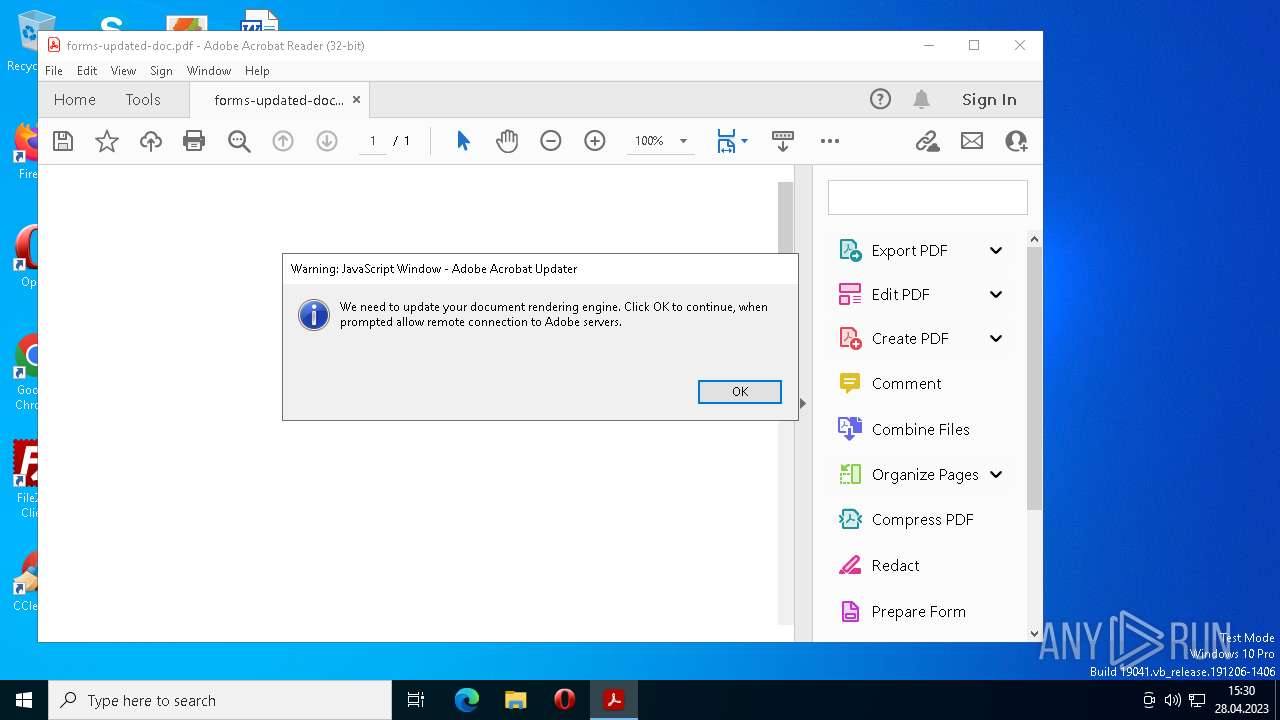
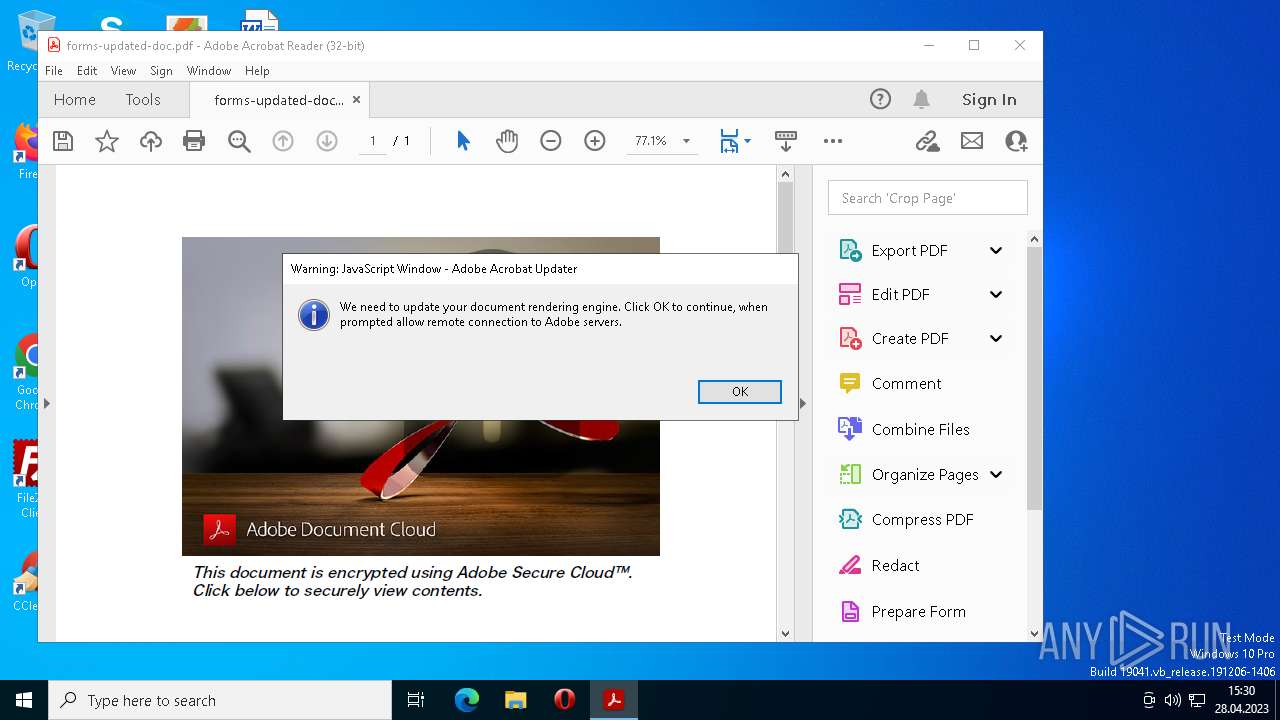
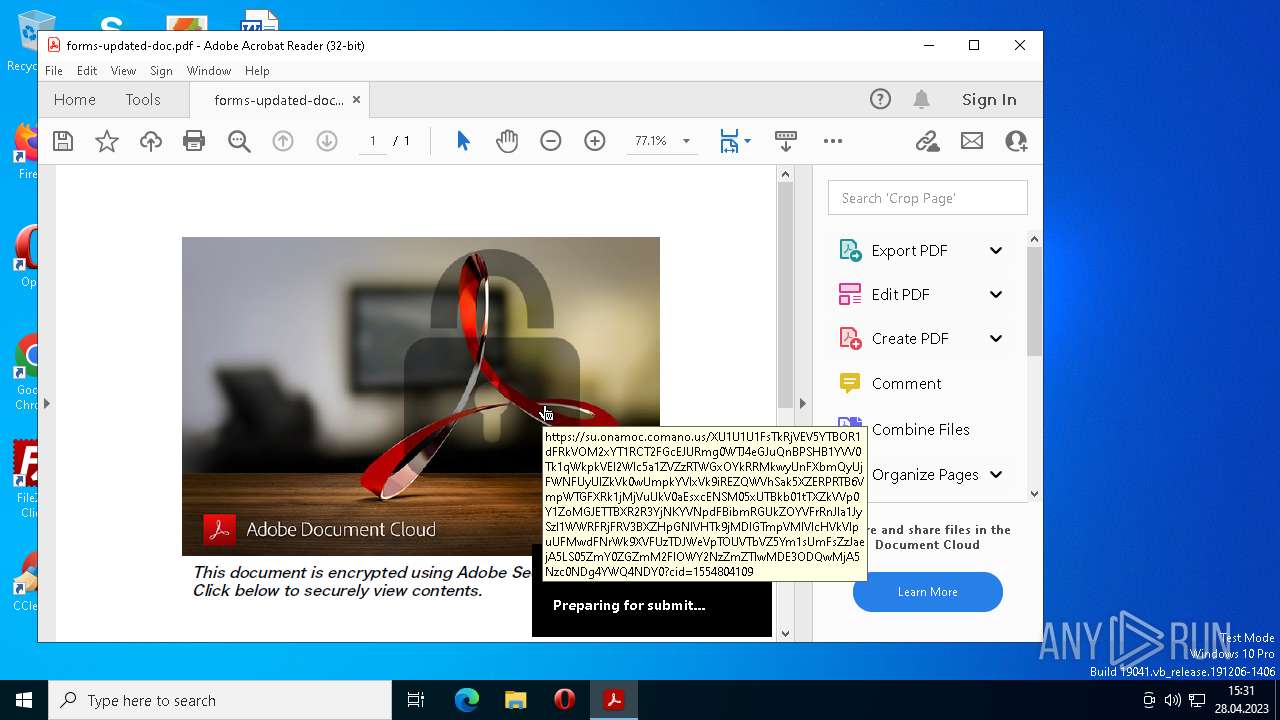
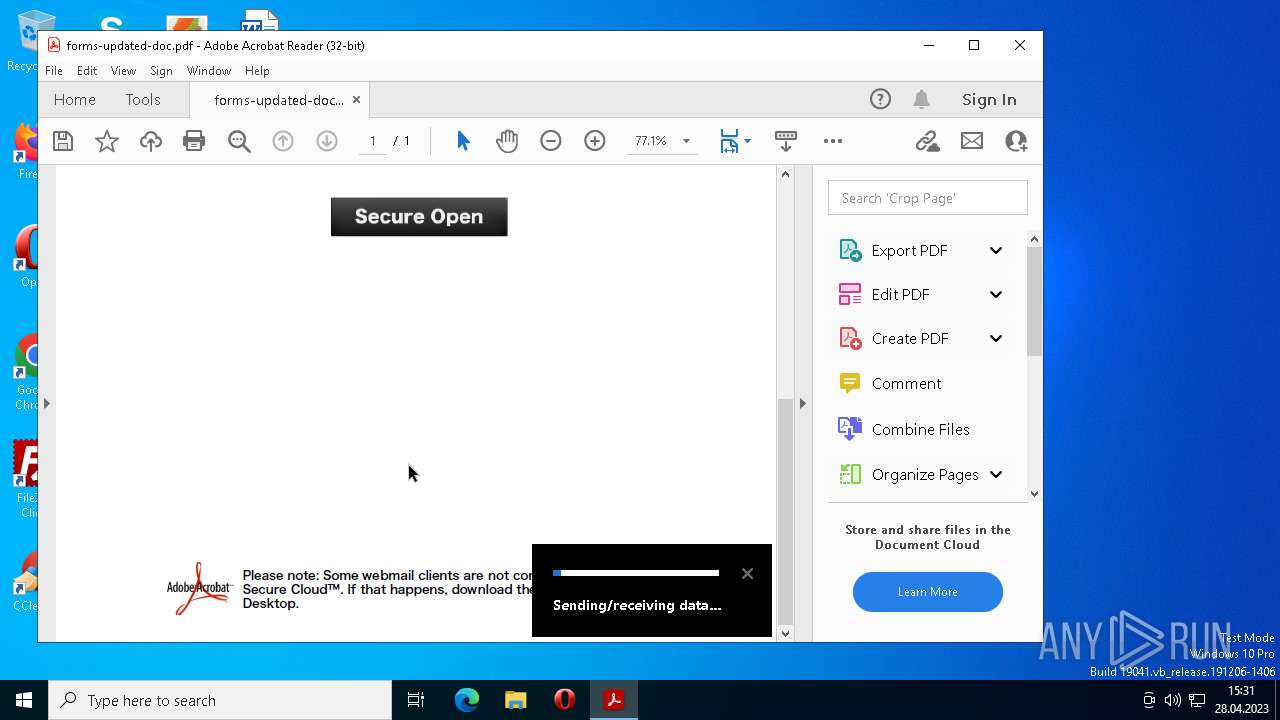
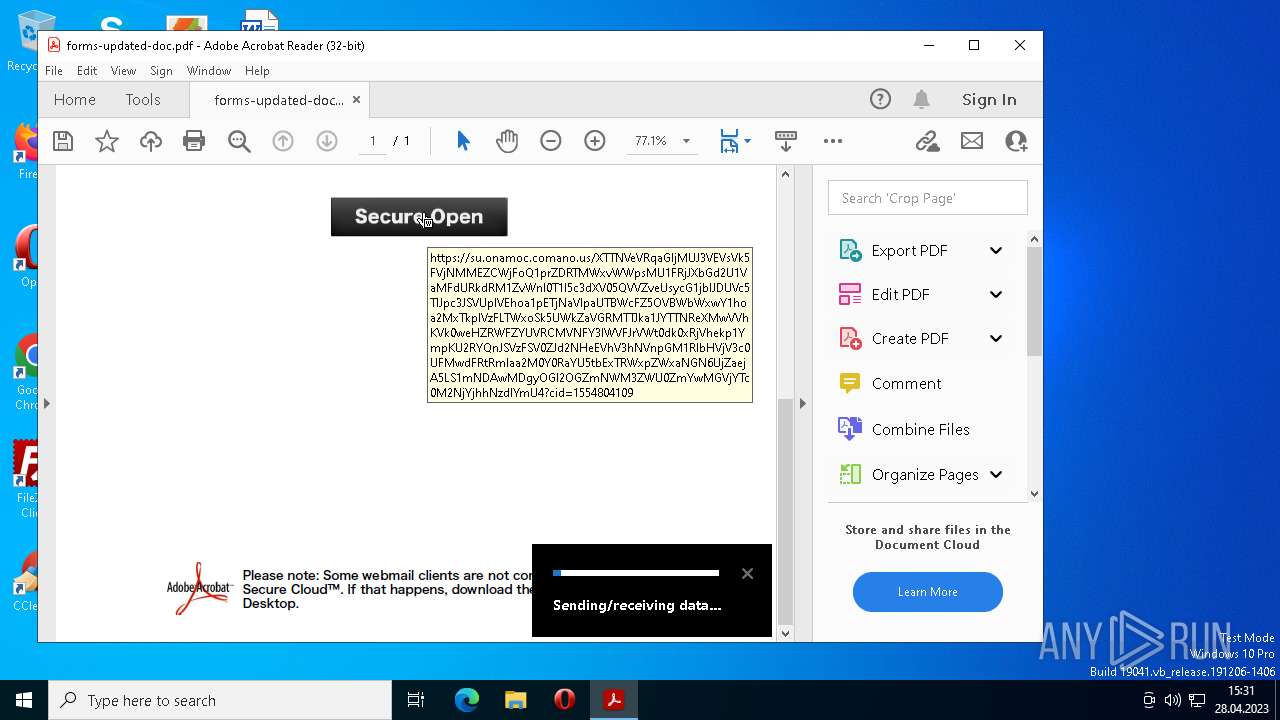
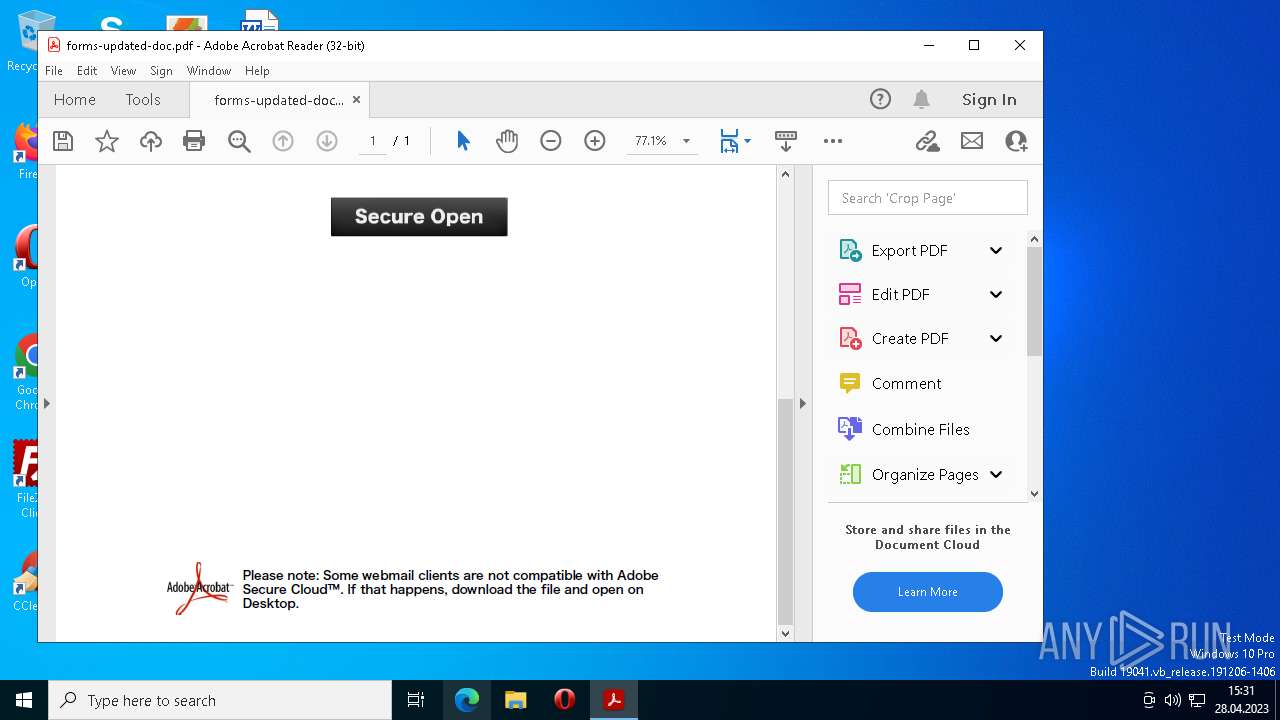
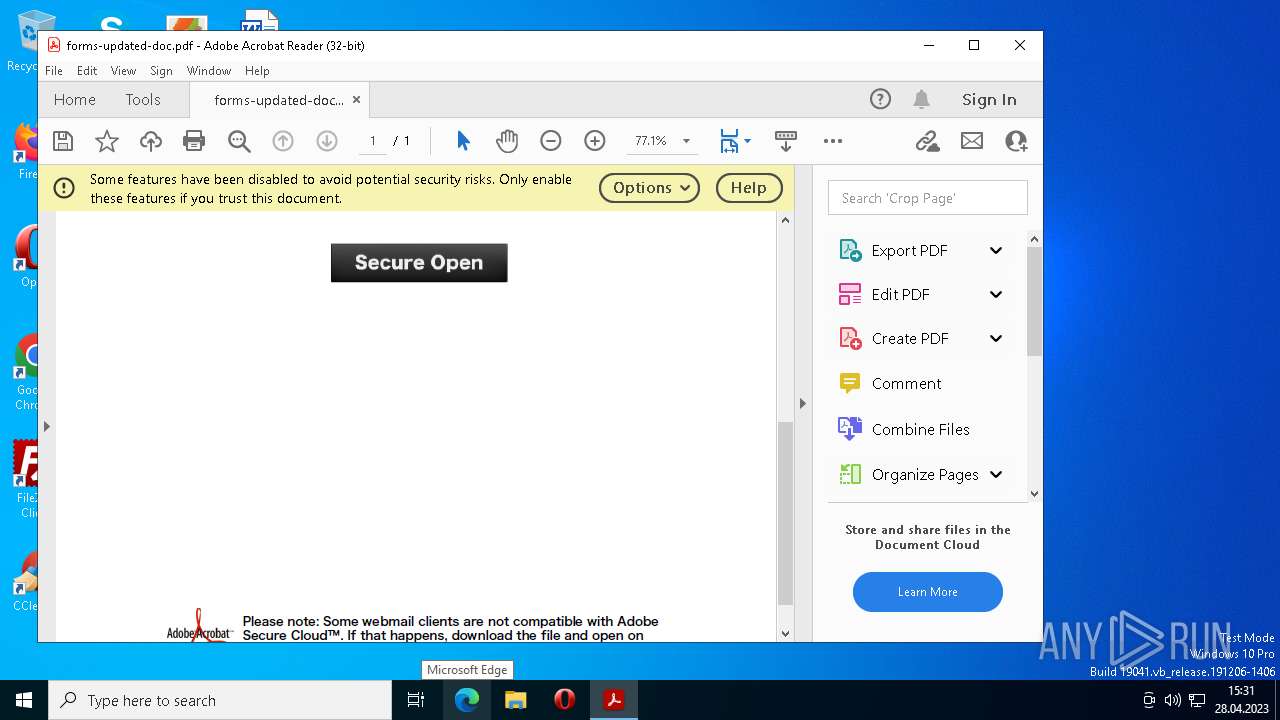
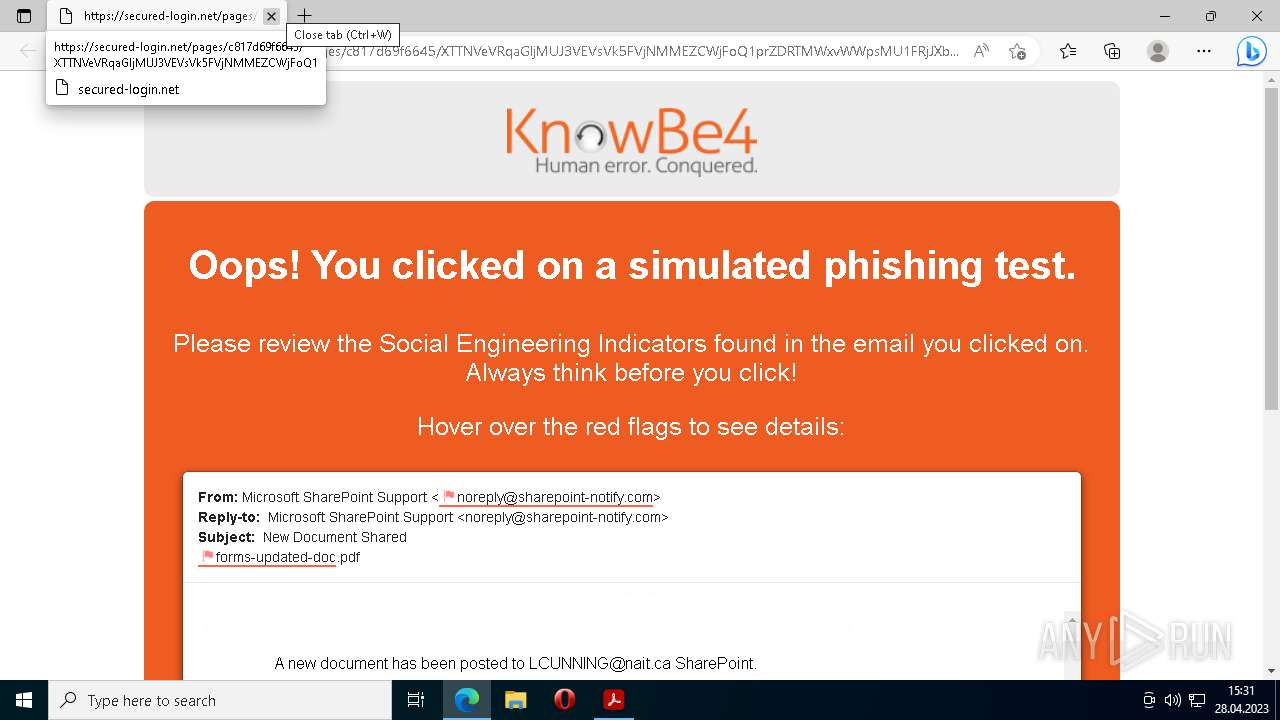
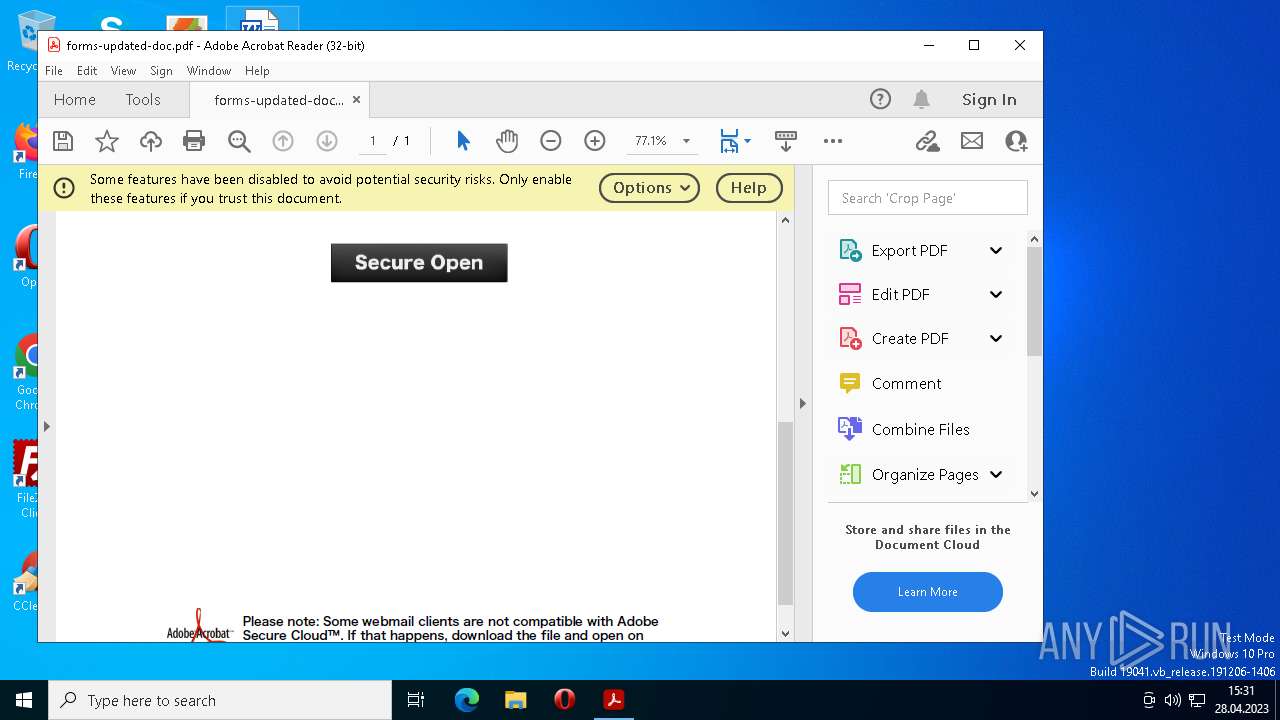
| File name: | forms-updated-doc.pdf |
| Full analysis: | https://app.any.run/tasks/ad31f4b5-e13e-413c-9970-102b08d9cd94 |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2023, 15:30:47 |
| OS: | Windows 10 Professional (build: 19044, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.6 |
| MD5: | D62C3B4653633D5EEF4569CB5F930B57 |
| SHA1: | 6D2032862632C60EB37E0CBD478603EDC39D6D9D |
| SHA256: | 25F4F80E2E0B480170CA68BCD88B8365A646EB935A4415D846C37B5C1336EA20 |
| SSDEEP: | 1536:9yZK6SH7RbBcq/hBOitOOdG538OZU+KaSxtLRU+9S/BqK365UBm/A4t:4ZWbBd/zLdy38AU+1SBU+wT3KUBmx |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- msedge.exe (PID: 3824)
- RdrCEF.exe (PID: 3272)
- AcroRd32.exe (PID: 5012)
- msedge.exe (PID: 7808)
The process checks LSA protection
- identity_helper.exe (PID: 7796)
- identity_helper.exe (PID: 4904)
Checks supported languages
- identity_helper.exe (PID: 7796)
- identity_helper.exe (PID: 4904)
Reads the computer name
- identity_helper.exe (PID: 7796)
- identity_helper.exe (PID: 4904)
Changes Internet Explorer settings (feature browser emulation)
- AcroRd32.exe (PID: 5012)
Create files in a temporary directory
- msedge.exe (PID: 3824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| Linearized: | No |
|---|---|
| PDFVersion: | 1.6 |
Total processes
115
Monitored processes
39
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/22.3.20314 Chrome/105.0.0.0" --lang=en-US --user-data-dir="C:\Users\admin\AppData\Local\CEF\User Data" --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\debug.log" --mojo-platform-channel-handle=1588 --field-trial-handle=1628,i,9605843609817446810,12432224371686954356,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 596 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/22.3.20314 Chrome/105.0.0.0" --lang=en-US --user-data-dir="C:\Users\admin\AppData\Local\CEF\User Data" --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\debug.log" --mojo-platform-channel-handle=2216 --field-trial-handle=1628,i,9605843609817446810,12432224371686954356,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe | RdrCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/22.3.20314 Chrome/105.0.0.0" --user-data-dir="C:\Users\admin\AppData\Local\CEF\User Data" --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2716 --field-trial-handle=1628,i,9605843609817446810,12432224371686954356,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 1808 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2236 --field-trial-handle=2056,i,14876727496178219847,3735601174513845453,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=111.0.5563.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=111.0.1661.62 --initial-client-data=0x124,0x128,0x12c,0x100,0x134,0x7a878650,0x7a878660,0x7a87866c | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 2020 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/22.3.20314 Chrome/105.0.0.0" --user-data-dir="C:\Users\admin\AppData\Local\CEF\User Data" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2432 --field-trial-handle=1628,i,9605843609817446810,12432224371686954356,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 3096 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2180 --field-trial-handle=2064,i,1078438717210631148,18093471649982331954,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 3272 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\acrocef_1\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 22.3.20314.0 Modules
| |||||||||||||||
| 3316 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4628 --field-trial-handle=2064,i,1078438717210631148,18093471649982331954,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 3560 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4304 --field-trial-handle=2064,i,1078438717210631148,18093471649982331954,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
Total events
39 798
Read events
39 668
Write events
128
Delete events
2
Modification events
| (PID) Process: | (5392) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 1 | |||
| (PID) Process: | (5012) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | AcroRd32.exe |
Value: 9999 | |||
| (PID) Process: | (5392) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\CommonFiles\Usage\Reader DC |
| Operation: | write | Name: | optin |
Value: 1 | |||
| (PID) Process: | (5012) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5012) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5012) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5012) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5012) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5012) AcroRd32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3824) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
2
Suspicious files
478
Text files
218
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5012 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\Reader\DesktopNotification\NotificationsDB\notificationsDB | sqlite | |
MD5:D4413FE1B40D9A863D236A2CBBECB194 | SHA256:4008C44AD258710284F37A5E3647488C8160E969877FD5974B07B2189F3384D2 | |||
| 4820 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\000001.dbtmp | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 4820 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 3272 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\wasm\index-dir\temp-index | binary | |
MD5:D75D7432571A0525AFC2DB56DA87756C | SHA256:83E52F3B75A5738153305604CCCEE2CC53BAC5790EA1E602E24B94A7DF221629 | |||
| 5392 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\Files\TESTING | mp3 | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 5392 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\Reader\DesktopNotification\NotificationsDB\notificationsDB-journal | binary | |
MD5:18089CA3F56AEE739BBAEF4F11842914 | SHA256:EDFF3492BC3C4DA9D8AEDBAE6C4EC870CFD0FE6931B6A59856A7E07FA180A71E | |||
| 3272 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\000001.dbtmp | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 3272 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\index | binary | |
MD5:54CB446F628B2EA4A5BCE5769910512E | SHA256:FBCFE23A2ECB82B7100C50811691DDE0A33AA3DA8D176BE9882A9DB485DC0F2D | |||
| 3272 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\CURRENT | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 3272 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\index-dir\temp-index | binary | |
MD5:E28C233898C260755C009608375A6786 | SHA256:301DEB2513CB859D95E996B1FA0665E4425519787868C1E8AE21A10D419B98E9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
30
DNS requests
45
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5012 | AcroRd32.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
5012 | AcroRd32.exe | GET | 200 | 52.222.250.174:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | US | der | 1.39 Kb | shared |
5012 | AcroRd32.exe | GET | 200 | 52.222.226.205:80 | http://ocsp.r2m02.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRmbQtwnInkvkvr7BNFR%2BS2lTYPjAQUwDFSzVpQw4J8dHHOy%2Bmc%2BXrrguICEAYLe%2BQP1Z2DctvOpU88jm4%3D | US | binary | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
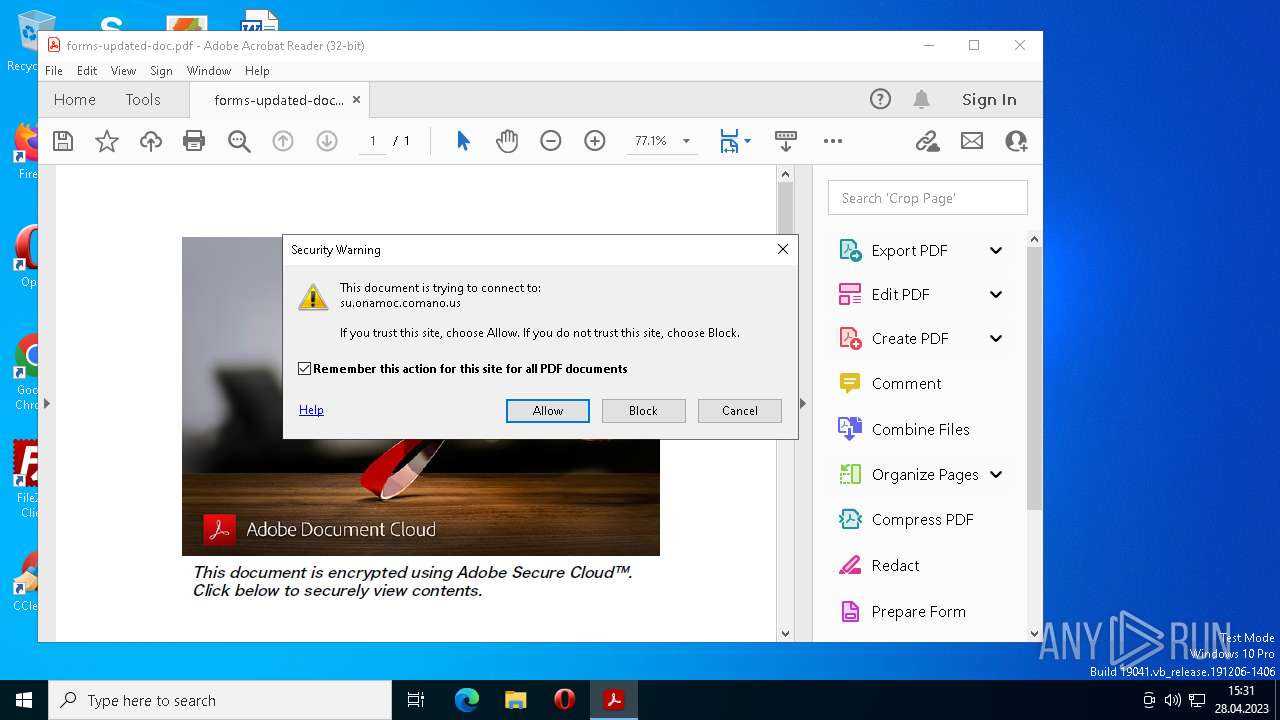
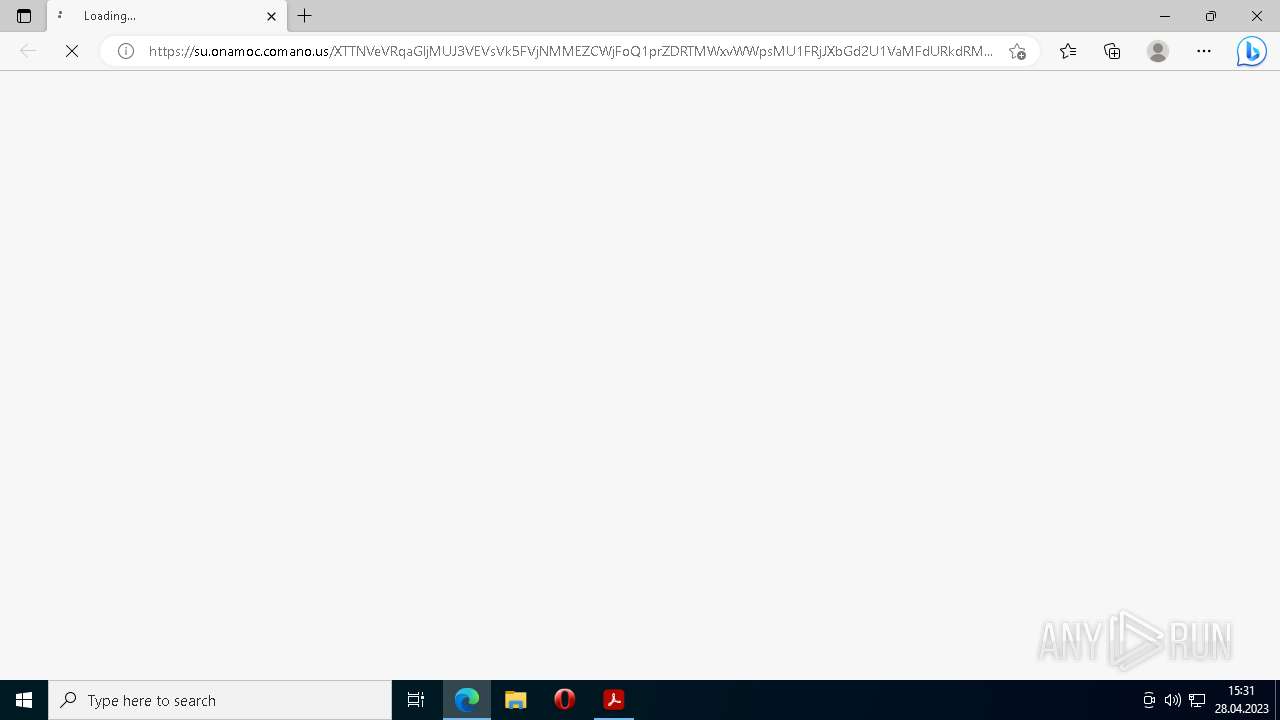
5012 | AcroRd32.exe | 52.5.176.152:443 | su.onamoc.comano.us | AMAZON-AES | US | unknown |
596 | RdrCEF.exe | 2.18.233.74:443 | armmf.adobe.com | AKAMAI-AS | DE | whitelisted |
5012 | AcroRd32.exe | 23.48.23.34:443 | acroipm2.adobe.com | Akamai International B.V. | DE | suspicious |
5012 | AcroRd32.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5012 | AcroRd32.exe | 52.222.250.174:80 | ocsp.rootca1.amazontrust.com | AMAZON-02 | US | whitelisted |
— | — | 52.222.226.205:80 | ocsp.r2m02.amazontrust.com | AMAZON-02 | US | unknown |
3096 | msedge.exe | 3.227.50.246:443 | su.onamoc.comano.us | AMAZON-AES | US | unknown |
3096 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3096 | msedge.exe | 20.105.73.143:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3096 | msedge.exe | 3.221.21.138:443 | su.onamoc.comano.us | AMAZON-AES | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
comano.us |
| unknown |
onamoc.comano.us |
| unknown |
su.onamoc.comano.us |
| suspicious |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
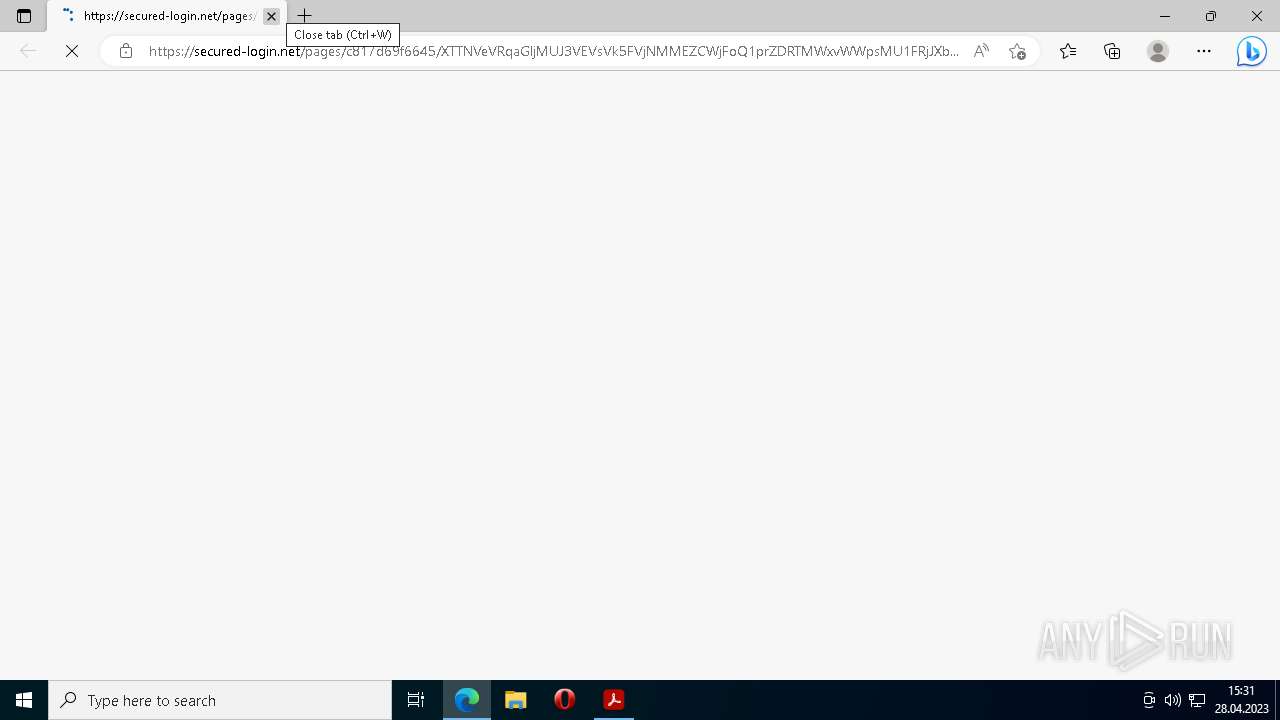
— | — | Successful Credential Theft Detected | ET POLICY Observed DNS Query to KnowBe4 Simulated Phish Domain |