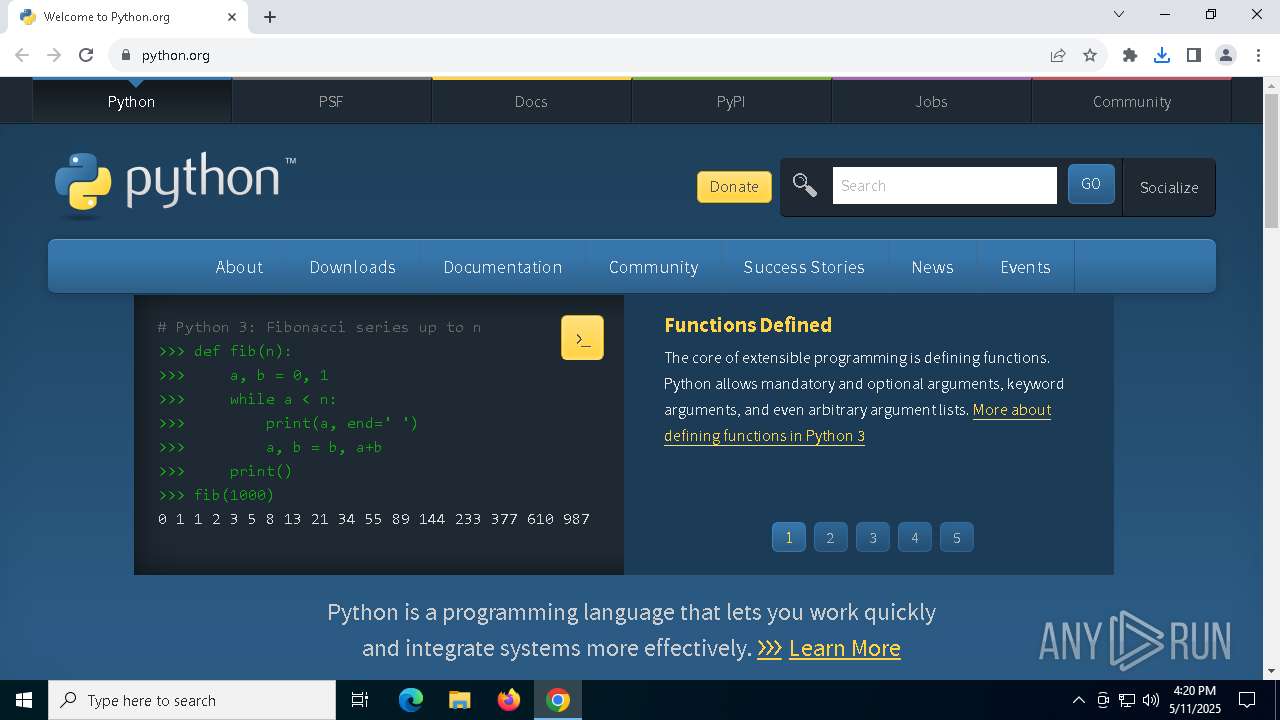
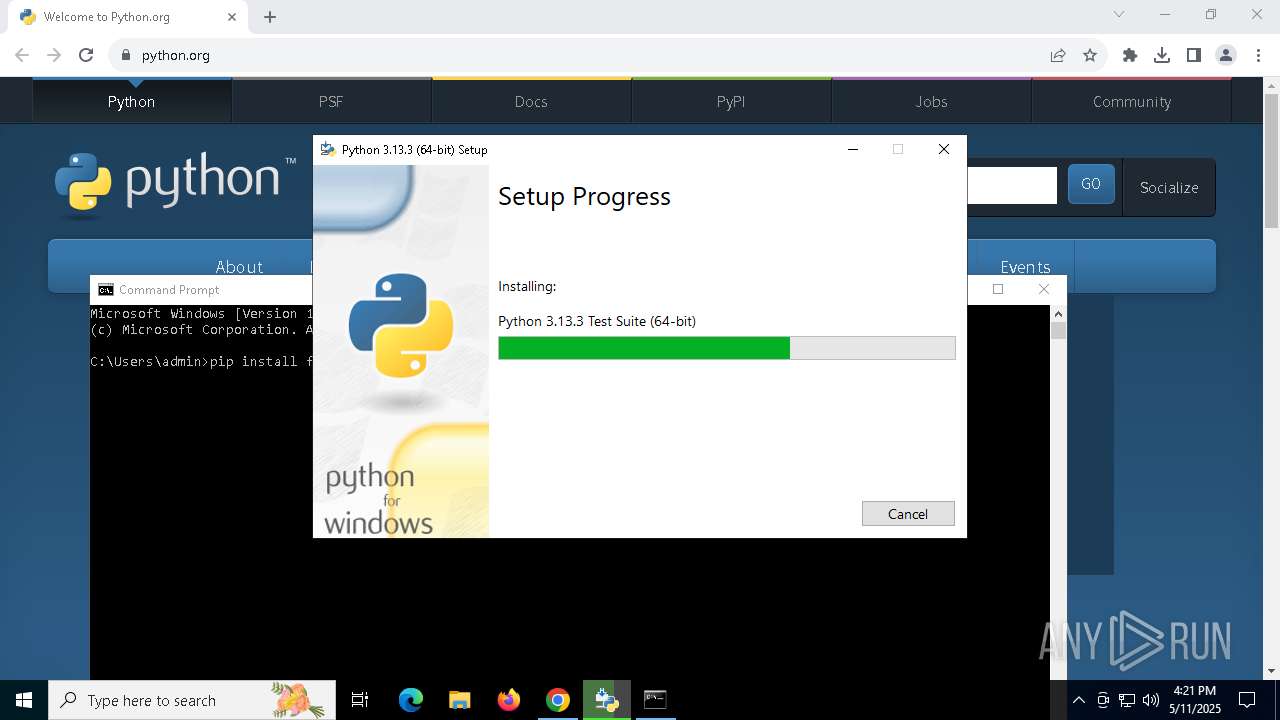
| URL: | https://python.org |
| Full analysis: | https://app.any.run/tasks/23b81e88-e356-49bf-b9a2-8419a87b275a |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 16:19:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B020AA1E3BC4746C2E3062B6F81BFC06 |
| SHA1: | EDB34DF73D486486ECB35228D1AF71D9FD3B4103 |
| SHA256: | 25D3E0D8D7300B27B0350BCA7DCC639042616DC1BA970D8C4C6B376901689ECF |
| SSDEEP: | 3:N8Yrgn:2Yrg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
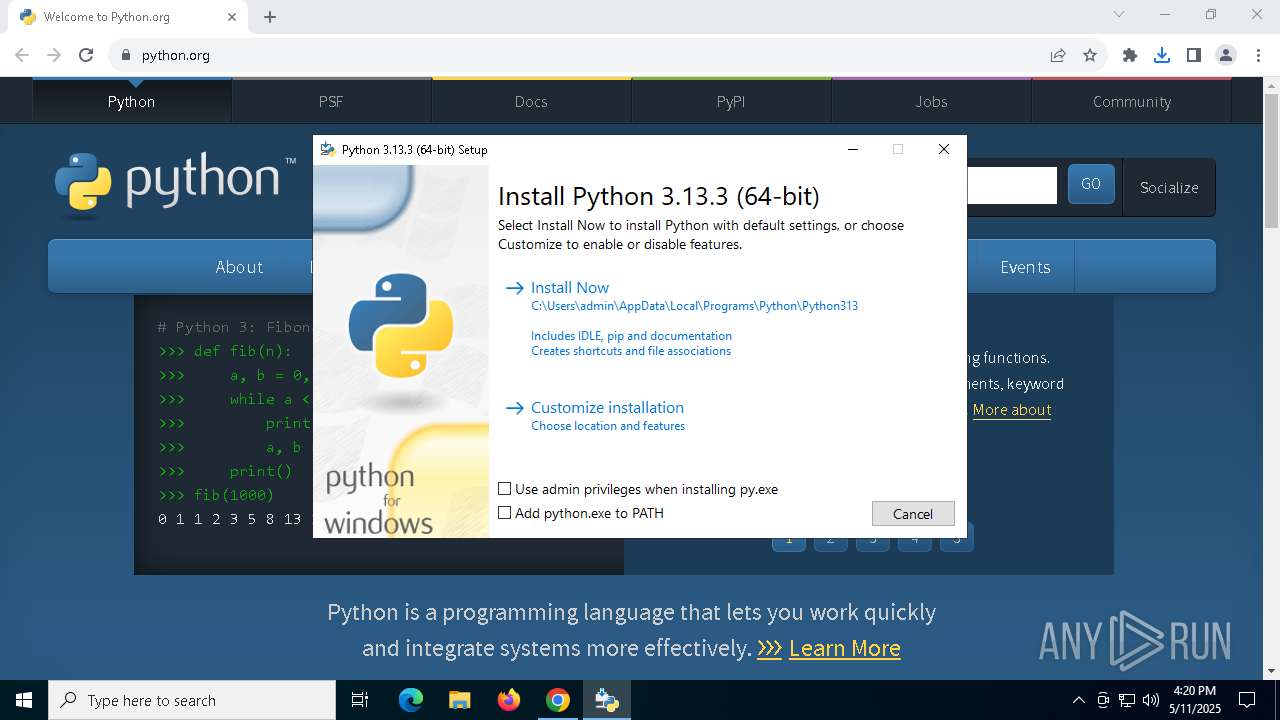
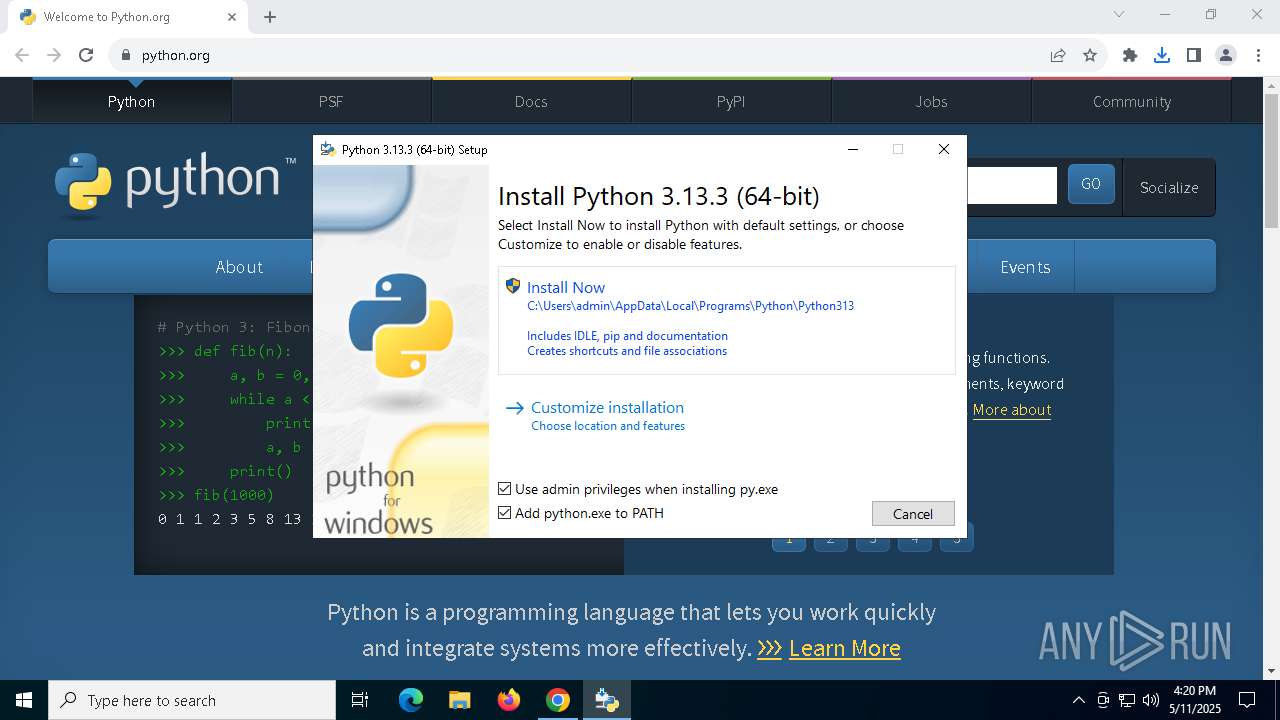
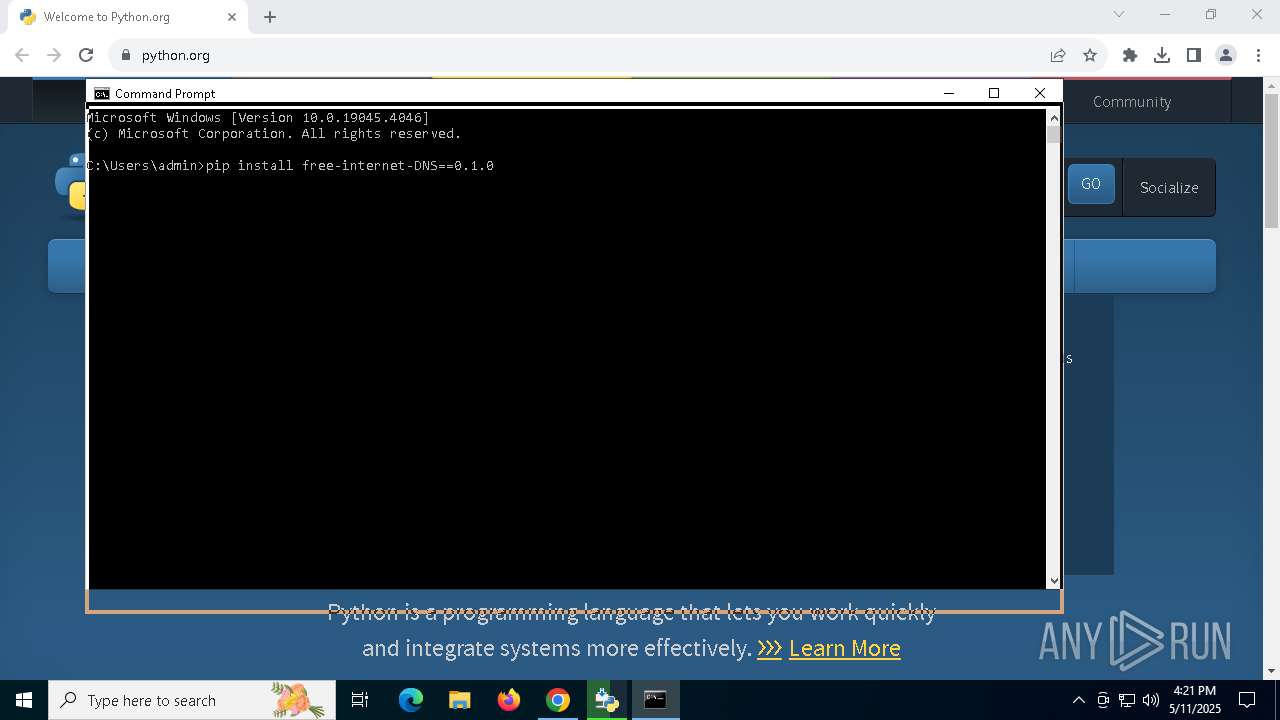
- python-3.13.3-amd64.exe (PID: 7904)
Executable content was dropped or overwritten
- python-3.13.3-amd64.exe (PID: 7904)
- python-3.13.3-amd64.exe (PID: 7976)
- python-3.13.3-amd64.exe (PID: 2268)
Starts itself from another location
- python-3.13.3-amd64.exe (PID: 7904)
Searches for installed software
- dllhost.exe (PID: 7508)
- python-3.13.3-amd64.exe (PID: 7904)
Executes as Windows Service
- VSSVC.exe (PID: 4464)
There is functionality for taking screenshot (YARA)
- python-3.13.3-amd64.exe (PID: 7904)
The process drops C-runtime libraries
- python-3.13.3-amd64.exe (PID: 7904)
- msiexec.exe (PID: 3888)
Process drops legitimate windows executable
- python-3.13.3-amd64.exe (PID: 7904)
- msiexec.exe (PID: 3888)
Process drops python dynamic module
- msiexec.exe (PID: 3888)
INFO
The sample compiled with english language support
- chrome.exe (PID: 2852)
- python-3.13.3-amd64.exe (PID: 7976)
- python-3.13.3-amd64.exe (PID: 7904)
- msiexec.exe (PID: 3888)
Executable content was dropped or overwritten
- chrome.exe (PID: 2852)
- msiexec.exe (PID: 3888)
Create files in a temporary directory
- python-3.13.3-amd64.exe (PID: 7976)
- python-3.13.3-amd64.exe (PID: 7904)
Checks supported languages
- python-3.13.3-amd64.exe (PID: 7904)
- python-3.13.3-amd64.exe (PID: 7976)
- python-3.13.3-amd64.exe (PID: 2268)
Reads the computer name
- python-3.13.3-amd64.exe (PID: 7904)
- python-3.13.3-amd64.exe (PID: 2268)
Process checks computer location settings
- python-3.13.3-amd64.exe (PID: 7904)
Application launched itself
- chrome.exe (PID: 2852)
Reads the software policy settings
- slui.exe (PID: 7812)
Manages system restore points
- SrTasks.exe (PID: 4428)
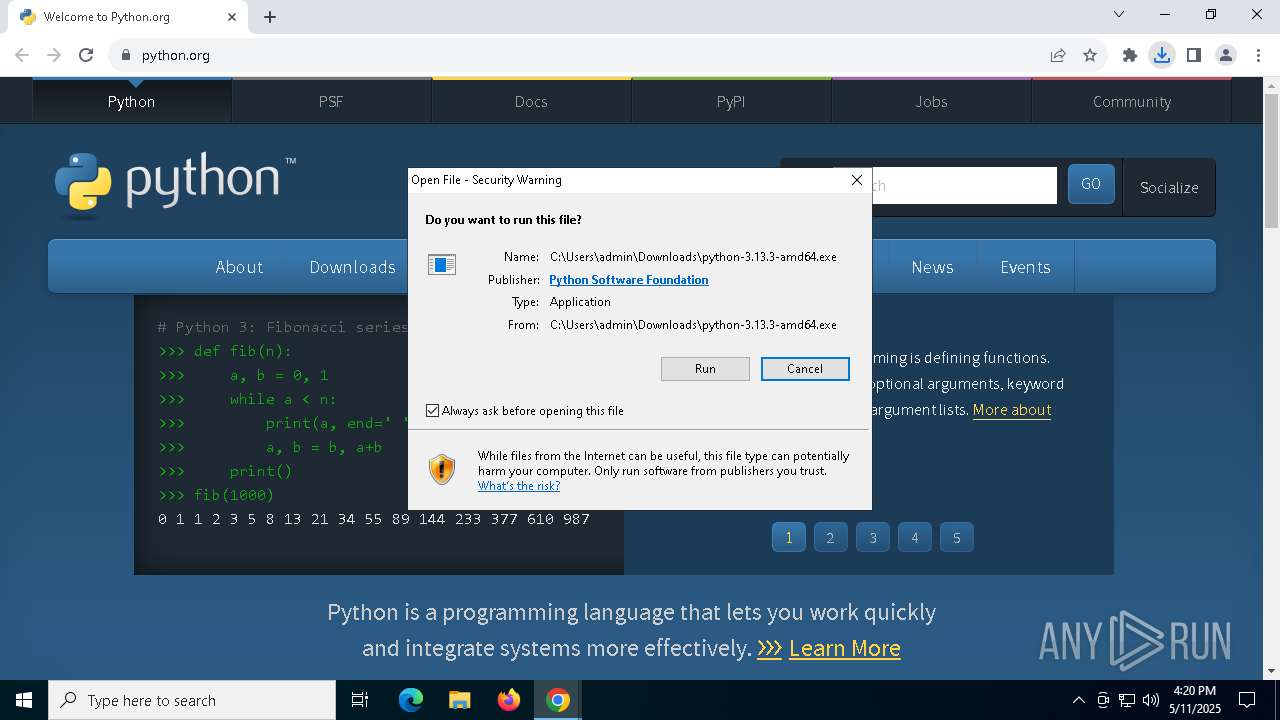
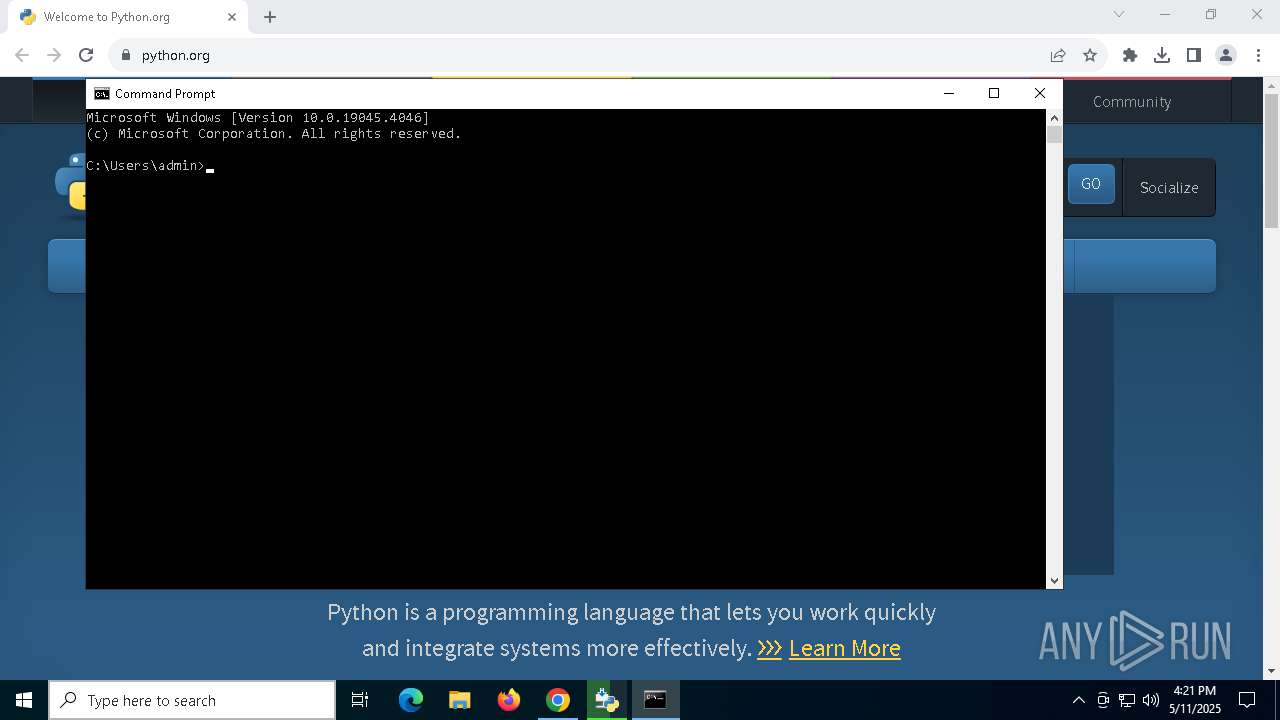
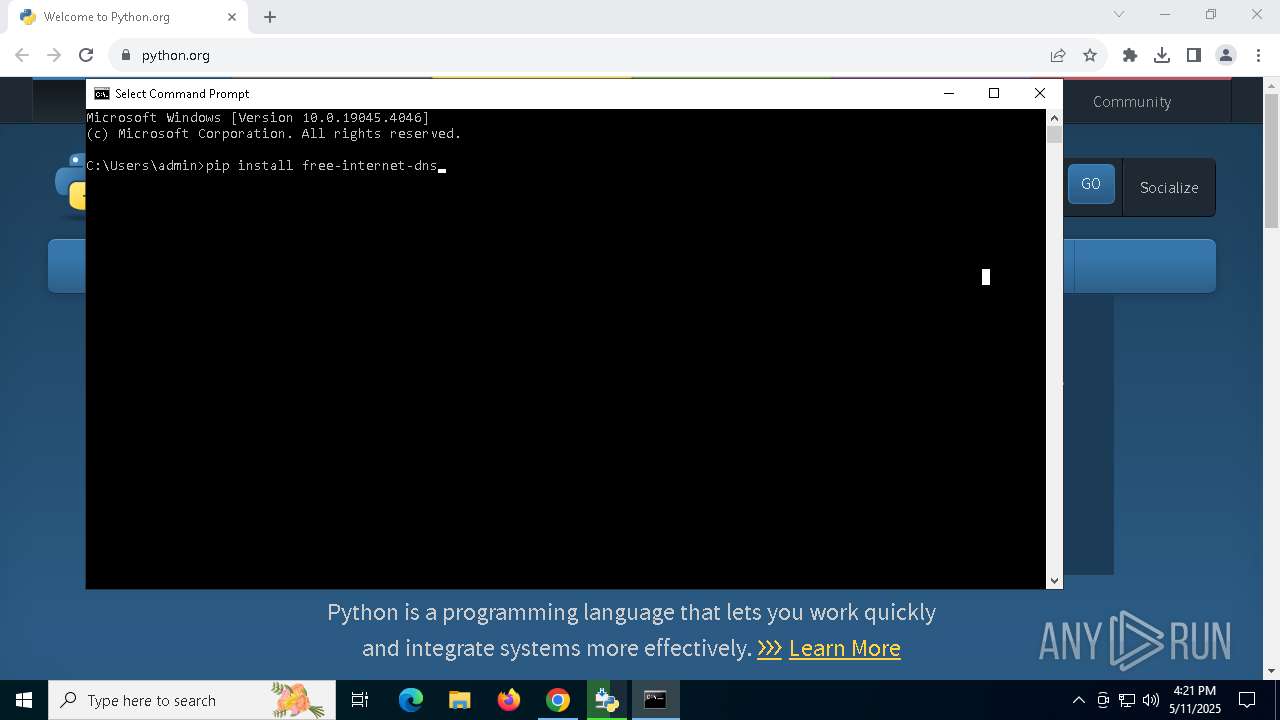
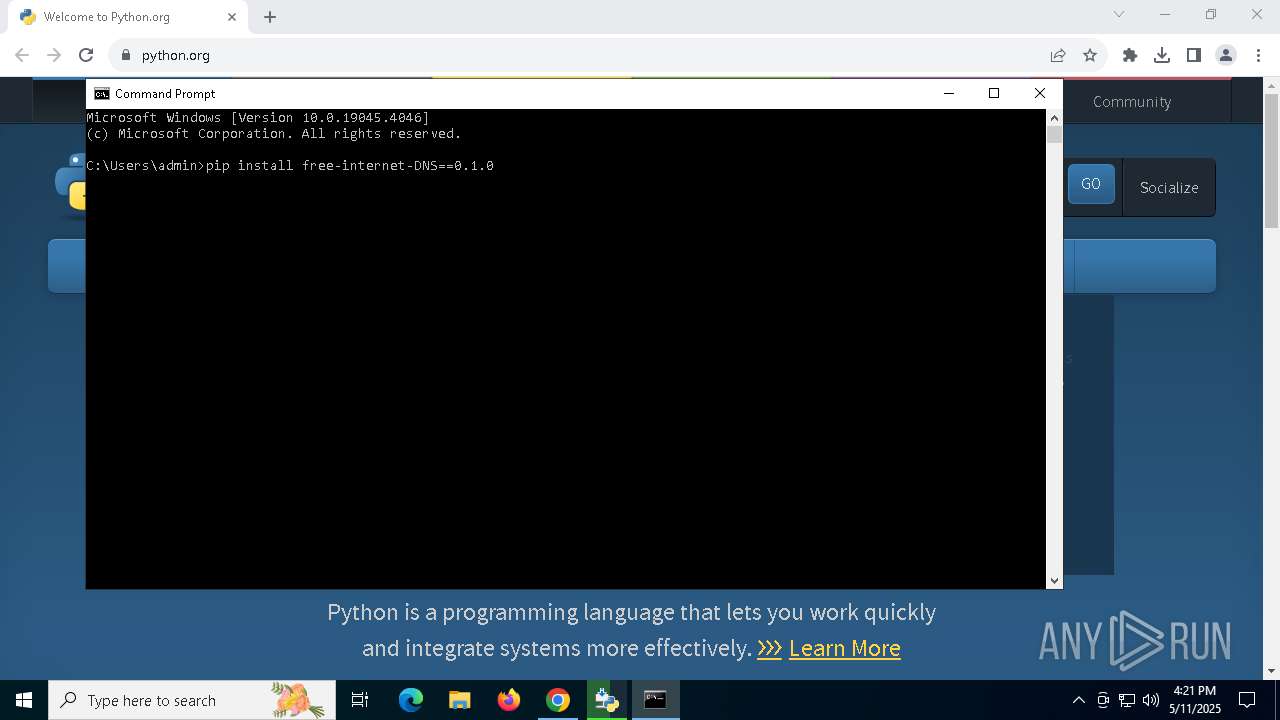
Manual execution by a user
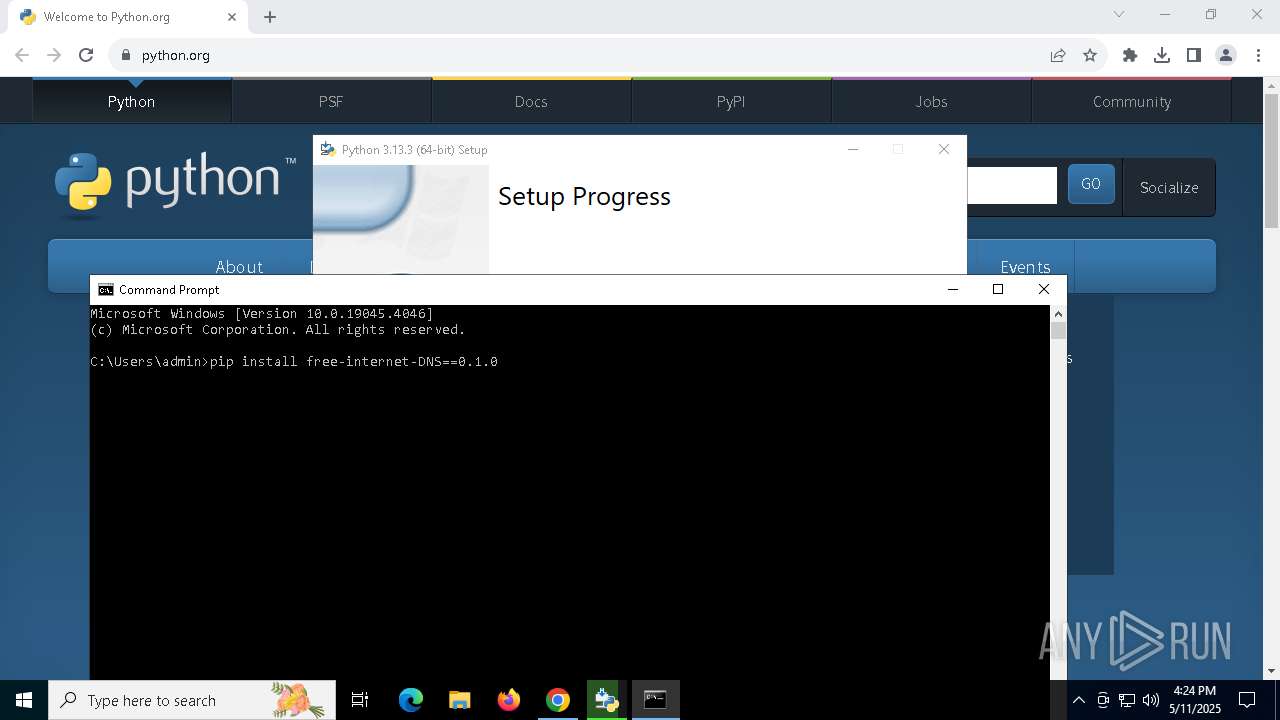
- cmd.exe (PID: 8056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
177
Monitored processes
32
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6112 --field-trial-handle=1928,i,17613772769106212803,4092945149834643284,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4916 --field-trial-handle=1928,i,17613772769106212803,4092945149834643284,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
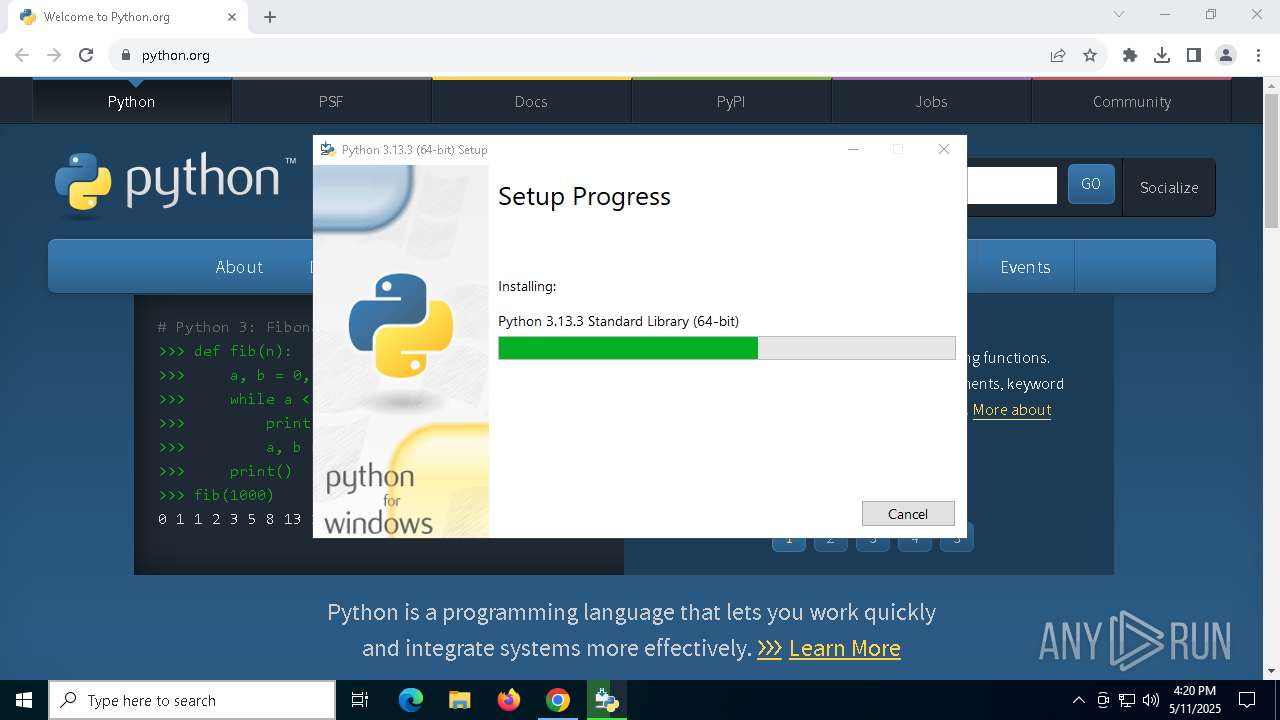
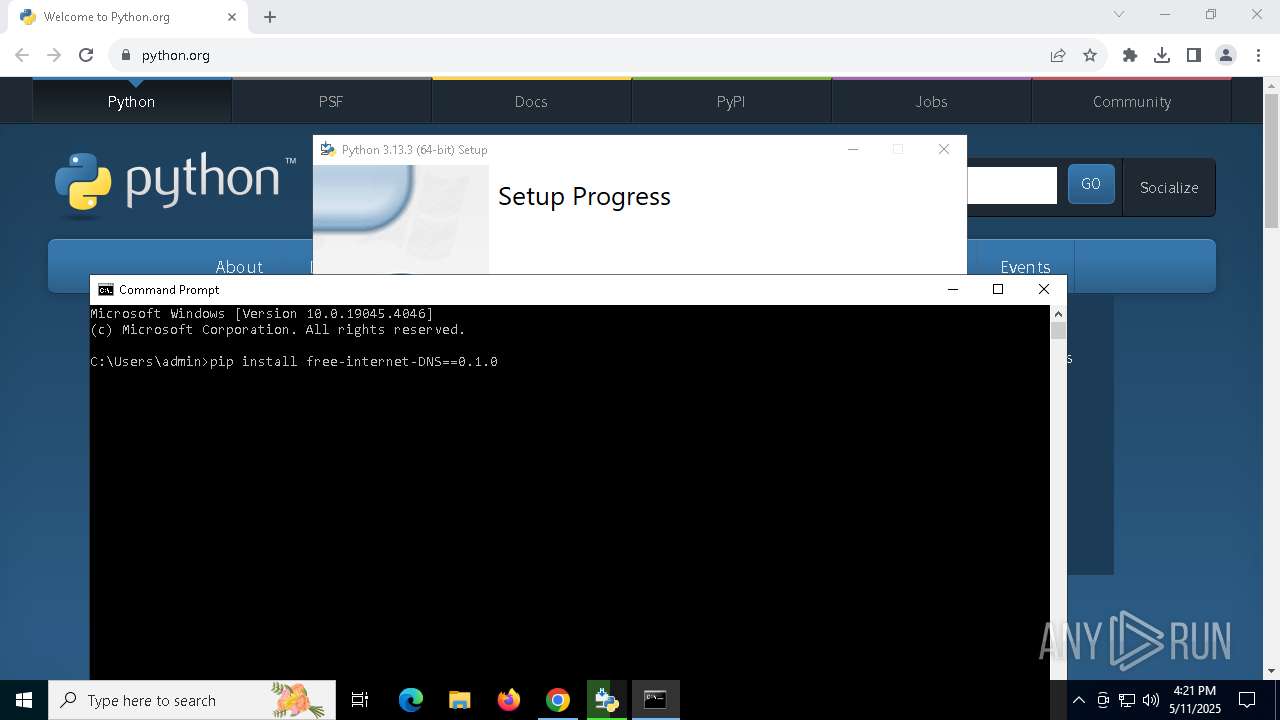
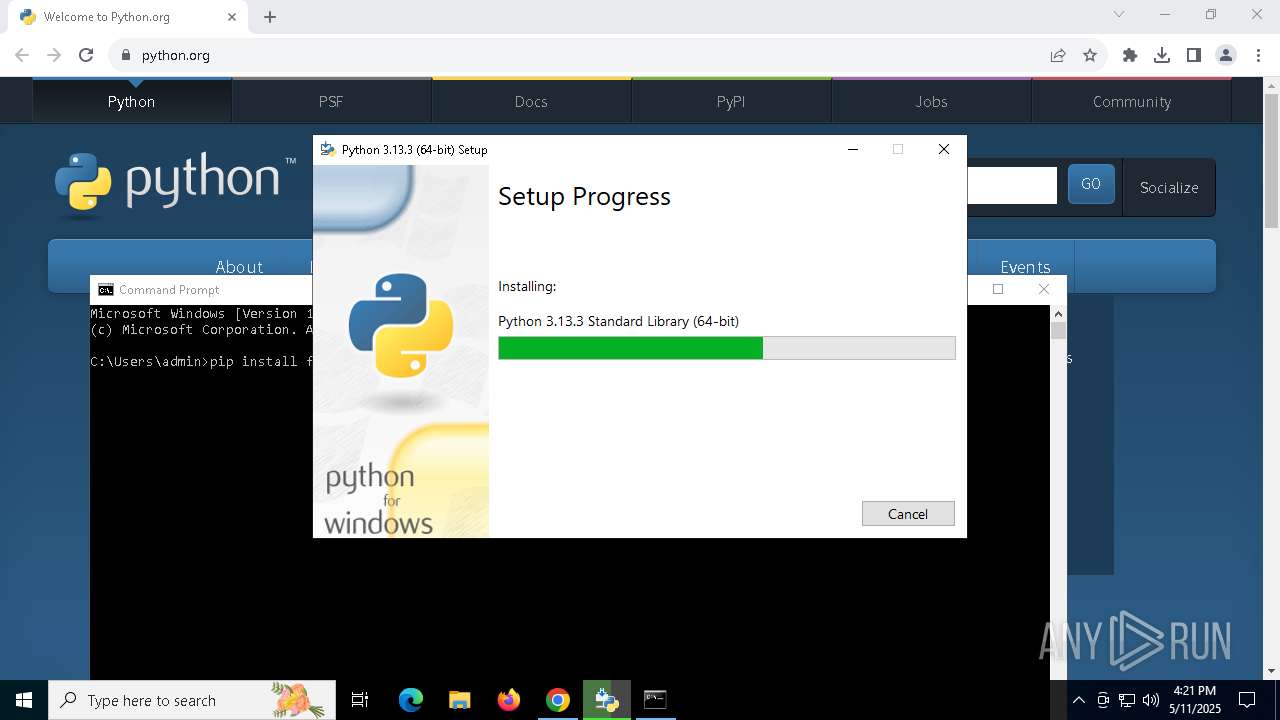
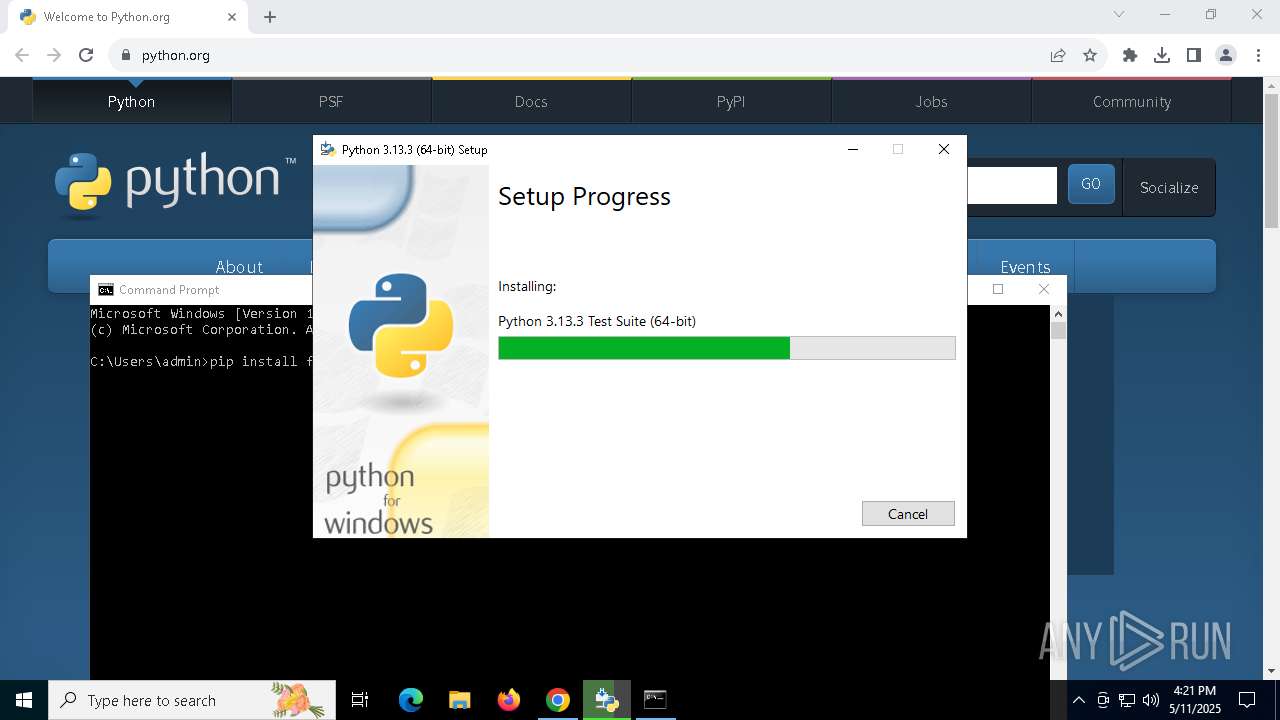
| 2268 | "C:\Users\admin\AppData\Local\Temp\{DD9FE86D-E224-4815-AAC7-756E6DF24F9E}\.be\python-3.13.3-amd64.exe" -q -burn.elevated BurnPipe.{CD54D2A7-39B8-4EC5-955E-0E66B6ACD8E3} {A28A04D2-20E0-4ED3-899B-2A3FFADB8582} 7904 | C:\Users\admin\AppData\Local\Temp\{DD9FE86D-E224-4815-AAC7-756E6DF24F9E}\.be\python-3.13.3-amd64.exe | python-3.13.3-amd64.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python 3.13.3 (64-bit) Version: 3.13.3150.0 Modules
| |||||||||||||||
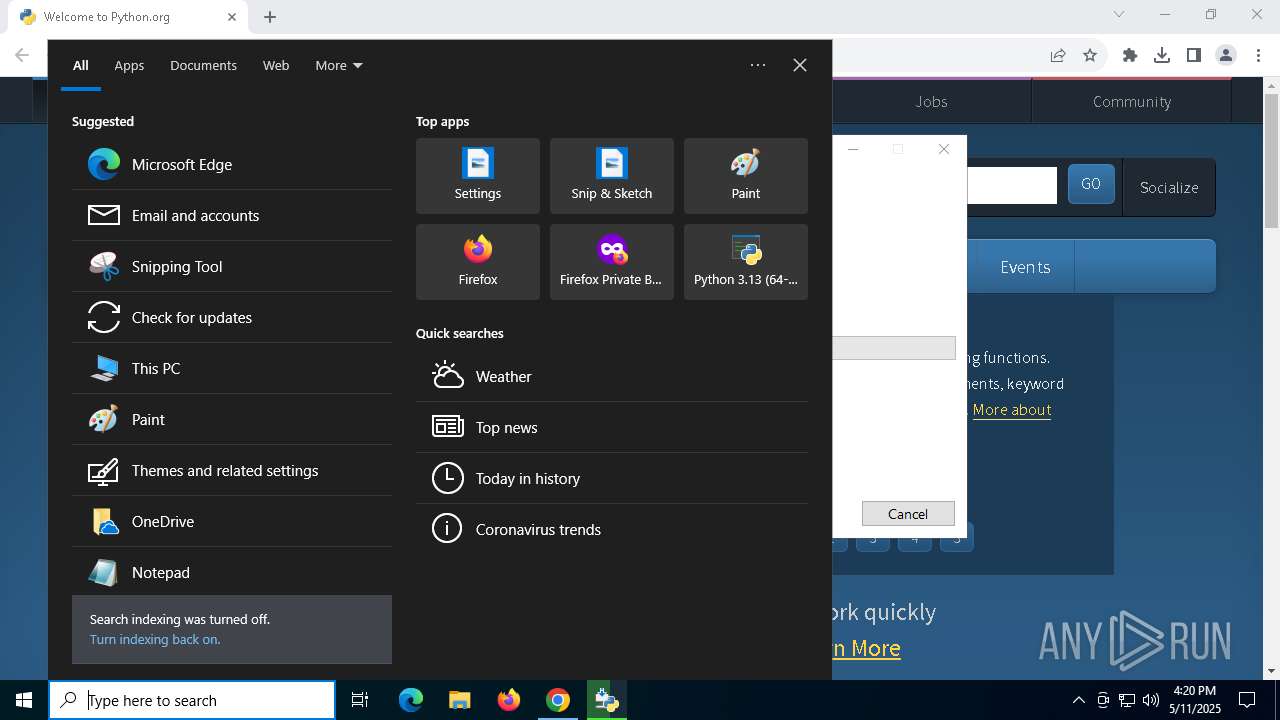
| 2852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://python.org" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3888 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4012 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5224 --field-trial-handle=1928,i,17613772769106212803,4092945149834643284,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4428 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4464 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5184 --field-trial-handle=1928,i,17613772769106212803,4092945149834643284,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
48 681
Read events
43 255
Write events
5 335
Delete events
91
Modification events
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6816) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000977C9B7F90C2DB01 | |||
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | ahfgeienlihckogmohjhadlkjgocpleb |
Value: 3B08F722C14555E595AF269F140EE426CE8DEBAD90D03EE9FF33B95CB34233F6 | |||
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | bjbddleefiddlmdfdfbgodgacjjldihj |
Value: 5CFE6AD362B9AABBD07085580BC6C063CF1C79A0B22ECB6BCBA21EECA68BA07F | |||
| (PID) Process: | (2852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | mhjfbmdgcfjbbpaeojofohoefgiehjai |
Value: F6EE482B70E472BD0FE04C8E130D7E2A0D87334BDC8F199AD874C100863BC5BE | |||
Executable files
97
Suspicious files
417
Text files
3 350
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c584.TMP | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c584.TMP | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c594.TMP | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c594.TMP | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c594.TMP | — | |
MD5:— | SHA256:— | |||
| 2852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c584.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
78
DNS requests
71
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2852 | chrome.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTOQYLFSE5GO%2FpaRVfYu7d9gZEbQAQU2UEpsA8PY2zvadf1zSmepEhqMOYCEzMAAAAHN4xbodlbjNQAAAAAAAc%3D | unknown | — | — | whitelisted |
5332 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5332 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2852 | chrome.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTDHsfuqfubd3pihvq4mgQVWgHWNwQUyH7SaoUqG8oZmAQHJ89QEE9oqKICEzMAAAAHh6M0o3uljhwAAAAAAAc%3D | unknown | — | — | whitelisted |
8032 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adbydczem5azdzgosq7w5ch3hcwa_20250424.754192769.14/obedbbhbpmojnkanicioggnmelmoomoc_20250424.754192769.14_all_ENUS500000_acbxhbfgjtcl2dyhrz3ueobjijbq.crx3 | unknown | — | — | whitelisted |
8032 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adbydczem5azdzgosq7w5ch3hcwa_20250424.754192769.14/obedbbhbpmojnkanicioggnmelmoomoc_20250424.754192769.14_all_ENUS500000_acbxhbfgjtcl2dyhrz3ueobjijbq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7336 | chrome.exe | 151.101.0.223:443 | python.org | FASTLY | US | whitelisted |
2852 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
python.org |
| whitelisted |
accounts.google.com |
| whitelisted |
www.python.org |
| whitelisted |
client.wns.windows.com |
| whitelisted |
analytics.python.org |
| whitelisted |
media.ethicalads.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7336 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
7336 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
7336 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
7336 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |