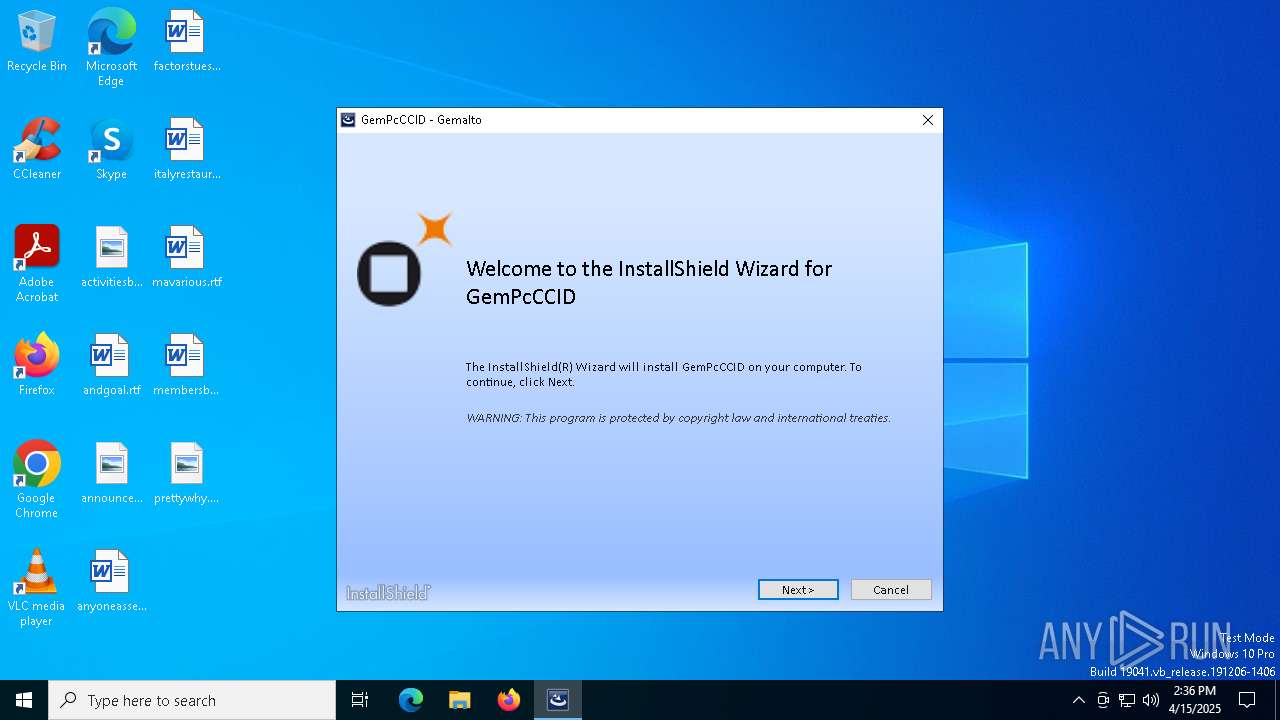
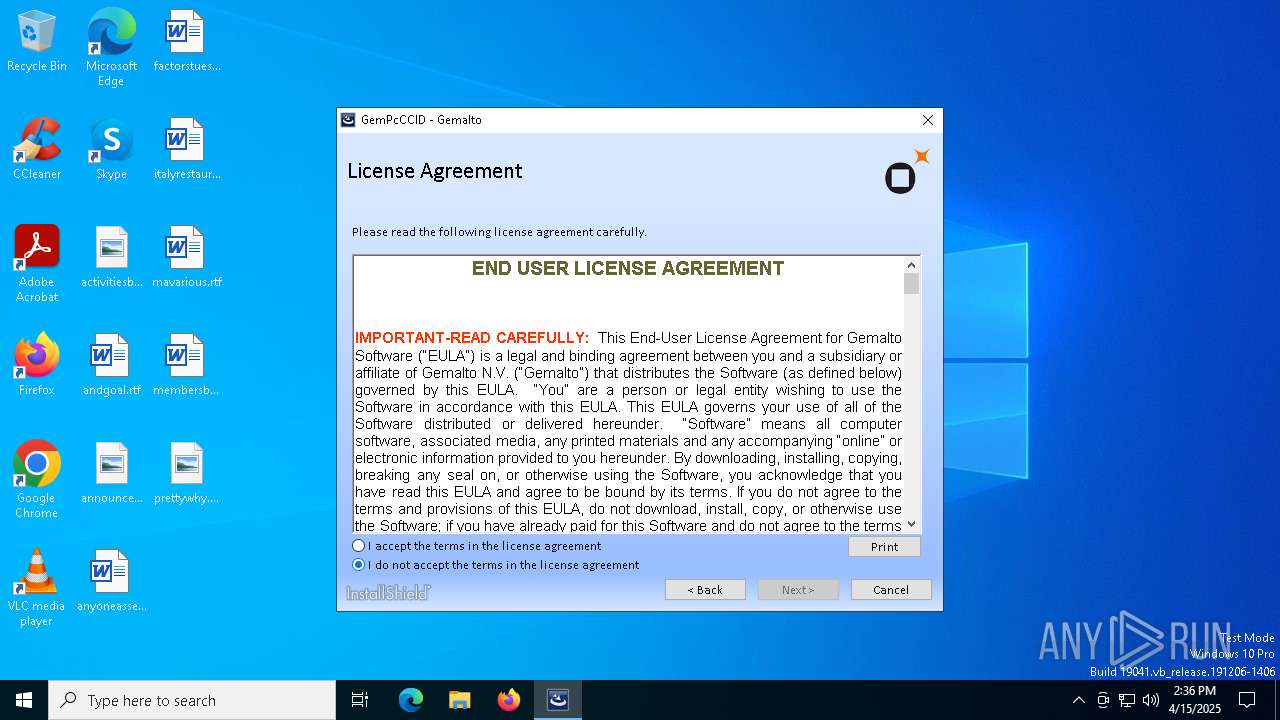
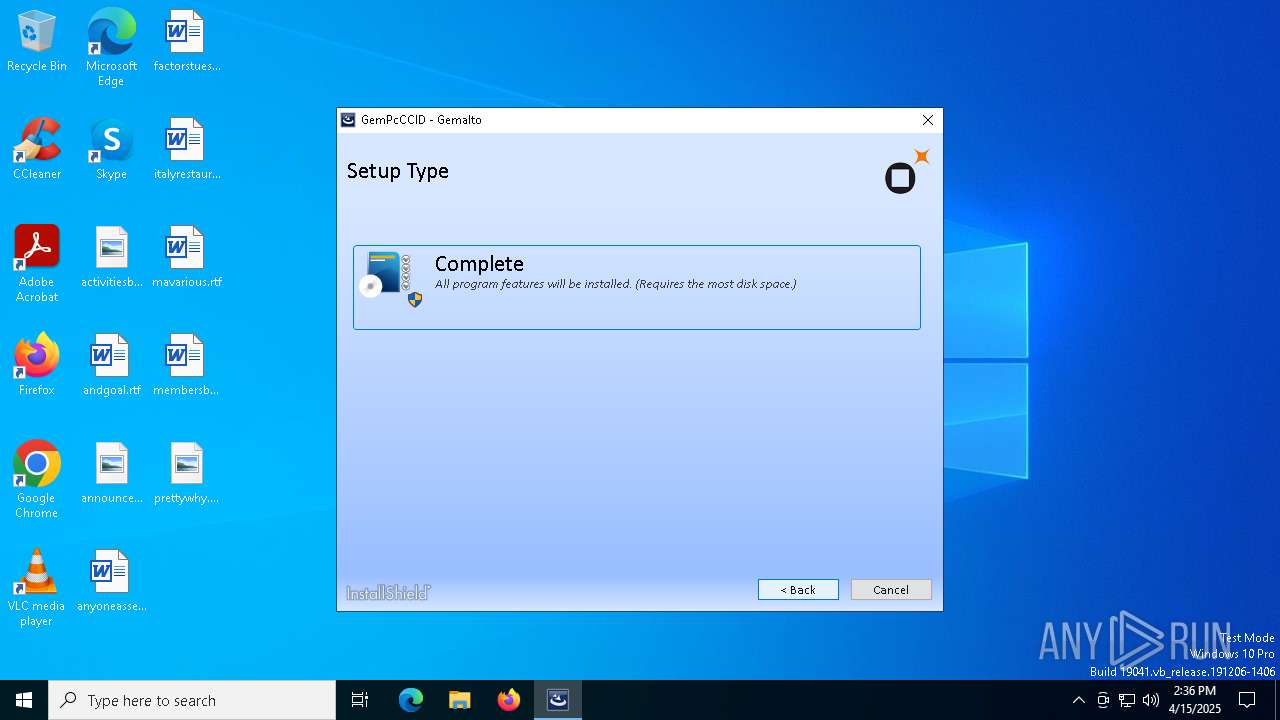
| File name: | GemPcCCID.exe |
| Full analysis: | https://app.any.run/tasks/0b6d94ea-1d01-4957-9b51-426a8f48ed5f |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 14:36:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 92281CEC4903AE3FEE213BA755E0F450 |
| SHA1: | B0E2D2484EA888684FA99D21BE9252CC68DF7A58 |
| SHA256: | 26210D1FD10AC68309EFDEC537C05D4CF44BC7B9E116E36B5BF0112C7DA0309B |
| SSDEEP: | 49152:WXjlAErpQTZUoTmIZ510fbc6t7GxzB/sAQl1ROEBg8FhXZeK2BZ+h8Gi0cRgRwIk:WXhAErpQTV8BDXW3G7ewwtuVS |
MALICIOUS
Executing a file with an untrusted certificate
- GemPcCCID.exe (PID: 1324)
Changes the autorun value in the registry
- GemPcCCID.exe (PID: 3956)
SUSPICIOUS
Reads security settings of Internet Explorer
- GemPcCCID.exe (PID: 3956)
- GemPcCCID.exe (PID: 1324)
Executable content was dropped or overwritten
- GemPcCCID.exe (PID: 3956)
- drvinst.exe (PID: 6268)
- GemPcCCID.exe (PID: 1324)
Application launched itself
- GemPcCCID.exe (PID: 3956)
- msiexec.exe (PID: 672)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 672)
Process drops legitimate windows executable
- msiexec.exe (PID: 672)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 672)
- drvinst.exe (PID: 6268)
Creates files in the driver directory
- msiexec.exe (PID: 1272)
- drvinst.exe (PID: 6268)
There is functionality for taking screenshot (YARA)
- GemPcCCID.exe (PID: 3956)
INFO
Reads the computer name
- GemPcCCID.exe (PID: 3956)
- msiexec.exe (PID: 672)
- setup64.exe (PID: 6388)
- GemPcCCID.exe (PID: 1324)
- msiexec.exe (PID: 1272)
- msiexec.exe (PID: 6872)
- drvinst.exe (PID: 6268)
Create files in a temporary directory
- GemPcCCID.exe (PID: 3956)
The sample compiled with english language support
- GemPcCCID.exe (PID: 3956)
- msiexec.exe (PID: 672)
- GemPcCCID.exe (PID: 1324)
- drvinst.exe (PID: 6268)
Checks supported languages
- GemPcCCID.exe (PID: 3956)
- setup64.exe (PID: 2136)
- GemPcCCID.exe (PID: 1324)
- setup64.exe (PID: 6388)
- msiexec.exe (PID: 672)
- msiexec.exe (PID: 1272)
- msiexec.exe (PID: 6872)
- drvinst.exe (PID: 6268)
Creates files or folders in the user directory
- GemPcCCID.exe (PID: 3956)
- msiexec.exe (PID: 672)
Process checks computer location settings
- GemPcCCID.exe (PID: 3956)
- GemPcCCID.exe (PID: 1324)
Reads the machine GUID from the registry
- msiexec.exe (PID: 672)
- drvinst.exe (PID: 6268)
Executable content was dropped or overwritten
- msiexec.exe (PID: 672)
The sample compiled with czech language support
- msiexec.exe (PID: 672)
Reads the software policy settings
- msiexec.exe (PID: 672)
- drvinst.exe (PID: 6268)
Creates a software uninstall entry
- msiexec.exe (PID: 672)
Creates files in the program directory
- GemPcCCID.exe (PID: 1324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (17.3) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (4.1) |
| .exe | | | Win32 Executable (generic) (2.8) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:06:08 04:33:14+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 861696 |
| InitializedDataSize: | 509952 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9f77e |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.4.0 |
| ProductVersionNumber: | 4.1.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Gemalto |
| FileDescription: | Setup Suite Launcher Unicode |
| FileVersion: | 4.1.4.0 |
| InternalName: | SetupSuite |
| LegalCopyright: | Copyright (c) 2015 Flexera Software LLC. All Rights Reserved. |
| OriginalFileName: | InstallShield SetupSuite.exe |
| ProductName: | GemPcCCID |
| ProductVersion: | 4.1.4.0 |
| InternalBuildNumber: | 154432 |
| ISInternalVersion: | 22.0.284 |
| ISInternalDescription: | Setup Suite Launcher Unicode |
Total processes
141
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | C:\Windows\System32\MsiExec.exe -Embedding CC848631C3E1847D0E6D553E94B8DFA4 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\AppData\Local\Temp\GemPcCCID.exe" -embedded:C27EB1A7-EE46-474F-AC2A-37C68CFBDB31 | C:\Users\admin\AppData\Local\Temp\GemPcCCID.exe | GemPcCCID.exe | ||||||||||||
User: admin Company: Gemalto Integrity Level: HIGH Description: Setup Suite Launcher Unicode Exit code: 0 Version: 4.1.4.0 Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\setup64.exe" -embedded:6C45B512-7D02-4E2F-A811-814E769E1CF6 | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\setup64.exe | — | GemPcCCID.exe | |||||||||||
User: admin Company: Flexera Software LLC Integrity Level: MEDIUM Description: Setup Suite Launcher Unicode Exit code: 0 Version: 22.0.284 Modules
| |||||||||||||||
| 2384 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3956 | "C:\Users\admin\AppData\Local\Temp\GemPcCCID.exe" | C:\Users\admin\AppData\Local\Temp\GemPcCCID.exe | explorer.exe | ||||||||||||
User: admin Company: Gemalto Integrity Level: MEDIUM Description: Setup Suite Launcher Unicode Exit code: 0 Version: 4.1.4.0 Modules
| |||||||||||||||
| 6268 | DrvInst.exe "4" "1" "C:\Program Files (x86)\Gemalto\ReaderTools\Installer\GemPcCCID\gemccid.inf" "9" "46dc8be8b" "0000000000000174" "WinSta0\Default" "00000000000001C8" "208" "C:\Program Files (x86)\Gemalto\ReaderTools\Installer\GemPcCCID" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | "C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\setup64.exe" -embedded:53C640B7-EEDD-4ADE-A52D-168492519FAB | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\setup64.exe | — | GemPcCCID.exe | |||||||||||
User: admin Company: Flexera Software LLC Integrity Level: HIGH Description: Setup Suite Launcher Unicode Exit code: 0 Version: 22.0.284 Modules
| |||||||||||||||
| 6872 | C:\Windows\System32\MsiExec.exe -Embedding B3D5DB535FCE4AB852F357CA96803850 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 677
Read events
8 544
Write events
112
Delete events
21
Modification events
| (PID) Process: | (3956) GemPcCCID.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\InstallShield\SuiteInstallers\{55610A8B-6A3F-4F94-B072-4962B78638E5} |
| Operation: | write | Name: | InfoPath |
Value: C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\_isB930 | |||
| (PID) Process: | (3956) GemPcCCID.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\InstallShield\SuiteInstallers\{55610A8B-6A3F-4F94-B072-4962B78638E5} |
| Operation: | write | Name: | Reboot |
Value: 1 | |||
| (PID) Process: | (3956) GemPcCCID.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | {55610A8B-6A3F-4F94-B072-4962B78638E5} |
Value: "C:\Users\admin\AppData\Local\Temp\GemPcCCID.exe" | |||
| (PID) Process: | (672) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: A0020000548486D513AEDB01 | |||
| (PID) Process: | (672) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: EB199EEA6135FA9AC423662CF62531A1EF95ED29E3ABB6BFC865274D2BA970B3 | |||
| (PID) Process: | (672) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10eea9.rbs |
Value: 31174163 | |||
| (PID) Process: | (672) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10eea9.rbsLow |
Value: | |||
| (PID) Process: | (1272) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\Windows\CurrentVersion\DIFxApp\Components\{24F1099D-3E18-4DB4-965C-802ABDB864AF} |
| Operation: | delete value | Name: | SymbolicLinkValue |
Value: | |||
Executable files
13
Suspicious files
32
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\setup64.exe | executable | |
MD5:A0639090C9BE5C67C83A48C7BFE127FB | SHA256:51766510BF904259EFB5645F045E58964A11AE9DA66A9DB13E18742B4CDE2C8B | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\ISLogoBig.png | image | |
MD5:04FF43EFF306751E225EAC0C0D9AE6BA | SHA256:995FF2F37E8688D9D65AA1219753A01078FB3CBD17B75B114AF56A61E3B63988 | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\Setup_UI.dll | executable | |
MD5:8E8E20D281492B194DA54C3729E51A1F | SHA256:3E467565F19B6E4CBAAD0B374FC9354BE65CFB769DEAD686B83A2B686BA647CD | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\setup.xml | xml | |
MD5:68FB19A74773828F56494498BD8DB5EE | SHA256:B1E6EC84482BEC345BE2C7324A26DBBF15A324832E6ED747FFB9590A509F050C | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\scale-150\Application.png | image | |
MD5:46B2EB6C23572DA87ADA5A342F854641 | SHA256:016604E80FFC9921EE9CA036B6DDE317094C9D1CD8BF4928087317C708EB7C84 | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\scale-150\Custom.png | image | |
MD5:41404BDC8ACC738078A96E03836A7017 | SHA256:2760DC6DA4DA352973B99D8209E54DC68C679D8C2800408F6D9481E03D9D3D9B | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\scale-150\Remove.png | image | |
MD5:3935F5F99E5930A26FF9C78E7004EF1E | SHA256:759A320B1B41F49D95333AE9636AB772C64DDE712208BBAE1850D134F870A70E | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\Remove.png | image | |
MD5:A96BBEFB78F0C3DBEA0C24163A7071B5 | SHA256:B83531648D506073C9E0A0481977EE378DE0D57EF2508145A7F23AF9E3344A41 | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\scale-150\Folder.png | image | |
MD5:F3F9575A23F7C4CD35C8324231F5BD9E | SHA256:2EE9AA1DDA88CD9964D342DDA3FE56164C9906D5441E8381297F4DCDAE6C3E9D | |||
| 3956 | GemPcCCID.exe | C:\Users\admin\AppData\Local\Temp\{AD36012E-CAEB-4949-9338-BD1663BF151B}\scale-150\ISLogoBig.png | image | |
MD5:D1EF62B54F9891D47FC45CEC0DC3BA66 | SHA256:C2CC87D11211DBC67AE85BF317393912A4DEB092A70A4D1AA746F31F4E127A18 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
20
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.195:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
672 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
672 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://s1.symcb.com/pca3-g5.crl | unknown | — | — | whitelisted |
672 | msiexec.exe | GET | 200 | 184.30.131.114:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEHcJrB3%2BQow3r824GVLHRC4%3D | unknown | — | — | whitelisted |
672 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | — | — | whitelisted |
672 | msiexec.exe | GET | 200 | 184.30.131.114:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEHcJrB3%2BQow3r824GVLHRC4%3D | unknown | — | — | whitelisted |
672 | msiexec.exe | GET | 200 | 2.23.79.3:80 | http://sv.symcb.com/sv.crl | unknown | — | — | whitelisted |
736 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
736 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.195:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
672 | msiexec.exe | 2.23.79.3:80 | s2.symcb.com | AKAMAI-AS | DE | whitelisted |
672 | msiexec.exe | 2.17.189.192:80 | s1.symcb.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
s2.symcb.com |
| whitelisted |
s1.symcb.com |
| whitelisted |
sv.symcd.com |
| whitelisted |
sv.symcb.com |
| whitelisted |