-2287-4fb9-9ff0-ade374b0b6da |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2024, 10:20:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6BFA49F5534F8A4D8CBB7EC78EC9896B |
| SHA1: | 166D4DABD2268A30652C75D9EBA55A97CC0A9CD8 |
| SHA256: | 26A634FAEF1C2ADAC22716E7792EC733F189A55B1AE934BE42E7FD899D80B136 |
| SSDEEP: | 12288:1ioNCeTSt/IObC1Ih9MxkQ5U3q3fbHTiKrPgDKEdT6Gn:1hNCeTSt/Lbjh9MxkQ5U3q3zHTiKrPgB |
MALICIOUS
No malicious indicators.SUSPICIOUS
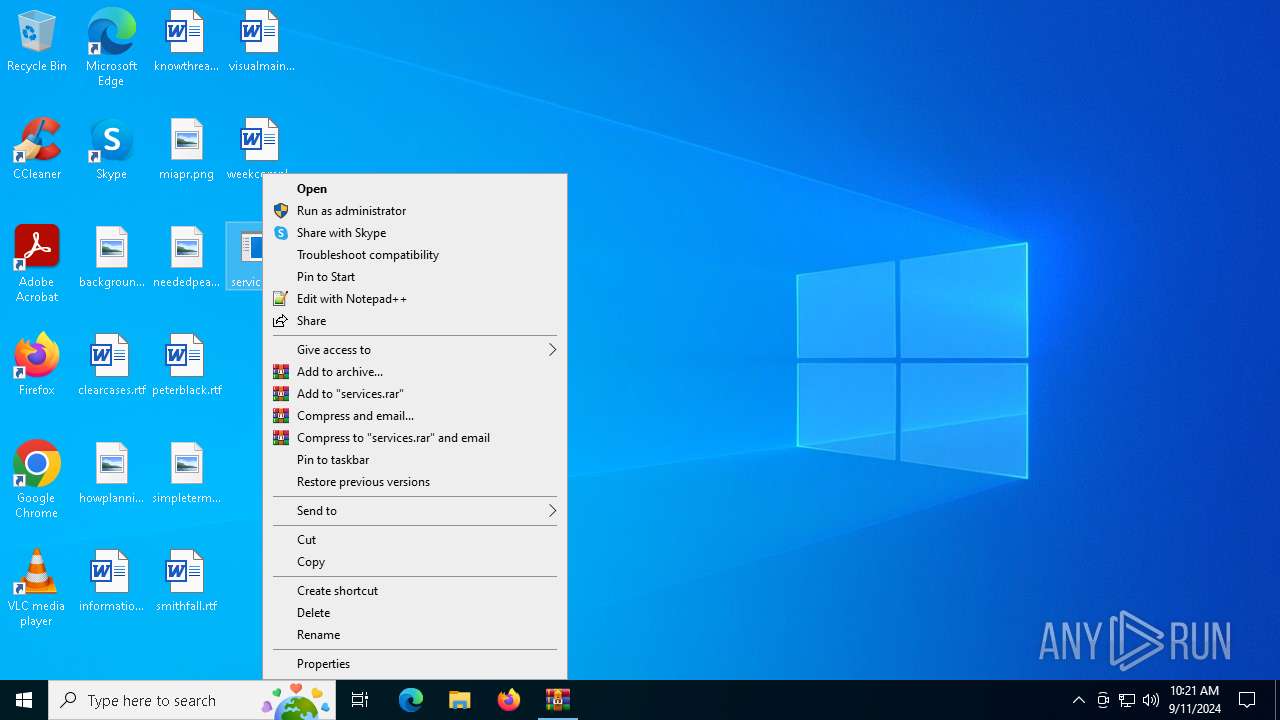
Process drops legitimate windows executable
- WinRAR.exe (PID: 5700)
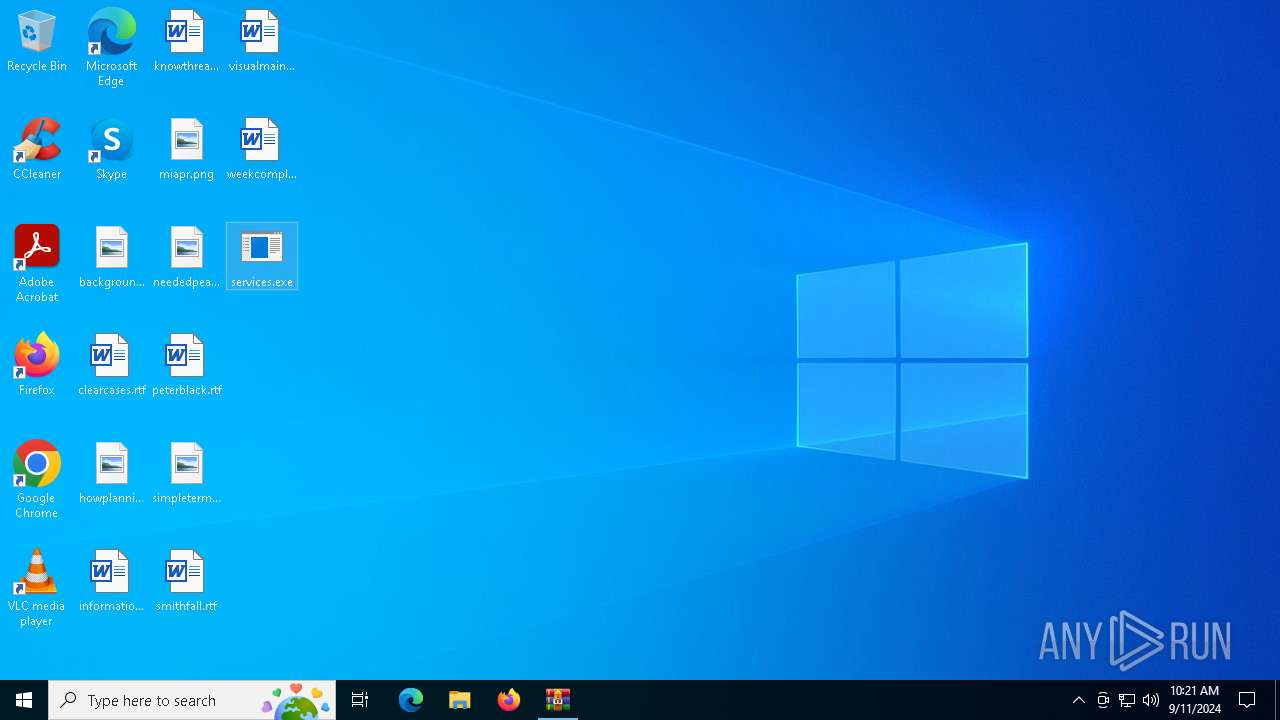
Starts a Microsoft application from unusual location
- services.exe (PID: 4980)
- services.exe (PID: 4128)
- services.exe (PID: 5888)
- services.exe (PID: 1712)
- services.exe (PID: 1496)
- services.exe (PID: 5044)
- services.exe (PID: 4100)
- services.exe (PID: 1840)
- services.exe (PID: 4088)
- services.exe (PID: 4064)
- services.exe (PID: 2092)
- services.exe (PID: 1372)
- services.exe (PID: 4068)
- services.exe (PID: 3112)
- services.exe (PID: 5980)
- services.exe (PID: 6416)
- services.exe (PID: 6308)
- services.exe (PID: 1156)
- services.exe (PID: 1656)
- services.exe (PID: 7092)
- services.exe (PID: 644)
- services.exe (PID: 2580)
- services.exe (PID: 752)
- services.exe (PID: 3832)
- services.exe (PID: 6968)
- services.exe (PID: 7152)
- services.exe (PID: 6112)
- services.exe (PID: 6916)
- services.exe (PID: 1184)
- services.exe (PID: 4132)
- services.exe (PID: 6984)
- services.exe (PID: 5476)
- services.exe (PID: 2768)
- services.exe (PID: 6184)
- services.exe (PID: 2136)
- services.exe (PID: 1140)
- services.exe (PID: 236)
- services.exe (PID: 6644)
- services.exe (PID: 1020)
- services.exe (PID: 376)
- services.exe (PID: 6876)
- services.exe (PID: 888)
- services.exe (PID: 3028)
- services.exe (PID: 1372)
- services.exe (PID: 1568)
- services.exe (PID: 6396)
- services.exe (PID: 4392)
- services.exe (PID: 3328)
- services.exe (PID: 6976)
- services.exe (PID: 3272)
- services.exe (PID: 2368)
- services.exe (PID: 6280)
- services.exe (PID: 6892)
- services.exe (PID: 4248)
- services.exe (PID: 6928)
- services.exe (PID: 1432)
- services.exe (PID: 232)
- services.exe (PID: 6100)
- services.exe (PID: 5088)
- services.exe (PID: 5772)
- services.exe (PID: 6264)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 5700)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5700)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5700)
Checks supported languages
- services.exe (PID: 4128)
- services.exe (PID: 4980)
- services.exe (PID: 5888)
- services.exe (PID: 1712)
- services.exe (PID: 1496)
- services.exe (PID: 5044)
- services.exe (PID: 1840)
- services.exe (PID: 4100)
- services.exe (PID: 4088)
- services.exe (PID: 4064)
- services.exe (PID: 2092)
- services.exe (PID: 1372)
- services.exe (PID: 4068)
- services.exe (PID: 5980)
- services.exe (PID: 6308)
- services.exe (PID: 3112)
- services.exe (PID: 6416)
- services.exe (PID: 2580)
- services.exe (PID: 1656)
- services.exe (PID: 7092)
- services.exe (PID: 1156)
- services.exe (PID: 752)
- services.exe (PID: 6968)
- services.exe (PID: 7152)
- services.exe (PID: 644)
- services.exe (PID: 6112)
- services.exe (PID: 3832)
- services.exe (PID: 1184)
- services.exe (PID: 6984)
- services.exe (PID: 5476)
- services.exe (PID: 6916)
- services.exe (PID: 4132)
- services.exe (PID: 2136)
- services.exe (PID: 2768)
- services.exe (PID: 6184)
- services.exe (PID: 1140)
- services.exe (PID: 6644)
- services.exe (PID: 1020)
- services.exe (PID: 376)
- services.exe (PID: 6876)
- services.exe (PID: 888)
- services.exe (PID: 236)
- services.exe (PID: 3028)
- services.exe (PID: 1568)
- services.exe (PID: 6976)
- services.exe (PID: 1372)
- services.exe (PID: 4392)
- services.exe (PID: 3272)
- services.exe (PID: 2368)
- services.exe (PID: 3328)
- services.exe (PID: 4248)
- services.exe (PID: 6280)
- services.exe (PID: 6892)
- services.exe (PID: 6396)
- services.exe (PID: 232)
- services.exe (PID: 1432)
- services.exe (PID: 6100)
- services.exe (PID: 5088)
- services.exe (PID: 6928)
- services.exe (PID: 5772)
- services.exe (PID: 6264)
Manual execution by a user
- services.exe (PID: 4980)
- services.exe (PID: 5888)
- services.exe (PID: 4128)
- services.exe (PID: 1712)
- services.exe (PID: 1496)
- services.exe (PID: 1372)
- services.exe (PID: 5044)
- services.exe (PID: 1840)
- services.exe (PID: 2092)
- services.exe (PID: 4088)
- services.exe (PID: 4100)
- services.exe (PID: 4064)
- services.exe (PID: 4068)
- services.exe (PID: 3112)
- services.exe (PID: 5980)
- services.exe (PID: 6308)
- services.exe (PID: 6416)
- services.exe (PID: 752)
- services.exe (PID: 1656)
- services.exe (PID: 7092)
- services.exe (PID: 1156)
- services.exe (PID: 2580)
- services.exe (PID: 3832)
- services.exe (PID: 6968)
- services.exe (PID: 7152)
- services.exe (PID: 644)
- services.exe (PID: 6112)
- services.exe (PID: 6984)
- services.exe (PID: 1184)
- services.exe (PID: 4132)
- services.exe (PID: 5476)
- services.exe (PID: 6916)
- services.exe (PID: 2768)
- services.exe (PID: 2136)
- services.exe (PID: 6184)
- services.exe (PID: 1140)
- services.exe (PID: 376)
- services.exe (PID: 6644)
- services.exe (PID: 1020)
- services.exe (PID: 888)
- services.exe (PID: 6876)
- services.exe (PID: 236)
- services.exe (PID: 1372)
- services.exe (PID: 1568)
- services.exe (PID: 6396)
- services.exe (PID: 3028)
- services.exe (PID: 6892)
- services.exe (PID: 6976)
- services.exe (PID: 3272)
- services.exe (PID: 2368)
- services.exe (PID: 3328)
- services.exe (PID: 4392)
- services.exe (PID: 4248)
- services.exe (PID: 6280)
- services.exe (PID: 6928)
- services.exe (PID: 1432)
- services.exe (PID: 232)
- services.exe (PID: 6100)
- services.exe (PID: 5772)
- services.exe (PID: 5088)
- services.exe (PID: 6264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:02 21:13:32 |
| ZipCRC: | 0x50b7efe5 |
| ZipCompressedSize: | 356240 |
| ZipUncompressedSize: | 716544 |
| ZipFileName: | services.exe |
Total processes
183
Monitored processes
62
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Users\admin\Desktop\services.exe" | C:\Users\admin\Desktop\services.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Services and Controller app Exit code: 0 Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 105
Read events
2 098
Write events
7
Delete events
0
Modification events
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\services.zip | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5700 | WinRAR.exe | C:\Users\admin\Desktop\services.exe | executable | |
MD5:4EACBE64BB1E7D58E8A26340ED1C7CBD | SHA256:1EFD9A81B2DDF21B3F327D67A6F8F88F814979E84085EC812AF72450310D4281 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
26
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1492 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6552 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1492 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |