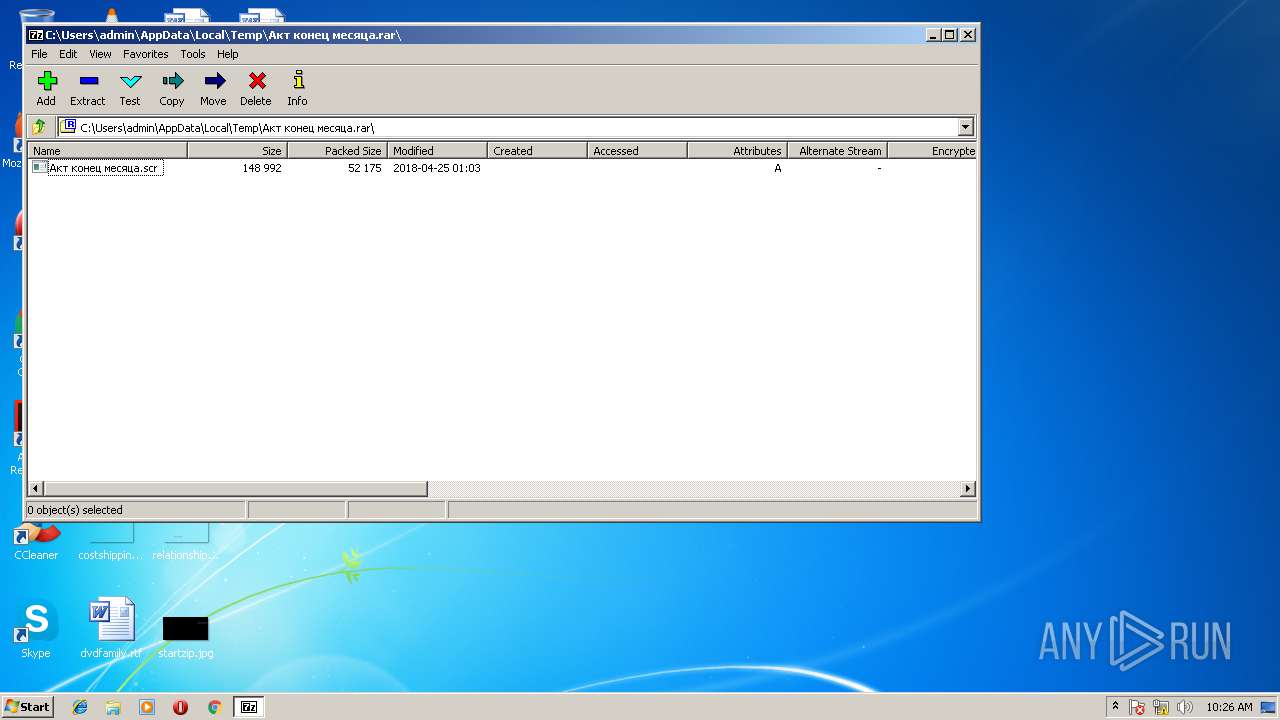
| File name: | Акт конец месяца.rar |
| Full analysis: | https://app.any.run/tasks/4502ecf4-499f-4202-86f8-8ec933db3260 |
| Verdict: | No threats detected |
| Analysis date: | April 25, 2018, 09:26:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F20E21522550B8CA470792EF5FCA3889 |
| SHA1: | EBC8D62F5BB2B48069875EEF541C90CDA5256783 |
| SHA256: | 25F7C3A06E8B4DD3A5D95F3E16D6C0360B458D637CB941DC73B57707E29F28BB |
| SSDEEP: | 1536:6f0/fEyOP43ETSRwzsbz/FBJ1Gegb5/Qxvx1SL:O0nEyOwuS3bzDJHg1Yxvx1SL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies the open verb of a shell class
- rundll32.exe (PID: 3440)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
34
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2412 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\7zO0DAE8870\.rsrc_1 | C:\Windows\system32\rundll32.exe | — | 7zFM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2768 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\Акт конец месяца.rar" | C:\Program Files\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
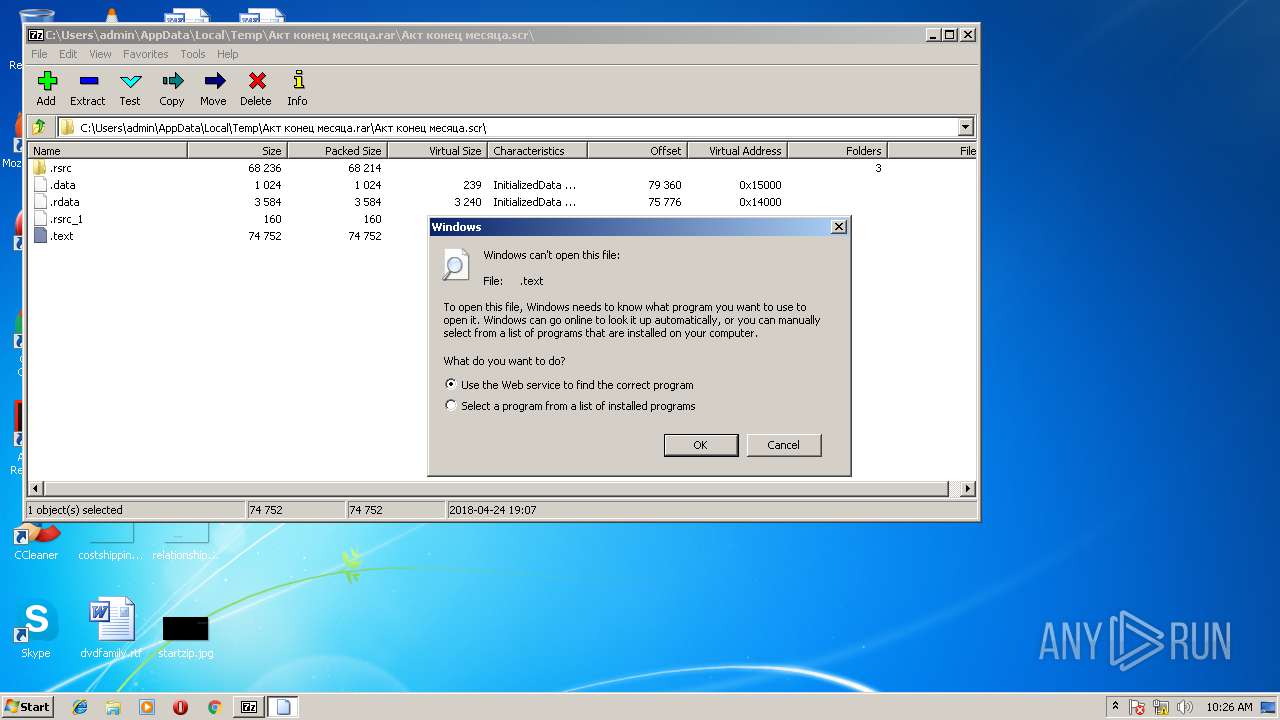
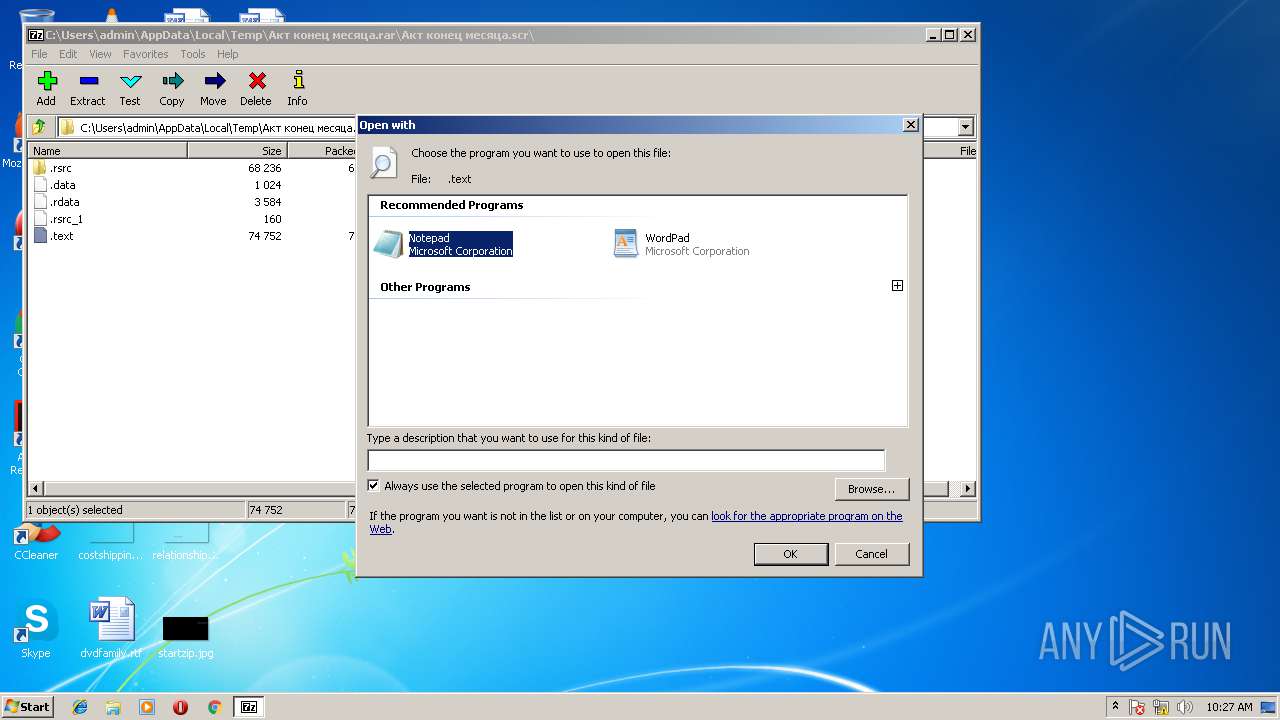
| 2836 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\7zO0DAD19EF\.text | C:\Windows\system32\NOTEPAD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\7zO0DAD19EF\.text | C:\Windows\system32\rundll32.exe | — | 7zFM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
797
Read events
733
Write events
64
Delete events
0
Modification events
| (PID) Process: | (2768) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar5 |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000003F00000001000000640000000F00000001000000640000000D00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000003600000001000000640000005A00000001000000640000005F00000001000000640000001F00000001000000640000002000000001000000640000002E00000001000000640000003E0000000100000064000000 | |||
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CLASSES_ROOT\text_auto_file |
| Operation: | write | Name: | |
Value: | |||
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CLASSES_ROOT\.text |
| Operation: | write | Name: | |
Value: text_auto_file | |||
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CLASSES_ROOT\text_auto_file\shell\edit\command |
| Operation: | write | Name: | |
Value: %SystemRoot%\system32\NOTEPAD.EXE %1 | |||
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CLASSES_ROOT\text_auto_file\shell\open\command |
| Operation: | write | Name: | |
Value: %SystemRoot%\system32\NOTEPAD.EXE %1 | |||
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.text\OpenWithList |
| Operation: | write | Name: | a |
Value: NOTEPAD.EXE | |||
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.text\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.text\OpenWithProgids |
| Operation: | write | Name: | text_auto_file |
Value: | |||
| (PID) Process: | (3440) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\91\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2768) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.PE |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000004D00000001000000640000002F00000001000000640000002400000001000000640000003000000001000000640000001F0000000100000064000000200000000100000064000000 | |||
Executable files
0
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2768 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zO0DAD19EF\.text | binary | |
MD5:— | SHA256:— | |||
| 2768 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zO0DAE8870\.rsrc_1 | text | |
MD5:E27460C94DA515F8ACAEDC3481255078 | SHA256:52FCC5B3C6CB2458E6361FE35191ED477BB3DA93FDF4FFDB126479CA014E529F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report