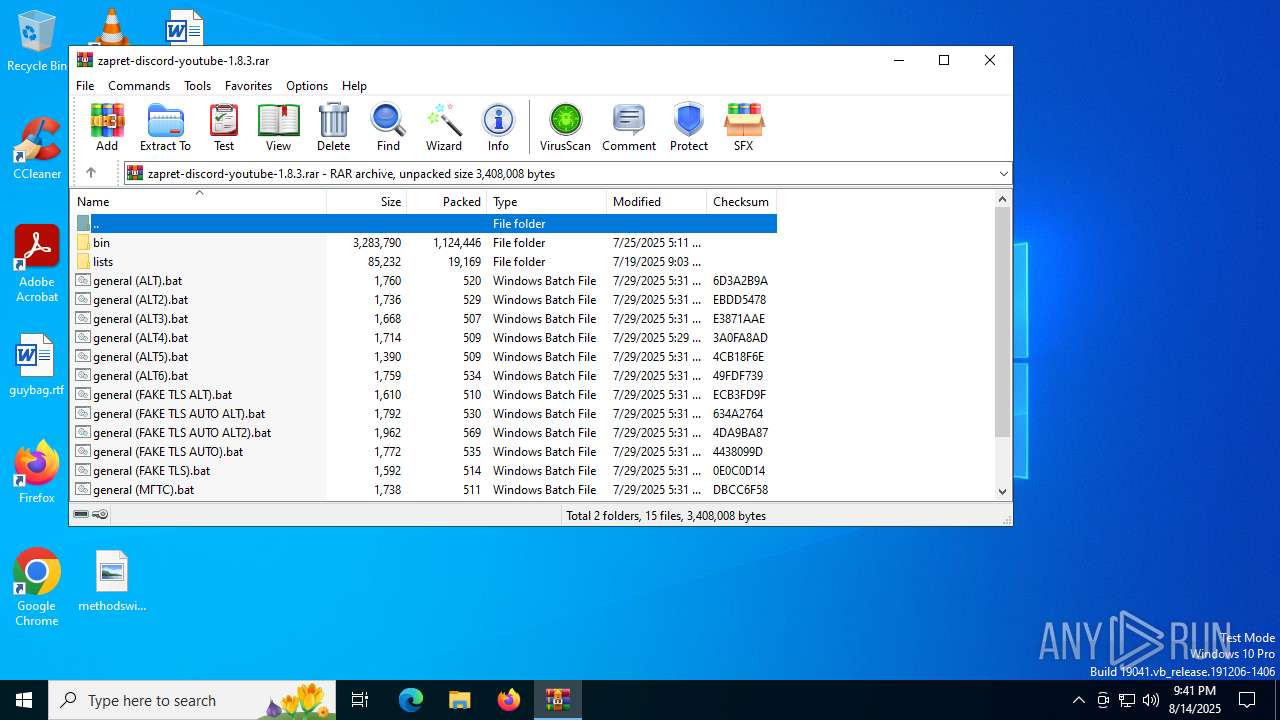
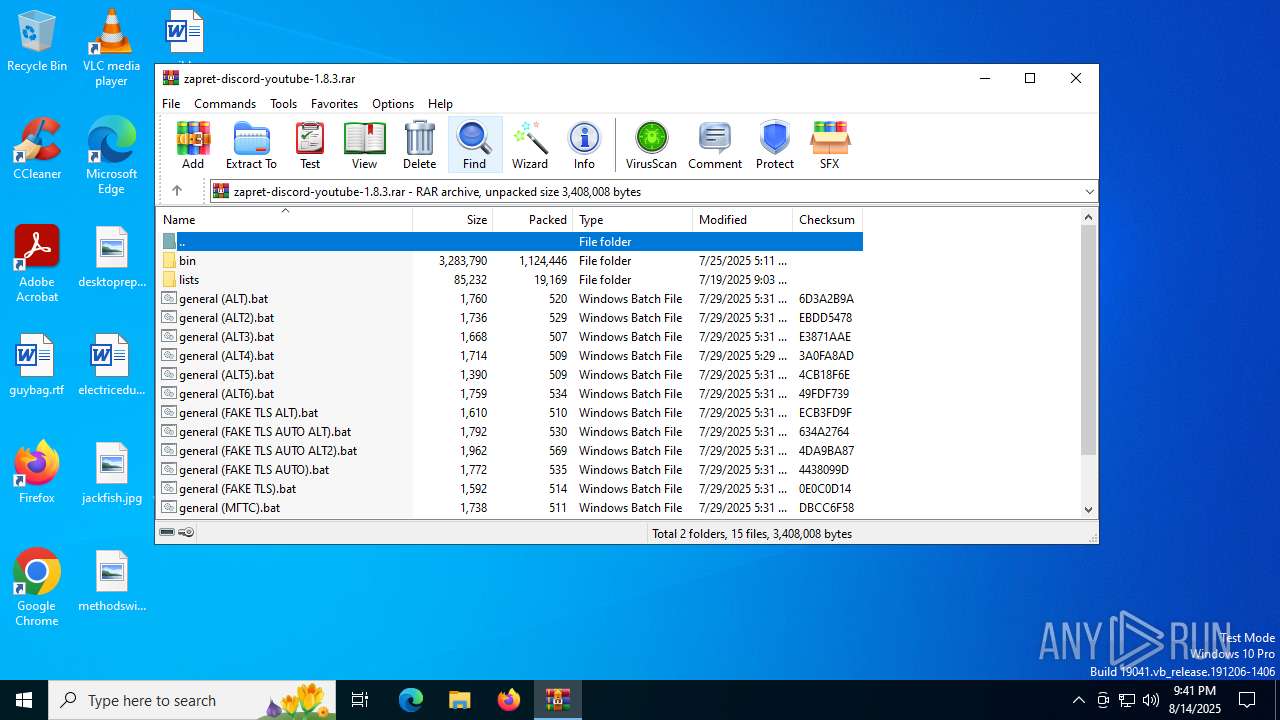
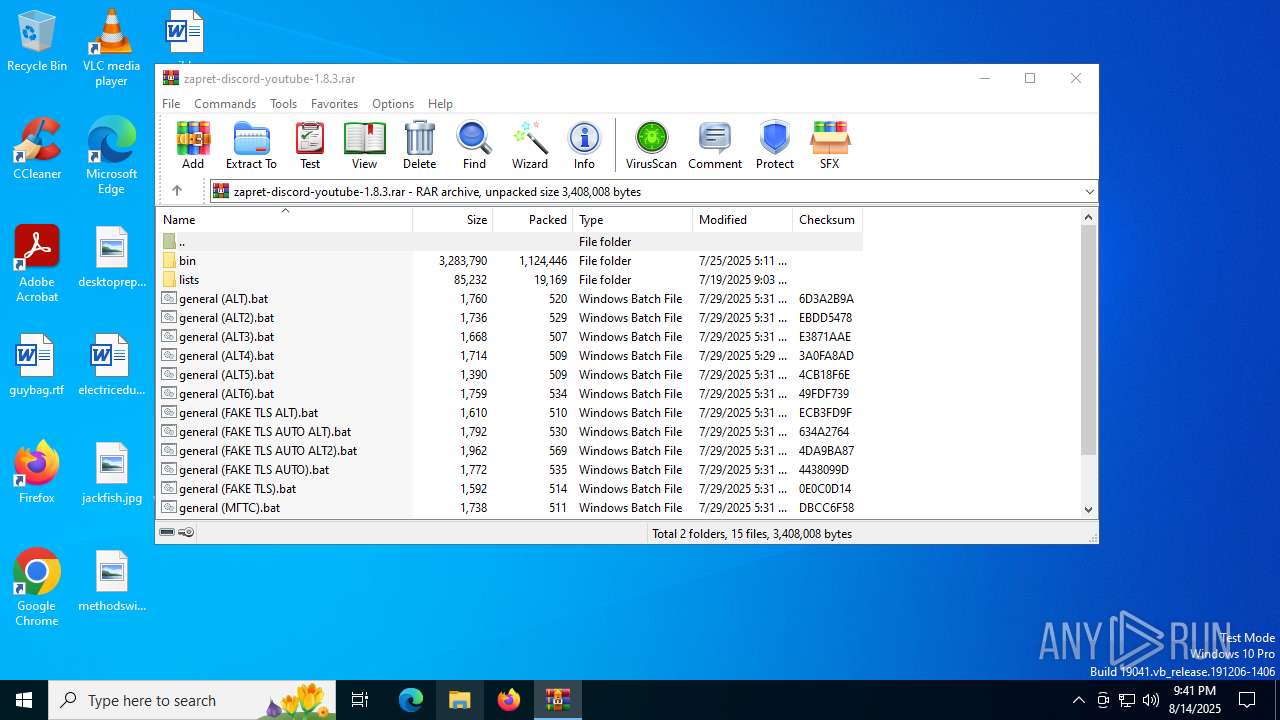
| File name: | zapret-discord-youtube-1.8.3.rar |
| Full analysis: | https://app.any.run/tasks/8499e3d9-b425-4d18-87d3-cb580acfb6ae |
| Verdict: | Malicious activity |
| Analysis date: | August 14, 2025, 21:41:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D0C054F3AFA7DDC996E714FE06610FE2 |
| SHA1: | 4D33D74455ACFB1CE079742B1FB3A704A3BC8998 |
| SHA256: | 25B65A8BFDC13EC0C99DF2A0496870E56AD87E2FE4B7D105CEBD388DBA05E635 |
| SSDEEP: | 49152:Ib4FMyNCQMf5udb/DNj7Ze9rm45sDC69wDe1fwTCFvppsBS9VWIwQtkcTa8ZM1Mk:Ib4utV58b/Jj789rv5D6uDefjFvppr9a |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 6232)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6232)
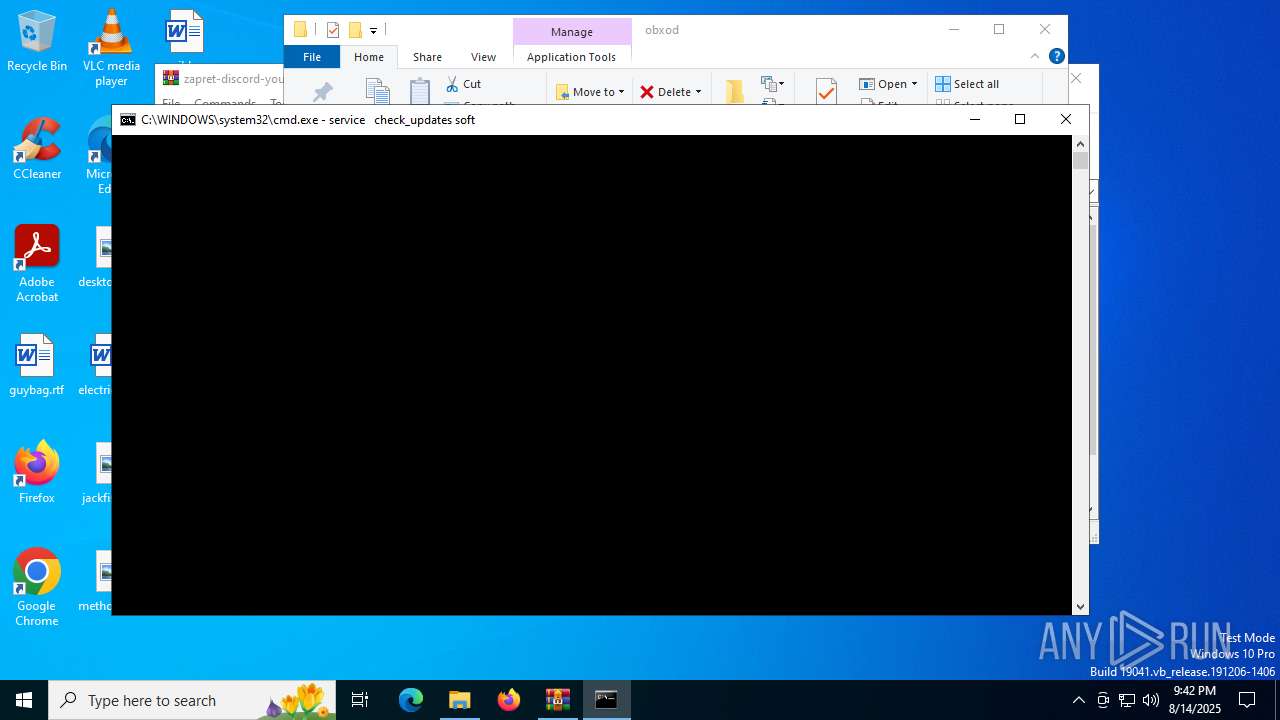
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4060)
- cmd.exe (PID: 7052)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5884)
Starts application with an unusual extension
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4060)
Hides command output
- cmd.exe (PID: 892)
Application launched itself
- cmd.exe (PID: 4060)
- cmd.exe (PID: 7052)
Starts SC.EXE for service management
- cmd.exe (PID: 5884)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 892)
Windows service management via SC.EXE
- sc.exe (PID: 4540)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6232)
Checks supported languages
- chcp.com (PID: 6176)
- chcp.com (PID: 768)
- winws.exe (PID: 4512)
- chcp.com (PID: 6540)
Changes the display of characters in the console
- cmd.exe (PID: 7052)
- cmd.exe (PID: 4060)
The sample compiled with english language support
- WinRAR.exe (PID: 6232)
Disables trace logs
- powershell.exe (PID: 5724)
Checks proxy server information
- slui.exe (PID: 5824)
- powershell.exe (PID: 5724)
Reads the software policy settings
- slui.exe (PID: 5824)
Reads the computer name
- winws.exe (PID: 4512)
Manual execution by a user
- cmd.exe (PID: 4060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 534 |
| UncompressedSize: | 1759 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | general (ALT6).bat |
Total processes
161
Monitored processes
18
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Users\admin\Documents\obxod\bin\winws.exe" --wf-tcp=80,443,12 --wf-udp=443,50000-50100,12 --filter-udp=443 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --new --filter-udp=50000-50100 --filter-l7=discord,stun --dpi-desync=fake --dpi-desync-repeats=6 --new --filter-tcp=80 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake,multisplit --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake,multidisorder --dpi-desync-split-pos=midsld --dpi-desync-repeats=8 --dpi-desync-fooling=md5sig,badseq --new --filter-udp=443 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --new --filter-tcp=80 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake,multisplit --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443,12 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake,multidisorder --dpi-desync-split-pos=midsld --dpi-desync-repeats=6 --dpi-desync-fooling=md5sig,badseq --new --filter-udp=12 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake --dpi-desync-autottl=2 --dpi-desync-repeats=10 --dpi-desync-any-protocol=1 --dpi-desync-fake-unknown-udp="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --dpi-desync-cutoff=n2 | C:\Users\admin\Documents\obxod\bin\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 768 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | C:\WINDOWS\system32\cmd.exe /c powershell -command "(Invoke-WebRequest -Uri \"https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/main/.service/version.txt\" -Headers @{\"Cache-Control\"=\"no-cache\"} -TimeoutSec 5).Content.Trim()" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2188 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Documents\obxod\general.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4512 | "C:\Users\admin\Documents\obxod\bin\winws.exe" --wf-tcp=80,443,12 --wf-udp=443,50000-50100,12 --filter-udp=443 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --new --filter-udp=50000-50100 --filter-l7=discord,stun --dpi-desync=fake --dpi-desync-repeats=6 --new --filter-tcp=80 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake,multisplit --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake,multidisorder --dpi-desync-split-pos=midsld --dpi-desync-repeats=8 --dpi-desync-fooling=md5sig,badseq --new --filter-udp=443 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --new --filter-tcp=80 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake,multisplit --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443,12 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake,multidisorder --dpi-desync-split-pos=midsld --dpi-desync-repeats=6 --dpi-desync-fooling=md5sig,badseq --new --filter-udp=12 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake --dpi-desync-autottl=2 --dpi-desync-repeats=10 --dpi-desync-any-protocol=1 --dpi-desync-fake-unknown-udp="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --dpi-desync-cutoff=n2 | C:\Users\admin\Documents\obxod\bin\winws.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4540 | sc query "zapret" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4916 | "C:\Users\admin\Documents\obxod\bin\winws.exe" --wf-tcp=80,443,12 --wf-udp=443,50000-50100,12 --filter-udp=443 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --new --filter-udp=50000-50100 --filter-l7=discord,stun --dpi-desync=fake --dpi-desync-repeats=6 --new --filter-tcp=80 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake,multisplit --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="C:\Users\admin\Documents\obxod\lists\list-general.txt" --dpi-desync=fake,multidisorder --dpi-desync-split-pos=midsld --dpi-desync-repeats=8 --dpi-desync-fooling=md5sig,badseq --new --filter-udp=443 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --new --filter-tcp=80 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake,multisplit --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443,12 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake,multidisorder --dpi-desync-split-pos=midsld --dpi-desync-repeats=6 --dpi-desync-fooling=md5sig,badseq --new --filter-udp=12 --ipset="C:\Users\admin\Documents\obxod\lists\ipset-all.txt" --dpi-desync=fake --dpi-desync-autottl=2 --dpi-desync-repeats=10 --dpi-desync-any-protocol=1 --dpi-desync-fake-unknown-udp="C:\Users\admin\Documents\obxod\bin\quic_initial_www_google_com.bin" --dpi-desync-cutoff=n2 | C:\Users\admin\Documents\obxod\bin\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5724 | powershell -command "(Invoke-WebRequest -Uri \"https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/main/.service/version.txt\" -Headers @{\"Cache-Control\"=\"no-cache\"} -TimeoutSec 5).Content.Trim()" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 451
Read events
11 422
Write events
16
Delete events
13
Modification events
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zapret-discord-youtube-1.8.3.rar | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6232) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
3
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\bin\cygwin1.dll | executable | |
MD5:A1C82ED072DC079DD7851F82D9AA7678 | SHA256:103104A52E5293CE418944725DF19E2BF81AD9269B9A120D71D39028E821499B | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\service.bat | text | |
MD5:67D38E9FB323022E8BB94D59A1E071DB | SHA256:95D6FC245EAF5F2A9F3E213A1AAD5D4453817F4B95249B6D889EC8BC3EE059E1 | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\general (FAKE TLS AUTO ALT2).bat | text | |
MD5:52DD8CA5A2D5E52DE28049269820B6AD | SHA256:5F468943D3CAD3EC9CB3FA51BCB5E26B4D96697370DCA3C550611CE07F5C0C07 | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\general (FAKE TLS AUTO).bat | text | |
MD5:84F88648F6B2D68B88E0325FD40F8429 | SHA256:08A95CB237E4D4A5C753E7F8D21AEFDBBC79976F242533D3E18272E763AC3ECF | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\general (FAKE TLS AUTO ALT).bat | text | |
MD5:FCF903E5FEDD675E6BE4E4E7E5CD23F9 | SHA256:FED65F9CC99F13F6AC95F93C08DB259E2B33B5DEE5BEED8C81CBDEC3BADF68D3 | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\general (ALT6).bat | text | |
MD5:A896910E928258719F7F5F22316A5BDD | SHA256:6C6BFB8BB7606181D91B3F6C13C789C4663DE47265B26217D53424BAA0CCCE85 | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\general (FAKE TLS ALT).bat | text | |
MD5:C203A7AB6B85AFF6943E42448B099F87 | SHA256:8B160DA9CE0ED064B2A212C50A5B6CEE4DA04BF41DAB2F02F4B70BEE68D70F29 | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\general (ALT2).bat | text | |
MD5:779EB1CC5877DD178ED4E05C96870039 | SHA256:76BD39660FC381E4D503CD3E58E2E4450C835F5A2937D2265D7E2981FCB0336E | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\general (FAKE TLS).bat | text | |
MD5:DCA4E32491E58815FBC3A0D4C0C1C349 | SHA256:3E0FD76E3BB65F65A692A3E40DEF8ED2E89437BF63E0FB1BD8A075213A5702C2 | |||
| 6232 | WinRAR.exe | C:\Users\admin\Documents\obxod\bin\WinDivert64.sys | executable | |
MD5:89ED5BE7EA83C01D0DE33D3519944AA5 | SHA256:8DA085332782708D8767BCACE5327A6EC7283C17CFB85E40B03CD2323A90DDC2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
23
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.27:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2528 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4400 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4400 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4 | System | GET | 200 | 104.76.201.34:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2348 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2288 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.27:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |