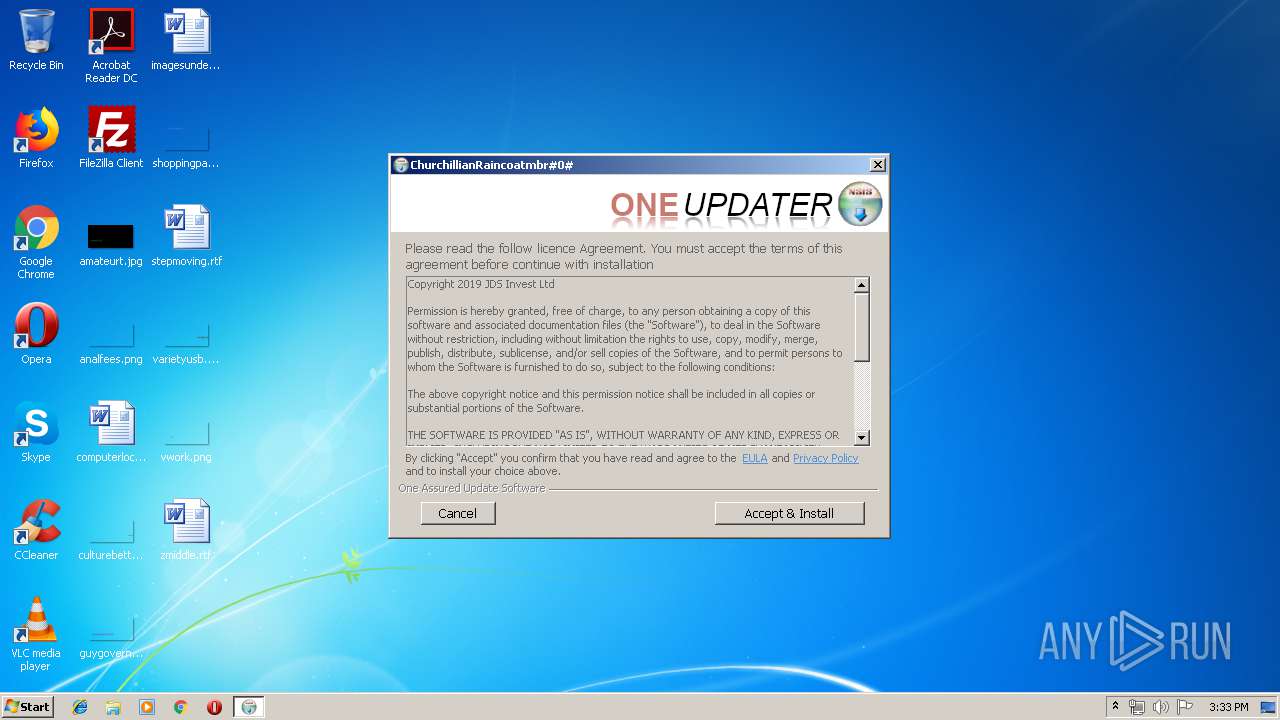
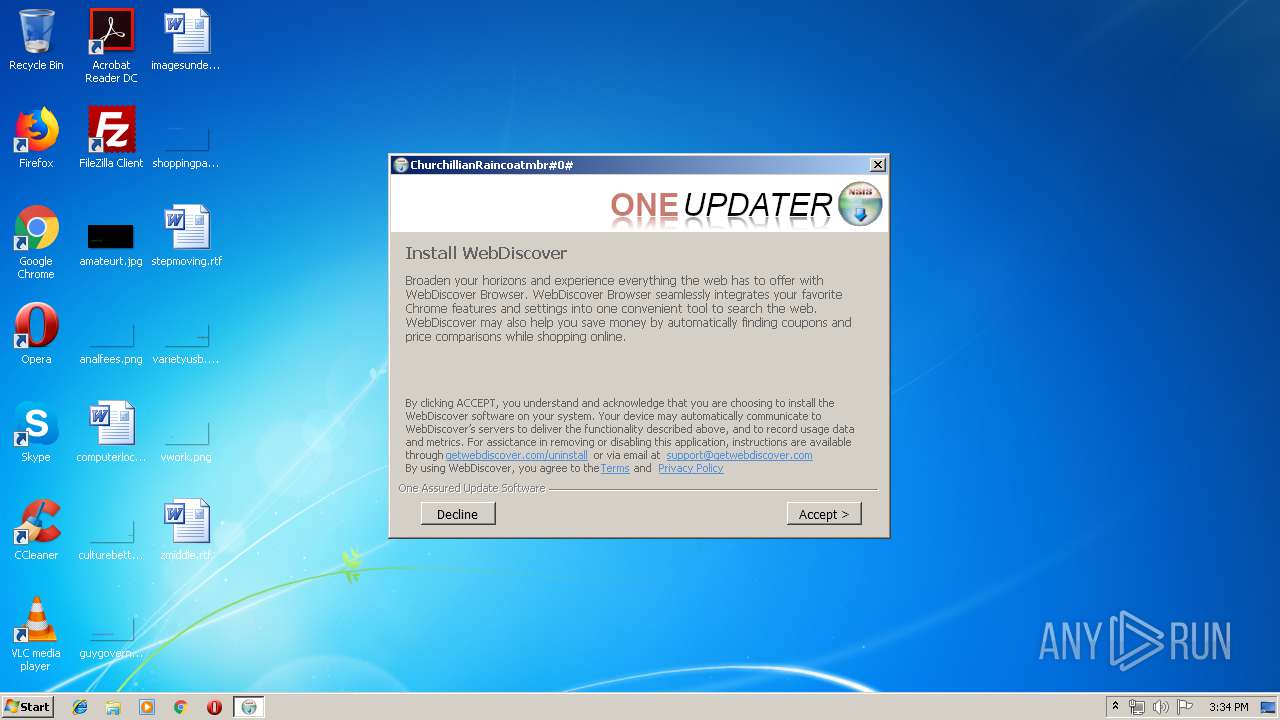
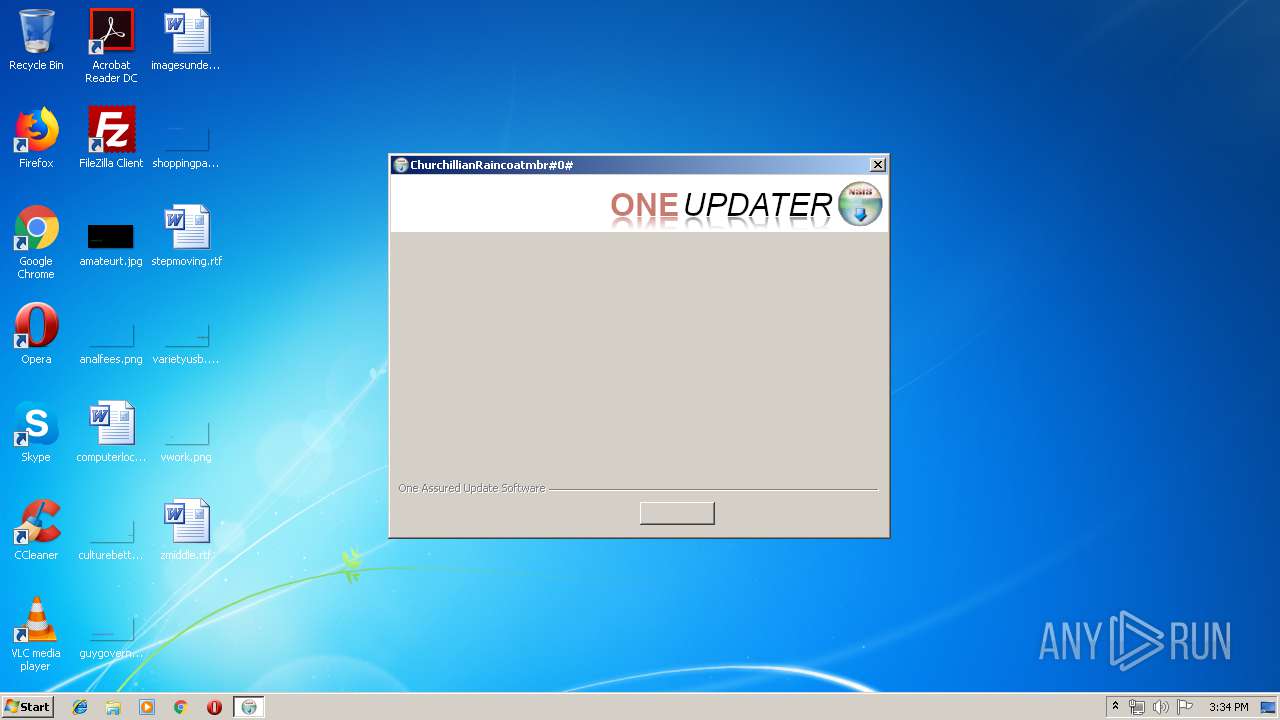
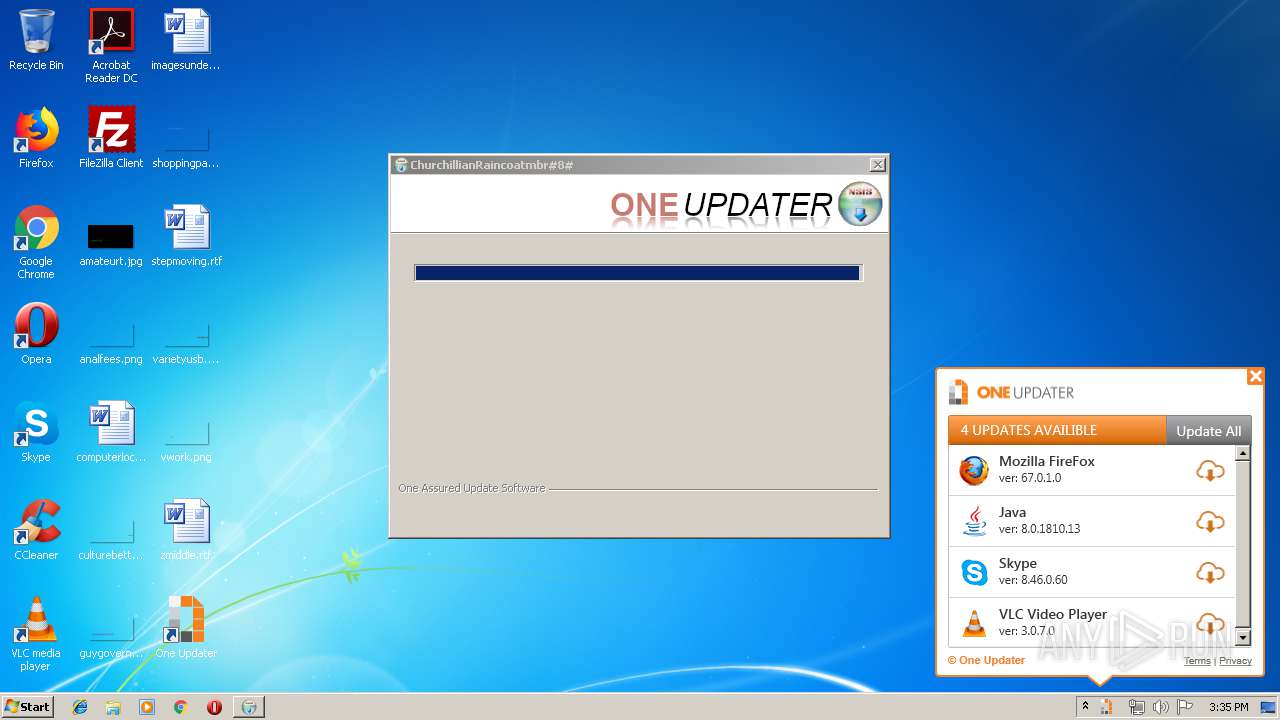
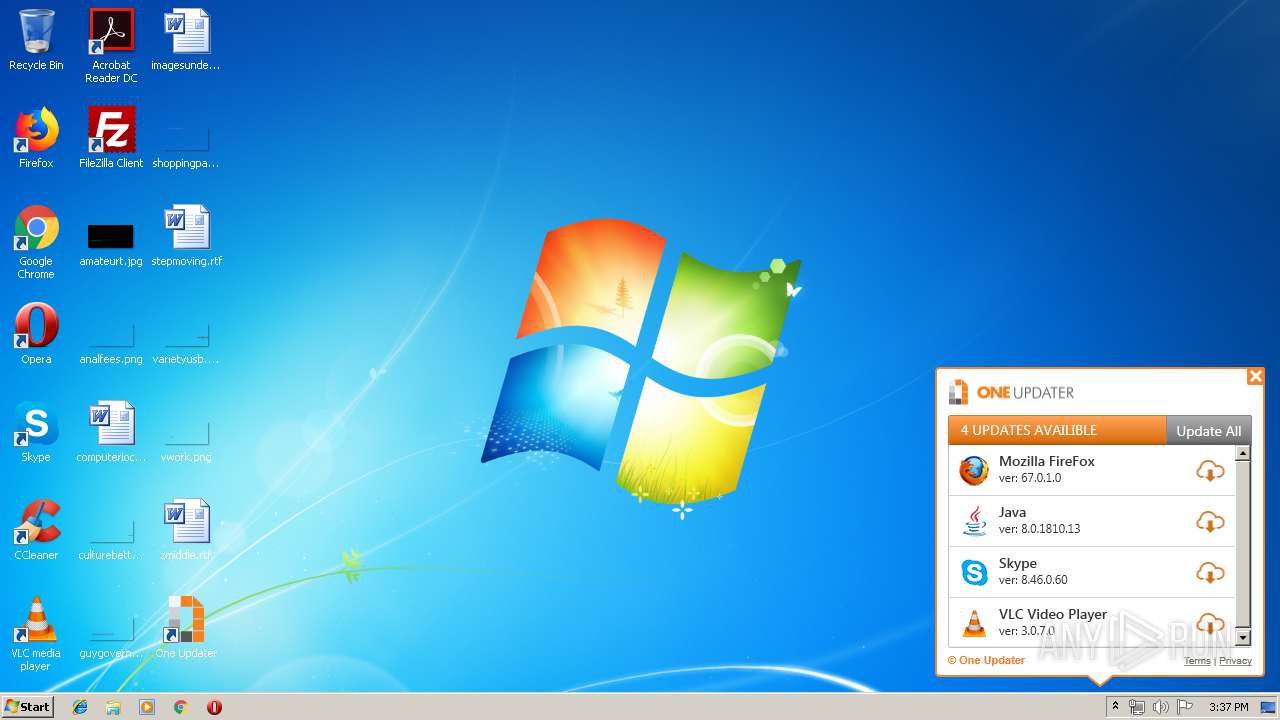
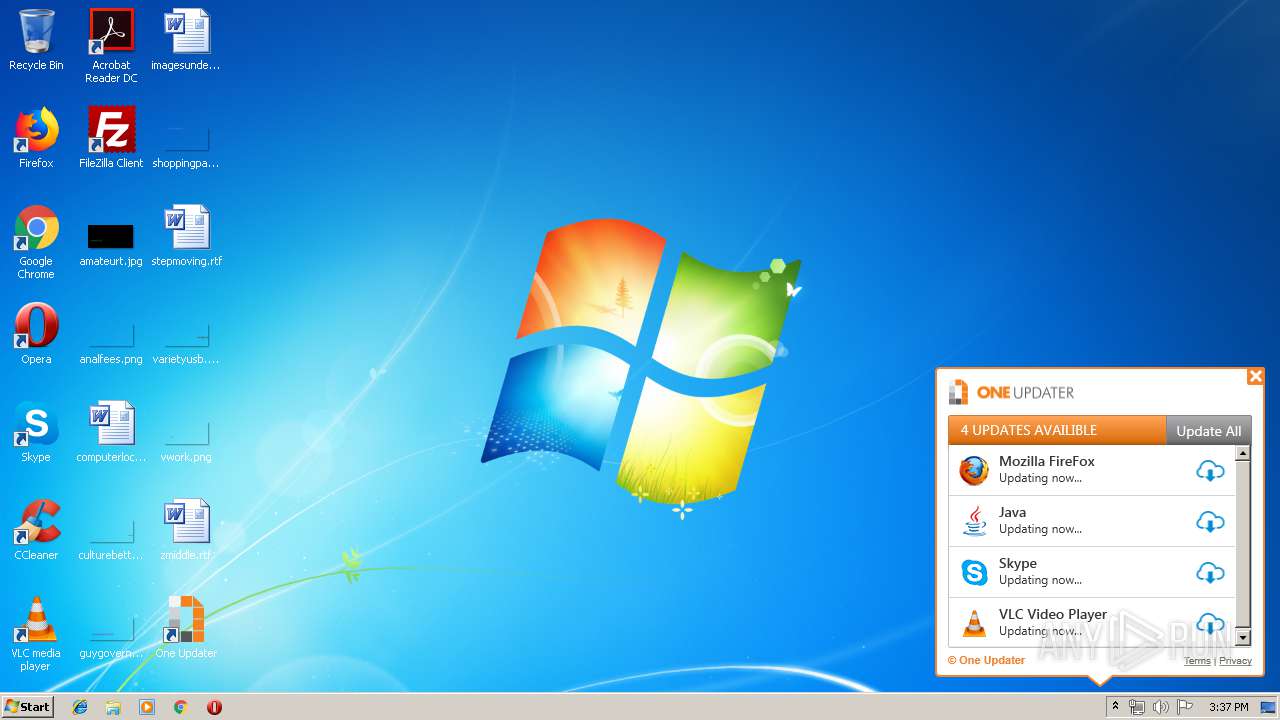
| File name: | ChurchillianRaincoatmbr.exe |
| Full analysis: | https://app.any.run/tasks/de59459f-ec5d-4be3-b370-ad192f53d080 |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2019, 14:33:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 501E0728F4CA6D0E202AA272FA9B37FE |
| SHA1: | B87A61201BE9FDD16A55713511A67B0DF43BEB84 |
| SHA256: | 25D1A466EDDBB946C1E2CBAA6C29941A16983F2DB3E0CD8F8F01D41A5CBECD76 |
| SSDEEP: | 49152:g8/YdgDRxZ9midlrleRCvKkhG6FfD3yNgdYMe8iGNa3G7M3qn:1YdcR/1nxeRoh9b3qO7xwyOqn |
MALICIOUS
Loads dropped or rewritten executable
- ChurchillianRaincoatmbr.exe (PID: 2844)
- ou.exe (PID: 3908)
Changes the autorun value in the registry
- ou.exe (PID: 3908)
Application was dropped or rewritten from another process
- OneUpdater.exe (PID: 920)
- ou.exe (PID: 3908)
SUSPICIOUS
Starts CMD.EXE for commands execution
- ChurchillianRaincoatmbr.exe (PID: 2844)
- cmd.exe (PID: 3896)
- cmd.exe (PID: 2184)
Executable content was dropped or overwritten
- ChurchillianRaincoatmbr.exe (PID: 2844)
- ou.exe (PID: 3908)
Application launched itself
- cmd.exe (PID: 3896)
Creates files in the user directory
- OneUpdater.exe (PID: 920)
- ChurchillianRaincoatmbr.exe (PID: 2844)
- ou.exe (PID: 3908)
Searches for installed software
- OneUpdater.exe (PID: 920)
Reads Environment values
- OneUpdater.exe (PID: 920)
Creates a software uninstall entry
- ou.exe (PID: 3908)
INFO
Dropped object may contain Bitcoin addresses
- ChurchillianRaincoatmbr.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:06:09 13:27:56+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 40960 |
| InitializedDataSize: | 2119680 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x1000 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.1.0 |
| ProductVersionNumber: | 4.0.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | One Assured Update Software |
| FileVersion: | 4.0.1.0 |
| LegalCopyright: | Copyright (C) 2019 JDS Invest Ltd |
| ProductName: | One Assured Update Software |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 09-Jun-2019 11:27:56 |
| Detected languages: |
|
| FileDescription: | One Assured Update Software |
| FileVersion: | 4.0.1.0 |
| LegalCopyright: | Copyright (C) 2019 JDS Invest Ltd |
| ProductName: | One Assured Update Software |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 7 |
| Time date stamp: | 09-Jun-2019 11:27:56 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
0x003A7000 | 0x0001F000 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 | |
.rsrc | 0x003C6000 | 0x001AB000 | 0x001AB000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99768 |
.data | 0x00571000 | 0x00053000 | 0x00052A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.92856 |
.adata | 0x005C4000 | 0x00001000 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21775 | 879 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.9993 | 3752 | UNKNOWN | English - United States | RT_ICON |
3 | 6.24459 | 2216 | UNKNOWN | English - United States | RT_ICON |
4 | 5.01502 | 1384 | UNKNOWN | English - United States | RT_ICON |
5 | 6.16057 | 1128 | UNKNOWN | English - United States | RT_ICON |
6 | 3.34146 | 744 | UNKNOWN | English - United States | RT_ICON |
7 | 3.04232 | 296 | UNKNOWN | English - United States | RT_ICON |
103 | 2.6691 | 104 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.69888 | 548 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.91148 | 248 | UNKNOWN | English - United States | RT_DIALOG |
Imports
advapi32.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
shlwapi.dll |
user32.dll |
version.dll |
Total processes
41
Monitored processes
6
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Users\admin\AppData\Local\One Updater\OneUpdater.exe" | C:\Users\admin\AppData\Local\One Updater\OneUpdater.exe | ou.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: OneUpdater Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2184 | cmd.exe /d /c cmd.exe /d /c IF EXIST "C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe" (start "" "C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe" /S) | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2844 | "C:\Users\admin\AppData\Local\Temp\ChurchillianRaincoatmbr.exe" | C:\Users\admin\AppData\Local\Temp\ChurchillianRaincoatmbr.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: One Assured Update Software Exit code: 0 Version: 4.0.1.0 Modules
| |||||||||||||||
| 3708 | cmd.exe /d /c IF EXIST "C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe" (start "" "C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe" /S) | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3896 | "C:\Windows\System32\cmd.exe" /d /c cmd.exe /d /c cmd.exe /d /c IF EXIST "C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe" (start "" "C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe" /S) | C:\Windows\System32\cmd.exe | — | ChurchillianRaincoatmbr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3908 | "C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe" /S | C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe | cmd.exe | ||||||||||||
User: admin Company: OUpdater © Integrity Level: MEDIUM Description: OUpdater Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
950
Read events
902
Write events
48
Delete events
0
Modification events
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2844) ChurchillianRaincoatmbr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ChurchillianRaincoatmbr_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
7
Suspicious files
0
Text files
17
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | ChurchillianRaincoatmbr.exe | C:\Users\admin\AppData\Local\Temp\nsx3712.tmp\eula.txt | — | |
MD5:— | SHA256:— | |||
| 3908 | ou.exe | C:\Users\admin\AppData\Local\One Updater\OneUpdater.exe | executable | |
MD5:— | SHA256:— | |||
| 2844 | ChurchillianRaincoatmbr.exe | C:\Users\admin\AppData\Local\NullSimple.Updater\ou.exe | executable | |
MD5:— | SHA256:— | |||
| 3908 | ou.exe | C:\Users\admin\AppData\Local\One Updater\uninstall.exe | executable | |
MD5:— | SHA256:— | |||
| 3908 | ou.exe | C:\Users\admin\Desktop\One Updater.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2844 | ChurchillianRaincoatmbr.exe | C:\Users\admin\AppData\Local\NullSimple.Updater\pcapd.exe | text | |
MD5:— | SHA256:— | |||
| 920 | OneUpdater.exe | C:\Users\admin\AppData\Roaming\OneUpdater\OneUpdaterConfig.xml | xml | |
MD5:— | SHA256:— | |||
| 2844 | ChurchillianRaincoatmbr.exe | C:\Users\admin\AppData\Local\Temp\nsx3712.tmp\nsDialogs.dll | executable | |
MD5:2A99D279AC3F7993A5BACDB35062240B | SHA256:BDD97526E02F5F9B18F2CDF97B06C8DCB517BFEAE9070007BA0BF4EDE000E22D | |||
| 2844 | ChurchillianRaincoatmbr.exe | C:\Users\admin\AppData\Local\Temp\nsx3712.tmp\play.wav | wav | |
MD5:9B1C9CB373DC9E6359C703B3B9020A42 | SHA256:57ABAC431F804A14BC4CC5E41B89FDC4B6BE1E682B2AFDFE41AC2348417AEBD9 | |||
| 2844 | ChurchillianRaincoatmbr.exe | C:\Users\admin\AppData\Local\Temp\nsx3712.tmp\accept.ico | image | |
MD5:C1F703873120BB852A901B6313BBAD9C | SHA256:6F2A7202A5E4ADDB1D1BD6DC1704BD2EE14DF229844847B57043545E4A689FE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
40
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
920 | OneUpdater.exe | GET | 200 | 104.24.96.33:80 | http://update.updater.one/version.php?software=ff&version=65.0.2.6995&os=6.1&arch=86&tt=1370656 | US | text | 36 b | malicious |
920 | OneUpdater.exe | GET | 200 | 104.24.96.33:80 | http://update.updater.one/version.php?software=java&version=8.0.920.14&os=6.1&arch=86&tt=1371562 | US | text | 39 b | malicious |
920 | OneUpdater.exe | GET | 200 | 104.24.96.33:80 | http://update.updater.one/update.php?software=ff&version=67.0.1.0&os=6.1&arch=86&tt=1370984 | US | text | 90 b | malicious |
920 | OneUpdater.exe | GET | 200 | 104.24.96.33:80 | http://update.updater.one/update.php?software=vlc&version=3.0.7.0&os=6.1&arch=86&tt=1372375 | US | text | 92 b | malicious |
920 | OneUpdater.exe | GET | 200 | 104.24.96.33:80 | http://update.updater.one/version.php?software=flash&version=26.0.0.131&os=6.1&arch=86&tt=1371265 | US | text | 38 b | malicious |
920 | OneUpdater.exe | GET | 200 | 104.24.96.33:80 | http://update.updater.one/version.php?software=skype&version=8.29.0.50&os=6.1&arch=86&tt=1371890 | US | text | 37 b | malicious |
920 | OneUpdater.exe | GET | 404 | 104.18.43.170:80 | http://opensoftwareupdaterserver.com/installers/firefox_67.0.1.exe | US | html | 3.57 Kb | shared |
920 | OneUpdater.exe | GET | 404 | 104.18.43.170:80 | http://opensoftwareupdaterserver.com/installers/firefox_67.0.1.exe | US | html | 3.57 Kb | shared |
920 | OneUpdater.exe | GET | 404 | 104.18.43.170:80 | http://opensoftwareupdaterserver.com/installers/firefox_67.0.1.exe | US | html | 3.57 Kb | shared |
920 | OneUpdater.exe | GET | 404 | 104.18.43.170:80 | http://opensoftwareupdaterserver.com/installers/firefox_67.0.1.exe | US | html | 3.57 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2844 | ChurchillianRaincoatmbr.exe | 104.25.123.116:443 | appsanctity.com | Cloudflare Inc | US | shared |
920 | OneUpdater.exe | 104.24.96.33:80 | update.updater.one | Cloudflare Inc | US | shared |
920 | OneUpdater.exe | 104.18.43.170:80 | opensoftwareupdaterserver.com | Cloudflare Inc | US | shared |
2844 | ChurchillianRaincoatmbr.exe | 104.25.124.116:443 | appsanctity.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
appsanctity.com |
| malicious |
update.updater.one |
| malicious |
opensoftwareupdaterserver.com |
| unknown |
Threats
Process | Message |
|---|---|
OneUpdater.exe | Load config error: System.InvalidOperationException: There is an error in XML document (0, 0). ---> System.Xml.XmlException: Root element is missing.
at System.Xml.XmlTextReaderImpl.Throw(Exception e)
at System.Xml.XmlTextReaderImpl.ParseDocumentContent()
at System.Xml.XmlTextReaderImpl.Read()
at System.Xml.XmlTextReader.Read()
at System.Xml.XmlReader.MoveToContent()
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderOUSettings.Read3_OUSettings()
--- End of inner exception stack trace ---
at System.Xml.Serialization.XmlSerializer.Deserialize(XmlReader xmlReader, String encodingStyle, XmlDeserializationEvents events)
at System.Xml.Serialization.XmlSerializer.Deserialize(TextReader textReader)
at OneUpdater.Configuration.Config`1.Load()
|
OneUpdater.exe | Load config error: System.InvalidOperationException: There is an error in XML document (0, 0). ---> System.Xml.XmlException: Root element is missing.
at System.Xml.XmlTextReaderImpl.Throw(Exception e)
at System.Xml.XmlTextReaderImpl.ParseDocumentContent()
at System.Xml.XmlTextReaderImpl.Read()
at System.Xml.XmlTextReader.Read()
at System.Xml.XmlReader.MoveToContent()
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderOUSettings.Read3_OUSettings()
--- End of inner exception stack trace ---
at System.Xml.Serialization.XmlSerializer.Deserialize(XmlReader xmlReader, String encodingStyle, XmlDeserializationEvents events)
at System.Xml.Serialization.XmlSerializer.Deserialize(TextReader textReader)
at OneUpdater.Configuration.Config`1.Load()
|
OneUpdater.exe | Load config error: System.InvalidOperationException: There is an error in XML document (0, 0). ---> System.Xml.XmlException: Root element is missing.
at System.Xml.XmlTextReaderImpl.Throw(Exception e)
at System.Xml.XmlTextReaderImpl.ParseDocumentContent()
at System.Xml.XmlTextReaderImpl.Read()
at System.Xml.XmlTextReader.Read()
at System.Xml.XmlReader.MoveToContent()
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderOUSettings.Read3_OUSettings()
--- End of inner exception stack trace ---
at System.Xml.Serialization.XmlSerializer.Deserialize(XmlReader xmlReader, String encodingStyle, XmlDeserializationEvents events)
at System.Xml.Serialization.XmlSerializer.Deserialize(TextReader textReader)
at OneUpdater.Configuration.Config`1.Load()
|
OneUpdater.exe | Load config error: System.InvalidOperationException: There is an error in XML document (0, 0). ---> System.Xml.XmlException: Root element is missing.
at System.Xml.XmlTextReaderImpl.Throw(Exception e)
at System.Xml.XmlTextReaderImpl.ParseDocumentContent()
at System.Xml.XmlTextReaderImpl.Read()
at System.Xml.XmlTextReader.Read()
at System.Xml.XmlReader.MoveToContent()
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderOUSettings.Read3_OUSettings()
--- End of inner exception stack trace ---
at System.Xml.Serialization.XmlSerializer.Deserialize(XmlReader xmlReader, String encodingStyle, XmlDeserializationEvents events)
at System.Xml.Serialization.XmlSerializer.Deserialize(TextReader textReader)
at OneUpdater.Configuration.Config`1.Load()
|