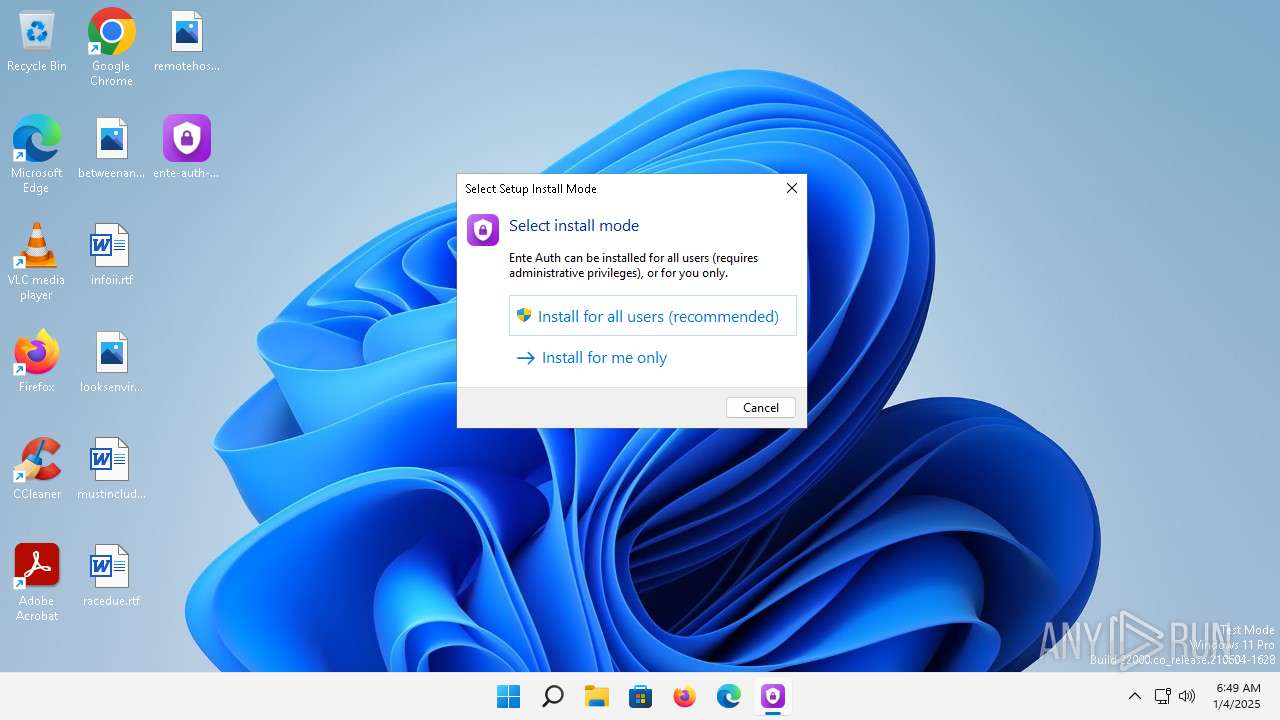
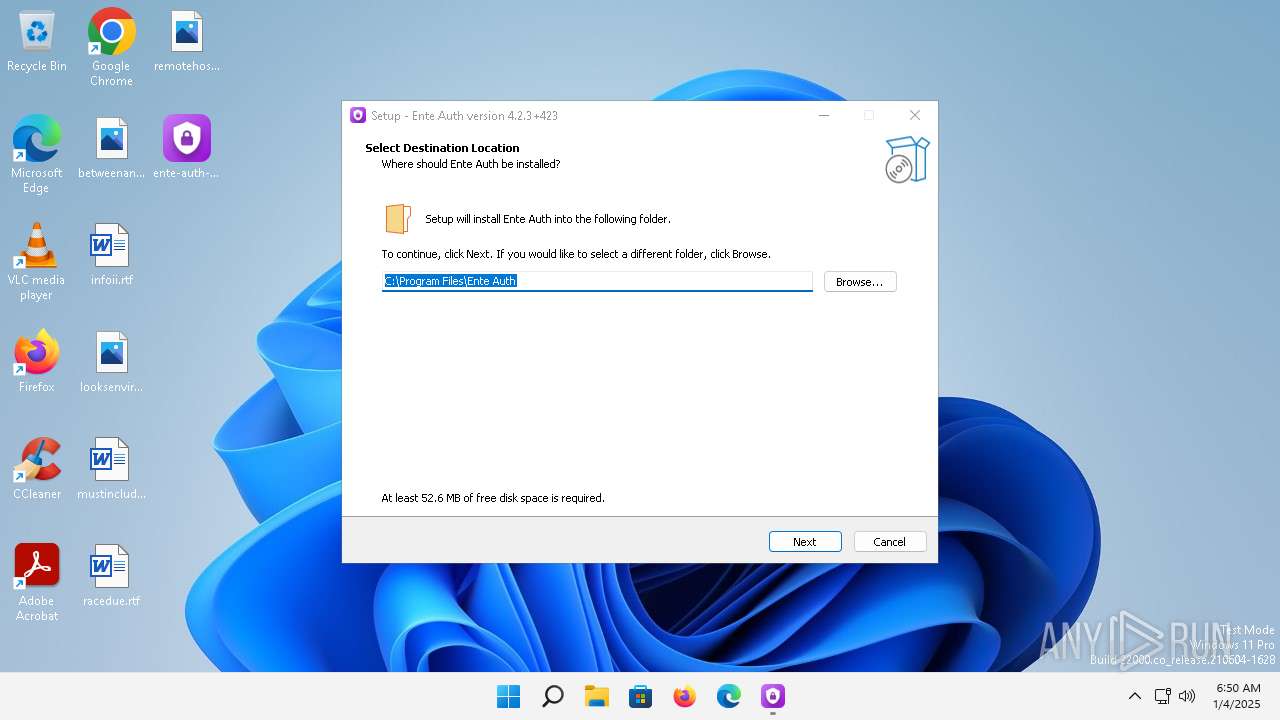
| File name: | ente-auth-v4.2.3-installer.exe |
| Full analysis: | https://app.any.run/tasks/4edd0238-de69-4f1e-8658-f41a3bce274b |
| Verdict: | Malicious activity |
| Analysis date: | January 04, 2025, 06:49:35 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | A98F27A78EBCB3EFC90CE2BDE82579D6 |
| SHA1: | 7A4A1B76FA9162BE910434A872543FFE2E11F74A |
| SHA256: | 2677A1611E4E303980FA0ABD10D3BA2E00952C44FFA81E63A9D5B7790B2664D8 |
| SSDEEP: | 98304:zrq3Bdw6pVpxeyvDB/fsxuZN2A1+YNl+mpsp1pPnstkc6xxyOaEdThZdaYUrPlLc:iGLNeihk90cAsbf9cNu3VzGvwrO |
MALICIOUS
Executing a file with an untrusted certificate
- ente-auth-v4.2.3-installer.exe (PID: 4752)
- ente-auth-v4.2.3-installer.exe (PID: 2744)
SUSPICIOUS
Reads security settings of Internet Explorer
- ente-auth-v4.2.3-installer.tmp (PID: 3004)
Reads the Internet Settings
- ente-auth-v4.2.3-installer.tmp (PID: 3004)
Reads the Windows owner or organization settings
- ente-auth-v4.2.3-installer.tmp (PID: 780)
Executable content was dropped or overwritten
- ente-auth-v4.2.3-installer.exe (PID: 4752)
- ente-auth-v4.2.3-installer.tmp (PID: 780)
- ente-auth-v4.2.3-installer.exe (PID: 2744)
Process drops legitimate windows executable
- ente-auth-v4.2.3-installer.tmp (PID: 780)
INFO
Reads the computer name
- ente-auth-v4.2.3-installer.exe (PID: 4752)
- ente-auth-v4.2.3-installer.tmp (PID: 3004)
- ente-auth-v4.2.3-installer.tmp (PID: 780)
Create files in a temporary directory
- ente-auth-v4.2.3-installer.exe (PID: 4752)
- ente-auth-v4.2.3-installer.exe (PID: 2744)
- ente-auth-v4.2.3-installer.tmp (PID: 780)
Checks supported languages
- ente-auth-v4.2.3-installer.exe (PID: 4752)
- ente-auth-v4.2.3-installer.tmp (PID: 3004)
- ente-auth-v4.2.3-installer.exe (PID: 2744)
- ente-auth-v4.2.3-installer.tmp (PID: 780)
Creates files in the program directory
- ente-auth-v4.2.3-installer.tmp (PID: 780)
The sample compiled with english language support
- ente-auth-v4.2.3-installer.tmp (PID: 780)
Drops a (possible) Coronavirus decoy
- ente-auth-v4.2.3-installer.tmp (PID: 780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:12 07:26:53+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 240640 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Ente Auth Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Ente Auth |
| ProductVersion: | 4.2.3+423 |
Total processes
111
Monitored processes
4
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 780 | "C:\Users\admin\AppData\Local\Temp\is-NCEMQ.tmp\ente-auth-v4.2.3-installer.tmp" /SL5="$B0214,17960188,926720,C:\Users\admin\Desktop\ente-auth-v4.2.3-installer.exe" /SPAWNWND=$C02CE /NOTIFYWND=$160150 /ALLUSERS | C:\Users\admin\AppData\Local\Temp\is-NCEMQ.tmp\ente-auth-v4.2.3-installer.tmp | ente-auth-v4.2.3-installer.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2744 | "C:\Users\admin\Desktop\ente-auth-v4.2.3-installer.exe" | C:\Users\admin\Desktop\ente-auth-v4.2.3-installer.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Ente Auth Setup Version: Modules
| |||||||||||||||
| 3004 | "C:\Users\admin\AppData\Local\Temp\is-82K7A.tmp\ente-auth-v4.2.3-installer.tmp" /SL5="$160150,17960188,926720,C:\Users\admin\Desktop\ente-auth-v4.2.3-installer.exe" | C:\Users\admin\AppData\Local\Temp\is-82K7A.tmp\ente-auth-v4.2.3-installer.tmp | — | ente-auth-v4.2.3-installer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4752 | "C:\Users\admin\Desktop\ente-auth-v4.2.3-installer.exe" /SPAWNWND=$C02CE /NOTIFYWND=$160150 /ALLUSERS | C:\Users\admin\Desktop\ente-auth-v4.2.3-installer.exe | ente-auth-v4.2.3-installer.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Ente Auth Setup Version: Modules
| |||||||||||||||
Total events
315
Read events
310
Write events
5
Delete events
0
Modification events
| (PID) Process: | (780) ente-auth-v4.2.3-installer.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 0C0300003ED905E6745EDB01 | |||
| (PID) Process: | (780) ente-auth-v4.2.3-installer.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 665A80E2AA1316F9586BDEE49E34961F9A795C475B6BC30028FD3A0E4F2DC551 | |||
| (PID) Process: | (780) ente-auth-v4.2.3-installer.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (780) ente-auth-v4.2.3-installer.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Ente Auth\app_links_plugin.dll | |||
| (PID) Process: | (780) ente-auth-v4.2.3-installer.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: AD03BC0CF881611C35A35431A3E654F65768AF716C05C41E638858E3559049FE | |||
Executable files
45
Suspicious files
18
Text files
2 321
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\flutter_secure_storage_windows_plugin.dll | executable | |
MD5:8CFC322B8521B9604B13B0B56B0C0D36 | SHA256:7C0B9CBE33DA2289BD08B1FA33A7AE90491E7A7059056655B7E680BC72420FDB | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\flutter_local_authentication_plugin.dll | executable | |
MD5:C48DDAC529C41E234F8933FAE8F8941C | SHA256:07635612FADB0185358064D596BF7121795446BAB1596D2757C83652CB86031F | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\is-QBSJV.tmp | executable | |
MD5:8768744873AA539C018DC5283A97626B | SHA256:892C9CD8633F1350C16846A927A76F95EBF22E0AB7312BFEA128A931F3ED7E88 | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\flutter_inappwebview_windows_plugin.dll | executable | |
MD5:9AFFFC35E42B24FCA3731A8F23BC24BD | SHA256:147021CCAE7DADE18CE9B2798730EB86D89757844FD3E5887EE3E9C11433EC45 | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\unins000.exe | executable | |
MD5:4440F1234FBC8348AE11A4C750BB6379 | SHA256:80D066ED766088C995648279319B535816492EC82F2A3CCF72082127DB0FABA8 | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Users\admin\AppData\Local\Temp\is-SVSUM.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\is-SFLCR.tmp | executable | |
MD5:4D746B596477BCBC9BD536CEEB9D0CEA | SHA256:92CCC43F9DBF63B30A5E7F473C9732FA8E3C4D7E10CDF510F82D71023E8E392B | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\app_links_plugin.dll | executable | |
MD5:8B992D9A8EBC486BF3D6FF7DC1356885 | SHA256:13A6EEF910B850C28C0436603DDB1BBE57B9D96E6968B430DBAC1A5F81CB2E8B | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\connectivity_plus_plugin.dll | executable | |
MD5:8D0F9963EE71505D4806AEE841759ECF | SHA256:E116B0FC3E7E4576CA47B8A26DDBE3BA254B22DA695868B3F36FE116CFDBB30E | |||
| 780 | ente-auth-v4.2.3-installer.tmp | C:\Program Files\Ente Auth\is-QR3LJ.tmp | executable | |
MD5:8D0F9963EE71505D4806AEE841759ECF | SHA256:E116B0FC3E7E4576CA47B8A26DDBE3BA254B22DA695868B3F36FE116CFDBB30E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
14
DNS requests
6
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.25.50.104:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2340 | MoUsoCoreWorker.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a2f4997073b2ab7b | unknown | — | — | whitelisted |
— | — | HEAD | 302 | 184.30.17.174:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | unknown |
— | — | HEAD | 200 | 194.60.69.120:443 | https://my.lanet.ua/access2.php?req=dns | unknown | — | — | unknown |
2860 | svchost.exe | GET | 200 | 2.22.50.144:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?d427199d7579a766 | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 2.22.50.144:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e5bd8b39a3217613 | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.17.174:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | html | 5.55 Kb | unknown |
— | — | GET | 200 | 184.30.17.174:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | html | 5.55 Kb | whitelisted |
— | — | GET | 200 | 184.30.17.174:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | html | 5.55 Kb | whitelisted |
— | — | GET | 200 | 184.30.17.174:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | html | 5.55 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 184.25.50.104:80 | — | Akamai International B.V. | DE | unknown |
2340 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2340 | MoUsoCoreWorker.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2860 | svchost.exe | 2.22.50.144:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
5552 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5568 | svchost.exe | 184.28.90.27:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
5568 | svchost.exe | 194.60.69.112:443 | my.lanet.ua | Lanet Network Ltd | UA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
my.lanet.ua |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |