| download: | index.html |
| Full analysis: | https://app.any.run/tasks/b017dd12-bd1f-4d12-ac88-f048bede7154 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 14:42:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, LF line terminators |
| MD5: | 2F81FA9845453C8012013979A063345B |
| SHA1: | 6A2216AF008BDC01274AB3DDA9B992A5AF0CB05B |
| SHA256: | 266C5541E5CC218BA9A7F73D6C827C05B2F4683F84824051A41654481FAFE2E0 |
| SSDEEP: | 6144:6aj8Ge0OTYdFsmtM2SYJey/KdzG1Ys7X+OjsgpPHsW41Hog:RKdzG1Ys7XCIg |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 3864)
Changes settings of System certificates
- iexplore.exe (PID: 1904)
Creates files in the user directory
- iexplore.exe (PID: 1904)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 1904)
Reads internet explorer settings
- iexplore.exe (PID: 1904)
Reads Internet Cache Settings
- iexplore.exe (PID: 1904)
Reads settings of System Certificates
- iexplore.exe (PID: 1904)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| baiduSiteVerification: | g5yt0h5wVy |
|---|---|
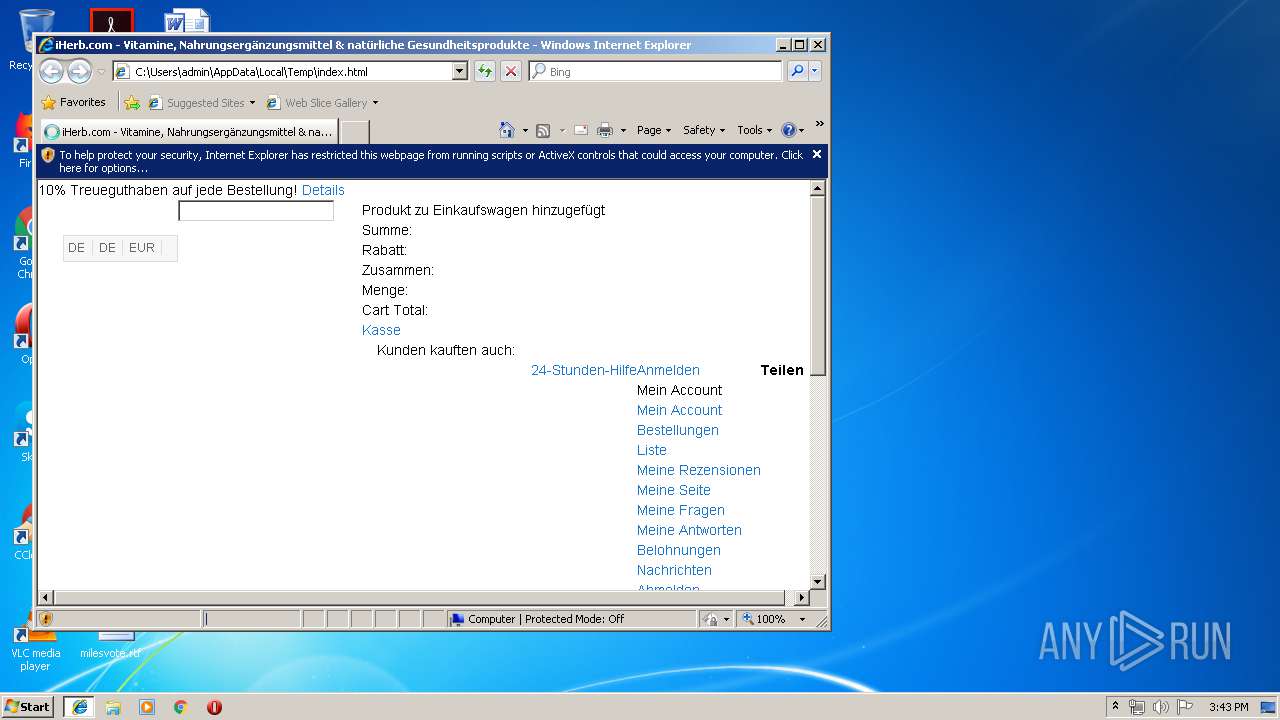
| Title: | iHerb.com - Vitamine, Nahrungsergänzungsmittel & natürliche Gesundheitsprodukte |
| Description: | 30.000+ erstklassige, gesunde Produkte; mit reduziertem Versand, unglaubliche Werte und Kundenbelohnungen. |
| formatDetection: | telephone=no |
| ContentType: | text/html; charset=utf-8 |
| HTTPEquivXUACompatible: | IE=edge |
| viewport: | width=device-width |
| googleSiteVerification: | zBEQuibjR3T_pcVIOOVisw5Zm_nOvhR78nG0Qj4KJ5M |
| msvalidate01: | 218C371F3F2FC3B0C10E5B28263F5392 |
| The: | 53b512aa45a3a17d78b3f7e92e3a00fb4518f252 |
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1904 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3864 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\index.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
553
Read events
446
Write events
100
Delete events
7
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {6A562FE9-6768-11E9-A370-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070400040019000E002A003A004D02 | |||
Executable files
0
Suspicious files
0
Text files
44
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\beesbanner0424de-de[1].jpg | image | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\four_sigmatic_v1_logo[1].png | image | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\advanced_orthomolecular_v3_logo[1].png | image | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\ie[1].png | image | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\wileys_finest_v1_logo[1].png | image | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\kirkman_v1_logo[1].png | image | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\chrome[1].png | image | |
MD5:— | SHA256:— | |||
| 1904 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\quest_nutrition_v1_logo[1].png | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
49
DNS requests
8
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3864 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
1904 | iexplore.exe | OPTIONS | 400 | 216.58.206.8:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 104.16.166.250:139 | s3.images-iherb.com | Cloudflare Inc | US | shared |
3864 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1904 | iexplore.exe | 104.16.167.250:443 | s3.images-iherb.com | Cloudflare Inc | US | shared |
4 | System | 104.16.166.250:445 | s3.images-iherb.com | Cloudflare Inc | US | shared |
— | — | 104.16.167.250:443 | s3.images-iherb.com | Cloudflare Inc | US | shared |
1904 | iexplore.exe | 216.58.206.8:80 | www.googletagmanager.com | Google Inc. | US | whitelisted |
4 | System | 216.58.206.8:139 | www.googletagmanager.com | Google Inc. | US | whitelisted |
4 | System | 104.16.167.250:445 | s3.images-iherb.com | Cloudflare Inc | US | shared |
4 | System | 216.58.206.8:445 | www.googletagmanager.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s3.images-iherb.com |
| suspicious |
dns.msftncsi.com |
| shared |
www.bing.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
10 ETPRO signatures available at the full report