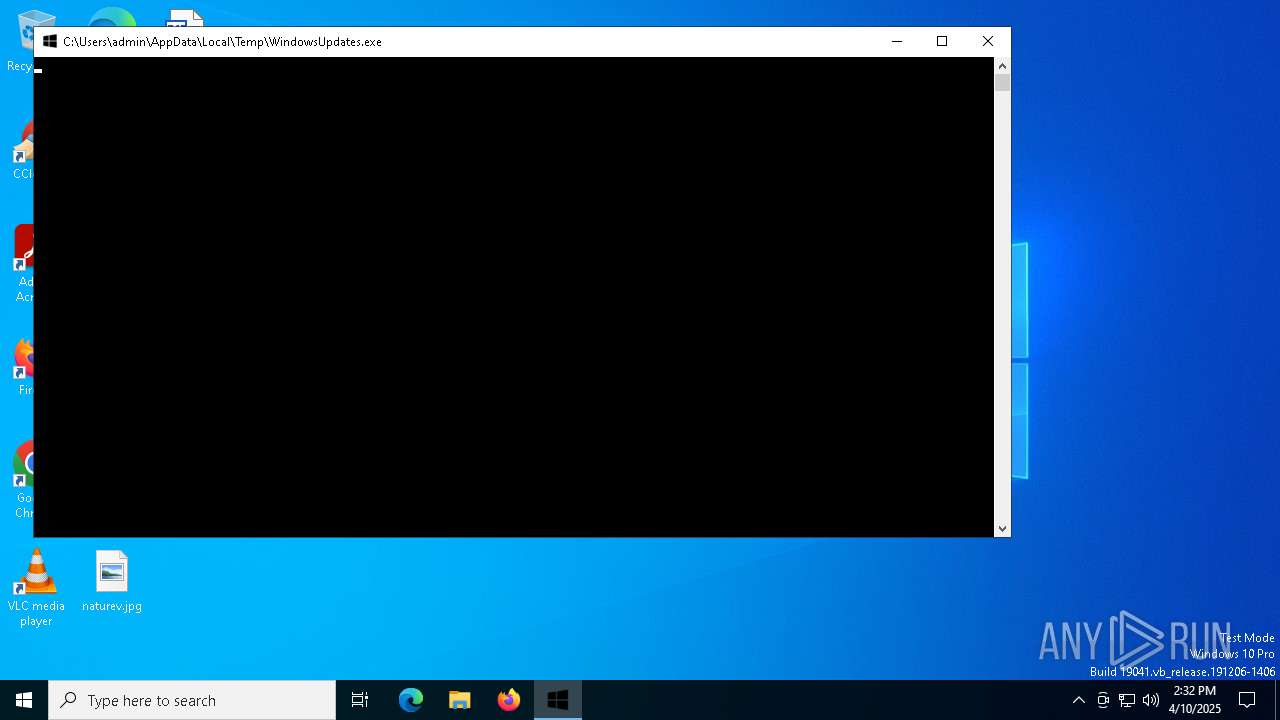
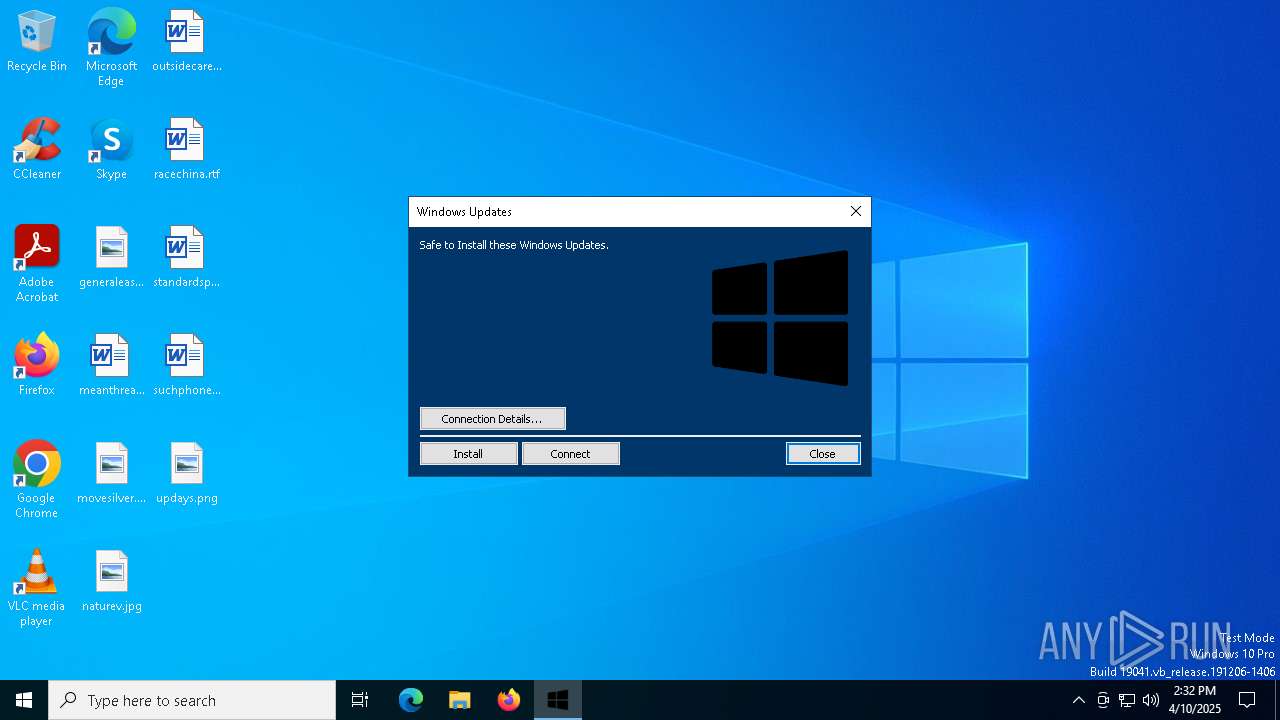
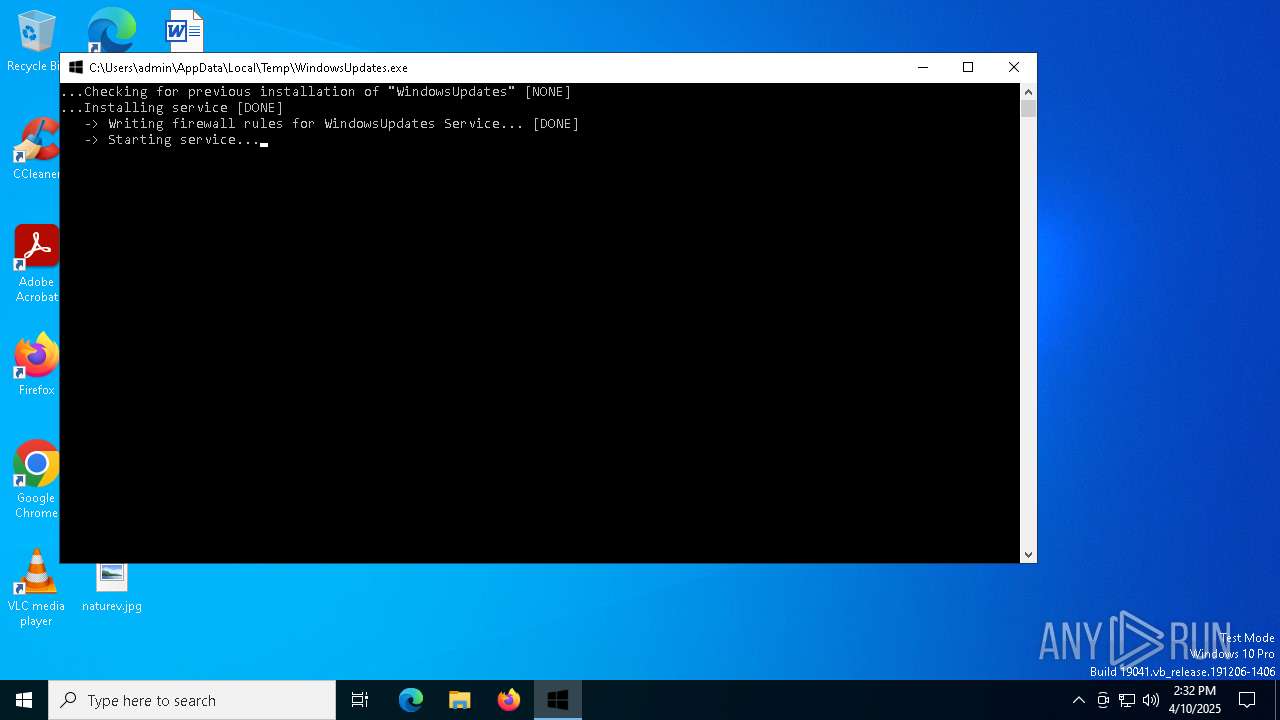
| File name: | WindowsUpdates.exe |
| Full analysis: | https://app.any.run/tasks/f3f95428-d811-4481-85f0-dd219ec318e7 |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2025, 14:32:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 6 sections |
| MD5: | A4A3F62DB6DE8CE84CE275FC1C3A4C00 |
| SHA1: | 655FB3B768A30AA48A70CFB34D19527843D1EE3C |
| SHA256: | 25F66AE1220A7EA09C0B5A06BA10D53ED461369C7AD357605D7DE03410D59577 |
| SSDEEP: | 98304:zh7Jc09d/1Xn0R7PRD+9KWFn1O6Al0QFUv6Azk7prpSPynGRter9t2oEhaI0vZRP:0zl |
MALICIOUS
Executing a file with an untrusted certificate
- WindowsUpdates.exe (PID: 6620)
- WindowsUpdates.exe (PID: 4172)
- WindowsUpdates.exe (PID: 1012)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 4424)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- WindowsUpdates.exe (PID: 6620)
Uses WMIC.EXE to obtain operating system information
- WindowsUpdates.exe (PID: 6620)
- WindowsUpdates.exe (PID: 1012)
MeshAgent potential remote access (YARA)
- WindowsUpdates.exe (PID: 6620)
Reads security settings of Internet Explorer
- WindowsUpdates.exe (PID: 6620)
Application launched itself
- WindowsUpdates.exe (PID: 6620)
Creates or modifies Windows services
- WindowsUpdates.exe (PID: 4172)
Executes as Windows Service
- WindowsUpdates.exe (PID: 1012)
Creates a software uninstall entry
- WindowsUpdates.exe (PID: 4172)
- WindowsUpdates.exe (PID: 1012)
Executable content was dropped or overwritten
- WindowsUpdates.exe (PID: 4172)
Uses WMIC.EXE to obtain computer system information
- WindowsUpdates.exe (PID: 1012)
Uses WMIC.EXE to obtain system information
- WindowsUpdates.exe (PID: 1012)
Starts POWERSHELL.EXE for commands execution
- WindowsUpdates.exe (PID: 1012)
The process hides Powershell's copyright startup banner
- WindowsUpdates.exe (PID: 1012)
The process bypasses the loading of PowerShell profile settings
- WindowsUpdates.exe (PID: 1012)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4424)
INFO
The sample compiled with english language support
- WindowsUpdates.exe (PID: 6620)
- WindowsUpdates.exe (PID: 4172)
Reads the computer name
- WindowsUpdates.exe (PID: 6620)
- WindowsUpdates.exe (PID: 1012)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 3900)
- WMIC.exe (PID: 1912)
- WMIC.exe (PID: 7000)
- WMIC.exe (PID: 968)
- WMIC.exe (PID: 5680)
- WMIC.exe (PID: 3896)
Checks supported languages
- WindowsUpdates.exe (PID: 6620)
- WindowsUpdates.exe (PID: 4172)
- WindowsUpdates.exe (PID: 1012)
Reads the machine GUID from the registry
- WindowsUpdates.exe (PID: 6620)
- WindowsUpdates.exe (PID: 1012)
Creates files in the program directory
- WindowsUpdates.exe (PID: 4172)
- WindowsUpdates.exe (PID: 1012)
Process checks computer location settings
- WindowsUpdates.exe (PID: 6620)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6760)
- powershell.exe (PID: 6512)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 2332)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:12:09 20:13:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 2458112 |
| InitializedDataSize: | 1345024 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c1570 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Microsoft Updates |
| FileVersion: | 2022-Dec-2 11:42:16-0800 |
| LegalCopyright: | Apache 2.0 License |
| ProductName: | Winupdates |
| ProductVersion: | Commit: 2022-Dec-2 11:42:16-0800 |
Total processes
161
Monitored processes
30
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | wmic os get oslanguage /FORMAT:LIST | C:\Windows\SysWOW64\wbem\WMIC.exe | — | WindowsUpdates.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\Program Files (x86)\Microsoft\WindowsUpdates\WindowsUpdates.exe" --meshServiceName="WindowsUpdates" --installedByUser="S-1-5-21-1693682860-607145093-2874071422-1001" | C:\Program Files (x86)\Microsoft\WindowsUpdates\WindowsUpdates.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: Microsoft Updates Version: 2022-Dec-2 11:42:16-0800 Modules
| |||||||||||||||
| 1300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | wmic SystemEnclosure get ChassisTypes | C:\Windows\SysWOW64\wbem\WMIC.exe | — | WindowsUpdates.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WindowsUpdates.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | powershell -noprofile -nologo -command - | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | WindowsUpdates.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3896 | wmic SystemEnclosure get ChassisTypes | C:\Windows\SysWOW64\wbem\WMIC.exe | — | WindowsUpdates.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 699
Read events
23 679
Write events
20
Delete events
0
Modification events
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WindowsUpdates |
| Operation: | write | Name: | ImagePath |
Value: "C:\Program Files (x86)\Microsoft\WindowsUpdates\WindowsUpdates.exe" --meshServiceName="WindowsUpdates" --installedByUser="S-1-5-21-1693682860-607145093-2874071422-1001" | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WindowsUpdates |
| Operation: | write | Name: | EstimatedSize |
Value: 3751 | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WindowsUpdates |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WindowsUpdates |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WindowsUpdates |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Microsoft\WindowsUpdates\WindowsUpdates.exe -funinstall --meshServiceName="WindowsUpdates" | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WindowsUpdates |
| Operation: | write | Name: | DisplayVersion |
Value: 2022-12-02 19:42:16.000+00:00 | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WindowsUpdates |
| Operation: | write | Name: | _InstalledBy |
Value: S-1-5-21-1693682860-607145093-2874071422-1001 | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WindowsUpdates |
| Operation: | write | Name: | DisplayName |
Value: Windows Updates | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WindowsUpdates |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Microsoft\WindowsUpdates\WindowsUpdates.exe | |||
| (PID) Process: | (4172) WindowsUpdates.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\WindowsUpdates |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Microsoft\WindowsUpdates\ | |||
Executable files
1
Suspicious files
7
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1012 | WindowsUpdates.exe | C:\Program Files (x86)\Microsoft\WindowsUpdates\WindowsUpdates.msh | text | |
MD5:F54FF1E38381E50EA7CA8EC2DD567D1F | SHA256:93C59BB2D6CE217AD7AB22777B54A8155510E8AC43F9A3D6547BA8BDE7A83328 | |||
| 4172 | WindowsUpdates.exe | C:\Program Files (x86)\Microsoft\WindowsUpdates\WindowsUpdates.exe | executable | |
MD5:A4A3F62DB6DE8CE84CE275FC1C3A4C00 | SHA256:25F66AE1220A7EA09C0B5A06BA10D53ED461369C7AD357605D7DE03410D59577 | |||
| 1012 | WindowsUpdates.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\9F7694EA089DF94AB8EB0E6A92A47F07BAAB6C29 | binary | |
MD5:6A329B88FF810FC7532E6A91E8C2B4AB | SHA256:FDDD5FB1E89F30073069369B4811B80DCEE8ECE5B1DA2E996FECC6389F9A2C6B | |||
| 1012 | WindowsUpdates.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\350BCBF87AB5B7B9FC19DFC09C528217A8F15146 | binary | |
MD5:0D7C263C1DFACA7B23397736C979ECFD | SHA256:901FE8267EE58C2497D43ABE09B45BF07D82612333A3D95E2D4E763D4E5D63BC | |||
| 4424 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_aqthm5bg.zjq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6760 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_n4ti4rb1.mfm.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6512 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_4bzq3a52.vdi.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1012 | WindowsUpdates.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\8E9DF70E3B687FC46CF7DDE56FEC6D3BA885A0C0 | binary | |
MD5:78206A10E9B8A02B6071C4658547EFC0 | SHA256:B7DA5D07A2232A5F7996761235F4DDF5D1439962826EEED59432A0CA3159D14E | |||
| 6512 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_iynquuum.aae.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2332 | powershell.exe | C:\Windows\Temp\__PSScriptPolicyTest_jcbu3tzt.css.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
17
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2384 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2384 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
omokta.com |
| malicious |